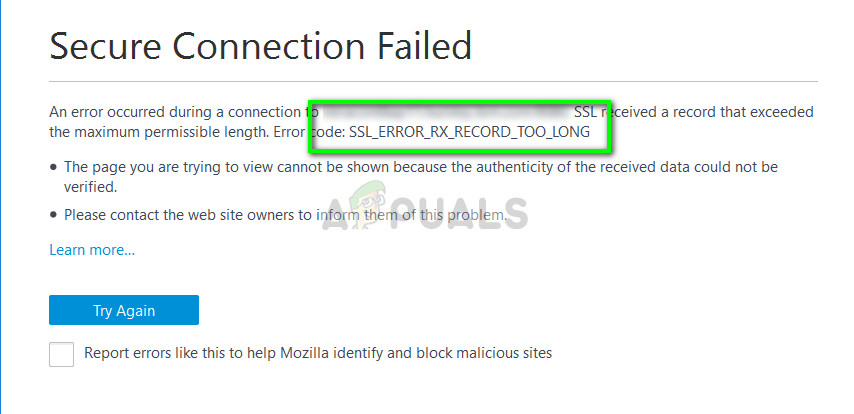
Troubled by seeing Apache ssl_error_rx_record_too_long on your website? You are not alone!
This error frequently occurs when SSL traffic is not set up properly on the target secure server.
At Bobcares, we often get requests from our customers regarding the Apache SSL certificate error as part of our Server Management Services.
Today, we’ll see how our Support Engineers find fix for our customers.
What are the causes of Apache ssl_error_rx_record_too_long?
Everyone wants their websites to be secure. But, improper implementation of security often results in errors like Apache ssl_error_rx_record_too_long.
Some possible causes for this error are:
- SSL traffic is not set up properly on the target server.
- DNS may not be correct in the DNS name on VirtualHost.
- Misconfigured proxy not allowing an SSL handshake on port 443 correctly.
But, how to fix this problem is the main question. Being in the hosting industry for more than a decade, we see many variants of SSL error. Let’s see how our Engineers handle this error in different scenarios.
What are the Fixes?
In simple terms, the fix for the SSL error involves handling the secure traffic reaching the server correctly. We’ll now take a look at the exact steps involved.
When a customer approaches us with Apache ssl_error_rx_record_too_long error, our Support Engineers initially replicate the error from our side. This eliminates any possible browser errors at the user’s computer.
We then proceed with the following actions:
1. We make sure that SSL is running on port 443. Because if SSL is running on a non-standard port, then Firefox may show this error.
netstat -lpan | grep :443We do this by adding the following in the Apache configuration httpd.conf file.
Listen 4432. Upon finding the correct port settings, we check and confirm that the SSL certificate is valid and not expired.
Also, we make sure not more than one SSL is sharing the same IP.
3. On IPv6, our Engineers include the IP Address for eliminating this error.
Listen x.x.x.x:4434. Similarly, when customers get this error on Windows, we check whether the host file on the Windows server is properly set.
If not, we do it by changing VirtualHost domain.com:443 to VirtualHost _default_:443.
Each server configuration differs and so the troubleshooting will not be identical. However, we check the path of the SSL traffic and make corrections. This solves the problem and makes the SSL version of the website working again.
[Having trouble with Apache SSL error? We’ll fix it for you.]
Conclusion
In short, we discussed in detail on possible causes and fixes for Apache ssl_error_rx_record_too_long error. Also, we saw the way by which our Support Engineers find the fix for this error.
PREVENT YOUR SERVER FROM CRASHING!
Never again lose customers to poor server speed! Let us help you.
Our server experts will monitor & maintain your server 24/7 so that it remains lightning fast and secure.
GET STARTED
var google_conversion_label = «owonCMyG5nEQ0aD71QM»;
Добрый день. Пытаюсь настроить хост через ssl. Вроде все элементарно просто, но что то не получается. Изначальный мануал брал тут
Файл хоста:
#<IfDefine SSL>
#<IfModule !mod_ssl.c>
#LoadModule ssl_module modules/mod_ssl.so
#</IfModule>
#<IfModule mod_ssl.c>
<VirtualHost xxx.xxx.xxx.xxx:443>
ServerAdmin info@site.su
ServerName myssl.site.su
DocumentRoot /var/www/site.su/myssl/
<Directory />
Options FollowSymLinks
AllowOverride None
</Directory>
<Directory /var/www/site.su/myssl/>
SSLRequire
Options Indexes FollowSymLinks MultiViews
AllowOverride None
Order allow,deny
allow from all
</Directory>
ScriptAlias /cgi-bin/ /usr/lib/cgi-bin/
<Directory "/usr/lib/cgi-bin">
AllowOverride None
Options +ExecCGI -MultiViews +SymLinksIfOwnerMatch
Order allow,deny
Allow from all
</Directory>
ErrorLog ${APACHE_LOG_DIR}/error.log
# Possible values include: debug, info, notice, warn, error, crit,
# alert, emerg.
LogLevel warn
CustomLog ${APACHE_LOG_DIR}/ssl_access.log combined
#Alias /doc/ "/usr/share/doc/"
#<Directory "/var/www/site.su/myssl/">
# Options Indexes MultiViews FollowSymLinks
# AllowOverride None
# Order deny,allow
# Deny from all
# Allow from 127.0.0.0/255.0.0.0 ::1/128
#</Directory>
# SSL Engine Switch:
# Enable/Disable SSL for this virtual host.
SSLEngine on
# A self-signed (snakeoil) certificate can be created by installing
# the ssl-cert package. See
# /usr/share/doc/apache2.2-common/README.Debian.gz for more info.
# If both key and certificate are stored in the same file, only the
# SSLCertificateFile directive is needed.
SSLCertificateFile /etc/ssl/certs/ssl-cert-snakeoil.pem
SSLCertificateKeyFile /etc/ssl/private/ssl-cert-snakeoil.key
#SSLCertificateFile /etc/apache2/ssl/apache.pem
#SSLCertificateKeyFile /etc/apache2/ssl/apache.key
# Server Certificate Chain:
# Point SSLCertificateChainFile at a file containing the
# concatenation of PEM encoded CA certificates which form the
# certificate chain for the server certificate. Alternatively
# the referenced file can be the same as SSLCertificateFile
# when the CA certificates are directly appended to the server
# certificate for convinience.
#SSLCertificateChainFile /etc/apache2/ssl.crt/server-ca.crt
# Certificate Authority (CA):
# Set the CA certificate verification path where to find CA
# certificates for client authentication or alternatively one
# huge file containing all of them (file must be PEM encoded)
# Note: Inside SSLCACertificatePath you need hash symlinks
# to point to the certificate files. Use the provided
# Makefile to update the hash symlinks after changes.
SSLCACertificatePath /etc/apache2/ssl/
SSLCACertificateFile /etc/apache2/ssl/apache.crt
# Certificate Revocation Lists (CRL):
# Set the CA revocation path where to find CA CRLs for client
# authentication or alternatively one huge file containing all
# of them (file must be PEM encoded)
# Note: Inside SSLCARevocationPath you need hash symlinks
# to point to the certificate files. Use the provided
# Makefile to update the hash symlinks after changes.
#SSLCARevocationPath /etc/apache2/ssl.crl/
#SSLCARevocationFile /etc/apache2/ssl.crl/ca-bundle.crl
# Client Authentication (Type):
# Client certificate verification type and depth. Types are
# none, optional, require and optional_no_ca. Depth is a
# number which specifies how deeply to verify the certificate
# issuer chain before deciding the certificate is not valid.
#SSLVerifyClient require
#SSLVerifyDepth 10
# Access Control:
# With SSLRequire you can do per-directory access control based
# on arbitrary complex boolean expressions containing server
# variable checks and other lookup directives. The syntax is a
# mixture between C and Perl. See the mod_ssl documentation
# for more details.
#<Location />
#SSLRequire ( %{SSL_CIPHER} !~ m/^(EXP|NULL)/
# and %{SSL_CLIENT_S_DN_O} eq "Snake Oil, Ltd."
# and %{SSL_CLIENT_S_DN_OU} in {"Staff", "CA", "Dev"}
# and %{TIME_WDAY} >= 1 and %{TIME_WDAY} <= 5
# and %{TIME_HOUR} >= 8 and %{TIME_HOUR} <= 20 )
# or %{REMOTE_ADDR} =~ m/^192.76.162.[0-9]+$/
#</Location>
# SSL Engine Options:
# Set various options for the SSL engine.
# o FakeBasicAuth:
# Translate the client X.509 into a Basic Authorisation. This means that
# the standard Auth/DBMAuth methods can be used for access control. The
# user name is the `one line' version of the client's X.509 certificate.
# Note that no password is obtained from the user. Every entry in the user
# file needs this password: `xxj31ZMTZzkVA'.
# o ExportCertData:
# This exports two additional environment variables: SSL_CLIENT_CERT and
# SSL_SERVER_CERT. These contain the PEM-encoded certificates of the
# server (always existing) and the client (only existing when client
# authentication is used). This can be used to import the certificates
# into CGI scripts.
# o StdEnvVars:
# This exports the standard SSL/TLS related `SSL_*' environment variables.
# Per default this exportation is switched off for performance reasons,
# because the extraction step is an expensive operation and is usually
# useless for serving static content. So one usually enables the
# exportation for CGI and SSI requests only.
# o StrictRequire:
# This denies access when "SSLRequireSSL" or "SSLRequire" applied even
# under a "Satisfy any" situation, i.e. when it applies access is denied
# and no other module can change it.
# o OptRenegotiate:
# This enables optimized SSL connection renegotiation handling when SSL
# directives are used in per-directory context.
#SSLOptions +FakeBasicAuth +ExportCertData +StrictRequire
<FilesMatch ".(cgi|shtml|phtml|php)$">
SSLOptions +StdEnvVars
</FilesMatch>
<Directory /usr/lib/cgi-bin>
SSLOptions +StdEnvVars
</Directory>
# SSL Protocol Adjustments:
# The safe and default but still SSL/TLS standard compliant shutdown
# approach is that mod_ssl sends the close notify alert but doesn't wait for
# the close notify alert from client. When you need a different shutdown
# approach you can use one of the following variables:
# o ssl-unclean-shutdown:
# This forces an unclean shutdown when the connection is closed, i.e. no
# SSL close notify alert is send or allowed to received. This violates
# the SSL/TLS standard but is needed for some brain-dead browsers. Use
# this when you receive I/O errors because of the standard approach where
# mod_ssl sends the close notify alert.
# o ssl-accurate-shutdown:
# This forces an accurate shutdown when the connection is closed, i.e. a
# SSL close notify alert is send and mod_ssl waits for the close notify
# alert of the client. This is 100% SSL/TLS standard compliant, but in
# practice often causes hanging connections with brain-dead browsers. Use
# this only for browsers where you know that their SSL implementation
# works correctly.
# Notice: Most problems of broken clients are also related to the HTTP
# keep-alive facility, so you usually additionally want to disable
# keep-alive for those clients, too. Use variable "nokeepalive" for this.
# Similarly, one has to force some clients to use HTTP/1.0 to workaround
# their broken HTTP/1.1 implementation. Use variables "downgrade-1.0" and
# "force-response-1.0" for this.
BrowserMatch "MSIE [2-6]"
nokeepalive ssl-unclean-shutdown
downgrade-1.0 force-response-1.0
# MSIE 7 and newer should be able to use keepalive
BrowserMatch "MSIE [17-9]" ssl-unclean-shutdown
</VirtualHost>
#</IfModule>
#</IfDefine>
Если раскомментировать строки IfModule и IfDefine то apache стартует без ошибок, но при попытке доступа к хосту браузер пишет:
Ошибка при установлении защищённого соединения
При соединении с myssl.site.su произошла ошибка. SSL получило запись, длина которой превышает максимально допустимую. (Код ошибки: ssl_error_rx_record_too_long)
Строки:
#SSLCertificateFile /etc/apache2/ssl/apache.pemвнесены мной вместо тех что используются выше. С ними браузер выдает ту же ошибку.
#SSLCertificateKeyFile /etc/apache2/ssl/apache.key
Браузер в любом случае выдает эту ошибку (
В логах apache при текущем конфиге пишет вот что:
[notice] Apache/2.2.22 (Ubuntu) PHP/5.3.10-1ubuntu3.18 with Suhosin-Patch mod_ssl/2.2.22 OpenSSL/1.0.1 configured -- resuming normal operations
Подскажите, пожалуйста, куда смотреть?
Пользователь решил продолжить мысль [time]17 Июнь 2015, 11:49:04[/time]:
Посмотрел эту статью. Поправил конфиг хоста и убрал из него все лишнее:
<VirtualHost xxx.xxx.xxx.xxx:443>
ServerAdmin info@site.su
ServerName myssl.site.su
DocumentRoot /var/www/site.su/myssl/
<Directory />
Options FollowSymLinks
AllowOverride None
</Directory>
<Directory /var/www/site.su/myssl/>
Options Indexes FollowSymLinks MultiViews
AllowOverride None
Order allow,deny
allow from all
</Directory>
ScriptAlias /cgi-bin/ /usr/lib/cgi-bin/
<Directory "/usr/lib/cgi-bin">
AllowOverride None
Options +ExecCGI -MultiViews +SymLinksIfOwnerMatch
Order allow,deny
Allow from all
</Directory>
ErrorLog ${APACHE_LOG_DIR}/error.log
LogLevel warn
CustomLog ${APACHE_LOG_DIR}/ssl_access.log combined
SSLEngine on
SSLCertificateFile /etc/apache2/ssl/apache.pem
SSLCertificateKeyFile /etc/apache2/ssl/apache.key
<FilesMatch ".(cgi|shtml|phtml|php)$">
SSLOptions +StdEnvVars
</FilesMatch>
<Directory /usr/lib/cgi-bin>
SSLOptions +StdEnvVars
</Directory>
BrowserMatch "MSIE [2-6]"
nokeepalive ssl-unclean-shutdown
downgrade-1.0 force-response-1.0
BrowserMatch "MSIE [17-9]" ssl-unclean-shutdown
</VirtualHost>
Ошибка в логе apache:
[error] VirtualHost xxx.xxx.xxx.xxx:443 -- mixing * ports and non-* ports with a NameVirtualHost address is not supported, proceeding with undefined results
[Wed Jun 17 10:40:26 2015] [warn] RSA server certificate is a CA certificate (BasicConstraints: CA == TRUE !?)
[Wed Jun 17 10:40:26 2015] [notice] Apache/2.2.22 (Ubuntu) PHP/5.3.10-1ubuntu3.18 with Suhosin-Patch mod_ssl/2.2.22 OpenSSL/1.0.1 configured -- resuming normal operations
Пользователь решил продолжить мысль [time]17 Июнь 2015, 16:25:16[/time]:
В общем победил.
Оказывается чтоб оно корректно работало, нужно в каждом файле хоста прописать вместо
<VirtualHost xxx.xxx.xxx.xxx:443>это
и
<VirtualHost xxx.xxx.xxx.xxx:80>
<VirtualHost *:443>
и
<VirtualHost *:80>
Все заработало.
In this post, we provide 6 fixes for the “ssl_error_rx_record_too_long” error.
When you use FireFox, there might be some instances that you’ll come across an error. One of them is the “ssl_error_rx_record_too_long” error. In this article, we’re going to go through the nature of this error, what causes it, and what are the possible fixes you can use.
Anyone else seeing this error on Blogspot?
SSL_ERROR_RX_RECORD_TOO_LONG pic.twitter.com/lcj5j4MB2V
— Terence Eden (@edent) November 29, 2016
If you use the latest Microsoft OS versions (e.g. Windows 7, 8, and 10), then there will be instances where you can come across the ssl_error_rx_record_too_long FireFox error.
This error appears when you connect to a website that has an HTTPS protocol using the FireFox browser and the secure connection fails. The problem, however, is that it can be tricky to figure out the exact cause of the problem. There are various factors including:
- Protocol issues
- Browser issues
- Security settings
- Software conflicts
If you’re not tech-savvy, this might sound alarming to you. Fortunately, this problem can be easily fixed by following the fixes mentioned below.
How to Fix the ssl_error_rx_record_too_long Error?
If you find the ssl_error_rx_record_too_long error recurring, then you need to fix it immediately. Here are the following fixes you can follow:
1st Fix: Change the Connection to HTTP Protocol
The very first fix you should try is to connect to the website without the secure protocol. According to Auslogics, the changes are done to the URL so as to bypass a secure connection. To achieve this, you have to follow these steps:
- Open the site with the ssl_error_rx_record_too_long error
- On the address bar, change https:// to http://
- After that, simply reload the page by either clicking on the Refresh icon or pressing the F5 button.
2nd Fix: Update Your Browser
According to Auslogics, your Firefox browser may fail to update itself automatically in accordance with the default settings. Hence it needs to be updated manually, as this may be causing the ssl_error_rx_record_too_long error. Here’s how:
- Open or launch your Firebox browser.
- Head to the upper right corner and look for the Menu icon. Click on it.
- After that, click Help then choose About Firefox from the drop-down.
- This will take you to the browser’s version screen. If your browser is currently outdated, simply update it.
Once you have updated the browser, restart it and check if the problem is fixed. If not, you might want to proceed to the next fix.
3rd Fix: Check Your Browser’s Proxy Settings
Windows Report suggests that the proxy connection might be the cause of the error, and as such recommends that you check its settings. However, there are no specific steps for this. Additionally, the HashedOut blog recommends that you shouldn’t attempt to configure the proxy on your own unless you’re an IT admin, as a misconfigured proxy setting can only lead to more problems.
Video Guide: How To Change Proxy Settings In Google Chrome
4th Fix: Start in Safe Mode
Safe mode can help fix several errors associated with your browser. This means that even the ssl_error_rx_record_too_long error can be solved by activating Firefox’s safe mode. As a matter of fact, the safe mode switches off all add-ons and extensions for a short time before turning back to default. To go to safe mode, follow the steps below as outlined by UGetFix:
- On your Firefox browser, click Open Menu then look for Help.
- From the drop-down list, click Restart with Add-ons Disabled then click Restart.
- Press Start in Safe Mode from the dialogue window that appears.
- After that, check whether the error has been resolved.
Video Guide: Open Google Chrome In Safe Mode
5th Fix: Disable All Add-ons
If the previous fix worked for you, then there’s no longer a need to fix it anymore. However, chances are you’ll still encounter the error when you open the website on a normal browser, and one of the probable cause of this is add-ons.
Add-ons are known to be important, but sometimes, they can also be the cause of the ssl_error_rx_record_too_long error. Thus, they need to be disabled. Here are the steps outlined by Windows Report:
- While still on Safe mode, click on the Menu button.
- Press the Help button from the drop-down menu then choose Restart with Add-ons Enabled.
- After that, in Firefox’s address bar, simply type about:addons then hit Enter.
- Click Disable for each of the add-ons you have added.
- Restart Firefox then visit the website again.
Video Guide: Disabling Chrome Extensions
6th Fix: Disable Your Antivirus Temporarily
In some cases, your antivirus may interpret some SSL certificates as a threat to your browsing activities. Hence, it will block any data from the page. This may be the reason behind the ssl_error_rx_record_too_long error. By disabling your antivirus, you can probably fix this issue.
If you are using a third-party antivirus, it’s best to check its manual so you can disable it. If you are using Microsoft’s Windows Defender, here are how you can do it as what Auslogics suggested (steps will vary depending on your OS version):
Windows 10:
- Press the Windows key or simply click on Start Menu.
- Look for the Gear icon to open the Settings page.
- On the Settings page, click Update and Security.
- Go to Windows Security.
- Select Virus and threat protection. Go to its settings.
- Scroll down to the Real-time protection option then switch it off.
Window 8:
- Navigate to the Start menu then look for the Control Panel.
- Enable the Icons view on your Control Panel.
- Look for the Window Defender icon and click on it.
- Head to Settings.
- On the left side, click on Real-time protection then turn it off by unchecking the box.
- Save the changes afterward.
Window 7:
- Go to your Control Panel from the Start menu.
- Click on the Control Panel and enable the Icons view.
- Click on the Windows Defender icon.
- Head to the Tools section then look for Options.
- On the left pane, click on Real-time Turn it off by unchecking the box next to it.
- Save your settings then exit.
Video Guide: How To Disable Or Enable Windows Defender In Windows 10
Forum Feedback
We looked through different tech forums and support board to find more about the ssl_error_rx_record_too_long message and the problems users have with it. In general, people wanted to know about ssl_error_rx_record_too_long Firefox fix, ssl_error_rx_record_too_long Apache, and ssl_error_rx_record_too_long debian 9. They were also interested in ssl_error_rx_record_too_long Chrome and letsencrypt.
A site owner reported that users couldn’t access the website and that they kept getting the message that ssl_error_rx_record_too_long on all browsers and platforms.
- After he did some research on the subject, he discovered that this error was caused by an incorrect implementation of the SSL on the server side.
- The solution was to check if he had opened and enabled the 443 port on the server.
- He also recommended that you check your vhost config if you’re using Apache2 and that your SSL certificate hadn’t expired.
Another person said that the only thing that solved the ssl_error_rx_record_too_long error was to reinstall the SSL. He also mentioned that you should recheck the SSL configuration to see if you had set the SSLEngine on.
An individual shared that you might get the ssl_error_rx_record_too_long error when the SSL port was speaking in HTTP. The user also commented that the problem could be related to the user’s proxy configuration and that the problem might not be on the server-side at all.
Another computer owner commented that he had problems opening his site using Firefox, but it was working well in Chrome. In Firefox he was getting the ssl_error_rx_record_too_long error, and he was wondering if the issue was related to the SSL certificate or it was a Firefox bug.
A computer expert explains that ssl_error_rx_record_too_long occurs when you haven’t configured a certificate properly on the server’s port. The port is opened to the server, but since the configuration is not correct, users can’t access the website. The person adds that it’s an error that you are likely to encounter in web servers like Apache and Nginx.
Another individual shared that he encountered the ssl_error_rx_record_too_long problem in Apache and that he spent a lot of time researching how to fix it. Finally, he realized that it was related to an issue with the VirtualHost record because he didn’t have a VirtualHost record for the 433 port.
A person pointed out that if you’re a regular user and you can’t access a website because of the ssl_error_rx_record_too_long, you should contact the website’s owner and notify him of the problem.
- The individual states that you can do little on your part to fix the problem because it’s almost always on the server-side.
- What’s more, he warned that turning off your antivirus or switching to HTTP to bypass the issue was dangerous and probably would compromise the security of your online communications.
Another forum poster observes that ssl_error_rx_record_too_long is usually the result of two things – misconfiguration of the listening port or issues with the TSL version. The user recommends that you update your SL/TLS library if you haven’t already done it and that you check that you’re not supporting TLS 1.0 and SSL 3.0.
Another poster pointed out that using an irregular port or not having a trusted certificate would also result in a ssl_error_rx_record_too_long error and that the configuration of the port will depend on the type of server. In addition to this, he advised that you check your certificate once more to ensure that it’s working properly.
A person commented that he was getting the ssl_error_rx_record_too_long error when he was visiting different websites.
- The computer user added that reloading the page sometimes worked but other times didn’t.
- Since it was obvious that the problem was not on the server side, he was wondering what was wrong with his system.
- Other forum members advised him to clear the cache or attempt to load the page in an incognito window.
- They also said that he could write HTTPS before the URL and see if it would solve the problem.
Another user shares that if you’re using Tomcat, you should check if the connector is properly configured to use SSL and that the port number is correct. He also mentions that in Apache you should see if the Listen port matches the numbers in the VirtualHost directive.
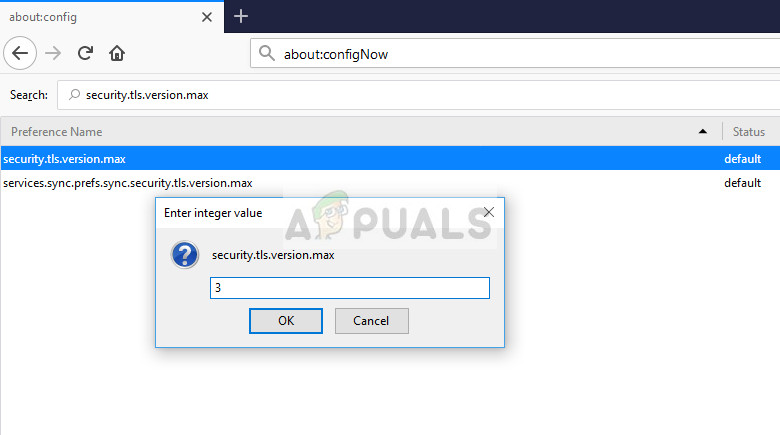
An individual also says that you might experience the ssl_error_rx_record_too_long error if Firefox has enabled TLS 1.3 and the security software has an issue with it. You can fix that by going to typing about:config in the address bar and change the value as follows security.tls.version.max = 3.
Conclusion
One of the above fixes might work to resolve your the ssl_error_rx_record_too_long error. However, if nothing ever worked, the last option would be to reinstall your Firefox browser. It’s pretty straightforward, really. You just have to uninstall it from your programs list then download a fresh copy of the browser and install once again.
Ryan is a computer enthusiast who has a knack for fixing difficult and technical software problems. Whether you’re having issues with Windows, Safari, Chrome or even an HP printer, Ryan helps out by figuring out easy solutions to common error codes.
The error “SSL_ERROR_RX_RECORD_TOO_LONG” occurs because the SSL traffic is not setup correctly in the target secure server. This error might also occur if there is a misconfigured proxy which isn’t allowing an SSL handshake on port 443 correctly.
In layman terms, it means that your browser cannot verify the secure data which is usually because an SSL certificate isn’t correctly configured. This error is widely reported more on Firefox as compared to others.
Now there will be two types of people reading this article; one will be regular users who are accessing a website and the other type will be users who are hosting servers and troubleshooting this issue at their end. We have listed solutions for both types with signifying the solutions for technical users by writing “for advanced users” in front of the heading. Take a look!
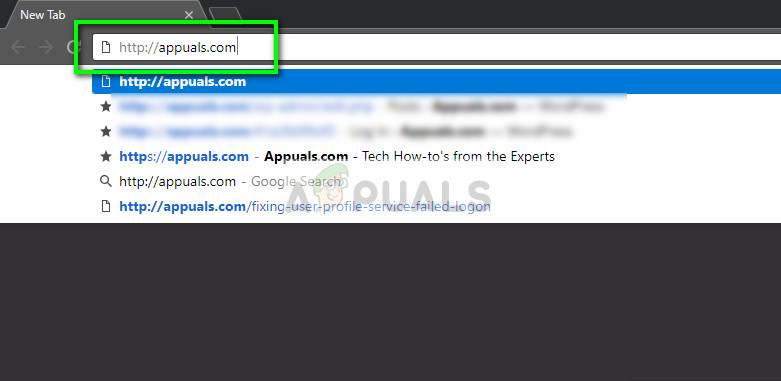
Solution 1: Entering the site with an HTTP protocol
The simplest solution for users who are accessing a specific website is using the HTTP protocol instead of HTTPS. The HTTPS protocol requires a secure handshake and also the SSL certificates. If there is a problem at the server side regarding the secure mechanism, you can still access the website using the default HTTP.
- Open your browser and type the address of the website and press Enter. Chances are that the browser will automatically set the protocol as HTTPS.
- Edit the address line and set it to HTTP.
- Now try accessing the website again and see if the error still pops up.
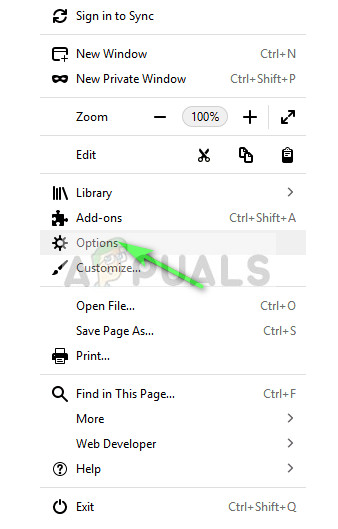
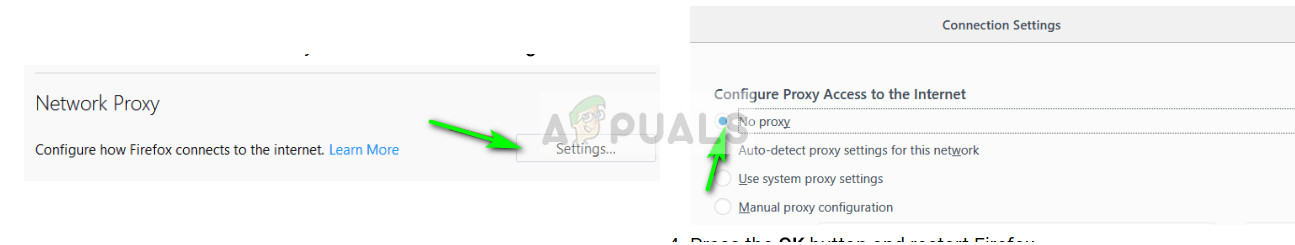
Solution 2: Disabling Proxy in Firefox
Majority of the users who face is this issue use Firefox as their browser. Firefox is known to cause these issues for a long time and a lot of users reported that disabling all the proxies solved the problem for them. Mind you that “auto-detect proxies on this network” is not the same as “No proxy”.
- Open Firefox, open the menu icon present on the top-right side and select “Options”.
- Navigate through the menu until you find “Network Proxy”. Click it and select the option “No proxy”.
- Save changes and restart Firefox. Now check if the problem is solved.
Solution 3: Disabling Antivirus Software
The reason why this error might occur is that of interference from Antivirus software installed on your computer. There are several options which protect your computer by also monitoring the network traffic and verifying all the certificates.
In this solution, you have to explore yourself and see if there are any settings in your antivirus which might be providing these services. For example one of these services is “HTTP scanning in AVG”. Disable all these types of protections and try connecting to the website again.
If you are unable to still fix the problem, you can disable the antivirus completely. You can check our article on How to Disable your Antivirus. Restart your computer after disabling and see if you can access the sites without any problem.
Solution 4: Disable TLS 1.3 (for advanced users)
Another workaround for this is disabling TLS 1.3 protocol using your Firefox settings. You can revert the settings if this doesn’t work for you.
- Type “about:config” in the address bar of Firefox.
- Now search for the entry “tls.version.max”. Change the value from 4 to 3.
- The value 4 stands for TLS 1.3 and 3 stands for TLS 1.2. Restart the browser and check if the problem is solved.
Solution 5: Additional Troubleshooting for Firefox Users
In addition to the above listed solutions, you can also try the following fixes for your Firefox browser. You can easily see how they are done at our website.
- Clear your cache and upgrade Firefox to the latest version available.
- Turn off all of Firefox’s add-ons.
- Refresh your browser entirely. Do note that your bookmarks may get erased at this point.
- Set the tls.version.max value to 0.
- If all the above steps don’t work for your Firefox, consider using an alternate browser such as Chrome for opening the site.
Solution 6: Changing Certificate (advanced users)
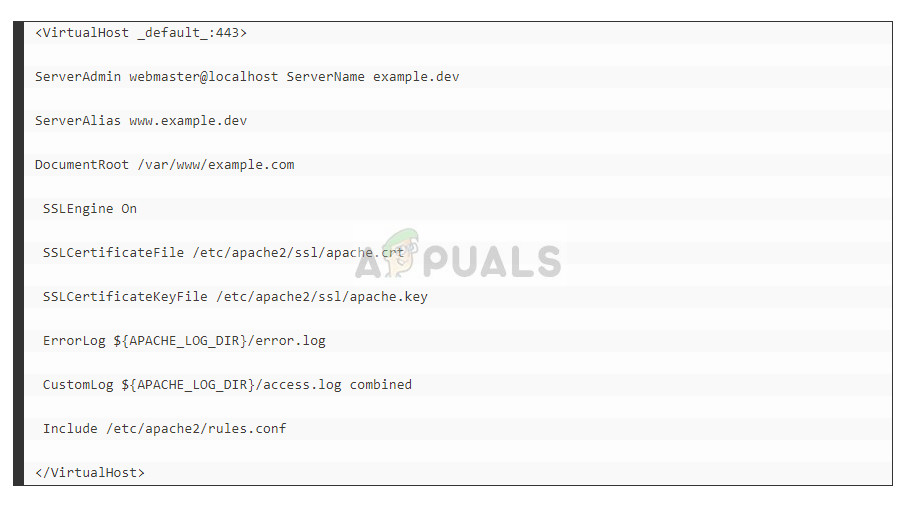
A simple workaround for this issue changing some certificate values of your server. We have included some code as a demonstration.
Here you have to change the default:443 to example.dev:443.
Solution 7: Changing nginx.conf files (for advanced users)
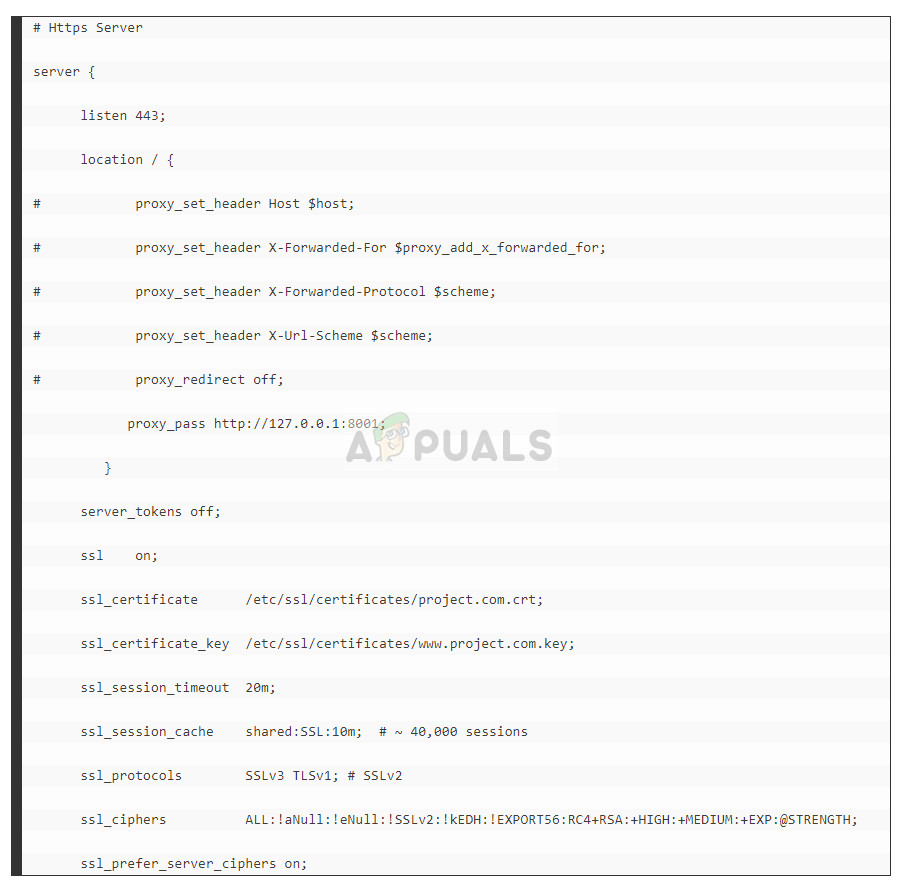
Another change which you can try to resolve the error is changing the nginx.conf file. This solution is specific for people who are using Nginx to run their site. The same principle applies that is we tweaking settings regarding the 443 port.
Below is a piece of code with the workaround mentioned below to help you understand.
Here you have to change listen 443; to listen 443 ssl; Furthermore, you should also remove the line “ssl on;”. Now check if the problem is solved.
Note: If you want to force e.g. phpmyadmin to use SSL/https you will run into this problem if this link is missing, you can use a2ensite default-ssl.
Solution 8: Doing additional checks (for advanced users)
In addition to above solutions, you should also make sure that the following statements hold.
- You should port 443 is open and enabled in the server. This is the standard port for https communications.
- If the SSL is using a non-standard then Firefox may prompt this error. You should ensure is running on port 443.
- If you are using Apache2, you should check that the port for SSL is 443. You can achieve this by setting the httpd.conf file as it follows:
- Make sure that the SSL certificates are not expired.
- If you are Apache2, you check your vhost config file. There are reports that changing <VirtualHost> to _default_ resolved the error.
- You should also make sure that you have only one SSL certificate on one IP. Ensure that all SSL certificates utilize their own dedicated IP.
- In Apache, check that the Listen <port> directive matches the port number in the VirtualHost directive for the website being secured, and that the SSL configuration statements (SSLEngine On, SSLCertificateFile <filename> and so on) appear in the VirtualHost directive for the website or in the SSL configuration file for the server.
Kevin Arrows
Kevin is a dynamic and self-motivated information technology professional, with a Thorough knowledge of all facets pertaining to network infrastructure design, implementation and administration. Superior record of delivering simultaneous large-scale mission critical projects on time and under budget.
There are a few different SSL-related errors in Apache that can cause the following issues:
- SSL errors are reported in the log file causing Apache to not start
- Untrusted certificate warnings in browsers or intermediate certificate errors on DigiCert.com/help
- The browser error message «ssl_error_rx_record_too_long»
Errors That Keep Apache from Starting
Errors that keep Apache from starting can be very frustrating. This usually happens when Apache is reading the configuration files and finds something it doesn’t know how to handle.
The first step when you experience this issue is to check your log file for an error that might point to the problem.
The default location of the log files is as follows:
| Debian (Ubuntu): | /var/log/apache2/error_log |
| Red Hat Enterprise Linux, CentOS: | /var/log/httpd/error_log |
| Windows: | C:Program FilesApache GroupApache2logserror.log |
| Default Location From Compiling Source Code: | /usr/local/apache2/logs/error_log |
If the log files are not in the above location, you may have defined a different log file location in your httpd.conf file or the VirtualHost section of your .conf file.
Some possible conf file errors you may find are listed below.
«Unable to configure RSA server private key» and «certificate routines:X509_check_private_key:key values mismatch» Errors
If you see one of these errors it usually means that the private key that is being loaded in the VirtualHost section of your .conf file doesn’t match the SSL Certificate being loaded in the same section.
To check if the two files match, run the following OpenSSL command on each of them:
openssl x509 -noout -modulus -in your_domain_com.crt | openssl md5
openssl rsa -noout -modulus -in your_domain_com.key | openssl md5
If the modulus of the two files doesn’t match exactly, do one of the following:
- Find the .key file matching your .crt file and update the VirtualHost in your .conf file to match.
-
Reissue your certificate by either generating two new files with the OpenSSL CSR Wizard
or by creating a new CSR from your existing private key file using the following command.Note that the existing private key must be at least 2048 bits. If the key is less than 2048 bits you will have to recreate the key.
openssl req -new -key your_domain_com.key -out your_domain_com.csr
«Invalid command ‘SSLEngine'» Error
This error can be caused by mod_ssl not being installed on a server. This module is required by Apache to create SSL connections.
To enable this module on CentOS/RedHat Linux run the following command from the console:
sudo yum install mod_ssl
To enable this module on a Debian-based distro run the following command:
a2enmod ssl
«SSL3_READ_BYTES:sslv3 alert handshake failure» and «SSL23_WRITE:ssl handshake failure» Errors
These errors are caused by a directive in the configuration file that requires mutual authentication. For example, if an SSL Certificate is sent from the server and then a separate SSL Certificate is sent back from the client during the SSL handshake, this error will occur.
In our experience, this directive is usually included by accident. To remove the directive and thus fix the error, open your conf file. Change SSLVerifyClient or SSLVerifyClient optional_no_ca to SSLVerifyClient none, then restart Apache.
This change will tell the Apache server to stop looking for a client certificate when completing the SSL handshake with a client computer.
Another possible cause of these errors is including the line SSLVerifyDepth 1 in the conf file. Comment out the line by adding a # to the beginning (ex. #SSLVerifyDepth 1).
«SSLSessionCache: Invalid argument: size has to be >=8192 bytes» Error
This error happens when the name of the folder where Apache for Windows is installed includes spaces or parenthesis.
To fix this, move all of the files for Apache to a different folder (ex. c:/Program Files (x86)/Apache2/ to c:/Apache/Apache2/).
Alternatively, you can change the folder name to a short name. Run the following command to find the short name for the folder:
dir /x C:
You will also need to add a backslash () to avoid the ~ character as follows:
C:/Program Files (x86)/Apache2/ will change to C:/Progra~2/Apache2/
Finally, restart Apache.
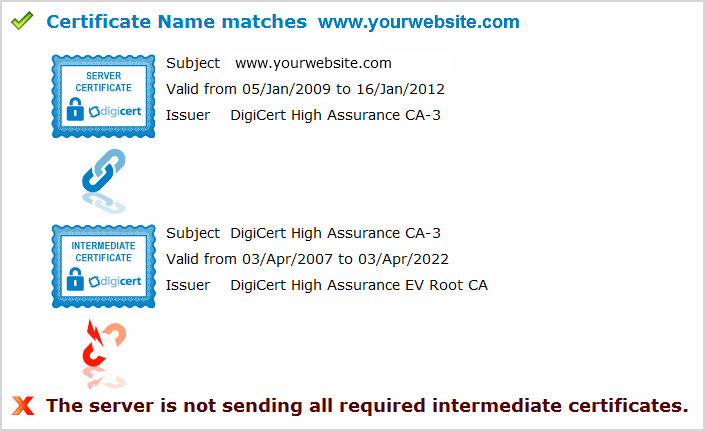
Untrusted and Missing Intermediate Certificate Errors
-
The VirtualHost section of your .conf file (usually httpd-ssl.conf, ssl.conf, or virtual-host.conf) for SSLCertificateChainFile is either commented out (e.g. #SSLCertificateChainFile),
or is pointing to the wrong SSL Intermediate Certificate file. To correct this, simply uncomment the line and make sure the SSLCertificateChain file points to DigiCertCA.crt. -
The VirtualHost section of your .conf file is configured correctly but you already have a virtual host configured using a different .conf file for the IP address and port that you
are trying to install the SSL Certificate to.
The problem is usually that the other .conf file is pointing to the wrong SSL Intermediate Certificate file.To find this file, run a quick grep command (change /etc/apache2/ to your Apache home directory). This will search all of the subfolders in the current directory for a .conf file containing SSLCertificateChainFile.
grep -i -r "SSLCertificateChainFile" /etc/apache2/On Windows use the following command:
findstr /s /i "SSLCertificateChainFile" *.conf
Two things can cause this error in the SSL Certificate Tester:
Once you find the file, uncomment the line if it is commented out (remove the #) and make sure the SSLCertificateChain file points to DigiCertCA.crt. Then restart Apache.
«SSL received a record that exceeded the maximum permissible length, ssl_error_rx_record_too_long» Error
-
The file /conf/extra/httpd-ssl.conf was configured with the correct SSL information but isn’t being loaded because httpd.conf isn’t loading it.
To fix this error, uncomment the following line (remove the #). Then restart Apache.
#Include conf/extra/httpd-ssl.conf -
Apache isn’t set to listen on port 443 for secure traffic. To fix this, add the following line before the <VirtualHost> block is loaded:
Listen 443If you’re using IPv6 you’ll need to include the IP address as well as the port:
Listen 192.168.0.1:443If you’re running https on a non-standard port you’ll need to tell Apache to listen for an SSL connection on that port:
Listen 192.168.0.1:8443 httpsIf you see the above inside of an <If DefineSSL> block, you need to make sure you are defining SSL when you start Apache. Normally SSL should be defined on its own,
but if it isn’t being defined you can try the following commands for earlier versions of Apache 2:
path/to/httpd -D SSL -k start
path/to/apachectl startssl
path/to/httpd startssl
-
If you’re running Apache under Windows make sure the host file on the Windows server is set up correctly. It should be in C:WindowsSystem32Driversetchosts.
Some people fix this error by changing VirtualHost your.domain.com:443 to VirtualHost _default_:443, etc. -
Make sure in the <VirtualHost> block Apache is configured to use SSL with the SSLEngine directive as follows:
<VirtualHost your.domain.com:443>
SSLEngine On
[rest of VirtualHost]
</VirtualHost>
This error most commonly appears in Firefox browsers, but similar errors can appear in other browsers as well.
This error often occurs because SSL traffic is not set up correctly on the server that you are trying to secure. For example, the DNS is not correct in the DNS name on your VirtualHost.
Here are some ways to fix this error:
This error can also occur if you have a misconfigured proxy that doesn’t allow you to do an SSL handshake on port 443 correctly.
The way to test this is to try connecting to the site from outside of your network with a few different web browsers and see if you still receive the error. If you do not receive the error the proxy is probably misconfigured.
This document (7012859) is provided subject to the disclaimer at the end of this document.
Environment
Apache
SUSE Linux Enterprise Server 10
SUSE Linux Enterprise Server 11
Situation
Browser returning Error: ssl_error_rx_record_too_long when attempting to view website over https.
For example, load browser, in the address bar, enter the url as follows: https://<ip_or dns_name> , hit <enter>
Page displays: ssl_error_rx_record_too_long
Resolution
Often times this error is seen with Apache, when port 443 has been enabled (i.e. by adding a vhost-ssl.conf file), but SSL itself has NOT yet been loaded and enabled.
Open the /etc/sysconfig/apache2 file and look for the APACHE_MODULES= line, and make sure that ssl is in the list of modules (if ssl is not part of the list, go ahead and add it just before the closing quotes). Here’s an example:
APACHE_MODULES=»actions alias auth_basic authn_file authz_host authz_groupfile authz_default authz_user
authn_dbm autoindex cgi dir env expires include log_config mime negotiation setenvif ssl suexec userdir php5 jk proxy proxy_ajp»
Notice ssl in the line. (NOTE: the position here is NOT important)
Next look for the Line APACHE_SERVER_FLAGES = «» and make sure the value between the quotes is SSL as follows:
APACHE_SERVER_FLAGS=»SSL»
Save the changes and run rcapache2 restart.
Disclaimer
This Support Knowledgebase provides a valuable tool for SUSE customers and parties interested in our products and solutions to acquire information, ideas and learn from one another. Materials are provided for informational, personal or non-commercial use within your organization and are presented «AS IS» WITHOUT WARRANTY OF ANY KIND.
- Document ID:7012859
- Creation Date:
16-Jul-2013 - Modified Date:03-Mar-2020
-
- SUSE Linux Enterprise Server
< Back to Support Search
For questions or concerns with the SUSE Knowledgebase please contact: tidfeedback[at]suse.com