Содержание
- Configure Exim for outbound remote mail problem
- Mr. Jinx
- Configuring and customizing Exim | Directadmin Docs
- ikkeben
- Mr. Jinx
- ikkeben
- SSL verify error: certificate name mismatch
- Legendary
- Legendary
- cPanelMichael
- Legendary
- Тема: Ошибка склейки цепочки сертификатов Exim
- Ошибка склейки цепочки сертификатов Exim
- SSL Certificate Name Mismatch Error
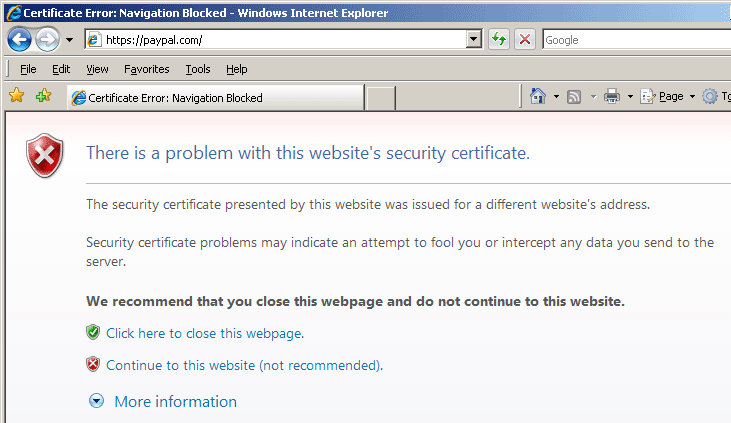
- «The security certificate presented by this website was issued for a different website’s address.»
- Different name mismatch errors in different web browsers
- Comments
Configure Exim for outbound remote mail problem
Mr. Jinx
Verified User
I have configured Exim to use a remote outbound mail server. As mail service, I make use of mxroute.com.
Followed this very nice tutorial:
Configuring and customizing Exim | Directadmin Docs
The problem is something goes wrong when the remote smtp server is resolved to an IPv6 address.
In /etc/exim.routers.pre.conf I have this line:
The weird part is «no IP address found for host 2a01» and after that it fails authentication.
It seems the first octet of the IPv6 address is being used instead of the complete IPv6 address?
If I replace the FQDN in /etc/exim.routers.pre.conf with an IPv4 address like this:
. then it works fine!
So any idea’s how to make the route_list accept FQDN’s that resolve to a proper IPv6 address?
ikkeben
Verified User
Square brackets because of the colons in ipv6. ?
- When IPv6 addresses are involved, it gets worse, because they contain colons of their own. To make this case easier, it is permitted to enclose an IP address (either v4 or v6) in square brackets if a port number follows. For example:
route_list = * » www.exim.org
Mr. Jinx
Verified User
I tried the square brackets, but it does not seem to work when using FQDN:
Error: no IP address found for host [smtp.example.com]
With double colons:
Error: no IP address found for host 2a01
ikkeben
Verified User
I tried the square brackets, but it does not seem to work when using FQDN:
Error: no IP address found for host [smtp.example.com]
With double colons:
Error: no IP address found for host 2a01
In above example exim.org the square brackets for IPv6 adress itself.
the smtp. is no fqdn the hostname itself should be FQDN but there i can be very wrong.
Do first some dns / ns test online for those hostname / servers you need there
and did you connect the ipv6 in admin with the ipv4 pointing or so i don’t know exactly now.
Источник
SSL verify error: certificate name mismatch
Legendary
Member
I have a couple of cPanel servers and today I noticed an SSL issue when sending/receiving emails.
Log from the sending server:
Take note of the following:
Legendary
Member
cPanelMichael
Administrator
You will notice this with Exim 4.86 based on the following changes:
What hostname is the user entering for outbound email in their email client?
Legendary
Member
You will notice this with Exim 4.86 based on the following changes:
What hostname is the user entering for outbound email in their email client?
Thanks for responding.
I’m not sure if the sender’s outbound mail server settings matter in this case as the error is logged by the sending server, meaning the issue is with the recipient server’s mail SSL setup.
1. Send mail from [email protected] (on server some.hostname1.com) to [email protected] (on server some.hostname2.com)
2. Email is received by the server some.hostname2.com and is delivered to [email protected]
3. All seems fine but an error is logged in some.hostname1.com‘s /var/log/exim_mainlog:
As mentioned above, a workaround to this issue is by changing cPanel’s default MX entry for the recipient (in this case, example2.com) to the server’s hostname. Then again what is the whole point of having mail SNI if we’re required to do this?
This isn’t an urgent issue as emails are being sent and received — I just happened to come across this issue and figured I’d ask if this behavior is 100% intentional or if it’s a bug. Hope this makes sense and thanks for your time!
Источник
Тема: Ошибка склейки цепочки сертификатов Exim
Опции темы
Поиск по теме
Ошибка склейки цепочки сертификатов Exim
При замене сертификата Exim (через панель — Почтовые домены — SSL сертификат) получил глюк в виде ошибки отправки почты.
После недолгих разбирательств выяснилось что панель неправильно склеивает сертификат.
Лог exim пестрил ошибкой:
В файле /etc/exim/ssl/exim.crt мы получаем сертификат склеенный таким образом:
А сертификат и ca сертификат нужно склеивать, вот так:
Когда вы уже научитесь качественно тестировать функционал, перед выпуском в продакшен.
Задолбался ваши косяки выискивать и руками исправлять.
___________________
CentOS 7
ISPmanager Lite 5.90.0
Последний раз редактировалось Pegas-x; 15.03.2017 в 21:54 .
Здравствуйте. Да, действительно, об этой проблеме известно разработчикам, исправим. Приносим свои извинения за доставленные неудобства.
К слову если кому понадобится, набросал скрипт замены сертификата по всем службам панели.
Только пути свои пропишите, если у вас они отличные от моих.
По крайней мере этот способ быстрее и надежнее, чем доверять панели 
Только внимательно проверьте пути к файлам и их названия у вас на сервере.
P.S. Предложение разработчикам, сделайте замену сертификатов для всех служб одной кнопкой. К примеру в списке сертификатов сделать кнопку, при нажатии на которую, выбранный администратором сертификат, будет установлен в качестве основного для: Exim, Dovecot, Proftpd, ihttpd и они будут автоматом перезапущены. Сделать это не сложно, а жизнь облегчит.
Последний раз редактировалось Pegas-x; 16.03.2017 в 22:27 .
Источник
SSL Certificate Name Mismatch Error
«The security certificate presented by this website was issued for a different website’s address.»
The name mismatch error indicates that the common name (domain name) in the SSL certificate doesn’t match the address that is in the address bar of the browser. For example, if the certificate is for www.paypal.com and you access the site without the «www» (https://paypal.com), you will get this SSL certificate name error. If you aren’t the website administrator you will want to always access the site with the full name (usually include the «www.» before the domain name) or ask the website owner to fix the problem.
If you are the website administrator, you will usually want to forward all traffic without the «www» to an address with the «www» and get an SSL certificate with the «www» in the common name. That way you will completely avoid the name mismatch error. Some certificate authorities get around this problem by issuing a certificate with SANs. So you can get a certificate for paypal.com and include a SAN of www.paypal.com so you don’t get a name mismatch error. Another common reason for this error is if you are accessing a server using an internal name when the SSL certificate on it just has the public name on it. In this situation you can get a UC certificate that has both the external public name and the internal server name in the certificate. You can verify whether you will get a name mismatch error by using our SSL Checker.
Most web browsers make it clear that you shouldn’t just continue when you receive this error. This is because, while most of the time it doesn’t, it could indicate that a phisher is trying to pass a website off as a legitimate site. You shouldn’t have to continue through this error message on legitimate web sites.
This error is often phrased differently depending on the web browser. These are some common ways the name mismatch error is stated in other browsers:
Different name mismatch errors in different web browsers
«The security certificate presented by this website was issued for a different website’s address.»
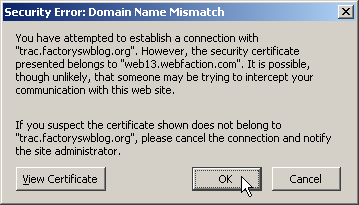
«You have attempted to establish a connection with «www.paypal.com». However, the security certificate presented belongs to «paypal.com.phishingsite.com». It is possible, though unlikely, that someone may be trying to intercept your communication with this web site.
If you suspect the certificate shown does not belong to «www.paypal.com», please cancel the connection and notify the site administrator.»
| Web Browser | Error Message |
|---|---|
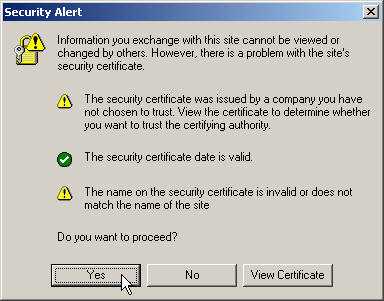
| Internet Explorer 6 | «The name on the security certificate is invalid or does not match the name of the site» |
| Internet Explorer 7 | |
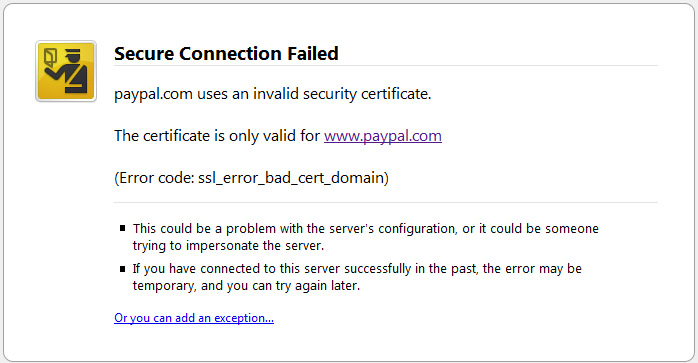
| Firefox 3 | «www.phishingsite.com uses an invalid security certificate. The certificate is only valid for: www.paypal.com» |
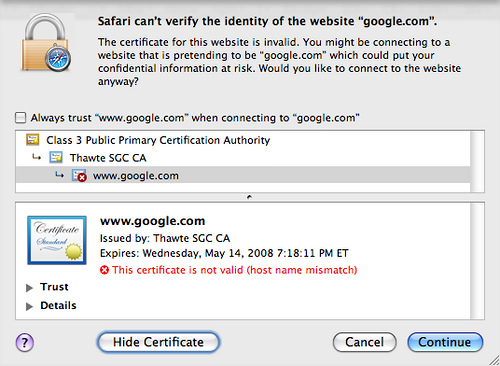
| Safari 3 | «This certificate is not valid (host name mismatch)» |
Originally posted on Thu Nov 6, 2008
if we have 2 profiles on WAS server with the same sub domain can we use the same SSL for both? would it still show this issue?
I am facing issue while accessing one site getting the certificate of different site where as both the site are binded with different IPs on same server. i.e — If I am accessing www.xyz.com I am getting the certificate of www.pqr.com.
I am recieving this error after dns records were pointed to a new server where the site would be hosted the current server uses a certificate that can be used more than once is there a way of fixing this at all?
Your certificate is *.myherbalife.com therefore when the web site has two or more «.» (periods) to left of myherbalife then you will get the mismatch error. The * portion of your URL refers to a wildcard however with SSL if you have a «.» as part of wildcard portion you will get this error. Suggest changing your DNS to use «-» instead of a «.»
Internet Explorer 7 «The security certificate presented by this website was issued for a different website’s address.»
I’m not getting the SECURITY ALERT Screen, prev i use to get it an when i click yes, it will go to the secured page.
Now my prob with the ceritifacte error is originally the certifacte was issue to «*.myherbalife.com» ( equifax) and now i tried to connect «dlm.myherbalife.com» that time i get this error.
help me to clear this error.
As Robert says, if you have a wildcard certificate for one domain, yo won’t have the error if the website is like
But if you use it for a websike like
you will get it, because the wildcard certificate it’s only for the services in «dominio.com», not for the subdomain «city.dominio.com».
Anyway it’s a valid certificate, as for «city.dominio.com» like for «dominio.com», the problem is the message (it doesn’t look nice). Internet Explorer have the option to disable it, but you need to do that in each IE client, so it’s not very effective. This otion is in Internet tools/Advanced Options/security/, it’s something like «Notify abaut the not mattching in the adress of the certificates» (I have it in spanish, so it’s not exatly this, but something like this).
CA are offering wildcard services which allows an organisation to release SSL fast but this results in a cert error. Does anyone know the best set-up for a wildcard entry to avoid the error message to the end user?
Ive got this issue using a watchguard firebox with single sign on. nightmare.
it tells me domain name mismatch when i open a particular website, pls what do i do to solve this problem. thanks
The security certificate presented by this website was not issued by a trusted certificate authority.
The security certificate presented by this website was issued for a different website’s address
I have a Mac and use Macmail, I haven’t made any changes to our email or site logins or certificates however I’m getting the dialog «Mail can’t verify the identity of «gives our mail server #» (which is the correct #). You might be connecting to a server that is pretending to be «number» .
I clicked «Show Certificate» and it gave me GeoTurst Global CA > .securesites.com. «This certificate is not valid (host name mismatch). I called our web host, Verio, and they said for now just Connect each time, don’t click «Always trust». this happens every time I open my email client. Could it be pisching or is this authentic? Can I click «Always Trust»?
Ander, thank you for your tip, it worked fine. Muchas gracias! 🙂
i can’t uploade from my wibe sit to server
tise error
Security Exception
Description: The application attempted to perform an operation not allowed by the security policy. To grant this application the required permission please contact your system administrator or change the application’s trust level in the configuration file.
Exception Details: System.Security.SecurityException: Request for the permission of type ‘System.Security.Permissions.FileIOPermission, mscorlib, Version=2.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089’ failed.
Line 210: ‘File.Copy(img_path.PostedFile.FileName, «c:»)
It sounds like your host is just using a shared certificate on your site. It would be more secure to use a separate certificate for your site, but you should be fairly safe to click through the warnings in this case.
Your certificate is *.myherbalife.com therefore when the web site has two or more «.» (periods) to left of myherbalife then you will get the mismatch error. The * portion of your URL refers to a wildcard however with SSL if you have a «.» as part of wildcard portion you will get this error. Suggest changing your DNS to use «-» instead of a «.»
I setup cname for a domain. Both are different domains like xyz.com, zxy.com and both are wildcard SSL enabled.
I am getting this below error in my browser.
You attempted to reach xyz.com, but instead you actually reached a server identifying itself as *.zxy.com. This may be caused by a misconfiguration on the server or by something more serious. An attacker on your network could be trying to get you to visit a fake (and potentially harmful) version of xyz.com.
Is there a way by which we can allow web application access with multiple URLS viz., using IP address (say 151.34.25.190), hostname (say 01hm45678) and complete hostname (say 01hm45678.india.com). The user should be able to access the we app using either of the URLs without giving any certificate error.
Yes, using Subject Alternative Name extensions.
Thinakaran, you’ll need to have both names included in the certificate to avoid the name mismatch error.
When i use the SSL checker with my Domain of www.limosa.com.au it comes up with someone elses domain name. what does this mean? i have no affiliation with this other domain and i am getting annoyed that i cannot read emails on my devices because they dont match up.
I need help this has been problem has been coming up for awhile it will not let me in to aol mail on uk side only usa side using .com. and also other sites i use a lot says the certificate is not right but these will not work by changing to .com as they uk sites any help would be appreciated. google chrome is browser.
i need help, In my magento ecommerce website i have activate the ssl certificate but it is not redirect to https://www.mixrack.com from mixrack.com
i have installed ssl certificate for a website runing on iis 8, certificate had been working fine until 15 days back, and on the same server Macfee EPO server is also runing. now when i accessing my website, certificate is not showing, i used ssl checker to check the appropriate certificate for the website, but it showing the MCAfee EPO server certificate , can some help me out to resolve this certificate problem,
When I check a site with a cPanel auto ssl cert https://www.sslshopper.com/. you report a possible problem in that «None of the names in the cert . . .»
and report this about the cert — Common name: li1265-51.members.linode.com
When every browser I check the cert in has the common name whm.topline.cloud, and viewing the cert has the following.
—
X509v3 Subject Alternative Name:
DNS:whm.topline.cloud, DNS:mail.whm.topline.cloud, DNS:www.whm.topline.cloud
—
I think the report is wrong in this instance.
Thanks for posting about this. I fixed the SSL Checker so that it grabs the correct certificate (the server seems to be sending a different certificate if you connect with the IPv6 address)
Nice, thanks for the quick fix, and a valuable tool.
You should not have to continue through this error message on legitimate website. This error is often phrased differently depending on the web browser.
www.Cricketlivehd.com had the same problem. the better way it to just call your hosting guys and get the common name changed on their servers to solve it all for you.
Has anyone been able to find a way to check hostname mismatch with OpenSSL
Horizon Hobby thinks it is my browser(s). Gawd!
They are missing a SAN in their cert to make it work. dummies!
SSL Wizard
Cheap SSL Certificates
Code Signing Certificates Wildcard Certificates
SSL Tools
Источник
Adblock
detector
 Robert (2014-12-13) Robert (2014-12-13) |
|
It looks like you have a certificate for *.dlm.myherbalife.com. That is why you get an error when you access it with dlm.myherbalife.com. You will need to change the common name in the certificate to *.myherbalife.com to get rid of the error. Talk to your certificate provider (GeoTrust) about how to do this. |
 Sandeep (2014-12-13) Sandeep (2014-12-13) |
 Vinayak (2014-12-13) Vinayak (2014-12-13) |
 Megini (2014-12-13) Megini (2014-12-13) |
 John (2014-12-13) John (2014-12-13) |
 Mary Sylvia.S (2014-12-13) Mary Sylvia.S (2014-12-13) |
 Ander (2014-12-13) Ander (2014-12-13) |
 Paul (2014-12-13) Paul (2014-12-13) |
 Sonic Bass (2014-12-13) Sonic Bass (2014-12-13) |
 ikye (2014-12-13) ikye (2014-12-13) |
 taje (2014-12-13) taje (2014-12-13) |
 AR (2014-12-13) AR (2014-12-13) |
 Andjelko (2014-12-13) Andjelko (2014-12-13) |
 marwan (2014-12-13) marwan (2014-12-13) |
 Robert (2014-12-13) Robert (2014-12-13) |
 sagar (2014-12-13) sagar (2014-12-13) |
 Thinakaran (2014-12-13) Thinakaran (2014-12-13) |
 Niti (2014-12-13) Niti (2014-12-13) |
 RickP (2015-01-31) RickP (2015-01-31) |
 Default Admin User (2014-12-13) Default Admin User (2014-12-13) |
 Nick (2014-12-13) Nick (2014-12-13) |
 Russ Hill (2015-01-20) Russ Hill (2015-01-20) |
 Pankaj Patil (2016-06-09) Pankaj Patil (2016-06-09) |
 vinay (2016-08-09) vinay (2016-08-09) |
 jimlongo (2018-06-04) jimlongo (2018-06-04) |
 SSL Shopper (2018-06-05) SSL Shopper (2018-06-05) |
 jimlongo (2018-06-05) jimlongo (2018-06-05) |
 Gaurav Maniar (2018-06-13) Gaurav Maniar (2018-06-13) |
 Faheem iqbal (2019-06-10) Faheem iqbal (2019-06-10) |
 Roberto Cortes (2020-09-08) Roberto Cortes (2020-09-08) |
 CP (2020-11-13) CP (2020-11-13) |
Golub Mikhail
unread,
Jul 28, 2015, 9:51:13 AM7/28/15
to exim-…@mailground.net
Доброе утро.
Как отключить запись этого «мусора» в лог?
SSL verify error: depth=1 error=certificate not trusted cert=
SSL verify error: certificate name mismatch:
Этот параметр не помог:
log_selector = -tls_certificate_verified
P.S. В 4.85 так не мусорило в лог.
—
Голуб Михаил
_______________________________________________
Exim-users mailing list
Exim-…@mailground.net
http://mailground.net/mailman/listinfo/exim-users
dawnshade
unread,
Jul 28, 2015, 10:01:39 AM7/28/15
to Exim MTA на русском
24 JH/06 Verification of the server certificate for a TLS connection is now tried
25 (but not required) by default. The verification status is now logged by
26 default, for both outbound TLS and client-certificate supplying inbound
| tls_verify_cert_hostnames | Use: smtp | Type: host list† | Default: * |
поставить в пустую строку не поможет в транспорте?
Вторник, 28 июля 2015, 9:50 +03:00 от Golub Mikhail <exim…@gmn.org.ua>:
Golub Mikhail
unread,
Jul 28, 2015, 10:50:48 AM7/28/15
to Exim MTA на русском
Спасибо, но не помогло.
Ошибки в лог пишутся при приеме сообщений – или из мира, или с внутренних серверов.
Они и на 4.85 были (так как опции сборки и конфиг те же), но в лог не писались.
Например:
2015-07-28 10:16:32 [77.88.21.89] SSL verify error: depth=1 error=unable to get local issuer certificate cert=/C=PL/O=Unizeto Technologies S.A./OU=Certum Certification Authority/CN=Certum Level IV CA
2015-07-28 10:16:32 [77.88.21.89] SSL verify error: depth=1 error=certificate not trusted cert=/C=PL/O=Unizeto Technologies S.A./OU=Certum Certification Authority/CN=Certum Level IV CA
Golub Mikhail
unread,
Jul 28, 2015, 2:15:56 PM7/28/15
to Exim MTA на русском
Опции сборки:
Exim version 4.86 #0 (FreeBSD 10.1) built 28-Jul-2015 10:36:45
Copyright (c) University of Cambridge, 1995 — 2015
(c) The Exim Maintainers and contributors in ACKNOWLEDGMENTS file, 2007 — 2015
Probably Berkeley DB version 1.8x (native mode)
Support for: crypteq use_setclassresources Perl Expand_dlfunc OpenSSL Content_Scanning Old_Demime DNSSEC PRDR Experimental_SPF Experimental_SRS
Lookups (built-in): lsearch wildlsearch nwildlsearch iplsearch cdb dbm dbmjz dbmnz dnsdb dsearch ldap ldapdn ldapm mysql passwd
Authenticators: plaintext
Routers: accept dnslookup ipliteral manualroute queryprogram redirect
Transports: appendfile/mbx autoreply pipe smtp
Fixed never_users: 0
Size of off_t: 8
Configuration file is /usr/local/etc/exim/configure
Т.е. использую openssl.
Golub Mikhail
unread,
Jul 28, 2015, 3:11:18 PM7/28/15
to Exim MTA на русском
Замена опции TLS на GNUTLS помогла.
Использовать openssl уже нельзя? 
> ——Original Message——
> From: Exim-users [mailto:exim-user…@mailground.net] On Behalf
> Of Golub Mikhail
> Sent: Tuesday, July 28, 2015 2:15 PM
> To: Exim MTA на русском
> Subject: Re: [Exim-users] Exim 4.86: SSL verify error
>
Victor Ustugov
unread,
Jul 28, 2015, 10:08:09 PM7/28/15
to Golub Mikhail
приветствую
Golub Mikhail wrote:
> Спасибо, но не помогло.
>
> Ошибки в лог пишутся при приеме сообщений – или из мира, или с
> внутренних серверов.
>
> Они и на 4.85 были (так как опции сборки и конфиг те же), но в лог не
> писались.
>
>
>
> Например:
>
> 2015-07-28 10:16:32 [77.88.21.89] SSL verify error: depth=1 error=unable
> to get local issuer certificate cert=/C=PL/O=Unizeto Technologies
> S.A./OU=Certum Certification Authority/CN=Certum Level IV CA
>
> 2015-07-28 10:16:32 [77.88.21.89] SSL verify error: depth=1
> error=certificate not trusted cert=/C=PL/O=Unizeto Technologies
> S.A./OU=Certum Certification Authority/CN=Certum Level IV CA
скорее всего это ошибки проверки сертификата при проведении встречной
проверки отправителя.
если тут же послать письмо от того же отправителя на данный сервер, то
сообщение об ошибке вряд ли будет выведено в лог повторно.
также при отключении встречной проверке отправителя скорее всего таких
сообщений при получении писем не будет.
> *From:*Exim-users [mailto:exim-user…@mailground.net] *On Behalf
> Of *dawnshade
> *Sent:* Tuesday, July 28, 2015 10:01 AM
> *To:* Exim MTA нарусском
> *Subject:* Re: [Exim-users] Exim 4.86: SSL verify error
>
>
>
> 24
> <http://git.exim.org/exim.git/blob/exim-4_86:/doc/doc-txt/ChangeLog#l24>JH/06 Verification of the server certificate for a TLS connection is now tried
>
> 25
> <http://git.exim.org/exim.git/blob/exim-4_86:/doc/doc-txt/ChangeLog#l25> (but not required) by default. The verification status is now logged by
>
> 26
> <http://git.exim.org/exim.git/blob/exim-4_86:/doc/doc-txt/ChangeLog#l26> default, for both outbound TLS and client-certificate supplying inbound
>
> 27
> <http://git.exim.org/exim.git/blob/exim-4_86:/doc/doc-txt/ChangeLog#l27> TLS connections
>
>
>
> *tls_verify_cert_hostnames*
>
>
>
> Use: /smtp/
>
>
>
> Type: /host//list/†
>
>
>
> Default: /*/
>
>
> поставить в пустую строку не поможет в транспорте?
>
> Вторник, 28 июля 2015, 9:50 +03:00 от Golub Mikhail <exim…@gmn.org.ua
> <mailto:exim…@gmn.org.ua>>:
>
> Доброе утро.
>
> Как отключить запись этого «мусора» в лог?
> SSL verify error: depth=1 error=certificate not trusted cert=
> SSL verify error: certificate name mismatch:
>
> Этотпараметрнепомог:
> log_selector = -tls_certificate_verified
>
> P.S. В4.85 такнемусориловлог.
>
> —
> ГолубМихаил
>
> _______________________________________________
> Exim-users mailing list
> Exim-…@mailground.net </compose?To=Exim%2du…@mailground.net>
> http://mailground.net/mailman/listinfo/exim-users
—
Best wishes Victor Ustugov mailto:vic…@corvax.kiev.ua
public GnuPG/PGP key: http://victor.corvax.kiev.ua/corvax.asc
ICQ UIN: 371808614 JID: corvax…@jabber.corvax.kiev.ua
nic-handle: CRV-UANIC
Golub Mikhail
unread,
Jul 28, 2015, 10:39:15 PM7/28/15
to Golub Mikhail
> Of Victor Ustugov
> Sent: Tuesday, July 28, 2015 10:08 PM
> To: Golub Mikhail
> Subject: Re: [Exim-users] Exim 4.86: SSL verify error
>
> скорее всего это ошибки проверки сертификата при проведении
> встречной проверки отправителя.
Нет, такое происходит при отправке письма на внутренний Exchange, например.
На тестовом сервере сразу три ошибки:
SSL verify error: depth=0 error=unable to get local issuer certificate cert=…
SSL verify error: depth=0 error=certificate not trusted cert=…
SSL verify error: depth=0 error=unable to verify the first certificate cert=…
А так при отправке на многие хосты в Интернете.
[108.174.3.215] SSL verify error: depth=1 error=certificate not trusted cert=/C=US/O=DigiCert Inc/CN=DigiCert Secure Server CA
[93.171.218.25] SSL verify error: depth=2 error=self signed certificate in certificate chain cert=/C=IL/O=StartCom Ltd./OU=Secure Digital Certificate Signing/CN=StartCom Certification Authority
[91.208.52.158] SSL verify error: depth=1 error=unable to get local issuer certificate cert=/C=US/O=thawte, Inc./CN=thawte SSL CA — G2
…
Как указывал dawnshade, параметр tls_verify_cert_hostnames пробовал добавлять в транспорт.
Не помогает 
И так tls_verify_cert_hostnames = *
И так tls_verify_cert_hostnames =!*
Victor Ustugov
unread,
Jul 28, 2015, 10:41:56 PM7/28/15
to Golub Mikhail
Golub Mikhail wrote:
> Спасибо, но не помогло.
можно попробовать в параметры remote_smtp транспорта добавить:
tls_try_verify_hosts = :
кстати, тогда в лог не будут выводиться и сообщения о проверке
сертификатов серверов отправителей при проведении встречной проверки
отправителя (если, конечно, для встречной проверки используется
remote_smtp транспорт).
> Ошибки в лог пишутся при приеме сообщений – или из мира, или с
> внутренних серверов.
>
> Они и на 4.85 были (так как опции сборки и конфиг те же), но в лог не
> писались.
>
>
>
> Например:
>
> 2015-07-28 10:16:32 [77.88.21.89] SSL verify error: depth=1 error=unable
> to get local issuer certificate cert=/C=PL/O=Unizeto Technologies
> S.A./OU=Certum Certification Authority/CN=Certum Level IV CA
>
> 2015-07-28 10:16:32 [77.88.21.89] SSL verify error: depth=1
> error=certificate not trusted cert=/C=PL/O=Unizeto Technologies
> S.A./OU=Certum Certification Authority/CN=Certum Level IV CA
>
>
>
>
>
>
>
> *From:*Exim-users [mailto:exim-user…@mailground.net] *On Behalf
> Of *dawnshade
> *Sent:* Tuesday, July 28, 2015 10:01 AM
> *To:* Exim MTA нарусском
> *Subject:* Re: [Exim-users] Exim 4.86: SSL verify error
>
>
>
> 24
> <http://git.exim.org/exim.git/blob/exim-4_86:/doc/doc-txt/ChangeLog#l24>JH/06 Verification of the server certificate for a TLS connection is now tried
>
> 25
> <http://git.exim.org/exim.git/blob/exim-4_86:/doc/doc-txt/ChangeLog#l25> (but not required) by default. The verification status is now logged by
>
> 26
> <http://git.exim.org/exim.git/blob/exim-4_86:/doc/doc-txt/ChangeLog#l26> default, for both outbound TLS and client-certificate supplying inbound
>
> 27
> поставить в пустую строку не поможет в транспорте?
>
> Вторник, 28 июля 2015, 9:50 +03:00 от Golub Mikhail <exim…@gmn.org.ua
> <mailto:exim…@gmn.org.ua>>:
>
> Доброе утро.
>
> Как отключить запись этого «мусора» в лог?
> SSL verify error: depth=1 error=certificate not trusted cert=
> SSL verify error: certificate name mismatch:
>
> Этотпараметрнепомог:
> log_selector = -tls_certificate_verified
>
> P.S. В4.85 такнемусориловлог.
>
> —
> ГолубМихаил
>
> _______________________________________________
> Exim-users mailing list
> Exim-…@mailground.net </compose?To=Exim%2du…@mailground.net>
> http://mailground.net/mailman/listinfo/exim-users
_______________________________________________
Victor Ustugov
unread,
Jul 28, 2015, 10:52:33 PM7/28/15
to Golub Mikhail
Golub Mikhail wrote:
>> ——Original Message——
>> From: Exim-users [mailto:exim-user…@mailground.net] On Behalf
>> Of Victor Ustugov
>> Sent: Tuesday, July 28, 2015 10:08 PM
>> To: Golub Mikhail
>> Subject: Re: [Exim-users] Exim 4.86: SSL verify error
>>
>> скорее всего это ошибки проверки сертификата при проведении
>> встречной проверки отправителя.
>
> Нет, такое происходит при отправке письма на внутренний Exchange, например.
> На тестовом сервере сразу три ошибки:
> SSL verify error: depth=0 error=unable to get local issuer certificate cert=…
> SSL verify error: depth=0 error=certificate not trusted cert=…
> SSL verify error: depth=0 error=unable to verify the first certificate cert=…
>
> А так при отправке на многие хосты в Интернете.
> [108.174.3.215] SSL verify error: depth=1 error=certificate not trusted cert=/C=US/O=DigiCert Inc/CN=DigiCert Secure Server CA
> [93.171.218.25] SSL verify error: depth=2 error=self signed certificate in certificate chain cert=/C=IL/O=StartCom Ltd./OU=Secure Digital Certificate Signing/CN=StartCom Certification Authority
> [91.208.52.158] SSL verify error: depth=1 error=unable to get local issuer certificate cert=/C=US/O=thawte, Inc./CN=thawte SSL CA — G2
> …
это понятно. я отвечал на «Ошибки в лог пишутся при приеме сообщений –
или из мира, или с внутренних серверов.»
то, что эти ошибки появляются при отсылке писем — это понятно. но при
приёме они появляться не должны.
если такие сообщения об ошибках появляются при приёме письма, значит на
самом деле была предпринята попытка если не отправки письма со стороны
этого сервера, то по крайней мере была предпринята попытка проведения
встречной проверки отправителя.
> Как указывал dawnshade, параметр tls_verify_cert_hostnames пробовал добавлять в транспорт.
> Не помогает 
> И так tls_verify_cert_hostnames = *
> И так tls_verify_cert_hostnames =!*
tls_verify_cert_hostnames — это несколько другая история.
этот параметр, судя по всему, должен отвечать за проверку соответствия
имени хоста сервера значению Common Name сертификата. ну и ещё алиасы
проверяются (имена хостов из поля Subject Alternative Name из X509v3
extensions сертификата). тот же WoGign подписывает сертификаты с
немерянной кучей алиасов, даже из разных доменов. да и StartCom’овские
сертификаты вроде идут с одним алиасом всегда.
но при этом сам сертификат всё равно должен пройти проверку валидности.
_______________________________________________
Golub Mikhail
unread,
Jul 28, 2015, 11:38:28 PM7/28/15
to Golub Mikhail
> то, что эти ошибки появляются при отсылке писем — это понятно. но при
> приёме они появляться не должны.
Внутреннюю структуру своих серверов я вроде знаю 
И знаю, что на Exchange письма с внешнего Exim уходят на один IP — ошибка SSL есть.
При отправке письма с Exchange во внешний мир (через шлюз Exim) письма на Exim попадают с других адресов — ошибка SSL тоже есть.
«tls_try_verify_hosts = : » — так я вообще отключу запрос на открытие TLS-сессии.
И тогда будет все чисто, но не будет TLS 
Victor Ustugov
unread,
Jul 28, 2015, 11:59:24 PM7/28/15
to Golub Mikhail
Golub Mikhail wrote:
>> то, что эти ошибки появляются при отсылке писем — это понятно. но при
>> приёме они появляться не должны.
>
> Внутреннюю структуру своих серверов я вроде знаю 
> И знаю, что на Exchange письма с внешнего Exim уходят на один IP — ошибка SSL есть.
>
> При отправке письма с Exchange во внешний мир (через шлюз Exim) письма на Exim попадают с других адресов — ошибка SSL тоже есть.
тогда не буду настаивать.
я лишь изложил результаты тестирования сообщений об ошибках при
включенной встречной проверке отправителя, отключенной встречной
проверке отправителя, а также при включенной проверке отправителя после
очистки кеша.
> «tls_try_verify_hosts = : » — так я вообще отключу запрос на открытие TLS-сессии.
> И тогда будет все чисто, но не будет TLS 
при использовании на стороне отправителя «tls_try_verify_hosts = : » в
настройках транспорта remote_smtp я в логах на стороне получателя
наблюдал «P=esmtps» при доставке.
на стороне отправителя ошибок проверки сертификата сервера получателя в
логах не было.
на сервере получателя самоподписанный сертификат.
но опять же, настаивать не буду.
_______________________________________________
Le…@lena.kiev.ua
unread,
Jul 29, 2015, 12:08:07 AM7/29/15
to Exim MTA на русском
После апгрейда Exim до 4.86 у меня появились в mainlog при отправке на mail.ru:
2015-07-28 21:39:28 +0300 1ZK9mc-0007bA-5S [217.69.139.150] SSL verify error: depth=2 error=unable to get local issuer certificate cert=/C=US/O=GeoTrust Inc./CN=GeoTrust Global CA
У меня FreeBSD на сервере и в домашнем компе.
В сервере Exim использует openssl из портов.
В домашнем компе установлены много портов, среди них curl и ca_root_nss.
Я скопировала из домашнего компа на сервер файл /usr/local/openssl/cert.pem
(который вроде от порта ca_root_nss, хотя pkg which этого не знает)
и рестартовала Exim: kill -HUP `cat /var/run/exim.pid`
Теперь такие сообщения в логе не появляются.
Victor Ustugov
unread,
Jul 29, 2015, 12:11:09 AM7/29/15
to Exim MTA на русском
Le…@lena.kiev.ua wrote:
> После апгрейда Exim до 4.86 у меня появились в mainlog при отправке на mail.ru:
>
> 2015-07-28 21:39:28 +0300 1ZK9mc-0007bA-5S [217.69.139.150] SSL verify error: depth=2 error=unable to get local issuer certificate cert=/C=US/O=GeoTrust Inc./CN=GeoTrust Global CA
>
> У меня FreeBSD на сервере и в домашнем компе.
> В сервере Exim использует openssl из портов.
> В домашнем компе установлены много портов, среди них curl и ca_root_nss.
> Я скопировала из домашнего компа на сервер файл /usr/local/openssl/cert.pem
> (который вроде от порта ca_root_nss, хотя pkg which этого не знает)
> и рестартовала Exim: kill -HUP `cat /var/run/exim.pid`
> Теперь такие сообщения в логе не появляются.
в случае самоподписанных сертификатов всё равно сообщения об ошибках
будут появляться (на сколько я понял, Михаилу и они не нужны).
_______________________________________________
Alexander Sheiko
unread,
Jul 29, 2015, 5:19:37 AM7/29/15
to Exim MTA на русском
Hello Lena,
Wednesday, July 29, 2015, 12:07:27 AM, you wrote:
Llku> У меня FreeBSD на сервере и в домашнем компе.
Llku> В сервере Exim использует openssl из портов.
Llku> Я скопировала из домашнего компа на сервер файл /usr/local/openssl/cert.pem
Копировать сертификаты не нужно, достаточно поставить порт security/ca_root_nss
и сделать:
ln -s /usr/local/share/certs/ca-root-nss.crt /usr/local/openssl/cert.pem
Если порт при установке это не предложит и не сделает сам.
Если использовать openssl из системы (чего мне хватает, зачем ещё ставить с
портов):
grep OPENSSL /etc/make.conf
OPTIONS_SET+=OPENSSL_BASE
И поставить порт security/ca_root_nss, то в нём можно поставить галочку:
Add symlink to /etc/ssl/cert.pem
Тогда получится так:
ls -l /etc/ssl/cert.pem
lrwxr-xr-x 1 root wheel 38 16 июл 19:23 /etc/ssl/cert.pem -> /usr/local/share/certs/ca-root-nss.crt
Эти корневые сертификаты будет использовать любой, собранный с системным openssl
софт, вроде wget.
—
WBR, Alexander Sheiko
Golub Mikhail
unread,
Jul 29, 2015, 9:02:21 AM7/29/15
to Exim MTA на русском
Суммируя написанное.
Был Exim 4.85, были такие же конгифи.
Файл /usr/local/openssl/cert.pem есть.
Ошибок в логе «SSL verify error» небыло.
OpenSSL системный, не из портов.
Порт ca_root_nss установлен был уже раньше — ca_root_nss-3.19.2
Переустановил и ca_root_nss и exim.
# ls -l /usr/local/openssl/cert.pem
-rw-r—r— 1 root wheel 953741 29 июл 08:32 /usr/local/openssl/cert.pem
Ошибка осталась 
Спасибо, буду искать решение.
> Of Alexander Sheiko
> Sent: Wednesday, July 29, 2015 5:19 AM
> To: Exim MTA на русском
> Subject: Re: [Exim-users] Exim 4.86: SSL verify error
>
Golub Mikhail
unread,
Jul 29, 2015, 9:07:29 AM7/29/15
to Exim MTA на русском
> ——Original Message——
> From: Exim-users [mailto:exim-user…@mailground.net] On Behalf
> Of Victor Ustugov
> Sent: Wednesday, July 29, 2015 12:11 AM
> To: Exim MTA на русском
> Subject: Re: [Exim-users] Exim 4.86: SSL verify error
>
> Le…@lena.kiev.ua wrote:
> > После апгрейда Exim до 4.86 у меня появились в mainlog при отправке
> на mail.ru:
> >
> > 2015-07-28 21:39:28 +0300 1ZK9mc-0007bA-5S [217.69.139.150] SSL verify
> error: depth=2 error=unable to get local issuer certificate
> cert=/C=US/O=GeoTrust Inc./CN=GeoTrust Global CA
> >
> > У меня FreeBSD на сервере и в домашнем компе.
> > В сервере Exim использует openssl из портов.
> > В домашнем компе установлены много портов, среди них curl и
> ca_root_nss.
> > Я скопировала из домашнего компа на сервер файл
> /usr/local/openssl/cert.pem
> > (который вроде от порта ca_root_nss, хотя pkg which этого не знает)
> > и рестартовала Exim: kill -HUP `cat /var/run/exim.pid`
> > Теперь такие сообщения в логе не появляются.
>
> в случае самоподписанных сертификатов всё равно сообщения об
> ошибках
> будут появляться (на сколько я понял, Михаилу и они не нужны).
На внутреннем сервере всегда был самоподписный сертификат.
И в случае с Exim 4.85 ошибок небыло. Появились на 4.86.
Le…@lena.kiev.ua
unread,
Jul 29, 2015, 9:09:59 AM7/29/15
to Exim MTA на русском
> OpenSSL системный, не из портов.
Системный использует /etc/ssl/cert.pem
> Переустановил и ca_root_nss и exim.
> # ls -l /usr/local/openssl/cert.pem
> -rw-r—r— 1 root wheel 953741 29 июл 08:32 /usr/local/openssl/cert.pem
Вот на него можно сделать ссылку.
Golub Mikhail
unread,
Jul 29, 2015, 9:22:42 AM7/29/15
to Exim MTA на русском
> > OpenSSL системный, не из портов.
>
> Системный использует /etc/ssl/cert.pem
>
> > Переустановил и ca_root_nss и exim.
> > # ls -l /usr/local/openssl/cert.pem
> > -rw-r—r— 1 root wheel 953741 29 июл 08:32 /usr/local/openssl/cert.pem
>
> Вот на него можно сделать ссылку.
# ls -l /etc/ssl/cert.pem
/etc/ssl/cert.pem -> /usr/local/openssl/cert.pem
# ls -l /usr/local/openssl/cert.pem
-rw-r—r— 1 root wheel 953741 29 июл 08:32 /usr/local/openssl/cert.pem
И при отправке на сервер с самоподписным сертификатом в логе ошибка — для теста доступен только такой сервер.
Тестирую на тестовом хосте без отправки «в мир».
На этом же хосте еще позавчера был 4.85 и ошибки в лог не писал.
Собственно, сейчас эти ошибки «SSL verify error», как я вижу, тоже проблем не вызывают — письма доставляются.
Но напрягает …
Golub Mikhail
unread,
Jul 29, 2015, 10:59:15 AM7/29/15
to Exim MTA на русском
Хорошо, подскажите еще, может какой-то параметр еще добавить в конфиг?
Ведь, как я понял, не у всех ошибки есть на 4.86.
Сейчас только эти параметры прописаны касательно TLS.
tls_certificate = цепочка сертификатов startssl.com + сертификат.
tls_privatekey = ключ.
tls_advertise_hosts = *
openssl_options = +dont_insert_empty_fragments +no_sslv3
Le…@lena.kiev.ua
unread,
Jul 29, 2015, 11:04:48 AM7/29/15
to Exim MTA на русском
> Хорошо, подскажите еще, может какой-то параметр еще добавить в конфиг?
> Ведь, как я понял, не у всех ошибки есть на 4.86.
А приведите строки лога полностью. Наверно, так и должно быть.
Это только предупреждения, письма проходят.
Golub Mikhail
unread,
Jul 29, 2015, 11:13:02 AM7/29/15
to Exim MTA на русском
Вот такие строки, например.
2015-07-29 11:06:07 [89.184.69.23] SSL verify error: depth=0 error=certificate not trusted cert=/O=*.mirohost.net/OU=Domain Control Validated/CN=*.mirohost.net
2015-07-29 11:06:07 [89.184.69.23] SSL verify error: depth=0 error=unable to verify the first certificate cert=/O=*.mirohost.net/OU=Domain Control Validated/CN=*.mirohost.net
Или
2015-07-29 11:05:35 1ZKMMn-0002N6-MV [207.46.163.138] SSL verify error: depth=2 error=unable to get local issuer certificate cert=/CN=Microsoft Internet Authority
2015-07-29 11:05:35 1ZKMMn-0002N6-MV [207.46.163.138] SSL verify error: depth=2 error=certificate not trusted cert=/CN=Microsoft Internet Authority
2015-07-29 11:05:37 1ZKMMn-0002N6-MV => ****@panduit.com R=dnslookup T=remote_smtp H=panduit-com.mail.protection.outlook.com [207.46.163.138] C=»250 2.6.0 …
Да, письма проходят …
Но такой ругани в лог на старой версии небыло.
Вот и хочу понять — кто виноват?
> ——Original Message——
> From: Exim-users [mailto:exim-user…@mailground.net] On Behalf
> Of Le…@lena.kiev.ua
> Sent: Wednesday, July 29, 2015 11:04 AM
> To: Exim MTA на русском
> Subject: Re: [Exim-users] Exim 4.86: SSL verify error
>
Golub Mikhail
unread,
Jul 29, 2015, 5:33:19 PM7/29/15
to Exim MTA на русском
В общем, решил пока так.
В файле src/tls-openssl.c убрал вывод в лог того, что мешало 
367c367
< log_write(0, LOG_MAIN, «[%s] SSL verify error: depth=%d error=%s cert=%s»,
—
> /* log_write(0, LOG_MAIN, «[%s] SSL verify error: depth=%d error=%s cert=%s»,
372c372
< *calledp = TRUE;
—
> */ *calledp = TRUE;
441c441
< log_write(0, LOG_MAIN,
—
> /* log_write(0, LOG_MAIN,
444c444
< dn);
—
> */ dn);
—
Голуб Михаил
Alexander Sheiko
unread,
Jul 29, 2015, 10:05:55 PM7/29/15
to Exim MTA на русском
Hello Golub,
Wednesday, July 29, 2015, 5:29:58 PM, you wrote:
GM> В общем, решил пока так.
GM> В файле src/tls-openssl.c убрал вывод в лог того, что мешало
Проблему подтверждаю. Exim собран с системным OpenSSL на 9.3-RELEASE-p20.
При чём wget, собранный из портов таким же образом, на сертификаты того же
сервера не ругается.
Ваш патч почему-то не прошёл (4 вхождение), пришлось править руками.
—
WBR, Alexander Sheiko
-
#1
I have configured Exim to use a remote outbound mail server. As mail service, I make use of mxroute.com.
Followed this very nice tutorial:
The problem is something goes wrong when the remote smtp server is resolved to an IPv6 address.
In /etc/exim.routers.pre.conf I have this line:
Code:
route_list = * smtp.example.com::587Sending an email, I get this error:
Code:
Connecting to smtp.example.com [2a01:xxx:xxx:xxxx::2]:587 ... connected
SMTP<< 220 smtp.example.com ESMTP Exim 4.94.2 Mon, 02 Aug 2021 16:22:20 +0000
SMTP>> EHLO myserver.com
SMTP<< 250-smtp.example.com Hello myserver.com [xxxx:xxxx:xxxx:xxxx:xxxx:xxxx:xxxx:xxxx]
250-SIZE 52428800
250-8BITMIME
250-PIPELINING
250-PIPE_CONNECT
250-AUTH PLAIN LOGIN
250-STARTTLS
250 HELP
SMTP>> STARTTLS
SMTP<< 220 TLS go ahead
SMTP>> EHLO myserver.com
SMTP<< 250-smtp.example.com Hello myserver.com [xxxx:xxxx:xxxx:xxxx:xxxx:xxxx:xxxx:xxxx]
250-SIZE 52428800
250-8BITMIME
250-PIPELINING
250-PIPE_CONNECT
250-AUTH PLAIN LOGIN
250 HELP
LOG: host_lookup_failed MAIN
no IP address found for host 2a01
SMTP>> MAIL FROM:<> SIZE=2946
SMTP>> RCPT TO:<[email protected]>
SMTP>> DATA
SMTP<< 250 OK
SMTP<< 550 relay not permitted, authentication required
SMTP<< 503-All RCPT commands were rejected with this error:
503-relay not permitted, authentication required
503 Valid RCPT command must precede DATA
SMTP>> QUIT
The weird part is «no IP address found for host 2a01» and after that it fails authentication.
It seems the first octet of the IPv6 address is being used instead of the complete IPv6 address?
If I replace the FQDN in /etc/exim.routers.pre.conf with an IPv4 address like this:
Code:
route_list = * 100.100.100.100::587… then it works fine!
So any idea’s how to make the route_list accept FQDN’s that resolve to a proper IPv6 address?
-
#2
Square brackets because of the colons in ipv6. ?
- When IPv6 addresses are involved, it gets worse, because they contain colons of their own. To make this case easier, it is permitted to enclose an IP address (either v4 or v6) in square brackets if a port number follows. For example:
route_list = * «</ [10.1.1.1]:1225 / [::1]:1226»
20. The manualroute router
Exim is a message transfer agent (MTA) developed at the University of Cambridge for use on Unix systems connected to the Internet.
www.exim.org
@DA moderators please add this in the DOCS?
Last edited: Aug 3, 2021
-
#3
I tried the square brackets, but it does not seem to work when using FQDN:
With one colon:
Code:
route_list = * [smtp.example.com]:587Error: no IP address found for host [smtp.example.com]
With double colons:
Code:
route_list = * [smtp.example.com]::587Error: no IP address found for host 2a01
-
#4
I tried the square brackets, but it does not seem to work when using FQDN:
With one colon:
Code:
route_list = * [smtp.example.com]:587Error: no IP address found for host [smtp.example.com]
With double colons:
Code:
route_list = * [smtp.example.com]::587Error: no IP address found for host 2a01
In above example exim.org the square brackets for IPv6 adress itself.
the smtp… is no fqdn the hostname itself should be FQDN but there i can be very wrong????
Do first some dns / ns test online for those hostname / servers you need there
and did you connect the ipv6 in admin with the ipv4 pointing or so i don’t know exactly now.
Last edited: Aug 3, 2021
-
#5
Using the literal IPv6 address in square brackets works, just like the IPv4 address.
However, this gives a minor error:
Code:
SSL verify error: certificate name mismatch:
That’s why I wanted to use the FQDN, which works if it would only resolve to IPv4. But Exim seems to have problems with IPv6.
No big deal though.. but weird that I couldn’t find any other reports about this problem.
-
#6
Using the literal IPv6 address in square brackets works, just like the IPv4 address.
However, this gives a minor error:Code:
SSL verify error: certificate name mismatch:That’s why I wanted to use the FQDN, which works if it would only resolve to IPv4. But Exim seems to have problems with IPv6.
No big deal though.. but weird that I couldn’t find any other reports about this problem.
Yup problems with yes<> no FQDN and mismatch x509 .. don’t know or same cause here topic from 15 July
-
#7
I have a workaround, in case someone else experience the same problem with IPv6 external SMTP host and Exim.
In exim.routers.pre.conf replace:
Code:
ignore_target_hosts = 127.0.0.0/8with:
Code:
ignore_target_hosts = <; 0000::0000/0 ; 127.0.0.0/8This will force the domainname to be resolved as IPv4 address.
Exim is a versatile mail transfer agent. This article builds upon Mail server. While the Exim wiki provides some helpful how-tos on certain specific use cases, a detailed description of all configuration options is available as well.
Installation
Install the exim package.
Basic configuration
The factual accuracy of this article or section is disputed.
Reason: Is the attribution of maildir format correct for the example configuration? (Discuss in Talk:Exim#Maildir format)
Exim comes with a bulky default configuration file which is located in /etc/mail/exim.conf. Many options in there are not necessary in a regular use case. By default configuration is done in a single file containing several chapters. Below is a very basic configuration, which provides: local delivers to system users (Maildir format) and authorized relaying to MX hosts. The description is based on a domain «mydomain.tld» served on a host «hostname.mydomain.tld». It is highly recommended to consult the official documentation before using the given documentation below.
Warning: The default permissions of the default configuration file is 0644. Which allows reading by any user. Change this as appropriate, perhaps to 0640, if you are keeping sensitive information (LDAP credentials et. al.) in there.
Main parameters
Main parameters contain some basic options. Using solely those options would open ports for connections but still no mail would be accepted nor relayed anywhere.
# be the responsible mail host for hostname.mydomain.tld (@) & mydomain.tld domainlist local_domains = @ : mydomain.tld # we don't relay. Not for foreign domains nor for a single host domainlist relay_to_domains = hostlist relay_from_hosts = # serve the on all used ports daemon_smtp_ports = 25 : 465 : 587 # do a reverse name lookup for all incoming connections host_lookup = * # Logging: log all events, add syslog to logging path & avoid double entries log_selector = +all log_file_path = : syslog syslog_duplication = false # undeliverables: discard bounce messages after 2d and all others after 7 d ignore_bounce_errors_after = 2d timeout_frozen_after = 7d
TLS, security & authentication
This article or section needs expansion.
Reason: Are there factual concerns with giving a low privilege user access to a private key? Why should the Exim private key get lost? (Discuss in Talk:Exim)
Warning: If you deploy TLS, be sure to follow Server-side TLS to prevent vulnerabilities.
To obtain a certificate, see OpenSSL#Usage.
The first part of the following options are still part of the first configuration section in Exim. Starting with «begin authenticators» the first special section in Exim configuration begins. There will be more such sections later.
Below some very basic security related options are defined, TLS is set up & a plain text authenticator using a user password lookup is introduced.
Warning: This example of an authenticator should not be used in production environment!
# actually not required: it's hard coded - anyway: no mail delivery to root
never_users = root
# don't show the exim version to everyone. Actually not even show the name.
smtp_banner = $smtp_active_hostname ESMTP $tod_full
# STARTTLS is offered to everyone
tls_advertise_hosts = *
tls_certificate = /path/to/exim/only/fullchain.pem
tls_privatekey = /path/to/exim/only/privkey.pem
# use all ciphers on port 25, use only good ciphers on port 587
tls_require_ciphers = ${if =={$received_port}{25}
{DEFAULT} {HIGH:!MD5:!SHA1:!SHA2}}
# traffic on port 465 always uses TLS
tls_on_connect_ports = 465
# special sections always start with a "begin"
begin authenticators
PLAIN:
# authentication protocol is plain text
driver = plaintext
# authentication is offered as plain text
public_name = PLAIN
server_prompts = :
# authentication is successful, if the password provided ($auth3)
# equals the password found in a lookup file for user ($auth2)
server_condition = ${if eq{$auth3}{${lookup{$auth2}dbm{/etc/authpwd}}}}
server_set_id = $auth2
# only offer plain text authentication after TLS is been negotiated
server_advertise_condition = ${if def:tls_in_cipher}
Note: Exim loads certificate files during mail processing with the low privilege user exim. While it is good to run an internet facing process with such a user, it is somewhat strange to give access to a private key to such user. If your server serves multiple purposes (e.g. HTTP, IMAP, SMTP) with multiple DNS aliases (CNAME or several names pointing to a single IP) it may be wise to request multiple certificates. If the Exim private key gets lost, damage is limited to SMTP.
Routing, transport & retry
For each recipient of a message routing is performed as follows: routers are tested in their order given in the routing section. For each router, conditions may apply (e.g. domains = ! +local_domains). Only if all conditions apply, the message will be handed over to the defined transport (e.g. transport = smtp). If transport fails or not all conditions of a router are fulfilled, the next router is tested.
begin routers # that's the relay router dnslookup: # the router type driver = dnslookup # the domains served on this router: not the local domain domains = ! +local_domains # the transport to be used (see transport section below) transport = remote_delivery # localhost is to be ignored if dns gives such result ignore_target_hosts = <; 0.0.0.0 ; 127.0.0.0/8 ; ::1 # a router list is processed until matched and successful transported. # if transport fails, we don't want the next router to be used no_more # local delivery localuser: # the transport type - we accept the mail locally driver = accept # this router serves only our domains domains = +local_domains # use transport named local_delivery transport = local_delivery # in case local delivery fails cannot_route_message = Unknown local user begin transports remote_delivery: driver = smtp local_delivery: #deliver to a local mailbox driver = appendfile file = /var/mail/$local_part # if routing or transport fails, try again after this (default) ruleset begin retry # Address or Domain Error Retries # ----------------- ----- ------- * * F,2h,15m; G,16h,1h,1.5; F,4d,6h
Use manualroute
If you want to use manualroute instead, comment out the dnslookup block and add the smarthost block.
#dnslookup:
# the router type
# driver = dnslookup
# the domains served on this router: not the local domain
# domains = ! +local_domains
# the transport to be used (see transport section below)
# transport = remote_delivery
# localhost is to be ignored if dns gives such result
# ignore_target_hosts = <; 0.0.0.0 ; 127.0.0.0/8 ; ::1
# a router list is processed until matched and successful transported.
# if transport fails, we don't want the next router to be used
# no_more
smarthost:
driver = manualroute
domains = !+local_domains
transport = remote_delivery
route_list = * smtp.myisp.com # change to the desired smtp server
ignore_target_hosts = <; 0.0.0.0 ; 127.0.0.0/8 ; ::1
ACL: Access Control Lists
Access Control Lists are at the heart of Exim. They are required for basic checks and may be used for sophisticated message processing. In general the overall message processing in Exim is:
connection > (authentication >) ACL > routing > transport
With this it is important to note that messages coming from authenticated clients are treated (by default) by the same ACL as messages coming from other mail servers.
Exim know a full set of different ACL. Good knowledge of the SMTP protocol is required to choose the correct set of ACL.
acl_smtp_connect > acl_smtp_helo > ... > acl_smtp_rcpt > ... > acl_smtp_data > ...
For a basic setup two ACL are mandatory: acl_smtp_rcpt and acl_smtp_data. These are default to deny while all other default to accept.
The example below just prevents being an open relay. This setup has multiple security flaws (e.g. all authenticated users may use any mail address). If added to an existing configuration, it must be added before any other special section (i.e. before any existing «begin»).
Warning: Do not use the following example in a production example! It lacks several required checks!
# use this ACL after SMTP RCPT TO: is received acl_smtp_rcpt = basic_acl_rcpt # use this ACL after SMTP DATA is finished, i.e. all data has been received acl_smtp_data = basic_acl_data begin acl basic_acl_rcpt: # accept all messages for which I am the receiving mail host accept domains = +local_domains # accept all messages from authenticated clients accept authenticated = * # deny all other messages (i.e. messages to be relayed from unauthorized # clients) deny message = "we are not an open relay" basic_acl_data: # we have done all checks after RCPT already accept
Hide machine name
If you have a laptop, or a machine in a smarthost configuration, where you do not want the name of the machine to appear in the outgoing email then you must enable exim’s rewriting facilities.
In the Rewriting section you should have something like:
*@machine.mydomain $1@mydomain
where machine is the hostname of your laptop or PC and mydomain is the domain name of the machine and the outgoing mail. To rewrite only sender domain, add special flag (F) in the line end. See upstream document for detail
Startup
Start/enable the exim.service.
Dovecot LMTP delivery & SASL authentication
This article or section needs expansion.
Reason: What is LMTP? (Discuss in Talk:Exim)
In this section the integration of Dovecot is described. It is assumed that Dovecot & Exim are already setup and configured. Dovecot will serve as SASL authenticator and local transport mechanism. For this purpose the Dovecot services will be setup as follows.
/etc/dovecot/conf.d/10-master.conf
service auth {
unix_listener exim-auth {
mode = 0600
user = exim
group = exim
}
# Auth process is run as this user.
user = $default_internal_user
}
service lmtp {
# a unix socket is preferred of a local port communication
unix_listener exim-lmtp {
mode = 0600
group = exim
user = exim
}
}
To use the Dovecot SASL in a TLS protected environment, add the following authenticator to Exim.
/etc/mail/exim.conf - authenticators section
PLAIN:
driver = dovecot
public_name = PLAIN
server_socket = /var/run/dovecot/exim-auth
server_set_id = $auth1
server_advertise_condition = ${if def:tls_in_cipher}
The existing router for local delivery can be reused. You may want to consider add a dsn_lasthop to the router definition. If DSN is used, Exim will assume final delivery of the message at this point. In the transport section the transport for local delivery must be replaced by the following transport definition.
/etc/mail/exim.conf - transports section
local_delivery: driver = lmtp socket = /var/run/dovecot/exim-lmtp batch_max = 200
Note: As of Exim 4.88 there is a limitation with the lmtp driver: in an ACL, verify = recipient/callout=no_cache will not work as expected, i.e. non-existent user accounts will not throw a failure. To accomplish a receipient check against Dovecot you must replace the driver above by a
driver = smtp protocol = lmtp port = 2525
The host is specified in the router, not the transport. Thus, the router must look like:
lmtp_router: driver = manualroute domains = +local_domains transport = local_delivery route_list = * 127.0.0.1 byname
Furthermore your Dovecot lmtp service must be adjusted accordingly. For example: here is a Git commit that fixes this exact issue.
Since Dovecot is configured to provide a unix socket for the exim user, you may harden your security by adding the following line to the main configuration section.
/etc/mail/exim.conf - main section
# don't deliver being root, drop privileges to exim user deliver_drop_privilege = true
Using Gmail as smarthost
In the beginning of the exim conf file, you must enable TLS using
tls_advertise_hosts = +local_network : *.gmail.com
or to advertise tls to all hosts
tls_advertise_hosts = *
More information about TLS can be found in the exim documentation.
Note: The following must be put in the appropriate sections of the configuration file, eg, after begin authenticators.
Add a router before or instead of the dnslookup router:
gmail_route: driver = manualroute transport = gmail_relay route_list = * smtp.gmail.com
Add a transport:
gmail_relay: driver = smtp port = 587 tls_verify_certificates = /etc/ssl/certs/ca-certificates.crt # this forces host verification. tls_verify_hosts = smtp.gmail.com hosts_require_auth = <; $host_address hosts_require_tls = <; $host_address
Because of host verification, your exim log might contain
SSL verify error: certificate name mismatch: "/C=US/ST=California/L=Mountain View/O=Google Inc/CN=smtp.gmail.com"
But this has no effect on mail-delivery and can be ignored.
Add an authenticator (replacing myaccount@gmail.com and mypassword with your own account details):
gmail_login: driver = plaintext public_name = LOGIN hide client_send = : myaccount@gmail.com : mypassword
$host_address is used for hosts_require_auth and hosts_require_tls instead of smtp.gmail.com to avoid occasional 530 5.5.1 Authentication Required errors. These are caused by the changing IP addresses in DNS queries for smtp.gmail.com. $host_address will expand to the particular IP address that was resolved by the gmail_route router.
For added security, use a per-application password. This works with Google Apps accounts as well.
Hardening
Rate limits
Security breaches happen. In case you do not have any service that submits local mail (receiving mail from localhost on a port is not considered local submission), completely disable local submission. Do so by adding acl_not_smtp = acl_local to the main section and add the following simple ACL to the acl section.
/etc/mail/exim.conf - acl section
acl_local: deny log_message = AL01: Local submission denied.
If local submission is required, consider imposing a rate limit to it. Do so by adding acl_not_smtp = acl_local to the main section and adding the following ACL to the acl section. It imposes 2 rate limits: 20 mails in a single minute and 30 mails in 10 minutes. With this a burst of local submitted alerts are possible while
/etc/mail/exim.conf - acl section
acl_local: # apply a limit of 30 mails to the administrator for alerts submitted # by local services deny ratelimit = 30 / 1m / strict recipients = admin@mydomain.tld : root@hostname.mydomain.tld log_message = AL01: Sender rate limit for local submission exceeded: $sender_rate / $sender_rate_period. # apply a burst limit of 3 mails per minute to everyone else deny ratelimit = 3 / 1m / strict !recipients = admin@mydomain.tld : root@hostname.mydomain.tld log_message = AL02: Sender rate limit for local submission exceeded: $sender_rate / $sender_rate_period. # apply a regular limit of 10 mails per 30 minutes to everyone else deny ratelimit = 10 / 30m / strict !recipients = admin@mydomain.tld : root@hostname.mydomain.tld log_message = AL03: Sender rate limit for local submission exceeded: $sender_rate / $sender_rate_period. accept
Troubleshooting
451 Temporary local problem
If you are getting a «451 Temporary Local Problem» when testing SMTP, you are probably sending as root. By default Exim will not allow you to send as root.
See also
- Official website
Common Name Mismatch Error — достаточно популярная ошибка, возникающая в том случае, когда значение Common Name или SAN вашего SSL/TLS-сертификата не соответствует домену. Ошибка может по-разному выводиться в зависимости от используемого браузера.
К примеру, в Internet Explorer сообщение об ошибке выглядит следующим образом: «There is a problem with this website’s security certificate. The security certificate presented by this website was issues for a different website’s address».
В Chrome сообщение об ошибке имеет вид: «Your connection is not private. Attackers might be trying to steal your information from URL (for example, passwords, messages, or credit cards) NET:ERR_CERT_COMMON_NAME_INVALID.
Если вы столкнулись с подобной ошибкой, не игнорируйте ее и не переходите на такой сайт. Возможно, что вы в конечном счете окажетесь на мошенническом сайте. Для владельцев сайтов рекомендации по устранению ошибки приведены далее.
Как решить проблему с Common Name Mismatch
Возможные причины появления ошибки:
1. Адрес сайта не был включен в common name сертификата
Эта причина является одной из самых распространенных. К примеру, вы приобрели SSL-сертификат, который распространяется на www.example.com, однако URL без www не был включен как SAN.
Чаще всего при покупке SSL-сертификата для доменного имени www.example.com удостоверяющие центры бесплатно включают и домен без www (после его успешной проверки). Добавить необходимый домен можно и после выпуска сертификата (для мультидоменных сертификатов). Для этого потребуется перевыпустить сертификат с новым составом SAN имен.
2. Сертификат не установлен или некорректно установлен на сервер.
Убедитесь в том, что сертификат установлен на сервер, и это было выполнено корректно. Сделать это можно с помощью нашего SSL-чекера.
3. Веб-сайт не использует SSL, но находится на том же самом IP-адресе, что и другой сайт с SSL-сертификатом.
Некоторые хостинги требуют поддержки выделенного IP-адреса для установки SSL. Если какой-либо клиент установит SSL-сертификат на общий IP-адрес, это может помешать работе других сайтов.
Также бывают случаи, когда клиентское соединение или хостинговые серверы не поддерживают SNI (Server Name Indication). Однако практически все современные хостинги поддерживают SNI.
Решить проблему в таком случае можно путем получения выделенного IP-адреса (и смены настроек DNS).
4. Вы пытаетесь получить доступ к IP-адресу.
Ошибка может произойти в том случае, если кто-либо пытается установить HTTPS-соединение для IP-адреса. HTTPS-запрос к IP-адресу не содержит имя сервера, что и выливается в подобную ошибку.
Чтобы решить проблему, просто перейдите на страницу, указав имя хоста, а не IP-адрес.
5. Параметры хостинга переопределяют настройки сертификата
Ваш хостинг-провайдер может иметь настройки, которые привязывают SSL к каждому из доменов. Если вы приобретете SSL/TLS-сертификат у стороннего провайдера и установите его, вы увидите ошибку Common Name Mismatch.
Перейдите в чекер SSL-сертификатов и посмотрите полные данные по сертификату. Если common name или SAN включают в себя имя вашего хостинг-провайдера, то в таком случае, вероятно, проблема как раз в этом.
Вам нужно будет связаться с хостинг-провайдером и попросить его удалить SSL-сертификат. Если он этого не сделает, то в таком случае вам понадобится найти другого провайдера. Вас не должны ограничивать в возможности установки SSL-сертификатов.
6. Доменное имя связано со старым IP-адресом, на котором стоит другой сертификат
Если доменное имя связано со старым IP-адресом, который еще не был изменен, и на нем стоит другой сертификат, то в таком случае можно столкнуться с ошибкой Common Name Mismatch Error. Решить эту проблему можно путем смены DNS.
7. DNS-записи были недавно изменены.
Ошибка может возникнуть, если IP-адрес, к которому привязан домен, недавно менялся. Если вы приобрели выделенный IP-адрес, и SSL-сертификат был установлен сразу после этого, домен по-прежнему может быть связан с прошлым IP-адресом.
Чтобы решить проблему, просто подождите некоторое время. Как только DNS-записи будут обновлены, ошибка исчезнет.
Заключение
Резюмируя вышесказанное, можно сделать вывод, что ошибка Common Name Mismatch Error происходит в результате неверных настроек сервера и указания неверных данных при покупке сертификата. Если проблема состоит в добавлении SAN, вы можете связаться с нами, и мы поможем вам оформить все грамотно.
Если же проблема связана с конфигурацией сервера, то в таком случае вам необходимо обратиться к своему хостингу или IT-специалистам.
Модератор: xM
Правила форума
Убедительная просьба юзать теги [code] при оформлении листингов.
Сообщения не оформленные должным образом имеют все шансы быть незамеченными.
-
ssh2
- рядовой
- Сообщения: 20
- Зарегистрирован: 2010-09-14 8:42:05
exim4 и ssl от публичного CA
Коллеги приветствую.
Потребовалось заменить самописный сертификат на «настоящий». После рестарта exim с новыми ключами, mta перестаёт принимать почту от google, сообщая в лог:
Код: Выделить всё
2014-12-22 02:42:55 TLS error on connection from mail-la0-f52.google.com [209.85.215.52] (cert/key setup: cert=/etc/exim4/exim.crt key=/etc/exim4/exim.key): The provided X.509 certificate list is
not sorted (in subject to issuer order) Авторизация клиентов при установлении SMTP судя по всему тоже перестаёт работать.
Сертификат получен банальным объединением в один файл General CA, intermediate и domain. Файл с ключом само собой верный. Этот же комплект прекрасно работает в dovecot и получает на http://www.ssllabs.com А+.
Поиск на форму не помог.
-
Хостинг HostFood.ru
Услуги хостинговой компании Host-Food.ru
Хостинг HostFood.ru
Тарифы на хостинг в России, от 12 рублей: https://www.host-food.ru/tariffs/hosting/
Тарифы на виртуальные сервера (VPS/VDS/KVM) в РФ, от 189 руб.: https://www.host-food.ru/tariffs/virtualny-server-vps/
Выделенные сервера, Россия, Москва, от 2000 рублей (HP Proliant G5, Intel Xeon E5430 (2.66GHz, Quad-Core, 12Mb), 8Gb RAM, 2x300Gb SAS HDD, P400i, 512Mb, BBU):
https://www.host-food.ru/tariffs/vydelennyi-server-ds/
Недорогие домены в популярных зонах: https://www.host-food.ru/domains/
-
xM
- ст. лейтенант
- Сообщения: 1316
- Зарегистрирован: 2009-01-15 23:57:41
- Откуда: Königsberg
- Контактная информация:
Re: exim4 и ssl от публичного CA
Непрочитанное сообщение
xM » 2014-12-22 15:31:48
Проверьте порядок следования в объединённом файле
-
ssh2
- рядовой
- Сообщения: 20
- Зарегистрирован: 2010-09-14 8:42:05
Re: exim4 и ssl от публичного CA
Непрочитанное сообщение
ssh2 » 2014-12-22 15:50:05
xM писал(а):Проверьте порядок следования в объединённом файле
Хм, с порядком всё в порядке как мне кажется. У других приложений нет проблем с использованием этого сертификата, кроме того
Код: Выделить всё
root@mail:/etc/exim4/ssl# openssl verify star_domain-full.crt
star_domain-full.crt: OKПрава и владельца я проверил в первую очередь.
-
xM
- ст. лейтенант
- Сообщения: 1316
- Зарегистрирован: 2009-01-15 23:57:41
- Откуда: Königsberg
- Контактная информация:
Re: exim4 и ssl от публичного CA
Непрочитанное сообщение
xM » 2014-12-22 19:39:28
-
xM
- ст. лейтенант
- Сообщения: 1316
- Зарегистрирован: 2009-01-15 23:57:41
- Откуда: Königsberg
- Контактная информация:
Re: exim4 и ssl от публичного CA
Непрочитанное сообщение
xM » 2014-12-22 19:44:01
Правильный порядок должен быть примерно такой
Код: Выделить всё
Certificate chain
0 s:/OU=Domain Control Validated/OU=PositiveSSL/CN=my.host
i:/C=GB/ST=Greater Manchester/L=Salford/O=COMODO CA Limited/CN=PositiveSSL CA 2
1 s:/C=GB/ST=Greater Manchester/L=Salford/O=COMODO CA Limited/CN=PositiveSSL CA 2
i:/C=SE/O=AddTrust AB/OU=AddTrust External TTP Network/CN=AddTrust External CA Root
2 s:/C=SE/O=AddTrust AB/OU=AddTrust External TTP Network/CN=AddTrust External CA Root
i:/C=SE/O=AddTrust AB/OU=AddTrust External TTP Network/CN=AddTrust External CA Root
Ну и немного для понимания
RFC-5246 ‘The Transport Layer Security (TLS) Protocol Version 1.2’
…
certificate_list
This is a sequence (chain) of certificates. The sender’s certificate MUST come first in the list. Each following certificate MUST directly certify the one preceding it. Because certificate validation requires that root keys be distributed independently, the self-signed certificate that specifies the root certificate authority MAY be omitted from the chain, under the assumption that the remote end must already possess it in order to validate it in any case.
…
Common Name Mismatch Error is a widespread error that occurs when the Common Name or SAN value of your SSL / TLS certificate does not correspond to the domain name. The error message may have different content depending on the browser used.
For example, Internet Explorer will display following error message: «There is a problem with this website’s security certificate. The security certificate presented by this website was issued for a different website’s address.
In Chrome, the error message looks like: «Your connection is not private. Attackers might be trying to steal your information from the URL (for example, passwords, messages, or credit cards) NET: ERR_CERT_COMMON_NAME_INVALID.
If you encounter any of the above mentioned or similar error messages, you should not disregard them and proceed further to such a web site. It is most likely that you will eventually end up on a fraudulent site. Recommendations for fixing an error for site owners are given below.
How to fix Common Name Mismatch problem
Possible causes of error:
1. The site address was not included in the common name of the certificate.
This reason is one of the most commonly occurred. For example, if you purchase an SSL certificate that extends to www.example.com, however URL without www was not included as a SAN.
Most often, when an SSL certificate is purchased for a domain name such as www.example.com, certifying authorities also include a domain without leading www prefix (after successfully validating it). Required domain name can be added after the issuance of the certificate (for multi-domain certificates). In order to accomplish that, you will need to reissue the certificate with the new SAN names.
2. The certificate is not installed or is incorrectly installed on the server.
Make sure that the certificate was properly installed on the server. This can be verified via our SSL-checker.
3. The website does not have SSL certificate installed, however it has the same IP address as another site with a properly installed SSL certificate.
Some hosting services may require static IP address for SSL installation. If an SSL certificate will be installed on a web site with a dynamic IP address, it may interfere with operations of other web sites.
In addition, there are certain cases when the client connection or hosting servers do not support SNI (Server Name Indication). However, almost every modern hosting provider supports SNI.
Above issue can be resolved by obtaining static IP address (and alter the DNS settings).
4. You are trying to access the IP address.
An error can occur if someone tries to establish an HTTPS connection for an IP address. The HTTPS request to the IP address does not contain the server name, which results in a similar error.
To solve the problem, simply go to the page and specify the host name, not the IP address.
5. Hosting parameters override certificate settings.
Your hosting provider may apply settings that bind SSL to each of the domains. If you purchase an SSL / TLS certificate from a third-party provider and install it, you will see a Common Name Mismatch error.
Go to the SSL certificate checker and overview an entire information about the certificate. In case if you find that a common name or SAN includes the name of your hosting provider, most likely that it is the root causing the issue.
You will need to contact the hosting provider and ask them to remove the SSL certificate. If he does not, then in this case you will need to find another provider. Your web hosting provider should not restrict your ability of installing an SSL certificate.
6. The domain name is associated with an old IP address used with another installed certificate.
If the domain name is associated with an old IP address that has not been changed and a different certificate is referring to the same IP address, then you may encounter a Common Name Mismatch Error. You can solve this problem by changing DNS record.
7. DNS records were recently changed.
An error may occur if the IP address with associated web domain has been recently changed. If you purchased a static IP address and installed an SSL certificate, the domain may still be linked to the previously used IP address.
Correct solution to the issue, would be to wait until DNS records will be updated. The error will disappear afterwards.
Summary
To summarize the above, we may conclude that the Common Name Mismatch Error occurs because of incorrect server settings or providing incorrect information when buying an SSL certificate. Should you require adding a SAN, you are welcome to contact us, and we will provide you our technical expertise on how to arrange this.
In case if problem is associated with the server configuration, you will need to seek for advice from your web hosting or IT-specialists.