-
#1
Добрый день, имеется новый m2 400 который требуется подключить как станцию к существующей сети, но в в списке сетей не на всех есть radio button именно на тех которые нужны его нет есть даже на старом домашнем tplink’e в чем может быть проблема?
-
#2
Добрый день, имеется новый m2 400 который требуется подключить как станцию к существующей сети, но в в списке сетей не на всех есть radio button именно на тех которые нужны его нет
есть даже на старом домашнем tplink’e в чем может быть проблема?
Не совсем понятен вопрос.
-
Автор темы
-
#3
Не совсем понятен вопрос.
Немогу подключится к своей сети ее видит но выбрать не даёт
-
Автор темы
-
#4
Нужные мне сети без «кнопочки»
-
#5
Немогу подключится к своей сети ее видит но выбрать не даёт
Покажите все настройки вашей «Тарелки».
И если метраж превышает от роутера (прим. 300м.) то вы не подключитесь, т.к. передатчики у роутера слабые, не как у «тарелки».
Если вы хотите подключить тарелку к такой же тарелке, — то выкладывайте все настройки и АП и СТ
-
Автор темы
-
#6
сигнал моей сети -50 выбирать даёт даже сети с -92
-
Автор темы
-
#7
Пытался подключится с компьютера по wifi к тарелки в логе остается STA does not want to use the Mechanism (37) и не подключает
-
Автор темы
-
#9
Я уже пробовал на трёх прошивках с офф сайта, результат тот же
-
#10
Я уже пробовал на трёх прошивках с офф сайта, результат тот же
Вопрос решен!!!
Начиная с версий прошивок 5.6.х — поддержка безопасностей «WEP/WPA-TKIP/WPA2-TKIP» — удалена.
Откатывайтесь на например: 5.5.11 или меняйте на точке, к которой хотите подключиться безопасность на: WPA2-AES
Последнее редактирование: 23 Май 2017
-
#11
Ну вот, помогаешь-помогаешь, а лайков 0
-
Автор темы
-
#12
Firmware Version: XW.v5.5.10-u2 -> результат тот же
Прошу помощи, потому что сам уже сломал голову, что за ерунда.
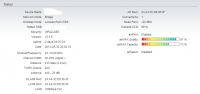
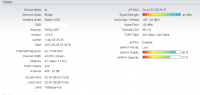
Расстояние между точками 1км, абсолютно прямая видимость.
Схема сети следующая: провайдер -> AP NanoBridge M5-400 (x.x.47.3) -> Station NanoBridge M5-300 (x.x.47.4) — > Mikrotik RB 2011
Линк работал исправно 1,5 года, и неделю назад началось…Все вроде работает , но иногда начинают подскакивать пинги, пакеты могут теряться. Причем по времени это хаотично, заметил, что ночью практически не бывает. От нагрузки конечно пинги повышаются, но допустим пропускаю я по мосту 50Мбит/с дуплекса, пинг повышается до 30-40мс, но ничего не теряется. А в ситуации, которую я наблюдаю нагрузка может быть 1Мбит/с — и пакеты потерялись.
Частоты менял, полосу менял с 40 на 20Мгц, мощность понижал — все равно наблюдается проблема.
Пошел на отчаяный шаг, заменил обе головки бриджей на новые(без переноса самих бриджей) — все равно проблема наблюдается.
Думаю может где то коннектор окислился. Такое возможно?
Скрины с AP, station, пинги с микротика прилагаю.
Логи staion
May 28 17:55:17 system: Start
May 28 17:55:18 FileSystem: Start check…
May 28 17:55:35 FileSystem: End check.
May 29 06:23:03 system: Stop
May 29 06:23:17 system: Start
May 29 06:23:17 syslogd started: BusyBox v1.11.2
May 29 06:23:17 dropbear[2835]: Not backgrounding
May 29 06:23:18 wireless: ath0 Set Mode:Managed
May 29 06:25:41 wpa-supplicant: Trying to associate with 24:a4:3c:d8:36:4f (SSID=’ed_bridge_odo’ freq=5120 MHz)
May 29 06:25:41 wireless: ath0 Set Mode:Managed
May 29 06:25:41 wireless: ath0 Set Frequency:5.12 GHz (Channel 24)
May 29 06:25:41 wireless: ath0 New Access Point/Cell address:24:A4:3C:D8:36:4F
May 29 06:25:41 wpa-supplicant: Associated with 24:a4:3c:d8:36:4f
May 29 06:25:41 wpa-supplicant: WPA: Key negotiation completed with 24:a4:3c:d8:36:4f [PTK=CCMP GTK=CCMP]
May 29 06:25:41 wpa-supplicant: CTRL-EVENT-CONNECTED — Connection to 24:a4:3c:d8:36:4f completed (auth) [id=0 id_str=]
May 29 07:05:53 wpa-supplicant: WPA: Group rekeying completed with 24:a4:3c:d8:36:4f [GTK=CCMP]
May 29 08:05:53 wpa-supplicant: WPA: Group rekeying completed with 24:a4:3c:d8:36:4f [GTK=CCMP]
May 29 09:05:53 wpa-supplicant: WPA: Group rekeying completed with 24:a4:3c:d8:36:4f [GTK=CCMP]
May 29 10:05:53 wpa-supplicant: WPA: Group rekeying completed with 24:a4:3c:d8:36:4f [GTK=CCMP]
May 29 11:05:53 wpa-supplicant: WPA: Group rekeying completed with 24:a4:3c:d8:36:4f [GTK=CCMP]
May 29 12:05:53 wpa-supplicant: WPA: Group rekeying completed with 24:a4:3c:d8:36:4f [GTK=CCMP]
May 29 13:05:53 wpa-supplicant: WPA: Group rekeying completed with 24:a4:3c:d8:36:4f [GTK=CCMP]
May 29 14:05:53 wpa-supplicant: WPA: Group rekeying completed with 24:a4:3c:d8:36:4f [GTK=CCMP]
May 29 15:05:53 wpa-supplicant: WPA: Group rekeying completed with 24:a4:3c:d8:36:4f [GTK=CCMP]
May 29 16:05:53 wpa-supplicant: WPA: Group rekeying completed with 24:a4:3c:d8:36:4f [GTK=CCMP]
May 29 17:05:53 wpa-supplicant: WPA: Group rekeying completed with 24:a4:3c:d8:36:4f [GTK=CCMP]
May 29 18:05:53 wpa-supplicant: WPA: Group rekeying completed with 24:a4:3c:d8:36:4f [GTK=CCMP]
May 29 19:05:53 wpa-supplicant: WPA: Group rekeying completed with 24:a4:3c:d8:36:4f [GTK=CCMP]
May 29 20:05:53 wpa-supplicant: WPA: Group rekeying completed with 24:a4:3c:d8:36:4f [GTK=CCMP]
May 29 20:12:09 wpa-supplicant: CTRL-EVENT-DISCONNECTED — Disconnect event — remove keys
May 29 20:12:09 wireless: ath0 Received deauth from 24:a4:3c:d8:36:4f. Reason: Unspecified (1).
May 29 20:12:09 wireless: ath0 New Access Point/Cell address:Not-Associated
May 29 20:13:00 wireless: ath0 Scan request completed
May 29 20:13:56 wireless: ath0 Scan request completed
May 29 20:13:56 wpa-supplicant: Trying to associate with 24:a4:3c:d8:36:4f (SSID=’ed_bridge_odo’ freq=5120 MHz)
May 29 20:13:56 wireless: ath0 Set Mode:Managed
May 29 20:13:56 wireless: ath0 Set Frequency:5.12 GHz (Channel 24)
May 29 20:13:56 wireless: ath0 New Access Point/Cell address:24:A4:3C:D8:36:4F
May 29 20:13:56 wpa-supplicant: Associated with 24:a4:3c:d8:36:4f
May 29 20:13:56 wpa-supplicant: WPA: Key negotiation completed with 24:a4:3c:d8:36:4f [PTK=CCMP GTK=CCMP]
May 29 20:13:56 wpa-supplicant: CTRL-EVENT-CONNECTED — Connection to 24:a4:3c:d8:36:4f completed (reauth) [id=0 id_str=]
May 29 21:12:24 wpa-supplicant: WPA: Group rekeying completed with 24:a4:3c:d8:36:4f [GTK=CCMP]
May 29 21:35:12 init: process ‘/bin/lighttpd -D -f /etc/lighttpd.conf’ (pid 2834) exited. Scheduling for restart.
May 29 21:35:12 init: starting pid 19781, tty ‘/dev/null’: ‘/bin/lighttpd -D -f /etc/lighttpd.conf’
May 29 22:12:24 wpa-supplicant: WPA: Group rekeying completed with 24:a4:3c:d8:36:4f [GTK=CCMP]
May 29 23:12:24 wpa-supplicant: WPA: Group rekeying completed with 24:a4:3c:d8:36:4f [GTK=CCMP]
May 29 23:26:16 init: process ‘/bin/lighttpd -D -f /etc/lighttpd.conf’ (pid 19781) exited. Scheduling for restart.
May 29 23:26:17 init: starting pid 23659, tty ‘/dev/null’: ‘/bin/lighttpd -D -f /etc/lighttpd.conf’
Логи AP
May 28 17:55:17 system: Start
May 28 17:55:18 FileSystem: Start check…
May 28 17:55:37 FileSystem: End check.
May 29 18:33:08 system: Stop
May 29 18:33:22 system: Start
May 29 19:53:26 system: Stop
May 29 19:53:40 system: Start
May 29 21:32:30 system: Stop
May 29 21:32:45 system: Start
May 29 21:32:45 syslogd started: BusyBox v1.11.2
May 29 21:32:45 wireless: ath0 Set Mode:Master
May 29 21:32:45 dropbear[4373]: Not backgrounding
May 29 21:34:18 wireless: ath0 MLME-AUTH.indication(addr=dc:9f:db:2a:74:82)
May 29 21:34:18 wireless: ath0 Registered node:DC:9F:DB:2A:74:82
May 29 21:34:18 hostapd: ath0: STA dc:9f:db:2a:74:82 IEEE 802.11: associated
May 29 21:34:18 hostapd: ath0: STA dc:9f:db:2a:74:82 WPA: pairwise key handshake completed (RSN)
May 29 22:32:46 hostapd: ath0: STA dc:9f:db:2a:74:82 WPA: group key handshake completed (RSN)
May 29 23:32:46 hostapd: ath0: STA dc:9f:db:2a:74:82 WPA: group key handshake completed (RSN)
May 30 00:32:46 hostapd: ath0: STA dc:9f:db:2a:74:82 WPA: group key handshake completed (RSN)
May 30 01:32:46 hostapd: ath0: STA dc:9f:db:2a:74:82 WPA: group key handshake completed (RSN)
May 30 02:32:46 hostapd: ath0: STA dc:9f:db:2a:74:82 WPA: group key handshake completed (RSN)
May 30 03:32:46 hostapd: ath0: STA dc:9f:db:2a:74:82 WPA: group key handshake completed (RSN)
May 30 04:32:46 hostapd: ath0: STA dc:9f:db:2a:74:82 WPA: group key handshake completed (RSN)
May 30 04:49:57 wireless: ath0 Received disassoc from dc:9f:db:2a:74:82. Reason: Station has left the basic service area and is disassociated (8).
May 30 04:49:57 wireless: ath0 STA-TRAFFIC-STAT mac=dc:9f:db:2a:74:82 rx_packets=27231431 rx_bytes=4880762214 tx_packets=36863276 tx_bytes=40896572639
May 30 04:49:57 wireless: ath0 Expired node:DC:9F:DB:2A:74:82
May 30 04:49:57 hostapd: ath0: STA dc:9f:db:2a:74:82 IEEE 802.11: disassociated
May 30 04:52:35 wireless: ath0 MLME-AUTH.indication(addr=dc:9f:db:2a:74:82)
May 30 04:52:35 wireless: ath0 Registered node:DC:9F:DB:2A:74:82
May 30 04:52:35 hostapd: ath0: STA dc:9f:db:2a:74:82 IEEE 802.11: associated
May 30 04:52:35 hostapd: ath0: STA dc:9f:db:2a:74:82 WPA: pairwise key handshake completed (RSN)
May 30 05:32:46 hostapd: ath0: STA dc:9f:db:2a:74:82 WPA: group key handshake completed (RSN)
May 30 06:32:46 hostapd: ath0: STA dc:9f:db:2a:74:82 WPA: group key handshake completed (RSN)
May 30 07:32:46 hostapd: ath0: STA dc:9f:db:2a:74:82 WPA: group key handshake completed (RSN)
May 30 08:32:46 hostapd: ath0: STA dc:9f:db:2a:74:82 WPA: group key handshake completed (RSN)
May 30 09:32:47 hostapd: ath0: STA dc:9f:db:2a:74:82 WPA: group key handshake completed (RSN)
May 30 10:32:47 hostapd: ath0: STA dc:9f:db:2a:74:82 WPA: group key handshake completed (RSN)
May 30 11:32:47 hostapd: ath0: STA dc:9f:db:2a:74:82 WPA: group key handshake completed (RSN)
May 30 12:32:47 hostapd: ath0: STA dc:9f:db:2a:74:82 WPA: group key handshake completed (RSN)
May 30 13:32:47 hostapd: ath0: STA dc:9f:db:2a:74:82 WPA: group key handshake completed (RSN)
May 30 14:32:47 hostapd: ath0: STA dc:9f:db:2a:74:82 WPA: group key handshake completed (RSN)
May 30 15:32:47 hostapd: ath0: STA dc:9f:db:2a:74:82 WPA: group key handshake completed (RSN)
May 30 16:32:47 hostapd: ath0: STA dc:9f:db:2a:74:82 WPA: group key handshake completed (RSN)
May 30 17:32:47 hostapd: ath0: STA dc:9f:db:2a:74:82 WPA: group key handshake completed (RSN)
May 30 18:32:47 hostapd: ath0: STA dc:9f:db:2a:74:82 WPA: group key handshake completed (RSN)
May 30 18:39:02 init: reloading /etc/inittab
May 30 18:39:02 system: Stop
May 30 18:39:03 wireless: ath0 Sending deauth to dc:9f:db:2a:74:82. Reason: Unspecified (1).
May 30 18:39:03 wireless: ath0 STA-TRAFFIC-STAT mac=dc:9f:db:2a:74:82 rx_packets=28908980 rx_bytes=8177276629 tx_packets=37813536 tx_bytes=39973552150
May 30 18:39:03 wireless: ath0 Expired node:DC:9F:DB:2A:74:82
May 30 18:39:03 dropbear[4373]: premature exit: Terminated by signal
May 30 18:39:03 init: process ‘/bin/hostapd /etc/aaa1.cfg’ (pid 4370) exited. Scheduling for restart.
May 30 18:39:03 init: process ‘/bin/dropbear -F -d /etc/persistent/dropbear_dss_host_key -r /etc/persistent/dropbear_rsa_host_key -p 22 ‘ (pid 4373
May 30 18:39:04 init: process ‘/bin/lighttpd -D -f /etc/lighttpd.conf’ (pid 4372) exited. Scheduling for restart.
May 30 18:39:06 syslogd exiting
May 30 18:39:16 system: Start
May 30 18:39:16 syslogd started: BusyBox v1.11.2
May 30 18:39:17 wireless: ath0 Set Mode:Master
May 30 18:39:17 dropbear[8954]: Not backgrounding
May 30 18:40:49 hostapd: ath0: STA dc:9f:db:2a:74:82 IEEE 802.11: associated
May 30 18:40:49 wireless: ath0 MLME-AUTH.indication(addr=dc:9f:db:2a:74:82)
May 30 18:40:49 wireless: ath0 Registered node:DC:9F:DB:2A:74:82
May 30 18:40:49 hostapd: ath0: STA dc:9f:db:2a:74:82 WPA: pairwise key handshake completed (RSN)
May 30 19:39:18 hostapd: ath0: STA dc:9f:db:2a:74:82 WPA: group key handshake completed (RSN)
May 30 20:39:18 hostapd: ath0: STA dc:9f:db:2a:74:82 WPA: group key handshake completed (RSN)
May 30 21:30:47 dropbear[9129]: Child connection from ::ffff:10.1.1.102:63489
May 30 21:30:55 dropbear[9129]: password auth succeeded for ‘ubnt’ from ::ffff:10.1.1.102:63489
May 30 21:31:05 dropbear[9129]: exit after auth (ubnt): Exited normally
May 30 21:39:18 hostapd: ath0: STA dc:9f:db:2a:74:82 WPA: group key handshake completed (RSN)
Изменено 5 сентября, 2014 пользователем mirex
Сообщения без ответов | Активные темы
| Автор | Сообщение |
|---|---|
|
vel21ripn |
Заголовок сообщения: DAP-2360/2690 как мониторить подключения клиентов?
|
|
|
В snmp trap нет информации ни о MAC ни о SSID подключенного клиента. Только факт подключения. trap на отключение клиента нет. Где можно посмотреть расшифровку кодов reason при отключении клиентов? В логах есть 0,1,3,6,7,8,9 |
| Вернуться наверх |
|
|
Mikhail Lesnikov |
Заголовок сообщения: Re: DAP-2360/2690 как мониторить подключения клиентов?
|
|
|
vel21ripn писал(а): trap на отключение клиента нет stationDisassocNotify {trapInstances 15} Получить информацию о подключенных клиентах (в т.ч. MAC и SSID) можно из dot11ClientInformationTable. Reason code (первоисточник — http://standards.ieee.org/getieee802/do … 1-2007.pdf ) |
| Вернуться наверх |
|
|
vel21ripn |
Заголовок сообщения: Re: DAP-2360/2690 как мониторить подключения клиентов?
|
|
|
Mikhail Lesnikov писал(а): Получить информацию о подключенных клиентах (в т.ч. MAC и SSID) можно из dot11ClientInformationTable. Для тех кто подключен на данный момент, а те кто подключились на короткое время и успели отключиться — нужно смотреть в логах. Цитата: Спасибо. Будем ждать. В DAP-2690 в логах замечена опечатка «Sucess:STA» |
| Вернуться наверх |
|
Кто сейчас на форуме |
|
Сейчас этот форум просматривают: нет зарегистрированных пользователей и гости: 9 |
| Вы не можете начинать темы Вы не можете отвечать на сообщения Вы не можете редактировать свои сообщения Вы не можете удалять свои сообщения Вы не можете добавлять вложения |
Hi,
I wonder if you could help me as I’m really struggling to adopt some of my devices after a factory reset, they seem to have remembered the old controller even after multiple resets. Any help would be really appreciated!
Thanks!
My network consists of:
-
UDM (not pro)
-
4 x US-8-150W
-
1 x UAP-AC-M
-
3 x UAP-AC-Pro
UDM Firmware: v1.9.3UDM Controller: v6.1.71
Yesterday I accidentally factory reset the UDM when trying to reboot it by holding down the button underneath. So I reconfigured the UDM through normal setup and then once it was online I restored a backup of my controller.
At this point all of the switches and access points showed as «Managed by another device«. Obviously that device was the same UDM device but before the accidental factory reset.
So I went around the house and reset every device using a small pin with the hardware reset button.
Two switches and two access points were then adopted and provisioned and are working as expected but the remaining switches (2 x US-8-150W and 2 x UAP-AC-PRO) are stuck at «adopting«.
Symptoms:
-
Their status LED is solid white after booting
-
They show as «Adopting» in the devices page of the controller
-
After a few minutes of «Adopting» they cycle back to «Disconnected» in the controller gui
-
They then continue in this Adopting / Disconnected Loop for ever
-
SSH «Info» command shows «Not Adopted» when first booted and then changes to «Server Reject (http://192.168.1.1:8080/inform)**«
-
Looking at /var/log/messages on the bad devices shows:
ace_reporter.reporter_fail(): Server Reject (http://192.168.1.1:8080/inform)
ace_reporter.reporter_fail(): initial contact failed #3, url=http://192.168.1.1:8080/inform, rc=5
-
The UDM log shows:
<inform-37> ERROR inform - invalid fingerprint:
-
I’ve read that I might need to delete the fingerprint from the database using the below, but mongo doesn’t seem to be installed and I don’t know how and where to install it from
mongo --port27117
use ace
db.device.remove({"mac":"XX:XX:XX:XX:XX:XX"});
exit
-
I can’t go on the old controller and forget the devices as the UDM I’m using is the old controller just after a factory reset it appears as new. Even with the backup restored.
Things that I have tried:
-
I’ve tried resetting with: set-default
-
I’ve tried resetting with: syswrapper.sh restore-default
-
I’ve tried resetting by holding the hardware reset button
-
I’ve tried upgrading each device to its most recent firmware and also rolling back to older versions of the firmware with: upgrade https://dl.ui.com/unifi/firmware/xxxxxxxxx.bin
-
I’ve tried setting the inform address as: set-inform http://192.168.1.1:8080/inform
-
I’ve verified that inform address is correct with one of the working APs as below:
AP-Garden-Front-BZ.v4.3.28# info
Model: UAP-AC-Mesh
Version: 4.3.28.11361
MAC Address: e0:63:da:b0:93:6e
IP Address: 192.168.1.113
Hostname: AP-Garden-Front
Uptime: 47855 seconds
Status: Connected (http://192.168.1.1:8080/inform)
AP-Garden-Front-BZ.v4.3.28#
-
Tried to remove the devices from the database but couldn’t get this to work
mongo --port27117
use ace
db.device.remove({"mac":"XX:XX:XX:XX:XX:XX"});
exit
-sh: mongo: not found
Logs and Stuff
Here are some screenshots showing the devices looping between «Adopting» and «Disconnected«
https://postimg.cc/Mv2MfFg1
https://postimg.cc/mtYcYSGJ
Here is the info command on the four devices that will not adopt:
----------------------------
UBNT-BZ.v4.3.28# info
Model: UAP-AC-Pro-Gen2
Version: 4.3.28.11361
MAC Address: e0:63:da:39:02:68
IP Address: 192.168.1.186
Hostname: UBNT
Uptime: 2132 seconds
Status: Server Reject (http://192.168.1.1:8080/inform)
----------------------------
UBNT-BZ.v4.3.28#
Model: UAP-AC-Pro-Gen2
Version: 4.3.28.11361
MAC Address: 74:83:c2:cc:74:9f
IP Address: 192.168.1.77
Hostname: UBNT
Uptime: 1401 seconds
Status: Server Reject (http://192.168.1.1:8080/inform)
UBNT-BZ.v4.3.28#
----------------------------
US-8-150W-US.5.43.18# info
Model: US-8-150W
Version: 5.43.18.12487
MAC Address: 74:ac:b9:16:40:0b
IP Address: 192.168.1.108
Hostname: US-8-150W
Uptime: 37927 seconds
Status: Not Adopted (http://192.168.1.1:8080/inform)
US-8-150W-US.5.43.18#
----------------------------
US-8-150W-US.5.43.23# info
Model: US-8-150W
Version: 5.43.23.12533
MAC Address: 74:ac:b9:3c:41:18
IP Address: 192.168.1.80
Hostname: US-8-150W
Uptime: 41245 seconds
Status: Server Reject (http://192.168.1.1:8080/inform)
US-8-150W-US.5.43.23#
Here is /var/log/messages for one of those devices showing the inform reject errors:
UBNT-BZ.v4.3.28# tail -20 /var/log/messages
Mon May 10 10:24:33 2021 user.err : mcad[1375]: ace_reporter.reporter_fail(): Not Adopted (http://192.168.1.1:8080/inform)
Mon May 10 10:24:33 2021 user.err : mcad[1375]: ace_reporter.reporter_fail(): initial contact failed #4, url=http://192.168.1.1:8080/inform, rc=6
Mon May 10 10:24:33 2021 user.info : mcad[1375]: ace_reporter.reporter_next_inform_method(): next inform family: 10
Mon May 10 10:24:40 2021 user.info : uplink-monitor[1381]: vwire.dec_meshv3_data(): crc=428dd9e5, crc_new=428dd9e5
Mon May 10 10:24:46 2021 authpriv.info dropbear[16770]: Child connection from 192.168.1.1:55822
Mon May 10 10:24:46 2021 authpriv.notice dropbear[16770]: Password auth succeeded for 'ubnt' from 192.168.1.1:55822
Mon May 10 10:24:47 2021 authpriv.info dropbear[16770]: Exit (ubnt): Disconnect received
Mon May 10 10:24:47 2021 user.err : mcad[1375]: ace_reporter.reporter_fail(): Server Reject (http://192.168.1.1:8080/inform)
Mon May 10 10:24:47 2021 user.err : mcad[1375]: ace_reporter.reporter_fail(): initial contact failed #1, url=http://192.168.1.1:8080/inform, rc=5
Mon May 10 10:24:55 2021 user.info : uplink-monitor[1381]: vwire.dec_meshv3_data(): crc=428dd9e5, crc_new=428dd9e5
Mon May 10 10:25:02 2021 user.err : mcad[1375]: ace_reporter.reporter_fail(): Server Reject (http://192.168.1.1:8080/inform)
Mon May 10 10:25:02 2021 user.err : mcad[1375]: ace_reporter.reporter_fail(): initial contact failed #2, url=http://192.168.1.1:8080/inform, rc=5
Mon May 10 10:25:11 2021 user.info : uplink-monitor[1381]: vwire.dec_meshv3_data(): crc=428dd9e5, crc_new=428dd9e5
Mon May 10 10:25:18 2021 user.err : mcad[1375]: ace_reporter.reporter_fail(): Server Reject (http://192.168.1.1:8080/inform)
Mon May 10 10:25:18 2021 user.err : mcad[1375]: ace_reporter.reporter_fail(): initial contact failed #3, url=http://192.168.1.1:8080/inform, rc=5
Mon May 10 10:25:26 2021 user.info : uplink-monitor[1381]: vwire.dec_meshv3_data(): crc=428dd9e5, crc_new=428dd9e5
Mon May 10 10:25:33 2021 user.err : mcad[1375]: ace_reporter.reporter_fail(): Not Adopted (http://192.168.1.1:8080/inform)
Mon May 10 10:25:33 2021 user.err : mcad[1375]: ace_reporter.reporter_fail(): initial contact failed #4, url=http://192.168.1.1:8080/inform, rc=6
Mon May 10 10:25:33 2021 user.info : mcad[1375]: ace_reporter.reporter_next_inform_method(): next inform family: 10
Mon May 10 10:25:41 2021 user.info : uplink-monitor[1381]: vwire.dec_meshv3_data(): crc=428dd9e5, crc_new=428dd9e5
UBNT-BZ.v4.3.28#
Here is the UDM log showing that the reason for reject is (probably) an invalid fingerprint:
[2021-05-10T09:45:32,193] <inform-37> ERROR inform - invalid fingerprint: expecting[85:05:a0:3e:b8:58:b9:e4:60:23:42:45:46:9a:75:ba], payload={anon_id=cbf9ada7-3175-4d, antenna_table=[{default=true, id=4, name=Combined, wifi0_gain=3, wifi1_gain=3}], architecture=mips, board_rev=31, bootid=0, bootrom_version=unifi-v2.0.6.306-ge8871a78, cfgversion=?, country_code=0, countrycode_table=[], default=true, discovery_response=true, dualboot=true, ever_crash=false, fingerprint=8f:ca:98:bc:9a:b1:22:72:2f:d9:74:5f:9e:54:d8:fd:13:e4:ed:a8, fw_caps=58654015, gateway_ip=192.168.1.1, gateway_mac=76:ac:b9:4a:08:5a, guest_kicks=0, guest_token=9F2BE8603DD37B22C6684CC3A32410DF, has_eth1=false, has_speaker=false, hash_id=6739427b8a0aba1f, hostname=UBNT, hw_caps=0, if_table=[{full_duplex=true, ip=0.0.0.0, mac=e0:63:da:39:02:68, max_vlan=96, name=eth0, netmask=0.0.0.0, num_port=2, rx_bytes=108000406, rx_dropped=70, rx_errors=0, rx_multicast=0, rx_packets=624440, speed=1000, tx_bytes=2136954649, tx_dropped=0, tx_errors=0, tx_packets=1587667, up=true}], inform_url=http://192.168.1.1:8080/inform, internet=true, ip=192.168.1.186, isolated=false, kernel_version=4.4.153, last_error=Server Reject (http://192.168.1.1:8080/inform), locating=false, mac=e0:63:da:39:02:68, manufacturer_id=4, model=U7PG2, model_display=UAP-AC-Pro-Gen2, netmask=255.255.255.0, port_table=[{attr_no_edit=true, autoneg=true, enable=true, flowctrl_rx=false, flowctrl_tx=false, full_duplex=true, is_uplink=false, jumbo=false, mac_table=[{age=4, mac=70:10:6f:3e:65:1a, static=false, uptime=1893, vlan=1}, {age=4, mac=dc:a6:32:c2:d9:79, static=false, uptime=2008, vlan=1}, {age=4, mac=70:10:6f:3e:65:18, static=false, uptime=2008, vlan=1}, {age=4, mac=00:17:88:40:6f:72, static=false, uptime=2002, vlan=1}, {age=4, mac=74:ac:b9:16:40:0c, static=false, uptime=2008, vlan=1}, {age=4, mac=74:ac:b9:16:40:0b, static=false, uptime=2008, vlan=1}, {age=4, mac=f8:d0:27:31:bc:47, static=false, uptime=1862, vlan=1}, {age=4, mac=54:10:ec:68:d1:e5, static=false, uptime=1996, vlan=1}, {age=4, mac=98:fa:9b:01:5b:21, static=false, uptime=2008, vlan=1}], media=GE, name=Main, poe_caps=0, port_idx=1, port_poe=false, rx_broadcast=10990, rx_bytes=110589287, rx_dropped=0, rx_errors=0, rx_multicast=10830, rx_packets=625239, speed=1000, stp_pathcost=0, stp_state=forwarding, tx_broadcast=6487, tx_bytes=2144273177, tx_dropped=0, tx_errors=0, tx_multicast=44693, tx_packets=1588107, up=true}, {autoneg=false, enable=true, flowctrl_rx=false, flowctrl_tx=false, full_duplex=false, is_uplink=false, jumbo=false, mac_table=[], media=GE, name=Secondary, poe_caps=0, port_idx=2, port_poe=false, rx_broadcast=0, rx_bytes=0, rx_dropped=0, rx_errors=0, rx_multicast=0, rx_packets=0, speed=0, stp_pathcost=0, stp_state=forwarding, tx_broadcast=0, tx_bytes=0, tx_dropped=0, tx_errors=0, tx_multicast=0, tx_packets=0, up=false}], qrid=f93bkP, radio_table=[{athstats={ast_ath_reset=0, ast_be_xmit=707, ast_cst=0, ast_deadqueue_reset=0, ast_fullqueue_stop=0, ast_txto=0, cu_self_rx=23, cu_self_tx=2, cu_total=30, n_rx_aggr=0, n_rx_pkts=2404, n_tx_bawadv=0, n_tx_bawretries=0, n_tx_pkts=0, n_tx_queue=0, n_tx_retries=0, n_tx_xretries=0, n_txaggr_compgood=0, n_txaggr_compretries=0, n_txaggr_compxretry=0, n_txaggr_prepends=0, name=wifi0, noise_floor=-95, satisfaction=-1, satisfaction_now=-1, satisfaction_real=-1}, builtin_ant_gain=3, builtin_antenna=true, ieee_modes=10, max_txpower=22, min_txpower=6, name=wifi0, nss=3, radio=ng, radio_caps=16420, scan_table=[]}, {athstats={ast_ath_reset=4, ast_be_xmit=0, ast_cst=0, ast_deadqueue_reset=38, ast_fullqueue_stop=0, ast_txto=0, cu_self_rx=0, cu_self_tx=0, cu_total=0, n_rx_aggr=162190, n_rx_pkts=1644833, n_tx_bawadv=230082, n_tx_bawretries=0, n_tx_pkts=1080, n_tx_queue=0, n_tx_retries=1, n_tx_xretries=18474, n_txaggr_compgood=0, n_txaggr_compretries=0, n_txaggr_compxretry=0, n_txaggr_prepends=0, name=wifi1, noise_floor=-95, satisfaction=-1, satisfaction_now=-1, satisfaction_real=-1}, builtin_ant_gain=3, builtin_antenna=true, has_dfs=true, has_fccdfs=true, ieee_modes=21, is_11ac=true, max_txpower=22, min_txpower=6, name=wifi1, nss=3, radio=na, radio_caps=50479140, scan_table=[{age=0, band=na, bssid=76:ac:b9:1a:08:5f, bw=80, center_freq=5770, channel=157, essid=, freq=5785, fw_version=, is_adhoc=false, is_default=false, is_isolated=false, is_locating=false, is_meshv3=true, is_ubnt=true, is_unifi=true, is_vport=false, is_vwire=true, model=UDM, model_display=UniFi Dream Machine, noise=-96, rssi=48, rssi_age=0, security=WPA2 (AES/CCMP), serialno=74ACB94A0859, signal=-48}, {age=0, band=na, bssid=76:ac:b9:1a:08:5f, bw=80, center_freq=5770, channel=157, essid=vwire-910e81cf117f6b6b, freq=5785, fw_version=, is_adhoc=false, is_default=false, is_isolated=false, is_locating=false, is_meshv3=true, is_ubnt=true, is_unifi=true, is_vport=false, is_vwire=true, model=UDM, model_display=UniFi Dream Machine, noise=-96, rssi=48, rssi_age=0, security=WPA2 (AES/CCMP), serialno=74ACB94A0859, signal=-48}]}], required_version=3.4.1, satisfaction=-1, satisfaction_now=-1, satisfaction_real=-1, scan_radio_table=[], selfrun_beacon=true, serial=E063DA390268, spectrum_scanning=false, ssh_session_table=[], state=1, stream_token=, switch_caps={feature_caps=32, max_aggregate_sessions=0, max_l3_intf=0, max_mirror_sessions=0, max_reserved_routes=0, max_static_routes=0}, sys_error_caps=0, sys_stats={loadavg_1=0.20, loadavg_15=0.09, loadavg_5=0.10, mem_buffer=0, mem_total=128622592, mem_used=63086592}, system-stats={cpu=9.4, mem=27.1, uptime=2023}, time=1620636331, time_ms=380, tm_ready=true, uplink=ath1, uptime=2023, vap_table=[{anomalies_bar_chart={high_dns_latency=0, high_icmp_rtt=0, high_tcp_latency=0, high_tcp_packet_loss=0, high_wifi_latency=0, high_wifi_retries=0, low_phy_rate=0, poor_stream_eff=0, sleepy_client=0, sta_arp_timeout=0, sta_dns_timeout=0, sta_ip_timeout=0, weak_signal=0}, anomalies_bar_chart_now={high_dns_latency=0, high_icmp_rtt=0, high_tcp_latency=0, high_tcp_packet_loss=0, high_wifi_latency=0, high_wifi_retries=0, low_phy_rate=0, poor_stream_eff=0, sleepy_client=0, sta_arp_timeout=0, sta_dns_timeout=0, sta_ip_timeout=0, weak_signal=0}, avg_client_signal=-48, bssid=76:ac:b9:1a:08:5f, ccq=333, channel=157, dns_avg_latency=0, essid=vwire-910e81cf117f6b6b, extchannel=1, icmp_avg_rtt=0, id=user, mac_filter_rejections=0, name=ath1, num_satisfaction_sta=0, num_sta=1, radio=na, radio_name=wifi1, reasons_bar_chart={phy_rate=0, signal=0, sleepy_client=0, sta_arp_timeout=0, sta_dns_latency=0, sta_dns_timeout=0, sta_icmp_rtt=0, sta_ip_timeout=0, stream_eff=0, tcp_latency=0, tcp_packet_loss=0, wifi_latency=0, wifi_retries=0}, reasons_bar_chart_now={phy_rate=0, signal=0, sleepy_client=0, sta_arp_timeout=0, sta_dns_latency=0, sta_dns_timeout=0, sta_icmp_rtt=0, sta_ip_timeout=0, stream_eff=0, tcp_latency=0, tcp_packet_loss=0, wifi_latency=0, wifi_retries=0}, rx_bytes=2137017785, rx_crypts=4210, rx_dropped=4210, rx_errors=4210, rx_frags=0, rx_nwids=0, rx_packets=1587958, rx_tcp_stats={goodbytes=839283, lat_avg=-1, lat_max=0, lat_min=4294967295, lat_samples=0, lat_sum=0, stalls=0}, satisfaction=-1, satisfaction_now=-1, satisfaction_real=-1, sta_table=[{anomalies=0, anomalies_now=0, auth_time=4252170324, authorized=true, ccq=333, dhcpend_time=0, dhcpstart_time=42801082, dns_avg_latency=0, hostname=ESP_34AEDD, idletime=0, is_11a=true, is_11ac=true, is_11n=true, mac=76:ac:b9:1a:08:5f, noise=-105, rssi=48, rx_bytes=2137000773, rx_bytes_mov=67917344, rx_mcast=0, rx_packets=1587944, rx_rate=780000, rx_rate_mov=780000, rx_retries=0, rx_tcp_stats={goodbytes=839283, lat_avg=-1, lat_max=0, lat_min=4294967295, lat_samples=0, lat_sum=0, stalls=0}, satisfaction=-1, satisfaction_now=-1, satisfaction_real=-1, satisfaction_reason=0, satisfaction_reason_now=0, serialno=74:ac:b9:4a:08:59, signal=-48, skip_satisfaction=1, state=11, state_ht=true, state_pwrmgt=false, tx_bytes=108459216, tx_bytes_mov=4230914, tx_combined_retries=53280, tx_data_mpdu_bytes=126917535, tx_packets=624954, tx_power=44, tx_rate=351000, tx_rate_mov=477750, tx_retries=53280, tx_retries_mov=2808, tx_rts_retries=0, tx_tcp_stats={goodbytes=0, lat_avg=68, lat_max=190, lat_min=0, lat_samples=578, lat_sum=39450, stalls=0}, tx_total=324537, tx_total_mov=10939, uptime=1722, vlan_id=0, wifi_tx_attempts=377817, wifi_tx_attempts_mov=13747, wifi_tx_dropped=0, wifi_tx_dropped_mov=0, wifi_tx_latency_mov={avg=473, max=10186, min=103, total=4204409, total_count=8887}, wifi_tx_success=324537}], state=RUN, tx_bytes=108460789, tx_combined_retries=53280, tx_data_mpdu_bytes=126917535, tx_dropped=0, tx_errors=1845, tx_packets=624961, tx_power=22, tx_retries=53280, tx_rts_retries=0, tx_success=324537, tx_tcp_stats={goodbytes=0, lat_avg=68, lat_max=190, lat_min=0, lat_samples=578, lat_sum=39450, stalls=0}, tx_total=324537, up=true, usage=uplink, wifi_tx_attempts=377817, wifi_tx_dropped=0, wifi_tx_latency_mov={avg=473, max=10186, min=103, total=4204409, total_count=8887}}, {anomalies_bar_chart={high_dns_latency=0, high_icmp_rtt=0, high_tcp_latency=0, high_tcp_packet_loss=0, high_wifi_latency=0, high_wifi_retries=0, low_phy_rate=0, poor_stream_eff=0, sleepy_client=0, sta_arp_timeout=0, sta_dns_timeout=0, sta_ip_timeout=0, weak_signal=0}, anomalies_bar_chart_now={high_dns_latency=0, high_icmp_rtt=0, high_tcp_latency=0, high_tcp_packet_loss=0, high_wifi_latency=0, high_wifi_retries=0, low_phy_rate=0, poor_stream_eff=0, sleepy_client=0, sta_arp_timeout=0, sta_dns_timeout=0, sta_ip_timeout=0, weak_signal=0}, avg_client_signal=0, bssid=00:00:00:00:00:00, ccq=0, channel=6, dns_avg_latency=-1, essid=E063DA390268, icmp_avg_rtt=-1, id=user, mac_filter_rejections=0, name=ath0, num_satisfaction_sta=0, num_sta=0, radio=ng, radio_name=wifi0, reasons_bar_chart={phy_rate=0, signal=0, sleepy_client=0, sta_arp_timeout=0, sta_dns_latency=0, sta_dns_timeout=0, sta_icmp_rtt=0, sta_ip_timeout=0, stream_eff=0, tcp_latency=0, tcp_packet_loss=0, wifi_latency=0, wifi_retries=0}, reasons_bar_chart_now={phy_rate=0, signal=0, sleepy_client=0, sta_arp_timeout=0, sta_dns_latency=0, sta_dns_timeout=0, sta_icmp_rtt=0, sta_ip_timeout=0, stream_eff=0, tcp_latency=0, tcp_packet_loss=0, wifi_latency=0, wifi_retries=0}, rx_bytes=0, rx_crypts=0, rx_dropped=0, rx_errors=0, rx_frags=0, rx_nwids=148, rx_packets=0, rx_tcp_stats={goodbytes=0, lat_avg=0, lat_max=0, lat_min=4294967295, lat_samples=0, lat_sum=0, stalls=0}, satisfaction=-1, satisfaction_now=-1, satisfaction_real=-1, sta_table=[], state=INIT, tx_bytes=0, tx_combined_retries=0, tx_data_mpdu_bytes=0, tx_dropped=29, tx_errors=0, tx_packets=0, tx_power=15, tx_retries=0, tx_rts_retries=0, tx_success=0, tx_tcp_stats={goodbytes=0, lat_avg=0, lat_max=0, lat_min=4294967295, lat_samples=0, lat_sum=0, stalls=0}, tx_total=0, up=false, usage=user, wifi_tx_attempts=0, wifi_tx_dropped=0}], version=4.3.28.11361, wifi_caps=573429, _mac=E0-63-DA-39-02-68, _authkey=20e33143e4cac314887c69dff98ffdb8, _encrypted=true, _protoheader=Header v0:
Magic: 544e4255
If you got this far thanks a lot!
This page will cover everything you need to know about ESP Easy WiFi and connecting it to an AP (Access Point).
Contents
- 1 Hidden SSID
- 2 Connection problems
- 2.1 Not using the AP with best signal
- 2.2 Refuse to connect to another AP with same SSID
- 3 WiFi disconnect codes
Hidden SSID
Currently there’s a problem if you use hidden SSID on channels 11 — 14.
Hidden channels are shown in the scan, but when selected it is not possible to connect to them on channel 11 and above.
This is probably related to the ESP core libraries.
Sometimes connecting to a hidden SSID may fail the first time, even when the channel number is below 1 — 10.
For these situations, it may help to temporally change the WiFi to not hidden and then after the units are connected hide the SSID again.
Connection problems
ESPeasy can switch to another AP with the same SSID and password when the original connection is lost.
The rules to reconnect are:
- First retry to connect to the previously connected AP (using the BSSID of that AP)
- Perform a scan and connect to the AP with the strongest RSSI (signal strength)
In practice there may be some issues.
Not using the AP with best signal
Both the ESP82xx and almost all Access Points do use power save options, which means the wifi radio is not always active and enabled.
An access point sends at a Beacon Interval of typical 100 ms. Some Access Points may allow changing this to lower values to improve response times for VoIP-like applications.
This Beacon Interval is to keep (idle) connections alive and to allow other devices to ‘see’ and connect to an access point.
An AP does not have to send a beacon signal every interval, as long as it sends the next one at the same interval.
A sent beacon signal may also get lost due to the shared nature of the WiFi medium.
A typical scan for available SSID’s may miss a beacon signal, since it will only listen for a short time (about 250 msec) to a channel and then hop to the next.
Also the ESP may receive some interrupt from a sensor during a scan and just miss the beacon signal.
This results in a list of found SSIDs from which the strongest one with the matching SSID is chosen.
Due to the issues mentioned above, the actual strongest AP may be omitted.
When a connection is lost, ESPeasy will try to reconnect to the last known AP (based on the BSSID) and thus keep reconnecting to the AP with a sub-optimal signal strength.
A simple reboot may break this cycle.
Refuse to connect to another AP with same SSID
There have been reports of users unable to connect to a different AP with the same SSID.
Even with the original AP switched off.
It seems like the ESP core libraries may store connection state to a different part of the flash memory.
This may affect other WiFi connections.
Current versions of ESPeasy prevent writing these settings, but when other firmware versions were used on the node, these settings may be present.
To wipe these conflicting settings, the whole flash has to be wiped clean using a tool like ESPtool.py.
After flashing the ESPeasy firmware again, it will allow connecting to any accesspoint again.
Future versions of ESPeasy may be able to clear these settings.
WiFi disconnect codes
The following codes may appear in the log:
| Code | Reason | Explanation | |
|---|---|---|---|
| 0 | Reserved | Normal working operation | |
| 1 | Unspecific Reason | We don’t know what’s wrong | |
| 2 | Previous authentication no longer valid | Client has associated but is not authorised. | |
| 3 | Deauthenticated because sending STA is leaving (or has left) IBSS or ESS | The access point went offline, deauthenticating the client. | |
| 4 | Disassociated due to inactivity | Client session timeout exceeded. | |
| 5 | Disassociated because AP is unable to handle all currently associated STAs | The access point is busy, performing load balancing, for example. | |
| 6 | Class 2 frame received from nonauthenticated STA | Client attempted to transfer data before it was authenticated. | |
| 7 | Class 3 frame received from nonassociated STA | Client attempted to transfer data before it was associated. | |
| 8 | Disassociated because sending STA is leaving (or has left) BSS | Operating System moved the client to another access point using non-aggressive load balancing. | |
| 9 | STA requesting (re)association is not authenticated with responding STA | Client not authorized yet, still attempting to associate with an access point. | |
| 10 | Disassociated because the information in the Power Capability element is unacceptable | ||
| 11 | Disassociated because the information in the Supported Channels element is unacceptable | ||
| 12 | Reserved | Not Used or Special Purpose | |
| 13 | Invalid information element. | ||
| 14 | Message integrity code (MIC) failure | ||
| 15 | 4-Way Handshake timeout | ||
| 16 | Group Key Handshake timeout | ||
| 17 | Information element in 4-Way Handshake different from (Re)Association Request/Probe | Response/Beacon frame | |
| 18 | Invalid group cipher or The link speed requested by the client or AP is incompatible. (i,e. trying to operate N only speeds on a G AP) |
Association denied due to requesting STA not supporting all of the data rates in the BSSBasicRateSet parameter | |
| 19 | Invalid pairwise cipher | ||
| 20 | Invalid AKMP | ||
| 21 | Unsupported RSN information element version | ||
| 22 | Invalid RSN information element capabilities | ||
| 23 | IEEE 802.1X authentication failed | ||
| 24 | Cipher suite rejected because of the security policy | ||
| 25-31 | Reserved | Not Used or Special Purpose | |
| 32 | Disassociated for unspecified, QoS-related reason | Quality of Service has denied the action. | |
| 33 | Disassociated because QoS AP lacks sufficient bandwidth for this QoS STA | ||
| 34 | Disassociated because excessive number of frames need to be acknowledged, but are not acknowledged due to AP transmissions and/or poor channel conditions | ||
| 35 | Disassociated because STA is transmitting outside the limits of its TXOPs | ||
| 36 | Requested from peer STA as the STA is leaving the BSS (or resetting) | ||
| 37 | Requested from peer STA as it does not want to use the mechanism | ||
| 38 | Requested from peer STA as the STA received frames using the mechanism for which a setup is required | ||
| 39 | Requested from peer STA due to timeout | ||
| 45 | Peer STA does not support the requested cipher suite | ||
| 45-65 | Reserved | Not Used or Special Purpose | |
| 99 | Typically “No Reason Code” / Unknown State | ||
| 535 | Reserved | Not Used or Special Purpose |