Howdy,
I run a Private Certificate Authority for my personal use and just to learn about SSL Certs. However, with the current build of FireFox I’m on ( 31 ) I can no longer visit sites I’ve secured with SSL Certs signed by this certificate authority, even though these SSL certs work just perfectly fine in Chrome and Internet Explorer. I keep getting a «sec_error_inadequate_cert_type» error. I can only assume that the certs I’ve been issuing are incorrect in some way, but the error is so vague and the error page doesn’t specify more.
I only discovered this when I realized some of my SSL certs had expired, and I went to re-issue them.
One of the certs that hasn’t expired yet but is experiencing problems can be found here:
- https://forums.silicateillusion.org
One of the Certs I’ve tried re-issuing, matching fields included as closely as I can to a Google SSL cert that I looked up is here:
- https://phpmyadmin.endofevolution.com
These certificates were generated using the application called SimpleAuthority, found here: http://simpleauthority.com/
A Site like Networking4All.com seems to believe the Certs are valid, excepting the CA that is Self Signed: http://www.networking4all.com/en/support/tools/site+check/report/?fqdn=phpmyadmin.endofevolution.com&protocol=https
Interestingly enough, using a different site like SSLShopper shows an error similar to FF31: http://www.sslshopper.com/ssl-checker.html#hostname=https://phpmyadmin.endofevolution.com
The certs are running on an Apache Web server: Apache/2.2.21 (Win32) mod_ssl/2.2.21 OpenSSL/1.0.0e PHP/5.3.10
The CA Cert is in FireFox’s store as trusted.
If needed, I can provide certs.
Howdy,
I run a Private Certificate Authority for my personal use and just to learn about SSL Certs. However, with the current build of FireFox I’m on ( 31 ) I can no longer visit sites I’ve secured with SSL Certs signed by this certificate authority, even though these SSL certs work just perfectly fine in Chrome and Internet Explorer. I keep getting a «sec_error_inadequate_cert_type» error. I can only assume that the certs I’ve been issuing are incorrect in some way, but the error is so vague and the error page doesn’t specify more.
I only discovered this when I realized some of my SSL certs had expired, and I went to re-issue them.
One of the certs that hasn’t expired yet but is experiencing problems can be found here:
* https://forums.silicateillusion.org
One of the Certs I’ve tried re-issuing, matching fields included as closely as I can to a Google SSL cert that I looked up is here:
* https://phpmyadmin.endofevolution.com
These certificates were generated using the application called SimpleAuthority, found here: http://simpleauthority.com/
A Site like Networking4All.com seems to believe the Certs are valid, excepting the CA that is Self Signed: http://www.networking4all.com/en/support/tools/site+check/report/?fqdn=phpmyadmin.endofevolution.com&protocol=https
Interestingly enough, using a different site like SSLShopper shows an error similar to FF31: http://www.sslshopper.com/ssl-checker.html#hostname=https://phpmyadmin.endofevolution.com
The certs are running on an Apache Web server: Apache/2.2.21 (Win32) mod_ssl/2.2.21 OpenSSL/1.0.0e PHP/5.3.10
The CA Cert is in FireFox’s store as trusted.
If needed, I can provide certs.
Выбранное решение
I discovered the problem: The CA Certificate I was using had extended usage included.
Refer to Bug: 1049176
I confirmed this by generating a new test CA with the the extended usage field excluded, then generating a new SSL Cert The certificate verifies properly now.
While I am relieved I have figured out what the problem is, being so vague with the error message is making me lean towards another browser for primary usage. The fact it took me 4 days and an extremely large amount of work to figure out why this was occurring was unacceptable, all because the error description was generic and included absolutely no details what so ever.
Прочитайте этот ответ в контексте
👍 2
Содержание
- Sec error inadequate cert type
- Полезная информация
- №1 26-06-2008 17:39:56
- Ошибка сертификата при подключении по https
- №2 26-06-2008 17:45:32
- Re: Ошибка сертификата при подключении по https
- №3 27-06-2008 09:09:43
- Re: Ошибка сертификата при подключении по https
- №4 27-06-2008 10:26:41
- Re: Ошибка сертификата при подключении по https
- №5 30-06-2008 10:30:54
- Re: Ошибка сертификата при подключении по https
- №6 05-07-2008 01:03:29
- Re: Ошибка сертификата при подключении по https
- Sec error inadequate cert type
- Выбранное решение
- Все ответы (6)
- Выбранное решение
- SecurityEngineering/x509Certs
- Contents
- A Web PKI x509 Certificate Primer
- Extensions
- Subject Alternate Name
- Basic Constraints
- Key Usage
- Extended Key Usages
- Name Constraints
- Authority Information Access
- Self Signed Certs
- CAs Included in Firefox
- Running your Own CA
- Generate your CA Root
- Generate your Intermediate cert
- Generate the end entity certificate
- Error Codes in Firefox
Sec error inadequate cert type
Полезная информация
Страницы: 1
№1 26-06-2008 17:39:56
Ошибка сертификата при подключении по https
При попытке подключиться к файрволу D-Link DFL-210 по протоколу https выдается страница со следующей ошибкой:
«Ошибка при установлении защищенного соединения. При соединении с 192.168.1.1:444 произошла ошибка. Этот тип сертификата не одобрен для приложения. (Код ошибки: sec_error_inadequate_cert_type)«.
Я понимаю, что в устройстве прописан неверный сертификат (вернее, сертификат с неверными параметрами), однако это устройство не имеет возможности управлять параметрами сертификата, а подключиться к нему очень хочется. Можно ли как-нибудь обойти эту ошибку?
№2 26-06-2008 17:45:32
Re: Ошибка сертификата при подключении по https
tdr
Скорее всего нет. Разве что поискать прошивку поновее или использовать другой браузер (IE точно такие ошибки игнорирует). Ошибка очень серьезная — перепутаны роли сертификата (вместо серверного сделан клиентский, что является грубым нарушением).
Все микробы умрут
№3 27-06-2008 09:09:43
Re: Ошибка сертификата при подключении по https
Это конечно понятно, но почему бы не отдать такую ситуацию на откуп пользователя, пусть он сам решает, идти дальше, или отказаться. Мне кажется это более логично, чем просто блокировать доступ без вариантов.
№4 27-06-2008 10:26:41
Re: Ошибка сертификата при подключении по https
tdr
С безопасностью не шутят.
Все микробы умрут
№5 30-06-2008 10:30:54
Re: Ошибка сертификата при подключении по https
Просмотрел свойства сертификата на устройстве и вот что получилось:
CommonName совпадает с адресом устройства (CN=192.168.1.1), по срокам ключ валиден, роль сертификата «Проверка подлинности сервера (1.3.6.1.5.5.7.3.1)», использование ключа «Цифровая подпись, Шифрование ключей, Шифрование данных, Согласование ключей, Подписывание сертификатов, Автономное подписание списка отзыва (CRL), Подписывание списка отзыва (CRL)», сертификат самоподписанный. Так что же заставляет ФФ3 выдавать ошибку «»Ошибка при установлении защищенного соединения. При соединении с 192.168.1.1:444 произошла ошибка. Этот тип сертификата не одобрен для приложения. (Код ошибки: sec_error_inadequate_cert_type)».» и блокировать доступ к устройству?
№6 05-07-2008 01:03:29
Re: Ошибка сертификата при подключении по https
tdr
Если считаете, что это баг, то вам в https://bugzilla.mozilla.org/enter_bug.cgi
Do not meddle in the affairs of Wizards, for they are subtle and quick to anger.
Источник
Sec error inadequate cert type
I run a Private Certificate Authority for my personal use and just to learn about SSL Certs. However, with the current build of FireFox I’m on ( 31 ) I can no longer visit sites I’ve secured with SSL Certs signed by this certificate authority, even though these SSL certs work just perfectly fine in Chrome and Internet Explorer. I keep getting a «sec_error_inadequate_cert_type» error. I can only assume that the certs I’ve been issuing are incorrect in some way, but the error is so vague and the error page doesn’t specify more.
I only discovered this when I realized some of my SSL certs had expired, and I went to re-issue them.
One of the certs that hasn’t expired yet but is experiencing problems can be found here:
One of the Certs I’ve tried re-issuing, matching fields included as closely as I can to a Google SSL cert that I looked up is here:
These certificates were generated using the application called SimpleAuthority, found here: http://simpleauthority.com/
Interestingly enough, using a different site like SSLShopper shows an error similar to FF31: http://www.sslshopper.com/ssl-checker.html#hostname=https://phpmyadmin.endofevolution.com
The certs are running on an Apache Web server: Apache/2.2.21 (Win32) mod_ssl/2.2.21 OpenSSL/1.0.0e PHP/5.3.10
The CA Cert is in FireFox’s store as trusted.
If needed, I can provide certs.
Выбранное решение
I discovered the problem: The CA Certificate I was using had extended usage included.
I confirmed this by generating a new test CA with the the extended usage field excluded, then generating a new SSL Cert The certificate verifies properly now.
While I am relieved I have figured out what the problem is, being so vague with the error message is making me lean towards another browser for primary usage. The fact it took me 4 days and an extremely large amount of work to figure out why this was occurring was unacceptable, all because the error description was generic and included absolutely no details what so ever.
Все ответы (6)
I get this error in Google Chrome as well.
Current Firefox releases no longer allow to add an exception with the switch to PKIX. You would have to disable PKIX temporarily when visiting a site that doesn’t work with it.
Note that you won’t be able to do this with the next 33 Firefox version as support for this pref has been removed.
- Bug 975229 — Remove NSS-based certificate verification
There are more changes to certificates, see:
Изменено 10 сентября 2014 г., 20:33:57 -0700 cor-el
I however, do not. It’s something specific to Firefox I seem to be having. Maybe I’m running an outdated version of Chrome? Which would be hard seeing as chrome itself says it’s up to date: Version 37.0.2062.120 m
I appreciate the link to Bug 1034124, However the SSL certificate itself IS NOT self signed. Only the CA is, which signed the SSL Cert. I guess what I mean to be asking is. Is Firefox Rejecting my SSL Cert, because my CA Is Self Signed?
I also offer the CA Cert for download since no one would have the cert in their stores. Would this also affect it?
I’ve attached a screen shot of the error I’m getting so that it’s available for the ticket. The following is also the «plaintext» verison of the error I’m getting:
«Certificate type not approved for application.»
I finally found a tool online that will show me the guts of the certificate: http://certlogik.com/ssl-checker/phpmyadmin.endofevolution.com/
Everything seems to be good.
Выбранное решение
I discovered the problem: The CA Certificate I was using had extended usage included.
I confirmed this by generating a new test CA with the the extended usage field excluded, then generating a new SSL Cert The certificate verifies properly now.
While I am relieved I have figured out what the problem is, being so vague with the error message is making me lean towards another browser for primary usage. The fact it took me 4 days and an extremely large amount of work to figure out why this was occurring was unacceptable, all because the error description was generic and included absolutely no details what so ever.
I however, do not. It’s something specific to Firefox I seem to be having. Maybe I’m running an outdated version of Chrome? Which would be hard seeing as chrome itself says it’s up to date: Version 37.0.2062.120 m I appreciate the link to Bug 1034124, However the SSL certificate itself IS NOT self signed. Only the CA is, which signed the SSL Cert. I guess what I mean to be asking is. Is Firefox Rejecting my SSL Cert, because my CA Is Self Signed? I also offer the CA Cert for download since no one would have the cert in their stores. Would this also affect it? I’ve attached a screen shot of the error I’m getting so that it’s available for the ticket. The following is also the «plaintext» verison of the error I’m getting: «Certificate type not approved for application.»
I however, do not. It’s something specific to Firefox I seem to be having. Maybe I’m running an outdated version of Chrome? Which would be hard seeing as chrome itself says it’s up to date: Version 37.0.2062.120 m I appreciate the link to Bug 1034124, However the SSL certificate itself IS NOT self signed. Only the CA is, which signed the SSL Cert. I guess what I mean to be asking is. Is Firefox Rejecting my SSL Cert, because my CA Is Self Signed? I also offer the CA Cert for download since no one would have the cert in their stores. Would this also affect it? I’ve attached a screen shot of the error I’m getting so that it’s available for the ticket. The following is also the «plaintext» verison of the error I’m getting: «Certificate type not approved for application.»
I had the same issue, what i did was, copy two cert from your computer 1 is trusted rootCA cert 2.root CA1 from mmc console save those two cert into local computer then import it into mozilla firefox, under options->Advanced-> Certificates->view certificate->authorities->import-> restart it should work
Изменено 16 февраля 2015 г., 23:48:37 -0800 Brad
Источник
SecurityEngineering/x509Certs
Contents
A Web PKI x509 Certificate Primer
X.509 (in this document referred as x509) is an ITU standard to describe certificates. Three versions of the x509 standard have been defined for web-pki. In this document we will be referring to the current standard in use for web pki: x509 v3, which is described in detail in RFC 5280. In general x509 certificates bind a signature to a validity period, a public key, a subject, an issuer, and a set of extensions. The extensions define extra properties of the certificate such as extra attributes of the certificate or constraints on the use of the certificate. In order for a certificate to be valid these three requirements must be met:
- There is a verification path from the site certificate to a trusted certificate of the user agent (ie if you follow the issuer path you will end on a self-signed certificate that is considered trusted by the browser).
- The attributes of the certificates in the verification path have valid parameters for that verification (for example the validity period of all the certificates are valid for the time the verification is being done)
- Revocation checks are considered OK for that particular validation.
One issue that is not commonly known is that the x509 trust graph is not a forest (a bunch of trees where each root is a trusted root) but a cyclic graph, where the same key/issuer can be a root or an intermediate for another root in the browsers key store (when roots create intermediates for each other it is called cross-signing).
Extensions
While RFC 5280 defines 16 extensions for webpki in this document we will be describing the six extensions we considered critical for understanding. Certificates can have other extensions not described on RFC 5280, but that is out of the scope of this document. Extensions can be marked as critical or non-critical, conforming certificate verification libraries should stop processing verification when encountering a critical extension that they do not understand ( and should continue prococessing if the extension is marked as non-critical) mozila::pkix has this behavior.
Subject Alternate Name
This extension defines what other names (such as DNS names) are valid for this certificate. This allows for a certificate to be used for more than one FQDN, for example you can have a certificate that is valid for both a.example.com and b.example.com
Basic Constraints
This allows certificates to be asserted as issuing certificates (it is mandatory for CA certificates). It can also be used to express the maximum depth of the trust path from the CA.
Key Usage
This extension is used to constrain the purpose for the key in the certificate. More than one key usage can be asserted. Examples of key usages are: digitalSginature, keyEncipherement, dataEncipherement, keyCertSig, crlSign. For CA certificates the keyCertSign bit MUST be asserted.
Extended Key Usages
This is another bitfield to constrain the usages of the key of the certificate. Its is directed mostly at what type of application the certificate was issued for. Examples of extended key usages are: serverAuth, clientAutn and OCSPSigning. For end-entity certificates for PKI this extension is required to exist with the serverAuth bit asserted.
Name Constraints
This is an extension exclusive for CA and indicates limits on the name space for its children. This is one of the most powerful extensions for businesses to have to help limit risk imposed by losing the private key of the CA.
This extension is primarily used to to describe the OCSP location for revocation checking. It is mandatory for certificates that chain up to a root in the Mozilla CA program.
Self Signed Certs
These are the steps to generate a certificate for www.example.com. Replace this value with the actual server name in the steps below.
1. Generate key:
«openssl genpkey -algorithm RSA -out key.pem -pkeyopt rsa_keygen_bits: 2048»
2048 is considered secure for the next 4 years.
«openssl req -new -key key.pem -days 1096 -extensions v3_ca -batch -out example.csr — utf8 -subj ‘/CN=www.example.com’
Make a new Certificate Signing Request (CSR) that will be valid for 3 years.
3. Write extensions file (make a new file with name openssl.ss.cnf with the following contents)
basicConstraints = CA:FALSE
subjectAltName =DNS:www.example.com
extendedKeyUsage =serverAuth
4. Self-sign csr (using SHA256) and append the extensions described in the file
«openssl x509 -req -sha256 -days 3650 -in example.csr -signkey key.pem -set-serial $ANY_INTEGER -extfile openssl.ss.cnf -out example.pem»
You can now use example.pem as your certfile
CAs Included in Firefox
When you visit a secure website, Firefox will validate the website’s certificate by checking that the certificate that signed it is valid, and checking that the certificate that signed the parent certificate is valid and so forth up to a root certificate that is known to be valid. This chain of certificates is called the Certificate Hierarchy.
If your certificates will only be used to verify one domain (e.g. *.yourcompany.com) but you want others outside of your organization to be able to browse to your website using https without having to manually import a root certificate, then you can get an SSL certificate from one of the CAs who already have a root certificate included in the major browsers.
Firefox uses a default set of X.509v3 root certificates for various Certification Authorities (CAs). The root certificates included by default have their «trust bits» set to indicate if the CA’s root certificates may be used to verify certificates for SSL servers, S/MIME email users, and/or digitally-signed code objects without having to ask users for further permission or information.
CAs apply to have their root certificates included by default in Mozilla products by following the Mozilla CA Certificate Policy and applying for inclusion as per CA:How_to_apply. Users may override the default root certificate settings using the Certificate Manager.
Running your Own CA
If you are going to have your own CA, we recommend building 3 certificates: a long term root cert, a medium term intermediate cert, and a short term end-entity cert. This type of hierarchy allows for a relatively simple long term root to be distributed to clients, and some flexibility on the intermediate cert so that you can change parameters based on best practices and security research.
Generate your CA Root
Update *.example.com and *.example.net below to match your domains.
- You are the domain owner of *.example.com and *.example.net.
- Your computer is not connected to the internet.
Steps to generate your CA root certificate:
- Generate key
- «openssl genpkey -algorithm RSA -out rootkey.pem -pkeyopt rsa_keygen_bits: 4096»
- 4096 is considered secure for the next 15 years.
- Generate csr
- «openssl req -new -key rootkey.pem -days 5480 -extensions v3_ca -batch -out root.csr — utf8 -subj ‘/C=US/O=Orgname/OU=SomeInternalName’
- Make a new Certificate Signing Request (CSR) that will be valid for 15 years.
- Write extensions File (openssl.root.cnf)
- basicConstraints = critical, CA:TRUE
- keyUsage = keyCertSign, cRLSign
- subjectKeyIdentifier = hash
- nameConstraints = permitted;DNS:example.com,permitted;DNS:example.net
- Self-sign csr (using SHA256) and append the extensions described in the file
- «openssl x509 -req -sha256 -days 3650 -in root.csr -signkey rootkey.pem -set-serial $ANY_SMALL_INTEGER -extfile openssl.root.cnf -out root.pem»
Now you have CA pem file with its associated key.
The following steps create an intermediate cert that is valid for 8 years.
- Generate key
- «openssl genpkey -algorithm RSA -out r=intkey.pem -pkeyopt rsa_keygen_bits: 3072»
- A 3072 bit key is considered secure for the next 8 years.
- Generate csr
- «openssl req -new -key intkey.pem -days 2922 -extensions v3_ca -batch -out int.csr — utf8 -subj ‘/C=US/O=Orgname/OU=SomeInternalName2’
- Make a new Certificate Signing Request (CSR) that will be valid for 8 years.
- Write extensions File (openssl.int.cnf)
- basicConstraints = critical, CA:TRUE
- authorityKeyIdentifier = keyid, issuer
- subjectKeyIdentifier = hash
- keyUsage = keyCertSign, cRLSign
- extendedKeyUsage =serverAuth
- authorityInfoAccess = OCSP;URI:http://ocsp.example.com:8888/
- Sign the intermediate csr with the root key and the intermediate extensions
- «openssl x509 -req -sha256 -days 2922 -in int.csr -CAkey rootkey.pem -CA root.pem -set_serial $SOME_LARGE_INTEGER -out int.pem -extfile openssl.int.cnf»
Generate the end entity certificate
Update www.example.com below to match your domain.
- Generate key
- «openssl genpkey -algorithm RSA -out eekey.pem -pkeyopt rsa_keygen_bits: 2048»
- 2048 is considered secure for the next 4 years.
- Generate csr
- «openssl req -new -key key.pem -days 1096 -extensions v3_ca -batch -out example.csr — utf8 -subj ‘/CN=www.example.com’
- Make a new Certificate Signing Request (CSR) that will be valid for 3 years.
- Write extensions file (make a new file with name openssl.ss.cnf with the following contents)
- basicConstraints = CA:FALSE
- subjectAltName =DNS:www.example.com
- extendedKeyUsage =serverAuth Security Notes
There are several organizations that provide recommendations regarding the security parameters for key/hash sizes given current computational power. For the end date of the root cert created following the instructions in this page (year 2017). These are the recomendations of bit sizes (from http://www.keylength.com/):
| Asymmetric | ECC(Key) | Hash | |
|---|---|---|---|
| Linestra(2004) | 1902 | 172 | 172 |
| Ecrypt 2012 | 2432 | 224 | 224 |
| NIST 2012 | 2048 | 224 | 224 |
| ANSSI 2010 | 4096 | 200 | 256 |
| RFC 3766 | 2358 | 200 | — |
| BSI | 1976 | 256 | 256 |
In other words, SHA1 is now deprecated for new uses. We should use at least 3072 key sizes and at least a 256 ECC curve. Thus the recommendation here is for the root to be 4096 if using RSA and p384 for the root key. (p384 also chosen for compatibility as most SSL/TLS implementations support this part of suite B).
Error Codes in Firefox
Here are some common errors that might be encountered when working with certificates in Firefox.
Источник
Полезная информация
№126-06-2008 17:39:56
- tdr
- Группа: Guest
- UA:
3.0
Ошибка сертификата при подключении по https
День добрый.
При попытке подключиться к файрволу D-Link DFL-210 по протоколу https выдается страница со следующей ошибкой:
«Ошибка при установлении защищенного соединения. При соединении с 192.168.1.1:444 произошла ошибка. Этот тип сертификата не одобрен для приложения. (Код ошибки: sec_error_inadequate_cert_type)«.
Я понимаю, что в устройстве прописан неверный сертификат (вернее, сертификат с неверными параметрами), однако это устройство не имеет возможности управлять параметрами сертификата, а подключиться к нему очень хочется. Можно ли как-нибудь обойти эту ошибку?
Заранее благодарен.
№226-06-2008 17:45:32
- lakostis
- Administrator
- Группа: Administrators
- Откуда: /dev/urandom
- Зарегистрирован: 07-10-2004
- Сообщений: 1300
- UA:
3.0
- Веб-сайт
Re: Ошибка сертификата при подключении по https
tdr
Скорее всего нет. Разве что поискать прошивку поновее или использовать другой браузер (IE точно такие ошибки игнорирует). Ошибка очень серьезная — перепутаны роли сертификата (вместо серверного сделан клиентский, что является грубым нарушением).
Отсутствует
№327-06-2008 09:09:43
- tdr
- Группа: Guest
- UA:
3.0
Re: Ошибка сертификата при подключении по https
Это конечно понятно, но почему бы не отдать такую ситуацию на откуп пользователя, пусть он сам решает, идти дальше, или отказаться. Мне кажется это более логично, чем просто блокировать доступ без вариантов.
№427-06-2008 10:26:41
- lakostis
- Administrator
- Группа: Administrators
- Откуда: /dev/urandom
- Зарегистрирован: 07-10-2004
- Сообщений: 1300
- UA:
3.0
- Веб-сайт
Re: Ошибка сертификата при подключении по https
tdr
С безопасностью не шутят.
Отсутствует
№530-06-2008 10:30:54
- tdr
- Группа: Guest
- UA:
3.0
Re: Ошибка сертификата при подключении по https
День добрый.
Просмотрел свойства сертификата на устройстве и вот что получилось:
CommonName совпадает с адресом устройства (CN=192.168.1.1), по срокам ключ валиден, роль сертификата «Проверка подлинности сервера (1.3.6.1.5.5.7.3.1)», использование ключа «Цифровая подпись, Шифрование ключей, Шифрование данных, Согласование ключей, Подписывание сертификатов, Автономное подписание списка отзыва (CRL), Подписывание списка отзыва (CRL)», сертификат самоподписанный. Так что же заставляет ФФ3 выдавать ошибку «»Ошибка при установлении защищенного соединения. При соединении с 192.168.1.1:444 произошла ошибка. Этот тип сертификата не одобрен для приложения. (Код ошибки: sec_error_inadequate_cert_type)».» и блокировать доступ к устройству?
tdr
№605-07-2008 01:03:29
- Unghost
- Призрак-админ
- Группа: Administrators
- Откуда: Moscow, Russia
- Зарегистрирован: 08-10-2004
- Сообщений: 11771
- UA:
3.1
Re: Ошибка сертификата при подключении по https
Do not meddle in the affairs of Wizards, for they are subtle and quick to anger.
Отсутствует
Certs I used, issued with vault internal CA does not work with firefox, it throws sec_error_inadequate_cert_type. Nothing else that I’ve seen except for firefox (version 42.0) complains about this. (Safari, Chrome, curl, wget, javax.net.ssl.HttpsURLConnection are all happy with the resulting CA and client certs)
First I build vault from master, mount the pki backend, create a CA, and add the role I call test. Finally I issue a test cert for semester.test.
./vault -version
Vault v0.5.0-dev (b2e172ede807394fadf845466a3371f27086899b)
./vault mount pki
./vault mount-tune -max-lease-ttl=87600h pki
./vault write pki/root/generate/internal common_name="Test CA" ttl=87600m
./vault write pki/roles/test allowed_domains="test" allow_subdomains="true" max_ttl="17520h"
./vault write pki/issue/test common_name=semester.test ttl=200h
Using the cert and key return from the vault write pki/issue/test common_name=semester.test ttl=200h command, I start a ssl server.
gnutls-serv --x509certfile /tmp/semester.test.pem --x509keyfile /tmp/semester.test.key.pem
Set static Diffie-Hellman parameters, consider --dhparams.
HTTP Server listening on IPv4 0.0.0.0 port 5556...done
HTTP Server listening on IPv6 :: port 5556...done
If I now go to the page with curl or wide range of different programs, it works.
This works:
curl https://semester.test:5556/ --cacert /tmp/test_ca.crt
wget https://semester.test:5556/ --ca-certificate /tmp/test_ca.crt
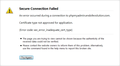
But, when using firefox (version 42.0), after importing my rest_ca.crt Root CA, it says Secure Connection Failed, with the error code: «Error code: sec_error_inadequate_cert_type».
This bz on mozilla.com seems to be relevant
When a private root CA has an extendedKeyUsage extension set it its certificate, firefox 31 will refuse to talk to servers certified by it, even if the root CA’s cert has been explicitly loaded and trusted as an authority for «identifying web sites». The error is SEC_ERROR_INADEQUATE_CERT_TYPE.
In that bugzilla, an article supposedly from the CA / Browser Forum is referenced. In Appendix B it says:
Root CA Certificate
Root Certificates MUST be of type X.509 v3.
[…]
extendedKeyUsage
This extension MUST NOT be present.
But, on my CA cert, that I generated from vault, using in the steps above:
-----BEGIN CERTIFICATE-----
MIIDQDCCAiigAwIBAgIUDeXwO+kKdepa++bhohll7dBWMc8wDQYJKoZIhvcNAQEL
BQAwEjEQMA4GA1UEAxMHVGVzdCBDQTAeFw0xNjAxMjkxMzI5MzJaFw0xNjAzMzAw
OTI5MzJaMBIxEDAOBgNVBAMTB1Rlc3QgQ0EwggEiMA0GCSqGSIb3DQEBAQUAA4IB
DwAwggEKAoIBAQDAm33l0Cjo1kYDM5bMAPsbuLABBKPfJZCsWdQWTWROA9xdlZBz
M5WN5RtGPtfNobX9qBxeCqn0X9xJL7ee8e9I/IJc4eZSIUTVIpeKpUeE/Yc7nLqx
tQ7GgMavpGv4UcsWV8vhM62G6wQ8whMvWyRXQZ4oREfTcFcX2+lz/d6yVN60AKqB
tvSoIxngO9Frhp4rDrmb0PHQOo95DKaBlW5LhqhxhsL2NNgGSpe7zlmCXmJz0Jsk
Q4049O94DyCx004lbTXjK5HUInG7he3nmTgWrcGMI2kA7s5uOqyBuJnh0+1qqW1Y
JSL5a4RXjFSWzIzwRYR+1RIIeatqdlndh/75AgMBAAGjgY0wgYowDgYDVR0PAQH/
BAQDAgGuMBMGA1UdJQQMMAoGCCsGAQUFBwMJMA8GA1UdEwEB/wQFMAMBAf8wHQYD
VR0OBBYEFNIyv19n5H7Aku+I4LYpmEcvAtQdMB8GA1UdIwQYMBaAFNIyv19n5H7A
ku+I4LYpmEcvAtQdMBIGA1UdEQQLMAmCB1Rlc3QgQ0EwDQYJKoZIhvcNAQELBQAD
ggEBABBgthjazVvG8XexiwrntRRap34yKtueELfO9EQTUlVEdpVwxeITx03xSBpL
8T+v+FiUS1OPp+KnIy4b+k8tR3czUPXZO0c9VN9hz+dAOSyr3xHqSn6ObKvibh+B
Z36yEAX45iGQdQupvKjuadI3uqXm2HHhTNppBTw6BCF3ZpqzQmaxMf+C/aeOSCuu
Ed/0EX9nO+zmFYbSmDG27RQzng2rDDrfiG3NG0/Oisj4CoIdA4Tzrp84uJ+Lgdv4
00//4t0bkndo07ztdPy5PR+SJ32bMSy+2SLQqBvjQnifRJZoxyvGDKu9O25s6HF1
bhi3LZI7zQSWI7ZSJFhmtqmIn4o=
-----END CERTIFICATE-----
It does contain this extension.
X509v3 Extended Key Usage:
OCSP Signing
I am no subject-matter expert, and am by no means sure that there could be no use cases where a CA should not have the eKU on it, but I think it would be good if vault could generate Root CA:s withot X509v3 Extended Key Usage.
Either way I am happy as long as I can create certificates from vault, which works well with firefox.
|
mihmig |
|
|
Статус: Активный участник Группы: Участники
|
Установлено: Сервер nginx запускается без ошибок, но при попытке открыть URL https://localhost/ Internet Explorer 11.0.9600.18426 (ОС только что скачала все обновления и перезагрузилась) Chromium Версия 52.0.2743.82 сборка взята из http://update.cryptopro.ru/chromium-gost/ CPFox 45.1.2 взятый из http://cryptopro.ru/products/cpfox В чём модет быть дело? Сертификат, конфиг и лог-файл сервера прикладываю (*.conf и *.crt файлы переименованы в txt, т.к. форум не даёт прикреплять файлы с этими расширениями). |
 |
|
|
Захар Тихонов |
|
|
Статус: Сотрудник Группы: Участники Сказал «Спасибо»: 36 раз |
Здравствуйте. Тут довольно все логично. IE говорит что нет доверия, т.к. в сертификате нет слова в CN «localhost» или в дополнительном имени субъекта. |
|
Техническую поддержку оказываем тут. |
|
 |
|
|
mihmig |
|
|
Статус: Активный участник Группы: Участники
|
Хм, переформировал сертификат на localhost. И ещё: почему-то заработало только после того как закомментировал опцию: |
 |
|
|
Захар Тихонов |
|
|
Статус: Сотрудник Группы: Участники Сказал «Спасибо»: 36 раз |
Так в CPFox получилось или нет? Если нет, то попробуйте в cpfox включить принудительного TLS 1.0 |
|
Техническую поддержку оказываем тут. |
|
 |
|
|
mihmig |
|
|
Статус: Активный участник Группы: Участники
|
Да, в CPFox получилось после изменения этих настроек: ув. tikhonov скажите, а в «обычном» FireFox (или Chrome) можно добиться работы через GOST SSL |
 |
|
| Пользователи, просматривающие эту тему |
|
Guest |
Быстрый переход
Вы не можете создавать новые темы в этом форуме.
Вы не можете отвечать в этом форуме.
Вы не можете удалять Ваши сообщения в этом форуме.
Вы не можете редактировать Ваши сообщения в этом форуме.
Вы не можете создавать опросы в этом форуме.
Вы не можете голосовать в этом форуме.
Problem
curl rejects the CA certificate below with 60) Certificate type not approved for application for SEC_ERROR_INADEQUATE_CERT_TYPE. I would like to understand the reason.
SEC_ERROR_INADEQUATE_CERT_TYPE
A certificate has an extended key usage extension that does not assert a required usage, or an end-entity certificate asserts the id-kp-OCSPSigning usage when it shouldn’t
Because as far as I looked at the RFC 3218, it looks all the required extended key usage extensions are asserted.
The curl command and reply
$ sudo curl -ivL
> --cert /etc/kubernetes/pki/apiserver-kubelet-client.crt
> --key /etc/kubernetes/pki/apiserver-kubelet-client.key
> --cacert /var/lib/kubelet/pki/kubelet.crt
> https://ip-172-31-4-117.us-west-1.compute.internal:10250/healthz
* Trying 172.31.4.117...
* TCP_NODELAY set
* Connected to ip-172-31-4-117.us-west-1.compute.internal (172.31.4.117) port 10250 (#0)
* Initializing NSS with certpath: sql:/etc/pki/nssdb
* CAfile: /var/lib/kubelet/pki/kubelet.crt
CApath: none
* Server certificate:
* subject: CN=ip-172-31-4-117.us-west-1.compute.internal@1514006010
* start date: Dec 23 05:13:30 2017 GMT
* expire date: Dec 23 05:13:30 2018 GMT
* common name: ip-172-31-4-117.us-west-1.compute.internal@1514006010
* issuer: CN=ip-172-31-4-117.us-west-1.compute.internal@1514006010
* NSS error -8101 (SEC_ERROR_INADEQUATE_CERT_TYPE)
* Certificate type not approved for application.
* stopped the pause stream!
* Closing connection 0
curl: (60) Certificate type not approved for application.
More details here: https://curl.haxx.se/docs/sslcerts.html
***curl failed to verify the legitimacy of the server*** and therefore could not
establish a secure connection to it. To learn more about this situation and
how to fix it, please visit the web page mentioned above.
CA certificate rejected by curl
$ openssl x509 -noout -text -in /var/lib/kubelet/pki/kubelet.crt
Certificate:
Data:
Version: 3 (0x2)
Serial Number: 1 (0x1)
Signature Algorithm: sha256WithRSAEncryption
Issuer: CN=ip-172-31-4-117.us-west-1.compute.internal@1514006010
Validity
Not Before: Dec 23 05:13:30 2017 GMT
Not After : Dec 23 05:13:30 2018 GMT
Subject: CN=ip-172-31-4-117.us-west-1.compute.internal@1514006010
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)
Modulus:
00:d5:48:65:86:4e:ec:08:a1:b1:26:4b:da:7c:e0:
d9:d0:16:96:93:9e:c0:f3:78:cb:27:a9:e1:99:d2:
10:73:70:e5:1e:ee:03:1a:55:51:29:c6:2e:62:71:
d9:c2:72:19:d3:36:41:9b:ef:74:ac:20:97:25:1b:
63:55:96:07:4d:02:01:c9:44:7d:f9:63:2b:50:98:
2a:fb:b7:03:0d:96:6d:6a:36:9d:93:ad:2c:6a:87:
7d:b8:aa:22:ca:f2:c4:a6:90:24:2b:4c:94:d1:4a:
3c:0d:c5:fa:48:fb:e5:82:30:17:f9:67:3a:1d:9b:
85:7a:bc:e9:e9:79:48:0e:53:41:fc:64:3a:c3:c1:
7e:ae:51:23:17:8e:db:1e:4c:99:56:a4:77:ad:74:
64:64:ab:a7:84:02:40:ec:c8:b1:51:2b:b3:80:7e:
b2:51:68:5c:d2:40:9d:f3:54:b9:76:2d:47:ea:f4:
51:c6:03:e9:c4:63:5c:5a:a7:7e:9a:97:89:45:99:
e8:a0:9b:5d:1d:15:94:f9:c9:2a:a4:19:a2:07:25:
2b:e6:0e:50:63:c0:6e:f9:a0:a7:ce:4a:ca:97:17:
64:2f:8a:e2:39:d5:e2:c9:c7:c4:53:f1:6e:14:22:
ca:02:cb:8a:0c:47:68:31:f2:0b:20:2c:a3:a5:5f:
cd:95
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Key Usage: critical
Digital Signature, Key Encipherment, Certificate Sign
X509v3 Extended Key Usage:
TLS Web Server Authentication
X509v3 Basic Constraints: critical
CA:TRUE
X509v3 Subject Alternative Name:
DNS:ip-172-31-4-117.us-west-1.compute.internal
Signature Algorithm: sha256WithRSAEncryption
bc:84:b2:5c:c1:a5:52:b7:03:ae:9c:53:47:4b:ca:8b:4a:90:
7f:41:0f:09:ff:77:5e:cc:7c:2c:0c:bc:37:71:c9:22:4e:7f:
eb:9f:a9:f8:04:1d:8d:39:67:52:46:9c:3b:dc:d8:1f:b0:00:
64:ed:2f:bf:8f:4c:8c:f2:6b:96:ec:99:66:19:39:1d:11:77:
52:6b:a8:f4:88:e1:ad:6b:61:af:bd:c0:fc:f7:c2:37:a2:c2:
7f:cc:de:98:a4:61:25:e2:78:b2:ab:94:31:0d:8f:2f:92:7b:
4a:4f:5b:1c:c2:e8:bd:43:cb:78:0e:f2:4b:b9:a5:54:0c:46:
0f:b0:92:f8:3c:57:08:6a:df:a4:cd:78:63:23:2f:13:12:7f:
89:7f:3d:c0:dd:c7:33:8d:55:76:10:38:47:2b:16:ce:d0:93:
c4:9e:28:42:1e:2b:f4:78:15:dd:89:1e:67:a5:a1:a1:13:30:
9a:2f:60:82:71:db:29:47:af:e7:61:71:1c:d6:72:27:61:17:
e1:31:aa:ee:84:0d:53:f8:66:18:49:34:5d:fb:50:fb:4f:c7:
b5:a1:8e:34:86:81:25:ad:31:d4:5c:9e:da:8d:08:85:a9:91:
c6:f8:83:c7:23:57:11:04:dc:90:5a:c9:5a:bf:dd:3c:9c:6a:
17:d8:d0:1f
Research
The kubernetes GitHub says:
- Change self signed certificates to not include extended key usage #311
- Switch to wget for integration apiserver checks
The NSS encryption library does not allow a CA to be used with the extended key usage present, at least in the way we are currently doing so. The generated self signed certificates extension section looks like:
...
X509v3 extensions:
X509v3 Key Usage: critical
Digital Signature, Key Encipherment, Certificate Sign
X509v3 Extended Key Usage:
TLS Web Server Authentication
X509v3 Basic Constraints: critical
CA:TRUE
X509v3 Subject Alternative Name:
DNS:localhost, IP Address:127.0.0.1, IP Address:127.0.0.1
RFC 3218
X509v3 Key Usage: critical
Digital Signature, Key Encipherment, Certificate Sign
and
X509v3 Basic Constraints: critical
CA:TRUE
should be satisfying RFC 3218 4.2.1.3 Key Usage.
The key usage extension defines the purpose (e.g., encipherment,
signature, certificate signing) of the key contained in the
certificate. The usage restriction might be employed when a key that
could be used for more than one operation is to be restricted.
…The keyCertSign bit is asserted when the subject public key is
used for verifying a signature on public key certificates. If the
keyCertSign bit is asserted, then the cA bit in the basic
constraints extension (section 4.2.1.10) MUST also be asserted.
X509v3 Extended Key Usage:
TLS Web Server Authentication
should be satisfying RFC 3218 4.2.1.13 Extended Key Usage
If the extension is present, then the certificate MUST only be used
for one of the purposes indicated. If multiple purposes are
indicated the application need not recognize all purposes indicated,
as long as the intended purpose is present. Certificate using
applications MAY require that a particular purpose be indicated in
order for the certificate to be acceptable to that application.If a CA includes extended key usages to satisfy such applications,
but does not wish to restrict usages of the key, the CA can include
the special keyPurposeID anyExtendedKeyUsage. If the
anyExtendedKeyUsage keyPurposeID is present, the extension SHOULD NOT
be critical.If a certificate contains both a key usage extension and an extended
key usage extension, then both extensions MUST be processed
independently and the certificate MUST only be used for a purpose
consistent with both extensions. If there is no purpose consistent
with both extensions, then the certificate MUST NOT be used for any
purpose.…
id-kp-serverAuth OBJECT IDENTIFIER ::= { id-kp 1 }
— TLS WWW server authentication
— Key usage bits that may be consistent: digitalSignature,
— keyEncipherment or keyAgreement
Root certificate key usage (non-self-signed end entity) suggests it would be OK not to have cRLSign/CRL signing flag.
Since a CA is supposed to issue certificate and CRL, it should have, on a general basis, the keyCertSign and cRLSign flags. These two flags are sufficient. If the CA does not intend to sign its own CRL, then it may omit the cRLSign flag;
Question
So why curl thinks the CA certificate does not assert a required usage?
Related
- Key usage extensions and extended key usage
- Missing ‘Key Usage’ on a CA certificate: can sign certificates?
- SSL Certs issued with PKI backend don’t work with firefox: sec_error_inadequate_cert_type #987
- curl: (60) Certificate type not approved for application where wget works
- GitHub — Network Security Services
- curl source code control
Topic: Self-signed CA -> Certificate — Firefox error (Read 4586 times)
Hi
I tried to create a CA from OPNsense and afterwards a website certificate from that CA.
I assigned it to the web interface of my OPNsense firewall.
But Firefox doesn’t like the CA/certificate created stating an error like this
SEC_ERROR_INADEQUATE_CERT_TYPE
I imported the CA into Firefox certificate store without any difference.
If I choose not to trust it for websites within Firefox I can access the web interface again.
Some searching show that, «I confirmed this by generating a new test CA with the the extended usage field excluded, then generating a new SSL Cert The certificate verifies properly now.»
Have some of you a workaround or fix?
Thanks
Logged
Help us a bit better understanding your problem.
You create a local CA internally System — Trust — Authorities
Afterwards you created a self signed certificte and here is where i lost you…
You installed it where exactly? On a webserver hosting a website?
Or on your OPNSense which actually has already one.
Also for Server you need to have a server cert. Webserver usually to establish the handshake.
For client cert authentication you would need a client cert.
Also import the local authority cert (there is a p12 option) into your pc maybe
hope this helps
a
Logged
English: Never try, never know!
Deutsch: Unversucht ist Unerfahren!
Thanks for your reply.
Yes I created a local CA and issued a server certificate from that CA to my OPNsense firewall, opnsense.domain.local, and assigned the new certificate to the web management interface… yes the one that actually have one self signed certificate from the installation process.
I hope that helps…
Looked/followed through this guide
https://docs.opnsense.org/manual/how-tos/self-signed-chain.html#the-certificate
Logged
« Last Edit: February 11, 2020, 12:43:09 pm by ArminF »
Logged
English: Never try, never know!
Deutsch: Unversucht ist Unerfahren!
I can confirm that Chromium acts the same…
I will also try to see which certificate I choose and retry to see if I made a mistake somewhere
Thanks!
Logged
Have you looked at Letsencrypt? Its root CA is publicly trusted.
System, Firmware, Plugins, os-acme-client
Bart…
Logged
ok, got it to work. Took a few tries.
Screenshots attached numbered
1 > System — Trust — Authority
Internal Root
Key lenght 4096
Digest SHA512
Lifetime 3640 (10 years)
2 > System — Trust — Certificates
Type Server
Key RSA
Key length 4096
Digest SHA512
Lifetime 825
3 >
Set DNS alternative Name DNS and IP
Then exported the LocalCA Cert (System — Trust — Authorities)
As i am on mac i had to set the system default to allow and trust always
Replace the Server Cert on System — Settings — Administration
Reloaded
Result > after reload chrome and safari shows valid
Maybe this helps!
Good Luck
A
« Last Edit: February 11, 2020, 02:32:40 pm by ArminF »
Logged
English: Never try, never know!
Deutsch: Unversucht ist Unerfahren!
Have you looked at Letsencrypt? Its root CA is publicly trusted.
System, Firmware, Plugins, os-acme-client
Bart…
Thank you! Will take a look
A
Logged
English: Never try, never know!
Deutsch: Unversucht ist Unerfahren!
Hi ArminF
Thanks for your detailed reply…
I finally figured it out… somehow (fat fingered, not paying attention) I had chosen a client certificate in stead of server certificate which of cause doesn’t work with a website!
But now I got a nice green bar in the certificate details under Firefox, just like I would have expected.
Thanks again for taking your time to reply!
And thanks to bartjsmit for the heads up on Letsencrypt!
Logged
Aloha,
you are welcome.
Interesting that you had to choose client cert.
Good that its working now.
«all ways lead to rome» we say here.
Cheers and happy config
armin
Logged
English: Never try, never know!
Deutsch: Unversucht ist Unerfahren!
Howdy,
I run a Private Certificate Authority for my personal use and just to learn about SSL Certs. However, with the current build of FireFox I’m on ( 31 ) I can no longer visit sites I’ve secured with SSL Certs signed by this certificate authority, even though these SSL certs work just perfectly fine in Chrome and Internet Explorer. I keep getting a «sec_error_inadequate_cert_type» error. I can only assume that the certs I’ve been issuing are incorrect in some way, but the error is so vague and the error page doesn’t specify more.
I only discovered this when I realized some of my SSL certs had expired, and I went to re-issue them.
One of the certs that hasn’t expired yet but is experiencing problems can be found here:
* https://forums.silicateillusion.org
One of the Certs I’ve tried re-issuing, matching fields included as closely as I can to a Google SSL cert that I looked up is here:
* https://phpmyadmin.endofevolution.com
These certificates were generated using the application called SimpleAuthority, found here: http://simpleauthority.com/
A Site like Networking4All.com seems to believe the Certs are valid, excepting the CA that is Self Signed: http://www.networking4all.com/en/support/tools/site+check/report/?fqdn=phpmyadmin.endofevolution.com&protocol=https
Interestingly enough, using a different site like SSLShopper shows an error similar to FF31: http://www.sslshopper.com/ssl-checker.html#hostname=https://phpmyadmin.endofevolution.com
The certs are running on an Apache Web server: Apache/2.2.21 (Win32) mod_ssl/2.2.21 OpenSSL/1.0.0e PHP/5.3.10
The CA Cert is in FireFox’s store as trusted.
If needed, I can provide certs.
»SniperFodder [[#answer-626818|said]]»
<blockquote>
I however, do not. It’s something specific to Firefox I seem to be having. Maybe I’m running an outdated version of Chrome? Which would be hard seeing as chrome itself says it’s up to date: Version 37.0.2062.120 m
I appreciate the link to Bug 1034124, However the SSL certificate itself IS NOT self signed. Only the CA is, which signed the SSL Cert. I guess what I mean to be asking is… Is Firefox Rejecting my SSL Cert, because my CA Is Self Signed?
I also offer the CA Cert for download since no one would have the cert in their stores. Would this also affect it?
I’ve attached a screen shot of the error I’m getting so that it’s available for the ticket. The following is also the «plaintext» verison of the error I’m getting:
«Certificate type not approved for application.»
</blockquote>
Similar Messages
-
NAC with EV SSL certs
Does anyone know if the NAC appliance supports EV SSL certs; especially version v4.7.x.
Any insight into older versions (4.1.3 and higher) for compatibility would be appreciated. Thanks!
benHello! The higher key length is a problem on an older version (4.1.3), not 4.7.x; etc where you can specify it. 4.1.3 you cannot specify it and it’s not strong enough.
Ben -
CertPrincipalName forced to wrong setting on server with wildcard SSL cert
Dears
After testing Exchange 2013 for a couple of weeks with a limited amount of IT personnel, we have migrated the first batch of users from 2010 to 2013.
That was the biggest mistake we’ve done this.. week..
The error is identified as an autodiscover/ssl problem. No matter what I specify in CertPrincipalName on CAS, Outlook resets itself to msstd:server.domain.com
I have tried with «none» and «msstd:*.domain.com» but it always resets to msstd:server.domain.com
Outlook Autoconfigure test returns the correct value. Any ideas?
All our clients are not domain members, so setting this with GPO is not an option.I have compared how autodiscover works for clients on 2013 and on 2010. It is definitely server related. Clients still on a 2010 mb server get’s the correct value msstd:*.domain.com.
The only difference I see in the autodiscover xml is that on 2013 there is two extra blocks of data for protocol «EXHTTP». One of these blocks does not contain the CertPrincipalName value.
<Protocol>
<Type>EXHTTP</Type>
<Server>mailbox.domain.com</Server>
<SSL>On</SSL>
<AuthPackage>Basic</AuthPackage>
<ASUrl>https://ex02.domain.com/EWS/Exchange.asmx</ASUrl>
<EwsUrl>https://ex02.domain.com/EWS/Exchange.asmx</EwsUrl>
<EmwsUrl>https://ex02.domain.com/EWS/Exchange.asmx</EmwsUrl>
<EcpUrl>https://ex02.domain.com/ecp/</EcpUrl>
<EcpUrl-um>?rfr=olk&p=customize/voicemail.aspx&exsvurl=1&realm=domain.com</EcpUrl-um>
<EcpUrl-aggr>?rfr=olk&p=personalsettings/EmailSubscriptions.slab&exsvurl=1&realm=domain.com</EcpUrl-aggr>
<EcpUrl-mt>PersonalSettings/DeliveryReport.aspx?rfr=olk&exsvurl=1&IsOWA=<IsOWA>&MsgID=<MsgID>&Mbx=<Mbx>&realm=domain.com</EcpUrl-mt>
<EcpUrl-ret>?rfr=olk&p=organize/retentionpolicytags.slab&exsvurl=1&realm=domain.com</EcpUrl-ret>
<EcpUrl-sms>?rfr=olk&p=sms/textmessaging.slab&exsvurl=1&realm=domain.com</EcpUrl-sms>
<EcpUrl-photo>PersonalSettings/EditAccount.aspx?rfr=olk&chgPhoto=1&exsvurl=1&realm=domain.com</EcpUrl-photo>
<EcpUrl-tm>?rfr=olk&ftr=TeamMailbox&exsvurl=1&realm=domain.com</EcpUrl-tm>
<EcpUrl-tmCreating>?rfr=olk&ftr=TeamMailboxCreating&SPUrl=<SPUrl>&Title=<Title>&SPTMAppUrl=<SPTMAppUrl>&exsvurl=1&realm=domain.com</EcpUrl-tmCreating>
<EcpUrl-tmEditing>?rfr=olk&ftr=TeamMailboxEditing&Id=<Id>&exsvurl=1&realm=domain.com</EcpUrl-tmEditing>
<EcpUrl-extinstall>Extension/InstalledExtensions.slab?rfr=olk&exsvurl=1&realm=domain.com</EcpUrl-extinstall>
<OOFUrl>https://ex02.domain.com/EWS/Exchange.asmx</OOFUrl>
<UMUrl>https://ex02.domain.com/EWS/UM2007Legacy.asmx</UMUrl>
<OABUrl>https://mailbox.domain.com/OAB/3abb5758-f1c7-4246-9f9f-bbf390f5febb/</OABUrl>
<ServerExclusiveConnect>On</ServerExclusiveConnect>
</Protocol> -
SSL cert on ASA 5512 from Thwate or Digitcert
I ran into the issue when I install SSL123 cert from Thwate . I did not have issue with SSL cert from DIgitcert- their process and steps are simple and using better encryoption — SHA256. Compare to Thwate — their support did not let me use SHA2 and I had to use SHA1 — according to some organisation SHA1 will be retired soon
Let me explain how to install SSL123 from Thwate into ASA 5510- you can follow their instruction — but generate CSR with 2048 — with 4096 did not work .Once you apply into their portal use SHA1 ( SHA2 did not work ) . Before you get email with their CA — install Root and Secondary intermidiate certificate — located in their website . After you get email with the new cert — you can install under Idendity certificates where still says pending .Note — there are CSR checker tools — before you apply it into CA _ google CSR checker — make sure your CSR does not have any errors
Note — When you install each certificate — trustpoint association could be in different order — example — ASDM_trustpoint0 , ASDM_trustpoint1 , ASDM_trustpoint2 etc . If you use the same ASDM_trustpoint0 for all certs- root , intermidiate and signed certificate — Did not work and you are getting ERROR — :Failed to parse or verify imported certificate
here is the link you can follow — https://search.thawte.com/support/ssl-digital-certificates/index?page=content&id=SO16141&actp=search&viewlocale=en_US&searchid=1429125296765
Finally you can check your SSL cert — google SSL checker to see if your chain as good all the way and what need to be fixedFirst of all, you don’t need the server names in the cert if your Exchange urls are configured to a load balanced url. Going forward, you will not be able to get a certificate from 3rd party with internal urls (server fqdn) in it.
When you export the certificate from CAS1, make sure that you include the private key as well (there will be a check box to tick) and import it back on CAS2.
If not, you can just import the certificate into CAS2 by selecting Import Exchange certificate in EMC and select the 3rd party cert (just like you imported on CAS1).
Yes, you need the certificate on both servers, otherwise you will get certificate errors on clients (assuming that there is some form of load balancing in place — NLB or hardware). -
Remote Desktop Services Single SSL Cert with multiple hosts
I am trying to use a single SSL Cert from a third party issuer. I have 3 servers in my deployement all are 2012R2. One contains the RD Web Access role, RD Gateway role, RD Licensing role, and RD Connection Broker role. The other 2 are
RD Session Hosts. I have the SSL cert for the server that has the Gateway and other roles. My deployement is primarily focused on deploying RemoteApp to Windows 8 Thin clients with GPO through the default URL. It works currently with the
exception that the user gets a certificate mismatch error because it is seeing the cert for the gateway server but is connecting to the host servers so the names don’t match. Is anyone else using a similar setup and had success with it? I am trying
to avoid buying an expensive wildcard cert to cover all of them.Hi,
Please verify that the .rdp file embedded in the RDWeb IE page matches the same one from RADC. To do this, log on to RD Web Access using IE, right-click and choose View Source. Find the goRDP function for the icon you want to examine and copy
the text between the ‘ marks. Next paste this into the escape text box the below page:
http://www.web-code.org/coding-tools/javascript-escape-unescape-converter-tool.html
Click complete unescape to get the plain text version. After that you can select all of the text in the clear text box, paste it into a blank Notepad window, then save as a .rdp file. Once you have the .rdp file created you can compare
it to the other ones and see if any of the names are different, see if it gets the certificate error as well when you double-click it, etc.
Do you have any proxy or other non-default network configuration on your Windows 8 embedded clients?
Thanks.
-TP -
ACE: Single SSL Cert for two domains with same VIP
At present I have a design that will use individual SSL cert per domain and link both certs to (two or one) serverfarm.
policy-map multi-match popvip_01
class POP_VIP01
loadbalance vip inservice
loadbalance policy POP-POp3_PMT or popPMT1
loadbalance vip icmp-reply
ssl-proxy server GINPOP_SSLPROXY
connection advanced-options TCP_PARAM_Y
class POP3_VIP02
loadbalance vip inservice
loadbalance policy POP-POp3_PMT or POPPMT2
loadbalance vip icmp-reply
ssl-proxy server GINPOP3_SSLPROXY
connection advanced-options TCP_PARAM_Y
however,
if I can get one single certificate to process both pop and pop3 domains, that use the same VIP/port, and if this will work with ACE, i’m inclined to design using this alternative.
ie,
pop.mydomain.com = 10.10.10.1 995
pop3.mydomain.com = 10.10.10.1 995
Any suggestions would be appriciated.Hello,
In order to achieve this then you will need to order a wildcard certifictae ie
*.mydomain.com
These certificates are more expensive and so you will probably find it cheaper to buy two certificates than one wildcard certificate.
Regards -
Http Analyzer connecting to server with self-signed SSL cert
When making webservice calls using Axis 1.3 to our development site that uses a self-signed SSL cert I am getting the following error when running the Http Analyzer:
javax.net.ssl.SSLHandshakeException: Received fatal alert: handshake_failure
Works fine if I turn off proxy in run configuration for project or when used against a site with a purchased cert. I assume the problem is with Http Analyzer not being able to find the server cert in a local keystore, is there a way to import the cert so that I can run Http Analyzer against the site?
Tried adding server cert to <jdkhome>/jre/lib/security/cacerts keystore but still have the problem.
Am using JDeveloper 10.1.3.
Thanks,
JohnI fixed that by getting certs from: https://www.startssl.com/?app=1.
The certs are free and work fine.
Since Iphone 4 apple does not accept unknown CA Authorities. -
How to get OS X to accept an SSL Cert the way other UNIX clients do?
I’m hoping some of the network gurus can suggest a solution for me. My current config is 10.5.4 on PPC.
I have a host that I need to connect to using SSL but their certificate has a host name mismatch (they are a small org, and can’t afford another SSL cert for the moment). I know the cert is valid, so I’m not worried about the security implications of using it.
On other *NIX clients, I simply have to add the cert into the root chain (e.g. /etc/ssl/certs/ca-certificates.crt), restart the application, and all apps will then accept it as valid.
On OS X, I’ve imported the cert into Keychain Access, marked it as «Always Trusted» and set up a policy to «alias» it to the URL I need to access with my application (not a web browser) (ref: KB article: HT1679) in both the login and the System keychains, yet the client application still errors out and refuses to connect to the URL.
How can I configure client SSL on OS X to work like other UNIX configurations? There doesn’t seem to be a way to override the extremely restricted behavior.
I have MacPorts installed and am open to an application specific «hack» if necessary, ala «LDLIBRARYPATH», if anyone thinks that’s feasible (which is what I am looking at now). Conceivably I could recompile the client application since it’s OSS, though I’d rather avoid that if possible.
Any suggestions would be appreciated.
Thanks in advance—
=N=when you connect with a web browser to an https site that has a mistmatched cert it warns you and you have to tell the browser to ignore the security issue to let you carry on.
what unix apps are you using to connect to this server? -
ITunes U cannot fetch HTTPS feeds with current generation of SSL certs
I’ve outlined this problem previously with no resolution, but given that public iTunes U sites are about to rely even more on feeds it’s even more important that a solution be found.
Here’s the summary of the unresolved thread http://discussions.apple.com/thread.jspa?messageID=11012798
iTunes U will no longer update valid feeds from our LMS. Our LMS is entirely SSL/TLS and recently had its certificate updated. The DigiCert certificate and feed are working at https://lms.brocku.ca/podcasts/site/BuildaPodcast . However iTunes U sends an E-Mail to the owner once it is changed to this URL that reads:
«iTunes U could not update the content because iTunes U could not download the specified feed (https://lms.brocku.ca/podcasts/site/BuildaPodcast). Until the issue is resolved, iTunes U continues to display the last downloadable version of the content. Verify that the feed specified in the feed URL field and the resource are available, and then try again»
In the interim we’ve been fetching the exact same RSS feed and hosting it at http://ctlet.brocku.ca/~mclare/podcast/BuildaPodcast so that iTunes U can fetch it with out SSL/TLS — but we can not do this for all podcasts.
Older versions of the command line tools like cURL (and its library) and wget have a similar problem. In their situation their root certificates are not fully updated. Could this be the case for the iTunes U feed fetcher?
Thanks for looking into this.
..attHi Mark,
Thanks, it is indeed now updating.
When I updated it yesterday (a little before 2:04 EST) I did not get the previous Error prompt — but I didn’t know if that was an iTunes 9 change in interface or the problem being solved. I did get an E-Mail from iTunes U <[email protected]> subject «iTunes U unable to update Course page group Brock University > Brock Community > Sakai > Help for Instructors» — full E-Mail below.
I edited the feed/section again today (10:12 EST) and the status appears to indicate that it was updated. BUT, I again received this E-Mail:
E-Mail :»Dear iTunes U administrator, instructor, or course manager,
Your ‘Sakai’ course in your brocku.ca iTunes U site populates its ‘Help for Instructors’ group track list automatically from an RSS feed, based on the podcast RSS feed URL and details you specified. iTunes U encountered the following error while trying to access the podcast RSS feed:
iTunes U could not update the content because iTunes U could not download the specified feed (https://lms.brocku.ca/podcasts/site/BuildaPodcast). Until the issue is resolved, iTunes U continues to display the last downloadable version of the content. Verify that the feed specified in the feed URL field and the resource are available, and then try again.
To check your iTunes U podcast RSS feed URL and details, edit your Course page group located at Brock University > Brock Community > Sakai > Help for Instructors.
Sincerely,
The iTunes U Team»
It is great that content will start moving now, but can anything be done about the spurious E-Mails? -
IMAP Mail Setup with self-signed SSL certs
I am unable to set up IMAP access to an email account of mine on the new iPhone mail app. The setup stalls at «verifying» and I can’t seem to save the info entered and then disable SSL in the advanced setup.
Also, it doesn’t seem possible to install SSL certs out of safari. On the computer I was able to navigate to the server via https and permanently accept the SSL cert. The option doenst exisit in Safari Mobile. If you have the servers cert (.der) file in the web root of the server, possible to download and install the certificate. This solved a similar problem for my ExchangeMail push with our Kerio server. Unfortunately, the certificate file of that other IMAP account is unavailable..If possible, instead of configuring it on the iPhone, try configuring it on your computer and using iTunes to sync the configuration itself to the iPhone. I am connecting fine to an IMAP server with a self-signed certificate. The first time I opened Mail (on the iPhone) it prompted me with a dialog saying the certificate was invalid but I was able to accept it. Since then, it has never prompted me again about validity of the certificate (even after rebooting the phone) so I believe the Mail program can permanently accept a self-signed certificate.
And yes, there doesn’t seem to be a way for Safari Mobile to permanently accept self-signed certificates. I have read that the iPhone is supposed to pull certificates from the Keychain but this does not appear to be the case. -
Generate SSL cert with stronger signature algorithm such as RSA-SHA 1 or SHA 2 from Certificate Authority Version: 5.2.3790.3959
We have a Certificate Authority (Version: 5.2.3790.3959) configured on Windows 2003 R2 server in our environment. How do i generated SSL cert with stronger signature algorithm such as with SHA1 or SHA2
Currently i am only able to generate SSL cert with md5RSA.Hi,
Since you are using Windows Server 2003 R2 as CA, the hash algorithm cannot be changed, while in Windows 2008 and 2008 R2, changing the hash algorithm is possible.
Therefore, you need to build a new CA to use a new algorithm.
More information for you:
Is it possible to change the hash algorithm when I renew the Root CA
http://social.technet.microsoft.com/Forums/windowsserver/en-US/91572fee-b455-4495-a298-43f30792357e/is-it-possible-to-change-the-hash-algorithm-when-i-renew-the-root-ca?forum=winserversecurity
Changing public key algorithm of a CA certificate
http://social.technet.microsoft.com/Forums/windowsserver/en-US/0fd19577-4b21-4bda-8f56-935e4d360171/changing-public-key-algorithm-of-a-ca-certificate?forum=winserversecurity
modify CA configuration after Migration
http://social.technet.microsoft.com/Forums/windowsserver/en-US/0d5bcb76-3a04-4bcf-b317-cc65516e984c/modify-ca-configuration-after-migration?forum=winserversecurity
Best Regards,
Amy Wang -
Need to check tls/ssl but getting stuck with «You must provide a value expression on the right-hand side of the ‘-‘ operator.»
I would like to disable ssl 3 but need to test what sites only support ssl 3. I keep getting stuck with an error that is over my head. I’ve tried manipulating the string a dozen different ways and keep getting the same error. I am not familiar with -notin
or how to specify which part of the property its checking: thanks a ton
http://blog.whatsupduck.net/2014/10/checking-ssl-and-tls-versions-with-powershell.html
line with issues:
$ProtocolNames = [System.Security.Authentication.SslProtocols] | gm -static -MemberType Property | where-object{$_.Name -notin @(«Default»,»None») | %{$_.Name}
You must provide a value expression on the right-hand side of the ‘-‘ operator.
At S:scriptstest23.ps1:50 char:126
+ $ProtocolNames = [System.Security.Authentication.SslProtocols] | gm -static -MemberType Property | where-object{$_.Name — <<<< noti
n @(«Default»,»None») | %{$_.Name}
+ CategoryInfo : ParserError: (:) [], ParseException
+ FullyQualifiedErrorId : ExpectedValueExpression
<#
.DESCRIPTION
Outputs the SSL protocols that the client is able to successfully use to connect to a server.
.NOTES
Copyright 2014 Chris Duck
http://blog.whatsupduck.net
Licensed under the Apache License, Version 2.0 (the «License»);
you may not use this file except in compliance with the License.
You may obtain a copy of the License at
http://www.apache.org/licenses/LICENSE-2.0
Unless required by applicable law or agreed to in writing, software
distributed under the License is distributed on an «AS IS» BASIS,
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
See the License for the specific language governing permissions and
limitations under the License.
.PARAMETER ComputerName
The name of the remote computer to connect to.
.PARAMETER Port
The remote port to connect to. The default is 443.
.EXAMPLE
Test-SslProtocols -ComputerName «www.google.com»
ComputerName : www.google.com
Port : 443
KeyLength : 2048
SignatureAlgorithm : rsa-sha1
Ssl2 : False
Ssl3 : True
Tls : True
Tls11 : True
Tls12 : True
#>
function Test-SslProtocols {
param(
[Parameter(Mandatory=$true,ValueFromPipelineByPropertyName=$true,ValueFromPipeline=$true)]
$ComputerName,
[Parameter(ValueFromPipelineByPropertyName=$true)]
[int]$Port = 443
begin {
$ProtocolNames = [System.Security.Authentication.SslProtocols] | gm -static -MemberType Property | where-object{$_.Name -notin @(«Default»,»None») | %{$_.Name}
process {
$ProtocolStatus = [Ordered]@{}
$ProtocolStatus.Add(«ComputerName», $ComputerName)
$ProtocolStatus.Add(«Port», $Port)
$ProtocolStatus.Add(«KeyLength», $null)
$ProtocolStatus.Add(«SignatureAlgorithm», $null)
$ProtocolNames | %{
$ProtocolName = $_
$Socket = New-Object System.Net.Sockets.Socket([System.Net.Sockets.SocketType]::Stream, [System.Net.Sockets.ProtocolType]::Tcp)
$Socket.Connect($ComputerName, $Port)
try {
$NetStream = New-Object System.Net.Sockets.NetworkStream($Socket, $true)
$SslStream = New-Object System.Net.Security.SslStream($NetStream, $true)
$SslStream.AuthenticateAsClient($ComputerName, $null, $ProtocolName, $false )
$RemoteCertificate = [System.Security.Cryptography.X509Certificates.X509Certificate2]$SslStream.RemoteCertificate
$ProtocolStatus[«KeyLength»] = $RemoteCertificate.PublicKey.Key.KeySize
$ProtocolStatus[«SignatureAlgorithm»] = $RemoteCertificate.PublicKey.Key.SignatureAlgorithm.Split(«#»)[1]
$ProtocolStatus.Add($ProtocolName, $true)
} catch {
$ProtocolStatus.Add($ProtocolName, $false)
} finally {
$SslStream.Close()
[PSCustomObject]$ProtocolStatus
Test-SslProtocols -ComputerName «www.google.com»V2 version:
function Test-SslProtocols {
param(
[Parameter(
Mandatory=$true,
ValueFromPipelineByPropertyName=$true,
ValueFromPipeline=$true
)]$ComputerName,
[Parameter(
ValueFromPipelineByPropertyName=$true
)][int]$Port = 443
begin {
$protocols=[enum]::GetNames([System.Security.Authentication.SslProtocols])|?{$_ -notmatch ‘none|default’}
process {
foreach($protocol in $protocols){
$ProtocolStatus = @{
ComputerName=$ComputerName
Port=$Port
KeyLength=$null
SignatureAlgorithm=$null
Protocol=$protocol
Active=$false
$Socket = New-Object System.Net.Sockets.Socket(‘Internetwork’,’Stream’, ‘Tcp’)
$Socket.Connect($ComputerName, $Port)
try {
$NetStream = New-Object System.Net.Sockets.NetworkStream($Socket, $true)
$SslStream = New-Object System.Net.Security.SslStream($NetStream, $true)
$SslStream.AuthenticateAsClient($ComputerName, $null, $protocol, $false )
$RemoteCertificate = [System.Security.Cryptography.X509Certificates.X509Certificate2]$SslStream.RemoteCertificate
$protocolstatus.Active=$true
$ProtocolStatus.KeyLength = $RemoteCertificate.PublicKey.Key.KeySize
$ProtocolStatus.SignatureAlgorithm = $RemoteCertificate.PublicKey.Key.SignatureAlgorithm.Split(«#»)[1]
catch {
Write-Host ‘Failed’
finally {
New-Object PsObject -Property $ProtocolStatus
$SslStream.Close()
Test-SslProtocols -ComputerName www.google.com
¯_(ツ)_/¯ -
How to setup SSL cert for SharePoint apps in a three tier farm with nlb
I am having trouble understanding how to setup the SSL certificate on SharePoint apps or in general its configuration
Please check the below thread..
https://social.technet.microsoft.com/Forums/sharepoint/en-US/53465d30-10b2-48c9-9541-5ade738156b4/how-to-setup-ssl-cert-for-apps
Don’t forget to mark it as an Answer if it resolves your issue and Vote Me as helpful if it useful.
Mahesh -
FTP with SSL cert on ACNS via WCCP
I have a client using an SSL cert to connect to an ftp server. The user is being redirected to a CE-511 via WCCP v2 but the FTP connection does not work. If I bypass the user (in my wccp acl) it works fine — following a default route to my PIX.
Any info, good or bad will be greatly appreciated.
— MattWhat is the software version running on the CE-511. Did you try upgrading to the latest version of the firmware. This should solve the issue.
-
Wildcard SSL cert on ASA
Is it possible to use a wildcard SSL cert on an ASA? That is, instead of getting a specific cert with the FQDN of the ASA, we would use the wildcard cert issued?
Absolutely, it’s especially needed in ASA vpn load balancing environments. When you connect to a FQDN that translates to a load balancing IP, one of the ASAs will do an http redirect to its individual hostname, your browser (or AnyConnect) will attempt that connection and ASA needs to have a certificate for that specific hostname. Having a wildcard cert on all ASAs resolves this. I’ve got this running on several customers.
If you need help with configuration, let me know.
You can either generate private keys on the ASA (and later export it to another ASA or other non-cisco devices), or you could import an existing wildcard certificate with the private keys (in PKCS12-BASE64 format)
Regards,
Roman
Maybe you are looking for
-
Session Time Out For UNLOGGED USER During Search -pls help
Hi, The problem lies in searchresultscontroller.java/searchcontroller.java file under search/web/handler of an application that supports educational note sharing. The problem is that — When I search with query strings in different fields(as you will
-
Preview Crashes.
Frequently—more often than not and with no pattern—Preview crashes. It so bad I had to install Adobe Reader. Does anyone know what’s up with it? Have workarounds or fixes? Here’s the crash report: Process: Preview [1601] Path:
-
Project Gantt Bar Bug in P6 (EPPM and PM) — A strange and Unique Issue
Hello All, I have 18 projects in my production EPS but one has a problem, i’ve been unable to resolve, so far. The Issue* In the Project-Layout-View (Project Space), when I look at project X’s Gantt Bar, following is observed. A- When he Project is O
-
How can I save iTunes videos in my icloud?
Hi how can i Save iTunes videos in my icloud?
-
FCP6 and Leopard. Fonts appear different
I have just loaded Leopard and done the update to 6.0.2 and the Helvetica Nue Bold Italic font looks very strange. Anybody else having problems with fonts and any tips. Thanks. Brett.