При попытке ручной репликации данных между контроллерами домена Active Directory в остатке Active Directory Sites and Services (dssite.msc) появилась ошибка:
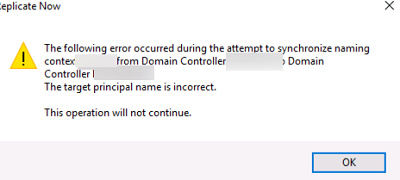
The following error occurred during the attempt to synchronize naming context from Domain Controller X to Domain Controller Y. The target principal name is incorrect. This operation will not continue.
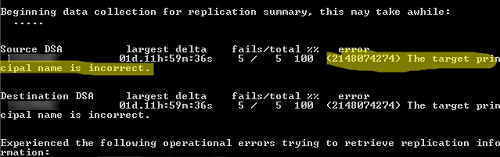
При проверке репликации с помощью repadmin, у одного из DC появляется ошибка:
(2148074274) The target principal name is incorrect.
В журнале событий DC есть такие ошибки:
Source: Security-Kerberos
Event ID: 4
The Kerberos client received a KRB_AP_ERR_MODIFIED error from the server DC2. The target name used was cifs/DC2.winitpro.ru. This indicates that the target server failed to decrypt the ticket provided by the client. This can occur when the target server principal name (SPN) is registered on an account other than the account the target service is using. Ensure that the target SPN is only registered on the account used by the server. This error can also happen if the target service account password is different than what is configured on the Kerberos Key Distribution Center for that target service. Ensure that the service on the server and the KDC are both configured to use the same password. If the server name is not fully qualified, and the target domain (winitpro.ru) is different from the client domain (winiptro.ru), check if there are identically named server accounts in these two domains, or use the fully-qualified name to identify the server.
Event ID 3210:
Failed to authenticate with \DC, a Windows NT domain controller for domain WINITPRO.
Event ID 5722:
The session setup from the computer 1 failed to authenticate. The name of the account referenced in the security database is 2. The following error occurred:
В первую очередь проверьте:
- Доступность проблемного контроллера домена с помощью простого ICMP ping
- Проверьте, что на нем доступен порт TCP 445 и опубликованы сетевые папки SysVol и NetLogon;
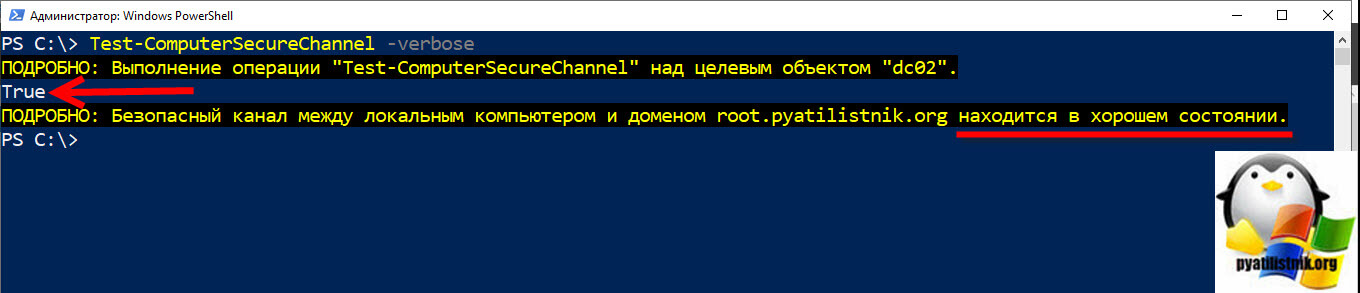
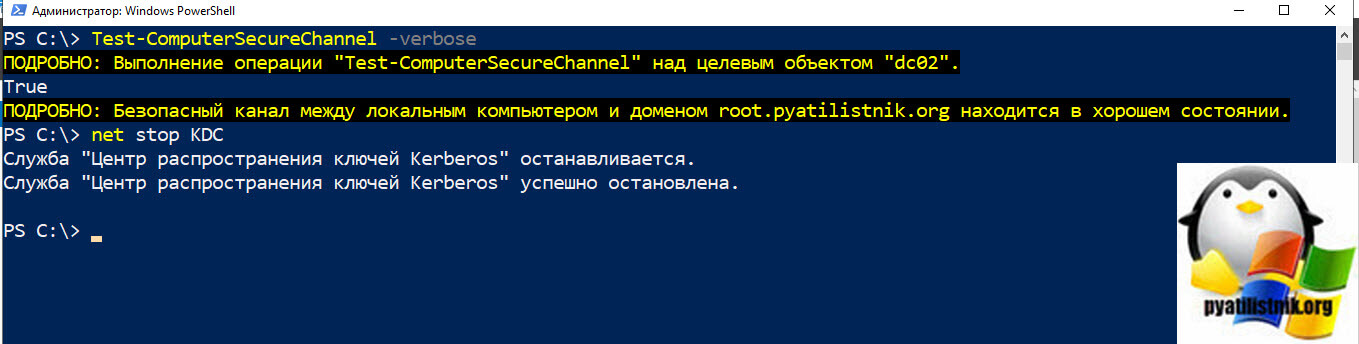
Если все ОК, значит проблема в том, между контроллерами домена нарушен безопасный канал передачи данных. Проверьте его с помощью PowerShell команды:
Test-ComputerSecureChannel -Verbose
Служба KDC на целевом контроллере домена не может расшифровать тикет Kerberos из-за того, что в ней хранится старый пароль этого контроллера домена.
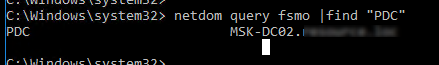
Чтобы исправить проблему, нужно сбросить этот пароль. Сначала нужно найти текущий контроллер домена с FSMO ролью PDC.
netdom query fsmo |find "PDC"
В нашем примере PDC находится на MSK-DC02. Мы будем исопользовать это имя в команде
netdom resetpwd
далее.
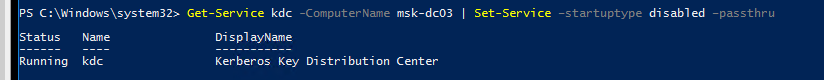
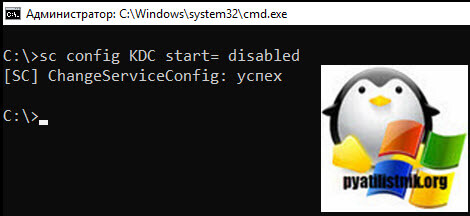
Остановите службу Kerberos Key Distribution Center (KDC) на контроллере домена, на котором появляется ошибка “The target principal name is incorrect” и измените тип запуска на Disabled. Можно изменить настройки службы из консоли services.msc или с помощью PowerShell:
Get-Service kdc -ComputerName msk-dc03 | Set-Service –startuptype disabled –passthru
Перезагрузите этот контроллер домена.
Теперь нужно сбросить безопасный канал связи с контроллером домена с ролью PDC:
netdom resetpwd /server:msk-dc02 /userd:winitproadministrator /passwordd:*
Укажите пароль администратора домена.
Перезагрузите проблемный DC и запустите службу KDC. Попробуйте запустить репликацию и проверить ошибки.
repadmin /syncall
repadmin /replsum
repadmin /showrepl
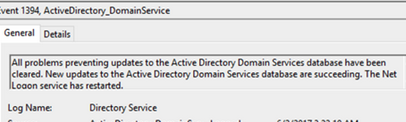
Если репликация успешно выполнена, в журнале Directory Service Event Viewerа должно появится событие Event ID 1394:
All Problems preventing updates to the Active Directory Domain Services database have been cleared. New Updates to the Active Directory Domain Services database are succeeding. The Net Logon service has restarted
Проверьте состояние вашего домена и контроллеров домена Active Directory согласно этого гайда.
I had an Active Directory replication problem at a customer site with a multi domain environment. Two domain controllers exists in a child domain called DC1 and DC2. DC1 resided in a remote branch location and DC2 exists in a datacentre.
- DC2 was able to replicate changes to DC1 without issues.
- DC1 was not able to replicate changes to DC2.
Please note the name of the domain and domain controllers involved have been renamed to protect customer privacy.
Symptoms
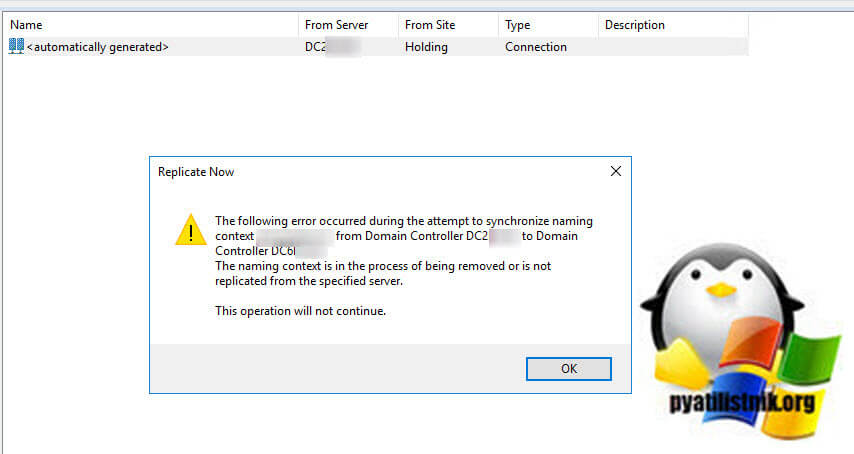
When attempting a manual replication attempt the following error was experienced:
The following error occurred during the attempt to synchronize naming context «ROOT DOMAIN» for domain controller DC1 to domain controller DC2:
The naming context is in the process of being removed or is not replicated from the specified server.
The operation will not continue.
When doing repadmin /showrepl all inbound replication partners came back successful under the last replication attempt however all outbound replication partners such as the replication attempt from DC1 to DC2 came back as failed with the following errors:
Source: RemoteSiteNameDC1
******* 216 CONSECUTIVE FAILURES since 2013-04-21 07:32:26
Last error: 8524 (0x214c):
Can’t retrieve message string 8524 (0x214c), error 1815.
Naming Context: CN=Configuration,DC=ROOTDOMAIN,DC=LOCAL
Source: RemoteSiteNameDC1
******* WARNING: KCC could not add this REPLICA LINK due to error.
Naming Context: DC=CHILDDOMAIN,DC=ROOTDOMAIN,DC=LOCAL
Source: RemoteSiteNameDC1
******* WARNING: KCC could not add this REPLICA LINK due to error.
Running a DCDiag on DC1 came back with the following errors:
Starting test: Connectivity
The host 9b2163cf-b8e7-4ad4-bd54-2342e6cfc1db._msdcs.rootdomain.local could not be resolved to an IP address. Check the DNS server, DHCP, server name etc.
Although the GUID DNS name 9b2163cf-b8e7-4ad4-bd54-2342e6cfc1db._msdcs.rootdomain.local couldn’t be resolved, the server name (DC1.child.rootdomain.local) resolved to the IP address xx.xx.xx.xx and was pingable. Check that the IP address is registered correctly with the DNS server.
Resolution
The following error message is the one which lead me to the resolution of this replication issue.
The host 9b2163cf-b8e7-4ad4-bd54-2342e6cfc1db._msdcs.rootdomain.local could not be resolved to an IP address. Check the DNS server, DHCP, server name etc.
Although the GUID DNS name 9b2163cf-b8e7-4ad4-bd54-2342e6cfc1db._msdcs.rootdomain.local couldn’t be resolved, the server name (DC1.child.rootdomain.local) resolved to the IP address xx.xx.xx.xx and was pingable. Check that the IP address is registered correctly with the DNS server.
The first domain you promote in a new Active Directory forest is the forest root domain (this can never be changed without building a new forest). The forest root domain contains a MSDCS container in DNS and contains a bunch of CNAME records for all domain controllers in the root domain as well as any child domains/new tree domains. These CNAME records are what Active Directory uses to lookup domain controllers when attempting to perform replication.
This is shown in the following screenshot.
The reason DC1 was unable to replicate to any other DC in the domain was because someone deleted the GUID mapping the CNAME record for DC1 from the msdcs container in Active Directory. From the DCDIAG error message we manually recreated the 9b2163cf-b8e7-4ad4-bd54-2342e6cfc1db._msdcs.rootdomain.local record mapping to DC1 as a CNAME record.
After 45 minutes replication began working again for DC1.
Hope this post helps someone with the same problem.
Содержание
- The following error occurred during the attempt to synchronize naming context
- Описание проблемы репликации между контроллерами
- Диагностика Active Directory
- Устранение проблем
- Дополнительные методы диагностики
- Дополнительные ссылки
- Популярные Похожие записи:
- 6 Responses to SyncAll exited with fatal Win32 error: 8440 (0x20f8), ошибка репликации в AD
The following error occurred during the attempt to synchronize naming context
Добрый день! Уважаемые читатели и гости одного из крупнейших IT блогов рунета Pyatilistnik.org. В прошлый раз мы с вами разобрали методы оплаты телефона Билайн, я привел вам варианты использования самых известных банков, мы сэкономили время, самый ценный ресурс в мире. Двигаемся дальше и сегодня разберем серьезную ошибку, которая может вам доставить уйму проблем при ее диагностике и в работе пользователей. Речь пойдет, о проблемах репликации между контроллерами домена, где на сбойном контроллере вы будите получать тьму ошибок, одной из которых будет «The target principal name is incorrect. SyncAll exited with fatal Win32 error: 8440 (0x20f8)«. Давайте восстанавливать правильную работу нашего AD.
Описание проблемы репликации между контроллерами
И так стали поступать заявки в систему технической поддержки, о том, что пользователь при попытке доступа по RDP получает ошибку:
Хотя пользователь уверял, что все верно вводил. Давайте разбираться в чем дело.
Диагностика Active Directory
Первым делом, я конечно же проверил не заблокирован ли пользователь, с ним было все прекрасно и он спокойно мог авторизовываться на других серверах компании. Параллельно другие сотрудники, из соседнего сайта Active Directory, получали такую же ошибку, поэтому я стал проверять репликации между контроллерами, таких ошибок я уже видел уйму:
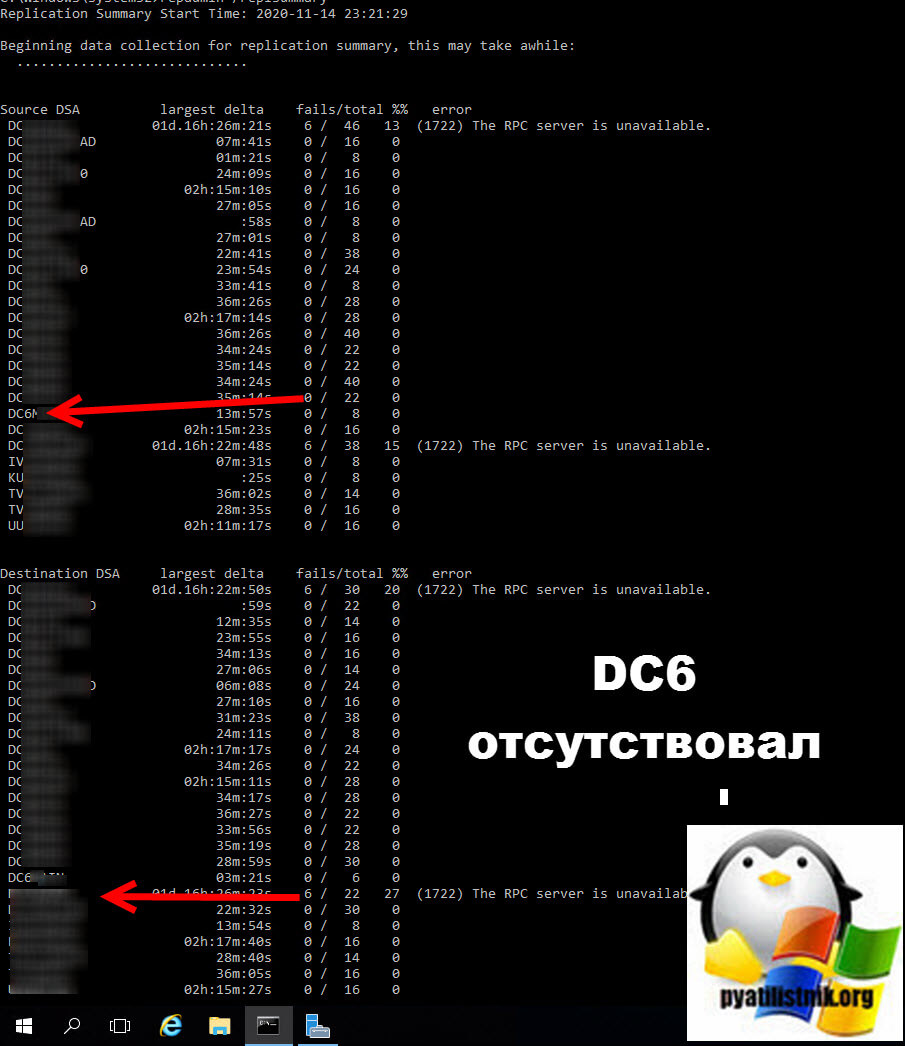
Напоминаю, что существует два инструмента, которые вам помогут произвести проверку репликации в лесу Active Directory, это repadmin и dcdiag, я не беру графические Active Directory Replication Status Tool. Моя AD состоит из 4 доменов, один корневой и три дочерних. Проблема была в одном из дочерних. Он состоял из четырех контроллеров домена, 3 из которых были в одном сайте, а оставшийся в другом. Первым делом я выполнил команду на контроллере из первого сайта:
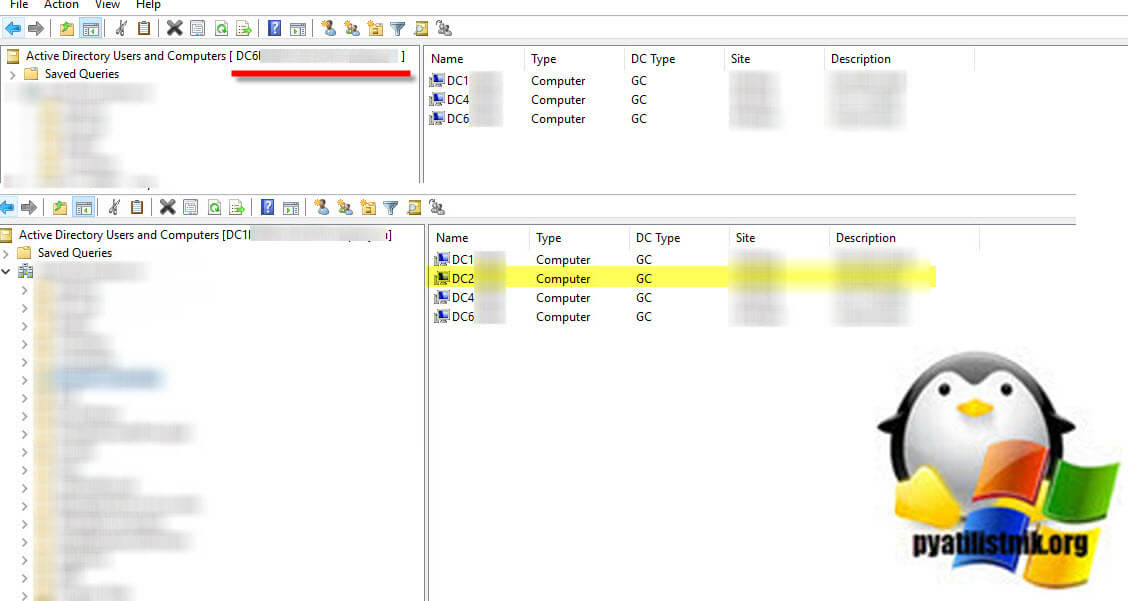
Ошибок он мне не показал, но меня привлекло, то что среди списка входящей и исходящей репликации, отсутствовал контроллер домена из другого сайта, тут я понял что проблема кроется явно уже в связи с ним. Контроллера DC6, просто не было
Естественно я начал подключаться к нему, прикол в том, что при попытке войти из под учетной записи пользователя корневого домена, я получил ту же ошибку «Неверное имя пользователя или пароль. Попробуйте снова (The user name or password is incorrect. Try again)», а вот под админом дочернего домена, все же пустило. Там я так же запустил в командной строке проверку репликации.
Тут уже сразу начались новые ошибки, с которыми я ранее не встречался:
Получается так, что с частью контроллеров домена, данный DC6 общался, а вот часть не видел.
Посмотрев как происходит реплика между сайтами, я понял, что входящая реплика идет от одного нового контроллера, а исходящая идет уже на другой. Открыв оснастку ADUC на DC6 я увидел, что нового контроллера домена DC2 просто нет в списке контейнера D0main Controllers, но зато присутствовал старый умерший контроллер.
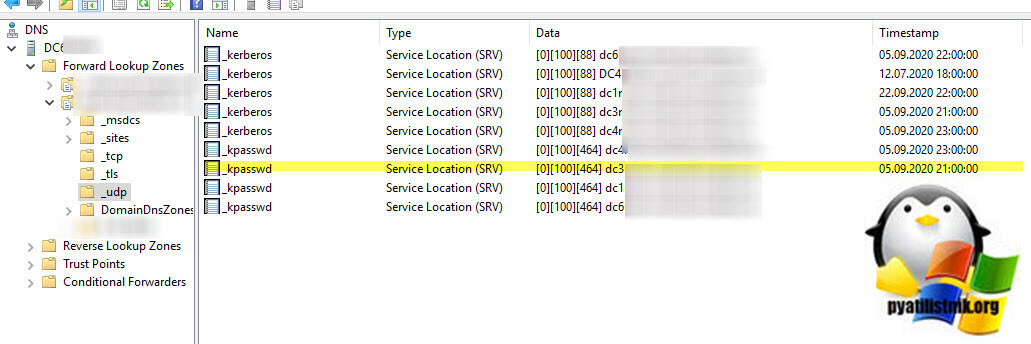
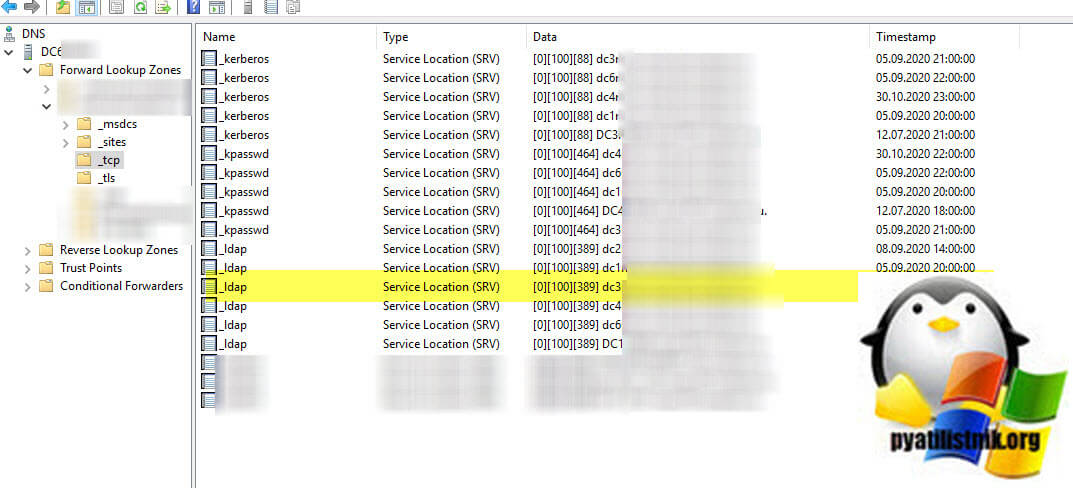
Далее я естественно заглянул и в оснастку DNS, где мне нужно было удостовериться, в наличии или отсутствии сервисных записей нового контроллера и старого. Я оказался прав, присутствовали записи старого контроллера. Записи SOA, так же сильно отличались.
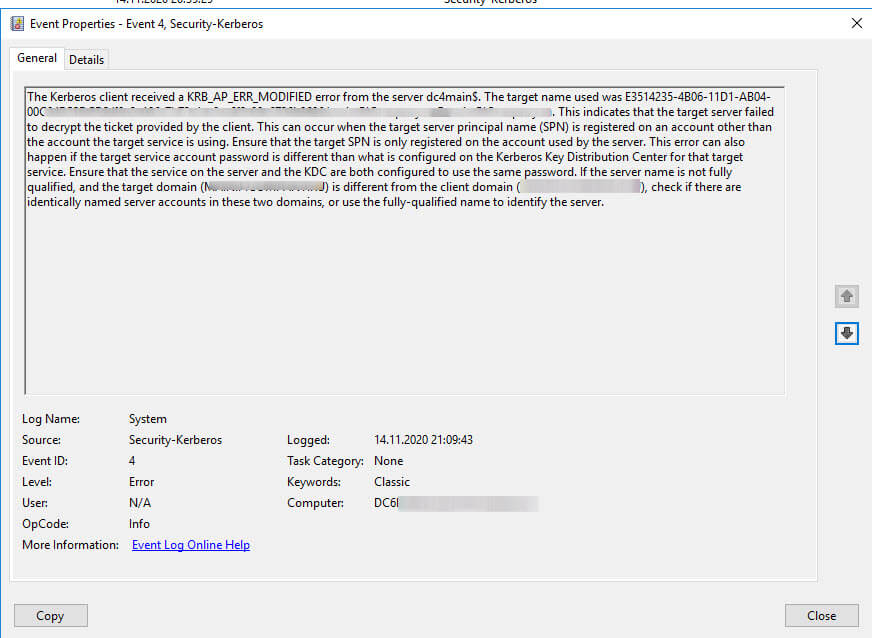
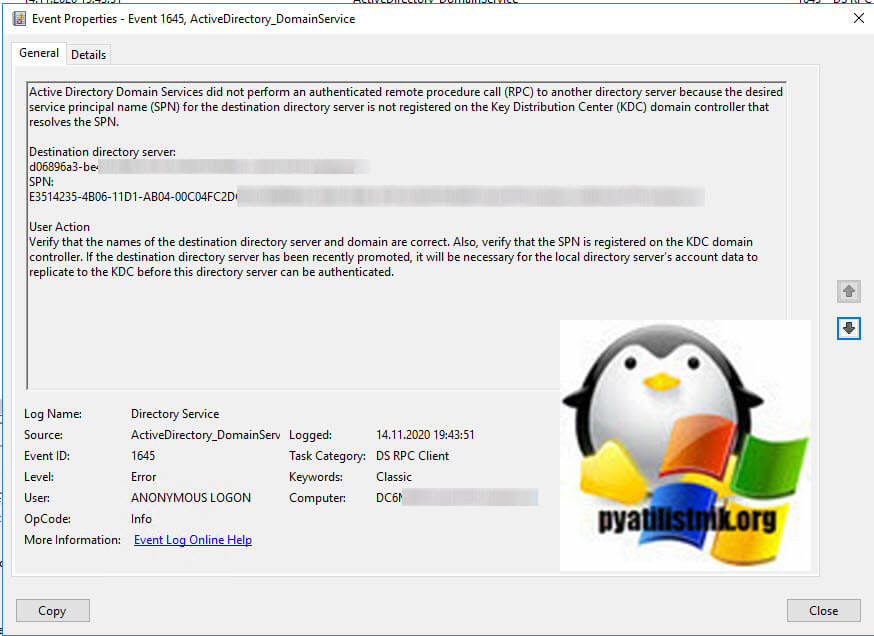
В логах Windows, через просмотр событий или Windows Admin Center, можно было наблюдать такие ошибки:
Destination directory server:
d06896a3-be4b-4b8a-b75f-e3453457526a0f._msdcs.pyatilistnik.org
SPN:
E3514235-4B06-11D1-AB04-00C04FC2DCD2/d06896a3-be4b-4b8a-b3453453526a0f/pyatilistnik.org
User Action
Verify that the names of the destination directory server and domain are correct. Also, verify that the SPN is registered on the KDC domain controller. If the destination directory server has been recently promoted, it will be necessary for the local directory server’s account data to replicate to the KDC before this directory server can be authenticated.
Устранение проблем
Первое на , что я наткнулся в качестве решений, это простая перезагрузка и правда, зачастую с Windows системами это один из действенных методов.
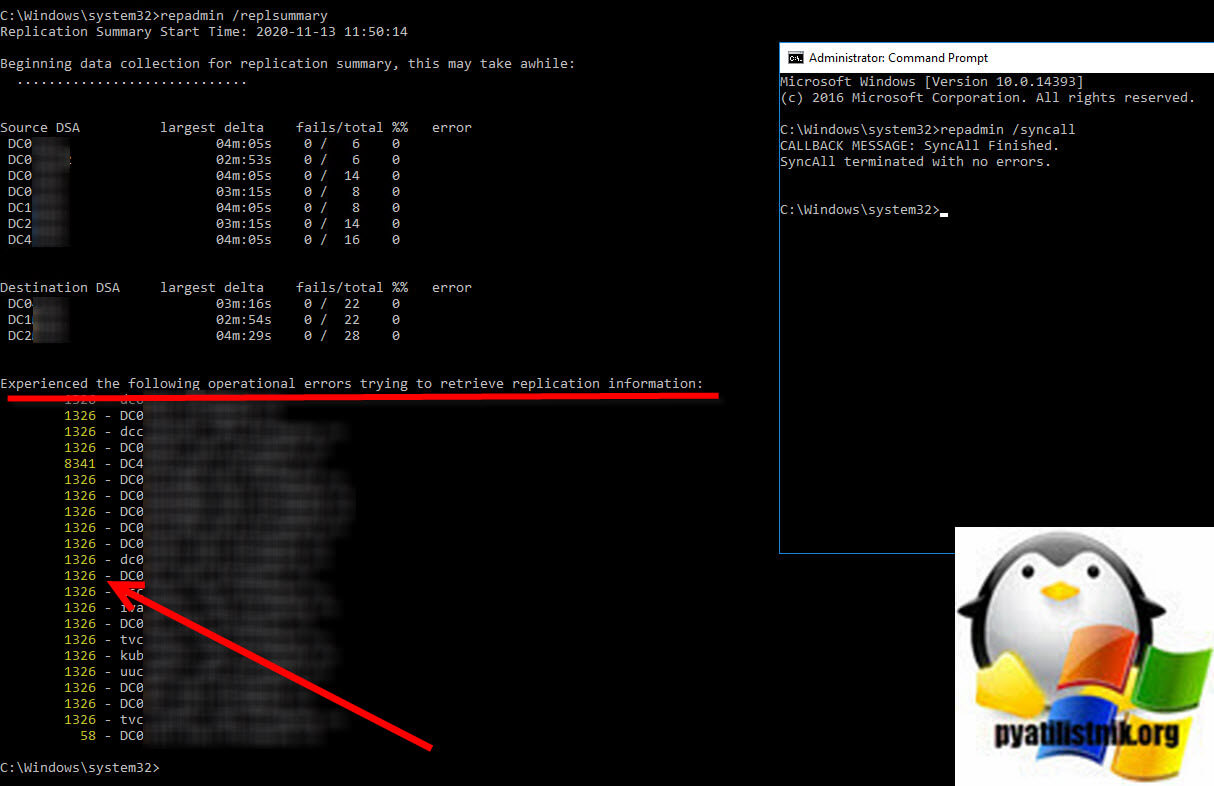
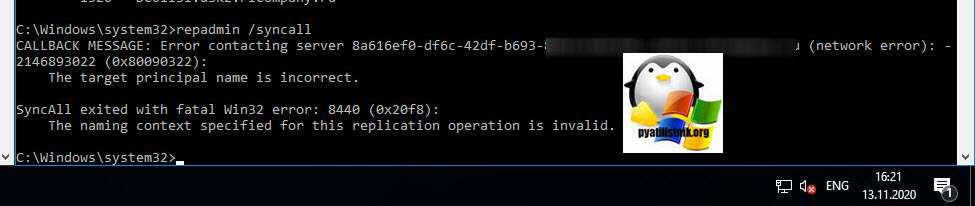
После перезагрузки я первым делом попытался выполнить принудительную синхронизацию, через команду:
В результате у меня она не прошла и я получил ошибку:
CALLBACK MESSAGE: Error contacting server CN=NTDS Settings,CN=DC6,CN=Servers,CN=root, CN=Sites,CN=Configuration,DC=pyatilistnik,DC=org (network error): -2146893022 (0x80090322):
The target principal name is incorrect.
SyncAll exited with fatal Win32 error: 8440 (0x20f8):
The naming context specified for this replication operation is invalid.
Так же показывались старые ошибки. Еще я попробовал команду, которая должна показать все ошибки при диагностике Active Directory:
В результате ошибок было еще больше 🙂
Я попытался вручную запустить входящую реплику через оснастку Active Directory Сайты и службы, но так же получил порцию новых ошибок.
Новые ошибки уже начали выводить меня на приблизительное решение данной проблемы. Ошибка «-2146893022 (0x80090322):The target principal name is incorrect. SyncAll exited with fatal Win32 error: 8440 (0x20f8)», говорит на, о том, что между мастером PDC и текущим контроллером домена не работает безопасный канал. Там мы производили его сброс через утилиту Netdom. Самое интересное, что команда проверяющая безопасный канал показывала, что с ним все в порядке.
Безопасный канал между локальным компьютером и доменом находится в хорошем состоянии, но ошибкам репликации на это безразницы.
На сбойном контроллере домена нужно выполнить:
- В командной строке или оболочке PowerShell вам необходимо остановить службу Key Distribution Center (Центр распространения ключей Kerberos) (KDC) на СБОЙНОМ контроллере домена.
Далее вам необходимо выставить у нее тип запуска «Отключено», для этого выполните команду:
После чего перезагрузите контроллер домена
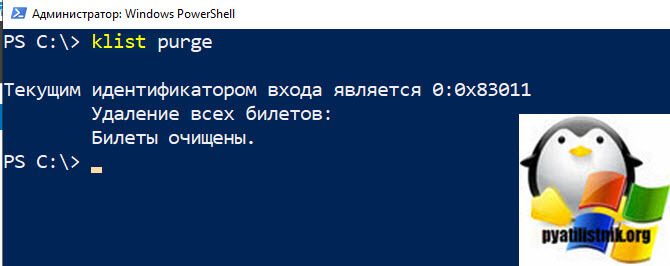
- На сбойном контроллере выполните команду, для того чтобы очистить билеты (Purge Tickets)
Далее на любом из контроллеров домена, который не является держателем роли FSMO DPC, вам нужно произвести сброс безопасного канала, я делаю эту команду на сбойном контроллере домена. Так же об этом советует Microsoft:
После перезагрузки компьютера используйте служебную программу Netdom для сброса безопасных каналов между этими контроллерами домена и держателем роли хозяина операций эмулятора PDC. Для этого выполните следующую команду с контроллеров домена, отличных от владельца роли хозяина операций эмулятора PDC:
Где server_name — это имя сервера, который является владельцем роли хозяина операций эмулятора PDC.
У меня это получилось вот так:
В результате вы должны получить «Пароль учетной записи локального компьютера успешно сброшен».
После сброса безопасного канала перезапустите контроллеры домена, я перезапустил сбойный и сервер с PDC ролью. Даже если вы попытаетесь сбросить безопасный канал с помощью утилиты Netdom, и команда не завершится успешно, продолжите процесс перезапуска. Если работает только владелец роли хозяина операций эмулятора PDC, KDC заставляет другие контроллеры домена повторно синхронизироваться с этим компьютером, вместо того, чтобы выдавать себе новый билет Kerberos.
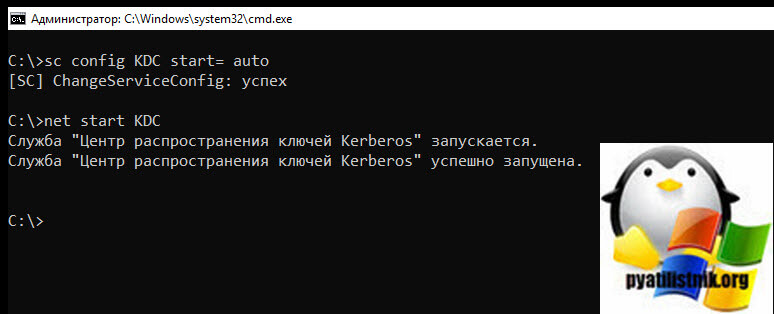
После перезагрузки на сбойном контроллере и на PDC выполните команду:
После чего можно запускать службу Key Distribution Center (Центр распространения ключей Kerberos) (KDC). Для этого выполните:
Дополнительные методы диагностики
- Если у вас контроллеры домена располагаются по разным сайтам, то обязательно проверьте все ли порты Active Directory вы открыли на своем оборудовании, самый главный порт 135, его можно проверить с обоих сторон, через утилиту Telnet.
- Если ничего не помогает, то я вам советую выключить сбойный контроллер и удалить его, почистить метаданные в AD и создать новый контроллер домена, для ускорения реплики при создании, сделайте файл IFM.
Дополнительные ссылки
- https://console.kim.sg/how-to-revive-dead-dns-server-on-the-last-standing-domain-controller-after-seizing-all-other-dcs/
- https://support.microsoft.com/en-sg/help/288167/error-message-target-principal-name-is-incorrect-when-manually-replica
- https://docs.microsoft.com/ru-ru/troubleshoot/windows-server/identity/replication-error-2146893022
На этом у меня все, мы с вами восстановили работу контроллеров домена и репликации, и больше не будет проблем с паролями. С вами был Иван Семин, автор и создатель IT портала Pyatilistnik.org.
Популярные Похожие записи:
6 Responses to SyncAll exited with fatal Win32 error: 8440 (0x20f8), ошибка репликации в AD
Добрый день! При попытке смены пароля (netdom /resetpwd) пишет:
Не удалось сбросить пароль учетной записи локального компьютера.
Неверное имя пользователя или пароль.
Не удалось выполнить команду.
Логин и пароль верные. Синхронизация не проходит, а сменить домен не могу так как проблема на контроллере домена.
Можете подробнее описать, что со сбойным контроллером?
Проблема такая же как и в посте не проходит репликация между доменами, проблема в главном домене.
Source DSA largest delta fails/total %% error
DC02 >60 days 5 / 5 100 (5) Access is denied.
DC03 >60 days 5 / 5 100 (8457) The destination server is currently rejecting replication requests.
dcgiag
Directory Server Diagnosis
Performing initial setup:
* Identified AD Forest.
Done gathering initial info.
Doing initial required tests
Testing server: baseDC02
Starting test: Connectivity
……………………. DC02 passed test Connectivity
Doing primary tests
Testing server: baseDC02
Starting test: Advertising
Warning: DsGetDcName returned information for \dc03.tarlan-auto.local, when we were trying to reach DC02.
SERVER IS NOT RESPONDING or IS NOT CONSIDERED SUITABLE.
……………………. DC02 failed test Advertising
Starting test: FrsEvent
……………………. DC02 passed test FrsEvent
Starting test: DFSREvent
There are warning or error events within the last 24 hours after the SYSVOL has been shared. Failing SYSVOL
replication problems may cause Group Policy problems.
……………………. DC02 failed test DFSREvent
Starting test: SysVolCheck
……………………. DC02 passed test SysVolCheck
Starting test: KccEvent
A warning event occurred. EventID: 0x8000061E
Time Generated: 08/04/2022 11:17:35
Event String:
All directory servers in the following site that can replicate the directory partition over this transport are currently unavailable.
An error event occurred. EventID: 0xC000051F
Time Generated: 08/04/2022 11:17:35
Event String:
The Knowledge Consistency Checker (KCC) has detected problems with the following directory partition.
A warning event occurred. EventID: 0x80000749
Time Generated: 08/04/2022 11:17:35
Event String:
The Knowledge Consistency Checker (KCC) was unable to form a complete spanning tree network topology. As a result, the following list of sites cannot be reached from the local site.
A warning event occurred. EventID: 0x8000061E
Time Generated: 08/04/2022 11:17:35
Event String:
All directory servers in the following site that can replicate the directory partition over this transport are currently unavailable.
An error event occurred. EventID: 0xC000051F
Time Generated: 08/04/2022 11:17:35
Event String:
The Knowledge Consistency Checker (KCC) has detected problems with the following directory partition.
A warning event occurred. EventID: 0x80000749
Time Generated: 08/04/2022 11:17:35
Event String:
The Knowledge Consistency Checker (KCC) was unable to form a complete spanning tree network topology. As a result, the following list of sites cannot be reached from the local site.
A warning event occurred. EventID: 0x8000061E
Time Generated: 08/04/2022 11:17:35
Event String:
All directory servers in the following site that can replicate the directory partition over this transport are currently unavailable.
An error event occurred. EventID: 0xC000051F
Time Generated: 08/04/2022 11:17:35
Event String:
The Knowledge Consistency Checker (KCC) has detected problems with the following directory partition.
A warning event occurred. EventID: 0x80000749
Time Generated: 08/04/2022 11:17:35
Event String:
The Knowledge Consistency Checker (KCC) was unable to form a complete spanning tree network topology. As a result, the following list of sites cannot be reached from the local site.
A warning event occurred. EventID: 0x8000061E
Time Generated: 08/04/2022 11:17:35
Event String:
All directory servers in the following site that can replicate the directory partition over this transport are currently unavailable.
An error event occurred. EventID: 0xC000051F
Time Generated: 08/04/2022 11:17:35
Event String:
The Knowledge Consistency Checker (KCC) has detected problems with the following directory partition.
A warning event occurred. EventID: 0x80000749
Time Generated: 08/04/2022 11:17:35
Event String:
The Knowledge Consistency Checker (KCC) was unable to form a complete spanning tree network topology. As a result, the following list of sites cannot be reached from the local site.
A warning event occurred. EventID: 0x8000082C
Time Generated: 08/04/2022 11:18:05
Event String:
A warning event occurred. EventID: 0x8000082C
Time Generated: 08/04/2022 11:29:06
Event String:
A warning event occurred. EventID: 0x8000082C
Time Generated: 08/04/2022 11:30:06
Event String:
A warning event occurred. EventID: 0x8000082C
Time Generated: 08/04/2022 11:30:36
Event String:
……………………. DC02 failed test KccEvent
Starting test: KnowsOfRoleHolders
……………………. DC02 passed test KnowsOfRoleHolders
Starting test: MachineAccount
……………………. DC02 passed test MachineAccount
Starting test: NCSecDesc
……………………. DC02 passed test NCSecDesc
Starting test: NetLogons
……………………. DC02 passed test NetLogons
Starting test: ObjectsReplicated
……………………. DC02 passed test ObjectsReplicated
Starting test: Replications
[Replications Check,Replications Check] Inbound replication is disabled.
To correct, run «repadmin /options DC02 -DISABLE_INBOUND_REPL»
[Replications Check,DC02] Outbound replication is disabled.
To correct, run «repadmin /options DC02 -DISABLE_OUTBOUND_REPL»
……………………. DC02 failed test Replications
Starting test: RidManager
The DS has corrupt data: rIDPreviousAllocationPool value is not valid
No rids allocated — please check eventlog.
……………………. DC02 failed test RidManager
Starting test: Services
NETLOGON Service is paused on [DC02]
……………………. DC02 failed test Services
Starting test: SystemLog
An error event occurred. EventID: 0x0000410B
Time Generated: 08/04/2022 11:14:05
Event String:
The request for a new account-identifier pool failed. The operation will be retried until the request succeeds. The error is
……………………. DC02 failed test SystemLog
Starting test: VerifyReferences
……………………. DC02 passed test VerifyReferences
Running partition tests on : ForestDnsZones
Starting test: CheckSDRefDom
……………………. ForestDnsZones passed test CheckSDRefDom
Starting test: CrossRefValidation
……………………. ForestDnsZones passed test CrossRefValidation
Running partition tests on : DomainDnsZones
Starting test: CheckSDRefDom
……………………. DomainDnsZones passed test CheckSDRefDom
Starting test: CrossRefValidation
……………………. DomainDnsZones passed test CrossRefValidation
Running partition tests on : Schema
Starting test: CheckSDRefDom
……………………. Schema passed test CheckSDRefDom
Starting test: CrossRefValidation
……………………. Schema passed test CrossRefValidation
Running partition tests on : Configuration
Starting test: CheckSDRefDom
……………………. Configuration passed test CheckSDRefDom
Starting test: CrossRefValidation
……………………. Configuration passed test CrossRefValidation
Running partition tests on : tarlan-auto
Starting test: CheckSDRefDom
……………………. tarlan-auto passed test CheckSDRefDom
Starting test: CrossRefValidation
……………………. tarlan-auto passed test CrossRefValidation
Running enterprise tests on : tarlan-auto.local
Starting test: LocatorCheck
……………………. tarlan-auto.local passed test LocatorCheck
Starting test: Intersite
……………………. tarlan-auto.local passed test Intersite
Пытался сбросить безопасный канал, пишет неверный логинпароль.
Спасибо за статьи, очень помогли решить проблему. У старого домена принудительно забрал fsmo роли, установил новый домен и настроил репликацию. Предыдущий коммент можно удалить)
Источник
| description | ms.assetid | title | author | ms.author | manager | ms.date | ms.topic |
|---|---|---|---|---|---|---|---|
|
Learn more about: Replication error 1753 There are no more endpoints available from the endpoint mapper |
0f21951c-b1bf-43bb-a329-bbb40c58c876 |
Replication error 1753 There are no more endpoints available from the endpoint mapper |
iainfoulds |
daveba |
daveba |
05/31/2017 |
article |
Replication error 1753 There are no more endpoints available from the endpoint mapper
Applies to: Windows Server 2022, Windows Server 2019, Windows Server
This article describes symptoms, cause and resolution steps for Active Directory operations that fail with Win32 error 1753: «There are no more endpoints available from the endpoint mapper.»
DCDIAG reports that the Connectivity test, Active Directory Replications test or KnowsOfRoleHolders test has failed with error 1753: «There are no more endpoints available from the endpoint mapper.»
Testing server: <site><DC Name>
Starting test: Connectivity
* Active Directory LDAP Services Check
* Active Directory RPC Services Check
[<DC Name>] DsBindWithSpnEx() failed with error 1753,
There are no more endpoints available from the endpoint mapper..
Printing RPC Extended Error Info:
Error Record 1, ProcessID is <process ID> (DcDiag)
System Time is: <date> <time>
Generating component is 2 (RPC runtime)
Status is 1753: There are no more endpoints available from the endpoint mapper. Detection location is 500
NumberOfParameters is 4
Unicode string: ncacn_ip_tcp
Unicode string: <source DC object GUID>._msdcs.contoso.com
Long val: -481213899
Long val: 65537
Error Record 2, ProcessID is 700 (DcDiag)
System Time is: <date> <time>
Generating component is 2 (RPC runtime)
Status is 1753: There are no more endpoints available from the endpoint mapper.
NumberOfParameters is 1
Unicode string: 1025
[Replications Check,<DC Name>] A recent replication attempt failed:
From <source DC> to <destination DC>
Naming Context: <DN path of directory partition>
The replication generated an error (1753):
There are no more endpoints available from the endpoint mapper.
The failure occurred at <date> <time>.
The last success occurred at <date> <time>.
3 failures have occurred since the last success.
The directory on <DC name> is in the process.
of starting up or shutting down, and is not available.
Verify machine is not hung during boot.
REPADMIN.EXE reports that replication attempt has failed with status 1753.
REPADMIN commands that commonly cite the 1753 status include but are not limited to:
- REPADMIN /REPLSUM
- REPADMIN /SHOWREPL
- REPADMIN /SHOWREPS
- REPADMIN /SYNCALL
Sample output from «REPADMIN /SHOWREPS» depicting inbound replication from CONTOSO-DC2 to CONTOSO-DC1 failing with the «replication access was denied» error is shown below:
Default-First-Site-NameCONTOSO-DC1
DSA Options: IS_GC
Site Options: (none)
DSA object GUID: b6dc8589-7e00-4a5d-b688-045aef63ec01
DSA invocationID: b6dc8589-7e00-4a5d-b688-045aef63ec01
==== INBOUND NEIGHBORS ======================================
DC=contoso,DC=com
Default-First-Site-NameCONTOSO-DC2 via RPC
DSA object GUID: 74fbe06c-932c-46b5-831b-af9e31f496b2
Last attempt @ <date> <time> failed, result 1753 (0x6d9):
There are no more endpoints available from the endpoint mapper.
<#> consecutive failure(s).
Last success @ <date> <time>.
The Check Replication Topology command in Active Directory Sites and Services returns «There are no more endpoints available from the endpoint mapper.»
Right-clicking on the connection object from a source DC and choosing Check Replication Topology fails with «There are no more endpoints available from the endpoint mapper.» The on-screen error message is shown below:
Dialog title text: Check Replication Topology
Dialog message text:
The following error occurred during the attempt to contact the domain controller: There are no more endpoints available from the endpoint mapper.
The Replicate now command in Active Directory Sites and Services returns «there are no more endpoints available from the endpoint mapper.»
Right-clicking on the connection object from a source DC and choosing Replicate now fails with «There are no more endpoints available from the endpoint mapper.»
The on-screen error message is shown below:
Dialog title text: Replicate Now
Dialog message text: The following error occurred during the attempt to synchronize naming context <%directory partition name%> from Domain Controller <Source DC> to Domain Controller <Destination DC>:
There are no more endpoints available from the endpoint mapper.
The operation will not continue
NTDS KCC, NTDS General or Microsoft-Windows-ActiveDirectory_DomainService events with the -2146893022 status are logged in the Directory Services log in Event Viewer.
Active Directory events that commonly cite the -2146893022 status include but are not limited to:
| Event ID | Event Source | Event String |
|---|---|---|
| 1655 | NTDS General | Active Directory attempted to communicate with the following global catalog and the attempts were unsuccessful. |
| 1925 | NTDS KCC | The attempt to establish a replication link for the following writable directory partition failed. |
| 1265 | NTDS KCC | An attempt by the Knowledge Consistency Checker (KCC) to add a replication agreement for the following directory partition and source domain controller failed. |
Cause
The steps below shows the RPC workflow starting with the registration of the server application with the RPC Endpoint Mapper (EPM) in step 1 to the passing of data from the RPC client to the client application in step 7.
ADDS RPC Workflow
- Server app registers its endpoints with the RPC Endpoint Mapper (EPM)
- Client makes an RPC call (on behalf of a user, OS or application initiated operation)
- Client side RPC contacts the target computers EPM and ask for the endpoint to complete the client call
- Server Machine’s EPM responds with an endpoint
- Client side RPC contacts the server app
- Server app executes the call, returns the result to the client RPC
- Client side RPC passes the result back to the client app
Failure 1753 is generated by a failure between steps #3 and #4. Specifically, error 1753 means that the RPC client (destination DC) was able to contact the RPC Server (source DC) over port 135 but the EPM on the RPC Server (source DC) was unable to locate the RPC application of interest and returned server side error 1753. The presence of the 1753 error indicates that the RPC client (destination DC) received the server side error response from the RPC Server (AD replication source DC) over the network.
Specific root causes for the 1753 error include:
- The server app never started (i.e. Step #1 in the «more information» diagram located above was never attempted).
- The server app started but there was some failure during initialization that prevented it from registering with the RPC Endpoint Mapper (i.e. Step #1 in the «more information» diagram above was attempted but failed).
- The server app started but subsequently died. (i.e. Step #1 in the «more information» diagram above was completed successfully, but was undone later because the server died).
- The server app manually unregistered its endpoints (similar to 3 but intentional. Not likely but included for completeness.)
- The RPC client (destination DC) contacted a different RPC server than the intended one due to a Name to IP mapping error in DNS, WINS or host/Lmhosts file.
Error 1753 is NOT caused by:
- A lack of network connectivity between the RPC client (destination DC) and RPC Server (source DC) over port 135
- A lack of network connectivity between the RPC server (source DC) using port 135 and the RPC client (destination DC) over the ephemeral port.
- A password mismatch or the inability by the source DC to decrypt a Kerberos encrypted packet
Resolutions
Verify that the service registering its service with the endpoint mapper has started
- For Windows 2000 and Windows Server 2003 DCs: Ensure that the source DC is booted into normal mode.
- For Windows Server 2008 or Windows Server 2008 R2: From the console of the source DC, start Services Manager (services.msc) and verify that the Active Directory Domain Services service is running.
Verify that RPC client (destination DC) connected to the intended RPC Server (source DC)
All DCs in a common Active Directory forest register a domain controller CNAME record in the _msdcs. <forest root domain> DNS zone regardless of what domain they reside in within the forest. The DC CNAME record is derived from the objectGUID attribute of the NTDS Settings object for each domain controller.
When performing replication-based operations, a destination DC queries DNS for the source DCs CNAME record. The CNAME record contains the source DC fully qualified computer name which is used to derive the source DCs IP address via DNS client cache lookup, Host / LMHost file lookup, host A / AAAA record in DNS, or WINS.
Stale NTDS Settings objects and bad name-to-IP mappings in DNS, WINS, Host and LMHOST files may cause the RPC client (destination DC) to connect to the wrong RPC Server (Source DC). Furthermore, the bad name-to-IP mapping may cause the RPC client (destination DC) to connect to a computer that does not even have the RPC Server Application of interest (the Active Directory role in this case) installed. (Example: a stale host record for DC2 contains the IP address of DC3 or a member computer).
Verify that the objectGUID for the source DC that exists in the destination DCs copy of Active Directory matches the source DC objectGUID stored in the source DCs copy of Active Directory. If there is a discrepancy, use repadmin /showobjmeta on the ntds settings object to see which one corresponds to last promotion of the source DC (hint: compare date stamps for the NTDS Settings object create date from /showobjmeta against the last promotion date in the source DCs dcpromo.log file. You may have to use the last modify / create date of the DCPROMO.LOG file itself). If the object GUIDs are not identical, the destination DC likely has a stale NTDS Settings object for the source DC whose CNAME record refers to a host record with a bad name to IP mapping.
On the destination DC, run IPCONFIG /ALL to determine which DNS Servers the destination DC is using for name resolution:
On the destination DC, run NSLOOKUP against the source DCs fully qualified DC CNAME record:
c:>nslookup -type=cname <fully qualified cname of source DC> <destination DCs primary DNS Server IP >
c:>nslookup -type=cname <fully qualified cname of source DC> <destination DCs secondary DNS Server IP>
Verify that the IP address returned by NSLOOKUP «owns» the host name / security identity of the source DC:
C:>NBTSTAT -A <IP address returned by NSLOOKUP in the step above>
Log onto the console of the source DC, run «IPCONFIG» from the CMD prompt and verify that the source DC owns the IP address returned by the NSLOOKUP command above
Check for stale / duplicate host to IP mappings in DNS
NSLOOKUP -type=hostname <single label hostname of source DC> <primary DNS Server IP on destination DC>
NSLOOKUP -type=hostname <single label hostname of source DC> <secondary DNS Server IP on destination DC>
NSLOOKUP -type=hostname <fully qualified computer name of source DC> <primary DNS Server IP on destination DC>
NSLOOKUP -type=hostname <fully qualified computer name of source DC> <secondary DNS Server IP on dest. DC>
If invalid IP addresses exist in host records, investigate whether DNS scavenging is enabled and properly configured.
If the tests above or a network trace doesn’t show a name query returning an invalid IP address, consider stale entries in HOST files, LMHOSTS files and WINS Servers. Note that DNS Servers can also be configured to perform WINS fallback name resolution.
- Verify that the server application (Active Directory et al) has registered with the endpoint mapper on the RPC server (source DC)
- Active Directory uses a mix of well-known and dynamically registered ports. This table lists well known ports and protocols used by Active Directory domain controllers.
| RPC Server Application | Port | TCP | UDP |
|---|---|---|---|
| DNS server | 53 | X | X |
| Kerberos | 88 | X | X |
| LDAP server | 389 | X | X |
| Microsoft-DS | 445 | X | X |
| LDAP SSL | 636 | X | X |
| Global Catalog Server | 3268 | X | |
| Global Catalog Server | 3269 | X |
Well-known ports are NOT registered with the endpoint mapper.
Active Directory and other applications also register services that receive dynamically assigned ports in the RPC ephemeral port range. Such RPC server applications are dynamically assigned TCP ports between 1024 and 5000 on Windows 2000 and Windows Server 2003 computers and ports between 49152 and 65535 range on Windows Server 2008 and Windows Server 2008 R2 computers. The RPC port used by replication can be hard-coded in the registry using the steps documented in KB article 224196. Active Directory continues to register with the EPM when configured to use a hard coded port.
Verify that the RPC Server application of interest has registered itself with the RPC endpoint mapper on the RPC Server (the source DC in the case of AD replication).
There are a number of ways to accomplish this task but one is to install and run PORTQRY from an admin privileged CMD prompt on the console of the source DC using the syntax:
portquery -n <source DC> -e 135 > file.txt
In the portqry output, note the port numbers dynamically registered by the «MS NT Directory DRS Interface» (UUID = 351…) for the ncacn_ip_tcp protocol. The snippet below shows sample portquery output from a Windows Server 2008 R2 DC:
UUID: e3514235-4b06-11d1-ab04-00c04fc2dcd2 MS NT Directory DRS Interface
ncacn_np:CONTOSO-DC01[pipelsass]
UUID: e3514235-4b06-11d1-ab04-00c04fc2dcd2 MS NT Directory DRS Interface
ncacn_np:CONTOSO-DC01[PIPEprotected_storage]
UUID: e3514235-4b06-11d1-ab04-00c04fc2dcd2 MS NT Directory DRS Interface
ncacn_ip_tcp:CONTOSO-DC01[49156]
UUID: e3514235-4b06-11d1-ab04-00c04fc2dcd2 MS NT Directory DRS Interface
ncacn_http:CONTOSO-DC01[49157]
UUID: e3514235-4b06-11d1-ab04-00c04fc2dcd2 MS NT Directory DRS Interface
ncacn_http:CONTOSO-DC01[6004]
Other possible ways to resolve this error:
-
Verify that the source DC is booted in normal mode and that the OS and DC role on the source DC have fully started.
-
Verify that the Active Directory Domain Service is running. If the service is currently stopped or was not configured with default startup values, reset the default startup values, reboot the modified DC then retry the operation.
-
Verify that the startup value and service status for RPC service and RPC Locator is correct for OS version of the RPC Client (destination DC) and RPC Server (source DC). If the service is currently stopped or was not configured with default startup values, reset the default startup values, reboot the modified DC then retry the operation.
-
In addition, ensure that the service context matches default settings listed in the following table.
Service Default status (Startup type) in Windows Server 2003 and later Default status (Startup type) in Windows Server 2000 Remote Procedure Call Started (Automatic) Started (Automatic) Remote Procedure Call Locator Null or Stopped (Manual) Started (Automatic)
-
-
Verify that the size of the dynamic port range has not been constrained. The Windows Server 2008 and Windows Server 2008 R2 NETSH syntax to enumerate the RPC port range is shown below:
netsh int ipv4 show dynamicport tcp netsh int ipv4 show dynamicport udp netsh int ipv6 show dynamicport tcp netsh int ipv6 show dynamicport udp -
Verify that hard coded port definitions defined in KB 224196 fall within the dynamic port range for source DCs OS version. Review KB article 224196 and ensure that the hard coded port falls within the ephemeral port range for the source DC’s operating system version.
-
Verify that the ClientProtocols key exists under HKLMSoftwareMicrosoftRpc and contains the following 5 default values:
ncacn_http REG_SZ rpcrt4.dll ncacn_ip_tcp REG_SZ rpcrt4.dll ncacn_nb_tcp REG_SZ rpcrt4.dll ncacn_np REG_SZ rpcrt4.dll ncacn_ip_udp REG_SZ rpcrt4.dll
More information
Example of a bad name to IP mapping causing RPC error 1753 vs. -2146893022: the target principal name is incorrect
The contoso.com domain consists of DC1 and DC2 with IP addresses x.x.1.1 and x.x.1.2. The host «A» / «AAAA» records for DC2 are correctly registered on all of the DNS Servers configured for DC1. In addition, the HOSTS file on DC1 contains an entry mapping DC2s fully qualified hostname to IP address x.x.1.2. Later, DC2’s IP address changes from X.X.1.2 to X.X.1.3 and a new member computer is joined to the domain with IP address x.x.1.2. AD Replication attempts triggered by the Replicate now command in Active Directory Sites and Services snap-in fails with error 1753 as shown in the trace below:
F# SRC DEST Operation
1 x.x.1.1 x.x.1.2 ARP:Request, x.x.1.1 asks for x.x.1.2
2 x.x.1.2 x.x.1.1 ARP:Response, x.x.1.2 at 00-13-72-28-C8-5E
3 x.x.1.1 x.x.1.2 TCP:Flags=......S., SrcPort=50206, DstPort=DCE endpoint resolution(135)
4 x.x.1.2 x.x.1.1 ARP:Request, x.x.1.2 asks for x.x.1.1
5 x.x.1.1 x.x.1.2 ARP:Response, x.x.1.1 at 00-15-5D-42-2E-00
6 x.x.1.2 x.x.1.1 TCP:Flags=...A..S., SrcPort=DCE endpoint resolution(135)
7 x.x.1.1 x.x.1.2 TCP:Flags=...A...., SrcPort=50206, DstPort=DCE endpoint resolution(135)
8 x.x.1.1 x.x.1.2 MSRPC:c/o Bind: UUID{E1AF8308-5D1F-11C9-91A4-08002B14A0FA} EPT(EPMP)
9 x.x.1.2 x.x.1.1 MSRPC:c/o Bind Ack: Call=0x2 Assoc Grp=0x5E68 Xmit=0x16D0 Recv=0x16D0
10 x.x.1.1 x.x.1.2 EPM:Request: ept_map: NDR, DRSR(DRSR) {E3514235-4B06-11D1-AB04-00C04FC2DCD2} [DCE endpoint resolution(135)]
11 x.x.1.2 x.x.1.1 EPM:Response: ept_map: 0x16C9A0D6 - EP_S_NOT_REGISTERED
At frame 10, the destination DC queries the source DCs end point mapper over port 135 for the Active Directory replication service class UUID E351…
In frame 11, the source DC, in this case a member computer that does not yet host the DC role and therefore has not registered the E351… UUID for the Replication service with its local EPM responds with symbolic error EP_S_NOT_REGISTERED which maps to decimal error 1753, hex error 0x6d9 and friendly error «there are no more endpoints available from the endpoint mapper».
Later, the member computer with IP address x.x.1.2 gets promoted as a replica «MayberryDC» in the contoso.com domain. Again, the Replicate now command is used to trigger replication but this time fails with the on-screen error «The target principal name is incorrect.» The computer whose network adapter is assigned the IP address x.x.1.2 is a domain controller, is currently booted into normal mode and has registered the E351… replication service UUID with its local EPM but it does not own the name or security identity of DC2 and cannot decrypt the Kerberos request from DC1 so the request now fails with error «The target principal name is incorrect.» The error maps to decimal error -2146893022 / hex error 0x80090322.
Such invalid host-to-IP mappings could be caused by stale entries in host / lmhost files, host A / AAAA registrations in DNS, or WINS.
Summary: This example failed because an invalid host-to-IP mapping (in the HOST file in this case) caused the destination DC to resolve to a «source» DC that did not have the Active Directory Domain Services service running (or even installed for that matter) so the replication SPN was not yet registered and the source DC returned error 1753. In the second case, an invalid host-to-IP mapping (again in the HOST file) caused the destination DC to connect to a DC that had registered the E351… replication SPN but that source had a different hostname and security identity than the intended source DC so the attempts failed with error -2146893022: The target principal name is incorrect.
Related Topics
- Troubleshooting Active Directory operations that fail with error 1753: There are no more endpoints available from the endpoint mapper.
- KB article 839880 Troubleshooting RPC Endpoint Mapper errors using the Windows Server 2003 Support Tools from the product CD
- KB article 832017 Service overview and network port requirements for the Windows Server system
- KB article 224196 Restricting Active Directory replication traffic and client RPC traffic to a specific port
- KB article 154596 How to configure RPC dynamic port allocation to work with firewalls
- How RPC Works
- How the Server Prepares for a Connection
- How the Client Establishes a Connection
- Registering the Interface
- Making the Server Available on the Network
- Registering Endpoints
- Listening for Client Calls
- How the Client Establishes a Connection
- Restricting Active Directory replication traffic and client RPC traffic to a specific port
- SPN for a Target DC in AD DS
Problem:
When one of the active directory server was offline for a long time and brought it back online, the replication won’t work due to two servers having different active directory information.
When you try to run replication, you receive an error message such as.
Dialog title text: Replicate Now Dialog message text: The following error occurred during the attempt to synchronize naming context <%active directory partition name%> from domain controller <source DC> to domain controller <destination DC>: Insufficient attributes were given to create an object. This object may not exist because it may have been deleted and already garbage collected. The operation will not continue
When you run dcdiag, you receive an error 8606
Starting test: Replications [Replications Check, <Destination DC>] A recent replication attempt failed: From <source DC> to <destination DC> Naming Context: <directory partition DN path> The replication generated an error (8606): Insufficient attributes were given to create an object. This object may not exist because it may have been deleted and already garbage collected The failure occurred at <date> <time> The last success occurred at <date> <time>
Solution:
First, run repadmin /options. If the replication is disabled, it will show you if the inbound or outbound replication is diabled.
Run the following command.
repadmin /options +DISABLE_OUTBOUND_REPL repadmin /options -DISABLE_OUTBOUND_REPL repadmin /options +DISABLE_INBOUND_REPL repadmin /options -DISABLE_INBOUND_REPL
This will clear up any replication that is diabled.
Then, we want to enable loose replication consistency.
- Locate and click the following registry key:
HKEY_LOCAL_MACHINESystemCurrentControlSetServicesNTDSParameters
- Click Add Value on the Edit menu.
- Add the following value:
Value Name: Strict Replication Consistency
Data type: REG_DWORD
Value data: If the value is 1, change it to 0.
Try running manual replication and see if the replication works. You will need to enable the loose replication consistency on both replication partner. (Otherwise, the replication will work one way only.) After the manual replicaiton is successful, you may disable the loose replication consistency back.
Troubleshooting AD Replication error 1722: The RPC server is unavailable
Support for Windows Server 2003 ended on July 14, 2015
Microsoft ended support for Windows Server 2003 on July 14,
2015. This change has affected your software updates and security
options.
Learn what this means for you and how to stay protected.
Symptoms
This
article describes the symptoms, cause and resolution for resolving
Active Directory replication failing with Win32 error 1722: The RPC
server is unavailable.
- DCPROMO Promotion of a replica DC fails to create an NTDS Settings object on the helper DC with error 1722
Dialog Title Text:
Active Directory Domain Services Installation Wizard
Dialog Message text:
The operation failed because: Active Directory Domain Services could
not create the NTDS Settings object for this Active Directory Domain
Controller CN=NTDS Settings,CN=<Name of DC being
promoted),CN=Servers,CN=<site
name>,CN=Sites,CN=Configuration,DC=<forest root domain> on
the remote AD DC <helper DC>.<domain name>.<top level
domain>. Ensure the provided network credentials have sufficient
permissions. «The RPC server is unavailable.» - DCDIAG reports that the Active Directory Replications test has failed with error 1722: “The RPC Server is unavailable»
[Replications Check,<DC Name>] A recent replication attempt failed:
From <source DC> to <destination DC>
Naming Context: <DN path of directory partition>
The replication generated an error (1722):
The RPC server is unavailable.
The failure occurred at <date> <time>.
The last success occurred at <date> <time>.
<X> failures have occurred since the last success.
[<dc name>] DsBindWithSpnEx() failed with error 1722,
The RPC server is unavailable..
Printing RPC Extended Error Info:
<snip> - REPADMIN.EXE reports that replication attempt has failed with status 1722 (0x6ba).
REPADMIN commands that commonly cite the -1722 (0x6ba) status include but are not limited to:
· REPADMIN /REPLSUM
· REPADMIN /SHOWREPL· REPADMIN /SHOWREPS
· REPADMIN /SYNCALLSample output from «REPADMIN /SHOWREPS» and REPADMIN /SYNCALL depicting «The RPC server is unavailable» error is shown below:
c:>repadmin /showreps
<site name><destination DC>
DC Options: <list of flags>
Site Options: (none)
DC object GUID: <NTDS settings object object GUID>
DC invocationID: <invocation ID string>==== INBOUND NEIGHBORS ======================================
DC=<DN path for directory partition>
<site name><source DC via RPC
DC object GUID: <source DCs ntds settings object object guid>
Last attempt @ <date> <time> failed, result 1722 (0x6ba):
The RPC server is unavailable.
<X #> consecutive failure(s).
Last success @ <date> <time>Sample output of «REPADMIN /SYNCALL» depicting «The RPC server is unavailable» error is shown below:
C:>repadmin /syncall
CALLBACK MESSAGE: Error contacting server
<object guid of NTDS Settings object>._msdcs.<forest root
domain>.<top level domain> (network error): 1722 (0x6ba):
The RPC server is unavailable. -
The «replicate now» command in Active Directory Sites and Services returns «The RPC server is unavailable.»
Right-clicking
on the connection object from a source DC and choosing «replicate
now» fails with «The RPC server is unavailable.. The on-screen error
message is shown below:Dialog title text:
Replicate Now
Dialog message test:
The following error occurred during the attempt to synchronize naming
context <DNS name of directory partition> from domain controller
<source Dc host name> to domain controller <destination DC
hostname>:The RPC server is unavailable. This operation will not
continue. This condition may be caused by a DNS lookup problem. For
information about troubleshooting common DNS lookup problems, please see
the following Microsoft Web site:http://go.microsoft.com/fwlink/?LinkId=5171 -
NTDS KCC, NTDS General or
Microsoft-Windows-ActiveDirectory_DomainService events with the 1722
status are logged in the directory service event log.Active Directory events that commonly cite the 1722 status include but are not limited to:
Event Source Event ID Event String Microsoft-Windows-ActiveDirectory_DomainService 1125 The Active Directory Domain Services Installation Wizard (Dcpromo)
was unable to establish connection with the following domain controller.NTDS KCC 1311 The Knowledge Consistency Checker (KCC) has detected problems with the following directory partition. NTDS KCC 1865 The Knowledge Consistency Checker (KCC) was unable to form a
complete spanning tree network topology. As a result, the following list
of sites cannot be reached from the local site.NTDS KCC 1925 The attempt to establish a replication link for the following writable directory partition failed. NTDS Replication 1960 Internal event: The following domain controller received an
exception from a remote procedure call (RPC) connection. The operation
may have failed.
Cause
RPC
is an intermediate layer between the network transport and the
application protocol. RPC itself has no special insight into failures
but attempts to map lower layer protocol failures into an error at the
RPC layer
RPC error 1722 / 0x6ba / RPC_S_SERVER_UNAVAILABLE is
logged when a lower layer protocol reports a connectivity failure. The
common case is that the abstract TCP CONNECT operation failed. In the
context of AD replication, the RPC client on the destination DC was not
able to successfully connect to the RPC server on the source DC. Common
causes for this are:
- Link local failure
- DHCP failure
- DNS failure
- WINS failure
- Routing failure (including blocked ports on firewalls)
- IPSec / Network authentication failures
- Resource limitations
- Higher layer protocol not running
- Higher layer protocol is returning this error
Resolution
Basic Troubleshooting Steps to Identify the problem.
1. Verify the startup value and service status for the is correct for
the Remote Procedure Call (RPC), Remote Procedure Call (RPC) Locator
and Kerberos Key Distribution Center. The OS version will determine the
correct values for the source and destination system that is logging
the replication error. Use the following table to help validate the
settings.
|
Service Name |
Windows 2000 |
Windows 2003 /R2 | Windows 2008 | Windows 2008 R2 |
| Remote Procedure Call (RPC) | Started / Automatic | Started / Automatic | Started / Automatic | Started / Automatic |
| Remote Procedure Call (RPC) Locator |
Started / Automatic (Domain Controllers) Not started / Manual(Member Servers) |
Not started / Manual | Not started / Manual | Not started / Manual |
| Kerberos Key Distribution Center (KDC) |
Started / Automatic (Domain Controllers) Not started / Disabled(Member Servers) |
Started / Automatic (Domain Controllers) Not started / Disabled(Member Servers) |
Started / Automatic (Domain Controllers) Not started / Disabled(Member Servers) |
Started / Automatic (Domain Controllers) Not started / Disabled(Member Servers) |
If you make any changes to match the settings above, reboot the
machine and verify both the startup value and service status match the
values documented in the table above.
2. Verify the ClientProtocols key exists under HKLMSoftwareMicrosoftRpc, and that it contains the correct default protocols.
| Protocol Name | Type | Data Value |
| ncacn_http | REG_SZ | rpcrt4.dll |
| ncacn_ip_tcp | REG_SZ | rpcrt4.dll |
| ncacn_np | REG_SZ | rpcrt4.dll |
| ncacn_ip_udp | REG_SZ | rpcrt4.dll |
If the ClientProtocols key or any of the 4 default values are missing, import the key from a known good server.
3. Verify DNS is working. DNS lookup failures are the cause of a
large amount of 1722 RPC errors when it comes to replication. There
are a few tools to use to help identify DNS errors:
- DCDIAG /TEST:DNS /V /E /F:<filename.log>
TheDCDIAG /TEST:DNS
command can validate DNS health of Windows 2000 Server (SP3 or later),
Windows Server 2003 and Windows Server 2008 family domain controllers.
This test was first introduced with Windows Server 2003 Service Pack 1.There are seven test groups for this command.
- Authentication (Auth)
- Basic (Basc)
- Records registration (RReg)
- Dynamic update (Dyn)
- Delegations (Del)
- Forwarders/Root hints (Forw)
Sample Output
TEST: Authentication (Auth)
Authentication test: Successfully completed
TEST: Basic (Basc)
Microsoft(R) Windows(R) Server 2003, Enterprise Edition (Service Pack level: 2.0) is supported
NETLOGON service is running
kdc service is running
DNSCACHE service is running
DNS service is running
DC is a DNS server
Network adapters information:
Adapter [00000009] Microsoft Virtual Machine Bus Network Adapter:
MAC address is 00:15:5D:40:CF:92
IP address is static
IP address: <IP Address
DNS servers:
<DNS IP Address> (DC.domain.com.) [Valid]
The A record for this DC was found
The SOA record for the Active Directory zone was found
The Active Directory zone on this DC/DNS server was found (primary)
Root zone on this DC/DNS server was not found
<omitted other tests for readability>
Summary of DNS test results:
Auth Basc Forw Del Dyn RReg Ext
________________________________________________________________
Domain: Ca.fragale
DC1 PASS PASS FAIL PASS PASS PASS n/a
Domain: child.Ca.fragale
DC2 PASS PASS n/a n/a n/a PASS n/a
Enterprise DNS infrastructure test results:
For parent domain domain.com and subordinate domain child:
Forwarders or root hints are not misconfigured from parent domain to subordinate domain
Error: Forwarders are configured from subordinate to parent domain but some of them failed DNS server tests
(See DNS servers section for error details)
Delegation is configured properly from parent to subordinate domain
……………………. domain.com failed test DNS
The summary provides remediation steps for the more common failures from this test.
Explanation and additional options for this test can be found at Domain Controller Diagnostics Tool (dcdiag.exe)
-
NLTEST /DSGETDC:<netbios or DNS domain name>
Nltest /dsgetdc: is used to exercise the dc locator process. Thus /dsgetdc:< domain name
> tries to find the domain controller for the domain. Using the
force flag forces domain controller location rather than using the
cache. You can also specify options such as /gc or /pdc to
locate a Global Catalog or a primary domain controller emulator. For
finding the Global Catalog, you must specify a «tree name,» which is the
DNS domain name of the root domain.Sample output:
DC: \DC.Domain.com
Address: \<IP Address>
Dom Guid: 5499c0e6-2d33-429d-aab3-f45f6a06922b
Dom Name: Domain.com
Forest Name: Domain.com
Dc Site Name: Default-First-Site-Name
Our Site Name: Default-First-Site-Name
Flags: PDC GC DS LDAP KDC TIMESERV WRITABLE DNS_DC DNS_DOMAIN DNS_FOREST CLOSE_SITE
The command completed successfully - Netdiag -v
Can be used with Windows 2003 and
earlier versions to gather specific information for networking
configuration and error. This tool takes some time to run when
executing the -v switch.Sample Output for the DNS test:
DNS test . . . . . . . . . . . . . : Passed
Interface {34FDC272-55DC-4103-B4B7-89234BC30C4A}
DNS Domain:
DNS Servers: <DNS Server Ip address >
IP Address: Expected registration with PDN (primary DNS domain name):
Hostname: DC.domain.com.
Authoritative zone: domain.com.
Primary DNS server: DC.domain.com <Ip Adress>
Authoritative NS:<Ip Adress>
Check the DNS registration for DCs entries on DNS server <DNS Server Ip address >
The Record is correct on DNS server ‘<DNS Server Ip address >’.
(You will see this line repeated several times for every entry for this DC. Including srv records.)
The Record is correct on DNS server ‘<DNS Server Ip address >’.
PASS — All the DNS entries for DC are registered on DNS server ‘<DNS Server Ip address >’. - ping -a <IP_of_problem_server>
This a simple quick test to validate the host record for a domain controller is resolving to the correct machine. - dnslint /s IP /ad IP
DNSLint is a Microsoft
Windows utility that helps you to diagnose common DNS name resolution
issues. The output for this is an htm file with alot of information
including:DNS server: localhost
IP Address: 127.0.0.1
UDP port 53 responding to queries: YES
TCP port 53 responding to queries: Not tested
Answering authoritatively for domain: NOSOA record data from server:
Authoritative name server: DC.domain.com
Hostmaster: hostmaster
Zone serial number: 14
Zone expires in: 1.00 day(s)
Refresh period: 900 seconds
Retry delay: 600 seconds
Default (minimum) TTL: 3600 seconds -
Additional authoritative (NS) records from server:
DC2.domain.com <IP Address>Alias (CNAME) and glue (A) records for forest GUIDs from server:
CNAME: 98d4aa0c-d8e2-499a-8f90-9730b0440d9b._msdcs.domain.com
Alias: DC.domain.com
Glue: <IP Adress>CNAME: a2c5007f-7082-4adb-ba7d-a9c47db1efc3._msdcs.domain.com
Alias: dc2.child.domain.com
Glue: <IP Address>For more information, Description of the DNSLint utility
4. Verify network ports are not blocked by a firewall or 3rd party application listening on the required ports.
The endpoint mapper (listening on port 135) tells the client which
randomly assigned port a service (FRS, AD replication, MAPI, etc.) is
listening on.
| Application protocol | Protocol | Ports |
| Global Catalog Server | TCP | 3269 |
| Global Catalog Server | TCP | 3268 |
| LDAP Server | TCP | 389 |
| LDAP Server | UDP | 389 |
| LDAP SSL | TCP | 636 |
| LDAP SSL | UDP | 636 |
| IPsec ISAKMP | UDP | 500 |
| NAT-T | UDP | 4500 |
| RPC | TCP | 135 |
| RPC randomly allocated high TCP ports¹ | TCP | 1024 — 5000 49152 — 65535* |
*This is the range in Windows Server 2008, Windows Vista,
Windows 7, and Windows 2008 R2.
Portqry can be used to identify if a port is blocked from a Dc when targeting another DC. It can be downloaded at:
PortQry Command Line Port Scanner Version 2.0
Example Syntax:
portqry -n <problem_server> -e 135
portqry -n <problem_server> -r 1024-5000
A graphical version of portqry, called Portqryui can be found at:
PortQryUI — User Interface for the PortQry Command Line Port Scanner
If the Dynamic Port range has ports being blocked, please use the
below links to configure a port range that manageble for the customer.
Additional Important links for configuration and working with Firewalls and Domain Controllers
HOWTO: Configure RPC Dynamic Port Allocation to Work with Firewall
Restricting Active Directory Replication Traffic to a Specific Port
How to Restrict FRS Replication Traffic to a Specific Static Port
How to Configure a Firewall for Domains and Trusts
A List of the Windows Server Domain Controller Default Ports
Port Requirements for the Microsoft Windows Server System
5. Bad NIC drivers — See network card vendors or OEMs for the latest drivers.
6. UDP fragmentation can cause replication errors that appear to
have a source of RPC server is unavailable. Event ID 40960 & 40961
errors with a source of LSASRV are very common for this particular
cause.
How to force Kerberos to use TCP instead of UDP in Windows
7. SMB signing mismatches between DCs. Using Default Domain
Controllers Policy to configure consistent settings for SMB Signing
under the following section will help address this cause:
Computer ConfigurationWindows SettingsSecurity SettingsLocal PoliciesSecurity Options
Microsoft network client: Digitally sign communications (always) Disabled.
Microsoft network client: Digitally sign communications (if server agrees) Enabled.
Microsoft network server: Digitally sign communications (always) Disabled.
Microsoft network server: Digitally sign communications (if client agrees) Enabled.
The settings can be found under the following registry keys:
HKEY_LOCAL_MACHINESystemCurrentControlSetServicesLanManWorkstationParameters
HKEY_LOCAL_MACHINESystemCurrentControlSetServicesLanManServerParameters
RequireSecuritySignature=always (0,disable, 1 enable).
EnableSecuritySignature=is server agrees (0,disable, 1 enable).
Additional Troubleshooting:
if the above do not provide a solution to the 1722, Then you can use
the following Diagnostic logging to gather more information:
Windows Server 2003 SP2 computers logs extended RPC Server info in NTDS Replication events 1960, 1961, 1962 and 1963.
Crank up NTDS Diagnostic logging
1 = basic, 2 and 3 add continually verbose info and 5 logs extended info.
From BetaArchive Wiki
Jump to:navigation, search
Article ID: 303305
Article Last Modified on 12/3/2007
- Microsoft Windows Server 2003, Standard Edition (32-bit x86)
- Microsoft Windows Server 2003, Enterprise Edition (32-bit x86)
- Microsoft Windows Small Business Server 2003 Premium Edition
- Microsoft Windows Small Business Server 2003 Standard Edition
This article was previously published under Q303305
SYMPTOMS
If you are in a domain in which a user or group has been granted the Replication Synchronization permission on an entire naming context, and you attempt to initiate replication with the Active Directory Sites and Services tool (Dssite.msc) in the context of that user or group, you can receive the following error message:
The following error occurred during the attempt to synchronize naming context Your_naming_context from domain controller Source_DC to domain controller Destination_DC: Replication access has been denied
The operation will not continue.
Yet, when you initiate replication of the specific naming context with either the Active Directory Replication Monitor (Replmon.exe) or the Repadmin.exe tool, both of these tools work as expected.
CAUSE
This behavior occurs because the Active Directory Sites and Services tool initiates replication on all common naming contexts between the replication partners. The container to which the user has the Replication Synchronization permission has replicated successfully. The containers in which the user does not have the right, however, do not replicate, and the user receives an «Access Denied» error message.
RESOLUTION
To work around this behavior, use either the Repadmin.exe or the Replmon.exe tool to initiate replication on specific naming contexts.
STATUS
This behavior is by design.
MORE INFORMATION
The operation returns the «Access Denied» error message. This message does not mean that the replication did not succeed.
To permit the synchronization of a single partition, grant the following permission on the partition head (root of the partition) by using Adsiedit.msc:
«Replication Synchronization» = Allowed
.
Additional query words: domain schema configuration DC= CN= OU=
Keywords: kberrmsg kbprb KB303305