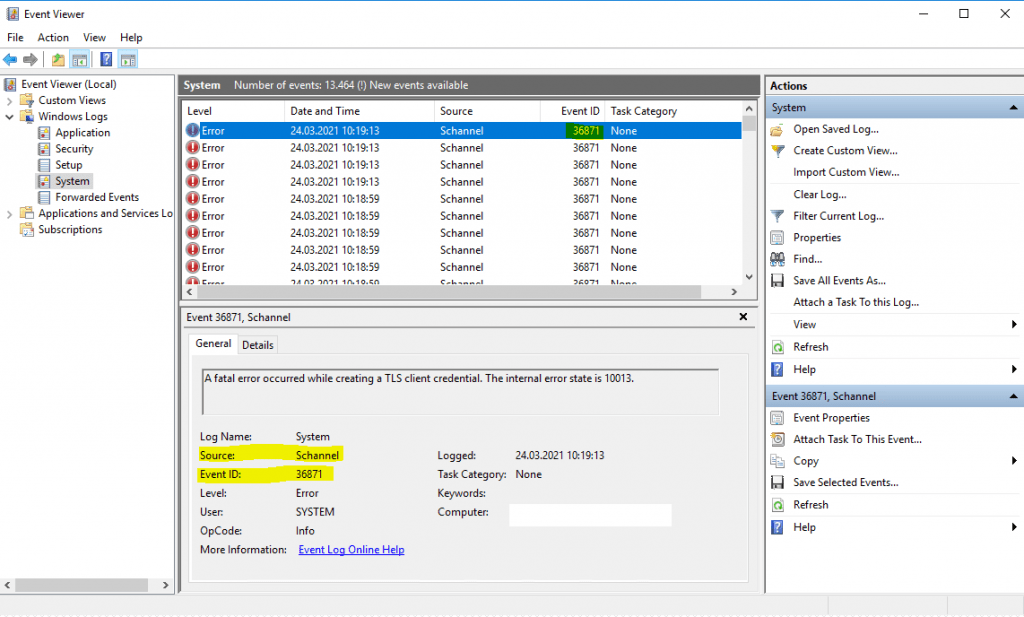
Если вы получаете фатальную ошибку при создании ошибки учетных данных клиента TLS в средстве просмотра событий, вы можете устранить проблему с помощью этого руководства. Эта ошибка возникает как в Windows 11, так и в Windows 10. Однако решения одинаковы независимо от операционной системы.

Все сообщение об ошибке говорит:
Неустранимая ошибка при создании учетных данных клиента TLS. Состояние внутренней ошибки — 10013.
Эта ошибка появляется на вашем компьютере, если у вас не включены TLS 1.0 и TLS 1.1. Хотя некоторым программам может не потребоваться TLS 1.2 или TLS 1.3, некоторым старым программам они могут понадобиться для подключения к Интернету. Если это произойдет, вы можете избавиться от этой ошибки с помощью этих решений.
Исправить Неустранимая ошибка при создании учетных данных клиента TLS. Состояние внутренней ошибки — 10013. при создании ошибки учетных данных клиента TLS выполните следующие действия:
- Включите TLS 1.0/1.1 с помощью свойств Интернета.
- Изменить значения в реестре
Чтобы узнать больше об этих шагах, продолжайте читать.
1]Включите TLS 1.0/1.1, используя свойства Интернета.
Как было сказано ранее, вам необходимо включить или включить TLS 1.0 и TLS 1.1 на вашем компьютере, чтобы решить эту проблему. Поскольку они не включены по умолчанию в Windows 11 и Windows 10, вам необходимо сделать это вручную. Для этого вы можете воспользоваться помощью Интернет-свойства панель. Чтобы включить TLS 1.0/1.1 в Windows 11/10, сделайте следующее:
- Найдите интернет-свойства в поле поиска на панели задач.
- Нажмите на отдельный результат поиска.
- Перейдите на вкладку «Дополнительно».
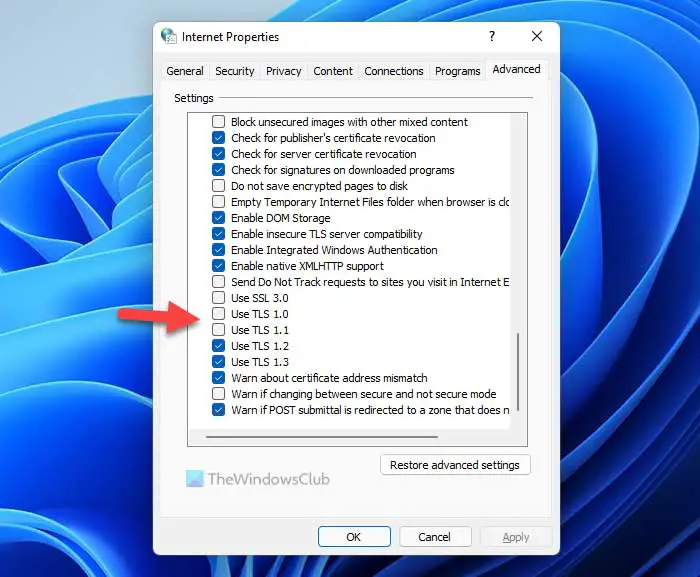
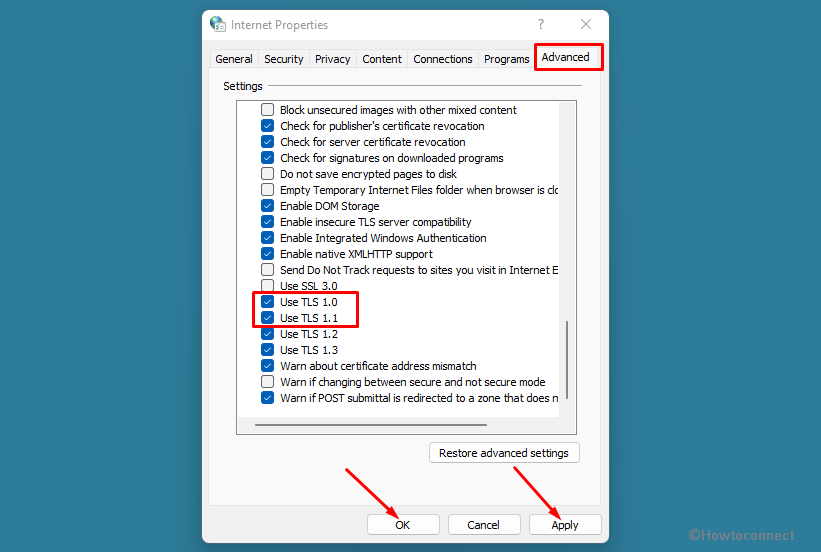
- Найдите TLS 1.0 и TLS 1.1.
- Отметьте оба флажка.
- Нажмите кнопку ОК.
Возможно, вам придется перезагрузить компьютер, чтобы выполнить работу. После этого вы не найдете вышеупомянутое сообщение об ошибке. Чтобы убедиться в этом, вы можете открыть средство просмотра событий и проверить, решена ли проблема или нет.
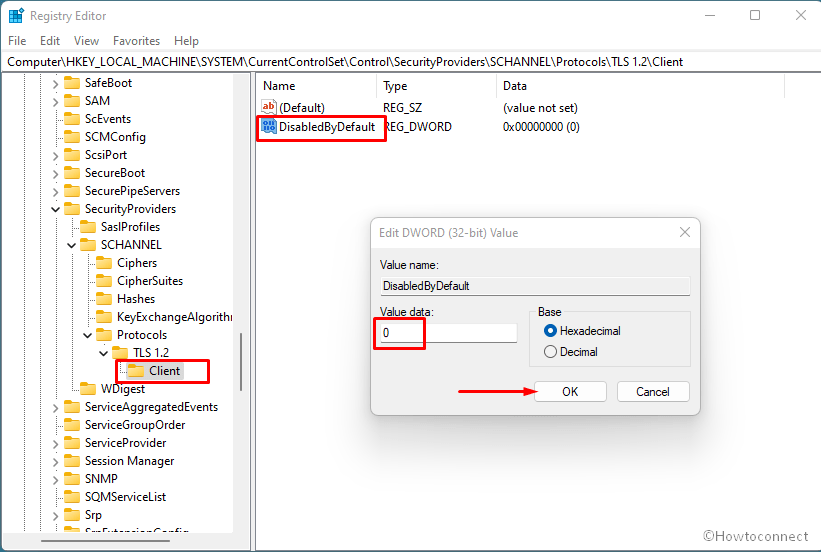
2]Изменить значения в реестре
Если вы получаете вышеупомянутую ошибку, простое изменение в файле реестра может решить проблему. Однако вам может понадобиться создать некоторые ключи и значения REG_DWORD. Будь то Windows 11, Windows 10 или любая другая старая версия, вы можете сделать следующее:
Нажмите Win + R, чтобы открыть окно «Выполнить».
Введите regedit> нажмите кнопку «ОК»> выберите вариант «Да».
Перейдите по этому пути:
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocols
Щелкните правой кнопкой мыши Протоколы > Создать > Ключ и назовите его TLS 1.2.
Щелкните правой кнопкой мыши TLS 1.2 > Создать > Ключ и назовите его как Клиент.
Щелкните правой кнопкой мыши «Клиент»> «Создать»> «Значение DWORD (32-разрядное)».
Установите имя DisabledByDefault.
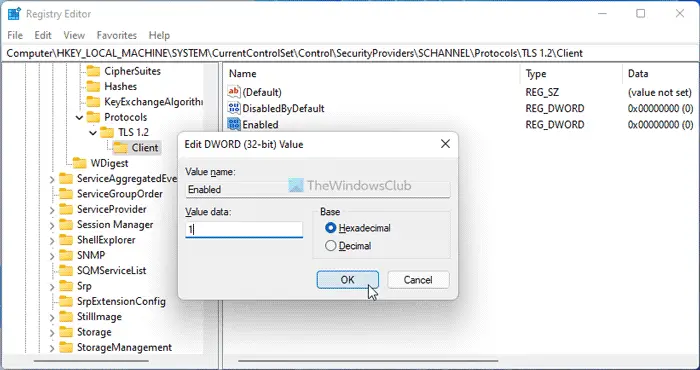
Щелкните правой кнопкой мыши «Клиент»> «Создать»> «Значение DWORD (32-разрядное)».
Установите имя как Включено.
Дважды щелкните по нему, чтобы установить значение данных равным 1.
Нажмите кнопку ОК.
Наконец, перезагрузите компьютер. После этого ваш компьютер больше не будет отображать такие сообщения об ошибках в средстве просмотра событий.
Как проверить, включен ли TLS 1.2?
Самый простой способ проверить, включен ли TLS 1.2 на ПК с Windows 11/10. Вы можете использовать Интернет-свойства панель. Для этого нажмите Win+R чтобы открыть приглашение «Выполнить», введите inetcpl.cpl, и ударил Войти кнопка. Затем переключитесь на Передовой вкладку и перейдите к Безопасность раздел. Теперь проверьте, Используйте TLS 1.2 флажок включен или нет. Если флажок установлен, TLS 1.2 включен.
Как проверить, включен ли TLS 1.0 на сервере?
Чтобы проверить, включен ли TLS 1.0 на сервере, вы можете выполнить те же действия, что и выше. Сказав это, вы можете искать интернет-свойства в поле поиска на панели задач и щелкните отдельное окно поиска. Перейти к Передовой вкладку и проверьте, Используйте TLS 1.0 флажок включен или нет.
Это все! Надеюсь, это руководство помогло.
Читайте . Как отключить TLS 1.0 в Windows 11/10.

- Remove From My Forums
-
Question
-
Recently deployed a Windows 2016 Standard Server, with Active Directory and Exchange 2016.
We have disabled SSL 1.0, 2.0 and 3.0 for both Server and Client, and have disabled TLS 1.0 and TLS 1.1.
We are repeatedly getting the following entry in our system log. What is causing this, and how can I fix it.
Answers
-
The issue and solution isn’t about exchange server, its a .Net Framework issue. Although the article is about Exchange Server its the part about configuring .Net that you need.
In short you need to make registry change:
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINESOFTWAREMicrosoft.NETFrameworkv4.0.30319]
«SystemDefaultTlsVersions»=dword:00000001
[HKEY_LOCAL_MACHINESOFTWAREWow6432NodeMicrosoft.NETFrameworkv4.0.30319]
«SystemDefaultTlsVersions»=dword:00000001This change is for any version of .Net 4
If you need to the same with earlier versions of .Net it is:
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINESOFTWAREMicrosoft.NETFrameworkv2.0.50727]
«SystemDefaultTlsVersions»=dword:00000001
[HKEY_LOCAL_MACHINESOFTWAREWow6432NodeMicrosoft.NETFrameworkv2.0.50727]
«SystemDefaultTlsVersions»=dword:00000001The registry change enables TLS 1.2 for .Net
-
Proposed as answer by
Friday, November 8, 2019 7:05 PM
-
Marked as answer by
Hamid Sadeghpour SalehMVP
Friday, January 31, 2020 12:19 PM
-
Proposed as answer by
If you are getting A fatal error occurred while creating a TLS client credential error in the Event Viewer, you can troubleshoot the problem with the help of this guide. This error occurs on Windows 11 as well as Windows 10. However, the solutions are the same irrespective of the operating system.

The entire error message says:
A fatal error occurred while creating a TLS client credential. The internal error state is 10013.
This error appears on your computer when you do not have the TLS 1.0 and TLS 1.1 enabled. Although some programs may not require when you have TLS 1.2 or TLS 1.3, some old programs might need them for connecting to the internet. If it happens, you can get rid of this error with the help of these solutions.
To fix A fatal error occurred while creating a TLS client credential, The internal error state is 10013 while creating a TLS client credential error, follow these steps:
- Enable TLS 1.0/1.1 using Internet Properties
- Change values in the Registry
To learn more about these steps, continue reading.
1] Enable TLS 1.0/1.1 using Internet Properties
As said earlier, you need to enable or turn on TLS 1.0 and TLS 1.1 on your computer in order to fix this issue. As these are not enabled by default on Windows 11 and Windows 10, you need to do that manually. For that, you can get the help of the Internet Properties panel. In order to enable TLS 1.0/1.1 on Windows 11/10, do the following:
- Search for internet properties in the Taskbar search box.
- Click on the individual search result.
- Switch to the Advanced tab.
- Find the TLS 1.0 and TLS 1.1.
- Tick both checkboxes.
- Click the OK button.
You may need to restart your computer to get the job done. Once done, you won’t find the aforementioned error message. To verify that, you can open the Event Viewer and check if the problem is resolved or not.
However, this needs to be a temporary measure only, as it is not very secure to use TLS 1.10 and TLS 1.1 for long.
2] Change values in the Registry
If you get the above-mentioned error, a simple change in the Registry file could fix the issue. However, you may need to create some keys and REG_DWORD values as well. Whether it is Windows 11, Windows 10, or any other older version, you can do the following:
Press Win+R to open the Run prompt.
Type regedit > click the OK button > click the Yes option.
Navigate to this path:
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocols
Right-click on Protocols > New > Key and name it as TLS 1.2.
Right-click on TLS 1.2 > New > Key and name it as Client.
Right-click on Client > New > DWORD (32-bit) Value.
Set the name as DisabledByDefault.
Right-click on Client > New > DWORD (32-bit) Value.
Set the name as Enabled.
Double-click on it to set the Value data as 1.
Click the OK button.
Finally, restart your computer. Once done, your computer won’t show such error messages in the Event Viewer anymore.
How do you check if TLS 1.2 is enabled?
The easiest way to check if TLS 1.2 is enabled or not on Windows 11/10 PC. You can use the Internet Properties panel. For that, press Win+R to open the Run prompt, type inetcpl.cpl, and hit the Enter button. Then, switch to the Advanced tab and navigate to the Security section. Now, check if the Use TLS 1.2 checkbox is enabled or not. If ticked, TLS 1.2 is turned on.
How do you check if TLS 1.0 is enabled on server?
To check if TLS 1.0 is enabled on the server or not, you can use the same steps as above. Having said that, you can search for internet properties in the Taskbar search box and click on the individual search box. Go to the Advanced tab and check if the Use TLS 1.0 checkbox is enabled or not.
That’s all! Hope this guide helped.
Read: How to disable TLS 1.0 in Windows 11/10.
A fatal error occurred while creating a TLS client credential. The internal error state is 10013″. The Windows tool prompts this message repeatedly and disturbs continuing ongoing tasks.
The fatal error occurred while creating a TLS client credential commonly appears when you launch a program, browse the web, or connect to a network. The reason is a disagreement between client and server on a mutual cipher to use to establish a secure connection. However, you can fix the internal error state is 10013 in Windows 11 or 10 simply using the methods in the upcoming parts of this post –
Here is how to Fix A fatal error occurred while creating a TLS client credential. The internal error state is 10013 Windows 11/10 –
For Windows 10 or 11 –
Way-1: Enable TLS 1.0 and 1.1 Protocols
- Press – Windows+R.
- Type – ncpa.cpl.
- Click OK or hit Enter.
- Once the Internet properties window opens up, click on the Advanced tab.
- Scroll down and check both Use TLS 1.0 and Use TLS 1.1.
- Click Apply and then OK.
- Reboot the device and check if the error A fatal error occurred while creating a TLS client credential still appears.
Way-2: Registry tweak to fix The internal error state is 10013
- Click – Search.
- Type – regedit. See – 9 Ways to Open Registry Editor in Windows 10.
- Hit – Enter.
- On User Account Control prompt, select – Yes.
- On the Registry Editor, navigate to the location –
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.2Client
- Go to right pane, right click and select New => DWORD (32-bit) Value.
- Name the value DisabledByDefault.
- Double click on this value and enter Value data 0.
- Click – OK.
- Similarly, create one more value named, Enabled. and put value data 1 for this.
- Close the registry editor and restart the PC.
For Windows Server
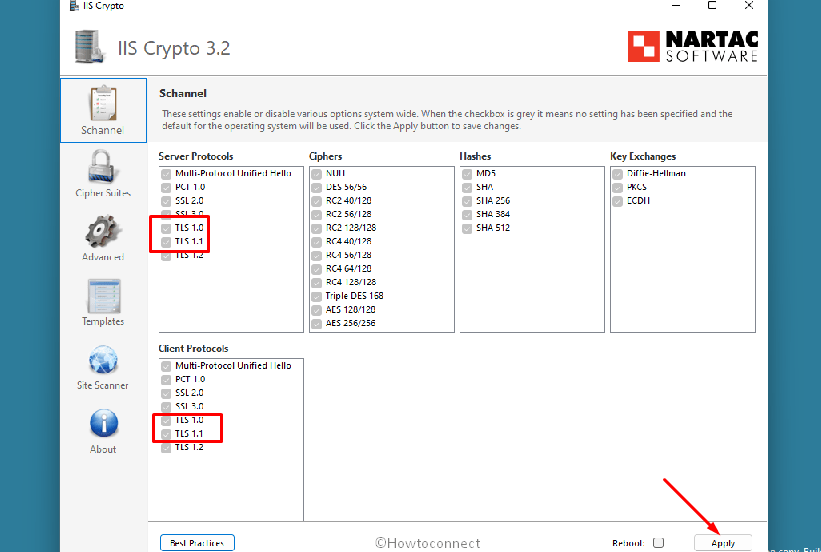
Way-3: Enable deprecated Transport Layer Security protocols
- Click on IIS Crypto GUI and download the tool.
- Double click on IISCrypto.exe and launch the app.
- By default, it opens with the Schannel tab.
- Check TLS 1.0 and TLS 1.1 in both the Server protocols and Client protocols sections.
- Click on – Apply. These are the deprecated protocols.
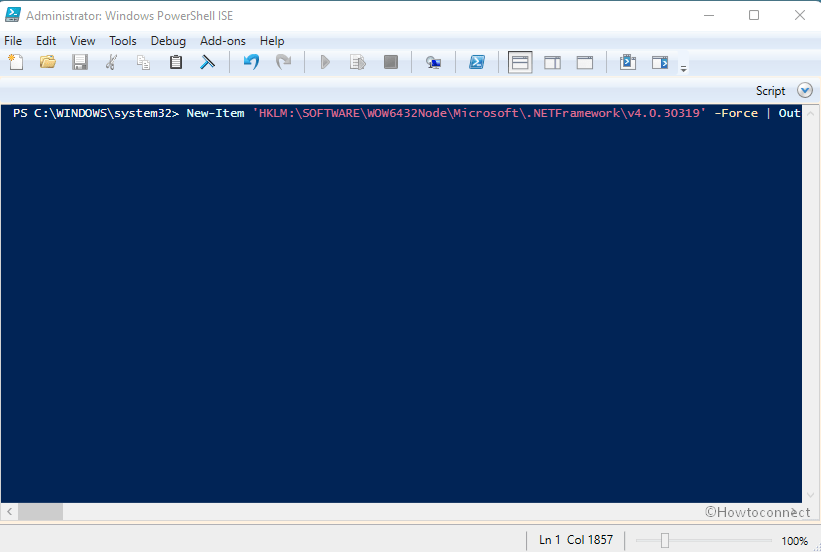
Way-4: Solve A fatal error occurred while creating a TLS client credential by running a PowerShell Script
You can also enable TLS 1.2 using a script. Simply follow the steps –
- Download TLS1.2_enable.
- Unpack the file by extracting the file.
- Right-click on the TLS1.2_enable.ps1 and select Run with PowerShell.
- Alternatively, launch PowerShell ISE.
- Copy the following script –
New-Item 'HKLM:SOFTWAREWOW6432NodeMicrosoft.NETFrameworkv4.0.30319' -Force | Out-Null New-ItemProperty -path 'HKLM:SOFTWAREWOW6432NodeMicrosoft.NETFrameworkv4.0.30319' -name 'SystemDefaultTlsVersions' -value '1' -PropertyType 'DWord' -Force | Out-Null New-ItemProperty -path 'HKLM:SOFTWAREWOW6432NodeMicrosoft.NETFrameworkv4.0.30319' -name 'SchUseStrongCrypto' -value '1' -PropertyType 'DWord' -Force | Out-Null New-Item 'HKLM:SOFTWAREMicrosoft.NETFrameworkv4.0.30319' -Force | Out-Null New-ItemProperty -path 'HKLM:SOFTWAREMicrosoft.NETFrameworkv4.0.30319' -name 'SystemDefaultTlsVersions' -value '1' -PropertyType 'DWord' -Force | Out-Null New-ItemProperty -path 'HKLM:SOFTWAREMicrosoft.NETFrameworkv4.0.30319' -name 'SchUseStrongCrypto' -value '1' -PropertyType 'DWord' -Force | Out-Null New-Item 'HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.2Server' -Force | Out-Null New-ItemProperty -path 'HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.2Server' -name 'Enabled' -value '1' -PropertyType 'DWord' -Force | Out-Null New-ItemProperty -path 'HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.2Server' -name 'DisabledByDefault' -value 0 -PropertyType 'DWord' -Force | Out-Null New-Item 'HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.2Client' -Force | Out-Null New-ItemProperty -path 'HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.2Client' -name 'Enabled' -value '1' -PropertyType 'DWord' -Force | Out-Null New-ItemProperty -path 'HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.2Client' -name 'DisabledByDefault' -value 0 -PropertyType 'DWord' -Force | Out-Null Write-Host 'TLS 1.2 has been enabled.'
- Paste the script in PowerShell ISE.
- Press – Enter.
- Restart the Windows Server.
- Now open Start Event Viewer. Go to Windows Logs and click – System.
- You will no longer find The error “Event ID 36871: A fatal error occurred while creating a TLS client credential. The internal error state is 10013.”
Methods list:
Way-1: Enable TLS 1.0 and 1.1 Protocols
Way-2: Registry tweak to fix The internal error state is 10013
Way-3: Enable deprecated Transport Layer Security protocols
Way-4: Run a PowerShell Script
That’s all!!
Repair any Windows problems such as Blue/Black Screen, DLL, Exe, application, Regisrty error and quickly recover system from issues using Reimage.
If you have disabled the deprecated server and client protocols TLS 1.0 and TLS 1.1 on your Windows Server as further down for security reasons.
And after that you will see a bunch of error messages as in the title of this post like this.
You have to add the following registry DWORD value like follows.
https://docs.microsoft.com/en-us/dotnet/framework/network-programming/tls#systemdefaulttlsversions
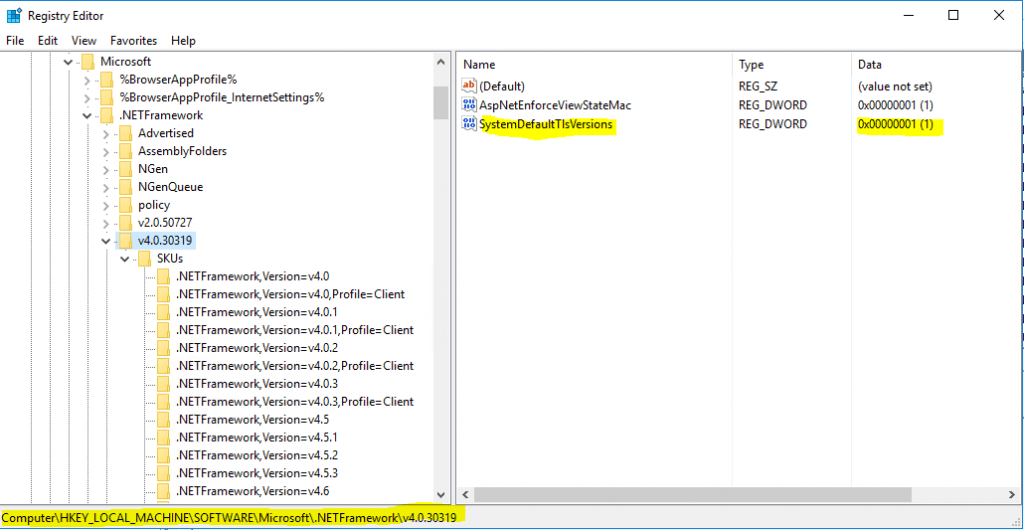
HKEY_LOCAL_MACHINESOFTWAREMicrosoft.NETFrameworkv4.0.30319
“SystemDefaultTlsVersions”=dword:00000001This registry key has a value of type DWORD. A value of 1 causes your app to allow the operating system to choose the protocol. A value of 0 causes your app to use protocols picked by the .NET Framework.
If your app targets .NET Framework 4.7 or later versions, this key defaults to a value of 1. That’s a secure default that we recommend. If your app targets .NET Framework 4.6.1 or earlier versions, the key defaults to 0. In that case, you should explicitly set its value to 1.
To ensure .NET Framework applications remain secure, the TLS version should not be hardcoded. .NET Framework applications should use the TLS version the operating system (OS) supports.
So in case of our error messages, .NET Framework was trying to use one of the disabled TLS 1.0 or TLS 1.1 client protocols. Now after setting SystemDefaultTlsVersions to 1, the operating system is now choosing the right and available protocol instead the .NET Framework itself.
This change is for any version of .NET 4 and 64 Bit Applications.
For versions before .NET 4 you need to add the value in HKEY_LOCAL_MACHINESOFTWAREMicrosoft.NETFrameworkv2.0.50727
After a reboot the error messages should stay out and disappear.
For 32 Bit Applications and .Net 4 and above you need to add the value in HKEY_LOCAL_MACHINESOFTWAREWOW6432NodeMicrosoft.NETFrameworkv4.0.30319 resp. v2.0.50727 for versions before .Net 4.
https://docs.microsoft.com/en-us/dotnet/framework/network-programming/tls#systemdefaulttlsversions
The following .REG file sets the registry keys and their variants to their most safe values:
Windows Registry Editor Version 5.00 [HKEY_LOCAL_MACHINESOFTWAREWOW6432NodeMicrosoft.NETFrameworkv2.0.50727] "SystemDefaultTlsVersions"=dword:00000001 "SchUseStrongCrypto"=dword:00000001 [HKEY_LOCAL_MACHINESOFTWAREWOW6432NodeMicrosoft.NETFrameworkv4.0.30319] "SystemDefaultTlsVersions"=dword:00000001 "SchUseStrongCrypto"=dword:00000001 [HKEY_LOCAL_MACHINESOFTWAREMicrosoft.NETFrameworkv2.0.50727] "SystemDefaultTlsVersions"=dword:00000001 "SchUseStrongCrypto"=dword:00000001 [HKEY_LOCAL_MACHINESOFTWAREMicrosoft.NETFrameworkv4.0.30319] "SystemDefaultTlsVersions"=dword:00000001 "SchUseStrongCrypto"=dword:00000001
Links
You may face the issue with Event ID 36871 after upgrading to a greater version of Windows 11 or 10. The issue will show ‘A fatal error occurred while creating a TLS client credential. The internal error state is 10013’ in Windows logs under the Console tree in Event Viewer.
You may wonder why a fatal error occurs when updating the Windows to a higher version. However, this error will be resolved easily, as long as you know the methods to fix it. Thankfully, this post will show you a guide on how to fix this fatal error when upgrading your Windows. Here you go!
What Is the Cause of the Fatal Error Issue When Upgrading Windows?
The Windows tool will require the error message that says ‘A fatal error occurred while creating a TLS client credential. The internal error state is 10013’ repeatedly. We think you will be bothered with this continuing ongoing task.
The fatal error that occurs while creating a TLS client credential will commonly appear as you launch a program, browse the web or also connect to a network. This issue occurs because of a disagreement between the server and client on a mutual cipher to use to build a secure connection.
It does not matter, as you can fix this fatal error easily. You definitely can solve the internal error state in Windows 11 or 10 by taking some steps that will show in the next section.
Fixing the Fatal Error When Upgrading Windows, Here’s How!
There are a bunch of methods that you can take to fix ‘A fatal error occurred while creating a TLS client credential. The internal error state is 10013’ message after upgrading the Windows to a higher version. Here are some methods that you can do to fix this fatal error:
Method 1: Enable TLS 1.0 and 1.1 Protocols
To fix the fatal error when upgrading the Windows to a higher version, you can try to enable Enable TLS 1.0 and 1.1 Protocols. To do so, you can do the following steps:
-
- First, you can open ‘Run’ by pressing Windows + R.
- On the command box, you can type ‘ncpa.cpl’.
- Then, you can click ‘OK’ or press ‘Enter’.
- After the Internet properties window pops up, you can then click the ‘Advanced’ tab.
- You may need to scroll down and check both ‘Use TLS 1.0’ and ‘Use TLS 1.1’.
- After that, click ‘Apply’. Then, click ‘OK’.
- Last, you can reboot the device and check if the fatal error while creating a TLS client credential still appears.
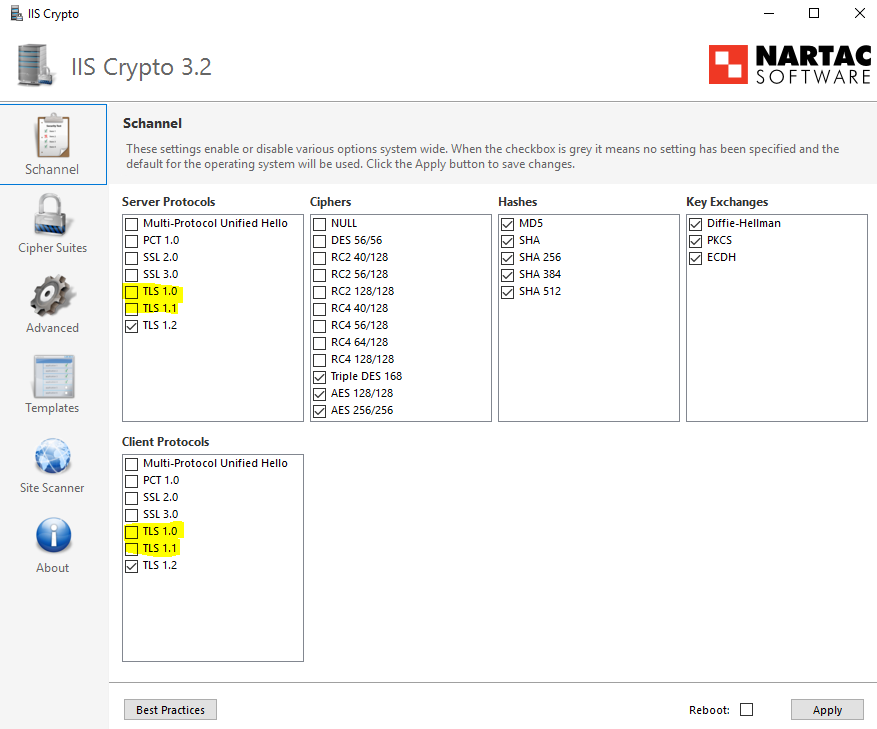
Method 2: Enable deprecated Transport Layer Security protocols
In addition to enabling the TLS 1.0 and 1.1 Protocols, you can also try to enable deprecated Transport Layer Security protocols. This way can be performed for Windows Server. Here’s how!
-
- First, you can click on IIS Crypto GUI and download the tool.
- After downloading the tool, you can then double click on IISCrypto.exe.
- Then, you can launch the app.
- By default, it will bring the ‘Schannel’ tab.
- You need to check TLS 1.0 and TLS 1.1 in both the Server protocols and Client protocols sections.
- You can then click on ‘Apply’ where they are the deprecated protocols.
Method 3: Registry tweak to fix The Internal error state is 10013
You can also try to make registry changes to fix the fatal error when upgrading the Windows to a higher version. This method can be performed for Windows 10 or 11. To do so, you can perform some steps, as follow:
-
- First, click the ‘Search’.
- Then, type the ‘regedit’ and hit ‘Enter’.
- You can choose ‘Yes’ on the User Account Control prompt.
- You can navigate to the location on the Registry Editor to ‘HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.2Client’
- After that, you can go to right pane and right click and choose ‘New => DWORD (32-bit) Value’
- You can name the value ‘DisabledByDefault’.
- Make sure to double click on the value and then enter Value data 0. Then, click ‘OK’.
- Similarly, you can make one more value named, Enabled. You can then put value data 1 for this.
- You can then close the registry editor and restart the PC.
Method 4: Running a PowerShell Script
For the last method, you can try to run a PowerShell Script to fix a fatal error occured while creating a TLS client credential. Well, you can try to enable TLS 1.2 using a script. Let’s follow the steps below!
-
- First, you need to download ‘TSL1.2_enable’ here.
- After the downloading process is completed, you can then extract the file.
- Then, right-click on the TLS1.2_enable.ps1 and choose ‘Run’ with PowerShell.
- As an alternative way, you can also launch PowerShell ISE.
- Then, copy the following Script:
New-ItemProperty -path ‘HKLM:SOFTWAREWOW6432NodeMicrosoft.NETFrameworkv4.0.30319’ -name ‘SystemDefaultTlsVersions’ -value ‘1’ -PropertyType ‘DWord’ -Force | Out-Null
New-ItemProperty -path ‘HKLM:SOFTWAREWOW6432NodeMicrosoft.NETFrameworkv4.0.30319’ -name ‘SchUseStrongCrypto’ -value ‘1’ -PropertyType ‘DWord’ -Force | Out-Null
New-Item ‘HKLM:SOFTWAREMicrosoft.NETFrameworkv4.0.30319’ -Force | Out-Null
New-ItemProperty -path ‘HKLM:SOFTWAREMicrosoft.NETFrameworkv4.0.30319’ -name ‘SystemDefaultTlsVersions’ -value ‘1’ -PropertyType ‘DWord’ -Force | Out-Null
New-ItemProperty -path ‘HKLM:SOFTWAREMicrosoft.NETFrameworkv4.0.30319’ -name ‘SchUseStrongCrypto’ -value ‘1’ -PropertyType ‘DWord’ -Force | Out-Null
New-Item ‘HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.2Server’ -Force | Out-Null
New-ItemProperty -path ‘HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.2Server’ -name ‘Enabled’ -value ‘1’ -PropertyType ‘DWord’ -Force | Out-Null
New-ItemProperty -path ‘HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.2Server’ -name ‘DisabledByDefault’ -value 0 -PropertyType ‘DWord’ -Force | Out-Null
New-Item ‘HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.2Client’ -Force | Out-Null
New-ItemProperty -path ‘HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.2Client’ -name ‘Enabled’ -value ‘1’ -PropertyType ‘DWord’ -Force | Out-Null
New-ItemProperty -path ‘HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.2Client’ -name ‘DisabledByDefault’ -value 0 -PropertyType ‘DWord’ -Force | Out-Null
Write-Host ‘TLS 1.2 has been enabled.’
-
- You can then paste the script above in PowerShell ISE.
- After that, you can press ‘Enter’.
- Then, you need to restart the Windows Server.
- Now, you can open Start ‘Event Viewer’ and go to ‘Windows Logs’ and then click the ‘System’.
- You will no longer see the error ‘Event ID 36871: A fatal error occurred while creating a TLS client credential. The internal error state is 10013.’ on your Windows.
Okay, those are four methods that you can use to try fixing ‘A fatal error occurred while creating a TLS client credential. The internal error state is 10013.’ after you upgrade your Windows to a higher version. Good Luck!!!
AUTHOR BIO
On my daily job, I am a software engineer, programmer & computer technician. My passion is assembling PC hardware, studying Operating System and all things related to computers technology. I also love to make short films for YouTube as a producer. More at about me…
To totally unlock this section you need to Log-in
Login
You may run into Schannel – The internal error state is 10013 message if your website fails establishing TLS connection and usually this could occur using Internet Explorer 11 to connect to modern websites or portals that are using TLS 1.2 or better protocols for encryption.
That is to say, here is the error message you will see in Event Viewer:
Error – Schannel – A fatal error occurred while creating an SSL client credential. The internal error state is 10013
This error is logged when there are Schannel Security Service Provider (SSP) related issues. For example, web server might be trying to use an encryption algorithm or protocol (or cipher suite, like the old RC4) that were actually disabled.
Similarly, incompatible machine keys or machine keys with insufficient file permissions may be other possible reasons of «The internal error state is 10013» error message and this could lead to multiple error entries of this kind into the Event Viewer on the machine from which we are trying to connect, for each try to connect to the website.
To solve «The internal error state is 10013» issue we will have to follow some simple steps: if after this modifications there will be no more 10013 errors logged, then you will have to make sure that all other applications and services (especially web services) you have configured, installed and enabled on your server are working as expected.
The first Method: Correct file permissions
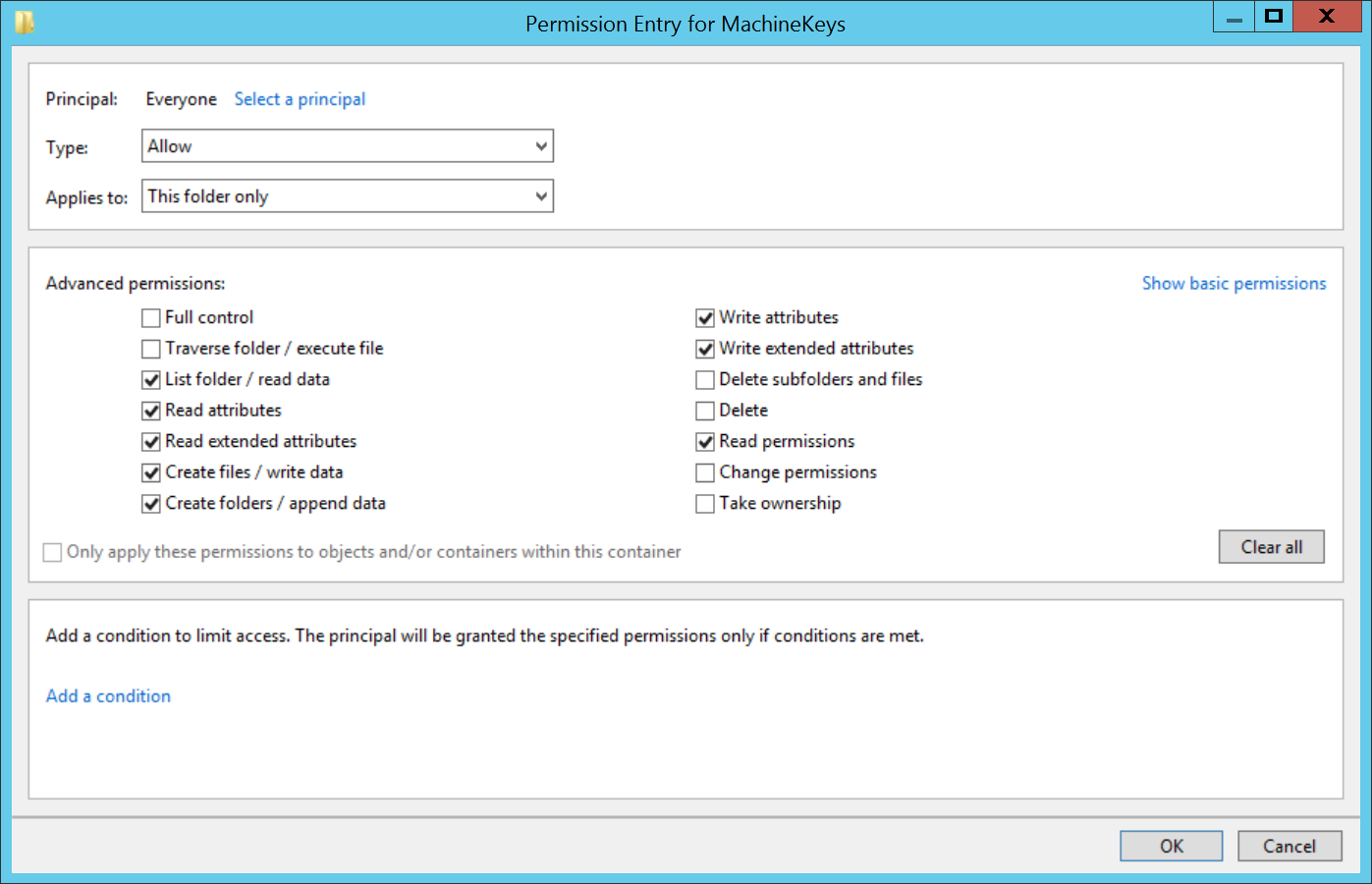
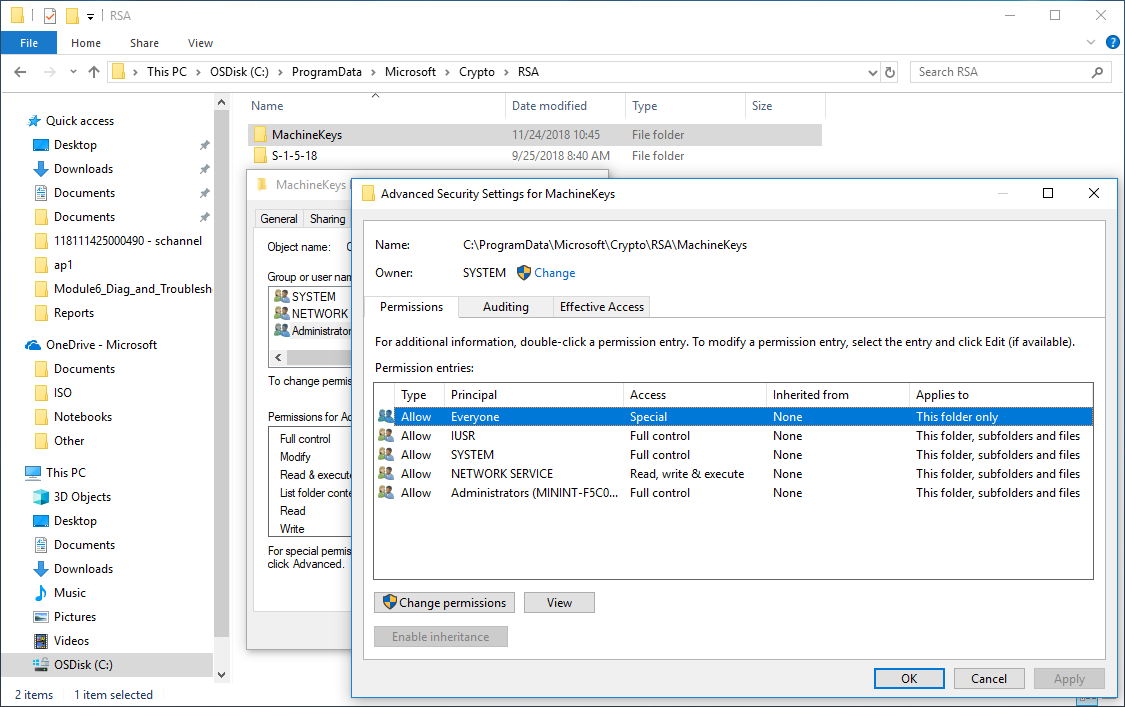
Correct the permissions on the C:ProgramDataMicrosoftCryptoRSAMachineKeys folder:
- Everyone: Special and Applies to: This folder only.
- Network Service: Read & Execute and Applies to: This folder, subfolders and files.
- Administrators: Full Control and Applies to: This folder, subfolder and files.
- SYSTEM: Full control and Applies to: This folder, subfolder and Files.
- IUSR (For IIS Anonymous User): Full Control and Applies to: This folder, subfolder and files.
For the Everyone Special permissions the following is the detail of the specific configuration:
The following screenshot will show the complete Security tab specification for the C:ProgramDataMicrosoftCryptoRSAMachineKeys folder:
Once you have completed the above permission changes or integration you will have to restart the server. At this point, if the issue was generated by permission changes to the MachineKeys folder then the 10013 eventserrors should dissappear. However, If you still see Schannel 10013 errors in the Event Viewer, then it means that there was no permission issues on the core MachineKeys folder, so we will go forward by enabling a local system policy that will force modern security protocols for encryption for several services (however, keep the changes you made until now).
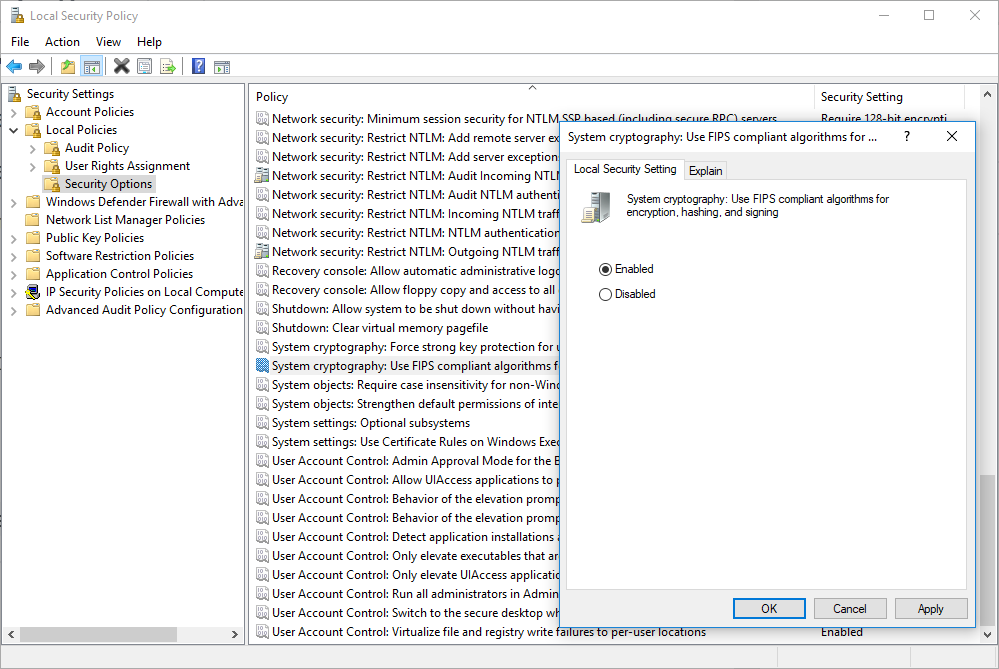
The second Method: Enable FIPS compliant algorithms
Enabling the FIPS compliant algorithms on a server could have several implications on some system implementations; however, in some cases, like this one, this policy should be enabled to let Internet Explorer 11 to properly reach and display TLS 1.2 websites and portals (this policy will not impact on other common browsers, like Google Chrome or Opera).
Actually, with this method we are going to enable on the system the Federal Information Processing Standard (FIPS) 140, that is a security implementation that is designed for certifying cryptographic software. Windows implements these certified algorithms to meet the requirements and standards for cryptographic modules for use by departments and agencies of the United States federal government.
Now we can see which changes are done to the system by applying this policy (Group Policy):
TLS/SSL
This policy setting determines whether the TLS/SSL security provider supports only the FIPS-compliant strong cipher suite known as TLS_RSA_WITH_3DES_EDE_CBC_SHA, which means that the provider only supports the TLS protocol as a client computer and as a server, if applicable. It uses only the Triple Data Encryption Standard (3DES) encryption algorithm for the TLS traffic encryption, only the Rivest-Shamir-Adleman (RSA) public key algorithm for the TLS key exchange and authentication, and only the Secure Hash Algorithm version 1 (SHA-1) hashing algorithm for the TLS hashing requirements.
Encrypting File System (EFS)
For the EFS service, this policy setting supports the 3DES and Advanced Encryption Standard (AES) encryption algorithms for encrypting file data supported by the NTFS file system. To encrypt file data, by default EFS uses the Advanced Encryption Standard (AES) algorithm with a 256-bit key in the Windows Server 2003, Windows Vista, and later, and it uses a DESX algorithm in Windows XP.
Remote Desktop Services (RDS)
If you’re using Remote Desktop Services, this policy setting should only be enabled if the 3DES encryption algorithm is supported.
BitLocker
For BitLocker, this policy setting needs to be enabled before any encryption key is generated. Recovery passwords created on Windows Server 2012 R2 and Windows 8.1 and later when this policy is enabled are incompatible with BitLocker on operating systems prior to Windows Server 2012 R2 and Windows 8.1; BitLocker will prevent the creation or use of recovery passwords on these systems, so recovery keys should be used instead. Additionally, if a data drive is password-protected, it can be accessed by a FIPS-compliant computer after the password is supplied, but the drive will be read-only.
Turning back to the specific issue, we will have to follow these steps:
- Go to Control Panel.
- Click Administrative Tools.
- Double click Local Security Policy (or just open gpedit.msc from Run).
- Once opened Local Security Settings, expand the Local Policies branch and finally click Security Options.
- Double click System cryptography: Use FIPS compliant algorithms for encryption, hashing, and signing to set the value of this property.
- Select Enabled.
- Click OK.
- Run gpupdate /force in a Command Prompt, with administrative privilege.
Take note that the change to this policy become effective without a device restart when they are saved locally or distributed through Group Policy, so after you have issued the gpupdate /force command you will be good to go and ready to reload Internet Explorer 11 to see if the issue has been solved. Even in Event Viewer you should not see anymore SChannel 10013 errors related to TLS.
NOTE: we strongly recommend that you implement this change on a beta or staging server to make sure your application is not malfunctioning due to this change. Once you are confident that your application is working fine after this change then you can implement it on your production server.
Checking IE11 Cryptographic Protocols
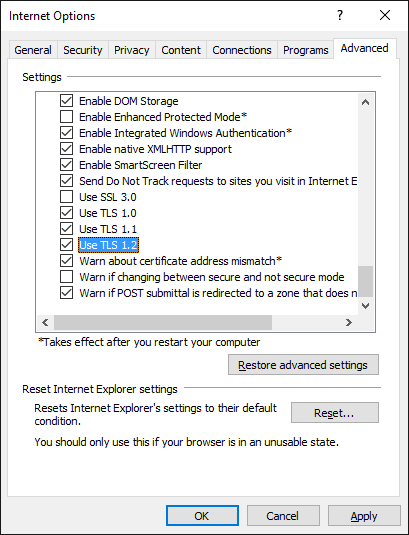
Finally, in Internet Explorer 11, make sure you have enabled only TLS protocols (no SSL2 and SSL3, they are insecure and deprecated).
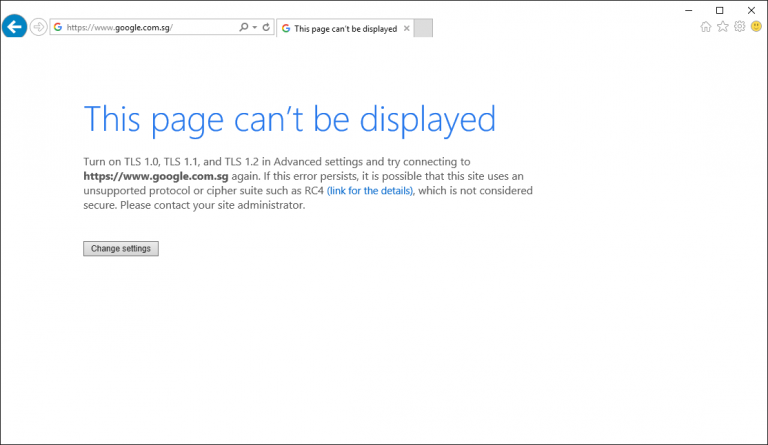
So, if after the enable of the FIPS algorithms you are getting the following error using Internet Explorer 11…
This page can’t be displayed – Turn on TLS 1.0, TLS 1.1, and TLS 1.2 in Advanced settings and try connecting to https://www.google.com again. If this error persists, it is possible that this site uses an unsupported protocol or cipher suite such as RC4 (link for the details), which is not considered secure. Please contact your site administrator.
…you will have to check (and enable if disabled) the ciphers in Tools > Internet Options > Advanced, in the Settings scrollbox, looking under Security, you will see cipher suites TLS 1.0, 1.1, and 1.2 (you will have to enable at least TLS 1.1 and TLS 1.2) that should be selected by default in Internet Explorer 11.
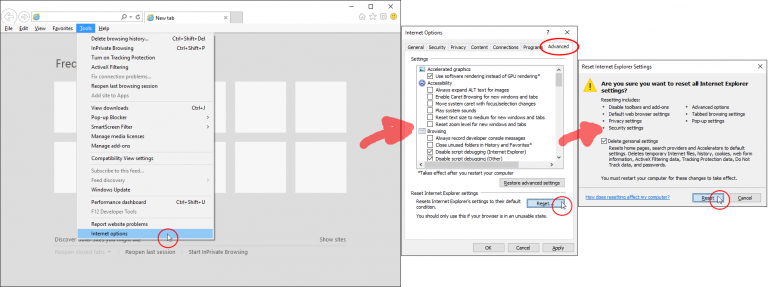
In alternative, you could just reset IE11 to default settings by going back to Tools > Internet Options > Advanced, under Reset Internet Explorer settings, and clicking on Reset. In the Reset Internet Explorer settings window, check the box Delete personal settings, and click on Reset.
Once done, simply restart IE11 and try browsing again.
Checking TLS 1.2 if Enabled
On older Windows Server platforms, like Server 2008 and Server 2008 R2, we recommends checking and enabling and using the TLS 1.2 protocol on your server.
By default, Windows Server 2008 and 2008 R2 does not have this feature enabled.
IMPORTANT NOTE: the internal error state of SChannel 10013 can be seen also if the system, even with FIPS 140 enabled by local policy (as in the second method shown above), is trying to reach a remote website that is still using a TLS 1.0 certificate but the TLS 1.0 on the local system, in the Windows Registry, has, for the TLS 1.0 protocol, the key DisabledByDefault has value 1 and Enabled has value 0 (so it is basically disabled system-wide, even if in Internet Explorer, in Internet Options, the TLS 1.0 is actually enabled).
Now, to check the TLS 1.2 protocol is correctly enabled (the same procedure can be followed also for TLS 1.0 and TLS 1.1) you will have to follow the steps below:
- Start the registry editor by clicking on Start and Run. Type in «regedit» into the Run field (without quotations).
- Highlight Computer at the top of the registry tree. Backup the registry first by clicking on File and then on Export.
- Select a file location to save the registry file.
NOTE: You will be editing the registry. This could have detrimental effects on your computer if done incorrectly, so it is strongly advised to make a backup.
Browse to the following registry key:
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocols
Right click on the Protocols folder and select New and then Key from the drop-down menu. This will create new folder. Rename this folder to TLS 1.2.
IMPORTANT NOTE: do this only if the TLS 1.2 is not already present/created.
Right click on the TLS 1.2 key and add two new keys underneath it.
Rename the two new keys as:
Client Server
- Right click on the Client key and select New and then DWORD (32-bit) Value from the drop-down list.
- Rename the DWORD to DisabledByDefault.
- Right-click the name DisabledByDefault and select Modify… from the drop-down menu.
- Ensure that the Value data field is set to 0 and the Base is Hexadecimal. Click on OK.
- Create another DWORD for the Client key as you did in the previous step.
- Rename this second DWORD to Enabled.
- Right-click the name Enabled and select Modify… from the drop-down menu.
- Ensure that the Value data field is set to 1 and the Base is Hexadecimal. Click on OK.
Repeat necessary steps for the Server key, by creating two DWORDs, DisabledByDefault and Enabled, and their values underneath the Server key.
Reboot the server. Your server should now support TLS 1.2 (remember to update Server 2008 and 2008 R2 to latest updates before creating or checking these registry keys).
NOTE: This article cannot be used on a Windows Server 2003 (IIS 6). Windows Server 2003 does not support the TLS 1.2 protocol.
Reverting Back
If you make a mistake or something just isn’t right, you can revert back to your previous registry settings by opening the Registry Editor and importing the backup you made in previous step.