Содержание
- Mikrotik openvpn tls error cannot locate hmac in incoming packet from
- Re: OpenVPN Access Server and Mikrotik ovpn client
- Re: OpenVPN Access Server and Mikrotik ovpn client
- Re: OpenVPN Access Server and Mikrotik ovpn client
- Re: OpenVPN Access Server and Mikrotik ovpn client
- Re: OpenVPN Access Server and Mikrotik ovpn client
- Re: OpenVPN Access Server and Mikrotik ovpn client
- Re: OpenVPN Access Server and Mikrotik ovpn client
- Re: OpenVPN Access Server and Mikrotik ovpn client
- Re: OpenVPN Access Server and Mikrotik ovpn client
- Mikrotik openvpn tls error cannot locate hmac in incoming packet from
- OpenVPN Support Forum
- TLS Error: cannot locate HMAC in incoming packet
- TLS Error: cannot locate HMAC in incoming packet
- Re: TLS Error: cannot locate HMAC in incoming packet
- Re: TLS Error: cannot locate HMAC in incoming packet
- Re: TLS Error: cannot locate HMAC in incoming packet
- OpenVPN Support Forum
- Disk Full: TLS Error: cannot locate HMAC in incoming packet from.
- Disk Full: TLS Error: cannot locate HMAC in incoming packet from.
- Re: Disk Full: TLS Error: cannot locate HMAC in incoming packet from.
- Re: Disk Full: TLS Error: cannot locate HMAC in incoming packet from.
- Re: Disk Full: TLS Error: cannot locate HMAC in incoming packet from.
- Re: Disk Full: TLS Error: cannot locate HMAC in incoming packet from.
- Re: Disk Full: TLS Error: cannot locate HMAC in incoming packet from.
- Re: Disk Full: TLS Error: cannot locate HMAC in incoming packet from.
- Re: Disk Full: TLS Error: cannot locate HMAC in incoming packet from.
- Re: Disk Full: TLS Error: cannot locate HMAC in incoming packet from.
- Re: Disk Full: TLS Error: cannot locate HMAC in incoming packet from.
- Mikrotik openvpn tls error cannot locate hmac in incoming packet from
- Re: OpenVPN tls-auth problem in RouterOS 4.6
- Re: OpenVPN tls-auth problem in RouterOS 4.6
- Re: OpenVPN tls-auth problem in RouterOS 4.6
- Re: OpenVPN tls-auth problem in RouterOS 4.6
- Re: OpenVPN tls-auth problem in RouterOS 4.6
- Re: OpenVPN tls-auth problem in RouterOS 4.6
- Re: OpenVPN tls-auth problem in RouterOS 4.6
Mikrotik openvpn tls error cannot locate hmac in incoming packet from
Wed Jun 05, 2013 8:07 pm
I’m having a hell of a time trying to get this to work.
I have an Openvpn AS server up and running. I am able to connect to it with the openvpn client without issue on a windows pc.
I have exported the user certificates using this guide http://docs.openvpn.net/administration- . or-a-user/
and uploaded/import to our Mikrotik.
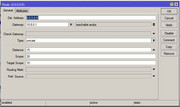
I have configured the ovpn-client interface as
Flags: X — disabled, R — running
0 name=»ovpn-out1″ mac-address=02:20:24:D4:0C:8C max-mtu=1500
connect-to=xx.xx.xx.xx.xx port=443 mode=ip user=»test» password=»test»
profile=default certificate=cert2 auth=sha1 cipher=blowfish128
add-default-route=no
In the logs i just see it dialing, terminating then disconnecting. over and over.
Any help to get this working would be greatly appreciated.
Re: OpenVPN Access Server and Mikrotik ovpn client
Wed Jun 05, 2013 11:36 pm
Re: OpenVPN Access Server and Mikrotik ovpn client
Thu Jun 06, 2013 5:39 am
Sorry guys, i have no where else to turn.
Re: OpenVPN Access Server and Mikrotik ovpn client
Thu Jun 06, 2013 6:13 am
Re: OpenVPN Access Server and Mikrotik ovpn client
Thu Jun 06, 2013 7:04 pm
Re: OpenVPN Access Server and Mikrotik ovpn client
Thu Jun 06, 2013 7:17 pm
Re: OpenVPN Access Server and Mikrotik ovpn client
Fri Jun 07, 2013 7:52 am
Re: OpenVPN Access Server and Mikrotik ovpn client
Fri Jun 07, 2013 3:30 pm
Re: OpenVPN Access Server and Mikrotik ovpn client
Sat Sep 07, 2013 3:46 pm
Re: OpenVPN Access Server and Mikrotik ovpn client
Mon Oct 21, 2013 10:52 pm
I suspect this is due to the mikrotik not supporting TLS AUTH. I get these errors on my openvpn server side:
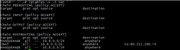
2013-10-16 18:50:02+0000 [-] OVPN 0 OUT: ‘Wed Oct 16 18:50:02 2013 196.209.220.252:46314 TLS: Initial packet from XXX.XXX.XXX.XXX:46314, sid=d7f8699d bdbac78b’
2013-10-16 18:50:02+0000 [-] OVPN 0 OUT: ‘Wed Oct 16 18:50:02 2013 196.209.220.252:46314 TLS Error: cannot locate HMAC in incoming packet from 196.209.220.252:46314’
2013-10-16 18:50:02+0000 [-] OVPN 0 OUT: ‘Wed Oct 16 18:50:02 2013 196.209.220.252:46314 Fatal TLS error (check_tls_errors_co), restarting’
2013-10-16 18:50:02+0000 [-] OVPN 0 OUT: ‘Wed Oct 16 18:50:02 2013 196.209.220.252:46314 SIGUSR1[soft,tls-error] received, client-instance restarting’
2013-10-16 18:50:12+0000 [-] OVPN 0 OUT: ‘Wed Oct 16 18:50:12 2013 TCP connection established with XXX.XXX.XXX.XXX:46315’
Upon investigation I found that Access Server uses TLS AUTH and Mikrotik does not support it.
+1 for Full OpenVPN Support: UDP, COMP-LZO and TLS AUTH
Источник
Mikrotik openvpn tls error cannot locate hmac in incoming packet from
09:22:44.403 — —— OpenVPN Start ——
09:22:44.404 — EVENT: CORE_THREAD_ACTIVE
09:22:44.418 — Frame=512/2048/512 mssfix-ctrl=1250
09:22:44.435 — UNUSED OPTIONS
5 [resolv-retry] [infinite]
6 [nobind]
7 [persist-key]
8 [persist-tun]
10 [verb] [3]
09:22:44.436 — EVENT: RESOLVE
09:22:44.443 — Contacting ххх.ххх.ххх.ххх:1194 via TCP
09:22:44.444 — EVENT: WAIT
09:22:44.560 — Connecting to [ххх.ххх.ххх.ххх]:1194 (ххх.ххх.ххх.ххх) via TCPv4
09:22:44.719 — EVENT: CONNECTING
09:22:44.832 — Tunnel Options:V4,dev-type tun,link-mtu 1559,tun-mtu 1500,proto TCPv4_CLIENT,cipher AES-128-CBC,auth SHA1,keysize 128,key-method 2,tls-client
09:22:44.837 — Creds: Username/Password
09:22:44.842 — Peer Info:
IV_GUI_VER=OC30Android
IV_VER=3.2
IV_PLAT=android
IV_NCP=2
IV_TCPNL=1
IV_PROTO=2
IV_AUTO_SESS=1
09:22:46.600 — VERIFY OK : depth=0
cert. version : 3
serial number : 01
issuer name : C=RU, ST=STA, L=Stavropol, O=Company, OU=server, CN=server, ??=server, emailAddress=mail@mail.ru
subject name : C=RU, ST=STA, L=Stavropol, O=Company, OU=server, CN=server, ??=server, emailAddress=mail@mail.ru
issued on : 2018-07-10 11:48:50
expires on : 2028-07-07 11:48:50
signed using : RSA with SHA-256
RSA key size : 4096 bits
basic constraints : CA=false
cert. type : SSL Server
key usage : Digital Signature, Key Encipherment
ext key usage : TLS Web Server Authentication
09:22:47.910 — TCP recv EOF
09:22:47.917 — Transport Error: Transport error on ‘ххх.ххх.ххх.ххх: NETWORK_EOF_ERROR
09:22:47.926 — EVENT: TRANSPORT_ERROR info=’Transport error on ‘ххх.ххх.ххх.ххх: NETWORK_EOF_ERROR’
09:22:47.935 — Client terminated, restarting in 5000 ms..
Источник
OpenVPN Support Forum
Community Support Forum
TLS Error: cannot locate HMAC in incoming packet
TLS Error: cannot locate HMAC in incoming packet
Post by dnilgreb » Fri Dec 11, 2020 2:06 pm
Why am I getting this? Is the IP at the end where someone is trying to connect from? I have a few of these, and do not recognize these addresses. Since the only certificates I have issued are for myself and my family, I have a pretty good idea about where connections are comig from.
Is there any risk here? What can I do to prevent this, if anything?
Re: TLS Error: cannot locate HMAC in incoming packet
Post by Pippin » Fri Dec 11, 2020 2:21 pm
Re: TLS Error: cannot locate HMAC in incoming packet
Post by TinCanTech » Fri Dec 11, 2020 4:37 pm
This is where the packet came from.
Openvpn officially uses port 1194 and so there are scanners out there searching on port 1194 for vulnerable servers. You can use a different port (security through obscurity) to evade these scanners or use openvpn’s security measures (—tls-auth, —tls-crypt and —tls-crypt-v2) to ensure thast the scanners will fail. Or do both ..
Re: TLS Error: cannot locate HMAC in incoming packet
Post by dnilgreb » Fri Dec 11, 2020 8:33 pm
Great answers, thanks!
So they are indeed attempts to connect to or communicate with my server?
Is it anything to do something about, or can/should I just disregard it as noise?
Источник
OpenVPN Support Forum
Community Support Forum
Disk Full: TLS Error: cannot locate HMAC in incoming packet from.
Disk Full: TLS Error: cannot locate HMAC in incoming packet from.
Post by dsetis » Thu Jun 21, 2018 11:14 am
Sometimes I have received attempts to connect to my server (not real connections I think), and each one of them, generating entries in my LOGFILE:
«TLS Error: cannot locate HMAC in incoming packet from. »
Result: 20G logfiles per day, that my rotate can’t manage..
What is the best way to solve it?
— «verb 0» isn’t a good option, i think.
— «disable the TLS security?» wrong way .
Any ideas?
Re: Disk Full: TLS Error: cannot locate HMAC in incoming packet from.
Post by TinCanTech » Thu Jun 21, 2018 8:01 pm
Re: Disk Full: TLS Error: cannot locate HMAC in incoming packet from.
Post by dsetis » Wed Jun 27, 2018 10:02 pm
Re: Disk Full: TLS Error: cannot locate HMAC in incoming packet from.
Post by TinCanTech » Wed Jun 27, 2018 10:34 pm
Result: 20G logfiles per day,
— «verb 0» isn’t a good option,
Re: Disk Full: TLS Error: cannot locate HMAC in incoming packet from.
Post by dsetis » Mon Jul 02, 2018 7:00 pm
With «0», I think no LOGS will be generated and its not so good.
with 1, the LOG is usefull, the problem is about the TLS attack. With 1, its flooding openvpn.log file
Re: Disk Full: TLS Error: cannot locate HMAC in incoming packet from.
Post by TinCanTech » Mon Jul 02, 2018 8:33 pm
Re: Disk Full: TLS Error: cannot locate HMAC in incoming packet from.
Post by dsetis » Tue Jul 03, 2018 2:32 pm
I was really confused.
I’m so sorry
I reversed mute option. 2 = less equals logs.
Thanks. Its working!
Re: Disk Full: TLS Error: cannot locate HMAC in incoming packet from.
Post by TinCanTech » Tue Jul 03, 2018 2:37 pm
Re: Disk Full: TLS Error: cannot locate HMAC in incoming packet from.
Post by dsetis » Tue Jul 03, 2018 3:13 pm
Now, again.. around 13k per second.
With verb 1 and mute 1
Tue Jul 3 12:08:23 2018 TLS Error: incoming packet authentication failed from 152.240.255.85:35215
Tue Jul 3 12:08:23 2018 Authenticate/Decrypt packet error: packet HMAC authentication failed
Tue Jul 3 12:08:23 2018 TLS Error: incoming packet authentication failed from 177.56.233.73:58123
Tue Jul 3 12:08:23 2018 Authenticate/Decrypt packet error: packet HMAC authentication failed
Tue Jul 3 12:08:23 2018 TLS Error: incoming packet authentication failed from 189.93.133.108:37127
Tue Jul 3 12:08:23 2018 Authenticate/Decrypt packet error: packet HMAC authentication failed
Tue Jul 3 12:08:23 2018 TLS Error: incoming packet authentication failed from 152.240.129.127:48610
Tue Jul 3 12:08:23 2018 Authenticate/Decrypt packet error: packet HMAC authentication failed
Tue Jul 3 12:08:23 2018 TLS Error: incoming packet authentication failed from 152.240.114.76:44890
Tue Jul 3 12:08:24 2018 Authenticate/Decrypt packet error: packet HMAC authentication failed
Tue Jul 3 12:08:24 2018 TLS Error: incoming packet authentication failed from 152.240.107.107:44177
Tue Jul 3 12:08:24 2018 Authenticate/Decrypt packet error: packet HMAC authentication failed
Tue Jul 3 12:08:24 2018 TLS Error: incoming packet authentication failed from 187.69.219.44:34305
Tue Jul 3 12:08:24 2018 Authenticate/Decrypt packet error: packet HMAC authentication failed
Tue Jul 3 12:08:24 2018 TLS Error: incoming packet authentication failed from 152.240.224.88:55099
Tue Jul 3 12:08:24 2018 Authenticate/Decrypt packet error: packet HMAC authentication failed
Tue Jul 3 12:08:24 2018 TLS Error: incoming packet authentication failed from 152.245.135.126:46313
Tue Jul 3 12:08:24 2018 Authenticate/Decrypt packet error: packet HMAC authentication failed
Tue Jul 3 12:08:24 2018 TLS Error: incoming packet authentication failed from 179.86.133.247:53054
Tue Jul 3 12:08:24 2018 Authenticate/Decrypt packet error: packet HMAC authentication failed
Tue Jul 3 12:08:24 2018 TLS Error: incoming packet authentication failed from 152.245.160.189:33492
Re: Disk Full: TLS Error: cannot locate HMAC in incoming packet from.
Post by TinCanTech » Tue Jul 03, 2018 3:24 pm
Источник
Mikrotik openvpn tls error cannot locate hmac in incoming packet from
Mon Mar 22, 2010 1:47 pm
After setup ovpn-server, i am trying to connect from Windows client (OpenVPN 2.1.1) and have problem.
auth-user-pass option in Windows not working without recompiling, so i am using «tls-auth ta.key 1» option on client side.
But for successfull connection i need to set parameter «tls-auth ta.key 0» on server side. Without that i have error while connecting: «TLS Error: cannot locate HMAC in incoming packet from «.
How can i set up this parameter on RouterOS?
Re: OpenVPN tls-auth problem in RouterOS 4.6
Tue Mar 23, 2010 11:35 am
Re: OpenVPN tls-auth problem in RouterOS 4.6
Tue Mar 23, 2010 2:19 pm
Re: OpenVPN tls-auth problem in RouterOS 4.6
Tue Mar 23, 2010 7:39 pm
I’ve followed the WIKI and I’m having similar problems when I try to get my ROS OVPN Client (v3.30) to speak to my ROS OVPN Server (v3.30).
I get the following error: terminating . TLS Handshake Failed
I don’t understand where I’m going wrong. PLEASE HELP .
Kindly see my configuration below:
SERVER SIDE CONFIGURATION
/ip pool add name=ovpn-pool ranges=10.15.32.34-10.15.32.38
/ppp profile add change-tcp-mss=default comment=»» local-address=10.15.32.33
name=»PROFILE» only-one=default remote-address=ovpn-pool
use-compression=default use-encryption=required use-vj-compression=default
/ppp secret add caller-id=»» comment=»» disabled=no limit-bytes-in=0
limit-bytes-out=0 name=»username» password=»password»
routes=»» service=ovpn
/interface ovpn-server server set auth=sha1,md5
cipher=blowfish128,aes128,aes192,aes256 default-profile=PROFILE
enabled=yes keepalive-timeout=disabled max-mtu=1500 mode=ip netmask=29
port=443 require-client-certificate=no
FIREWALL RULE TO ALLOW ACCESS:
ip firewall filter add action=accept chain=input comment=»OpenVPN» disabled=no dst-port=443 protocol=tcp
/interface ovpn-client
add name=»ovpn-out1″ connect-to=W.X.Y.Z port=443 mode=ip user=»username» password=»password» profile=default
certificate=none cipher=aes256 add-default-route=no
NB: I’ve posted this previously, however, response was slow in Beta
Re: OpenVPN tls-auth problem in RouterOS 4.6
Wed Mar 24, 2010 8:12 am
Re: OpenVPN tls-auth problem in RouterOS 4.6
Thu Mar 25, 2010 4:52 am
Ok, I’ve entered created and uploaded and imported the server side certificate and client side certificate.
The server is now telling me that a connection is established, however, the OVPN client and server status is disconnected.
I must be missing something really silly here. Please help.
Kindly see below:
SERVER
name=»username» service=ovpn caller-id=»» password=»password» profile=default routes=»» limit-bytes-in=0 limit-bytes-out=0
2 ovpn-pool 10.15.32.34-10.15.32.38
ppp profile print
Flags: * — default
0 * name=»default» use-compression=default use-vj-compression=default use-encryption=default only-one=default change-tcp-mss=yes
1 name=»Beya_Voip» local-address=10.15.32.33 remote-address=ovpn-pool use-compression=default use-vj-compression=default
use-encryption=required only-one=default change-tcp-mss=default
Ovpn-Server Server:
interface ovpn-server server print
enabled: yes
port: 443
mode: ip
netmask: 29
mac-address: FE:50:A6:C5:67:B9
max-mtu: 1500
keepalive-timeout: disabled
default-profile: Beya_Voip
certificate: cert1
require-client-certificate: yes
auth: sha1,md5
cipher: blowfish128,aes128,aes192,aes256
CLIENT
interface ovpn-client print detail
Flags: X — disabled, R — running
0 name=»ovpn-out1″ mac-address=FE:84:A8:9E:19:43 max-mtu=1500 connect-to=172.16.0.1 port=443 mode=ip user=»username»
password=»password» profile=default certificate=cert1 auth=sha1 cipher=aes256 add-default-route=no
LOG
21:43:01 ovpn,info TCP connection established from W.X.Y.Z
21:43:02 ovpn,info TCP connection established from W.X.Y.Z
21:43:05 ovpn,info TCP connection established from W.X.Y.Z
21:43:05 ovpn,info TCP connection established from W.X.Y.Z
PING from Client:
ping 10.15.32.33
10.15.32.33 ping timeout
10.15.32.33 ping timeout
10.15.32.33 ping timeout
10.15.32.33 ping timeout
10.15.32.33 ping timeout
10.15.32.33 ping timeout
10.15.32.33 ping timeout
Re: OpenVPN tls-auth problem in RouterOS 4.6
Fri Apr 02, 2010 10:22 am
i have the same problem with tls, so i created certificate with easy-rsa in linux and when i set up ovpn server a choose certificate for it, mikrotik respond: Couldn´t change ovpn server — no certificate found. I created certificate
./pkitool —initca
./pkitool —pass —server RB450
./pkitool —pass client1
the passpahre is:test
when I import crt, key to mikrotik a write passphare:test, is it okay? The i can view 2 certificate on my mikrotik server, but when i can apply to ovpn server it respond with answer above. Can you tell me please what i do wrong?
Re: OpenVPN tls-auth problem in RouterOS 4.6
Fri Apr 02, 2010 10:25 am
i have the same problem with tls, so i created certificate with easy-rsa in linux and when i set up ovpn server a choose certificate for it, mikrotik respond: Couldn´t change ovpn server — no certificate found. I created certificate
./pkitool —initca
./pkitool —pass —server RB450
./pkitool —pass client1
the passpahre is:test
when I import crt, key to mikrotik a write passphare:test, is it okay? The i can view 2 certificate on my mikrotik server, but when i can apply to ovpn server it respond with answer above. Can you tell me please what i do wrong?
Источник
Здравствуйте.
Можно с разрешения ТС подобный вопрос задать, чтоб темы не плодить.
Подскажите пожалуйста. Поднял сервер openvpn на ubuntu server 18.04, на микрот установил сертификат и ключ. Пробую соединиться — не получается.
Лог сервера:
Код: Выделить всё
Thu Nov 14 01:32:07 2019 TCP connection established with [AF_INET]***.***.***.***:53340
Thu Nov 14 01:32:07 2019 185.184.233.160:53340 TLS: Initial packet from [AF_INET]***.***.***.***:53340, sid=53ffafd8 2edccd19
Thu Nov 14 01:32:07 2019 185.184.233.160:53340 TLS Error: cannot locate HMAC in incoming packet from [AF_INET]***.***.***.***:53340
Thu Nov 14 01:32:07 2019 185.184.233.160:53340 Fatal TLS error (check_tls_errors_co), restarting
Thu Nov 14 01:32:07 2019 185.184.233.160:53340 SIGUSR1[soft,tls-error] received, client-instance restartingконфигурация сервера:
Код: Выделить всё
port 1194
# Протокол может быть UDP или TCP, я выбрал 1-й вариант.
proto tcp
# Если вы выберите протокол TCP, здесь должно быть устройство tap. Однако, это вариант я не проверял, поэтому ищите информацию отдельно. FIXME
dev tun
# Указываем где искать ключи
ca /etc/openvpn/keys/ca.crt
cert /etc/openvpn/keys/server.crt
key /etc/openvpn/keys/server.key # This file should be kept secret
dh /etc/openvpn/keys/dh2048.pem
# Для 12.04 dh1024.pem
# Задаем IP и маску виртуальной сети. Произвольно, но если не уверены лучше делайте как показано здесь
server 10.8.0.0 255.255.255.0
# Указыем, где хранятся файлы с настройками IP-адресов клиентов (создадим ниже)
client-config-dir ccd
# Запоминать динамически выданные адреса для VPN-клиентов и при последующих подключениях назначать те же значения.
ifconfig-pool-persist ipp.txt
# Указываем сети, в которые нужно идти через туннель (сеть-клиента).
route 192.168.0.0 255.255.255.0
# Включаем TLS
tls-server
tls-auth /etc/openvpn/keys/ta.key 0
tls-timeout 120
auth SHA1
cipher AES-256-CBC
# Если нужно, чтобы клиенты видели друг друга раскомментируйте
;client-to-client
keepalive 10 120
# Сжатие трафика
;comp-lzo
# Максимум клиентов
max-clients 10
user nobody
group nogroup
# Не перечитывать ключи, не закрывать и переоткрывать TUNTAP устройство, после получения SIGUSR1 или ping-restart
persist-key
persist-tun
status openvpn-status.log
log /var/log/openvpn.log
# Детальность логирования
verb 3
# Защита от повторов (максимум 20 одинаковых сообщений подряд)
mute 20
# Файл отозванных сертификатов. Разремить, когда такие сертификаты появятся.
;crl-verify /etc/openvpn/crl.pemлог с микрота:
Настраивал по мануалу с вики ubuntu.ru
Где может быть ошибка?
благодарю
- Печать
Страницы: [1] Вниз
Тема: openvpn + mikrotik (Прочитано 1075 раз)
0 Пользователей и 1 Гость просматривают эту тему.

YDenis
Здравствуйте.
Подскажите пожалуйста. Поднял сервер openvpn на ubuntu server 18.04, на микрот установил сертификат и ключ. Пробую соединиться — не получается.
Лог сервера:
Thu Nov 14 01:32:07 2019 TCP connection established with [AF_INET]***.***.***.***:53340
Thu Nov 14 01:32:07 2019 185.184.233.160:53340 TLS: Initial packet from [AF_INET]***.***.***.***:53340, sid=53ffafd8 2edccd19
Thu Nov 14 01:32:07 2019 185.184.233.160:53340 TLS Error: cannot locate HMAC in incoming packet from [AF_INET]***.***.***.***:53340
Thu Nov 14 01:32:07 2019 185.184.233.160:53340 Fatal TLS error (check_tls_errors_co), restarting
Thu Nov 14 01:32:07 2019 185.184.233.160:53340 SIGUSR1[soft,tls-error] received, client-instance restarting
конфигурация сервера:
port 1194
# Протокол может быть UDP или TCP, я выбрал 1-й вариант.
proto tcp
# Если вы выберите протокол TCP, здесь должно быть устройство tap. Однако, это вариант я не проверял, поэтому ищите информацию отдельно. FIXME
dev tun
# Указываем где искать ключи
ca /etc/openvpn/keys/ca.crt
cert /etc/openvpn/keys/server.crt
key /etc/openvpn/keys/server.key # This file should be kept secret
dh /etc/openvpn/keys/dh2048.pem
# Для 12.04 dh1024.pem
# Задаем IP и маску виртуальной сети. Произвольно, но если не уверены лучше делайте как показано здесь
server 10.8.0.0 255.255.255.0
# Указыем, где хранятся файлы с настройками IP-адресов клиентов (создадим ниже)
client-config-dir ccd
# Запоминать динамически выданные адреса для VPN-клиентов и при последующих подключениях назначать те же значения.
ifconfig-pool-persist ipp.txt
# Указываем сети, в которые нужно идти через туннель (сеть-клиента).
route 192.168.0.0 255.255.255.0
# Включаем TLS
tls-server
tls-auth /etc/openvpn/keys/ta.key 0
tls-timeout 120
auth SHA1
cipher AES-256-CBC
# Если нужно, чтобы клиенты видели друг друга раскомментируйте
;client-to-client
keepalive 10 120
# Сжатие трафика
comp-lzo
# Максимум клиентов
max-clients 10
user nobody
group nogroup
# Не перечитывать ключи, не закрывать и переоткрывать TUNTAP устройство, после получения SIGUSR1 или ping-restart
persist-key
persist-tun
status openvpn-status.log
log /var/log/openvpn.log
# Детальность логирования
verb 3
# Защита от повторов (максимум 20 одинаковых сообщений подряд)
mute 20
# Файл отозванных сертификатов. Разремить, когда такие сертификаты появятся.
;crl-verify /etc/openvpn/crl.pem
Настраивал по мануалу с вики ubuntu.ru
Где может быть ошибка?
благодарю
Пользователь добавил сообщение 14 Ноября 2019, 08:43:09:
Нашел ошибку.
Закоментировать
;tls-server
;tls-auth /etc/openvpn/keys/ta.key 0
;tls-timeout 120
« Последнее редактирование: 14 Ноября 2019, 08:43:09 от YDenis »

YDenis
Ребята, на клиентских машинах за миктротом не могу добиться выхода в инет через openvpn туннель.
Здравствуйте.
Подскажите пожалуйста. На арубе на ubuntu server 18.04 поднял opevpn сервер.
Конфигурация:
port 443ccd:
proto tcp
dev tun
ca /etc/openvpn/keys/ca.crt
cert /etc/openvpn/keys/server.crt
key /etc/openvpn/keys/server.key
dh /etc/openvpn/keys/dh2048.pem
server 10.8.0.0 255.255.255.0
push "dhcp-option DNS 8.8.8.8"
client-config-dir /etc/openvpn/ccd
auth SHA1
cipher AES-256-CBC
client-to-client
keepalive 10 120
max-clients 10
user nobody
group nogroup
persist-key
persist-tun
status openvpn-status.log
log /var/log/openvpn.log
verb 3
mute 20
ifconfig-push 10.8.0.50 10.8.0.1Ip сервера openvpn — 10.8.0.1/24
Ip клиента на микроте — 10.8.0.50
Микрот соединение поднял, но в статусе соединения поле с remote и local ip пустые. Но в роутинге появились динамические маршруты с верными адресами:
С микрота трансроут на ya.ru:
Пинг с ubuntu на микрот:
Включаю маршрут на микроте — все пакеты завернуть на openvpn:
Пинг с клиенткой машины за микротом (192.168.1.200) при включенном выше маршруте:
iptables:
Плиз, где я неверно сделал?
Благодарю
« Последнее редактирование: 17 Ноября 2019, 16:51:12 от YDenis »
- Печать
Страницы: [1] Вверх
Mikrotik OpenVPN Client и OpenVPN Server
5
Посты
3
Пользователи
1
Likes
5,866
Просмотры
(@uj2062)
New Member
Присоединился: 3 года назад
Сообщения: 2
Topic starter
09.09.2019 09:51
Добрый день. Прошу прощения за оффтоп, вопрос скорее про настройку ovpn-сервера для подключения mikrotik-клиента.
Есть mikrotik в качестве граничного устройства небольшой сети с несколькими сегментами.
Есть VPS (Debian 9) с установленным OpenVPN сервером.
Есть несколько клиентов в интернете, которым необходимо обеспечить доступ к одному из сегментов за микротиком.
Возникла проблема при настройке сервера, не могу отключить TLS, который mikrotik не понимает, и получаю ошибку сервера «TLS Error: cannot locate HMAC in incoming packet from «
Буду признателен за помощь.
server.conf :
port 1194
proto tcp
dev tun
sndbuf 0
rcvbuf 0
ca ca.crt
cert server.crt
key server.key
dh dh.pem
auth SHA1
#tls-auth ta.key 0
#tls-server
#tls-auth none
key-direction 0
topology subnet
server 192.168.8.0 255.255.255.0
ifconfig-pool-persist ipp.txt
push «redirect-gateway def1 bypass-dhcp»
push «dhcp-option DNS 217.12.200.200»
push «route 192.168.8.0 255.255.255.0»
keepalive 10 120
cipher BF-CBC
user nobody
group nogroup
persist-key
persist-tun
;status openvpn-status.log
client-config-dir ccd
verb 5
crl-verify crl.pem
client-to-client
push «route 0.0.0.0 0.0.0.0 vpn_gateway 512»
status openvpn-status.log
log openvpn.log
(@zerox)
Prominent Member Admin
Присоединился: 9 лет назад
Сообщения: 806
09.09.2019 12:46
Я для микротиков поднимаю отдельный туннель. Вот пример конфига с работающего сервера vpn.
port 1195
proto tcp
dev tun2ca /etc/openvpn/keys/ca.crt
cert /etc/openvpn/keys/router.crt
key /etc/openvpn/keys/router.key
dh /etc/openvpn/keys/dh1024.pem
crl-verify /etc/openvpn/crl.pemserver 10.10.110.0 255.255.255.0
push "dhcp-option DNS 10.1.3.21"
push "route 10.1.3.0 255.255.255.0"
push "route 10.1.4.0 255.255.255.0"
push "route 10.1.5.0 255.255.255.0"
push "route 10.10.100.0 255.255.255.0"
push "route 10.10.101.0 255.255.255.0"
push "route 10.10.102.0 255.255.255.0"
push "route 10.10.103.0 255.255.255.0"
push "route 10.10.104.0 255.255.255.0"
push "route 10.10.110.0 255.255.255.0"client-config-dir ccd-mikrotik-tcp
ifconfig-pool-persist mikrotik-tcp.txt
route 10.1.5.0 255.255.255.0
route 10.10.110.0 255.255.255.0
client-to-client
auth SHA1
cipher BF-CBC
keepalive 10 30
max-clients 100
user nobody
group nobody
persist-key
persist-tun
status /var/log/openvpn/status-mikrotik-tcp.log
log /var/log/openvpn/log-mikrotik-tcp.log
verb 3
push "ping 10"
push "ping-restart 20"
(@uj2062)
New Member
Присоединился: 3 года назад
Сообщения: 2
Topic starter
12.09.2019 10:15
@zerox
Спасибо, помогло. Смущает скорость соединения, пинги между клиентами прыгают иногда до 800 мс. Средние 150-200 мс. Говорят в микротике гораздо удачней реализован sstp-client. Не было опыта установки связки softether — mikrotik sstp client ?
(@zerox)
Prominent Member Admin
Присоединился: 9 лет назад
Сообщения: 806
12.09.2019 11:48
@uj2062
В общем случае, у меня проблем на каналах до 50-ти мегабит с микротиком и openvpn нет. Пинги не скачат, скорости нормальные. Обращаю только внимание на cipher BF-CBC Сейчас это считается не безопасным. Нужно использовать другие алгоритмы, если нужна 100% защита. Мне это чаще всего не нужно, поэтому я жертвую защитой в пользу быстродействия.
(@farrukhg84)
Estimable Member
Присоединился: 4 года назад
Сообщения: 105
21.04.2020 08:13
А как прописать в настройках клиента ip address DNS серверов ( у нас их две). VPN-server настроен на микротике
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and
privacy statement. We’ll occasionally send you account related emails.
Already on GitHub?
Sign in
to your account
Comments
I keep getting TLS Error: cannot locate HMAC in incoming packet from [AF_INET]xx.xx.xx.xx:xxxxx when my OpenVPN client connected to the server. It seems tls-auth /etc/openvpn/pki/ta.key doesn’t work.
If I comment this line and it will generate a log message like xx.xx.xx.xx:xxxxx TLS: Initial packet from [AF_INET]xx.xx.xx.xx:xxxxx, sid=a1b9713f 033e1970, but xx.xx.xx.xx:xxxxx TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity) & xx.xx.xx.xx:xxxxx TLS Error: TLS handshake failed will be generated after a while. The connection is still failed. Could you please advise the solution? Really appreciate.
Same issue here. To fix this, you can either comment out the tls-auth option from the openvpn.conf file; or add the tls-auth and key-redirection into the end of client configuration file, as below:
<tls-auth>
-----BEGIN OpenVPN Static key V1-----
(contents of ta.key)
-----END OpenVPN Static key V1-----
</tls-auth>
key-direction 1
Had to add tls-server to the server.conf for this to work
I don’t think this is a server issue. It is a client side problem. You should inspect your OpenVPN client configuration especially TLS auth part.