Posted On October 12, 2020
TLDR: This can also be caused by a mismatch in security policy “Network Security: Configure encryption types allowed for Kerberos“.
Consider the following scenario:
- You have a web site set up to use Kerberos authentication. It doesn’t matter what kind of site, but we’ll say it’s a SharePoint site, since that’s the theme around here.
- The site is at https://teams.contoso.com and its application pool is running as service account CONTOSOSP_WEB_APP_SVC.
- Kernel Mode authentication is not enabled in IIS Manager.
-
Domain users try to access the site and get three authentication prompts and then Access Denied.
- Note: It’s possible that some users could have this “access denied” behavior, while others have no trouble accessing the site.
- You look in the System event log on the web server(s) and find this error:
Event Type: Error
Event Source: Kerberos
Event Category: None
Event ID: 4
Date: The present
Time: Doesn’t matter
User: N/A
Computer: WFE1
Description:
The Kerberos client received a KRB_AP_ERR_MODIFIED error from the server SP_WEB_APP_SVC. The target name used was HTTP/teams.contoso.com. This indicates that the target server failed to decrypt the ticket provided by the client. This can occur when the target server principal name (SPN) is registered on an account other than the account the target service is using. Ensure that the target SPN is only registered on the account used by the server. This error can also happen if the target service account password is different than what is configured on the Kerberos Key Distribution Center for that target service. Ensure that the service on the server and the KDC are both configured to use the same password. If the server name is not fully qualified, and the target domain (CONTOSO.COM) is different from the client domain (CONTOSO.COM), check if there are identically named server accounts in these two domains, or use the fully-qualified name to identify the server.
Most commonly, the “KRB_AP_ERR_MODIFIED” error means that you have a Service Principal Name (SPN) issue, specifically, the SPN has been added to the wrong account. You should check those things first.
In our scenario above, we know that the application pool is running as a domain account and Kernel Mode authentication is disabled, which is the typical configuration for a SharePoint web app. In that case, we need an HTTP SPN set for the site host name, and set on the account running the application pool.
We can use SETSPN -l (that’s a lower case L) to see which SPNs have been set on our service account:
Command: setspn -l CONTOSOSP_WEB_APP_SVC
Example output:
Registered ServicePrincipalNames for CN=SP_WEB_APP_SVC,OU=Service Accounts,DC=contoso,DC=com:
HTTP/teams.contoso.com
HTTP/teams
You an also do it the opposite way, where you search for a given SPN to see which account it’s set on. For that you use SETSPN -q
Command: setspn -q HTTP/teams.contoso.com
Example output:
Checking domain DC=contoso,DC=com
CN=SP_WEB_APP_SVC,OU=Service Accounts,DC=contoso,DC=com
HTTP/teams.contoso.com
HTTP/teams
Existing SPN found!
And you can use SETSPN -x to check if there are any duplicate SPNs, meaning the same SPN set on more than one account. That situation will also cause Kerberos to fail, so if it finds any duplicates, you should probably take care of those.
That all looks good, now what?
Lets say you look through all of this, and it all checks out:
- The application pool is running as the account you expect (CONTOSOSP_WEB_APP_SVC)
- Kernel Mode Authentication is disabled.
- The SPN is in the correct format (HTTP/teams.contoso.com)
- The SPN is set on the application pool account, and only that account.
Now that we’ve gone through the most common reasons for “KRB_AP_ERR_MODIFIED”, we’ll get to a lesser-known problem, which is what spawned this blog post.
All “KRB_AP_ERR_MODIFIED” means is that the encryption key used to encrypt the Kerberos ticket is not the same as the key that the server is trying to use to decrypt it. This can happen if the encryption algorithm is different between client and server, which can be controlled by a Windows security policy called “Network Security: Configure encryption types allowed for Kerberos“. If this setting is configured differently between the client machine and the web server, the result can be a mismatch in encryption types, a failure to decrypt the Kerberos ticket, and the “KRB_AP_ERR_MODIFIED” error, resulting in Access Denied.
You can check this by looking at the Local Security Policy on both client and server.
SecPol.msc > Security Settings > Local Policies > Security Options > Network Security: Configure encryption types allowed for Kerberos

Example:
Lets say that on the problem client machine, the policy is undefined, which would allow the user to get a Kerberos ticket encrypted with the “RC4_HMAC_MD5” algorithm.
However, on the web server side, the “Configure encryption types allowed for Kerberos” policy is defined, and is set to only allow these three:
– AES128_HMAC_SHA1
– AES256_HMAC_SHA1
– Future encryption types

Because the encryption type used by the client machine is not included in the “allowed” list on the server, the server is unable to decrypt the Kerberos ticket, and authentication fails with “KRB_AP_ERR_MODIFIED”.
Resolution:
Use Group Policy to define the same settings for “Network Security: Configure encryption types allowed for Kerberos” and make sure it’s applied consistently to both servers and client machines.
Other Tips:
If you’re wondering which encryption type was used to encrypt a Kerberos ticket, you can run the command “klist” on the client. It will display all of the Kerberos tickets currently assigned to the user. You’re looking for the one that matches the SPN you’re using for the site.
Command: klist
Example output:
Client: josh @ CONTOSO.COM
Server: HTTP/teams.contoso.com @ CONTOSO.COM
KerbTicket Encryption Type: AES-256-CTS-HMAC-SHA1-9
Ticket Flags 0x40a10000 -> forwardable renewable…
Start Time: 10/12/2020 11:36:54 (local)
End Time: 10/12/2020 21:36:54 (local)
Renew Time: 10/19/2020 11:36:54 (local)
Session Key Type: AES-256-CTS-HMAC-SHA1-96
Cache Flags: 0
Kdc Called: DC01
Hi,
We are getting this error from some servers in our environment when trying to connect to a SQL Server, but not from all (so, we do have some that are able to connect fine to it)
The Kerberos client received a KRB_AP_ERR_MODIFIED error from the server <SQLServiceAccount>. The target name used was MSSQLSvc/<SQLServerName-FQDN>:1433. This indicates that the target server failed to decrypt the ticket provided by the client.
This can occur when the target server principal name (SPN) is registered on an account other than the account the target service is using. Ensure that the target SPN is only registered on the account used by the server. This error can also happen if the target
service account password is different than what is configured on the Kerberos Key Distribution Center for that target service. Ensure that the service on the server and the KDC are both configured to use the same password. If the server name is not fully qualified,
and the target domain (<Domain>) is different from the client domain (<Domain>), check if there are identically named server accounts in these two domains, or use the fully-qualified name to identify the server.
Details:
| Server | <SQLServiceAccount> |
| Targetname | MSSQLSvc/<SQLServerName-FQDN>:1433 |
We are trying to test using an UDL File, and when Kerberos Logging is enabled, we are seeing this (Source: Security-Kerberos, Event 3):
A Kerberos error message was received:
on logon session
Client Time:
Server Time: 15:0:15.0000 1/8/2019 Z
Error Code: 0x29 KRB_AP_ERR_MODIFIED
Extended Error:
Client Realm:
Client Name:
Server Realm: <Domain>
Server Name: <SQLServiceAccount>
Target Name:
Error Text:
File: 3
Line: 587
Error Data is in record data.
SPNs look ok when checking with the Kerberos Configuration Troubleshooting tool (and the fact that other servers in the same environment are working (there are multiple working, and multiple failing)… All are in the same domain (single domain environment)..
and all of them are able to talk to other SQL Servers that coexist with the problematic one.
Any ideas/suggestions, on what I can look at next to troubleshoot this?
Содержание
- The kerberos client received a KRB_AP_ERR_MODIFIED error from the server
- Symptoms
- Cause
- Resolution
- More information
- Клиент kerberos получил KRB_AP_ERR_MODIFIED ошибку с сервера.
- Симптомы
- Причина
- Решение
- Дополнительные сведения
- Kerberos – KRB_AP_ERR_MODIFIED is not always an SPN problem
- Consider the following scenario:
- That all looks good, now what?
- Example:
- Resolution:
- Other Tips:
- Kerberos error krb ap err modified
- Answered by:
- Question
The kerberos client received a KRB_AP_ERR_MODIFIED error from the server
The article helps you to resolve the issue that the kerberos client received a KRB_AP_ERR_MODIFIED error from the server.
Applies to: В Windows Server 2003
Original KB number: В 558115
Symptoms
During access to NLB virtual IP/NLB Virtual Name, the user may prompt to a username and password, and the following error may add to the local system event log:
«The kerberos client received a KRB_AP_ERR_MODIFIED error from the server host/myserver.domain.com. This indicates that the password used to encrypt the kerberos service ticket is different than that on the target server. Commonly, this is due to identically named machine accounts in the target realm (domain.com), and the client realm. Please contact your system administrator.»
Cause
During access to the IIS 6 web site that support Windows Integrated Authentication, the following issues may occur:
- Mismatch DNS name resolution. The issue is common in an NLB environment that uses multiple IPs or network adapters.
- The user doesn’t have a Local NTFS access permission.
- The Web Site is using Application Pool with a poor permission setting.
Resolution
To resolve the error issue, consider to implement the following tests:
Verify that the IIS has been set up with correct NTFS settings.
Integrated Windows Authentication (IIS 6.0)
Verify that each cluster node has been set up with correct DNS settings.
Verify that the node has been set up with correct Application Pool settings:
Configuring Application Pool Identity with IIS 6.0 (IIS 6.0)
Verify that internet explorer has been set up with a correct security setting.
More information
Authentication and Access Control Diagnostics 1.0 (x86)
Internet Information Services Diagnostic Tools
Community Solutions Content Disclaimer
Microsoft corporation and/or its respective suppliers make no representations about the suitability, reliability, or accuracy of the information and related graphics contained herein. All such information and related graphics are provided «as is» without warranty of any kind. Microsoft and/or its respective suppliers hereby disclaim all warranties and conditions with regard to this information and related graphics, including all implied warranties and conditions of merchantability, fitness for a particular purpose, workmanlike effort, title and non-infringement. You specifically agree that in no event shall Microsoft and/or its suppliers be liable for any direct, indirect, punitive, incidental, special, consequential damages or any damages whatsoever including, without limitation, damages for loss of use, data or profits, arising out of or in any way connected with the use of or inability to use the information and related graphics contained herein, whether based on contract, tort, negligence, strict liability or otherwise, even if Microsoft or any of its suppliers has been advised of the possibility of damages.
Источник
Клиент kerberos получил KRB_AP_ERR_MODIFIED ошибку с сервера.
Эта статья поможет устранить проблему, из-за которую клиент Kerberos KRB_AP_ERR_MODIFIED ошибку с сервера.
Применяется к: Windows Server 2003
Исходный номер базы знаний: 558115
Симптомы
Во время доступа к виртуальному IP-адресу или виртуальному имени сетевой подсистемы балансировки сетевой нагрузки пользователь может ввести имя пользователя и пароль, а в журнал событий локальной системы может быть добавлена следующую ошибку:
Идентификатор события: 4
Источник: Kerberos
Тип: Ошибка
«Клиент kerberos получил KRB_AP_ERR_MODIFIED с узла сервера/myserver.domain.com. Это означает, что пароль, используемый для шифрования билета службы Kerberos, отличается от пароля на целевом сервере. Как правило, это связано с одинаковыми именованными учетными записями компьютеров в целевой области (domain.com) и клиентской области. Обратитесь к системному администратору».
Причина
Во время доступа к веб-сайту IIS 6, который поддерживает встроенную проверку подлинности Windows, могут возникнуть следующие проблемы:
- Несоответствие разрешения DNS-имен. Эта проблема распространена в среде балансировки сетевой подсистемы балансировки нагрузки, использующей несколько IP-адресов или сетевых адаптеров.
- У пользователя нет разрешения на локальный доступ NTFS.
- Веб-сайт использует пул приложений с неудовлетворительной настройкой разрешений.
Решение
Чтобы устранить ошибку, рассмотрите возможность реализации следующих тестов:
Убедитесь, что службы IIS настроены с правильными параметрами NTFS.
Встроенная проверка подлинности Windows (IIS 6.0)
Убедитесь, что для каждого узла кластера настроены правильные параметры DNS.
Убедитесь, что узел настроен с правильными параметрами пула приложений:
Настройка удостоверения пула приложений с помощью IIS 6.0 (IIS 6.0)
Убедитесь, что в Internet Explorer настроен правильный параметр безопасности.
Дополнительные сведения
Проверка подлинности и контроль доступа диагностики 1.0 (x86)
Средства диагностики служб Internet Information Services
Отказ от ответственности за содержимое общедоступных решений
Корпорация Майкрософт и/или ее поставщики не делают никаких заявлений относительно пригодности, надежности или точности сведений и соответствующих изображений, приведенных в настоящем документе. Все эти сведения и соответствующие изображения предоставлены «как есть» без каких-либо гарантий. Корпорация Майкрософт и/или ее поставщики настоящим отказываются от каких-либо гарантийных обязательств и условий в отношении этих сведений и соответствующих изображений, включая все подразумеваемые гарантии и условия товарной пригодности, применимости для конкретных целей, качества исполнения, прав собственности и отсутствия нарушений прав интеллектуальной собственности. В частности, вы подтверждаете свое согласие с тем, что корпорация Майкрософт и/или ее поставщики ни при каких обстоятельствах не несут ответственности за прямой или косвенный ущерб, штрафные санкции, случайные, фактические, косвенные или иные убытки, включая, в частности, убытки от утраты эксплуатационных качеств, от потери данных или прибылей в связи с использованием или невозможностью использовать эти сведения и соответствующие изображения, содержащиеся в настоящем документе, возникшие вследствие соглашения, гражданского правонарушения, халатности, объективной ответственности или иным образом, даже если корпорация Майкрософт или ее поставщики заранее были извещены о возможности такого ущерба.
Источник
Kerberos – KRB_AP_ERR_MODIFIED is not always an SPN problem
TLDR: This can also be caused by a mismatch in security policy “Network Security: Configure encryption types allowed for Kerberos“.
Consider the following scenario:
- You have a web site set up to use Kerberos authentication. It doesn’t matter what kind of site, but we’ll say it’s a SharePoint site, since that’s the theme around here.
- The site is at https://teams.contoso.com and its application pool is running as service account CONTOSOSP_WEB_APP_SVC.
- Kernel Mode authentication is not enabled in IIS Manager.
- Note: It’s possible that some users could have this “access denied” behavior, while others have no trouble accessing the site.
The Kerberos client received a KRB_AP_ERR_MODIFIED error from the server SP_WEB_APP_SVC. The target name used was HTTP/teams.contoso.com. This indicates that the target server failed to decrypt the ticket provided by the client. This can occur when the target server principal name (SPN) is registered on an account other than the account the target service is using. Ensure that the target SPN is only registered on the account used by the server. This error can also happen if the target service account password is different than what is configured on the Kerberos Key Distribution Center for that target service. Ensure that the service on the server and the KDC are both configured to use the same password. If the server name is not fully qualified, and the target domain (CONTOSO.COM) is different from the client domain (CONTOSO.COM), check if there are identically named server accounts in these two domains, or use the fully-qualified name to identify the server.
Most commonly, the “KRB_AP_ERR_MODIFIED” error means that you have a Service Principal Name (SPN) issue, specifically, the SPN has been added to the wrong account. You should check those things first.
In our scenario above, we know that the application pool is running as a domain account and Kernel Mode authentication is disabled, which is the typical configuration for a SharePoint web app. In that case, we need an HTTP SPN set for the site host name, and set on the account running the application pool.
We can use SETSPN -l (that’s a lower case L) to see which SPNs have been set on our service account:
Command: setspn -l CONTOSOSP_WEB_APP_SVC
Registered ServicePrincipalNames for CN=SP_WEB_APP_SVC,OU=Service Accounts,DC=contoso,DC=com:
You an also do it the opposite way, where you search for a given SPN to see which account it’s set on. For that you use SETSPN -q
Command: setspn -q HTTP/teams.contoso.com
And you can use SETSPN -x to check if there are any duplicate SPNs, meaning the same SPN set on more than one account. That situation will also cause Kerberos to fail, so if it finds any duplicates, you should probably take care of those.
That all looks good, now what?
Lets say you look through all of this, and it all checks out:
- The application pool is running as the account you expect (CONTOSOSP_WEB_APP_SVC)
- Kernel Mode Authentication is disabled.
- The SPN is in the correct format (HTTP/teams.contoso.com)
- The SPN is set on the application pool account, and only that account.
Now that we’ve gone through the most common reasons for “KRB_AP_ERR_MODIFIED”, we’ll get to a lesser-known problem, which is what spawned this blog post.
All “KRB_AP_ERR_MODIFIED” means is that the encryption key used to encrypt the Kerberos ticket is not the same as the key that the server is trying to use to decrypt it. This can happen if the encryption algorithm is different between client and server, which can be controlled by a Windows security policy called “Network Security: Configure encryption types allowed for Kerberos“. If this setting is configured differently between the client machine and the web server, the result can be a mismatch in encryption types, a failure to decrypt the Kerberos ticket, and the “KRB_AP_ERR_MODIFIED” error, resulting in Access Denied.
You can check this by looking at the Local Security Policy on both client and server.
SecPol.msc > Security Settings > Local Policies > Security Options > Network Security: Configure encryption types allowed for Kerberos
Example:
Lets say that on the problem client machine, the policy is undefined, which would allow the user to get a Kerberos ticket encrypted with the “RC4_HMAC_MD5” algorithm.
However, on the web server side, the “Configure encryption types allowed for Kerberos” policy is defined, and is set to only allow these three:
– Future encryption types
Because the encryption type used by the client machine is not included in the “allowed” list on the server, the server is unable to decrypt the Kerberos ticket, and authentication fails with “KRB_AP_ERR_MODIFIED”.
Resolution:
Use Group Policy to define the same settings for “Network Security: Configure encryption types allowed for Kerberos” and make sure it’s applied consistently to both servers and client machines.
Other Tips:
If you’re wondering which encryption type was used to encrypt a Kerberos ticket, you can run the command “klist” on the client. It will display all of the Kerberos tickets currently assigned to the user. You’re looking for the one that matches the SPN you’re using for the site.
Command: klist
KerbTicket Encryption Type: AES-256-CTS-HMAC-SHA1-9
Ticket Flags 0x40a10000 -> forwardable renewable…
Источник
Kerberos error krb ap err modified
This forum has migrated to Microsoft Q&A. Visit Microsoft Q&A to post new questions.
Answered by:
Question
since one night i receive the following error message on all member Server in a branch office for a special subent.
Other Member server i a different subnet are not getting these errors. Before those member servers (new setup)
worked fine for about 2-3 Month:
Log Name: System
Source: Microsoft-Windows-Security-Kerberos
Date: 09.10.2013 02:47:27
Event ID: 4
Task Category: None
Level: Error
Keywords: Classic
User: N/A
Computer: server
Description:
The Kerberos client received a KRB_AP_ERR_MODIFIED error from the server dc01$.
The target name used was cifs/dc01.local. This indicates that the target server
failed to decrypt the ticket provided by the client. This can occur when the target server principal name (SPN)
is registered on an account other than the account the target service is using. Please ensure that the target SPN
is registered on, and only registered on, the account used by the server. This error can also happen when the target
ervice is using a different password for the target service account than what the Kerberos Key Distribution Center (KDC)
has for the target service account. Please ensure that the service on the server and the KDC are both updated to use the current password.
If the server name is not fully qualified, and the target domain (domain.local) is different from the client domain (domain.local),
check if there are identically named server accounts in these two domains, or use the fully-qualified name to identify the server.
These servers have no routing to the local Domain Controllers, instead they contact the DCs at the main office. So the
KRB_AP_ERR_MODIFIED error is coming from both DCs at the main office, not specific to one pc.
Effects that i have:
— no logon with RDP possible (wrong username or password)
— Service which Relay on Kerberos Auth have Problems
So when i reboot the server in most cases its working again for some time. I also find out, when deleting the cached
Kerberos Tickets with kerbtray its working.
Any ideas what could cause the problem. As mentioned, it happend for all member servers in this subnet starting in the
same night. As always, nothing was changed 😉
Источник
This post has been republished via RSS; it originally appeared at: IIS Support Blog articles.
KRB_AP_ERR_MODIFIED is a common Kerberos failure message. This means some encrypted Kerberos authentication data sent by the client did not decrypt properly at the server.
When a Kerberos client requests a ticket for a specific service, the service is actually identified by its SPN. The KDC grants the client a service ticket that is encrypted using service’s secret key. Basically, the AD account password that that matches the SPN requested.
Under some scenarios, KDC may generate a service ticket that encrypted with password of a wrong account (or not expected one). Then, when client provide that ticket to the service for authentication, the service can’t decrypt it and authentication failed with KRB_AP_ERR_MODIFED.
In short, this happens because KDC issued a ticket encrypted using password of account A, but on the service side, it tries to decrypt this using the password of account B.
Common cause for this are duplicated SPN, wrong DNS settings, two computers in different domains have the same name, client requests wrong SPN. And from IIS 7, it may due to the wrong setting of IIS (kernel/user mode authentication).
Collect data and identify the cause of Kerberos failure
Tools Used to collect data
- 1. Registry Editor(build in tool)
- 2. KList(build in for Windows 2008+)
http://technet.microsoft.com/en-us/library/hh134826(WS.10).aspx
- 3. Ipconfig (build in tool).
http://technet.microsoft.com/en-us/library/dd197434(WS.10).aspx
- 4. Network Monitor
http://www.microsoft.com/download/en/details.aspx?displaylang=en&id=4865
Steps to collect data
- 1. Enable Kerberos log on both client machine.
262177 How to enable Kerberos event logging
http://support.microsoft.com/default.aspx?scid=kb;EN-US;262177
- 2. Open a command console with elevated privilege, and run “klist purge” to clear cached Kerberos tickets.
- 3. Run “ipconfig /flushdns” to clear DNS cache.
- 4. Run Network monitor on both client and web server.
- 5. Reproduce the problem.
- 1. Network Monitor Trace
Identify the Kerberos error
By expanding the authenticate field in the HTTP response header returned by IIS, we could locate the reason for Kerberos authentication error.
— Http: Response, HTTP/1.1, Status: Unauthorized, URL: / , Using GSS-API Authentication
ProtocolVersion: HTTP/1.1
StatusCode: 401, Unauthorized
Reason: Unauthorized
…
— WWWAuthenticate: Negotiate …
— Authenticate: Negotiate oWwwaqADCgEBomMEYWBfBgkqhkiG9xIBAgIDAH5QME6abcdIBBaEDAgEepBEYDzIwMTExMabcd0MDUxMDE0WqUabcd2mAwIBKakKGwhURVNULkNPTaoXMBWgAwIBAaEOMAwbCmNvbnRvc29zdmM=
WhiteSpace:
— NegotiateAuthorization:
Scheme: Negotiate
— GssAPI: 0x1
— NegotiationToken:
— ChoiceTag:
— NegTokenResp:
— ResponseToken: 0x1
— KerberosToken: 0x1
— KerberosInitToken:
…
— InnerContextToken: 0x1
— KerberosToken: 0x1
TokId: Krb5Error (0x300)
— Error: KRB_ERROR (30)
….
+ ErrorCode: KRB_AP_ERR_MODIFIED (41)
+ Realm: TEST.COM
+ Sname: contososvc
Date: Fri, 14 Oct 2011 05:10:14 GMT
ContentLength: 341
It would be more straightforward using Wireshark.
- 2. From the system event log of client side, follow event will be logged.
Log Name: System
Source: Microsoft-Windows-Security-Kerberos
Date: 10/13/2011 10:10:05 PM
Event ID: 4
Task Category: None
Level: Error
Keywords: Classic
User: N/A
Computer: IIS02.test.com
Description:
The Kerberos client received a KRB_AP_ERR_MODIFIED error from the server contososvc. The target name used was HTTP/iis01.test.com. This indicates that the target server failed to decrypt the ticket provided by the client. This can occur when the target server principal name (SPN) is registered on an account other than the account the target service is using. Please ensure that the target SPN is registered on, and only registered on, the account used by the server. This error can also happen when the target service is using a different password for the target service account than what the Kerberos Key Distribution Center (KDC) has for the target service account. Please ensure that the service on the server and the KDC are both updated to use the current password. If the server name is not fully qualified, and the target domain (TEST.COM) is different from the client domain (TEST.COM), check if there are identically named server accounts in these two domains, or use the fully-qualified name to identify the server.
In this event, the SPN used is HTTP/iis01.test.com, and the account used to decrypt the ticket is contososvc. This happens because the account account used to encrypt the ticket is not contososvc.
Scenario 1: Duplicated SPN
In the case of a duplicated SPN, the same SPN was registered on at least two accounts. For example, a SPN was registered on two accounts: A and B. What happens is that KDC will generate a service ticket that may be encrypted with password of account A. Then, when the client sends that ticket to the service during authentication, the service may try to decrypt this using account B.
Detect duplicated SPN using setspn
On Windows 2008 and later, detect duplicated SPN is easier. Since Windows Server 2008, the setspn itself includes a feature to search SPNs.
Besides HTTP/ SPN, please remember to check HOST/ SPN as well. HOST/ SPN will be used as a failover/alternative if HTTP/ SPN does not exist. In case of this scenario, wrong HOST/ SPN will result in Kerberos failure as well.
Here is a sample output of setspn on Windows Server 2008 SP2. For more details about this tool, please reference this document.
SetSPN
http://technet.microsoft.com/en-us/library/cc731241(WS.10).aspx
Find duplicated SPN using ldifde
For Windows 2003 and XP, we can use another tool named ldifde to search duplicated SPN. Here is a sample query for HTTP/contoso. Please remember, don’t forget HOST/ SPN as well.
Here is an example output of ldifde, for more details about this tool, please reference follow document.
http://technet.microsoft.com/en-us/library/cc731033(WS.10).aspx
The SPN is forest-wide object, it has to be unique inside the whole domain. For a complex environment, using follow command to search the entire forest, like this:
Ldifde -s GCName -t 3268 -f d:spn.ldf -d “dc=test, dc=com” –l ServicePrincipleName –r “(ServicePrincipalName=HTTP/contoso)”
In addition, we can use a wild card search like this:
Ldifde -s GCName -t 3268 –f d:spn.ldf -d “dc=test, dc=com” -l servicePrincipalName -r (servicePrincipalName=*contoso*)
Scenario 2: Internet Explorer (or other client) requested ticket for wrong SPN
This is a specific scenario which most related to the behavior of client. This problem occurs if the Web site uses a CNAME resource record in the Domain Name System (DNS). For example, the DNS setting looks like this:
Contoso CNAME iis01.test.com
iis01.test.com A 10.0.5.2
When you use Internet Explorer to access the Web site, Internet Explorer uses the host name of the server ((IIS01)) instead of the CNAME resource record(Contoso) to contact the server. The authentication may fail with KRB_AP_ERR_MODIFIED.
HTTP/Contoso.test.com Registered on testcontososvc
HOST/IIS01.test.com Registered on testiis01(machine account)
Identify this scenario from Network Monitor trace.
- 1. IE sends request to http://contoso, and a DNS query for contoso was sent.
+ Ipv4: src=10.0.5.3, Dest = 10.0.5.1, Next Protocol = UDP, Packet ID = 9717, Total IP Length = 62
+ Udp: SrcPort = 64506, DstPort = DNS(53), Length = 42
— Dns: QueryId = 0x4BB1, QUERY (Standard query), Query for contoso.test.com of type Host Addr on class Internet
…..
- 2. DNS response for contoso
+ Ipv4: src=10.0.5.1, Dest = 10.0.5.3, Next Protocol = UDP, Packet ID = 6526, Total IP Length = 98
+ Udp: SrcPort = DNS(53), DstPort = 64506, Length = 78
— Dns: QueryId = 0x4BB1, QUERY (Standard query), Response — Success, 49, 0
QueryIdentifier: 19377 (0x4BB1)
…..
— ARecord: contoso.test.com of type CNAME on class Internet: iis01.test.com
— ARecord: iis01.test.com of type Host Addr on class Internet: 10.0.5.2
….
- 3. TGS ticket request, IE requests SPN for : HTTP/iis01.test.com instead of expected HTTP/contoso.test.com
+ Ipv4: src=10.0.5.3, Dest = 10.0.5.1, Next Protocol = TCP, Packet ID = 9728, Total IP Length = 0
+ Tcp: Flags=…AP…, SrcPort=50044, DstPort=Kerberos(88), PayloadLen=1488, Seq=4106960882 — 4106962370, Ack=354586390, Win=513 (scale factor 0x8) = 131328
— Kerberos: TGS Request Realm: TEST.COM Sname: HTTP/iis01.test.com
…
Solutions for CName
- 1. If the client is IE, KB 911149 described the solution for this problem.
Error message in Internet Explorer when you try to access a Web site that requires Kerberos authentication on a Windows XP-based computer: «HTTP Error 401 — Unauthorized: Access is denied due to invalid credentials»
http://support.microsoft.com/default.aspx?scid=kb;EN-US;911149
- 2. If the client is an application uses System.Net.HttpWebRequest, using CustomTargetNameDictionary.
AuthenticationManager.CustomTargetNameDictionary
http://msdn.microsoft.com/en-us/library/system.net.authenticationmanager.customtargetnamedictionary.aspx
- 3. On DNS server side, configure the IIS server to a host record (A) instead of Alias(CNAME).
Scenario 3: SPN set to unexpected account (Wrong IIS 7+ authentication settings)
Internet Information Services (IIS) 7.0 enables kernel mode authentication by default. Kernel mode authentication runs under the machine account no matter what account is used to run the application pool. The machine account is used to decrypt the Kerberos ticket.
However, there are some scenarios you need to use a domain service account for authentication process instead of machine account. For example, a web arm scenario.
For this scenario, Instead of disabling kernel mode authentication in IIS, you can configure IIS to use the Web application pool’s identity for authentication (by setting useAppPoolCredentials=»true»).
For IIS 7+, we have 3 Windows authentication configuration. Different scenario requires register SPN on different accounts. In the scenario of improper SPN and IIS 7 configuration, it may result in authentication failure with KRB_AP_ERR_MODIFIED if the SPN was set to unexpected account.
- · Kernel mode authentication disabled
- · Kernel mode authentication enabled, useAppPoolCredentials
- · Kernel mode authentication enabled
NOTE: Machine account includes all accounts can represent the machine on network including Network Service, Local System, Local Service and ApplicationPoolIdentity for IIS 7+. Service accounts means a domain account used as the application pool identity.
Here, I listed couple of scenarios which can result in Kerberos authentication failed with KRB_AP_ERR_MODIFIED.
Scenarios result in KRB_AP_ERR_MODIFIED
Wrong Configuration Scenario 1
|
Kernel Mode Authentication |
Enabled(default) |
|
useAppPoolCredentials |
False(default) |
|
Application Pool Identity |
Service Account like (domaincontosoService) |
|
Web Site Binding To |
IIS server’s NetBIOS Name. Access like this way: http(s)://IIS_Server_NetBIOS_Name http(s)://IIS_Server_FQDN |
|
SPN |
HTTP/ SPN registered on service account |
|
Comments |
For this scenario, the Kerberos ticket is encrypted by service account, and is decrypted by IIS server’s computer account. |
Wrong Configuration Scenario 2
|
Kernel Mode Authentication |
Enabled(default) |
|
useAppPoolCredentials |
False(default) |
|
Application Pool Identity |
Service Account like (domaincontosoService) |
|
Web Site Binding To |
A customized host header. Access like this way: http(s)://Contoso |
|
SPN |
HTTP/ SPN registered on service account |
|
Comments |
For this scenario, the Kerberos ticket is encrypted by service account, and decrypted by IIS server’s computer account. |
Wrong Configuration Scenario 3
|
Kernel Mode Authentication |
Enabled(default) |
|
useAppPoolCredentials |
True |
|
Application Pool Identity |
Service Account like (domaincontosoService) |
|
Web Site Binding To |
IIS server’s NetBIOS Name. Access like this way: http(s)://IIS_Server_NetBIOS_Name http(s)://IIS_Server_FQDN |
|
SPN |
HTTP/ IIS_Server_NetBIOS_Name doesn’t registered on any account Or, registered on IIS server’s computer account |
|
Comments |
For this scenario, the Kerberos ticket is encrypted by IIS server’s computer account, and decrypted by service account. |
SPN and IIS configuration reference
Scenario 1
|
Kernel Mode Authentication |
Enabled(default) |
|
useAppPoolCredentials |
False(default) |
|
Application Pool Identity |
No Matter |
|
URL used to access web site |
http(s)://IIS_Server_NetBIOS_Name http(s)://IIS_Server_FQDN |
|
SPN requirement |
No HTTP/ SPN required. By default, the HOST/ IIS_Server_NetBIOS_Name will be used. If you want, you can register HTTP/ IIS_Server_NetBIOS_Name on the server name. |
|
Comments |
This is the default scenario for IIS 7+ when using IIS server’s computer name to access the web application. |
Scenario 2
|
Kernel Mode Authentication |
Enabled(default) |
|
useAppPoolCredentials |
False(default) |
|
Application Pool Identity |
No Matter |
|
URL used to access web site |
http(s)://Customer_Host_Name |
|
SPN requirement |
Need register SPN on IIS server’s computer account, like: SetSPN -a HTTP/Customer_Host_NAME IIS_SRV_NetBIOS |
|
Comments |
Some application requires this when they need special permission for application pool identity. |
Scenario 3
|
Kernel Mode Authentication |
Enabled(default) |
|
useAppPoolCredentials |
True |
|
Application Pool Identity |
Service Account like (domaincontosoService) |
|
URL used to access web site |
http(s)://Customer_Host_Name |
|
SPN requirement |
Need register SPN on service account, like: SetSPN -a HTTP/Customer_Host_NAME domaincontosoService |
|
Comments |
|
Scenario 4
|
Kernel Mode Authentication |
Enabled(default) |
|
useAppPoolCredentials |
True |
|
Application Pool Identity |
Service Account like (domaincontosoService) |
|
URL used to access web site |
http(s)://IIS_Server_NetBIOS_Name http(s)://IIS_Server_FQDN |
|
SPN requirement |
Need register SPN on service account, like: SetSPN -a HTTP/IIS_SERVER_FQDN domaincontosoService |
|
Comments |
You need select this scenario if you want web site binding to IIS server’s computer name and running the site with a domain account. |
Scenario 5
|
Kernel Mode Authentication |
Disabled |
|
useAppPoolCredentials |
No Matter |
|
Application Pool Identity |
Service Account like (domaincontosoService) |
|
URL used to access web site |
http(s)://Customer_Host_Name |
|
SPN requirement |
Need register SPN on service account, like: SetSPN -a HTTP/Customer_Host_NAME domaincontosoService |
|
Comments |
This is same for IIS 6 scenario. |
Scenario 6
|
Kernel Mode Authentication |
Disabled |
|
useAppPoolCredentials |
No Matter |
|
Application Pool Identity |
Service Account like (domaincontosoService) |
|
URL used to access web site |
http(s)://IIS_SERVER_NetBIOS_NAME |
|
SPN requirement |
Need register SPN on service account, like: SetSPN -a HTTP/ IIS_SERVER_NetBIOS_NAME domaincontosoService |
|
Comments |
This is same for IIS 6 scenario. |
Scenario 7
|
Kernel Mode Authentication |
Disabled |
|
useAppPoolCredentials |
No Matter |
|
Application Pool Identity |
Machine Account |
|
URL used to access web site |
http(s)://Customer_Host_Name |
|
SPN requirement |
Need register SPN on IIS server’s computer account, like: SetSPN -a HTTP/Customer_Host_NAME IIS_SRV_NetBIOS |
|
Comments |
This is same for IIS 6 scenario. |
Scenario 8
|
Kernel Mode Authentication |
Disabled |
|
useAppPoolCredentials |
No Matter |
|
Application Pool Identity |
Machine Account |
|
URL used to access web site |
http(s)://IIS_SERVER_NetBIOS_NAME |
|
SPN requirement |
No HTTP/ SPN required. By default, the HOST/ IIS_Server_NetBIOS_Name will be used. If you want, you can register HTTP/ IIS_Server_NetBIOS_Name on the server name. |
|
Comments |
This is similar to the default scenario of IIS 6. |
Author : Wei
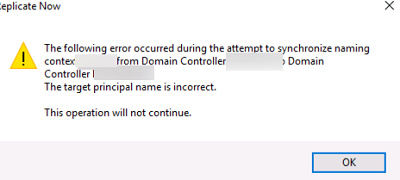
При попытке ручной репликации данных между контроллерами домена Active Directory в остатке Active Directory Sites and Services (dssite.msc) появилась ошибка:
The following error occurred during the attempt to synchronize naming context from Domain Controller X to Domain Controller Y. The target principal name is incorrect. This operation will not continue.
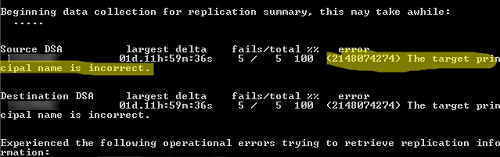
При проверке репликации с помощью repadmin, у одного из DC появляется ошибка:
(2148074274) The target principal name is incorrect.
В журнале событий DC есть такие ошибки:
Source: Security-Kerberos
Event ID: 4
The Kerberos client received a KRB_AP_ERR_MODIFIED error from the server DC2. The target name used was cifs/DC2.winitpro.ru. This indicates that the target server failed to decrypt the ticket provided by the client. This can occur when the target server principal name (SPN) is registered on an account other than the account the target service is using. Ensure that the target SPN is only registered on the account used by the server. This error can also happen if the target service account password is different than what is configured on the Kerberos Key Distribution Center for that target service. Ensure that the service on the server and the KDC are both configured to use the same password. If the server name is not fully qualified, and the target domain (winitpro.ru) is different from the client domain (winiptro.ru), check if there are identically named server accounts in these two domains, or use the fully-qualified name to identify the server.
Event ID 3210:
Failed to authenticate with \DC, a Windows NT domain controller for domain WINITPRO.
Event ID 5722:
The session setup from the computer 1 failed to authenticate. The name of the account referenced in the security database is 2. The following error occurred:
В первую очередь проверьте:
- Доступность проблемного контроллера домена с помощью простого ICMP ping
- Проверьте, что на нем доступен порт TCP 445 и опубликованы сетевые папки SysVol и NetLogon;
Если все ОК, значит проблема в том, между контроллерами домена нарушен безопасный канал передачи данных. Проверьте его с помощью PowerShell команды:
Test-ComputerSecureChannel -Verbose
Служба KDC на целевом контроллере домена не может расшифровать тикет Kerberos из-за того, что в ней хранится старый пароль этого контроллера домена.
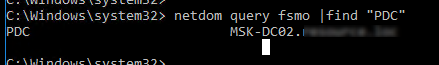
Чтобы исправить проблему, нужно сбросить этот пароль. Сначала нужно найти текущий контроллер домена с FSMO ролью PDC.
netdom query fsmo |find "PDC"
В нашем примере PDC находится на MSK-DC02. Мы будем исопользовать это имя в команде
netdom resetpwd
далее.
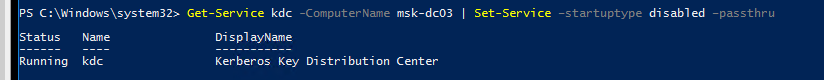
Остановите службу Kerberos Key Distribution Center (KDC) на контроллере домена, на котором появляется ошибка “The target principal name is incorrect” и измените тип запуска на Disabled. Можно изменить настройки службы из консоли services.msc или с помощью PowerShell:
Get-Service kdc -ComputerName msk-dc03 | Set-Service –startuptype disabled –passthru
Перезагрузите этот контроллер домена.
Теперь нужно сбросить безопасный канал связи с контроллером домена с ролью PDC:
netdom resetpwd /server:msk-dc02 /userd:winitproadministrator /passwordd:*
Укажите пароль администратора домена.
Перезагрузите проблемный DC и запустите службу KDC. Попробуйте запустить репликацию и проверить ошибки.
repadmin /syncall
repadmin /replsum
repadmin /showrepl
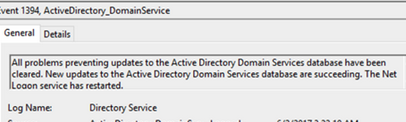
Если репликация успешно выполнена, в журнале Directory Service Event Viewerа должно появится событие Event ID 1394:
All Problems preventing updates to the Active Directory Domain Services database have been cleared. New Updates to the Active Directory Domain Services database are succeeding. The Net Logon service has restarted
Проверьте состояние вашего домена и контроллеров домена Active Directory согласно этого гайда.
Success! It appears the error in my last message was (obviously) the place to look for a solution. A quick Google search brought me to this page Opens a new window in which a similar problem is described. The accepted answers for this problem list a few sites that may hold the answer. In the end, it was this one Opens a new window that brought me to a solution.
In the event that the linked pages disappear, I will provide a quick rundown of what happened and what steps I took to resolve the issue. All of the unnecessary and ultimately worthless «fixes» I attempted will not be mentioned in this review.
As stated, the issue began when a user arrived in IT complaining about a missing home folder drive. In trying to investigate the issue while a help desk tech visited the affected machine, I discovered that I could not access \domain.com which is the beginning of the home folder location (\domain.comfolderfolderhome). After several failed attempts to fix the issue, I discovered the error mentioned in my previous post. As mentioned, the second linked page in this reply brought me to a website where a similar problem was being discussed. The owner of that blog mentioned using a third-party tool called ADFind to query his AD environment for the SPN in the error. When that search yielded no results, he tried the «catch-all» SPN by adjusting the command to read (in my case):
Text
adfind -f "servicePrincipalName=HOST/domain.com" -gcb
For me, this returned a value for a recently-added Federation Services service account. I had been attempting to build an ADFS server to prepare my environment for our soon-to-be move to O365. Since the first attempt at configuring the ADFS server failed, the ADFS service account could be deleted without issue. Deleting this AD account made the \domain.com location immediately available.
Thank you to both of the respondents to this thread.
1 found this helpful
thumb_up
thumb_down