Problem
System was initially working OK (no problems/errors).
Customer then modifies the Microsoft networking TLS settings (on both the Controller application server and SQL database server) so that:
- TLS 1.0 disabled
- TLS 1.1 disabled
- TLS 1.2 enabled
After making those changes, user launches Controller client. User then:
- Chooses database
- Types in username/password
An error appears.
Symptom
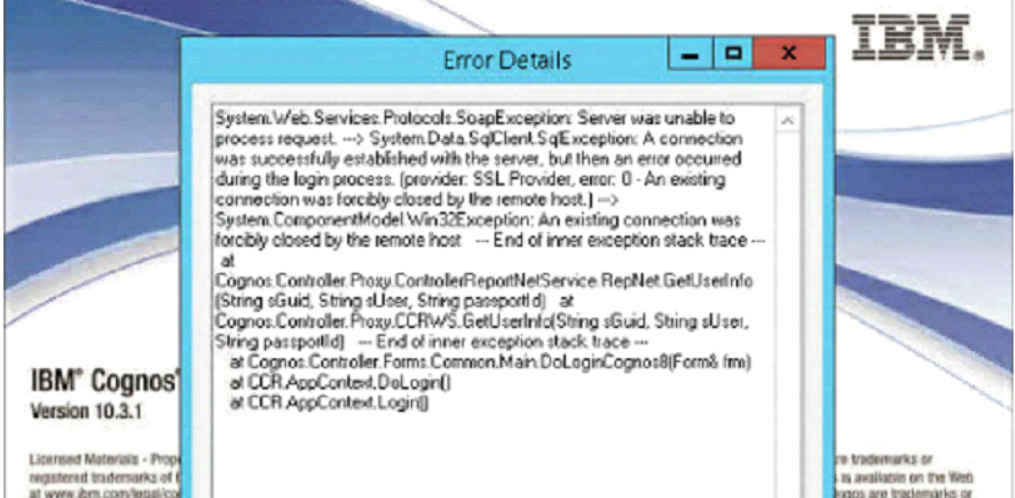
System.Web.Services.Protocols.SoapException: Server was unable to process request. —> System.Data.SqlClient.SqlException: A connection was successfully established with the server, but then an error occurred during the login process. (provider: SSL Provider, error: 0 — An existing connection was forcibly closed by the remote host.) —> System.ComponentModel.Win32Exception: An existing connection was forcibly closed by the remote host
— End of inner exception stack trace —
at Cognos.Controller.Proxy.ControllerReportNetService.RepNet.GetUserInfo(String sGuid, String sUser, String passportId)
at Cognos.Controller.Proxy.CCRWS.GetUserInfo(String sGuid, String sUser, String passportId)
— End of inner exception stack trace —
at Cognos.Controller.Forms.Common.Main.DoLoginCognos8(Form& frm)
at CCR.AppContext.DoLogin()
at CCR.AppContext.Login()
Cause
The Controller application server cannot connect to the Microsoft SQL database server.
Example
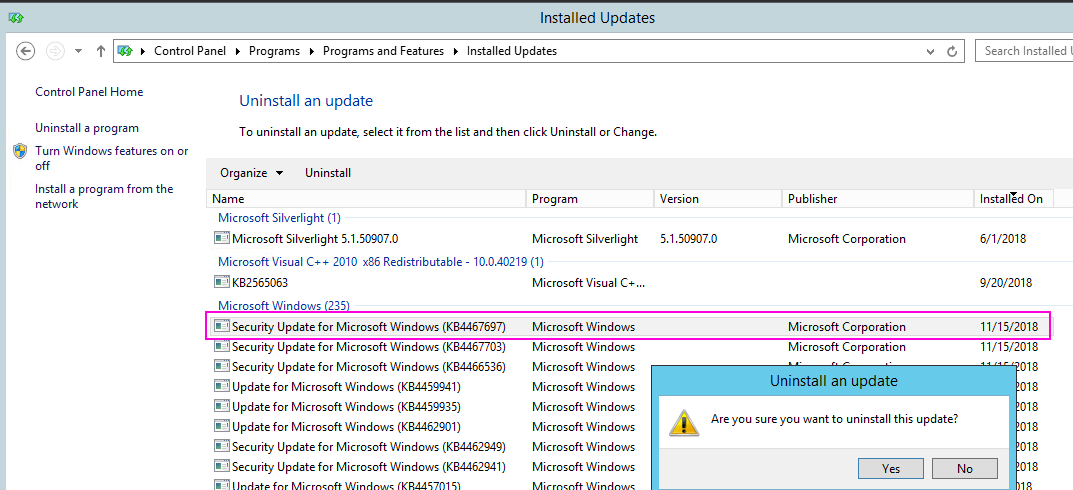
In one real-life customer scenario, the cause was Microsoft patch KB4467697 (on the Controller application server).
Resolving The Problem
Fix:
Uninstall the Microsoft patch KB4467697 from the Controller application server:
Workaround:
Re-enable the TLS 1.0/1.1 protocols (on both the Controller application server and SQL database server).
Related Information
Document Location
Worldwide
[{«Business Unit»:{«code»:»BU059″,»label»:»IBM Software w/o TPS»},»Product»:{«code»:»SS9S6B»,»label»:»IBM Cognos Controller»},»Component»:»»,»Platform»:[{«code»:»PF033″,»label»:»Windows»}],»Version»:»All Versions»,»Edition»:»»,»Line of Business»:{«code»:»LOB10″,»label»:»Data and AI»}}]
Posted by blakhani on November 14, 2014
I said earlier that I have bunch of *good* friends who remember me whenever they get any issue with SQL Server. So I got a call from my friend and he told that he is not able to connect to SQL Server from some client. Since it’s only few client, we can easily rule out the issue with SQL Engine not allowing connection. I asked him to connect via SQL Server Management Studio and got below error.
TITLE: Connect to Server
——————————
Cannot connect to SQLDBServer.
——————————
ADDITIONAL INFORMATION:
A connection was successfully established with the server, but then an error occurred during the pre-login handshake. (provider: SSL Provider, error: 0 – The token supplied to the function is invalid) (Microsoft SQL Server, Error: -2146893048)
For help, click: http://go.microsoft.com/fwlink?ProdName=Microsoft+SQL+Server&EvtSrc=MSSQLServer&EvtID=-2146893048&LinkId=20476
——————————
BUTTONS:
OK
——————————
Did basic troubleshooting as below
- Tested basic connectivity like ping, telnet etc. everything is working fine, except the connection to SQL engine from this machine.
- Error message says SSL but there was no certificate used in SQL Server.
- There was no certificate used.
Next major task is to find out what is the difference in both servers. So I asked him what were the things done on “bad” client. He said that he applied bunch on Windows updates. Looking at list I found one which talks about SSL.
http://support.microsoft.com/kb/2643584 (MS12-006: Vulnerability in SSL/TLS could allow information disclosure: January 10, 2012)
We check the machines and found that SendExtraRecord was 1 on “bad” client whereas other “good” clients it was 2.
Here were the steps taken to solve the issue. (taken from KB)
- Click Start, click Run, type regedit in the Open box, and then click OK.
- Locate and then click the following subkey in the registry:
HKEY_LOCAL_MACHINESystemCurrentControlSetControlSecurityProvidersSCHANNEL
- On the Edit menu, point to New, and then click DWORD Value.
- Type SendExtraRecord for the name of the DWORD value, and then press Enter.
- Right-click SendExtraRecord, and then click Modify.
- In the Value data box, type 2 to disable the split record in schannel, and then click OK.
- Exit Registry Editor.
In our case it was 1 and making it 2 fixed the issue and were were able to covert bad clients to good clients.
Hope this helps.
Cheers,
Balmukund
This entry was posted on November 14, 2014 at 3:30 AM and is filed under Connectivity, Error.
Tagged: pre-login handshake, SQL, SSL Provider, The token supplied to the function is invalid. You can follow any responses to this entry through the RSS 2.0 feed.
You can leave a response, or trackback from your own site.
Содержание
- Sql provider ssl provider error 0
- Asked by:
- Question
- All replies
- The certificate received from the remote server was issued by an untrusted certificate authority error when you connect to SQL Server
- Symptoms
- Cause
- Resolution
- Export the server certificate
- Install the root certificate authority (CA) on the client machine
- Help: SQL Server
- Sharing my knowlege about SQL Server Troubleshooting Skills
- Blog Stats
- Blogroll
- Select GETDATE()
- Subscribe
- Follow Blog via Email
- Date provider: SSL Provider, error: 0 – The token supplied to the function is invalid ) (Microsoft SQL Server, Error: -2146893048) For help, click: http://go.microsoft.com/fwlink?ProdName=Microsoft+SQL+Server&EvtSrc=MSSQLServer&EvtID=-2146893048&LinkId=20476 —————————— BUTTONS: OK ——————————
- Sql provider ssl provider error 0
- Asked by:
- Question
- All replies
Sql provider ssl provider error 0
This forum has migrated to Microsoft Q&A. Visit Microsoft Q&A to post new questions.
Asked by:
Question
Cannot connect to xxxxx.
A connection was successfully established with the server, but then an error occurred during the login process.
(provider: SSL Provider, error: 0 — An existing connection was forcibly closed by the remote host.) (Microsoft SQL Server, Error: 10054)
For help, click: http://go.microsoft.com/fwlink?ProdName=Microsoft%20SQL%20Server&EvtSrc=MSSQLServer&EvtID=10054&LinkId=20476
An existing connection was forcibly closed by the remote host
Are you trying to connect the SQL instance using ssms and sqlcmd from your database server locally or from a remote server? Would you please confirm the following points first?
1. First check whether the server name or alias of SQL server is set correctly
2. Check whether TCP/IP protocol is enabled on the client side and SQL server side
3. Make local connection first to determine whether the problem is SQL server itself or the network layer
4. Check whether the SQL server Browser service of SQL server starts normally
5. Ping the IP address of the server where SQL server is installed to see if it works, and test whether the port number of SQL server listening is enabled
6. If step5 fails, check the firewall configuration to see whether the corresponding port number is opened in the firewall
7. Check whether the local connection and maximum connection Numbers are set correctly in the connection property of the database instance.
By the way, you need to check your SSL and TLS settings. The settings between the client and server should be somewhat consistent.
Источник
The certificate received from the remote server was issued by an untrusted certificate authority error when you connect to SQL Server
This article helps you resolve the problem that occurs when you try to make an encrypted connection to SQL Server.
Original product version: В SQL Server
Original KB number: В 2007728
Symptoms
When connecting to SQL Server, you may receive the following error message:
A connection was successfully established with the server, but then an error occurred during the login process. (provider: SSL Provider, error: 0 — The certificate chain was issued by an authority that is not trusted.) (.Net SqlClient Data Provider)
Additionally, the following error message is logged in the Windows System event log.
Cause
This error occurs when you try to make an encrypted connection to SQL Server using a non-verifiable certificate. This could happen in the following scenarios:
| Scenario | Server-side encryption | Client-side encryption | Certificate type | Certificate issuing authority present in Trusted Root Certification Authorities store |
|---|---|---|---|---|
| 1 | Yes | No | You provision a certificate from a non-trusted source (the certificate issuing authority is not listed as a trusted authority in Trusted Root Certification Authorities on the client machine) | No |
| 2 | Off | Yes | SQL Server self-generated certificate | Self-signed certificates do not show up in this store. |
When establishing encrypted connections to SQL Server, Secure Channel (Schannel) creates the list of trusted certificate authorities by searching the Trusted Root Certification Authorities store on the local computer. During the TLS handshake, the server sends its public key certificate to the client. The issuer of a public key certificate is known as a Certificate Authority (CA). The client has to ensure that the certificate authority is one that the client trusts. This is achieved by knowing the public key of trusted CAs in advance. When Schannel detects a certificate that was issued by an untrusted certification authority, such as in the above two cases, you get the error message listed in the Symptoms section.
Resolution
If you intentionally use either a certificate from a non-trusted authority or a self-signed certificate to encrypt connections to SQL Server, you can use one of the following options:
For Scenario 1: Add the certificate authority to the Trusted Root Certification Authorities store on the client computer initiating encrypted connection. To do this, complete the Export the server certificate and Install the root certificate authority (CA) on the client machine procedures listed below in that sequence.
Export the server certificate
The example uses a file named caCert.cer as a certificate file. You must obtain this certificate file from the server. The following steps explain how to export the server certificate to a file:
Click Start and then Run, and type MMC. (MMC is an acronym for the Microsoft Management Console.)
In MMC, open the Certificates.
Expand Personal and then Certificates.
Right-click the server certificate, and then select All Tasks->Export.
Click Next to move past the welcome dialog box of the Certificate Export Wizard.
Confirm that No, do not export the private key is selected, and then click Next.
Make sure that either DER encoded binary X.509 (.CER) or Base-64 encoded X.509 (.CER) is selected, and then click Next.
Enter an export file name.
Click Next, and then click Finish to export the certificate.
Start the Certificates snap-in for MMC on the client computer and then add the Certificates snap-in.
In the Certificates snap-in dialog box, choose Computer account, and then choose Next.
In the Select Computer pane, choose Local computer: (the computer this console is running on), and then choose Finish.
Choose OK to close the Add or Remove Snap-ins dialog box.
In the left pane of MMC, expand the Certificates (Local Computer) node.
Expand the Trusted Root Certification Authorities node, right-click the Certificates subfolder, select All Tasks, and then choose Import.
In the Certificate Import Wizard, on the Welcome page, choose Next.
On the File to Import page, choose Browse.
Browse to the location of the caCert.cer certificate file, select the file, and then choose Open.
On the File to Import page, choose Next.
On the Certificate Store page, accept the default selection, and then choose Next.
On the Completing the Certificate Import Wizard page, choose Finish.
For scenarios 1 and 2: Set Trust Server Certificate setting to true in your client application.
For more information on how to do this, review the following topics:
If you are using SQL Server Management Studio, you can click on the Options tab, and check the box Trust Server certificate option in the Connection Properties tab.
Caution: SSL connections that are encrypted by using a self-signed certificate do not provide strong security. They are susceptible to man-in-the-middle attacks. You shouldn’t rely on SSL using self-signed certificates in a production environment or on servers that are connected to the Internet.
If the configuration discussed in the previous sections of this article is unintended, you can use one of the following options to resolve this problem:
Configure database engine to use encryption as per the procedure in Enable encrypted connections to the Database Engine.
If encryption is not required:
Disable encryption settings (if any) in your client application.
Disable server-side encryption using SQL Server Configuration manager. For more information on how to do this, review Configure Server.
Источник
Help: SQL Server
Sharing my knowlege about SQL Server Troubleshooting Skills
Blog Stats
Blogroll
Select GETDATE()
November 2014
| M | T | W | T | F | S | S |
|---|---|---|---|---|---|---|
| 1 | 2 | |||||
| 3 | 4 | 5 | 6 | 7 | 8 | 9 |
| 10 | 11 | 12 | 13 | 14 | 15 | 16 |
| 17 | 18 | 19 | 20 | 21 | 22 | 23 |
| 24 | 25 | 26 | 27 | 28 | 29 | 30 |
Subscribe
Follow Blog via Email
Date provider: SSL Provider, error: 0 – The token supplied to the function is invalid ) (Microsoft SQL Server, Error: -2146893048)
For help, click: http://go.microsoft.com/fwlink?ProdName=Microsoft+SQL+Server&EvtSrc=MSSQLServer&EvtID=-2146893048&LinkId=20476
——————————
BUTTONS:
OK
——————————
Did basic troubleshooting as below
- Tested basic connectivity like ping, telnet etc. everything is working fine, except the connection to SQL engine from this machine.
- Error message says SSL but there was no certificate used in SQL Server.
- There was no certificate used.
Next major task is to find out what is the difference in both servers. So I asked him what were the things done on “bad” client. He said that he applied bunch on Windows updates. Looking at list I found one which talks about SSL.
http://support.microsoft.com/kb/2643584 (MS12-006: Vulnerability in SSL/TLS could allow information disclosure: January 10, 2012)
We check the machines and found that SendExtraRecord was 1 on “bad” client whereas other “good” clients it was 2.
Here were the steps taken to solve the issue. (taken from KB)
- Click Start, click Run, type regedit in the Open box, and then click OK.
- Locate and then click the following subkey in the registry:
In our case it was 1 and making it 2 fixed the issue and were were able to covert bad clients to good clients.
Источник
Sql provider ssl provider error 0
This forum has migrated to Microsoft Q&A. Visit Microsoft Q&A to post new questions.
Asked by:
Question
server: SQL Server 2016 13.0.5026.0
1. SSMS 12.0.2000.8
A connection was successfully established with the server, but then an error occurred during the login process. (provider: SSL Provider, error: 0 — An existing connection was forcibly closed by the remote host.) (Microsoft SQL Server, Error: 10054)
C:Program FilesMicrosoft SQL ServerClient SDKODBC110ToolsBinn>.sqlcmd -E -S serverinstance
Sqlcmd: Error: Microsoft ODBC Driver 11 for SQL Server : SSL Provider: An existing connection was forcibly closed by the remote host.
.
Sqlcmd: Error: Microsoft ODBC Driver 11 for SQL Server : Client unable to establish connection.
1) Are you trying to connect the SQL instance using ssms and sqlcmd from your database server locally or from a remote server?
2) Is browser service running on your DB server.
3) is firewall opened for the remote connection in your database server.
4) Is this a new installation or this issue has cropped up recently?
Regards;
Vivek Janakiraman
www.jbswiki.com
I’m getting this issue after installing KB4467697 with SQL Server 2014 SP2 CU 10:
“A connection was successfully established with the server, but then an error occurred during the login process. (provider: SSL Provider, error: 0 – No process is on the other end of the pipe.) (.Net SqlClient Data Provider)
(Microsoft SQL Server, Error: 233)”
Uninstalling that patch, SQL connections is OK.
1) Are you trying to connect the SQL instance using ssms and sqlcmd from your database server locally or from a remote server? remote server
2) Is browser service running on your DB server. yes
3) is firewall opened for the remote connection in your database server. No
4) Is this a new installation or this issue has cropped up recently? the SQL Server 2016 is new installed
1) Are you trying to connect the SQL instance using ssms and sqlcmd from your database server locally or from a remote server? remote server
2) Is browser service running on your DB server. yes
3) is firewall opened for the remote connection in your database server. No
4) Is this a new installation or this issue has cropped up recently? the SQL Server 2016 is new installed
Try opening the port which SQLServer uses (by default its 1433 unless you changed it) in the firewall for inbound connections
I also have a doubt that since you use SSMS 12.0 which is earlier version one and you’re trying to connect to SQL 2016 it can even be TLS 1.2 related issue
I would suggest getting a recent version of SSMS (17.x) and try connecting to see if issue persists
Please Mark This As Answer if it solved your issue
Please Vote This As Helpful if it helps to solve your issue
Visakh
—————————-
My Wiki User Page
My MSDN Page
My Personal Blog
My Facebook Page
Источник
Полностью ошибка звучит как «Подключение к серверу успешно установлено, но затем произошла ошибка при входе (provider: SSL Provider, error:0 — Предоставлен неправильный дескриптор)»
Для подключения используем строку Data Source=tcp:x.x.x.x.;Initial Catalog=bd_name;Persist Security Info=True;User Id=saturn;Password=password;MultipleActiveResultSets=True
Это ошибку вызывают как наша программа, так и встроенный обозреватель (Database Manager) в IIS 8.
Но, что удивительно — SQL Manager for SQL Server (portable, lite edition) подключается нормально.
Очень прошу: подскажите, в какую сторону копать?
ПО: IIS 8, Windows Server 2012, MS SQL 2012 Standart.
-
Вопрос заданболее трёх лет назад
-
5650 просмотров
1. HKEY_LOCAL_MACHINESOFTWAREMicrosoftMSSQLServerClientSuperSocketNetLib должна быть, вот параметра Force Protocol Encryption там может и не быть (это нормально). на стороне сервера sql
2. HKEY_LOCAL_MACHINESOFTWAREMicrosoftMicrosoft SQL ServerMSSQL11.MSSQLSERVERMSSQLServerSuperSocketNetLib
«ForceEncryption»=dword:00000000
«HideInstance»=dword:00000000
«Certificate»=»»
«ExtendedProtection»=dword:00000000
«MSSQL11.MSSQLSERVER» — имя вашего экземпляра sql.
параметры такие стоят?
3. на сервере iis — панель управления — администрирование — источники данных ODBC попробуйте добавить вашу базу в пользовательский DSN, проходит?
Пригласить эксперта
1. HKEY_LOCAL_MACHINESOFTWAREMicrosoftMSSQLServerClientSuperSocketNetLibEncryptForce Protocol Encryption какое значение стоит? Если 1, то изменить на 0 и перезагрузить сервер, помогло? Если да, то остальные вопросы не важны.
2. сервер и клиент на разных компьютерах?
3. криптографическое по на компьютерах используется? если да, то где, клиентский компьютер, сервер sql?
1. Это смотреть на стороне сервера mssql или на стороне iis? (ветки мы эти не нашли).
2. На разных бд и iis на разных серваках стоят.
3. нет такое по нет.
Мне больше всего интересно почему SQL Manager for SQL Server подключается.
моя строка подключения выглядит так :
«Data Source=DESKTOP-Qasd11O\Sasd01;Database=Kourse;User ID=user;Password=123;Connect Timeout=30;Encrypt=False;TrustServerCertificate=True;ApplicationIntent=ReadWrite;MultiSubnetFailover=False»,
помогло исправление TrustServerCertificate=false на true
-
Показать ещё
Загружается…
10 февр. 2023, в 04:49
50000 руб./за проект
10 февр. 2023, в 02:20
3000 руб./за проект
10 февр. 2023, в 01:33
1500 руб./за проект
Минуточку внимания
Join the DZone community and get the full member experience.
Join For Free
SSL certificates are very important for authenticating websites and ensuring connections are encrypted. However, there are some scenarios when they can create headaches. Rather than throw the baby out with the bathwater and abandon the use of SSL, you should know how to use them properly.
One issue that you can run into will occur when connecting with a remote computer. You might try to connect to an SQL Server from a remote computer with the same credentials that you used to connect locally. Unfortunately, you might receive an error like this.
“A connection was successfully established with the server, but then an error occurred during the login process. (provider: SSL Provider, error: 0 — The certificate chain was issued by an authority that is not trusted.) (.Net SqlClient Data Provider).”
There is no way to connect to the server when this error message occurs. The message discusses a certificate and references the SSL provider of the SQL Server. However, you have not installed a certificate on the server, so you won’t be able to identify the underlying issue.
You need to know how to resolve these issues. You also need to make sure that they work with different content settings, such as PowerPoint templates created with a tool like SlideUplift. I mentioned this in my previous article Relationship Between SSL Certificate Key Length and SQL Performance, which established the importance of optimizing SSL when testing PowerPoint presentations and other content settings.
The server will install a self-signed certificate for it, unless you specify that you would like another one to be setup. This certificate is created by the SQL Server. It won’t be supported by a real public key infrastructure. This means that the certificate can encrypt communications and validate their integrity. Unfortunately, it does not verify that you are connecting to the right server, since the only ‘authority’ that assures us that the server is the correct one is the server itself.
That is precisely what this error message is about. What it tells us is that, by default, as the identity of the server cannot be verified, it does not allow the connection.
Something similar happens with many other services that use an SSL certificate by default. For example, when connecting for the first time to a remote computer using a Terminal Server (also called Remote Desktop), you will be asked whether or not you want to trust the certificate and therefore connect to the server.
This makes sense since there are three main purposes of a digital certificate:
- Privacy of the information, which includes encrypting communications in transit.
- The integrity of the communication, which combines them with digital summaries.
- Trust, which is ensured by verifying that communications come from whom they say they come from and that they are not communicating with their intended servers.
The first two purposes can’t be supported if trust is not adequately established.
How Do You Solve This Problem?
If the error is issued by the SQL Server Management Studio when you try to connect from the login screen, then you have to go to the advanced options of that dialog. After reaching this section, you will need to go to the tab named ‘Connection Properties’ and make sure that the ‘Encrypt connection’ option is checked.
You can always uncheck it and prevent the error from occurring, but then the traffic between your computer and the remote SQL Server will no longer be secured, which entirely defeats the purpose of SSL encryptions.
The next step is to go to the ‘Additional Connection Parameters’ tab. You must then write a switch to make the connection trust the remote SQL Server certificate. This additional parameter is:
TrustServerCertificate=True.
Just type it in the text box in that window. After clicking on ‘Connect,’ you will notice that the error disappears and will be able to work normally.
If the error is being given by an application, we only have to modify the connection string and put the same parameter at the end.
If you do this, then you have to be sure that the server we are connecting to is the one we are interested in and that no security problem could be falsifying the DNS so that you connect to another site.
Connection string
sql
Opinions expressed by DZone contributors are their own.