Body
From MQ 7.1.0.2 onwards, the dreaded AMQ9633 «bad certificate» error message was enhanced with some additional information to help you understand which certificate was rejected and why. This is the most common error seen for SSL/TLS handshake errors and so I’d like to explain how to use the new information to understand the cause of the error.
Example AMQ9633 error
Below is an example of the new style of message with the new section highlighted in bold text, taken from a queue manager error log:
23/10/2014 08:31:41 — Process(1234.2) User(Fred) Program(amqrmppa.exe)
Host(hostname.example.com) Installation(Installation1)
VRMF(7.5.0.3) QMgr(QMGR1)
AMQ9633: Bad SSL certificate for channel ‘????’.
EXPLANATION:
A certificate encountered during SSL handshaking is regarded as bad for one of
the following reasons:
(a) it was formatted incorrectly and could not be validated
(b) it was formatted correctly but failed validation against the Certification
Authority (CA) root and other certificates held on the local system
(c) it was found in a Certification Revocation List (CRL) on an LDAP server
(d) a CRL was specified but the CRL could not be found on the LDAP server
(e) an OCSP responder has indicated that it is revoked
The channel is ‘????’; in some cases its name cannot be determined and so is
shown as ‘????’. The remote host is ‘host2.example.com (10.0.0.2)’. The channel
did not start.
The details of the certificate which could not be validated are
‘[Class=]GSKVALMethod::X509[Issuer=]CN=Example Certificate Authority,O=IBM,C=US[#=]67322456fe4af6de[Subject=]CN=Example MQ Certificate,O=IBM,C=US’.
The certificate validation error was 575010.
ACTION:
Check which of the possible causes applies on your system. Correct the error,
and restart the channel.
This error might indicate that the remote end of the channel is configured to
send the wrong certificate. Check the certificate label configuration at the
remote end of the channel and ensure that the local key repository contains all
of the necessary CA certificates.
For completeness, I should also mention that MQ 8.0 is able to determine the channel name in many cases so you should see fewer errors for channel ‘????’ (although there are still some cases where we can’t do that yet). The error messages are improving over time!
Understanding this error
The bold text in the message above shows the details of the problematic certificate. The main fields are:
- [Issuer=] — the Issuer Distinguished Name (DN) of the certificate, in this case CN=Example Certificate Authority,O=IBM,C=US
- [Subject=] — the Subject DN of the certificate, in this case CN=Example MQ Certificate,O=IBM,C=US
- [#=] — the serial number of the certificate in hexadecimal string form, in this case 67322456fe4af6de
So now we know which certificate had a problem. But what went wrong?
For this, there’s a numeric certificate validation error, which is usually a 6-digit number beginning with «575». The certificate validation errors are listed in the product documentation in Table 2 of the Secure Sockets Layer (SSL) and Transport Layer Security (TLS) return codes topic. For convenience, here’s a copy of the current table:
| Return code (decimal) | Explanation |
|---|---|
| 575001 | Internal error |
| 575002 | ASN error due to a malformed certificate |
| 575003 | Cryptographic error |
| 575004 | Key database error |
| 575005 | Directory error |
| 575006 | Invalid implementation library |
| 575008 | No appropriate validator |
| 575009 | The root CA is not trusted |
| 575010 | No certificate chain was built |
| 575011 | Digital signature algorithm mismatch |
| 575012 | Digital signature mismatch |
| 575013 | X.509 version does not allow Key IDs |
| 575014 | X.509 version does not allow extensions |
| 575015 | Unknown X.509 certificate version |
| 575016 | The certificate validity range is invalid |
| 575017 | The certificate is not yet valid |
| 575018 | The certificate has expired |
| 575019 | The certificate contains unknown critical extensions |
| 575020 | The certificate contains duplicate extensions |
| 575021 | The issuers directory name does not match the issuer’s issuer |
| 575022 | The Authority Key ID serial number value does not match the serial number of the issuer |
| 575023 | The Authority Key ID and Subject Key ID do not match |
| 575024 | Unrecognized issuer alternative name |
| 575025 | The certificate Basic Constraints forbid use as a CA |
| 575026 | The certificate has a non-zero Basic Constraints path length but is not a CA |
| 575027 | The certificate Basic Constraints maximum path length was exceeded |
| 575028 | The certificate is not permitted to sign other certificates |
| 575029 | The certificate is not signed by a CA |
| 575030 | Unrecognized Subject Alternative Name |
| 575031 | The certificate chain is invalid |
| 575032 | The certificate is revoked |
| 575033 | Unrecognized CRL distribution point |
| 575034 | Name chaining failed |
| 575035 | Certificate is not in a chain |
| 575036 | The CRL is not yet valid |
| 575037 | The CRL has expired |
| 575038 | The certificate version does not allow critical extensions |
| 575039 | Unknown CRL distribution points |
| 575040 | No CRLs for CRL distribution points |
| 575041 | Indirect CRLs are not supported |
| 575042 | Missing issuing CRL distribution point name |
| 575043 | Distribution points do not match |
| 575044 | No available CRL data source |
| 575045 | CA Subject name is null |
| 575046 | Distinguished names do not chain |
| 575047 | Missing Subject Alternative Name |
| 575048 | Unique ID mismatch |
| 575049 | Name not permitted |
| 575050 | Name excluded |
| 575051 | CA certificate is missing Critical Basic Constraints |
| 575052 | Name constraints are not critical |
| 575053 | Name constraints minimum subtree value if set is not zero |
| 575054 | Name constraints maximum subtree value if set is not allowed |
| 575055 | Unsupported name constraint |
| 575056 | Empty policy constraints |
| 575057 | Bad certificate policies |
| 575058 | Certificate policies not acceptable |
| 575059 | Bad acceptable certificate policies |
| 575060 | Certificate policy mappings are critical |
| 575061 | Revocation status could not be determined |
| 575062 | Extended key usage error |
| 575063 | Unknown OCSP version |
| 575064 | Unknown OCSP response |
| 575065 | Bad OCSP key usage extension |
| 575066 | Bad OCSP nonce |
| 575067 | Missing OCSP nonce |
| 575068 | No OCSP client available |
So we can see that our example error 575010 means that no certificate chain was built. A certificate chain is a sequence of related certificates which are linked by digital signatures (each certificate is the signer of the next one, up to the root certificate which is self-signed).
Failure to build a certificate chain usually means that our key repository lacks one of the Certificate Authority (CA) certificates needed to validate the remote certificate. Other errors have different causes, but since a missing CA certificate is a common error then it’s worth looking at the next steps.
How to fix this error
In this example, our queue manager which wrote the error message doesn’t have one of the CA certificates required. The first thing to do is to check that the issuer of the certificate is present in the queue manager’s key repository. In this case, the issuer has a DN of «CN=Example Certificate Authority,O=IBM,C=US» so check to see if the CA certificate is in the key repository. To do this, we must search for a certificate with a Subject DN of «CN=Example Certificate Authority,O=IBM,C=US»; this is because a CA certificate’s Subject DN is equal to the Issuer DN of any certificates signed by that CA, so we must find the certificate with a Subject DN that matches the problematic certificate’s Issuer DN.
To check for the CA certificate, either:
- Start the iKeyman GUI using the strmqikm command. Open the key repository file and then navigate to the Signer Certificates section using the drop-down list in the middle of the window. Double-click each certificate label in turn to view the certificate.
- Use the command-line to find out which certificates are in the key repository by listing their labels. Then display the details for each certificate in turn until you find the one with the correct subject:
runmqckm -cert -list -db key.kdb -pw password
runmqckm -cert -details -db key.kdb -pw password -label certlabel
Since this is a 575010 error, you’ll probably find that the CA certificate is missing so this is the CA certificate you need to add. Follow the steps described in the product documentation Adding a CA certificate (or the public part of a self-signed certificate) into a key repository, on UNIX®, Linux or Windows systems topic to add the missing CA certificate.
However, it’s possible that you might find the CA certificate is already present. In that case, check whether it’s a root CA: generally a root CA certificate has Subject DN and Issuer DN fields set to the same value. If the CA certificate is not a root CA then take the Issuer DN and look for the certificate which has that as its Subject DN: add that certificate if it’s missing. Repeat the process as many times as necessary until you reach a root CA certificate that’s in the key repository.
Important final steps
Finally, once all certificates are in place, remember that MQ caches the key repository in memory so that changes don’t take effect immediately. To clear the cache:
- For a client application, restart the application.
- For a queue manager, issue the REFRESH SECURITY TYPE(SSL) MQSC command. Note that this command will terminate any active SSL/TLS channels, so take care to run it at a suitable time.
People often forget to clear the cached key repository and then wonder why their changes don’t take effect. If you change your key repository in any way, always remember to clear the cached data.
The ability to examine the certificates and clear the cached key repository state are useful for many SSL/TLS connectivity problems. Now you know how to examine the certificates, you can use this technique to fix other AMQ9633 errors using the numeric validation error and the certificate details.
title image (modified) credit: (cc) Some rights reserved by Nemo
[{«Business Unit»:{«code»:»BU053″,»label»:»Cloud & Data Platform»},»Product»:{«code»:»»,»label»:»»},»Component»:»»,»Platform»:[{«code»:»»,»label»:»»}],»Version»:»»,»Edition»:»»,»Line of Business»:{«code»:»»,»label»:»»}}]
MQ TLS uses private and public certificates contained in key repositories. Certificates have labels: a unique identifier representing a digital certificate stored in a key repository that provide a human-readable name with which to refer to a particular certificate. The certificate label is separate from the certificate’s Subject Distinguished Name or Subject Common Name fields. The Subject Distinguished Name and Subject Common Name are fields within the certificate itself. These are defined when the certificate is created and cannot be changed. The label associated with a digital certificate can be changed if needed. On Linux the certificate label can contain up to 64 characters. The certificate label cannot contain spaces. Labels are case sensitive. You can set the certificate label to a value of your choice. If you do not set a value, a default label is used that follows the naming convention ibmwebspheremq
Troubleshooting
Keystore files
In case of errors first check MQ TLS keystores and examine certificates in order to solve communications problems.
Determine the location of the queue manager’s key database by using runmqsc to display the queue manager SSLKEYR attribute.
$ runmqsc SSL1
5724-H72 (C) Copyright IBM Corp. 1994, 2016.
Starting MQSC for queue manager SSL1.
DISPLAY QMGR SSLKEYR
1 : DISPLAY QMGR SSLKEYR
AMQ8408: Display Queue Manager details.
QMNAME(SSL1) SSLKEYR(/var/mqm/qmgrs/SSL1/ssl/key)
One MQSC command read.
No commands have a syntax error.
Make sure that the directories in the key repository path are accessible to IBM MQ. The key repository files should also be accessible to IBM MQ, but secured against unwanted access by other users.
$ ls -ld /var /var/mqm /var/mqm/qmgrs /var/mqm/qmgrs/SSL1 /var/mqm/qmgrs/SSL1/ssl drwxr-xr-x 15 root root 4096 jun 19 22:28 /var drwxrwsr-x 14 mqm mqm 4096 jul 27 11:02 /var/mqm drwxrwsr-x 5 mqm mqm 4096 jul 27 11:02 /var/mqm/qmgrs drwxrwsr-x 22 mqm mqm 4096 jul 29 21:12 /var/mqm/qmgrs/SSL1 drwxrws--- 2 mqm mqm 4096 jul 27 11:02 /var/mqm/qmgrs/SSL1/ssl $ ls -l /var/mqm/qmgrs/SSL1/ssl/ total 16 -rw------- 1 mqm mqm 88 jul 27 11:02 key.crl -rw------- 1 mqm mqm 88 jul 27 11:02 key.kdb -rw------- 1 mqm mqm 88 jul 27 11:02 key.rdb -rw------- 1 mqm mqm 193 jul 27 11:02 key.sth
Key management is doe usingthe runmqakm command which is simmilar to gsk8capicmd
The runmqakm command allows the -stashed option to recall the key repository password from the stash file rather than typing it on the command line.
runmqakm -cert -list -db /var/mqm/qmgrs/SSL1/ssl/key.kdb -fips -stashed Certificates found * default, - personal, ! trusted, # secret key ! ssl2_signer_Cert - ibmwebspheremqssl1
For MQ channel communications to use TLS, there are a couple requirements. TLS requires:
- Ciphers — used to communicate over the wire
- Certificates — used to identify and validate each of the entities communicating.
For an MQ queue manager to do TLS communications, the queue manager MUST have a keystore, and in most cases it also needs a personal certificate. (ie: queue manager personal certificate required if SSL is configured on Receiver or SVRCONN channels, in effect the TLS server side of a connection)
An MQ queue manager uses a CMS type keystore to hold its personal certificate(s), signer certificates and certificate requests. The keystore location and base file name is identified in the queue manager’s SSLKEYR property.
If a Channel has the SSLCIPH property set, then SSL communications is attempted. If there is any issue/error during SSL initialization/negotiation, the channel will fail to start.
Looking up error codes related to TLS
Both sides of the communication MUST be configured for the same cipherspec/ciphersuite.
If an error occurs you can find information in the queue managers error log, this looks like:
30-07-17 10:16:35 - Process(5771.4) User(mqm) Program(amqrmppa)
Host(MQ) Installation(Installation1)
VRMF(9.0.2.0) QMgr(SSL2)
AMQ9999: Channel '????' to host 'localhost (127.0.0.1)' ended abnormally.
EXPLANATION:
The channel program running under process ID 5771 for channel '????' ended
abnormally. The host name is 'localhost (127.0.0.1)'; in some cases the host
name cannot be determined and so is shown as '????'.
ACTION:
Look at previous error messages for the channel program in the error logs to
determine the cause of the failure. Note that this message can be excluded
completely or suppressed by tuning the "ExcludeMessage" or "SuppressMessage"
attributes under the "QMErrorLog" stanza in qm.ini. Further information can be
found in the System Administration Guide.
----- amqrmrsa.c : 938 --------------------------------------------------------
30-07-17 10:17:24 - Process(5771.5) User(mqm) Program(amqrmppa)
Host(MQ) Installation(Installation1)
VRMF(9.0.2.0) QMgr(SSL2)
AMQ9633: Bad SSL certificate for channel '????'.
EXPLANATION:
A certificate encountered during SSL handshaking is regarded as bad for one of
the following reasons:
(a) it was formatted incorrectly and could not be validated
(b) it was formatted correctly but failed validation against the Certification
Authority (CA) root and other certificates held on the local system
(c) it was found in a Certification Revocation List (CRL) on an LDAP server
(d) a CRL was specified but the CRL could not be found on the LDAP server
(e) an OCSP responder has indicated that it is revoked
The channel is '????'; in some cases its name cannot be determined and so is
shown as '????'. The remote host is 'localhost (127.0.0.1)'. The channel did
not start.
The details of the certificate which could not be validated are
'[Class=]GSKVALMethod::X509[Issuer=]CN=SSL1,O=IBM,C=US[#=]334e11a4a012db28[Subject=]CN=SSL1,O=IBM,C=US[Class=]GSKVALMethod::PKIX[Issuer=]CN=SSL1,O=IBM,C=US[#=]334e11a4a012db28[Subject=]CN=SSL1,O=IBM,C=US'.
The certificate validation error was 575010.
ACTION:
Check which of the possible causes applies on your system. Correct the error,
and restart the channel.
This error might indicate that the remote end of the channel is configured to
send the wrong certificate. Check the certificate label configuration at the
remote end of the channel and ensure that the local key repository contains all
of the necessary CA certificates.
----- amqccisa.c : 7812 -------------------------------------------------------
The error: «The certificate validation error was 575051.» gives additional information. Look it up at IBM or in the table in the appendix og the blog.
That tells us «CA certificate is missing Critical Basic Constraints». A bit obfuscating because in this case the certificate is simply missing in the queuemanagers keystore.
MQ tracing is useless to debug TLS
For many problems strmqtrc tracing facility is helpful. Not in debugging TLS however. Trace files for TLS are generated, still names SSL, and but you cannot format any of tese trace files. These trace files are binary files….
Appendix 1: How to create a test setup with 2 local queue managers and a TLS secured channel in between:
crtmqm SSL1
strmqm SSL1
crtmqm SSL2
strmqm SSL2
runmqsc SSL1 <&lEOT
define chl(SSL1_SSL2) chltype(sdr) conname('127.0.0.1(2013)') xmitq(SSL2.QX) SSLCIPH(TLS_RSA_WITH_AES_256_GCM_SHA384)
def ql(SSL2.QX) usage(xmitq)
define qremote(SSL2.QR) rname(Q2) rqmname(SSL2) xmitq (SSL2.QX)
define listener (LIST) trptype(TCP) port (2014) control(qmgr)
define channel (CHAN1) CHLTYPE(SVRCONN)
ALTER QMGR CHLAUTH(DISABLED)
ALTER QMGR CONNAUTH(' ')
REFRESH SECURITY TYPE(CONNAUTH)
END
EOT
runmqsc SSL2 <<EOT
define listener (SSL2.LSR) trptype(TCP) port (2013) control(qmgr)
start listener(SSL2.LSR)
display lsstatus(SSL2.LSR)
define channel(SSL1_SSL2) chltype(rcvr) sslcauth(REQUIRED)
def qlocal(Q2)
define channel (CHAN1) CHLTYPE(SVRCONN)
ALTER QMGR CHLAUTH(DISABLED)
ALTER QMGR CONNAUTH(' ')
REFRESH SECURITY TYPE(CONNAUTH)
END
EOT
runmqsc SSL1 <<EOT
start chl(SSL1_SSL2)
dis chs(SSL1_SSL2)
stop channel (SSL1_SSL2) STATUS(INACTIVE)
END
EOT
runmqakm -keydb -create -db /var/mqm/qmgrs/SSL1/ssl/key.kdb -type cms -pw passw0rd -stash
runmqakm -keydb -create -db /var/mqm/qmgrs/SSL2/ssl/key.kdb -type cms -pw passw0rd -stash
runmqsc SSL1 <<EOT
display qmgr SSLKEYR
END
EOT
runmqsc SSL2 <<EOT
display qmgr SSLKEYR
END
EOT
runmqakm -cert -create -db /var/mqm/qmgrs/SSL1/ssl/key.kdb -pw passw0rd -label ibmwebspheremqssl1 -dn "CN=SSL1,O=IBM,C=US" -size 2048
runmqakm -cert -create -db /var/mqm/qmgrs/SSL2/ssl/key.kdb -pw passw0rd -label ibmwebspheremqssl2 -dn "CN=SSL2,O=IBM,C=US" -size 2048
runmqakm -cert -extract -db /var/mqm/qmgrs/SSL1/ssl/key.kdb -pw passw0rd -label ibmwebspheremqssl1 -target /var/mqm/qmgrs/SSL1/ssl/ssl1.arm
runmqakm -cert -extract -db /var/mqm/qmgrs/SSL2/ssl/key.kdb -pw passw0rd -label ibmwebspheremqssl2 -target /var/mqm/qmgrs/SSL2/ssl/ssl2.arm
runmqakm -cert -add -db /var/mqm/qmgrs/SSL1/ssl/key.kdb -pw passw0rd -label ssl2_signer_Cert -file /var/mqm/qmgrs/SSL2/ssl/ssl2.arm
runmqakm -cert -add -db /var/mqm/qmgrs/SSL2/ssl/key.kdb -pw passw0rd -label ssl1_signer_Cert -file /var/mqm/qmgrs/SSL1/ssl/ssl1.arm
runmqsc SSL2 <<EOT
alter chl(SSL1_SSL2) chltype(rcvr) sslciph(TLS_RSA_WITH_AES_128_CBC_SHA)
REFRESH SECURITY TYPE (SSL)
END
EOT
runmqsc SSL1 <<EOT
alter chl(SSL1_SSL2) chltype(sdr) sslciph(TLS_RSA_WITH_AES_128_CBC_SHA)
REFRESH SECURITY TYPE (SSL)
END
EOT
runmqsc SSL1 <<EOT
start chl(SSL1_SSL2)
dis chs(SSL1_SSL2)
END
EOT
Appendix 2: Certificate error codes
| 1 | Handle is not valid. |
| 3 | An internal error has occurred. |
| 4 | Insufficient storage is available |
| 5 | Handle is in the incorrect state. |
| 6 | Key label is not found. |
| 7 | No certificates available. |
| 8 | Certificate validation error. |
| 9 | Cryptographic processing error. |
| 10 | ASN processing error. |
| 11 | LDAP processing error. |
| 12 | An unexpected error has occurred. |
| 102 | Error detected while reading key database or SAF key ring. |
| 103 | Incorrect key database record format. |
| 106 | Incorrect key database password. |
| 109 | No certificate authority certificates. |
| 201 | No key database password supplied. |
| 202 | Error detected while opening the key database. |
| 203 | Unable to generate temporary key pair |
| 204 | Key database password is expired. |
| 302 | Connection is active. |
| 401 | Certificate is expired or is not valid yet. |
| 402 | No SSL cipher specifications. |
| 403 | No certificate received from partner. |
| 405 | Certificate format is not supported. |
| 406 | Error while reading or writing data. |
| 407 | Key label does not exist. |
| 408 | Key database password is not correct. |
| 410 | SSL message format is incorrect. |
| 411 | Message authentication code is incorrect. |
| 412 | SSL protocol or certificate type is not supported. |
| 413 | Certificate signature is incorrect. |
| 414 | Certificate is not valid. |
| 415 | SSL protocol violation. |
| 416 | Permission denied. |
| 417 | Self-signed certificate cannot be validated. |
| 420 | Socket closed by remote partner. |
| 421 | SSL V2 cipher is not valid. |
| 422 | SSL V3 cipher is not valid. |
| 427 | LDAP is not available. |
| 428 | Key entry does not contain a private key. |
| 429 | SSL V2 header is not valid. |
| 431 | Certificate is revoked. |
| 432 | Session renegotiation is not allowed. |
| 433 | Key exceeds allowable export size. |
| 434 | Certificate key is not compatible with cipher suite. |
| 435 | Certificate authority is unknown. |
| 436 | Certificate revocation list cannot be processed. |
| 437 | Connection closed. |
| 438 | Internal error reported by remote partner. |
| 439 | Unknown alert received from remote partner. |
| 501 | Buffer size is not valid. |
| 502 | Socket request would block. |
| 503 | Socket read request would block. |
| 504 | Socket write request would block. |
| 505 | Record overflow. |
| 601 | Protocol is not SSL V3 or TLS V1. |
| 602 | Function identifier is not valid. |
| 701 | Attribute identifier is not valid. |
| 702 | The attribute has a negative length, which is invalid. |
| 703 | The enumeration value is invalid for the specified enumeration type. |
| 704 | Invalid parameter list for replacing the SID cache routines. |
| 705 | The value is not a valid number. |
| 706 | Conflicting parameters were set for additional certificate validation |
| 707 | The AES cryptographic algorithm is not supported. |
| 708 | The PEERID does not have the correct length. |
| 1501 | GSK_SC_OK |
| 1502 | GSK_SC_CANCEL |
| 1601 | The trace started successfully. |
| 1602 | The trace stopped successfully. |
| 1603 | No trace file was previously started so it cannot be stopped. |
| 1604 | Trace file already started so it cannot be started again. |
| 1605 | Trace file cannot be opened. The first parameter of gsk_start_trace() must be a valid full path filename. |
| 575001 | Internal error |
| 575002 | ASN error due to a malformed certificate |
| 575003 | Cryptographic error |
| 575004 | Key database error |
| 575005 | Directory error |
| 575006 | Invalid implementation library |
| 575008 | No appropriate validator |
| 575009 | The root CA is not trusted |
| 575010 | No certificate chain was built |
| 575011 | Digital signature algorithm mismatch |
| 575012 | Digital signature mismatch |
| 575013 | X.509 version does not allow Key IDs |
| 575014 | X.509 version does not allow extensions |
| 575015 | Unknown X.509 certificate version |
| 575016 | The certificate validity range is invalid |
| 575017 | The certificate is not yet valid |
| 575018 | The certificate has expired |
| 575019 | The certificate contains unknown critical extensions |
| 575020 | The certificate contains duplicate extensions |
| 575021 | The issuers directory name does not match the issuer’s issuer |
| 575022 | The Authority Key ID serial number value does not match the serial number of the issuer |
| 575023 | The Authority Key ID and Subject Key ID do not match |
| 575024 | Unrecognized issuer alternative name |
| 575025 | The certificate Basic Constraints forbid use as a CA |
| 575026 | The certificate has a non-zero Basic Constraints path length but is not a CA |
| 575027 | The certificate Basic Constraints maximum path length was exceeded |
| 575028 | The certificate is not permitted to sign other certificates |
| 575029 | The certificate is not signed by a CA |
| 575030 | Unrecognized Subject Alternative Name |
| 575031 | The certificate chain is invalid |
| 575032 | The certificate is revoked |
| 575033 | Unrecognized CRL distribution point |
| 575034 | Name chaining failed |
| 575035 | Certificate is not in a chain |
| 575036 | The CRL is not yet valid |
| 575037 | The CRL has expired |
| 575038 | The certificate version does not allow critical extensions |
| 575039 | Unknown CRL distribution points |
| 575040 | No CRLs for CRL distribution points |
| 575041 | Indirect CRLs are not supported |
| 575042 | Missing issuing CRL distribution point name |
| 575043 | Distribution points do not match |
| 575044 | No available CRL data source |
| 575045 | CA Subject name is null |
| 575046 | Distinguished names do not chain |
| 575047 | Missing Subject Alternative Name |
| 575048 | Unique ID mismatch |
| 575049 | Name not permitted |
| 575050 | Name excluded |
| 575051 | CA certificate is missing Critical Basic Constraints |
| 575052 | Name constraints are not critical |
| 575053 | Name constraints minimum subtree value if set is not zero |
| 575054 | Name constraints maximum subtree value if set is not allowed |
| 575055 | Unsupported name constraint |
| 575056 | Empty policy constraints |
| 575057 | Bad certificate policies |
| 575058 | Certificate policies not acceptable |
| 575059 | Bad acceptable certificate policies |
| 575060 | Certificate policy mappings are critical |
| 575061 | Revocation status could not be determined |
| 575062 | Extended key usage error |
| 575063 | Unknown OCSP version |
| 575064 | Unknown OCSP response |
| 575065 | Bad OCSP key usage extension |
| 575066 | Bad OCSP nonce |
| 575067 | Missing OCSP nonce |
| 575068 | No OCSP client available |
Appendix 3: Links
- IBM MQ 8.0 TLS error codes
- Diagnostic improvements in MQ TLS
- Troubleshooting channels by IBM (antiquated)
- gsk8capicmd reference
- Overview of TLS handshake (MQ 7)
- Redbook on IBM MQ V8 Enhancements
- TLS (MQ 9)
- MQ TLS Demistified
- Managing certificates with gskit
- TLS explained
Appendix 4: running TCP Dump
Running TCP Dump on the Listener Port of the receiver channel at least shows there is connectivity.
In our example «tcpdump -i lo port 2013 -X» results in:
11:03:46.482390 IP localhost.41832 > localhost.2013: Flags [S], seq 3824546413, win 43690, options [mss 65495,sackOK,TS val 188398717 ecr 0,nop,wscale 7], length 0
0x0000: 4500 003c 30cf 4000 4006 0beb 7f00 0001 E..<0.@.@.......
0x0010: 7f00 0001 a368 07dd e3f5 f26d 0000 0000 .....h.....m....
0x0020: a002 aaaa fe30 0000 0204 ffd7 0402 080a .....0..........
0x0030: 0b3a bc7d 0000 0000 0103 0307 .:.}........
11:03:46.482400 IP localhost.2013 > localhost.41832: Flags [S.], seq 1532232513, ack 3824546414, win 43690, options [mss 65495,sackOK,TS val 188398717 ecr 188398717,nop,wscale 7], length 0
0x0000: 4500 003c 0000 4000 4006 3cba 7f00 0001 E..<..@.@.<.....
0x0010: 7f00 0001 07dd a368 5b54 0341 e3f5 f26e .......h[T.A...n
0x0020: a012 aaaa fe30 0000 0204 ffd7 0402 080a .....0..........
0x0030: 0b3a bc7d 0b3a bc7d 0103 0307 .:.}.:.}....
11:03:46.482408 IP localhost.41832 > localhost.2013: Flags [.], ack 1, win 342, options [nop,nop,TS val 188398717 ecr 188398717], length 0
0x0000: 4500 0034 30d0 4000 4006 0bf2 7f00 0001 E..40.@.@.......
0x0010: 7f00 0001 a368 07dd e3f5 f26e 5b54 0342 .....h.....n[T.B
0x0020: 8010 0156 fe28 0000 0101 080a 0b3a bc7d ...V.(.......:.}
0x0030: 0b3a bc7d .:.}
11:03:46.483321 IP localhost.41832 > localhost.2013: Flags [P.], seq 1:90, ack 1, win 342, options [nop,nop,TS val 188398717 ecr 188398717], length 89
0x0000: 4500 008d 30d1 4000 4006 0b98 7f00 0001 E...0.@.@.......
0x0010: 7f00 0001 a368 07dd e3f5 f26e 5b54 0342 .....h.....n[T.B
0x0020: 8018 0156 fe81 0000 0101 080a 0b3a bc7d ...V.........:.}
0x0030: 0b3a bc7d 1603 0100 5401 0000 5003 01f2 .:.}....T...P...
0x0040: a07d 596e f4f5 3cf5 ae22 4b03 c935 8bad .}Yn..<.."K..5..
0x0050: 6261 c745 8230 22b7 a2b1 28fc f2b1 7e00 ba.E.0"...(...~.
0x0060: 0004 00ff 002f 0100 0023 0000 001f 001d ...../...#......
0x0070: 0000 1a73 736c 3135 662d 7373 6c32 2e63 ...ssl15f-ssl2.c
0x0080: 686c 2e6d 712e 6962 6d2e 636f 6d hl.mq.ibm.com
11:03:46.483330 IP localhost.2013 > localhost.41832: Flags [.], ack 90, win 342, options [nop,nop,TS val 188398717 ecr 188398717], length 0
0x0000: 4500 0034 c1e0 4000 4006 7ae1 7f00 0001 E..4..@.@.z.....
0x0010: 7f00 0001 07dd a368 5b54 0342 e3f5 f2c7 .......h[T.B....
0x0020: 8010 0156 fe28 0000 0101 080a 0b3a bc7d ...V.(.......:.}
0x0030: 0b3a bc7d .:.}
11:03:46.484657 IP localhost.2013 > localhost.41832: Flags [P.], seq 1:951, ack 90, win 342, options [nop,nop,TS val 188398718 ecr 188398717], length 950
0x0000: 4500 03ea c1e1 4000 4006 772a 7f00 0001 E.....@.@.w*....
0x0010: 7f00 0001 07dd a368 5b54 0342 e3f5 f2c7 .......h[T.B....
0x0020: 8018 0156 01df 0000 0101 080a 0b3a bc7e ...V.........:.~
0x0030: 0b3a bc7d 1603 0103 b102 0000 4d03 0100 .:.}........M...
0x0040: 0000 f201 009d 61cf ad2e a43a ab21 6ce1 ......a....:.!l.
0x0050: 8eec 26a3 d2d9 9984 ffaf ec1a ab72 8020 ..&..........r..
0x0060: 6f0e 5ed6 c0d6 b5e6 adb6 6330 a6f7 1daa o.^.......c0....
0x0070: d7fc b1b9 bcbd b120 9bcd 9f8f 1d5a 99d4 .............Z..
0x0080: 002f 0000 05ff 0100 0100 0b00 0322 0003 ./..........."..
0x0090: 1f00 031c 3082 0318 3082 0200 a003 0201 ....0...0.......
0x00a0: 0202 0851 0fc2 90c1 8e5f c930 0d06 092a ...Q....._.0...*
0x00b0: 8648 86f7 0d01 0105 0500 302a 310b 3009 .H........0*1.0.
0x00c0: 0603 5504 0613 0255 5331 0c30 0a06 0355 ..U....US1.0...U
0x00d0: 040a 1303 4942 4d31 0d30 0b06 0355 0403 ....IBM1.0...U..
0x00e0: 1304 5353 4c32 301e 170d 3137 3037 3239 ..SSL20...170729
0x00f0: 3038 3136 3334 5a17 0d31 3830 3733 3030 081634Z..1807300
0x0100: 3831 3633 345a 302a 310b 3009 0603 5504 81634Z0*1.0...U.
0x0110: 0613 0255 5331 0c30 0a06 0355 040a 1303 ...US1.0...U....
0x0120: 4942 4d31 0d30 0b06 0355 0403 1304 5353 IBM1.0...U....SS
0x0130: 4c32 3082 0122 300d 0609 2a86 4886 f70d L20.."0...*.H...
0x0140: 0101 0105 0003 8201 0f00 3082 010a 0282 ..........0.....
0x0150: 0101 00c5 4528 0ba8 2fc8 c8b7 8f00 aafe ....E(../.......
0x0160: 9bc4 fcea 039d eab2 d8c6 62b5 391d 96a0 ..........b.9...
0x0170: 1438 3986 dbe4 6b61 12e0 b2c7 1960 6a04 .89...ka.....`j.
0x0180: 8698 8378 9129 24f0 9e6b 5e43 001f 1d01 ...x.)$..k^C....
0x0190: 0f9a a522 39d9 e7df 0963 2340 3cf5 498e ..."9....c#@<.I.
0x01a0: 496d d10a 2395 efbe b249 e662 e23e c057 Im..#....I.b.>.W
0x01b0: 4250 199b 8a52 b263 4182 44ed cbc0 fa63 BP...R.cA.D....c
0x01c0: d06c 3143 fb7a 8886 6fed 80f2 970b 16be .l1C.z..o.......
0x01d0: 8d2f 6dec f00f b29f 76a1 1874 db89 cb7e ./m.....v..t...~
0x01e0: 7ecf 58fd 631b a66b 93a1 fe8d 48c5 de65 ~.X.c..k....H..e
0x01f0: 6fd5 140a c082 b980 0d3a 10bc 127d 3edb o........:...}>.
0x0200: 592e 69cb 4e41 6128 b8b8 561f e06f 22ed Y.i.NAa(..V..o".
0x0210: 7248 83d9 9068 e38d 6ff3 322b 4fa3 f62e rH...h..o.2+O...
0x0220: f010 2534 0e24 f9fd 04bb 3350 56a9 e41b ..%4.$....3PV...
0x0230: d080 f60c d2c3 a490 b578 07a7 5fb5 6b45 .........x.._.kE
0x0240: 397a c9c0 da0b 38cc a37c db56 c7d6 cfbf 9z....8..|.V....
0x0250: ef9f 9102 0301 0001 a342 3040 301d 0603 .........B0@0...
0x0260: 551d 0e04 1604 144f 51af f301 3599 8535 U......OQ...5..5
0x0270: 895a 98da e048 9907 a9fa 7a30 1f06 0355 .Z...H....z0...U
0x0280: 1d23 0418 3016 8014 4f51 aff3 0135 9985 .#..0...OQ...5..
0x0290: 3589 5a98 dae0 4899 07a9 fa7a 300d 0609 5.Z...H....z0...
0x02a0: 2a86 4886 f70d 0101 0505 0003 8201 0100 *.H.............
0x02b0: 844f c6ed 6a3c f3e3 24c9 8cf4 c321 0c4a .O..j<..$....!.J
0x02c0: fe03 df57 7450 fe29 29e5 0626 0900 1253 ...WtP.))..&...S
0x02d0: 6396 a7ed 53cc c8d1 c72f 06f3 86e1 31db c...S..../....1.
0x02e0: 41c9 3f04 6d01 8432 8c32 5450 79b3 3b53 A.?.m..2.2TPy.;S
0x02f0: 32dd fa02 2f11 a30c e052 93bd 7c09 324e 2.../....R..|.2N
0x0300: 1942 e72f 948f c803 898c 289f aaae ee35 .B./......(....5
0x0310: 8f33 6d66 d9cd 09e0 3b59 914c f52e 0282 .3mf....;Y.L....
0x0320: 4cab ed1c 6c90 3a55 36c4 b6b4 8dd6 0c3a L...l.:U6......:
0x0330: 3ef4 f20e 15f4 1501 9b96 ccd8 10f2 0ea4 >...............
0x0340: 706c 46e2 2319 eaa7 dea7 9e9e 643a 852a plF.#.......d:.*
0x0350: 4938 e206 50ad d89e 53ba 4e1f 4c31 1896 I8..P...S.N.L1..
0x0360: 138c dd83 2df6 1a93 289d 580d 235a 6572 ....-...(.X.#Zer
0x0370: c932 409f e428 53be 09ff e97f b668 d3e2 .2@..(S......h..
0x0380: 0b80 7bbd 982d dc31 f77c e934 f5a1 f7d0 ..{..-.1.|.4....
0x0390: c43d c6d3 186d 11fa db53 7f32 f315 68e8 .=...m...S.2..h.
0x03a0: f3f3 8e3a 2e5b 59db 27a9 0654 22e4 b0cf ...:.[Y.'..T"...
0x03b0: 0d00 0032 0101 002e 002c 302a 310b 3009 ...2.....,0*1.0.
0x03c0: 0603 5504 0613 0255 5331 0c30 0a06 0355 ..U....US1.0...U
0x03d0: 040a 1303 4942 4d31 0d30 0b06 0355 0403 ....IBM1.0...U..
0x03e0: 1304 5353 4c32 0e00 0000 ..SSL2....
11:03:46.484899 IP localhost.41832 > localhost.2013: Flags [.], ack 951, win 357, options [nop,nop,TS val 188398718 ecr 188398718], length 0
0x0000: 4500 0034 30d2 4000 4006 0bf0 7f00 0001 E..40.@.@.......
0x0010: 7f00 0001 a368 07dd e3f5 f2c7 5b54 06f8 .....h......[T..
0x0020: 8010 0165 fe28 0000 0101 080a 0b3a bc7e ...e.(.......:.~
0x0030: 0b3a bc7e .:.~
11:03:46.487947 IP localhost.41832 > localhost.2013: Flags [P.], seq 90:1425, ack 951, win 357, options [nop,nop,TS val 188398719 ecr 188398718], length 1335
0x0000: 4500 056b 30d3 4000 4006 06b8 7f00 0001 E..k0.@.@.......
0x0010: 7f00 0001 a368 07dd e3f5 f2c7 5b54 06f8 .....h......[T..
0x0020: 8018 0165 0360 0000 0101 080a 0b3a bc7f ...e.`.......:..
0x0030: 0b3a bc7e 1603 0105 320b 0003 2200 031f .:.~....2..."...
0x0040: 0003 1c30 8203 1830 8202 00a0 0302 0102 ...0...0........
0x0050: 0208 334e 11a4 a012 db28 300d 0609 2a86 ..3N.....(0...*.
0x0060: 4886 f70d 0101 0505 0030 2a31 0b30 0906 H........0*1.0..
0x0070: 0355 0406 1302 5553 310c 300a 0603 5504 .U....US1.0...U.
0x0080: 0a13 0349 424d 310d 300b 0603 5504 0313 ...IBM1.0...U...
0x0090: 0453 534c 3130 1e17 0d31 3730 3732 3930 .SSL10...1707290
0x00a0: 3831 3633 335a 170d 3138 3037 3330 3038 81633Z..18073008
0x00b0: 3136 3333 5a30 2a31 0b30 0906 0355 0406 1633Z0*1.0...U..
0x00c0: 1302 5553 310c 300a 0603 5504 0a13 0349 ..US1.0...U....I
0x00d0: 424d 310d 300b 0603 5504 0313 0453 534c BM1.0...U....SSL
0x00e0: 3130 8201 2230 0d06 092a 8648 86f7 0d01 10.."0...*.H....
0x00f0: 0101 0500 0382 010f 0030 8201 0a02 8201 .........0......
0x0100: 0100 9c3a 3aa5 9b3a 0872 e754 e665 ad2f ...::..:.r.T.e./
0x0110: a21c 30c9 24e5 5cba 6264 e1fe e5af a622 ..0.$..bd....."
0x0120: 2f46 459b 8f73 5ae3 55a5 9581 c3ae 4134 /FE..sZ.U.....A4
0x0130: d780 278a a469 88c8 761b a385 0133 09f7 ..'..i..v....3..
0x0140: b0c8 e127 471d 3f1f 832b f2eb a75a d4ce ...'G.?..+...Z..
0x0150: 3f60 066f 53a3 bf28 867f 3677 601f 1f6e ?`.oS..(..6w`..n
0x0160: ae73 58c4 24e7 9be5 f9ff 7a8c 7365 77fa .sX.$.....z.sew.
0x0170: c917 ce53 5fca b097 8422 5ba0 9d67 be9e ...S_...."[..g..
0x0180: 19e3 b646 97c3 3628 0faf 86bc d1b4 90c0 ...F..6(........
0x0190: 8755 45de d89d bdf9 d6b0 5b3c df1a 317c .UE.......[<..1|
0x01a0: f62a 1a55 61c2 0e6e 1ae8 51b6 69f1 6f74 .*.Ua..n..Q.i.ot
0x01b0: c718 866b b4f6 6ffd 0d6c 60f6 724b bc99 ...k..o..l`.rK..
0x01c0: 695b 7c51 4ebe 2f21 1da9 041b 2e43 229a i[|QN./!.....C".
0x01d0: 771b 3cc0 8703 b5b5 eb72 dd7e 9c46 240f w.<......r.~.F$.
0x01e0: 439a aa47 7f32 9b38 1683 f4e0 42f7 668a C..G.2.8....B.f.
0x01f0: ee32 ae9e a033 dce6 8459 1d5d 9bd1 48a5 .2...3...Y.]..H.
0x0200: 4585 0203 0100 01a3 4230 4030 1d06 0355 E.......B0@0...U
0x0210: 1d0e 0416 0414 ad74 f83e e11a a48a 842c .......t.>.....,
0x0220: abbb 74fa 0d3e 6fe6 3154 301f 0603 551d ..t..>o.1T0...U.
0x0230: 2304 1830 1680 14ad 74f8 3ee1 1aa4 8a84 #..0....t.>.....
0x0240: 2cab bb74 fa0d 3e6f e631 5430 0d06 092a ,..t..>o.1T0...*
0x0250: 8648 86f7 0d01 0105 0500 0382 0101 006e .H.............n
0x0260: 8dca a0e9 5605 be95 73ad 9e5c 16d0 8b88 ....V...s......
0x0270: 0ec5 8d8e 35d5 0f93 b415 fb46 364e 51e7 ....5......F6NQ.
0x0280: a5ee b8ce 92ed 7cbe 7708 d95a 6668 57b1 ......|.w..ZfhW.
0x0290: 10cb e4ad e1f2 a0e5 d99f cc7a f36d 3cc3 ...........z.m<.
0x02a0: 8293 747f ea90 d24d fcc9 8738 a694 a8f4 ..t....M...8....
0x02b0: 9f02 4f1a 31ec 645d 1fee 1731 e7d0 5223 ..O.1.d]...1..R#
0x02c0: b7c7 58a3 6a16 9a07 5917 6aa6 49ef 3f4c ..X.j...Y.j.I.?L
0x02d0: fa37 20db a510 93de 5200 5084 3a5d 5a17 .7......R.P.:]Z.
0x02e0: 80f8 14fd cb3f 8f32 cd35 ecd6 592a e057 .....?.2.5..Y*.W
0x02f0: 5213 07d7 51e4 a023 4835 c605 2b17 ef56 R...Q..#H5..+..V
0x0300: 5276 87a3 7db4 1b83 af5d 8a3a 914c d078 Rv..}....].:.L.x
0x0310: a63a e74e d677 7e6a 07ca fded 4b09 c665 .:.N.w~j....K..e
0x0320: 93ce c760 d49d b3f1 4992 7cd2 bf44 442b ...`....I.|..DD+
0x0330: a39c a1a3 978e 70aa 9c7b 92ac 003e 02c2 ......p..{...>..
0x0340: 4cd8 59a7 d183 5d50 5b46 ecef 05e4 ce9f L.Y...]P[F......
0x0350: ce12 89a6 7d36 a88e 68e8 02e3 11e5 0d10 ....}6..h.......
0x0360: 0001 0201 00c0 2f4d b3c9 cf9f 8a80 2611 ....../M......&.
0x0370: acff 0a3d d098 cf0f 72e1 5501 b46a bb16 ...=....r.U..j..
0x0380: 5576 805a 7034 c245 caa1 230f 3eaa 5be2 Uv.Zp4.E..#.>.[.
0x0390: cf03 6e6f 2d7a 2fb2 bf7a ede7 0e49 5408 ..no-z/..z...IT.
0x03a0: 1e23 2a2f 5b25 70a9 ef9d e1b9 e760 3762 .#*/[%p......`7b
0x03b0: 4e46 26c2 c267 ea9d 2fee f6ab f5bf a0ea NF&..g../.......
0x03c0: 21f8 0b43 9ab3 3375 e973 bcb3 0462 0f24 !..C..3u.s...b.$
0x03d0: b7cb 0a12 7996 b463 7fb2 de24 362d 7fd6 ....y..c...$6-..
0x03e0: b8ec 05f1 d778 d88a 5fdc 44a5 8457 21b9 .....x.._.D..W!.
0x03f0: 7b79 55ab 57fb e872 2f20 7d21 7938 612c {yU.W..r/.}!y8a,
0x0400: 7687 18ea a73e cd18 14ae 37ef 593b 0d8c v....>....7.Y;..
0x0410: 66a6 da48 ed58 6e77 72b7 5247 bcd9 dd54 f..H.Xnwr.RG...T
0x0420: 2b53 7c73 21eb 4871 807b 8015 35d4 3593 +S|s!.Hq.{..5.5.
0x0430: 2f0f d788 afba e97e 8938 21d2 77a7 d123 /......~.8!.w..#
0x0440: 8b0b b03a d460 4e36 c713 421f a784 76c4 ...:.`N6..B...v.
0x0450: c8c5 f97a fa51 0ea6 eecc 2ec5 44f2 7052 ...z.Q......D.pR
0x0460: 93cb 2035 760f 0001 0201 000f 7fc3 4d94 ...5v.........M.
0x0470: 9651 be4f a864 d381 9668 1858 92c5 78f1 .Q.O.d...h.X..x.
0x0480: dbb8 30f9 5c3a a369 4210 c2e7 09b1 c94a ..0.:.iB......J
0x0490: e6a6 3cef cd2a b534 4365 6a68 2d45 0a9a ..<..*.4Cejh-E..
0x04a0: c07b c7f6 5d5b d03a 43be 57db 722e b256 .{..][.:C.W.r..V
0x04b0: d277 bb8d 5917 76b7 a4a5 8643 eafd 1024 .w..Y.v....C...$
0x04c0: 8dfb 2df5 24a9 24b5 790a 7031 e2d4 074f ..-.$.$.y.p1...O
0x04d0: 0008 f209 020a aedd ecb1 cad7 a062 09d1 .............b..
0x04e0: 3260 0732 57c6 5601 3b06 71fc a2e6 0969 2`.2W.V.;.q....i
0x04f0: 8c8c 1f03 b8ae cf88 a9d9 ddfd de0b e32f .............../
0x0500: a3cc f184 6cc3 22eb 063f ba30 a715 fc09 ....l."..?.0....
0x0510: 452e f187 b1e1 1e20 56ab e8a1 6a2e 6feb E.......V...j.o.
0x0520: 64a4 6a82 f331 6e16 355f 6a15 2225 5390 d.j..1n.5_j."%S.
0x0530: 0f03 dd6c 85cc 054b 94c1 2433 0c58 5e53 ...l...K..$3.X^S
0x0540: 7b82 4fa4 7ec1 c8c1 f7fc 6034 7377 905a {.O.~.....`4sw.Z
0x0550: 88a8 7bd3 d179 a8e7 71a6 8b08 7c47 e16c ..{..y..q...|G.l
0x0560: 58b9 db26 569e 366a 6df1 56 X..&V.6jm.V
11:03:46.488211 IP localhost.2013 > localhost.41832: Flags [.], ack 1425, win 1365, options [nop,nop,TS val 188398719 ecr 188398719], length 0
0x0000: 4500 0034 c1e2 4000 4006 7adf 7f00 0001 E..4..@.@.z.....
0x0010: 7f00 0001 07dd a368 5b54 06f8 e3f5 f7fe .......h[T......
0x0020: 8010 0555 fe28 0000 0101 080a 0b3a bc7f ...U.(.......:..
0x0030: 0b3a bc7f .:..
11:03:46.489234 IP localhost.2013 > localhost.41832: Flags [P.], seq 951:958, ack 1425, win 1365, options [nop,nop,TS val 188398719 ecr 188398719], length 7
0x0000: 4500 003b c1e3 4000 4006 7ad7 7f00 0001 E..;..@.@.z.....
0x0010: 7f00 0001 07dd a368 5b54 06f8 e3f5 f7fe .......h[T......
0x0020: 8018 0555 fe2f 0000 0101 080a 0b3a bc7f ...U./.......:..
0x0030: 0b3a bc7f 1503 0100 0202 2a .:........*
11:03:46.489704 IP localhost.2013 > localhost.41832: Flags [F.], seq 958, ack 1425, win 1365, options [nop,nop,TS val 188398719 ecr 188398719], length 0
0x0000: 4500 0034 c1e4 4000 4006 7add 7f00 0001 E..4..@.@.z.....
0x0010: 7f00 0001 07dd a368 5b54 06ff e3f5 f7fe .......h[T......
0x0020: 8011 0555 fe28 0000 0101 080a 0b3a bc7f ...U.(.......:..
0x0030: 0b3a bc7f .:..
11:03:46.490692 IP localhost.41832 > localhost.2013: Flags [P.], seq 1425:1431, ack 959, win 357, options [nop,nop,TS val 188398719 ecr 188398719], length 6
0x0000: 4500 003a 30d4 4000 4006 0be8 7f00 0001 E..:0.@.@.......
0x0010: 7f00 0001 a368 07dd e3f5 f7fe 5b54 0700 .....h......[T..
0x0020: 8018 0165 fe2e 0000 0101 080a 0b3a bc7f ...e.........:..
0x0030: 0b3a bc7f 1403 0100 0101 .:........
11:03:46.490712 IP localhost.2013 > localhost.41832: Flags [R], seq 1532233472, win 0, length 0
0x0000: 4500 0028 a829 4000 4006 94a4 7f00 0001 E..(.)@.@.......
0x0010: 7f00 0001 07dd a368 5b54 0700 0000 0000 .......h[T......
0x0020: 5004 0000 a444 0000 P....D..
11:03:46.837933 IP localhost.41834 > localhost.2013: Flags [S], seq 1964284478, win 43690, options [mss 65495,sackOK,TS val 188398806 ecr 0,nop,wscale 7], length 0
0x0000: 4500 003c 58c5 4000 4006 e3f4 7f00 0001 E......
0x0020: a002 aaaa fe30 0000 0204 ffd7 0402 080a .....0..........
0x0030: 0b3a bcd6 0000 0000 0103 0307 .:..........
11:03:46.837943 IP localhost.2013 > localhost.41834: Flags [S.], seq 2336824420, ack 1964284479, win 43690, options [mss 65495,sackOK,TS val 188398806 ecr 188398806,nop,wscale 7], length 0
0x0000: 4500 003c 0000 4000 4006 3cba 7f00 0001 E..<..@.@.<.....
0x0010: 7f00 0001 07dd a36a 8b49 1c64 7514 9a3f .......j.I.du..?
0x0020: a012 aaaa fe30 0000 0204 ffd7 0402 080a .....0..........
0x0030: 0b3a bcd6 0b3a bcd6 0103 0307 .:...:......
11:03:46.837952 IP localhost.41834 > localhost.2013: Flags [.], ack 1, win 342, options [nop,nop,TS val 188398806 ecr 188398806], length 0
0x0000: 4500 0034 58c6 4000 4006 e3fb 7f00 0001 E..4X.@.@.......
0x0010: 7f00 0001 a36a 07dd 7514 9a3f 8b49 1c65 .....j..u..?.I.e
0x0020: 8010 0156 fe28 0000 0101 080a 0b3a bcd6 ...V.(.......:..
0x0030: 0b3a bcd6 .:..
11:03:46.840044 IP localhost.41834 > localhost.2013: Flags [P.], seq 1:90, ack 1, win 342, options [nop,nop,TS val 188398807 ecr 188398806], length 89
0x0000: 4500 008d 58c7 4000 4006 e3a1 7f00 0001 E...X.@.@.......
0x0010: 7f00 0001 a36a 07dd 7514 9a3f 8b49 1c65 .....j..u..?.I.e
0x0020: 8018 0156 fe81 0000 0101 080a 0b3a bcd7 ...V.........:..
0x0030: 0b3a bcd6 1603 0100 5401 0000 5003 01f2 .:......T...P...
0x0040: a07d 5981 4b2e 4b1d 1d07 b365 81a2 8d0f .}Y.K.K....e....
0x0050: 86cb 95d4 b172 fd4a e380 d33c beb3 2300 .....r.J...<..#.
0x0060: 0004 00ff 002f 0100 0023 0000 001f 001d ...../...#......
0x0070: 0000 1a73 736c 3135 662d 7373 6c32 2e63 ...ssl15f-ssl2.c
0x0080: 686c 2e6d 712e 6962 6d2e 636f 6d hl.mq.ibm.com
11:03:46.840055 IP localhost.2013 > localhost.41834: Flags [.], ack 90, win 342, options [nop,nop,TS val 188398807 ecr 188398807], length 0
0x0000: 4500 0034 de9e 4000 4006 5e23 7f00 0001 E..4..@.@.^#....
0x0010: 7f00 0001 07dd a36a 8b49 1c65 7514 9a98 .......j.I.eu...
0x0020: 8010 0156 fe28 0000 0101 080a 0b3a bcd7 ...V.(.......:..
0x0030: 0b3a bcd7 .:..
11:03:46.841440 IP localhost.2013 > localhost.41834: Flags [P.], seq 1:951, ack 90, win 342, options [nop,nop,TS val 188398807 ecr 188398807], length 950
0x0000: 4500 03ea de9f 4000 4006 5a6c 7f00 0001 E.....@.@.Zl....
0x0010: 7f00 0001 07dd a36a 8b49 1c65 7514 9a98 .......j.I.eu...
0x0020: 8018 0156 01df 0000 0101 080a 0b3a bcd7 ...V.........:..
0x0030: 0b3a bcd7 1603 0103 b102 0000 4d03 0100 .:..........M...
0x0040: 0000 f26f a3eb 0f31 4a7f 4443 ee29 65db ...o...1J.DC.)e.
0x0050: 27ec 5766 9738 5b67 f366 3607 8b4b b220 '.Wf.8[g.f6..K..
0x0060: 5e8b 894b 7f9e 5aa1 0157 7743 42ee a5e8 ^..K..Z..WwCB...
0x0070: 10bf fd15 6b77 0652 c010 cc80 421b f160 ....kw.R....B..`
0x0080: 002f 0000 05ff 0100 0100 0b00 0322 0003 ./..........."..
0x0090: 1f00 031c 3082 0318 3082 0200 a003 0201 ....0...0.......
0x00a0: 0202 0851 0fc2 90c1 8e5f c930 0d06 092a ...Q....._.0...*
0x00b0: 8648 86f7 0d01 0105 0500 302a 310b 3009 .H........0*1.0.
0x00c0: 0603 5504 0613 0255 5331 0c30 0a06 0355 ..U....US1.0...U
0x00d0: 040a 1303 4942 4d31 0d30 0b06 0355 0403 ....IBM1.0...U..
0x00e0: 1304 5353 4c32 301e 170d 3137 3037 3239 ..SSL20...170729
0x00f0: 3038 3136 3334 5a17 0d31 3830 3733 3030 081634Z..1807300
0x0100: 3831 3633 345a 302a 310b 3009 0603 5504 81634Z0*1.0...U.
0x0110: 0613 0255 5331 0c30 0a06 0355 040a 1303 ...US1.0...U....
0x0120: 4942 4d31 0d30 0b06 0355 0403 1304 5353 IBM1.0...U....SS
0x0130: 4c32 3082 0122 300d 0609 2a86 4886 f70d L20.."0...*.H...
0x0140: 0101 0105 0003 8201 0f00 3082 010a 0282 ..........0.....
0x0150: 0101 00c5 4528 0ba8 2fc8 c8b7 8f00 aafe ....E(../.......
0x0160: 9bc4 fcea 039d eab2 d8c6 62b5 391d 96a0 ..........b.9...
0x0170: 1438 3986 dbe4 6b61 12e0 b2c7 1960 6a04 .89...ka.....`j.
0x0180: 8698 8378 9129 24f0 9e6b 5e43 001f 1d01 ...x.)$..k^C....
0x0190: 0f9a a522 39d9 e7df 0963 2340 3cf5 498e ..."9....c#@<.I.
0x01a0: 496d d10a 2395 efbe b249 e662 e23e c057 Im..#....I.b.>.W
0x01b0: 4250 199b 8a52 b263 4182 44ed cbc0 fa63 BP...R.cA.D....c
0x01c0: d06c 3143 fb7a 8886 6fed 80f2 970b 16be .l1C.z..o.......
0x01d0: 8d2f 6dec f00f b29f 76a1 1874 db89 cb7e ./m.....v..t...~
0x01e0: 7ecf 58fd 631b a66b 93a1 fe8d 48c5 de65 ~.X.c..k....H..e
0x01f0: 6fd5 140a c082 b980 0d3a 10bc 127d 3edb o........:...}>.
0x0200: 592e 69cb 4e41 6128 b8b8 561f e06f 22ed Y.i.NAa(..V..o".
0x0210: 7248 83d9 9068 e38d 6ff3 322b 4fa3 f62e rH...h..o.2+O...
0x0220: f010 2534 0e24 f9fd 04bb 3350 56a9 e41b ..%4.$....3PV...
0x0230: d080 f60c d2c3 a490 b578 07a7 5fb5 6b45 .........x.._.kE
0x0240: 397a c9c0 da0b 38cc a37c db56 c7d6 cfbf 9z....8..|.V....
0x0250: ef9f 9102 0301 0001 a342 3040 301d 0603 .........B0@0...
0x0260: 551d 0e04 1604 144f 51af f301 3599 8535 U......OQ...5..5
0x0270: 895a 98da e048 9907 a9fa 7a30 1f06 0355 .Z...H....z0...U
0x0280: 1d23 0418 3016 8014 4f51 aff3 0135 9985 .#..0...OQ...5..
0x0290: 3589 5a98 dae0 4899 07a9 fa7a 300d 0609 5.Z...H....z0...
0x02a0: 2a86 4886 f70d 0101 0505 0003 8201 0100 *.H.............
0x02b0: 844f c6ed 6a3c f3e3 24c9 8cf4 c321 0c4a .O..j<..$....!.J
0x02c0: fe03 df57 7450 fe29 29e5 0626 0900 1253 ...WtP.))..&...S
0x02d0: 6396 a7ed 53cc c8d1 c72f 06f3 86e1 31db c...S..../....1.
0x02e0: 41c9 3f04 6d01 8432 8c32 5450 79b3 3b53 A.?.m..2.2TPy.;S
0x02f0: 32dd fa02 2f11 a30c e052 93bd 7c09 324e 2.../....R..|.2N
0x0300: 1942 e72f 948f c803 898c 289f aaae ee35 .B./......(....5
0x0310: 8f33 6d66 d9cd 09e0 3b59 914c f52e 0282 .3mf....;Y.L....
0x0320: 4cab ed1c 6c90 3a55 36c4 b6b4 8dd6 0c3a L...l.:U6......:
0x0330: 3ef4 f20e 15f4 1501 9b96 ccd8 10f2 0ea4 >...............
0x0340: 706c 46e2 2319 eaa7 dea7 9e9e 643a 852a plF.#.......d:.*
0x0350: 4938 e206 50ad d89e 53ba 4e1f 4c31 1896 I8..P...S.N.L1..
0x0360: 138c dd83 2df6 1a93 289d 580d 235a 6572 ....-...(.X.#Zer
0x0370: c932 409f e428 53be 09ff e97f b668 d3e2 .2@..(S......h..
0x0380: 0b80 7bbd 982d dc31 f77c e934 f5a1 f7d0 ..{..-.1.|.4....
0x0390: c43d c6d3 186d 11fa db53 7f32 f315 68e8 .=...m...S.2..h.
0x03a0: f3f3 8e3a 2e5b 59db 27a9 0654 22e4 b0cf ...:.[Y.'..T"...
0x03b0: 0d00 0032 0101 002e 002c 302a 310b 3009 ...2.....,0*1.0.
0x03c0: 0603 5504 0613 0255 5331 0c30 0a06 0355 ..U....US1.0...U
0x03d0: 040a 1303 4942 4d31 0d30 0b06 0355 0403 ....IBM1.0...U..
0x03e0: 1304 5353 4c32 0e00 0000 ..SSL2....
11:03:46.842299 IP localhost.41834 > localhost.2013: Flags [.], ack 951, win 357, options [nop,nop,TS val 188398807 ecr 188398807], length 0
0x0000: 4500 0034 58c8 4000 4006 e3f9 7f00 0001 E..4X.@.@.......
0x0010: 7f00 0001 a36a 07dd 7514 9a98 8b49 201b .....j..u....I..
0x0020: 8010 0165 fe28 0000 0101 080a 0b3a bcd7 ...e.(.......:..
0x0030: 0b3a bcd7 .:..
11:03:46.849053 IP localhost.41834 > localhost.2013: Flags [P.], seq 90:1425, ack 951, win 357, options [nop,nop,TS val 188398809 ecr 188398807], length 1335
0x0000: 4500 056b 58c9 4000 4006 dec1 7f00 0001 E..kX.@.@.......
0x0010: 7f00 0001 a36a 07dd 7514 9a98 8b49 201b .....j..u....I..
0x0020: 8018 0165 0360 0000 0101 080a 0b3a bcd9 ...e.`.......:..
0x0030: 0b3a bcd7 1603 0105 320b 0003 2200 031f .:......2..."...
0x0040: 0003 1c30 8203 1830 8202 00a0 0302 0102 ...0...0........
0x0050: 0208 334e 11a4 a012 db28 300d 0609 2a86 ..3N.....(0...*.
0x0060: 4886 f70d 0101 0505 0030 2a31 0b30 0906 H........0*1.0..
0x0070: 0355 0406 1302 5553 310c 300a 0603 5504 .U....US1.0...U.
0x0080: 0a13 0349 424d 310d 300b 0603 5504 0313 ...IBM1.0...U...
0x0090: 0453 534c 3130 1e17 0d31 3730 3732 3930 .SSL10...1707290
0x00a0: 3831 3633 335a 170d 3138 3037 3330 3038 81633Z..18073008
0x00b0: 3136 3333 5a30 2a31 0b30 0906 0355 0406 1633Z0*1.0...U..
0x00c0: 1302 5553 310c 300a 0603 5504 0a13 0349 ..US1.0...U....I
0x00d0: 424d 310d 300b 0603 5504 0313 0453 534c BM1.0...U....SSL
0x00e0: 3130 8201 2230 0d06 092a 8648 86f7 0d01 10.."0...*.H....
0x00f0: 0101 0500 0382 010f 0030 8201 0a02 8201 .........0......
0x0100: 0100 9c3a 3aa5 9b3a 0872 e754 e665 ad2f ...::..:.r.T.e./
0x0110: a21c 30c9 24e5 5cba 6264 e1fe e5af a622 ..0.$..bd....."
0x0120: 2f46 459b 8f73 5ae3 55a5 9581 c3ae 4134 /FE..sZ.U.....A4
0x0130: d780 278a a469 88c8 761b a385 0133 09f7 ..'..i..v....3..
0x0140: b0c8 e127 471d 3f1f 832b f2eb a75a d4ce ...'G.?..+...Z..
0x0150: 3f60 066f 53a3 bf28 867f 3677 601f 1f6e ?`.oS..(..6w`..n
0x0160: ae73 58c4 24e7 9be5 f9ff 7a8c 7365 77fa .sX.$.....z.sew.
0x0170: c917 ce53 5fca b097 8422 5ba0 9d67 be9e ...S_...."[..g..
0x0180: 19e3 b646 97c3 3628 0faf 86bc d1b4 90c0 ...F..6(........
0x0190: 8755 45de d89d bdf9 d6b0 5b3c df1a 317c .UE.......[<..1|
0x01a0: f62a 1a55 61c2 0e6e 1ae8 51b6 69f1 6f74 .*.Ua..n..Q.i.ot
0x01b0: c718 866b b4f6 6ffd 0d6c 60f6 724b bc99 ...k..o..l`.rK..
0x01c0: 695b 7c51 4ebe 2f21 1da9 041b 2e43 229a i[|QN./!.....C".
0x01d0: 771b 3cc0 8703 b5b5 eb72 dd7e 9c46 240f w.<......r.~.F$.
0x01e0: 439a aa47 7f32 9b38 1683 f4e0 42f7 668a C..G.2.8....B.f.
0x01f0: ee32 ae9e a033 dce6 8459 1d5d 9bd1 48a5 .2...3...Y.]..H.
0x0200: 4585 0203 0100 01a3 4230 4030 1d06 0355 E.......B0@0...U
0x0210: 1d0e 0416 0414 ad74 f83e e11a a48a 842c .......t.>.....,
0x0220: abbb 74fa 0d3e 6fe6 3154 301f 0603 551d ..t..>o.1T0...U.
0x0230: 2304 1830 1680 14ad 74f8 3ee1 1aa4 8a84 #..0....t.>.....
0x0240: 2cab bb74 fa0d 3e6f e631 5430 0d06 092a ,..t..>o.1T0...*
0x0250: 8648 86f7 0d01 0105 0500 0382 0101 006e .H.............n
0x0260: 8dca a0e9 5605 be95 73ad 9e5c 16d0 8b88 ....V...s......
0x0270: 0ec5 8d8e 35d5 0f93 b415 fb46 364e 51e7 ....5......F6NQ.
0x0280: a5ee b8ce 92ed 7cbe 7708 d95a 6668 57b1 ......|.w..ZfhW.
0x0290: 10cb e4ad e1f2 a0e5 d99f cc7a f36d 3cc3 ...........z.m<.
0x02a0: 8293 747f ea90 d24d fcc9 8738 a694 a8f4 ..t....M...8....
0x02b0: 9f02 4f1a 31ec 645d 1fee 1731 e7d0 5223 ..O.1.d]...1..R#
0x02c0: b7c7 58a3 6a16 9a07 5917 6aa6 49ef 3f4c ..X.j...Y.j.I.?L
0x02d0: fa37 20db a510 93de 5200 5084 3a5d 5a17 .7......R.P.:]Z.
0x02e0: 80f8 14fd cb3f 8f32 cd35 ecd6 592a e057 .....?.2.5..Y*.W
0x02f0: 5213 07d7 51e4 a023 4835 c605 2b17 ef56 R...Q..#H5..+..V
0x0300: 5276 87a3 7db4 1b83 af5d 8a3a 914c d078 Rv..}....].:.L.x
0x0310: a63a e74e d677 7e6a 07ca fded 4b09 c665 .:.N.w~j....K..e
0x0320: 93ce c760 d49d b3f1 4992 7cd2 bf44 442b ...`....I.|..DD+
0x0330: a39c a1a3 978e 70aa 9c7b 92ac 003e 02c2 ......p..{...>..
0x0340: 4cd8 59a7 d183 5d50 5b46 ecef 05e4 ce9f L.Y...]P[F......
0x0350: ce12 89a6 7d36 a88e 68e8 02e3 11e5 0d10 ....}6..h.......
0x0360: 0001 0201 0098 a11f 3e8e 557e af83 72ea ........>.U~..r.
0x0370: 850f 3b92 ba93 6fd4 90a5 e3b0 d6a7 85a7 ..;...o.........
0x0380: 3085 520d 761e f6f1 fccb fffa b8d3 1ffe 0.R.v...........
0x0390: c36e a647 b7a8 8b5c cc0e e44f e9ab 78ab .n.G......O..x.
0x03a0: 29b8 1a1b c79e 7087 20cc 00c3 5d04 f660 ).....p.....]..`
0x03b0: dacd 8c7a 19b7 b140 640d ed6e e24f 874c ...z...@d..n.O.L
0x03c0: 8311 8d26 59c4 2125 767a 8e85 3a4b bfc9 ...&Y.!%vz..:K..
0x03d0: df9f 8f76 21ab 6210 2692 4f17 5bc4 e56a ...v!.b.&.O.[..j
0x03e0: 600f 96e2 8ff8 5a59 18b2 93ee 0e07 66f5 `.....ZY......f.
0x03f0: e4d8 c80b bfbe 61f0 3ad8 e77b 27ab f81e ......a.:..{'...
0x0400: e60e 6399 0019 67c5 eec6 defe fe9e 1861 ..c...g........a
0x0410: 4405 9952 3ecf fab5 32f6 5bf4 89e9 6741 D..R>...2.[...gA
0x0420: 43ea 76f3 55b3 e2ea f45b 5f72 7d25 8df6 C.v.U....[_r}%..
0x0430: 82a7 8ee9 8de0 e529 85e7 ebd6 a84d 220d .......).....M".
0x0440: 7a4f 536d 0d31 2fb6 b45a 253f 2e1c 05ad zOSm.1/..Z%?....
0x0450: c7ce e6b8 bf92 722e 136d 2780 60e0 c782 ......r..m'.`...
0x0460: 08d6 d6a6 da0f 0001 0201 0032 e37c a04a ...........2.|.J
0x0470: 810d 9885 eb24 ab30 9c02 6a31 22fa 5d3e .....$.0..j1".]>
0x0480: ced2 9b14 8e17 9e2e 8032 1b42 4aeb d53a .........2.BJ..:
0x0490: 71e5 aa75 b9cc a0c9 9d98 f092 4259 3946 q..u........BY9F
0x04a0: 46ef 0ae1 e671 326d b867 9fd9 1e56 7f6e F....q2m.g...V.n
0x04b0: 1b5f 6636 c7d0 982d 853d adfd e75a 9f75 ._f6...-.=...Z.u
0x04c0: 717c 9284 55b4 d8cf 7157 c3cb 7770 05b9 q|..U...qW..wp..
0x04d0: 0aa4 6939 5a2f d898 8e0b df75 6a0d c325 ..i9Z/.....uj..%
0x04e0: 7156 a75a 165c 145b ece8 76a4 b05d b273 qV.Z..[..v..].s
0x04f0: c7d5 19c4 d6ba 2b49 cc50 30da da03 ba7a ......+I.P0....z
0x0500: 3402 c778 275a 91a2 6aa9 f0e5 3ee7 6a07 4..x'Z..j...>.j.
0x0510: 95d3 b7a3 d943 b072 90b4 dfa4 b40a a5f3 .....C.r........
0x0520: cacb d600 5c5d 5deb 759a 4e25 3cf3 543c ....]].u.N%<.T<
0x0530: 09cc 94aa cef6 aad9 f4a7 5637 9902 9d77 ..........V7...w
0x0540: fc20 6c1e d5b9 3cdf c9cb 1713 2bde 5a00 ..l...<.....+.Z.
0x0550: 50b5 16b9 4a6b 8c5c 0e91 e6f8 19f1 f3f1 P...Jk.........
0x0560: 99ca f9e9 c629 d971 4194 52 .....).qA.R
11:03:46.849295 IP localhost.2013 > localhost.41834: Flags [.], ack 1425, win 1365, options [nop,nop,TS val 188398809 ecr 188398809], length 0
0x0000: 4500 0034 dea0 4000 4006 5e21 7f00 0001 E..4..@.@.^!....
0x0010: 7f00 0001 07dd a36a 8b49 201b 7514 9fcf .......j.I..u...
0x0020: 8010 0555 fe28 0000 0101 080a 0b3a bcd9 ...U.(.......:..
0x0030: 0b3a bcd9 .:..
11:03:46.850383 IP localhost.2013 > localhost.41834: Flags [P.], seq 951:958, ack 1425, win 1365, options [nop,nop,TS val 188398809 ecr 188398809], length 7
0x0000: 4500 003b dea1 4000 4006 5e19 7f00 0001 E..;..@.@.^.....
0x0010: 7f00 0001 07dd a36a 8b49 201b 7514 9fcf .......j.I..u...
0x0020: 8018 0555 fe2f 0000 0101 080a 0b3a bcd9 ...U./.......:..
0x0030: 0b3a bcd9 1503 0100 0202 2a .:........*
11:03:46.854876 IP localhost.2013 > localhost.41834: Flags [F.], seq 958, ack 1425, win 1365, options [nop,nop,TS val 188398810 ecr 188398809], length 0
0x0000: 4500 0034 dea2 4000 4006 5e1f 7f00 0001 E..4..@.@.^.....
0x0010: 7f00 0001 07dd a36a 8b49 2022 7514 9fcf .......j.I."u...
0x0020: 8011 0555 fe28 0000 0101 080a 0b3a bcda ...U.(.......:..
0x0030: 0b3a bcd9 .:..
11:03:46.859981 IP localhost.41834 > localhost.2013: Flags [P.], seq 1425:1431, ack 959, win 357, options [nop,nop,TS val 188398812 ecr 188398809], length 6
0x0000: 4500 003a 58ca 4000 4006 e3f1 7f00 0001 E..:X.@.@.......
0x0010: 7f00 0001 a36a 07dd 7514 9fcf 8b49 2023 .....j..u....I.#
0x0020: 8018 0165 fe2e 0000 0101 080a 0b3a bcdc ...e.........:..
0x0030: 0b3a bcd9 1403 0100 0101 .:........
11:03:46.860003 IP localhost.2013 > localhost.41834: Flags [R], seq 2336825379, win 0, length 0
0x0000: 4500 0028 a87c 4000 4006 9451 7f00 0001 E..(.|@.@..Q....
0x0010: 7f00 0001 07dd a36a 8b49 2023 0000 0000 .......j.I.#....
0x0020: 5004 0000 5b2a 0000 P...[*..
Colin’s comments at the bottom.
AMQ9633E: Bad SSL certificate for channel ‘QMAQCLIENTTLS’.
Process(7877.1) User(colinpaice) Program(amqsgetc)
Host(colinpaice) Installation(Installation1)
VRMF(9.2.1.0)
Time(2021-02-08T14:31:18.169Z)
RemoteHost(127.0.0.1)
ArithInsert1(414) ArithInsert2(575010)
CommentInsert1(QMAQCLIENTTLS)
CommentInsert2(
[Class=]GSKVALMethod::X509
[Issuer=]CN=SS,O=SSS,C=GB [#=]73cb2...
[Subject=]CN=SS,O=SSS,C=GB
[Class=]GSKVALMethod::PKIX
[Issuer=]CN=SS,O=SSS,C=GB[#=]73cb2...
[Subject=]CN=SS,O=SSS,C=GB)
CommentInsert3(localhost (127.0.0.1)(1414))
EXPLANATION:
A certificate encountered during SSL handshaking is regarded as bad for one of
the following reasons:
(a) it was formatted incorrectly and could not be validated
(b) it was formatted correctly but failed validation against the Certification
Authority (CA) root and other certificates held on the local system
(c) it was found in a Certification Revocation List (CRL) on an LDAP server
(d) a CRL was specified but the CRL could not be found on the LDAP server
(e) an OCSP responder has indicated that it is revoked
The channel is ‘QMAQCLIENTTLS’; in some cases its name cannot be determined and so is shown as ‘????’. The remote host is ‘localhost (127.0.0.1)(1414)’. The channel did not start.
The details of the certificate which could not be validated are
‘[Class=]GSKVALMethod::X509[Issuer=]CN=SS,O=SSS,C=GB[#=]73cb2b49d0e56bbeaa95ec8ea01fccc549a97ba8[Subject=]CN=SS,O=SSS,C=GB[Class=]GSKVALMethod::PKIX[Issuer=]CN=SS,O=SSS,C=GB[#=]73cb2b49d0e56bbeaa95ec8ea01fccc549a97ba8[Subject=]CN=SS,O=SSS,C=GB’.
The certificate validation error was 575010.
ACTION:
Check which of the possible causes applies on your system. Correct the error, and restart the channel.
This error might indicate that the remote end of the channel is configured to send the wrong certificate. Check the certificate label configuration at the remote end of the channel and ensure that the local key repository contains all of the necessary CA certificates.
Colin’s comments
The certificate sent from the server to the client could not be authenticated.
In this case the certificate is self signed, as the Issuer [Issuer=]CN=SS,O=SSS,C=GB is the same as the subject [Subject=]CN=SS,O=SSS,C=GB.
The issuer needs to be in the clients keystore. If the certificate is self signed it needs to be in the keystore. If the certificate is signed, then a certificate in the certificate chain needs to be in the keystore.
If the AMQ9633 message has
The details of the certificate which could not be validated are
‘[Class=]GSKVALMethod::X509
[Issuer=]CN=…,OU=…,O=…
[Subject=]CN=CSQ9…OU=…,O=…
[Class=]GSKVALMethod::PKIX
The certificate validation error was 575010
It cannot find the Issuer’s certicate.
Use the runmqakm -cert -list all -db ….kdb -type cms -stashed -v command for the client keystore. The -v flag lists the DN of the subject and the Issuer. For example my server’s keystore gives
Certificates found * default, - personal, ! trusted, # secret key ! ca256 CN=SSCA256,OU=CA,O=SSS,C=GB CN=SSCA256,OU=CA,O=SSS,C=GB - ECEC_SERVER CN=ecec,O=cpwebuser,C=GB CN=SSCA256,OU=CA,O=SSS,C=GB - SS_SERVER CN=SS,O=SSS,C=GB CN=SS,O=SSS,C=GB - RSA_SERVER CN=rsaca256,O=cpwebuser,C=GB CN=SSCA256,OU=CA,O=SSS,C=GB
The certificate needs to be added to the client keystore, for example
runmqakm -cert -add -file ~/ssl/ssl2/ss.pem -type cms -stashed -db zzclient.kdb -label ss
After adding it to the client’s keystore a list of the client keystore gives
Certificates found * default, - personal, ! trusted, # secret key ! ca256 CN=SSCA256,OU=CA,O=SSS,C=GB CN=SSCA256,OU=CA,O=SSS,C=GB ! ss CN=SS,O=SSS,C=GB CN=SS,O=SSS,C=GB - rsaca256_client CN=rsaca256,O=cpwebuser,C=GB CN=SSCA256,OU=CA,O=SSS,C=GB
With the self signed certificate in the key store the request works.
If the AMQ9633 message has
CommentInsert1(ECRSA1024)
CommentInsert2(????)
CommentInsert3(127.0.0.1)
Where the cipher spec has ????, it means the request did not even reach MQ. Check the the RSA key size below.
RSA key size not supported on a certificate
In MQ 9.2 there is the mqclient.ini and qm.ini option
SSL:
MinimumRSAKeySize=4096
For a certificate sent to this machine, if the RSA key size is smaller than this value you get the error. You cannot tell the keysize from the message, only the keystore.
Use the command
runmqakm -cert -details -type cms -stashed -db …..kdb -label …
to display the key type and keys site.
- Change the mqclient.ini to remove the MinimumRSAKeySize value, until the problem is resolved, then reinstate it.
- Change the certificate to use a stronger key size, or use Elliptic.
RSA key size not supported on a CA certificate
A certificate sent to this client/server has been signed by a CA with type RSA. If the CA’s key size is too small, you get the AMQ9633 error. You cannot tell the keysize from the message, only the keystore.
At the sending end,
- use runmqakm -cert -details -type cms -stashed -db …..kdb -label … to display the certificate, and the Issuer.
- use runmqakm -cert -list -type cms -stashed -db …..kdb -label … to display the list of certificates in the keystore. Find the label for the Issuer DN.
- use runmqakm -cert -details -type cms -stashed -db …..kdb -label … to display the CA certificate.
- Change the CA to have a larger key size, or change it to Elliptic.
- Change the mqclient.ini to remove the MinimumRSAKeySize value, until the problem is resolved, then reinstate it.
Re-issue any certificates the CA has signed.
Reissue the CA to all systems and update the key stores
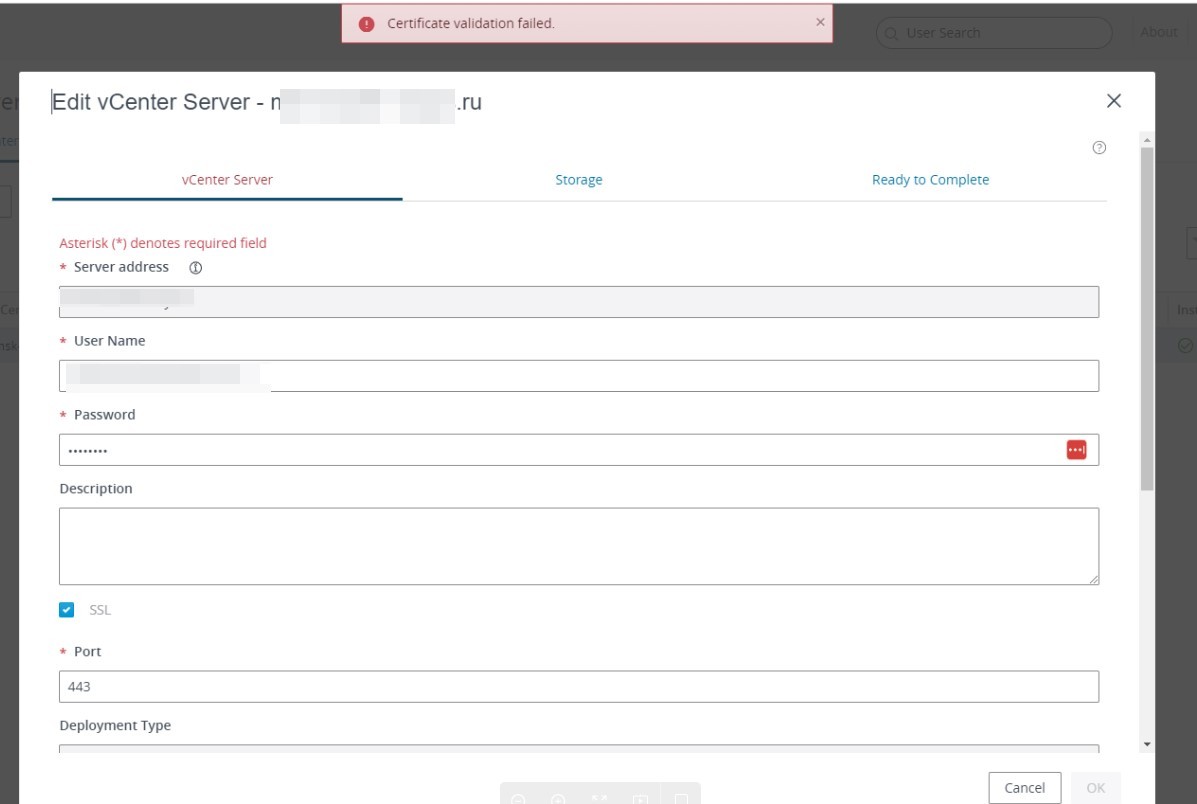
Зачастую после установки SSL-сертификатов многие пользователи сталкиваются с ошибками, которые препятствуют корректной работе защищенного протокола HTTPS.
Предлагаем разобраться со способами устранения подобных ошибок.
Что такое SSL?
SSL (Secure Socket Layer) — это интернет-протокол для создания зашифрованного соединения между пользователем и сервером, который гарантирует безопасную передачу данных.
Когда пользователь заходит на сайт, браузер запрашивает у сервера информацию о наличии сертификата. Если сертификат установлен, сервер отвечает положительно и отправляет копию SSL-сертификата браузеру. Затем браузер проверяет сертификат, название которого должно совпадать с именем сайта, срок действия сертификата и наличие корневого сертификата, выданного центром сертификации.
Причины возникновения ошибок SSL-соединения
Когда сертификат работает корректно, адресная строка браузера выглядит примерно так:
Но при наличии ошибок она выглядит несколько иначе:
Существует множество причин возникновения таких ошибок. К числу основных можно отнести:
- Некорректную дату и время на устройстве (компьютер, смартфон, планшет и т.д.);
- Ненадежный SSL-сертификат;
- Брандмауэр или антивирус, блокирующие сайт;
- Включенный экспериментальный интернет-протокол QUIC;
- Отсутствие обновлений операционной системы;
- Использование SSL-сертификата устаревшей версии 3.0;
- Появление ошибки «Invalid CSR» при генерации сертификата из панели управления облачного провайдера.
Давайте рассмотрим каждую из них подробнее.
Проблемы с датой и временем
Если на устройстве установлены некорректные дата и время, ошибка SSL-соединения неизбежна, ведь при проверке сертификата происходит проверка срока его действия. Современные браузеры умеют определять такую ошибку самостоятельно и выводят сообщение о неправильно установленной дате или времени.
Для исправления этой ошибки достаточно установить на устройстве актуальное время. После этого необходимо перезагрузить страницу или браузер.
Ненадежный SSL-сертификат
Иногда при переходе на сайт, защищенный протоколом HTTPS, появляется ошибка «SSL-сертификат сайта не заслуживает доверия».
Одной из причин появления такой ошибки, как и в предыдущем случае, может стать неправильное время. Однако есть и вторая причина — браузеру не удается проверить цепочку доверия сертификата, потому что не хватает корневого сертификата. Для избавления от такой ошибки необходимо скачать специальный пакет GeoTrust Primary Certification Authority, содержащий корневые сертификаты. После скачивания переходим к установке. Для этого:
- Нажимаем сочетание клавиш Win+R и вводим команду certmgr.msc, жмем «Ок». В Windows откроется центр сертификатов.
- Раскрываем список «Доверенные корневые центры сертификации» слева, выбираем папку «Сертификаты», кликаем по ней правой кнопкой мышки и выбираем «Все задачи — импорт».
- Запустится мастер импорта сертификатов. Жмем «Далее».
- Нажимаем кнопку «Обзор» и указываем загруженный ранее сертификат. Нажимаем «Далее»:
- В следующем диалоговом окне указываем, что сертификаты необходимо поместить в доверенные корневые центры сертификации, и нажимаем «Далее». Импорт должен успешно завершиться.
После вышеперечисленных действий можно перезагрузить устройство и проверить отображение сайта в браузере.
Брандмауэр или антивирус, блокирующие сайт
Некоторые сайты блокируются брандмауэром Windows. Для проверки можно отключить брандмауэр и попробовать зайти на нужный сайт. Если SSL-сертификат начал работать корректно, значит дело в брандмауэре. В браузере Internet Explorer вы можете внести некорректно работающий сайт в список надежных и проблема исчезнет. Однако таким образом вы снизите безопасность своего устройства, так как содержимое сайта может быть небезопасным, а контроль сайта теперь отключен.
Также SSL может блокировать антивирусная программа. Попробуйте отключить в антивирусе проверку протоколов SSL и HTTPS и зайти на сайт. При необходимости добавьте сайт в список исключений антивируса.
Включенный экспериментальный протокол QUIC
QUIC — это новый экспериментальный протокол, который нужен для быстрого подключения к интернету. Основная задача протокола QUIC состоит в поддержке нескольких соединений. Вы можете отключить этот протокол в конфигурации вашего браузера.
Показываем как отключить QUIC на примере браузера Google Chrome:
- Откройте браузер и введите команду chrome://flags/#enable-quic;
- В появившемся окне будет выделен параметр: Experimental QUIC protocol (Экспериментальный протокол QUIC). Под названием этого параметра вы увидите выпадающее меню, в котором нужно выбрать опцию: Disable.
- После этого просто перезапустите браузер.
Этот способ работает и в Windows и в Mac OS.
Отсутствие обновлений операционной системы
Проблемы с SSL-сертификатами могут возникать и из-за того, что на вашей операционной системе давно не устанавливались обновлений. Особенно это касается устаревших версий Windows (7, Vista, XP и более ранние). Установите последние обновления и проверьте работу SSL.
Использование SSL-сертификата версии 3.0
Некоторые сайты используют устаревший SSL-протокол версии 3.0, который не поддерживают браузеры. По крайней мере, по умолчанию. Чтобы браузер поддерживал устаревший SSL необходимо сделать следующее (на примере браузера Google Chrome):
- Откройте браузер и перейдите в раздел «Настройки».
- Прокрутите страницу настроек вниз и нажмите «Дополнительные».
- В разделе «Система» найдите параметр «Настройки прокси-сервера» и кликните на него.
- Откроется окно. Перейдите на вкладку «Дополнительно».
- В этой вкладке вы увидите чекбокс «SSL 3.0».
- Поставьте галочку в чекбоксе, нажмите кнопку «Ок» и перезагрузите браузер.
Ошибки «Invalid CSR» при генерации сертификата из панели управления облачного провайдера
В процессе активации сертификата можно столкнуться с ошибкой «Invalid CSR». Такая ошибка возникает по следующим причинам:
- Неправильное имя FQDN (полное имя домена) в качестве Common Name (в некоторых панелях управления это поле может также называться Host Name или Domain Name). В этом поле должно быть указано полное доменное имя вида domain.com или subdomain.domain.com (для субдоменов). Имя домена указывается без https://. В качестве данного значения нельзя использовать интранет-имена (text.local). В запросе для wildcard-сертификатов доменное имя необходимо указывать как *.domain.com.
- В CSR или пароле есть не латинские буквы и цифры. В CSR поддерживаются только латинские буквы и цифры – спецсимволы использовать запрещено. Это правило распространяется и на пароли для пары CSR/RSA: они не должны содержать спецсимволов.
- Неверно указан код страны. Код страны должен быть двухбуквенным ISO 3166-1 кодом (к примеру, RU, US и т.д.). Он указывается в виде двух заглавных букв.
- В управляющей строке не хватает символов. CSR-запрос должен начинаться с управляющей строки ——BEGIN CERTIFICATE REQUEST—— и заканчиваться управляющей строкой ——END CERTIFICATE REQUEST——. С каждой стороны этих строк должно быть по 5 дефисов.
- В конце или начале строки CSR есть пробелы. Пробелы на концах строк в CSR не допускаются.
- Длина ключа меньше 2048 бит. Длина ключа должна быть не менее 2048 бит.
- В CRS-коде для сертификата для одного доменного имени есть SAN-имя. В CSR-коде для сертификата, предназначенного защитить одно доменное имя, не должно быть SAN (Subject Alternative Names). SAN-имена указываются для мультидоменных (UCC) сертификатов.
- При перевыпуске или продлении сертификата изменилось поле Common Name. Это поле не должно меняться.
Содержание
- Certificate validation failure cisco anyconnect как исправить windows 10
- What is Cisco AnyConnect?
- Cisco AnyConnect Review: Features
- What is “Cisco AnyConnect Certificate Validation Failure” Error on Windows?
- [Tips & Tricks] How to fix Cisco AnyConnect Certificate Validation Failure Problem?
- Procedure 1: Repair the Installation
- Procedure 2: Allow VPN to freely communicate through Firewall
- Procedure 3: Check Virtual Adapter driver in Device Manger and update it
- Procedure 4: Tweak Registry and Repair Cisco VPN
- Procedure 5: Update the AnyConnect
- Procedure 6: Create Trustpoints for each certificate being installed
- Procedure 7: Perform Clean Reinstallation
- Conclusion
- Certificate validation failure cisco anyconnect как исправить windows 10
- Answered by:
- Question
- Answers
- All replies
- How to Fix “VPN Certificate Validation Failure” Error
- 1. Go through standard troubleshooting steps
- 2. Double-check the VPN client profile
- 3. Has the SSL/TLS certificate expired?
- 4. Install a new SSL or TLS certificate
- I want to use the PEM client certificate. What should I do?
- 5. Configure cryptography
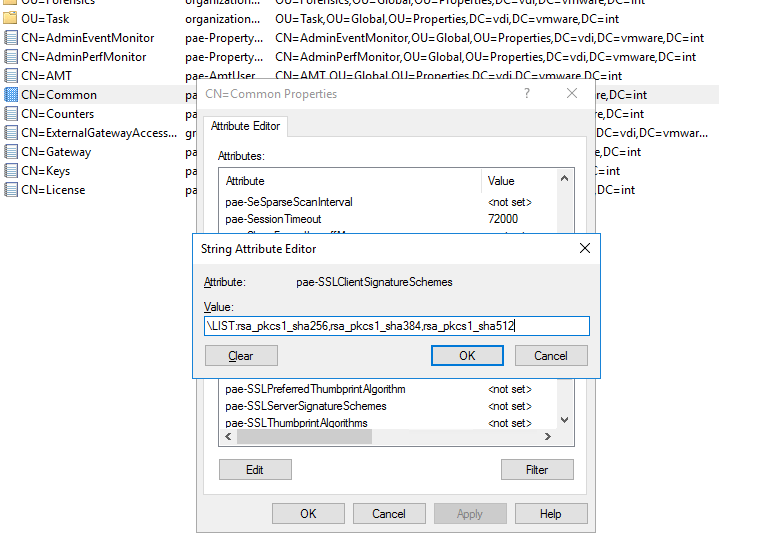
- 1. Allowing SSL client certificates to be used on the outside
- 2. Fixing TLS version mismatch and changing cryptography method
- 6. Enable or disable Windows OCSP Service Nonce
- 1. Enable OCSP Nonce on Windows Server
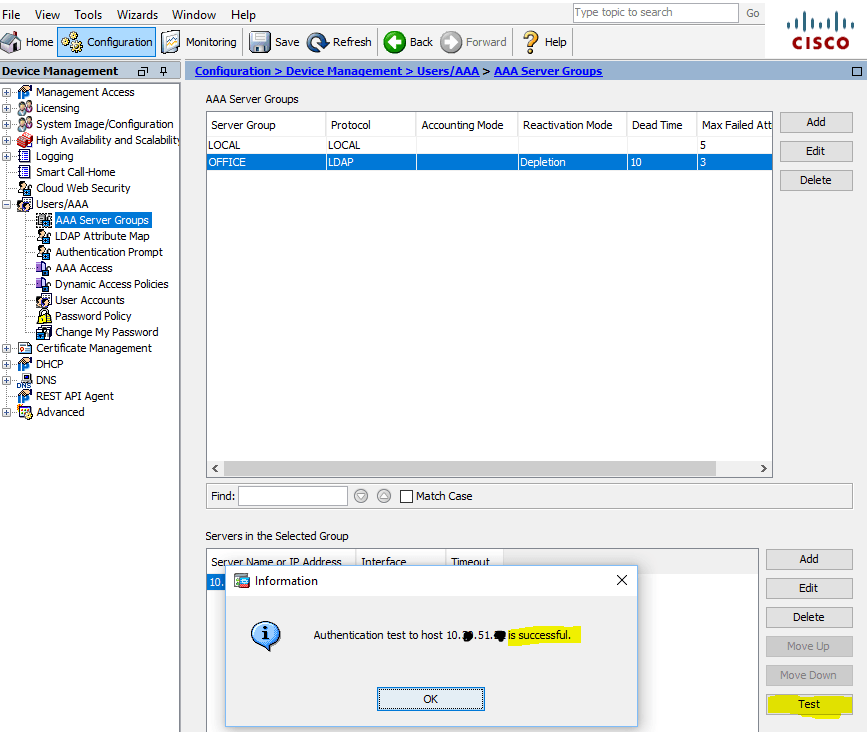
- 2. Disable Nonce via ASA TrustPoint
- Milan
- Certificate validation failure cisco anyconnect как исправить windows 10
- Спрашивающий
- Вопрос
- Available Languages
- Download Options
- Contents
- Introduction
- Prerequisites
- Requirements
- Components Used
- Troubleshooting Process
- Installation and Virtual Adapter Issues
- Disconnection or Inability to Establish Initial Connection
- Problems with Passing Traffic
- AnyConnect Crash Issues
- Fragmentation / Passing Traffic Issues
- Uninstall Automatically
- Issue Populating the Cluster FQDN
- Backup Server List Configuration
- AnyConnect: Corrupt Driver Database Issue
- Repair
- Failed Repair
- Analyze the Database
- Error Messages
- Error: Unable to Update the Session Management Database
- Solution 1
- Solution 2
- Error: «Module c:Program FilesCiscoCisco AnyConnect VPN Clientvpnapi.dll failed to register»
- Solution
- Error: «An error was received from the secure gateway in response to the VPN negotiation request. Please contact your network administrator»
- Solution
- Error: Session could not be established. Session limit of 2 reached.
- Solution 1
- Solution 2
- Error: Anyconnect not enabled on VPN server while trying to connect anyconnect to ASA
- Solution
- Error:- %ASA-6-722036: Group client-group User xxxx IP x.x.x.x Transmitting large packet 1220 (threshold 1206)
- Solution
- Error: The secure gateway has rejected the agent’s vpn connect or reconnect request.
- Solution
- Error: «Unable to update the session management database»
- Solution
- Error: «The VPN client driver has encountered an error»
- Solution
- Error: «Unable to process response from xxx.xxx.xxx.xxx»
- Solution
- Solution
- Solution
- Error: «The server certificate received or its chain does not comply with FIPS. A VPN connection will not be established»
- Solution
- Error: «Certificate Validation Failure»
- Solution
- Error: «VPN Agent Service has encountered a problem and needs to close. We are sorry for the inconvenience»
- Solution
- Error: «This installation package could not be opened. Verify that the package exists»
- Solution
- Error: «Error applying transforms. Verify that the specified transform paths are valid.»
- Solution
- Error: «The VPN client driver has encountered an error»
- Solution
- Error: «A VPN reconnect resulted in different configuration setting. The VPN network setting is being re-initialized. Applications utilizing the private network may need to be restored.»
- Solution
- AnyConnect Error While Logging In
- Solution
- IE Proxy Setting is Not Restored after AnyConnect Disconnect on Windows 7
- Solution
- Error: AnyConnect Essentials can not be enabled until all these sessions are closed.
- Solution
- Error: Connection tab on Internet option of Internet Explorer hides after getting connected to the AnyConnect client.
- Solution
- Error: Few users getting Login Failed Error message when others are able to connect successfully through AnyConnect VPN
- Solution
- Error: The certificate you are viewing does not match with the name of the site you are trying to view.
- Solution
- Cannot Launch AnyConnect From the CSD Vault From a Windows 7 Machine
- Solution
- AnyConnect Profile Does Not Get Replicated to the Standby After Failover
- Solution
- AnyConnect Client Crashes if Internet Explorer Goes Offline
- Solution
- Error Message: TLSPROTOCOL_ERROR_INSUFFICIENT_BUFFER
- Solution
- Error Message: «Connection attempt has failed due to invalid host entry»
- Solution
- Error: «Ensure your server certificates can pass strict mode if you configure always-on VPN»
- Solution
- Error: «An internal error occurred in the Microsoft Windows HTTP Services»
- Solution
- Error: «The SSL transport received a Secure Channel Failure. May be a result of a unsupported crypto configuration on the Secure Gateway.»
- Solution
Certificate validation failure cisco anyconnect как исправить windows 10
If you are facing “Cisco AnyConnect Certificate Validation Failure” problem while trying to connect on the AnyConnect Client, then you are in right place. Here, we are discussing on “ How to fix AnyConnect Certificate error ” in details and providing some recommended methods to fix this error. Let’s starts the discussion.
What is Cisco AnyConnect?
“Cisco AnyConnect” is proprietary application that lets users connect to VPN service. Many universities use this application as part of service they pay for from Cisco that’s why public institutions unnecessarily rely on this closed-source software for their own students. This doesn’t just amount to handling control to a private corporation, thereby privatizing public money. This software also provide extra security layer to reduce potentially unwanted attacks and privacy vulnerability.
Cisco AnyConnect is unified endpoint agent that delivers multiple security services to protect the enterprise. Its wide range of security services includes functions such as remote access, posture enforcement, web security features, and roaming protection. It gives all the security features for IT department to provide a robust, user-friendly, and highly secure mobile experience as well.
Cisco AnyConnect security mobility client is modular endpoint software product that not only provides VPN access via SSL (Secure Socket Layer) and IPsec IKEv2 but also offers improved security via various built-in modules including compliance through VPN and ASA or through wired /wireless, and VPN with Cisco identity Services Engine (ISE), Off-network roaming protection with Cisco Umbrella.
Since, Cisco has been a long-term target of NSA spying program. It also doesn’t work well on Linux. There is nothing wrong with supporting free and open source solutions like OpenVPN which are used by numerous users worldwide. Linux, iOS, Windows, MacOS and Android OS are some of the popular tools that integrate with Cisco Anyconnect.
Cisco AnyConnect Review: Features
What is “Cisco AnyConnect Certificate Validation Failure” Error on Windows?
“AnyConnect Certificate error” is common error reported by numerous users on Cisco official forum site or other popular platforms and asked for the solution. Users explained on Cisco Community website that the error appears when they run their own CA that gives out the client certificates for our users as well as the identity certificate for ASA, and in order to click on “Connect” on AnyConnect Client, their client receives “No Valid Certificates available for authentication” message.
Furthermore, he also created a DART bundle and in there I can see that the certificate is selected from the “Microsoft Store”, but after that he receive several errors regarding SCHANNEL. Then, he tried another certificate authentication and finds no certificates followed by “Cisco AnyConnect Certificate Validation Failure” Error.
Certificate Validation Failure Error States:
When we talk about “Anyconect Certificate validation Failure error”, it explained that it can’t verify the VPN server which is to be expected since it uses the self-signed certificate, but if they connect anyway, then they receive the certification selection and the login works fine. It means username & password for login is taken from the certificate.
[Tips & Tricks] How to fix Cisco AnyConnect Certificate Validation Failure Problem?
Procedure 1: Repair the Installation
Step 1: Click on “Start” button and type “Control Panel” in Windows search and open “Control Panel”
Step 2: In the opened “Control Panel”, choose “Uninstall a program” and find “Cisco AnyConnect VPN” client and choose “Repair”
Step 3: Follow On-Screen instructions to finish the repairing process. Once done, restart your computer and please check if the problem is resolved.
Procedure 2: Allow VPN to freely communicate through Firewall
Step 1: Click on “Start” button and type “Allow an App” in Windows Search and open “Allow an App through Windows Firewall”
Step 2: Now, click on “Change Settings”
Step 3: Make sure that “Cisco VPN” is on the list and it’s allowed to communicate through Windows Firewall. If not, click “Allow another App” and add it
Step 4: Check both “Private” and “Publicrong” > Network boxes
Step 5: Confirm changes and open Cisco VPN
Procedure 3: Check Virtual Adapter driver in Device Manger and update it

Step 1: Press “Windows + X” key from keyboard and select “Device Manager”
Step 2: In the opened “Device Manager” window, locate and expand “Network Adapters”
Step 3: Right-click on Virtual Adapter and select “Update driver software”
Step 4: Follow On-Screen instructions to finish the updating process.
Step 5: Once done, restart your computer and please check if the problem is resolved.
Procedure 4: Tweak Registry and Repair Cisco VPN
Step 1: Press “Windows + R” keys together from keyboard and type “regedit” in “Run Dialog Box” and then hit “Ok” button
Step 2: In the opened “Registry Editor” window, navigate to “HKEY_LOCAL_MACHINE/SYSTEM/Current/Control/SetServices/CVirtA”
Step 3: Right-click on the “DisplayName” registry entry and choose “Modify”
Step 4: Under “Value Data” section, make sure that the only body of text which stands is Cisco System VPN Adapter
Step 5: Save the changes and try running Cisco AnyConnect VPN again.
Procedure 5: Update the AnyConnect
Step 1: Go to “ASDM > Configuration > Remote Access VPN > Network (Client) Access > AnyConnect Client Software”
Step 2: You can either replace the existing the image or add a new one.
Step 3: After that, connect to the ASA. The client will be updated automatically.
Procedure 6: Create Trustpoints for each certificate being installed
Step 1: Open the “Cisco ASDM”
Step 2: Under “Remote Access VPN” window pane, click on “Configuration” tab and expand “Certificate Management” and click on “CA Certificates”
Step 3: Click on “Add” button
Step 4: Assign a “TrustPoint Name” to the certificate like “DigiCertCA2” and select “Install from the file” Radio button and browse to “DigiCertCA2.crt”, then click on “Install Certificate”. Repeat this process of adding new trustpoint and installing certificate file for “DigiCertCA.crt”
Step 5: Under “Remote Access VPN”, expand “Certificate Management” to “Identify Certificates”. Select the identity you created for the CSR with “Expiry Data” and click on “Install > Install Certificate”
Step 6: The Certificate now needs to be enabled. To do so, click on “Advanced > SSL Settings > Edit > Primary Enrolled Certificate” and select your certificate and then click on “Ok”
Step 7: ASDM will then show your Certificate details under trustpoint
Procedure 7: Perform Clean Reinstallation
Step 1: Navigate to “Control Panel” and choose “Uninstall a program”
Step 2: Uninstall “Cisco AnyConnect VPN Client”
Step 3: Navigate to System partition and delete everything Cisco-related from programs folder
Step 4: Once uninstalled completely, restart your computer
Step 5: After that, download latest version of “Cisco AnyConnect” from “Cisco official website”
Step 6: Double-click on installer file and follow on-screen instructions to finish the installation.
Step 7: Once installed, restart your computer again and please check if the AnyConnect Certificate error is resolved.
Conclusion
Cisco AnyConnect is VPN service that offers Standard VPN encryption and protection. When we talk about AnyConnect Secure Mobility Client, it is modular endpoint software product. It not only provides Virtual Private Network (VPN) access through Secure Sockets layer (SSL) and Internet Protocol Security (IPsec) Internet Key Exchange version2 (IKEv2), but also offers enhanced security through various built-in modules.
I am sure this article helped you to “Fix Cisco AnyConnect Certificate Validation Failure Windows 10” with several easy methods/procedures. You can choose/follow either one or all procedures to fix this issue.
If you are unable to fix Cisco AnyConnect Certificate Validation Failure problem with the solutions mentioned above, then it might possible that your System has infected with malware or viruses. According to security researchers, malware or viruses cause several damages in your computer.
In this case, you can scan your computer with powerful antivirus software that has the ability to delete all types of malware or viruses from System.
Источник
Certificate validation failure cisco anyconnect как исправить windows 10
This forum has migrated to Microsoft Q&A. Visit Microsoft Q&A to post new questions.
Answered by:
Question
Is this issue related to AD. or what is the possible cause for this?
Answers
I would start by digging further into the Group Policy Object that is supposed to be pushing the certificates out. Does everything look like it’s configure properly?(https://blogs.technet.microsoft.com/yungchou/2013/10/21/enterprise-pki-with-windows-server-2012-r2-active-directory-certificate-services-part-1-of-2/)
If it’s just a small set of machines aren’t getting the certificates, is there anything in common with those machines or users? Are they in the same Active Directory OU? Are they getting other group policies? Try to figure out what makes these particular users/machines different.
Is the certificate added to the Trust Store?
The following link will be helpful:
Further, kindly check if the certificate is not expired.
Certificate is not expired, i believe its gets pushed to the clients automitically from server.
How should i proceed further
Kindly post your query here:
According to your description, I think you may meet with this condition.
If so, I find out a similar case, maybe can give you some prompt.
Also, I suggest to contact Cisco support for help, I browse their community, many users faced same error message like you, they may give you more suitable suggestions.
Please Note: Since the website is not hosted by Microsoft, the link may change without notice. Microsoft does not guarantee the accuracy of this information.
Please remember to mark the replies as answers if they help, and unmark the answers if they provide no help. If you have feedback for TechNet Support, contact tnmff@microsoft.com.
I got more info on this
PKI CA server is configured with the default ADCS templates & integrated with AD, further then the certificates are pushed off to the users based on the templates by AD.
Now if the certificates are not pushed to the user, what should i check?
I would start by digging further into the Group Policy Object that is supposed to be pushing the certificates out. Does everything look like it’s configure properly?(https://blogs.technet.microsoft.com/yungchou/2013/10/21/enterprise-pki-with-windows-server-2012-r2-active-directory-certificate-services-part-1-of-2/)
If it’s just a small set of machines aren’t getting the certificates, is there anything in common with those machines or users? Are they in the same Active Directory OU? Are they getting other group policies? Try to figure out what makes these particular users/machines different.
This helped me a lot to understand the concept.
as of now we have only couple of machine in different OU facing the issue.
will investigate further and update you.
If it’s just a couple of machines, it’s possible that something is wrong with those machines themselves, and perhaps not your Certificate Services or Group Policy. If you look in the Event Viewer on the problem machines, see if they are processing *any* group policies at all. And see if any other errors are popping up in the Event Viewer.
Machines that have had malware in the past may exhibit strange behavior. So make sure to run a virus scan on any problem machines and make sure they are clean. Sometimes, you just have to rebuild a machine, because who knows what it’s been through in the past that is making it abnormal today.
Came across the same issue a few days back and found what was actually causing this error.
The reason validation fails is because the ASA certificate has only All issuance policies, but no Application polices and marking the above two as critical in the client’s certificate will change it to a type that is not considered valid by the ASA certificate.
Источник
How to Fix “VPN Certificate Validation Failure” Error
The “VPN certificate validation failure” error is exclusive to the Cisco AnyConnect VPN client for Windows, Mac, and Linux. An added reason for a quick solution is that the software is frequently used in a business setting, interconnecting computers into a secure, efficient network. And while it performs wonderfully most of the time, things sure can go wrong unexpectedly. What’s more, employees can’t always reach a network engineer and are often left to their own devices. That’s precisely when we’d like to swoop in and save the day. Let’s demonstrate how to fix the “VPN certificate validation failure” error.
1. Go through standard troubleshooting steps
Before you get into an array of unnecessary steps, make sure the problem isn’t a glitch, bug, or temporary downtime. By this, we mean going through steps 1 through 6 in our “VPN connection failed. The Request was aborted” error fix guide. Once you’ve tried that and it didn’t work, press on.
2. Double-check the VPN client profile
In essence, you need to verify the hostname and host address are still valid. Even if you haven’t made changes manually, your network admin might have, to the server or the client. To demonstrate this, we’ll use Cisco AnyConnect VPN client profile on macOS:
3. Has the SSL/TLS certificate expired?
A common cause of the “VPN certificate validation failure” error is the expiration of the SSL certificate. While in the past they were issued for longer, in 2022 the period is reduced to either 12 months or 13 months (397 days). Although there are many ways to do this, we’ll use the ASDM client to demonstrate checking SSL/TLS certificate expiration date:
4. Install a new SSL or TLS certificate
If your certificate expired, then you know regenerating them is the way to fix the “VPN certificate validation failure” error. Here’s what to do:
I want to use the PEM client certificate. What should I do?
So, you’re using AnyConnect VPN on Linux or Mac. If you haven’t installed certificates yet, download the client certificate and its private key and place them here:
/.cisco/certificates/client/private/” (private key here)
Clarification. The certificate must end with .pem while the private key must end with .key. Also, they must have identical file names.
5. Configure cryptography
Although there are ways to do this within the GUI, it’s much quicker and easier to simply run CLI (command-line interface) commands. Here’s what you can try:
1. Allowing SSL client certificates to be used on the outside
This is a step Cisco itself recommends as a permanent fix for the “VPN certificate validation failure” error. It simply makes client-side certificates available externally. Here’s how to proceed:
2. Fixing TLS version mismatch and changing cryptography method
There’s a chance that your VPN client isn’t up to date, or that there’s some sort of conflict which makes it use TLS 1.0 or TLS 1.1. This creates a problem when your cryptography tries to negotiate TLS 1.2. To fix this, open the CLI and proceed in one of 3 ways:
6. Enable or disable Windows OCSP Service Nonce
Without getting into specifics, you should know that Microsoft Windows uses RFC 5019 while Cisco AnyConnect VPN’s ASA is only compliant with RFC 2560. As such, on Windows, it won’t accept requests signed by ASA certificates and thus print “VPN certificate validation failure” error. You can fix this in one of 2 ways:
1. Enable OCSP Nonce on Windows Server
Are you (or your company) using an Online Certificate Status Protocol (OCSP) responder on your Windows Server? If so, do this:
2. Disable Nonce via ASA TrustPoint
Although Cisco recommends the method above, you can also try to disable OCSP via the CLI. After launching the appropriate interface, use these commands:
Tip. Replace WIN-2K12-01_Root_CA with the actual TrustPoint name of your certificate (you can see it using method 4).
Milan
VPN is one of my passions. I love being secure and helping others avoid any potential threats online. I also contribute to several VPN guide websites online.
Источник
Certificate validation failure cisco anyconnect как исправить windows 10
Этот форум закрыт. Спасибо за участие!
Спрашивающий
Вопрос
После апгрейда с Windows 7 до Windows 8 я, как и многие другие пользователи, столкнулся с проблемой подключения к офису через Cisco VPN Client. В моём случае под Windows 7 был установлен Cisco AnyConnect 2.5.6005, который работал без нареканий.
После апгрейда система сообщила, что AnyConnect требуется переустановить, но переустановка мне не помогла. Возникала ошибка Failed to enable Virtual Adapter. Симптомы были схожими, как описано в статье
Я всё же не стал ничего ковырять в системе и решил просто скачать последнюю версию Cisco AnyConnect c сайта cisco.com. На данный момент последняя версия 3.1.01065.
Но тут возникли другие проблемы. Cisco AnyConnect не видит SSL сертификат VPN сервера, настроенного на Cisco ASA 5510. Выдаёт следующее сообщение «No valid certificates available for authentication».
Сертификат для Cisco ASA 5510 выдавался нашим корпоративным центром сертификации по шаблону «WebServer». Этот сертификат, а также сертификат самого центра сертификации я импортировал в Доверенные корневые центры сертификации через консоль certmgr.msc. В списке сертификатов я их вижу и оба они действительные.
Есть предположение, что Cisco AnyConnect смотрит сертификаты через свойства обозревателя и, не обнаруживая его там, выдаёт ошибку «No valid certificates available for authentication». Хотя повторюсь, что на Windows 7 никаких проблем с сертификатами не было.
Как заставить Cisco AnyConnect всё таки увидить сертификат?
Тот же самый вопрос, который я задавал сначала там
Источник
Available Languages
Download Options
Contents
Introduction
This document describes a troubleshooting scenario which applies to applications that do not work through the Cisco AnyConnect VPN Client.
Prerequisites
Requirements
There are no specific requirements for this document.
Components Used
The information in this document is based on a Cisco Adaptive Security Appliance (ASA) that runs Version 8.x.
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, make sure that you understand the potential impact of any command.
Troubleshooting Process
This typical troubleshooting scenario applies to applications that do not work through the Cisco AnyConnect VPN Client for end-users with Microsoft Windows-based computers. These sections address and provide solutions to the problems:
Installation and Virtual Adapter Issues
Complete these steps:
Note: Hidden folders must be made visible in order to see these files.
If you see errors in the setupapi log file, you can turn up verbosity to 0x2000FFFF.
If this is an initial web deploy install, this log is located in the per-user temp directory.
If this is an automatic upgrade, this log is in the temp directory of the system:
The filename is in this format: anyconnect-win-x.x.xxxx-k9-install-yyyyyyyyyyyyyy.log. Obtain the most recent file for the version of the client you want to install. The x.xxxx changes based on the version, such as 2.0.0343, and yyyyyyyyyyyyyy is the date and time of the install.
Note: After you type into this prompt, wait. It can take between two to five minutes for the file to complete.
Windows XP and Windows Vista:
Refer to AnyConnect: Corrupt Driver Database Issue in order to debug the driver issue.
Disconnection or Inability to Establish Initial Connection
If you experience connection problems with the AnyConnect client, such as disconnections or the inability to establish an initial connection, obtain these files:
From the console of the ASA, type write net x.x.x.x:ASA-Config.txt where x.x.x.x is the IP address of a TFTP server on the network.
Note: Always save it as the .evt file format.
If the user cannot connect with the AnyConnect VPN Client, the issue might be related to an established Remote Desktop Protocol (RDP) session or Fast User Switching enabled on the client PC. The user can see the AnyConnect profile settings mandate a single local user, but multiple local users are currently logged into your computer. A VPN connection will not be established error message error on the client PC. In order to resolve this issue, disconnect any established RDP sessions and disable Fast User Switching. This behavior is controlled by the Windows Logon Enforcement attribute in the client profile, however currently there is no setting that actually allows a user to establish a VPN connection while multiple users are logged on simultaneously on the same machine. Enhancement request CSCsx15061 
Note: Make sure that port 443 is not blocked so the AnyConnect client can connect to the ASA.
In order to resolve this issue, upgrade the AnyConnect client version to be compatible with the ASA software image.
When you log in the first time to the AnyConnect, the login script does not run. If you disconnect and log in again, then the login script runs fine. This is the expected behavior.
This error is seen when the AnyConnect image is missing from the ASA. Once the image is loaded to the ASA, AnyConnect can connect without any issues to the ASA.
This error can be resolved by disabling Datagram Transport Layer Security (DTLS). Go to Configuration > Remote Access VPN > Network (Client) Access > AnyConnect Connection Profiles and uncheck the Enable DTLS check box. This disables DTLS.
The svc keepalive and svc dpd-interval commands are replaced by the anyconnect keepalive and anyconnect dpd-interval commands respectively in ASA Version 8.4(1) and later as shown here:
Problems with Passing Traffic
When problems are detected with passing traffic to the private network with an AnyConnect session through the ASA, complete these data-gathering steps:
For example, if the VPN Client needs to access a resource which is not in the routing table of the VPN Gateway, the packet is routed through the standard default gateway. The VPN gateway does not need the complete internal routing table in order to resolve this. The tunneled keyword can be used in this instance.
AnyConnect Crash Issues
Complete these data-gathering steps:
When the crash occurs, gather the .log and .dmp files from C:Documents and SettingsAll UsersApplication DataMicrosoftDr Watson. If these files appear to be in use, then use ntbackup.exe.
Note: Always save it as the .evt file format.
Fragmentation / Passing Traffic Issues
Some applications, such as Microsoft Outlook, do not work. However, the tunnel is able to pass other traffic such as small pings.
This can provide clues as to a fragmentation issue in the network. Consumer routers are particularly poor at packet fragmentation and reassembly.
It is recommended that you configure a special group for users that experience fragmentation, and set the SVC Maximum Transition Unit (MTU) for this group to 1200. This allows you to remediate users who experience this issue, but not impact the broader user base.
Problem
TCP connections hang once connected with AnyConnect.
Solution
In order to verify if your user has a fragmentation issue, adjust the MTU for AnyConnect clients on the ASA.
Uninstall Automatically
Problem
The AnyConnect VPN Client uninstalls itself once the connection terminates. The client logs show that keep installed is set to disabled.
Solution
AnyConnect uninstalls itself despite that the keep installed option is selected on the Adaptive Security Device Manager (ASDM). In order to resolve this issue, configure the svc keep-installer installed command under group-policy.
Issue Populating the Cluster FQDN
Problem: AnyConnect client is pre-populated with the hostname instead of the cluster Fully Qualified Domain Name (FQDN).
When you have a load-balancing cluster set up for SSL VPN and the client attempts to connect to the cluster, the request is redirected to the node ASA and the client logs in successfully. After some time, when the client tries to connect to the cluster again, the cluster FQDN is not seen in the Connect to entries. Instead, the node ASA entry to which the client has been redirected is seen.
Solution
This occurs because the AnyConnect client retains the host name to which it last connected. This behavior is observed and a bug has been filed. For complete details about the bug, refer to Cisco bug ID CSCsz39019. The suggested workaround is to upgrade the Cisco AnyConnect to Version 2.5.
Backup Server List Configuration
A backup server list is configured in case the main server selected by the user is not reachable. This is defined in the Backup Server pane in the AnyConnect profile. Complete these steps:
AnyConnect: Corrupt Driver Database Issue
This entry in the SetupAPI.log file suggests that the catalog system is corrupt:
Repair
This issue is due to Cisco bug ID CSCsm54689. In order to resolve this issue, make sure that Routing and Remote Access Service is disabled before you start AnyConnect. If this does not resolve the issue, complete these steps:
Failed Repair
If the repair fails, complete these steps:
Analyze the Database
You can analyze the database at any time in order to determine if it is valid.
Error Messages
Error: Unable to Update the Session Management Database
Solution 1
This issue is due to Cisco bug ID CSCsm51093. In order to resolve this issue, reload the ASA or upgrade the ASA software to the interim release mentioned in the bug. Refer to Cisco bug ID CSCsm51093 
Solution 2
This issue can also be resolved if you disable threat-detection on ASA if threat-detection is used.
Error: «Module c:Program FilesCiscoCisco AnyConnect VPN Clientvpnapi.dll failed to register»
When you use the AnyConnect client on laptops or PCs, an error occurs during the install:
When this error is encountered, the installer cannot move forward and the client is removed.
Solution
These are the possible workarounds to resolve this error:
The log message related to this error on the AnyConnect client looks similar to this:
Error: «An error was received from the secure gateway in response to the VPN negotiation request. Please contact your network administrator»
When clients try to connect to the VPN with the Cisco AnyConnect VPN Client, this error is received.
This message was received from the secure gateway:
«Illegal address class» or «Host or network is 0» or «Other error»
Solution
The issue occurs because of the ASA local IP pool depletion. As the VPN pool resource is exhausted, the IP pool range must be enlarged.
Cisco bug ID is CSCsl82188 is filed for this issue. This error usually occurs when the local pool for address assignment is exhausted, or if a 32-bit subnet mask is used for the address pool. The workaround is to expand the address pool and use a 24-bit subnet mask for the pool.
Error: Session could not be established. Session limit of 2 reached.
Solution 1
This error occurs because the AnyConnect essential license is not supported by ASA version 8.0.4. You need to upgrade the ASA to version 8.2.2. This resolves the error.
Note: Regardless of the license used, if the session limit is reached, the user will receive the login failed error message.
Solution 2
This error can also occur if the vpn-sessiondb max-anyconnect-premium-or-essentials-limit session-limit command is used to set the limit of VPN sessions permitted to be established. If the session-limit is set as two, then the user cannot establish more than two sessions even though the license installed supports more sessions. Set the session-limit to the number of VPN sessions required in order to avoid this error message.
Error: Anyconnect not enabled on VPN server while trying to connect anyconnect to ASA
You receive the Anyconnect not enabled on VPN server error message when you try to connect AnyConnect to the ASA.
Solution
This error is resolved if you enable AnyConnect on the outside interface of the ASA with ASDM. For more information on how to enable AnyConnect on the outside interface, refer to Configure Clientless SSL VPN (WebVPN) on the ASA.
Error:- %ASA-6-722036: Group client-group User xxxx IP x.x.x.x Transmitting large packet 1220 (threshold 1206)
The %ASA-6-722036: Group User IP Transmitting large packet 1220 (threshold 1206) error message appears in the logs of the ASA. What does this log mean and how is this resolved?
Solution
This log message states that a large packet was sent to the client. The source of the packet is not aware of the MTU of the client. This can also be due to compression of non-compressible data. The workaround is to turn off the SVC compression with the svc compression none command. This resolves the issue.
Error: The secure gateway has rejected the agent’s vpn connect or reconnect request.
Solution
The router was missing pool configuration after reload. You need to add the concerned configuration back to the router.
The «The secure gateway has rejected the agent’s vpn connect or reconnect request. A new connection requires a re-authentication and must be started manually. Please contact the network administrator if the problem persists. The following message was received from the secure gateway: No License» error occurs when the AnyConnect mobility license is missing. Once the license is installed, the issue is resolved.
Error: «Unable to update the session management database»
Solution
This problem is related to memory allocation on the ASA. This issue is mostly encountered when the ASA Version is 8.2.1. Originally, this requires a 512MB RAM for its complete functionality.
As a permanent workaround, upgrade the memory to 512MB.
As a temporary workaround, try to free the memory with these steps:
Error: «The VPN client driver has encountered an error»
This is an error message obtained on the client machine when you try to connect to AnyConnect.
Solution
In order to resolve this error, complete this procedure in order to manually set the AnyConnect VPN agent to Interactive:
This sets the registry Type value DWORD to 110 (default is 010) for the HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesvpnagent.
Note: If this is to be used, then the preference would be to use the .MST transform in this instance. This is because if you set this manually with these methods, it requires that this be set after every install/upgrade process. This is why there is a need to identify the application that causes this problem.
When Routing and Remote Access Service (RRAS) is enabled on the Windows PC, AnyConnect fails with the The VPN client driver has encountered an error. error message. In order to resolve this issue, make sure that Routing and RRAS is disabled before starting AnyConnect. Refer to Cisco bug ID CSCsm54689 for more information.
Error: «Unable to process response from xxx.xxx.xxx.xxx»
Solution
In order to resolve this error, try these workarounds:
Solution
This error message occurs mostly because of configuration issues that are improper or an incomplete configuration. Check the configuration and make sure it is as required to resolve the issue.
Secure VPN via remote desktop is not supported error message appears.
Solution
This issue is due to these Cisco bug IDs: CSCsu22088 and CSCso42825. If you upgrade the AnyConnect VPN Client, it can resolve the issue. Refer to these bugs for more information.
Error: «The server certificate received or its chain does not comply with FIPS. A VPN connection will not be established»
When you attempt to VPN to the ASA 5505, the The server certificate received or its chain does not comply with FIPS. A VPN connection will not be established error message appears.
Solution
true
false
Then, restart the computer. Users must have administrative permissions in order to modify this file.
Error: «Certificate Validation Failure»
Users are unable to launch AnyConnect and receive the Certificate Validation Failure error.
Solution
Certificate authentication works differently with AnyConnect compared to the IPSec client. In order for certificate authentication to work, you must import the client certificate to your browser and change the connection profile in order to use certificate authentication. You also need to enable this command on your ASA in order to allow SSL client-certificates to be used on the outside interface:
ssl certificate-authentication interface outside port 443
Error: «VPN Agent Service has encountered a problem and needs to close. We are sorry for the inconvenience»
When AnyConnect Version 2.4.0202 is installed on a Windows XP PC, it stops at updating localization files and an error message shows that the vpnagent.exe fails.
Solution
This behavior is logged in Cisco bug ID CSCsq49102. The suggested workaround is to disable the Citrix client.
Error: «This installation package could not be opened. Verify that the package exists»
When AnyConnect is downloaded, this error message is received:
«Contact your system administrator. The installer failed with the following error: This installation package could not be opened. Verify that the package exists and that you can access it, or contact the application vendor to verify that this is a valid Windows Installer package.»
Solution
Complete these steps in order to fix this issue:
Error: «Error applying transforms. Verify that the specified transform paths are valid.»
This error message is recieved during the auto-download of AnyConnect from the ASA:
This is the error message received when connecting with AnyConnect for MacOS:
Solution
Complete one of these workarounds in order to resolve this issue:
If neither of these workarounds resolve the issue, contact Cisco Technical Support.
Error: «The VPN client driver has encountered an error»
This error is received:
Solution
This issue can be resolved when you uninstall the AnyConnect Client, and then remove the anti-virus software. After this, reinstall the AnyConnect Client. If this resolution does not work, then reformat the PC in order to fix this issue.
Error: «A VPN reconnect resulted in different configuration setting. The VPN network setting is being re-initialized. Applications utilizing the private network may need to be restored.»
This error is received when you try to launch AnyConnect:
Solution
In order to resolve this error, use this:
The svc mtu command is replaced by the anyconnect mtu command in ASA Version 8.4(1) and later as shown here:
AnyConnect Error While Logging In
Problem
The AnyConnect receives this error when it connects to the Client:
Solution
The issue can be resolved if you make these changes to the AnyConnect profile:
Add this line to the AnyConnect profile:
IE Proxy Setting is Not Restored after AnyConnect Disconnect on Windows 7
Problem
In Windows 7, if the IE proxy setting is configured for Automatically detect settings and AnyConnect pushes down a new proxy setting, the IE proxy setting is not restored back to Automatically detect settings after the user ends the AnyConnect session. This causes LAN issues for users who need their proxy setting configured for Automatically detect settings.
Solution
This behavior is logged in Cisco bug ID CSCtj51376. The suggested workaround is to upgrade to AnyConnect 3.0.
Error: AnyConnect Essentials can not be enabled until all these sessions are closed.
This error message is received on Cisco ASDM when you attempt to enable the AnyConnect Essentials license:
Solution
This is the normal behavior of the ASA. AnyConnect Essentials is a separately licensed SSL VPN client. It is entirely configured on the ASA and provides the full AnyConnect capability, with these exceptions:
This license cannot be used at the same time as the shared SSL VPN premium license. When you need to use one license, you need to disable the other.
Error: Connection tab on Internet option of Internet Explorer hides after getting connected to the AnyConnect client.
The connection tab on the Internet option of Internet Explorer hides after you are connected to the AnyConnect client.
Solution
This is due to the msie-proxy lockdown feature. If you enable this feature, it hides the Connections tab in Microsoft Internet Explorer for the duration of an AnyConnect VPN session. If you disable the feature, it leaves the display of the Connections tab unchanged.
Error: Few users getting Login Failed Error message when others are able to connect successfully through AnyConnect VPN
A few users receive the Login Failed Error message when others can connect successfully through the AnyConnect VPN.
Solution
This issue can be resolved if you make sure the do not require pre-authentication checkbox is checked for the users.
Error: The certificate you are viewing does not match with the name of the site you are trying to view.
During the AnyConnect profile update, an error is shown that says the certificate is invalid. This occurs with Windows only and at the profile update phase. The error message is shown here:
Solution
This can be resolved if you modify the server list of the AnyConnect profile in order to use the FQDN of the certificate.
This is a sample of the XML profile:
Cannot Launch AnyConnect From the CSD Vault From a Windows 7 Machine
When the AnyConnect is launched from the CSD vault, it does not work. This is attempted on Windows 7 machines.
Solution
Currently, this is not possible because it is not supported.
AnyConnect Profile Does Not Get Replicated to the Standby After Failover
The AnyConnect 3.0 VPN client with ASA Version 8.4.1 software works fine. However, after failover, there is no replication for the AnyConnect profile related configuration.
Solution
This problem has been observed and logged under Cisco bug ID CSCtn71662. The temporary workaround is to manually copy the files to the standby unit.
AnyConnect Client Crashes if Internet Explorer Goes Offline
When this occurs, the AnyConnect event log contains entries similar to these:
Solution
This behavior is observed and logged under Cisco bug ID CSCtx28970. In order to resolve this, quit the AnyConnect application and relaunch. The connection entries reappear after relaunch.
Error Message: TLSPROTOCOL_ERROR_INSUFFICIENT_BUFFER
The AnyConnect client fails to connect and the Unable to establish a connection error message is received. In the AnyConnect event log, the TLSPROTOCOL_ERROR_INSUFFICIENT_BUFFER error is found.
Solution
This occurs when the headend is configured for split-tunneling with a very large split-tunnel list (approximately 180-200 entries) and one or more other client attributes are configured in the group-policy, such as dns-server.
In order to resolve this issue, complete these steps:
For more information, refer to Cisco bug ID CSCtc41770.
Error Message: «Connection attempt has failed due to invalid host entry»
The Connection attempt has failed due to invalid host entry error message is received while AnyConnect is authenticated with the use of a certificate.
Solution
In order to resolve this issue, try either of these possible solutions:
For more information, refer to Cisco bug ID CSCti73316.
Error: «Ensure your server certificates can pass strict mode if you configure always-on VPN»
When you enable the Always-On feature on AnyConnect, the Ensure your server certificates can pass strict mode if you configure always-on VPN error message is received.
Solution
This error message implies that if you want to use the Always-On feature, you need a valid sever certificate configured on the headend. Without a valid server certificate, this feature does not work. Strict Cert Mode is an option that you set in the AnyConnect local policy file in order to ensure the connections use a valid certificate. If you enable this option in the policy file and connect with a bogus certificate, the connection fails.
Error: «An internal error occurred in the Microsoft Windows HTTP Services»
This Diagnostic AnyConnect Reporting Tool (DART) shows one failed attempt:
Also, refer to the event viewer logs on the Windows machine.
Solution
This could be caused due to a corrupted Winsock connection. Reset the connection from the command promt with this command and restart your windows machine:
netsh winsock reset
Error: «The SSL transport received a Secure Channel Failure. May be a result of a unsupported crypto configuration on the Secure Gateway.»
This Diagnostic AnyConnect Reporting Tool (DART) shows one failed attempt:
Solution
Windows 8.1 does not support RC4 according to the following KB update:
Either configure DES/3DES ciphers for SSL VPN on the ASA using the command «ssl encryption 3des-sha1 aes128-sha1 aes256-sha1 des-sha1» OR edit the Windows Registry file on the client machine as mentioned below:
Источник
Я получаю эту ошибку:
удаленный сертификат недействителен в соответствии с процедурой проверки.
всякий раз, когда я пытаюсь отправить электронную почту с помощью SMTP-сервера Gmail в моем коде C#.
Может ли кто-нибудь указать мне правильное направление для решения этой проблемы?
ниже приведена трассировка стека…
at System.Net.Security.SslState.StartSendAuthResetSignal(ProtocolToken message, AsyncProtocolRequest asyncRequest, Exception exception)
at System.Net.Security.SslState.CheckCompletionBeforeNextReceive(ProtocolToken message, AsyncProtocolRequest asyncRequest)
at System.Net.Security.SslState.StartSendBlob(Byte[] incoming, Int32 count, AsyncProtocolRequest asyncRequest)
at System.Net.Security.SslState.ProcessReceivedBlob(Byte[] buffer, Int32 count, AsyncProtocolRequest asyncRequest)
at System.Net.Security.SslState.StartReadFrame(Byte[] buffer, Int32 readBytes, AsyncProtocolRequest asyncRequest)
at System.Net.Security.SslState.StartReceiveBlob(Byte[] buffer, AsyncProtocolRequest asyncRequest)
at System.Net.Security.SslState.CheckCompletionBeforeNextReceive(ProtocolToken message, AsyncProtocolRequest asyncRequest)
at System.Net.Security.SslState.StartSendBlob(Byte[] incoming, Int32 count, AsyncProtocolRequest asyncRequest)
at System.Net.Security.SslState.ProcessReceivedBlob(Byte[] buffer, Int32 count, AsyncProtocolRequest asyncRequest)
at System.Net.Security.SslState.StartReadFrame(Byte[] buffer, Int32 readBytes, AsyncProtocolRequest asyncRequest)
at System.Net.Security.SslState.StartReceiveBlob(Byte[] buffer, AsyncProtocolRequest asyncRequest)
at System.Net.Security.SslState.CheckCompletionBeforeNextReceive(ProtocolToken message, AsyncProtocolRequest asyncRequest)
at System.Net.Security.SslState.StartSendBlob(Byte[] incoming, Int32 count, AsyncProtocolRequest asyncRequest)
at System.Net.Security.SslState.ProcessReceivedBlob(Byte[] buffer, Int32 count, AsyncProtocolRequest asyncRequest)
at System.Net.Security.SslState.StartReadFrame(Byte[] buffer, Int32 readBytes, AsyncProtocolRequest asyncRequest)
at System.Net.Security.SslState.StartReceiveBlob(Byte[] buffer, AsyncProtocolRequest asyncRequest)
at System.Net.Security.SslState.CheckCompletionBeforeNextReceive(ProtocolToken message, AsyncProtocolRequest asyncRequest)
at System.Net.Security.SslState.StartSendBlob(Byte[] incoming, Int32 count, AsyncProtocolRequest asyncRequest)
at System.Net.Security.SslState.ProcessReceivedBlob(Byte[] buffer, Int32 count, AsyncProtocolRequest asyncRequest)
at System.Net.Security.SslState.StartReadFrame(Byte[] buffer, Int32 readBytes, AsyncProtocolRequest asyncRequest)
at System.Net.Security.SslState.StartReceiveBlob(Byte[] buffer, AsyncProtocolRequest asyncRequest)
at System.Net.Security.SslState.CheckCompletionBeforeNextReceive(ProtocolToken message, AsyncProtocolRequest asyncRequest)
at System.Net.Security.SslState.StartSendBlob(Byte[] incoming, Int32 count, AsyncProtocolRequest asyncRequest)
at System.Net.Security.SslState.ProcessReceivedBlob(Byte[] buffer, Int32 count, AsyncProtocolRequest asyncRequest)
at System.Net.Security.SslState.StartReadFrame(Byte[] buffer, Int32 readBytes, AsyncProtocolRequest asyncRequest)
at System.Net.Security.SslState.StartReceiveBlob(Byte[] buffer, AsyncProtocolRequest asyncRequest)
at System.Net.Security.SslState.CheckCompletionBeforeNextReceive(ProtocolToken message, AsyncProtocolRequest asyncRequest)
at System.Net.Security.SslState.StartSendBlob(Byte[] incoming, Int32 count, AsyncProtocolRequest asyncRequest)
at System.Net.Security.SslState.ForceAuthentication(Boolean receiveFirst, Byte[] buffer, AsyncProtocolRequest asyncRequest)
at System.Net.Security.SslState.ProcessAuthentication(LazyAsyncResult lazyResult)
at System.Net.TlsStream.CallProcessAuthentication(Object state)
at System.Threading.ExecutionContext.Run(ExecutionContext executionContext, ContextCallback callback, Object state)
at System.Net.TlsStream.ProcessAuthentication(LazyAsyncResult result)
at System.Net.TlsStream.Write(Byte[] buffer, Int32 offset, Int32 size)
at System.Net.PooledStream.Write(Byte[] buffer, Int32 offset, Int32 size)
at System.Net.Mail.SmtpConnection.Flush()
at System.Net.Mail.SmtpConnection.GetConnection(String host, Int32 port)
at System.Net.Mail.SmtpTransport.GetConnection(String host, Int32 port)
at System.Net.Mail.SmtpClient.GetConnection()
at System.Net.Mail.SmtpClient.Send(MailMessage message)
at BulkEmail.frmemail.mailsending(String toaddress, String fromaddress, String fromname, String subject, String pwd, String attachements, String mailmessage, String htmlmessage, Int32 i, Int32 j, String replytoaddress)
Ошибки на connect server horizon C:ProgramDataVMwareVDMlogs
2022-09-13T11:11:08.024+03:00 ERROR (1238-1A54) <ajp-nio-127.0.0.1-8009-exec-7> [Connection4] Connection to the vCenter Server https://msk-vcsa01.adminbd.ru:443/sdk failed.
2022-09-13T11:11:08.031+03:00 DEBUG (1238-1A54) <ajp-nio-127.0.0.1-8009-exec-7> [Connection4] [EXCEPTION] Connection to the vCenter Server https://msk-vcsa01.adminbd.ru:443/sdk failed.: javax.xml.ws.WebServiceException: Could not send Message. com.vmware.vdi.logger.Logger.debug(Logger.java:44)
javax.xml.ws.WebServiceException: Could not send Message.
at org.apache.cxf.jaxws.JaxWsClientProxy.mapException(JaxWsClientProxy.java:183)
at org.apache.cxf.jaxws.JaxWsClientProxy.invoke(JaxWsClientProxy.java:145)
at com.sun.proxy.$Proxy273.retrieveServiceContent(Unknown Source)
at com.vmware.vdi.vcwrapper.Connection4.connect(SourceFile:199)
at com.vmware.vdi.vcwrapper.Connection4.connect(SourceFile:173)
at com.vmware.vdi.vcwrapper.ConnectionManager.getConnection4(SourceFile:93)
at com.vmware.vdi.vlsi.server.utils.certificate.VirtualCenterCertificateHandler.validate(VirtualCenterCertificateHandler.java:60)
at com.vmware.vdi.vlsi.server.utils.certificate.ServerSpecCertificateHandler.validate(ServerSpecCertificateHandler.java:42)
at com.vmware.vdi.vlsi.server.utils.certificate.ServerSpecCertificateHandler.validate(ServerSpecCertificateHandler.java:10)
at com.vmware.vdi.vlsi.server.utils.certificate.CertificateServer.validate(CertificateServer.java:58)
at com.vmware.vdi.vlsi.server.utils.certificate.CertificateServer.validate(CertificateServer.java:41)
at java.base/jdk.internal.reflect.NativeMethodAccessorImpl.invoke0(Native Method)
at java.base/jdk.internal.reflect.NativeMethodAccessorImpl.invoke(Unknown Source)
at java.base/jdk.internal.reflect.DelegatingMethodAccessorImpl.invoke(Unknown Source)
at java.base/java.lang.reflect.Method.invoke(Unknown Source)
at com.vmware.vdi.vlsi.rest.service.impl.VlsiMethodWrapper.invoke(VlsiMethodWrapper.java:49)
at com.vmware.vdi.vlsi.rest.reflect.impl.VlsiInvocation.invoke(VlsiInvocation.java:81)
at com.vmware.vdi.vlsi.rest.reflect.ReflectEngine.invokeService(ReflectEngine.java:79)
at com.vmware.vdi.vlsi.rest.RestApiServlet.doPost(RestApiServlet.java:145)
at javax.servlet.http.HttpServlet.service(HttpServlet.java:681)
at javax.servlet.http.HttpServlet.service(HttpServlet.java:764)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:231)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166)
at org.apache.catalina.filters.FailedRequestFilter.doFilter(FailedRequestFilter.java:97)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:193)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166)
at com.vmware.vdi.vlsi.rest.EncodingFilter.doFilter(EncodingFilter.java:37)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:193)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166)
at com.vmware.vdi.vlsi.rest.authentication.RestApiAuthFilter.doFilter(RestApiAuthFilter.java:143)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:193)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166)
at com.github.ziplet.filter.compression.CompressingFilter.doFilter(CompressingFilter.java:263)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:193)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166)
at org.apache.catalina.core.StandardWrapperValve.invoke(StandardWrapperValve.java:197)
at org.apache.catalina.core.StandardContextValve.invoke(StandardContextValve.java:97)
at org.apache.catalina.authenticator.AuthenticatorBase.invoke(AuthenticatorBase.java:543)
at org.apache.catalina.core.StandardHostValve.invoke(StandardHostValve.java:135)
at org.apache.catalina.core.StandardEngineValve.invoke(StandardEngineValve.java:78)
at org.apache.catalina.connector.CoyoteAdapter.service(CoyoteAdapter.java:367)
at org.apache.coyote.ajp.AjpProcessor.service(AjpProcessor.java:526)
at org.apache.coyote.AbstractProcessorLight.process(AbstractProcessorLight.java:65)
at org.apache.coyote.AbstractProtocol$ConnectionHandler.process(AbstractProtocol.java:882)
at org.apache.tomcat.util.net.NioEndpoint$SocketProcessor.doRun(NioEndpoint.java:1691)
at org.apache.tomcat.util.net.SocketProcessorBase.run(SocketProcessorBase.java:49)
at org.apache.tomcat.util.threads.ThreadPoolExecutor.runWorker(ThreadPoolExecutor.java:1191)
at org.apache.tomcat.util.threads.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:659)
at org.apache.tomcat.util.threads.TaskThread$WrappingRunnable.run(TaskThread.java:61)
at java.base/java.lang.Thread.run(Unknown Source)
Caused by: javax.net.ssl.SSLHandshakeException: SSLHandshakeException invoking https://msk-vcsa01.adminbd.ru:443/sdk: Certificates do not conform to algorithm constraints
at java.base/jdk.internal.reflect.NativeConstructorAccessorImpl.newInstance0(Native Method)
at java.base/jdk.internal.reflect.NativeConstructorAccessorImpl.newInstance(Unknown Source)
at java.base/jdk.internal.reflect.DelegatingConstructorAccessorImpl.newInstance(Unknown Source)
at java.base/java.lang.reflect.Constructor.newInstance(Unknown Source)
at org.apache.cxf.transport.http.HTTPConduit$WrappedOutputStream.mapException(HTTPConduit.java:1400)
at org.apache.cxf.transport.http.HTTPConduit$WrappedOutputStream.close(HTTPConduit.java:1384)
at org.apache.cxf.transport.AbstractConduit.close(AbstractConduit.java:56)
at org.apache.cxf.transport.http.HTTPConduit.close(HTTPConduit.java:671)
at org.apache.cxf.interceptor.MessageSenderInterceptor$MessageSenderEndingInterceptor.handleMessage(MessageSenderInterceptor.java:63)
at org.apache.cxf.phase.PhaseInterceptorChain.doIntercept(PhaseInterceptorChain.java:308)
at org.apache.cxf.endpoint.ClientImpl.doInvoke(ClientImpl.java:530)
at org.apache.cxf.endpoint.ClientImpl.invoke(ClientImpl.java:441)
at org.apache.cxf.endpoint.ClientImpl.invoke(ClientImpl.java:356)
at org.apache.cxf.endpoint.ClientImpl.invoke(ClientImpl.java:314)
at org.apache.cxf.frontend.ClientProxy.invokeSync(ClientProxy.java:96)
at org.apache.cxf.jaxws.JaxWsClientProxy.invoke(JaxWsClientProxy.java:140)
... 48 more
2022-09-13T10:02:03.532+03:00 ERROR (150C-1244) <ABSGC33> [cc] Error executing request
2022-09-13T10:03:52.516+03:00 ERROR (02B4-0674) <ajp-nio-127.0.0.1-8009-exec-8> [Connection4] Connection to the vCenter Server https://msk-vcsa01.adminbd.ru:443/sdk failed.
2022-09-13T10:03:52.579+03:00 ERROR (02B4-0674) <ajp-nio-127.0.0.1-8009-exec-8> [FaultUtilBase] UnexpectedFault: Unexpected failure during certificate validation.
2022-09-13T10:03:52.587+03:00 ERROR (02B4-0674) <ajp-nio-127.0.0.1-8009-exec-8> [RestApiServlet] Unexpected fault:(vdi.fault.UnexpectedFault) {
errorMessage = Unexpected failure during certificate validation.,
causeString = null,
causeStackTrace = null,
errorCode = CERTIFICATE_VALIDATION_FAILED,
errorAttributes = null
} for uri /view-vlsi/rest/v1/Certificate/Validate
2022-09-13T10:05:22.602+03:00 ERROR (02B4-143C) <ajp-nio-127.0.0.1-8009-exec-7> [Connection4] Connection to the vCenter Server https://msk-vcsa01.adminbd.ru:443/sdk failed.
2022-09-13T10:05:22.606+03:00 ERROR (02B4-143C) <ajp-nio-127.0.0.1-8009-exec-7> [FaultUtilBase] UnexpectedFault: Unexpected failure during certificate validation.
2022-09-13T10:05:22.607+03:00 ERROR (02B4-143C) <ajp-nio-127.0.0.1-8009-exec-7> [RestApiServlet] Unexpected fault:(vdi.fault.UnexpectedFault) {
errorMessage = Unexpected failure during certificate validation.,
causeString = null,
causeStackTrace = null,
errorCode = CERTIFICATE_VALIDATION_FAILED,
errorAttributes = null
} for uri /view-vlsi/rest/v1/Certificate/Validate
https://kb.vmware.com/s/article/89331
Заходим в ADSI Edit
- Измените первый выбор на Select или введите Distinguished Name и введите dc=vdi,dc=vmware,dc=int
- Измените второй выбор на Выберите или введите домен или сервер и введите localhost . Нажмите ОК .
3. Перейдите в « Свойства» > «Глобальные» . Справа дважды щелкните CN=Common .
4. pae-SSLClientSignatureSchemes LIST:rsa_pkcs1_sha256,rsa_pkcs1_sha384,rsa_pkcs1_sha512
5. Перезагрузка сервера. Делаем на каждом сервере Connection-Server .
Similar Posts:
Содержание
- Cisco certificate validation failure ошибка windows
- Вопрос
- Certificate validation failure cisco anyconnect как исправить
- 7 ответов
Cisco certificate validation failure ошибка windows
Вопрос
После апгрейда с Windows 7 до Windows 8 я, как и многие другие пользователи, столкнулся с проблемой подключения к офису через Cisco VPN Client. В моём случае под Windows 7 был установлен Cisco AnyConnect 2.5.6005, который работал без нареканий.
После апгрейда система сообщила, что AnyConnect требуется переустановить, но переустановка мне не помогла. Возникала ошибка Failed to enable Virtual Adapter. Симптомы были схожими, как описано в статье
Я всё же не стал ничего ковырять в системе и решил просто скачать последнюю версию Cisco AnyConnect c сайта cisco.com. На данный момент последняя версия 3.1.01065.
Но тут возникли другие проблемы. Cisco AnyConnect не видит SSL сертификат VPN сервера, настроенного на Cisco ASA 5510. Выдаёт следующее сообщение «No valid certificates available for authentication».
Сертификат для Cisco ASA 5510 выдавался нашим корпоративным центром сертификации по шаблону «WebServer». Этот сертификат, а также сертификат самого центра сертификации я импортировал в Доверенные корневые центры сертификации через консоль certmgr.msc. В списке сертификатов я их вижу и оба они действительные.
Но есть одно хитрое НО. Дело в том, что, если посмотреть список сертификатов через свойства обозревателя Internet Explorer (в закладке «Содержание» — «Сертификаты»), то почему-то сертификат Cisco ASA не отображается в списке Доверенных корневых центрах сертификации, как буд-то его нет в системе, а если открыть certmgr.msc, то там он есть! Чудеса. Сертификат от самого центра сертификации присутствует и там и тут.
Есть предположение, что Cisco AnyConnect смотрит сертификаты через свойства обозревателя и, не обнаруживая его там, выдаёт ошибку «No valid certificates available for authentication». Хотя повторюсь, что на Windows 7 никаких проблем с сертификатами не было.
Как заставить Cisco AnyConnect всё таки увидить сертификат?
Тот же самый вопрос, который я задавал сначала там
Certificate validation failure cisco anyconnect как исправить
Я установил безопасный мобильный клиент cisco anyconnect 4.2.01022 (+ все необходимые пакеты).
Затем добавили .pfx сертификатов в хранилище gnone2-key .
Затем я запустил cisco anyconnect, защищенный мобильный клиент, набрал, где подключиться, но cisco продолжает говорить мне, что Certificate validation failure
была создана, но не помогла. Как подключиться?
Таким образом, я извлек некоторые сертификаты в разных форматах:
Поместили все 4 из них в 3 разных местах:
Доверенные CA и корневые сертификаты
UPD2: пытался настроить cisco anyconnect, совместимый с openconnect (который интегрирован в сетевой центр linux): Он просит установить:
Но если пытается подключиться:
Я принимаю – и ту же ошибку Ошибка проверки сертификата, полный журнал:
PS: На окнах выполняются одинаковые шаги, добавлен сертификат двойным щелчком, затем запускается клиент cisco, набирается сервер, затем он спрашивает пароль на сервере, которого я хочу, – и затем я был подключен.
Когда я пытаюсь подключиться, используя Cisco AnyConnect VPN Client, я получаю эту ошибку:
Попытка подключения не удалась из-за проблемы с сертификатом сервера .
У меня была эта проблема в моей предыдущей установке Ubuntu 11.10. Тогда я мог бы исправить это, используя некоторые учебники в Интернете (я не помню, какой именно). В основном они предложили установить 4-5 пакетов, а затем и несколько ln -s . Но на этот раз никто из них не работает. Может ли кто-нибудь помочь мне шаг за шагом?
7 ответов
Я могу подтвердить, что эта проблема существует. Клиент Anyconnect работал нормально с 11.10, но перестает работать с 12.04. Старый трюк со ссылками на библиотеки Firefox больше не работает. Я использую OpenConnect.
Подробнее о проблеме Cisco Anyconnect:
Как видно из журнала: пользователь был удалось войти, но клиенту Anyconnect все еще не удалось установить vpn-соединение.
Клиент Cisco AnyConnect VPN (версия 2.5.3055).
Убедитесь, что у вас установлен Firefox и вы можете его успешно запустить. Если все прошло успешно, попробуйте выполнить еще несколько шагов по устранению неполадок.
Вот как я это сделал.
Затем я выяснил, какой центр сертификации мы используем, а именно COMODO, нашел сайт, который использует этот ЦС, загрузил его с помощью браузера и поместил в
Проблема решена в Ubuntu 12.04 64 бит. смотрите здесь: http://www.oit.uci.edu/security/vpn/vpn-lin.html
У меня сработало следующее исправление – новая установка 12.04 LTS 32bit (с Firefox 12). Установил клиент AnyConnect, затем попытался запустить его.
Получил это сообщение:
AnyConnect не может подтвердить, что он подключен к вашему безопасному шлюзу. Локальная сеть может быть ненадежной. Пожалуйста, попробуйте другую сеть.
Проверен системный журнал в Ubuntu. Много такого рода вещей:
Создано / .cisco/certificates/ca каталогов в /opt с использованием sudo
Мы используем Globalsign в качестве нашего центра сертификации. Поэтому я просто скопировал все файлы Globalsign .pem из /etc/ssl/certs . Если вы не знаете своего провайдера, вы можете просто скопировать все.
или если CA неизвестен
Мне удалось запустить клиент AnyConnect и подключиться к VPN
Надеюсь, это поможет.
Я попробовал эти решения, перечисленные выше, и ни одно из них не помогло. Но когда я попробовал некоторые из приведенных ниже решений, связанных с библиотеками Firefox, я добился успеха!
Я не могу сказать, какое решение является ЛУЧШИМ, но я следовал указаниям на обоих этих сайтах и имел успех. Возможно, вы можете найти решение, которое работает для вас. Если вы знаете, какой из них лучший, пожалуйста, сообщите нам, какая переменная решает проблему немедленно. Все, что я знаю, это то, что после внесения некоторых из этих изменений я наконец-то заработал на своей Cisco Anyconnect VPN. Я Firefox на Ubuntu 12.04.
Сразу хочу отметить, — не собираюсь устраивать холивар на счет того, что лучше — ASDM or console: на вкус и цвет все фломастеры разные…Я предпочитаю ASDM и настройки такого плана произвожу именно через нее. Поэтому статья будет насыщенна картинками (скринами)
Итак, приступим. Начнем с настройки LDAP сервера (в нашем случае это DC ActiveDirectory), для этого переходим в Configuration > DeviceManagement > Users/AAA > AAA Server Groups и создаем группу, назовем ее OFFICE, Protocol указываем LDAP
Configuration Cisco ASA AAA Server Groups
Для того, чтобы добавить сервер в созданную группу, нам необходимо предварительно создать LDAP Atribute Map. Для этого переходим в соответствующий раздел: Configuration > DeviceManagement > Users/AAA >LDAP Attribute Map и создаем новую карту: в нашем случае это Map Name: AD, Mapping of Attribute Name > LDAP Attribute Name: memberOf, Cisco Attribute Name: IETF-Radius-Class
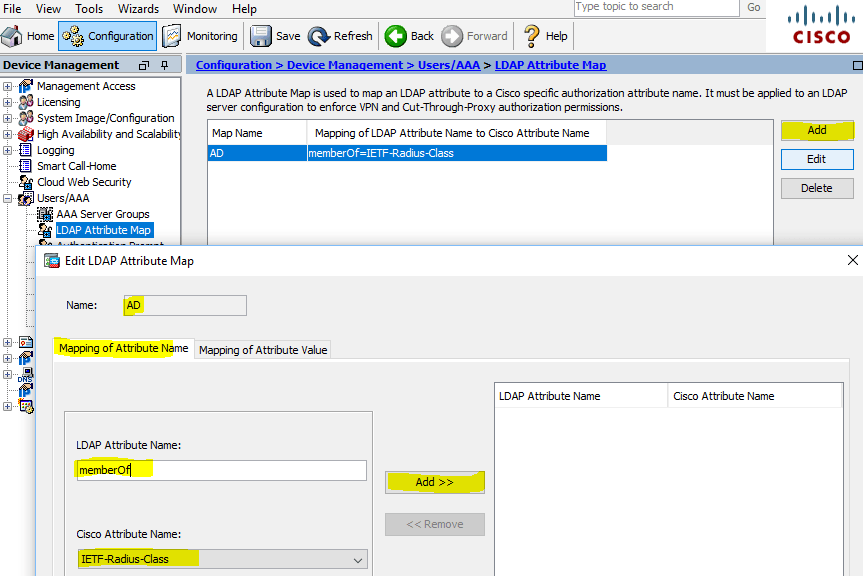
LDAP Attribute Map
Теперь можно добавить сервер (настроить подключение к контроллеру домена), указываем интерфейс, через который будем подключаться, IP адрес DC, Server Type: Microsoft, Base DN, Naming Attribute: sAMAccountName, Login DN, Login Password, только что созданную карту LDAP Attribute Map: AD, Group Base DN:
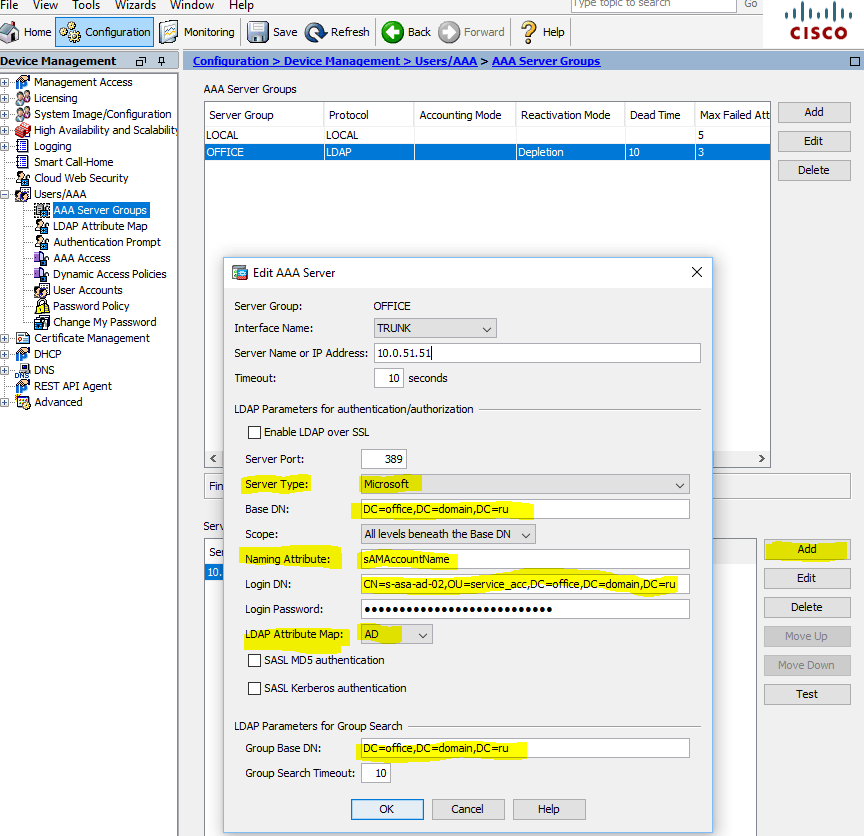
AAA Server — Microsoft DC
Add AAA Server
После добавления сервера делаем проверку, проходим аутентификацию учетной записью AD:
Test AAA Server — Authentication
Теперь можно добавить сертификат удостоверяющего центра (используется Microsoft CA, в рамках статьи о его настройке рассказывать не буду, единственное о чем следует обязательно помнить: Cisco ASA не воспринимает сертификаты с Signature algorithm RSASSA-PSS, который Microsoft предлагает использовать по умолчанию. мы меняли на sha512RSA):
Identity Certificates Signature algorithm RSASSA-PSS — sha512
Переходим Configuration > DeviceManagement >Certificate Management > Identity Certificates и импортируем в формате PKCS12 (*.pfx сертификат + private key):

Identity Certificates Signature algorithm sha512RSA (ECDSA 521 bits)
С подготовительными действиями закончили, можно переходить к настройке профилей для AnyConnect VPN. Для примера, будем использовать 2 профиля, у которых будут разные IP Address Pools и соотв. ACL, Dynamic Access Policies, Group Policies и соответственно 2 группы ActiveDirectory. При подключении пользователей по ВПН используем политику «Туннелирование только указанных сетей», так называемый Split Tunneling, чтобы не гнать весь пользовательский траффик через впн. Но это «на любителя», может кому-то, наоборот, такое потребуется — последнее время это очень актуально 😉
Начнем с IP Address Pools, для этого переходим в Configuration > Remote Access VPN > Network (Client) Access > Address Assignment > Address Pools
Создадим пул адресов (сегмент) для администраторов (назовем, например VPN_Admins):
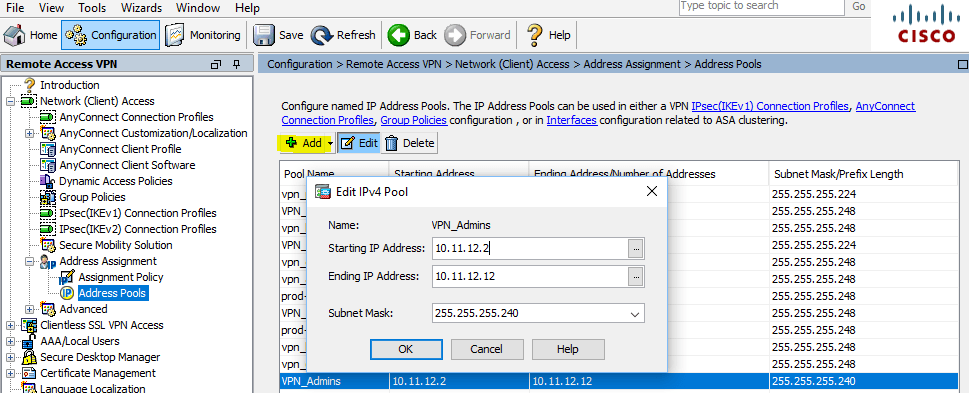
Address Assignment — Address Pools
Далее создадим политику (это основная часть настроеек профиля, в которой можно задат: протоколы, которые будут использоваться для туннелей, время доступа, количество одновременных логинов, закрыть доступы к определенным VLAN, выставить таймауты, задать DNS серверы, настроить Split Tunneling, клиентский файерволл и тд и тп) — в общем этой настройке следует уделить особое внимание! Итак, начнем: Configuration > Remote Access VPN > Network (Client) Access > Group Policies, Add Internal Group Policy
Все выставленные параметры сугубо индивидуальны — в нашем случае немного параноидальны Указаны протоколы, которые допускаются для создания туннеля (Tunneling Protocols), временной период для доступа по ВПН (Access Hours), количество одновременных подключений с одной учетной записью (Simultaneous Logins), максимальное время для сеанса и пр.:
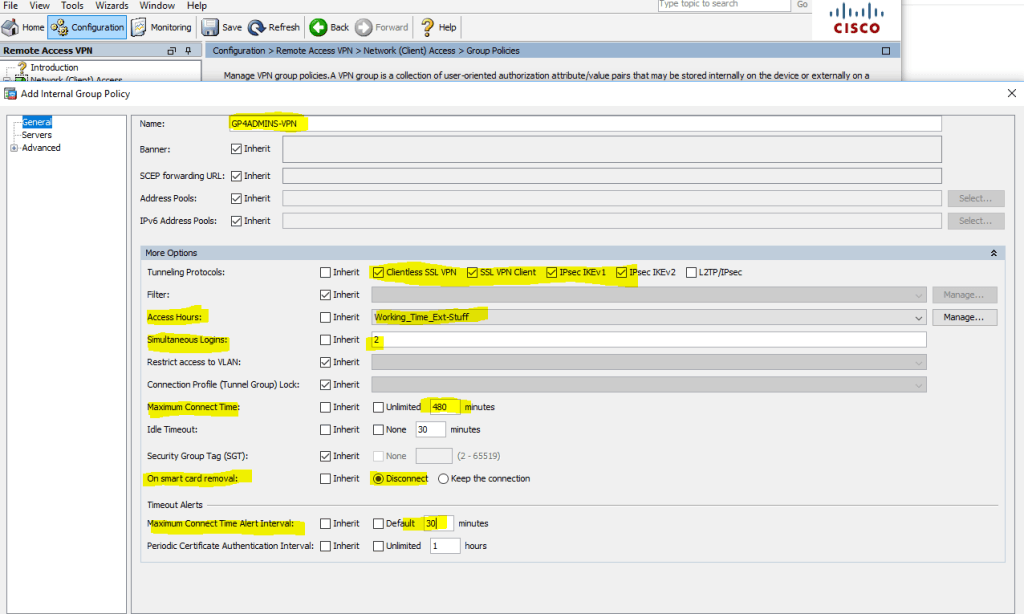
Configuration > Remote Access VPN > Network (Client) Access > Group Policies > Add Internal Group Policy
Следующая полезная настройка — вкладка Servers, в которой мы можем указать внутр. ДНС серверы, для пользователей ВПН AnyConnect, чтобы они могли обращаться к внутренним ресурсам по имени:
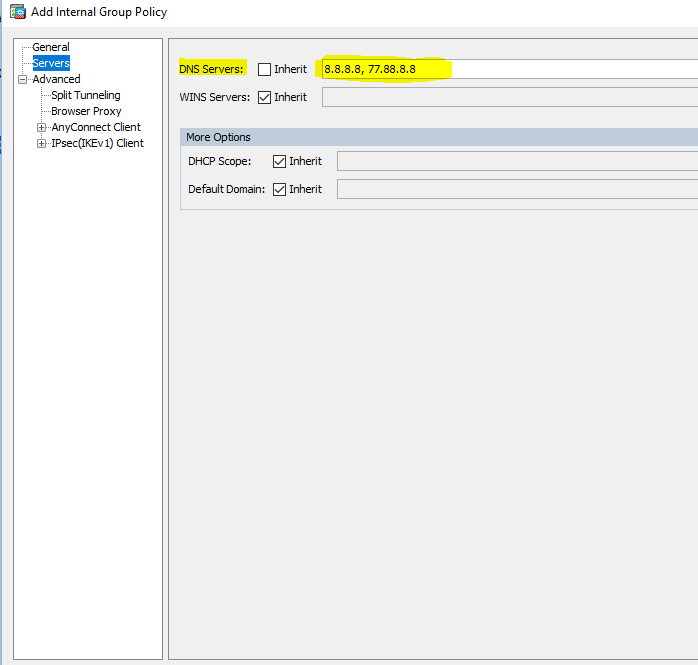
Configuration > Remote Access VPN > Network (Client) Access > Group Policies > Edit Internal Group Policy — Servers
Теперь перейдем к еще одной интересной опции — настройке Split Tunneling. Как я уже писал ранее — будем использовать политику «туннелирование только указанных сетей» (мы не заворачиваем в туннель весь траффик пользователей и разрешаем доступ к локальным ресурсам — опция «Local Lan Access» далее будет отдельно рассмотрена):
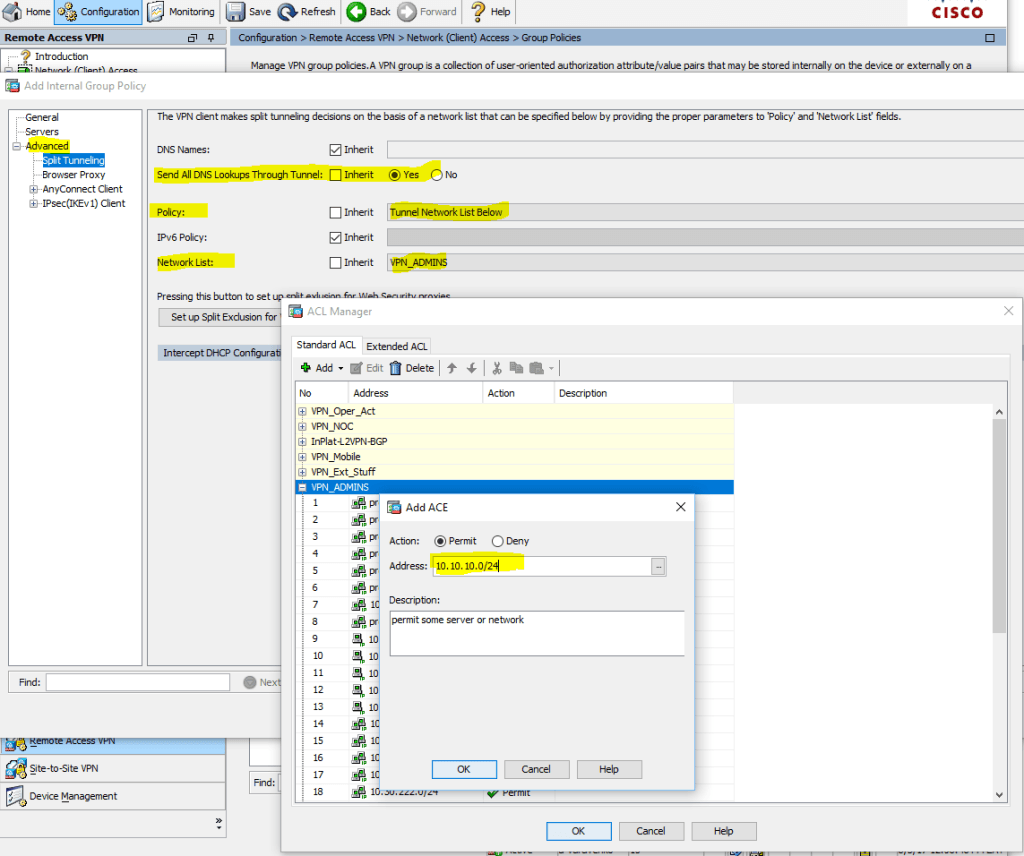
Configuration > Remote Access VPN > Network (Client) Access > Group Policies > Edit Internal Group Policy > Advanced > Split Tunneling >
Ранее мы указали к каким сетямхостам мы разрешили доступ, теперь ограничим доступ к ним по протоколампортам (еще один ACL):

Configuration > Remote Access VPN > Network (Client) Access > Group Policies > Edit Internal Group Policy > Advanced > AnyConnect Client > Client Firewall > Private Network Rule
В итоге, после подключения к впн AnyConnect клиентом, можно увидеть маршруты в сторону туннеля и правила файерволла:

AnyConnect Client > Route Details
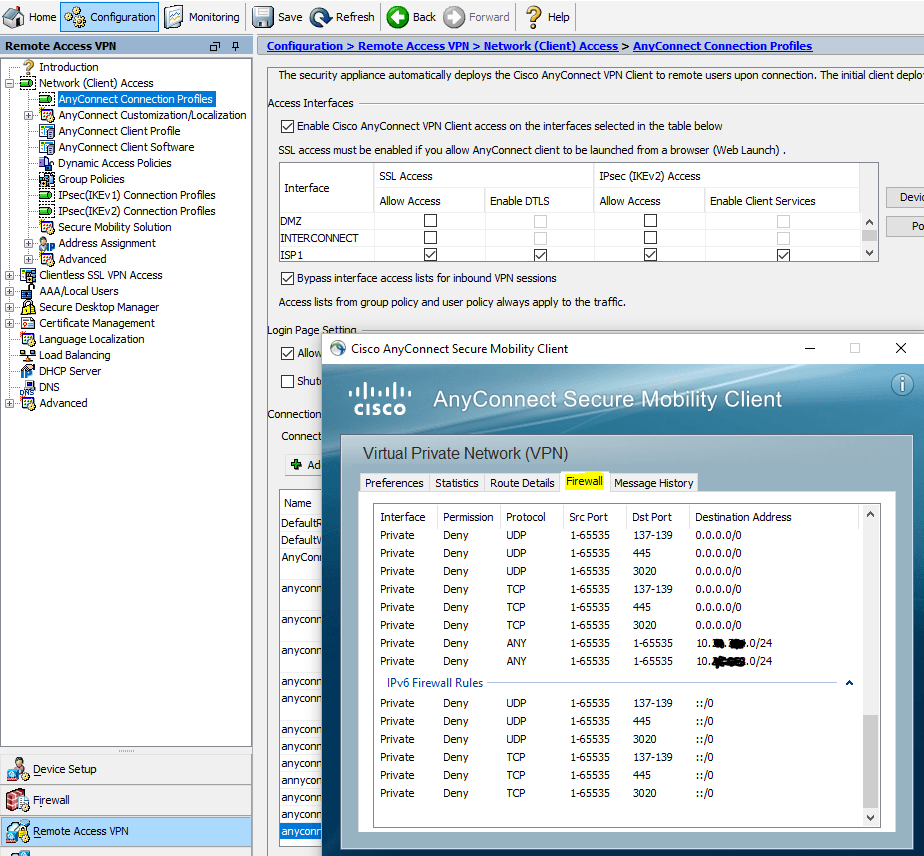
AnyConnect Client > Firewall
Теперь можно перейти непосредственно к созданию профиля AnyConnect, переходим Configuration > Remote Access VPN > Network (Client) Access > AnyConnect Connection Profiles >, Add AnyConnect Connection Profile
и указываем: Name, Aliases, далее Authentication Method (AAA and certificate), AAA Server Group, Client Address Pools, Group Policy — все созданное ранее!

Configuration > Remote Access VPN > Network (Client) Access > AnyConnect Connection Profiles > Add AnyConnect Connection Profile > Basic
И теперь небольшой «лайфхак» — мы из пользовательского сертификата вытащим значение E-mail и с помощью регулярки (.*)@ отрежем от него @domain.ru
(значение E-mail должно быть %AD username%@somedomain.ru ) и подставим его в поле Username при подключении.

Configuration > Remote Access VPN > Network (Client) Access > AnyConnect Connection Profiles > Add AnyConnect Connection Profile > Advanced > Authentication > Username Mapping from Certificate
Когда профили настроили — мы уже можем подключаться, потому как будет отрабатывать политика по умолчанию DfltAccessPolicy для всех пользователей, прошедших аутентификацию (у нее самый высокий приоритет). Мы же хотим, чтобы для разных групп ActiveDirectory использовался свой профиль и отрабатывала своя групповая политика политика доступа. Поэтому, переходим: Configuration > Remote Access VPN > Network (Client) Access > Dynamic Access Policies и запрещаем DfltAccessPolicy (на самом деле не запрещаем, а делаем Terminate с уведомлением пользователя — хорошая диагностика того, что пользователь не включен в требую группу ActiveDirectory):
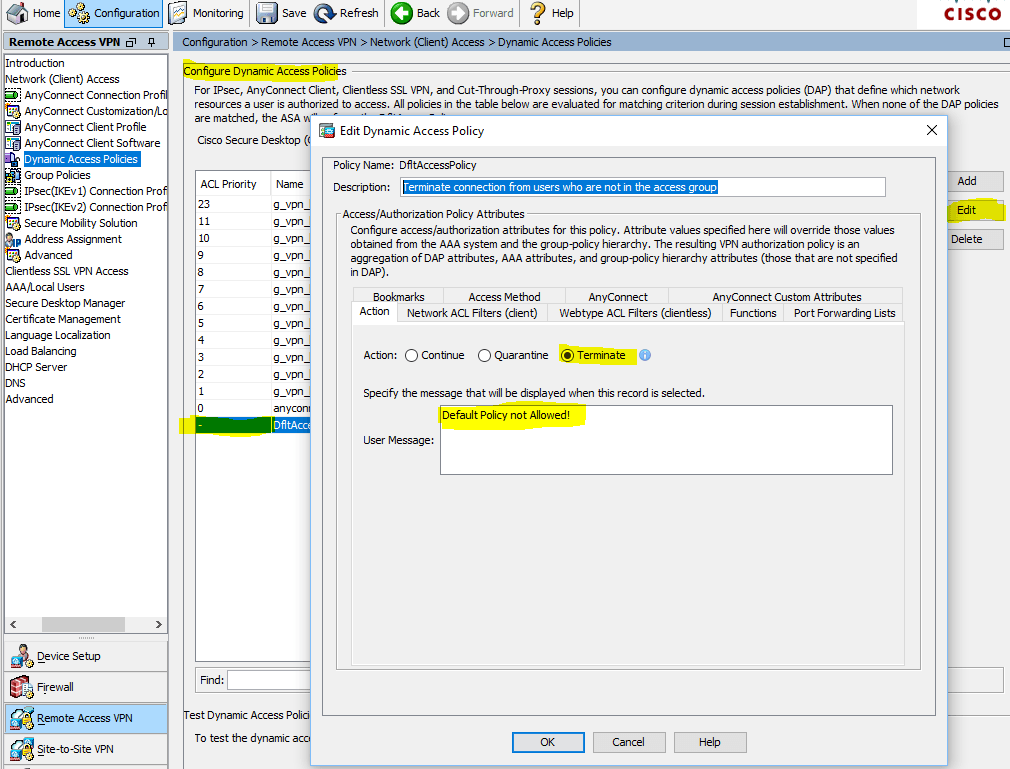
Configuration > Remote Access VPN > Network (Client) Access > Dynamic Access Policies
Terminate connection from users who are not in the access group
После того, как политику по умолчанию запретили, — создадим новую:
Configuration > Remote Access VPN > Network (Client) Access > Dynamic Access Policies > Add Dynamic Access Policy

Configuration > Remote Access VPN > Network (Client) Access > Dynamic Access Policies > Add Dynamic Access Policy with AAA Attributes
где g_vpn_level_01 — созданная в ActiveDirectory группа безопасности, куда мы включаем необходимые админские учетки, для подключения по ВПН AnyConnect с профилем VPN-ADMINS:

Configuration > Remote Access VPN > Network (Client) Access > Dynamic Access Policies > Add Dynamic Access Policy with AAA Attributes > Get AD Groups
ну и заключительный «штрих» — рекомендую сохранить созданный профиль в файл (полезно, например, для синхронизации профилей для StandBy unit при Failover конфигурации):
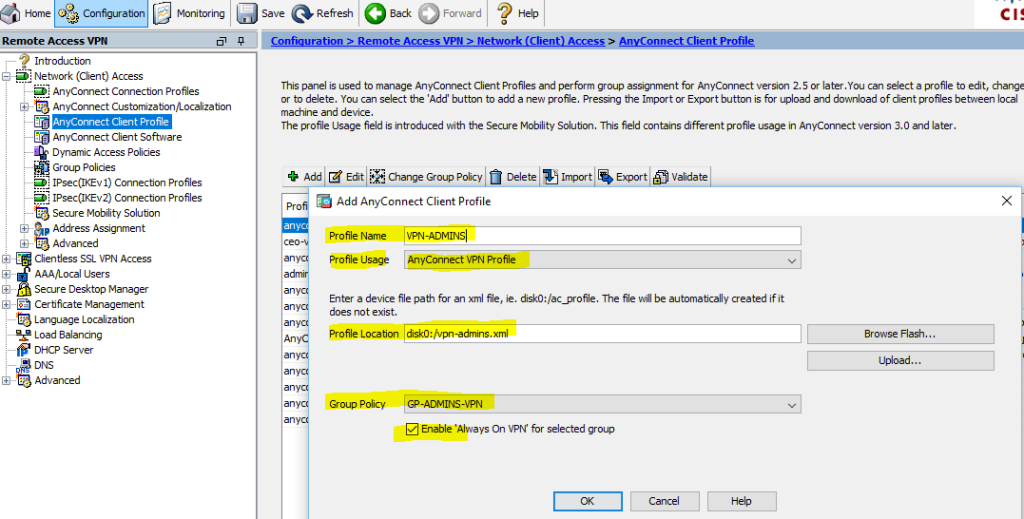
Configuration > Remote Access VPN > Network (Client) Access > AnyConnect Client Profile
После того, как профиль сохранен — его можно немного «потюнинговать»: помните я говорил про опцию»Local Lan Access«? Она как раз здесь настраивается. А еще здесь же можно настроить выбор хранилища сертификатов; автообновление клиента AnyConnect; разрешитьзапретить возможность подключения к компьютеру через рдп, при подключенном впн; указать версию протокола (IPv4 or IPv6 or both); параметры сертификатов и серверов; мобильные политики. В общем — есть, что «подкрутить» под ваши нужды!
Configuration > Remote Access VPN > Network (Client) Access > AnyConnect Client Profile > Edit
Для второй группы — «VPN-USERS» проделываем тоже самое…
Using Ubuntu Focal fossa. I was trying to install a checkpoint ssl software for VPN, but seems like something messed up all my certificates. Now whenever I try
sudo apt-get update
I get the following errors.
Get:1 file:/var/cudnn-local-repo-ubuntu2004-8.3.1.22 InRelease
Ign:1 file:/var/cudnn-local-repo-ubuntu2004-8.3.1.22 InRelease
Get:2 file:/var/cudnn-local-repo-ubuntu2004-8.3.1.22 Release [564 B]
Get:2 file:/var/cudnn-local-repo-ubuntu2004-8.3.1.22 Release [564 B]
Ign:3 https://dl.google.com/linux/chrome/deb stable InRelease
Ign:4 https://gitlab.com/feren-os/feren-repositories-neon-focal/raw/master stable InRelease
Err:5 https://dl.google.com/linux/chrome/deb stable Release
Certificate verification failed: The certificate is NOT trusted. The certificate issuer is unknown. Could not handshake: Error in the certificate verification. [IP: 74.125.68.91 443]
Ign:6 https://dl.winehq.org/wine-builds/ubuntu focal InRelease
Ign:7 https://gitlab.com/feren-os/feren-repositories-focal/raw/master stable InRelease
Err:8 https://dl.winehq.org/wine-builds/ubuntu focal Release
Certificate verification failed: The certificate is NOT trusted. The certificate issuer is unknown. Could not handshake: Error in the certificate verification. [IP: 199.232.46.217 443]
Ign:9 https://packages.microsoft.com/repos/azure-cli focal InRelease
Err:10 https://gitlab.com/feren-os/feren-repositories-neon-focal/raw/master stable Release
Certificate verification failed: The certificate is NOT trusted. The certificate issuer is unknown. Could not handshake: Error in the certificate verification. [IP: 172.65.251.78 443]
Ign:11 https://packages.microsoft.com/repos/ms-teams stable InRelease
Err:12 https://gitlab.com/feren-os/feren-repositories-focal/raw/master stable Release
Certificate verification failed: The certificate is NOT trusted. The certificate issuer is unknown. Could not handshake: Error in the certificate verification. [IP: 172.65.251.78 443]
Err:13 https://packages.microsoft.com/repos/azure-cli focal Release
Certificate verification failed: The certificate is NOT trusted. The certificate issuer is unknown. Could not handshake: Error in the certificate verification. [IP: 40.65.182.21 443]
Ign:14 https://download.docker.com/linux/ubuntu focal InRelease
Ign:15 https://desktop-download.mendeley.com/download/apt stable InRelease
Err:16 https://packages.microsoft.com/repos/ms-teams stable Release
Certificate verification failed: The certificate is NOT trusted. The certificate issuer is unknown. Could not handshake: Error in the certificate verification. [IP: 40.65.182.21 443]
Err:17 https://download.docker.com/linux/ubuntu focal Release
Certificate verification failed: The certificate is NOT trusted. The certificate issuer is unknown. Could not handshake: Error in the certificate verification. [IP: 13.33.33.8 443]
Err:19 https://desktop-download.mendeley.com/download/apt stable Release
Certificate verification failed: The certificate is NOT trusted. The certificate issuer is unknown. Could not handshake: Error in the certificate verification. [IP: 162.159.130.86 443]
Ign:20 https://packagecloud.io/AtomEditor/atom/any any InRelease
Ign:21 https://developer.download.nvidia.com/compute/cuda/repos/ubuntu2004/x86_64 InRelease
Err:22 https://developer.download.nvidia.com/compute/cuda/repos/ubuntu2004/x86_64 Release
Certificate verification failed: The certificate is NOT trusted. The certificate issuer is unknown. Could not handshake: Error in the certificate verification. [IP: 152.199.39.144 443]
Hit:23 http://archive.ubuntu.com/ubuntu focal InRelease
Hit:24 http://archive.canonical.com/ubuntu focal InRelease
Ign:25 http://repo.vivaldi.com/stable/deb stable InRelease
Hit:26 http://repo.vivaldi.com/stable/deb stable Release
Hit:27 http://deb.volian.org/volian scar InRelease
Get:28 http://archive.ubuntu.com/ubuntu focal-updates InRelease [114 kB]
Hit:29 http://ppa.launchpad.net/alessandro-strada/ppa/ubuntu focal InRelease
Err:30 https://packagecloud.io/AtomEditor/atom/any any Release
Certificate verification failed: The certificate is NOT trusted. The certificate issuer is unknown. Could not handshake: Error in the certificate verification. [IP: 52.52.107.175 443]
Get:31 http://security.ubuntu.com/ubuntu focal-security InRelease [114 kB]
Hit:33 http://ppa.launchpad.net/inkscape.dev/stable/ubuntu focal InRelease
Get:34 http://archive.ubuntu.com/ubuntu focal-backports InRelease [108 kB]
Reading package lists... Done
W: https://dl.google.com/linux/chrome/deb/dists/stable/InRelease: No system certificates available. Try installing ca-certificates.
W: https://gitlab.com/feren-os/feren-repositories-neon-focal/raw/master/dists/stable/InRelease: No system certificates available. Try installing ca-certificates.
W: https://dl.google.com/linux/chrome/deb/dists/stable/Release: No system certificates available. Try installing ca-certificates.
W: https://dl.winehq.org/wine-builds/ubuntu/dists/focal/InRelease: No system certificates available. Try installing ca-certificates.
W: https://gitlab.com/feren-os/feren-repositories-focal/raw/master/dists/stable/InRelease: No system certificates available. Try installing ca-certificates.
E: The repository 'https://dl.google.com/linux/chrome/deb stable Release' no longer has a Release file.
N: Updating from such a repository can't be done securely, and is therefore disabled by default.
N: See apt-secure(8) manpage for repository creation and user configuration details.
W: https://dl.winehq.org/wine-builds/ubuntu/dists/focal/Release: No system certificates available. Try installing ca-certificates.
W: https://packages.microsoft.com/repos/azure-cli/dists/focal/InRelease: No system certificates available. Try installing ca-certificates.
E: The repository 'https://dl.winehq.org/wine-builds/ubuntu focal Release' no longer has a Release file.
N: Updating from such a repository can't be done securely, and is therefore disabled by default.
N: See apt-secure(8) manpage for repository creation and user configuration details.
W: https://gitlab.com/feren-os/feren-repositories-neon-focal/raw/master/dists/stable/Release: No system certificates available. Try installing ca-certificates.
E: The repository 'https://gitlab.com/feren-os/feren-repositories-neon-focal/raw/master stable Release' no longer has a Release file.
N: Updating from such a repository can't be done securely, and is therefore disabled by default.
N: See apt-secure(8) manpage for repository creation and user configuration details.
W: https://packages.microsoft.com/repos/ms-teams/dists/stable/InRelease: No system certificates available. Try installing ca-certificates.
W: https://gitlab.com/feren-os/feren-repositories-focal/raw/master/dists/stable/Release: No system certificates available. Try installing ca-certificates.
E: The repository 'https://gitlab.com/feren-os/feren-repositories-focal/raw/master stable Release' no longer has a Release file.
N: Updating from such a repository can't be done securely, and is therefore disabled by default.
N: See apt-secure(8) manpage for repository creation and user configuration details.
W: https://packages.microsoft.com/repos/azure-cli/dists/focal/Release: No system certificates available. Try installing ca-certificates.
W: https://download.docker.com/linux/ubuntu/dists/focal/InRelease: No system certificates available. Try installing ca-certificates.
E: The repository 'https://packages.microsoft.com/repos/azure-cli focal Release' no longer has a Release file.
N: Updating from such a repository can't be done securely, and is therefore disabled by default.
N: See apt-secure(8) manpage for repository creation and user configuration details.
W: https://desktop-download.mendeley.com/download/apt/dists/stable/InRelease: No system certificates available. Try installing ca-certificates.
W: https://packages.microsoft.com/repos/ms-teams/dists/stable/Release: No system certificates available. Try installing ca-certificates.
W: https://download.docker.com/linux/ubuntu/dists/focal/Release: No system certificates available. Try installing ca-certificates.
E: The repository 'https://packages.microsoft.com/repos/ms-teams stable Release' no longer has a Release file.
N: Updating from such a repository can't be done securely, and is therefore disabled by default.
N: See apt-secure(8) manpage for repository creation and user configuration details.
E: The repository 'https://download.docker.com/linux/ubuntu focal Release' no longer has a Release file.
N: Updating from such a repository can't be done securely, and is therefore disabled by default.
N: See apt-secure(8) manpage for repository creation and user configuration details.
W: https://desktop-download.mendeley.com/download/apt/dists/stable/Release: No system certificates available. Try installing ca-certificates.
E: The repository 'https://desktop-download.mendeley.com/download/apt stable Release' no longer has a Release file.
N: Updating from such a repository can't be done securely, and is therefore disabled by default.
N: See apt-secure(8) manpage for repository creation and user configuration details.
W: https://packagecloud.io/AtomEditor/atom/any/dists/any/InRelease: No system certificates available. Try installing ca-certificates.
W: https://developer.download.nvidia.com/compute/cuda/repos/ubuntu2004/x86_64/InRelease: No system certificates available. Try installing ca-certificates.
W: https://developer.download.nvidia.com/compute/cuda/repos/ubuntu2004/x86_64/Release: No system certificates available. Try installing ca-certificates.
E: The repository 'https://developer.download.nvidia.com/compute/cuda/repos/ubuntu2004/x86_64 Release' no longer has a Release file.
N: Updating from such a repository can't be done securely, and is therefore disabled by default.
N: See apt-secure(8) manpage for repository creation and user configuration details.
W: https://packagecloud.io/AtomEditor/atom/any/dists/any/Release: No system certificates available. Try installing ca-certificates.
E: The repository 'https://packagecloud.io/AtomEditor/atom/any any Release' no longer has a Release file.
N: Updating from such a repository can't be done securely, and is therefore disabled by default.
what’s the way out, save the nuclear option of reinstalling everything?
N: See apt-secure(8) manpage for repository creation and user configuration details.
N: Skipping acquire of configured file 'main/binary-i386/Packages' as repository 'http://deb.volian.org/volian scar InRelease' doesn't support architecture 'i386'