Содержание
- Occasional unspecified certficate verification error with PSK on Windows Server 2019
- Details
- Description
- Jira Integration with self signed cert throws unspecified certificate verification error even openssl works
- Summary
- Rehash: How to Fix the SSL/TLS Handshake Failed Error
- Fixes for the SSL/TLS handshake failed error for both internet users and site owners
- What Is the SSL/TLS Handshake?
- The SSL/TLS Handshake Process in TLS 1.2 vs TLS 1.3
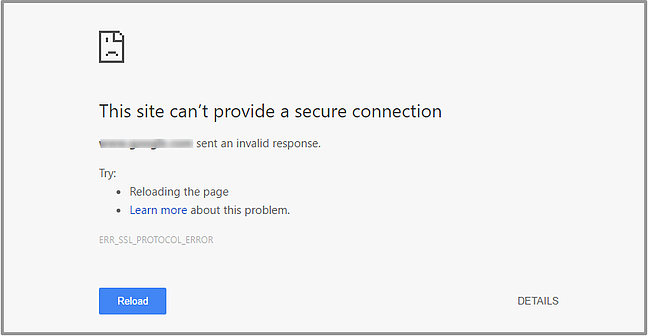
- An Overview of SSL/TLS Handshake Failed Errors
- SSL/TLS Handshake Failed — Client Errors
- Incorrect System Time
- Browser Error
- Man-in-the-Middle
- SSL/TLS Handshake Failed: Server-Side Errors
- Protocol Mismatch
- Cipher Suite Mismatch
- Incorrect SSL/TLS Certificate
- Incorrect Host Name
- Incorrect Certificate Chain
- Expired/Revoked Certificates
- Self-Signed Replacements
- SNI-Enabled Servers
- What Not to Do – Don’t Reward Bad SSL/TLS Implementations
- Author
Occasional unspecified certficate verification error with PSK on Windows Server 2019
Details
Description
Steps to reproduce:
- Upgraded both server and agents from 4.4.x to 5.0.6
- Using active agent checks and TLS with PSK, on Windows servers
Server logs occasionally:
10377:20201216:125835.926 failed to accept an incoming connection: from 10.11.22.33: unspecified certificate verification error: TLS handshake set result code to 5:
10374:20201216:125835.928 failed to accept an incoming connection: from 10.22.33.10: unspecified certificate verification error: TLS handshake set result code to 5:
10374:20201216:125907.068 failed to accept an incoming connection: from 10.33.33.8: unspecified certificate verification error: TLS handshake set result code to 5:
At the same time client (10.11.22.33 agent above) logs:
12628:20201216:125833.259 active check data upload to [zabbix-server-ip:10051] started to fail ( [connect] TCP successful, cannot establish TLS to [ [zabbix-server-ip] :10051]: SSL_connect() timed out)
12628:20201216:125835.938 active check data upload to [zabbix-server-ip:10051] is working again
Expected:
No messages in the logs when agents connect and send data to server.
Initially we had server 4.4.10 on Debian Linux 9 (Stretch) and agents 4.4.x, and we didn’t have those errors.
Then we first changed the server to a new one with Debian Linux 10 (Buster) with server 4.4.10 (new installation, copied the configurations), and that’s when the error messages started.
We then upgraded both server and agents to 5.0.6, but the occasional errors continued. There are less errors though with 5.0.6.
Notable detail is that agents on Linux, on Windows 10 or on Windows Server 2016 do not cause these errors (agents are 4.0.x, 4.4.x or 5.0.6).
Debian 9 server (old server with no problems) openssl version: OpenSSL 1.1.0l 10 Sep 2019
Debian 10 server (current) openssl version: OpenSSL 1.1.1d 10 Sep 2019
Источник
Jira Integration with self signed cert throws unspecified certificate verification error even openssl works
Summary
We self host our JIRA and GitLab (Docker).
We want to integrate the JIRA Features in Gitlab like descripted here: https://docs.gitlab.com/ee/user/project/integrations/jira.html
We entered a valid administrator account in username / password-fields.
We entered a valid url (https://jira.DOMAIN.int:8443).
We looked for the right transition ID and entered it (71 in our case).
Error: Test failed. Save anyway.
The integration_json.log shows:
SSL_connect returned=1 errno=0 state=error: certificate verify failed (unspecified certificate verification error)
What we have done so far?
- entered the correct host in /etc/hosts
- download the self signed certificat with Chrome in 3 files (main certificat and 2 roots certificat)
- Run reconfigure in gitlab and see the output, that all 3 files are recognized in Recipe: gitlab::add_trusted_certs
- Look in the /opt/gitlab/embedded/ssl/certs and see 3 correct system links to the 3 files in /etc/gitlab/trusted-certs
- Run OpenSSL from Gitlab: Connected!
*root@c9cab22e6481:/etc/gitlab# echo | /opt/gitlab/embedded/bin/openssl s_client -connect jira.xxx.int:8443 CONNECTED(00000003) Can’t use SSL_get_servername depth=0 C = DE, ST = RLP, L = KO, O = xxx AG, OU = GOE, CN = JIRA verify return:1
Certificate chain 0 s:C = DE, ST = RLP, L = KO, O = xxx AG, OU = GOE, CN = JIRA i:C = DE, ST = RLP, L = KO, O = xxx AG, OU = GOE, CN = JIRA
——BEGIN CERTIFICATE—— MIIDVTCCAj2gAwIBAgIEU135NjANBgkqhkiG9w0BAQsFADBbMQswCQYDVQQGEwJE RTEMMAoGA1UECBMDUkxQMQswCQYDVQQHEwJLTzEUMBIGA1UEChMLR09FUkxJVFog QUcxDDAKBgNVBAsTA0dPRTENMAsGA1UEAxMESklSQTAeFw0xODA3MjMxMDU0NTRa Fw0yMjA4MzExMDU0NTRaMFsxCzAJBgNVBAYTAkRFMQwwCgYDVQQIEwNSTFAxCzAJ BgNVBAcTAktPMRQwEgYDVQQKEwtHT0VSTElUWiBBRzEMMAoGA1UECxMDR09FMQ0w CwYDVQQDEwRKSVJBMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAjeh6 g6I5ErXj6ZaIf9f+RIHZRbDDjRxk1APXWN914iO6EA+l/tdGvSKY0e4WJu16hOPn klUYq+iaMKVE9LTezu7W1LZ2r+QiDMus7GV3z+x1wq3UZ8m/Mxnr4iiz6WIemWEY Gdifmsa6BVicai/RZs3sQeVpuO3qovKbKV1DxbJ9TX+g2OFrEYqwE6mZiRR23/kp IzOeNOlhWtVYyjRXpIMmyGpWE+/H3ijVIMKBe2UDb59ORsxILGIk9llfDBWw7e1h Zx7MfCwQ5tb5B75a1He4ROAolymYigszgU+lEwmFcM+cu58gfyU99eF/QaLESBSS J3ZMP5+6xt2s3bCxEQIDAQABoyEwHzAdBgNVHQ4EFgQU3SRIHlvXyp+CDR5SCNww ramoI8kwDQYJKoZIhvcNAQELBQADggEBAB/mB7rys9JHZdvxzXI9z068MjXVifcK jif2GoSV3LC1PQXET4OxcpLdEVCuZP9KFKOQBYriblrlxT7uXoipqZ0VNN7EgYNv ivEZcKV6+JtkASCJMD1Tv1iWqoKZeJHgu2EJVQUnL3ZOsl4u57awYAaou8u25O1s ZtRe4V6GKdgetsp98qMK0B0YLM2+Ot8Nb2sWE6m+gDbMizRblny9hbv9znJbNSWE WgDmPK+ZKJQyumXZU+oJ5bvmPfA79H69mqytHRl42d7ql9yQlscuBYGVHoxevOKk Z94kd889sAjF2dZR7nc2JN4rV1qUNDB4tHV+o0RTmw9hBMg+E6sPYa4= ——END CERTIFICATE——
subject=C = DE, ST = RLP, L = KO, O = xxx AG, OU = GOE, CN = JIRA
issuer=C = DE, ST = RLP, L = KO, O = xxx AG, OU = GOE, CN = JIRA
No client certificate CA names sent Peer signing digest: SHA256 Peer signature type: RSA Server Temp Key: ECDH, P-256, 256 bits
SSL handshake has read 1345 bytes and written 419 bytes Verification: OK
New, TLSv1.2, Cipher is ECDHE-RSA-AES256-GCM-SHA384 Server public key is 2048 bit Secure Renegotiation IS supported No ALPN negotiated SSL-Session: Protocol : TLSv1.2 Cipher : ECDHE-RSA-AES256-GCM-SHA384 Session-ID: 5F0445083881A3E4B6DE86A7C1238D35F05BFBB914FD9F8E6F463C4CA87BFF03 Session-ID-ctx: Master-Key: 5CF9A153121058D6E1D9D3D0D63F8A17BB813ED22464FFA8A35398F8069D34580359299E6EA80E08413D9B2524714B7C PSK identity: None PSK identity hint: None SRP username: None Start Time: 1594115336 Timeout : 7200 (sec) Verify return code: 0 (ok) Extended master secret: yes
- Run openssl x509 -in /etc/gitlab/trusted-certs/certificat.cer -text -noout
Certificate: Data: Version: 3 (0x2) Serial Number: 1398667574 (0x535df936) Signature Algorithm: sha256WithRSAEncryption Issuer: C = DE, ST = RLP, L = KO, O = xxx AG, OU = GOE, CN = JIRA Validity Not Before: Jul 23 10:54:54 2018 GMT Not After : Aug 31 10:54:54 2022 GMT Subject: C = DE, ST = RLP, L = KO, O = xxx AG, OU = GOE, CN = JIRA Subject Public Key Info: Public Key Algorithm: rsaEncryption RSA Public-Key: (2048 bit) Modulus: 00:8d:e8:7a:83:a2:39:12:b5:e3:e9:96:88:7f:d7: fe:44:81:d9:45:b0:c3:8d:1c:64:d4:03:d7:58:df: 75:e2:23:ba:10:0f:a5:fe:d7:46:bd:22:98:d1:ee: 16:26:ed:7a:84:e3:e7:92:55:18:ab:e8:9a:30:a5: 44:f4:b4:de:ce:ee:d6:d4:b6:76:af:e4:22:0c:cb: ac:ec:65:77:cf:ec:75:c2:ad:d4:67:c9:bf:33:19: eb:e2:28:b3:e9:62:1e:99:61:18:19:d8:9f:9a:c6: ba:05:58:9c:6a:2f:d1:66:cd:ec:41:e5:69:b8:ed: ea:a2:f2:9b:29:5d:43:c5:b2:7d:4d:7f:a0:d8:e1: 6b:11:8a:b0:13:a9:99:89:14:76:df:f9:29:23:33: 9e:34:e9:61:5a:d5:58:ca:34:57:a4:83:26:c8:6a: 56:13:ef:c7:de:28:d5:20:c2:81:7b:65:03:6f:9f: 4e:46:cc:48:2c:62:24:f6:59:5f:0c:15:b0:ed:ed: 61:67:1e:cc:7c:2c:10:e6:d6:f9:07:be:5a:d4:77: b8:44:e0:28:97:29:98:8a:0b:33:81:4f:a5:13:09: 85:70:cf:9c:bb:9f:20:7f:25:3d:f5:e1:7f:41:a2: c4:48:14:92:27:76:4c:3f:9f:ba:c6:dd:ac:dd:b0: b1:11 Exponent: 65537 (0x10001) X509v3 extensions: X509v3 Subject Key Identifier: DD:24:48:1E:5B:D7:CA:9F:82:0D:1E:52:08:DC:30:AD:A9:A8:23:C9 Signature Algorithm: sha256WithRSAEncryption 1f:e6:07:ba:f2:b3:d2:47:65:db:f1:cd:72:3d:cf:4e:bc:32: 35:d5:89:f7:0a:8e:27:f6:1a:84:95:dc:b0:b5:3d:05:c4:4f: 83:b1:72:92:dd:11:50:ae:64:ff:4a:14:a3:90:05:8a:e2:6e: 5a:e5:c5:3e:ee:5e:88:a9:a9:9d:15:34:de:c4:81:83:6f:8a: f1:19:70:a5:7a:f8:9b:64:01:20:89:30:3d:53:bf:58:96:aa: 82:99:78:91:e0:bb:61:09:55:05:27:2f:76:4e:b2:5e:2e:e7: b6:b0:60:06:a8:bb:cb:b6:e4:ed:6c:66:d4:5e:e1:5e:86:29: d8:1e:b6:ca:7d:f2:a3:0a:d0:1d:18:2c:cd:be:3a:df:0d:6f: 6b:16:13:a9:be:80:36:cc:8b:34:5b:96:7c:bd:85:bb:fd:ce: 72:5b:35:25:84:5a:00:e6:3c:af:99:28:94:32:ba:65:d9:53: ea:09:e5:bb:e6:3d:f0:3b:f4:7e:bd:9a:ac:ad:1d:19:78:d9: de:ea:97:dc:90:96:c7:2e:05:81:95:1e:8c:5e:bc:e2:a4:67: de:24:77:cf:3d:b0:08:c5:d9:d6:51:ee:77:36:24:de:2b:57: 5a:94:34:30:78:b4:75:7e:a3:44:53:9b:0f:61:04:c8:3e:13: ab:0f:61:ae
- Flush trusted-certs-directory-hash with rm /var/opt/gitlab/trusted-certs-directory-hash
Источник
Rehash: How to Fix the SSL/TLS Handshake Failed Error
Fixes for the SSL/TLS handshake failed error for both internet users and site owners
It’s time for another technical article. Today, we’re going to discuss the SSL/TLS handshake failed error and the ways to fix it. Like many SSL error messages, the SSL handshake error can be triggered from both the client-side and the server-side, so sometimes it can be fixed by regular internet users and other times it’s indicative of a configuration issue on the website’s part.
Regardless of its origins, this can be a frustrating SSL error because it prevents you from making a secure connection with the website you’re attempting to access. This is bad for users and site owners alike — for the site owners because it drives away business (potentially straight into the arms of your competitors).
We’ll get into what the SSL/TLS handshake is, then we’ll cover the reasons for the SSL/TLS handshake failed error and what you can do to fix it.
Let’s hash it out.
What Is the SSL/TLS Handshake?
At the beginning of every HTTPS connection, the client (the internet user’s web browser) and the server (hosting the website) must go through a series of checks — for lack of a better term — to authenticate one another and determine the parameters of the encrypted connection. This is known as the TLS handshake, although some within the industry still refer to it as an SSL handshake.
(SSL is no longer technically accurate since it’s a deprecated protocol. However, we’ll still refer to it as such throughout the article because people still commonly use the term. So, you’ll see “SSL handshake” and “TLS handshake” used interchangeably throughout the content, but just know that we’re still talking about the TLS handshake.)
The TLS handshake process accomplishes three things:
- Authenticates the server as the rightful owner of the asymmetric public/private key pair.
- Determines the TLS version and cipher suite that will be used for the connection.
- Exchanges the symmetric session key that will be used for communication.
If you simplify public key infrastructure (PKI) —which serves as the infrastructure for the entire SSL/TLS ecosystem — it’s really about secure key exchange. During an HTTPS connection, the communication is actually done with symmetric session keys — generally 256-bit advanced encryption standard (AES) keys — that are generated on the client side of things. When a symmetric key is generated, both parties get a copy. They can use it to encrypt and decrypt the data that transmits between them.
While 256-bit encryption is still sufficiently robust, the real security is at the gate where a much larger, much stronger private key (generally a 2048-bit RSA key) helps handle the authentication portion of the connection. Authentication is important because the client wants to make sure it’s connecting with the correct party. That’s essentially what the SSL/TLS handshake is for — it’s a set of checks where:
- The client and server authenticate one another,
- They determine the parameters of the HTTPS connections (what cipher suite will be used), and then
- The client encrypts a copy of the session key and sends it to the server for use during the connection.
Historically, the SSL/TLS handshake has added a small bit of latency to a connection, which is what led to the claim that HTTPS slows down your website. That latency has been addressed in more recent versions of the TLS protocol though, so that’s almost entirely untrue today — especially with HTTP/2 and HTTP/3.
Currently, there are two different versions of the TLS handshake in use: TLS 1.2 and TLS 1.3.
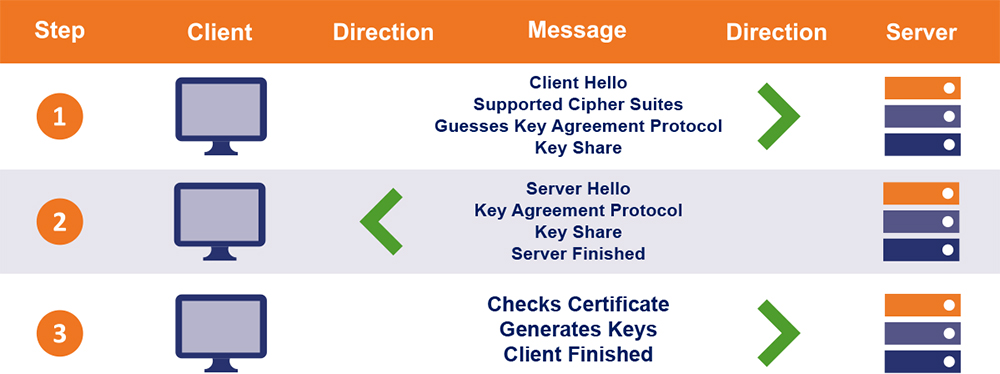
The SSL/TLS Handshake Process in TLS 1.2 vs TLS 1.3
TLS 1.2 uses a handshake that makes multiple roundtrips between the client and the server.
Wondering how the TLS handshake process works? We’re not going to go step-by-step, but essentially:
- The client and server ping one another.
- The server presents its SSL/TLS certificate.
- The client authenticates the certificate authority (CA)-signed certificate.
- They exchange a list of supported cipher suites and agree on one, then key exchange occurs.
This process involves a lot of steps — all of which occur in a short amount of time.
TLS 1.3, on the other hand, has refined the TLS handshake to a single round-trip.
Obviously, this cuts down on the time that it takes for a connection to start — we’re talking milliseconds here so maybe not noticeably (except at scale) — and makes everything more efficient. TLS 1.3 also allows 0-RTT resumption, which streamlines subsequent connections to a TLS 1.3-enabled website even more.
But, given the number of moving parts in a TLS handshake, there’s plenty that can go wrong if a website or a device are misconfigured. A couple years ago we wrote about fixing TLS handshakes failed errors on Firefox, but these errors are far more universal than that. So now let’s talk about what can go wrong with the TLS handshake and what need to be done to fix it.
In Everything Encryption By Patrick Nohe
There’s a lot going on underneath the hood when you connect to a website via HTTPS. First and foremost, everyone needs to… shake hands?!
An Overview of SSL/TLS Handshake Failed Errors
To make this article a little bit easier to follow, we’re going to put all of the possible causes for SSL/TLS handshake failed errors (SSL handshake errors) and who can fix them. After that, we’ll have a dedicated section for each where we’ll cover how to fix them.
| CAUSE | DESCRIPTION OF THE TLS HANDSHAKE ERROR | FIX |
| Incorrect System Time | Client device has the incorrect time & date. | Client |
| Browser Error | A browser configuration is causing the error. | Client |
| Man-in-the-Middle | A third party is intercepting/manipulating connection. | Client |
| Protocol Mismatch | The protocol used by client is not supported by server. | Server |
| Cipher Suite Mismatch | Cipher suite used by client is not supported by server. | Server |
| Incorrect Certificate |
|
Server |
| SNI-Enabled Server | Client can’t communicate with SNI-enabled server. | Server |
Now, let’s dive into fixing these SSL handshake failed errors. Then we’ll finish with a couple of things you should definitely not do from the client-side to try and fix this mistake.
 SSL/TLS Handshake Failed — Client Errors
SSL/TLS Handshake Failed — Client Errors
When a handshake fails, it’s usually something going on with the website/server and its SSL/TLS configuration. This results in that pesky SSL/TLS handshake error.
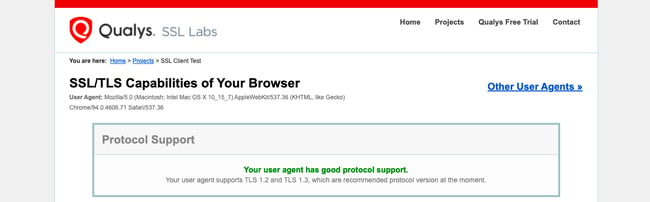
Really, it’s just TLS configuration at this point as support for SSL 3.0 has been almost entirely deprecated. (SSL Labs reports that only 4.6% of sites still support the SSL 3.0. protocol as of August 2020.)
However, there are a few contexts in which a client-side error can cause the SSL/TLS handshake failed error. And a lot of them may seem pretty trivial — things like making sure your system time is correct and your browser is current.
But, as we discussed, there are a lot of moving parts with the TLS handshake, and sometimes even the tiniest hiccup can cause the whole thing to go kaput.
So, let’s go over a few of the client-side fixes for this issue.
Incorrect System Time
I’m really not sure why anyone would take their system clock off of the universal time option, but apparently it happens. Maybe you want to abide your own personal clock like some kind of psychopath or maybe the setting just got accidentally changed — it’s none of my business, really — but if your system time is wrong it can cause problems with TLS handshake. As a result, this can cause the SSL/TLS handshake failed error.
That’s largely owing to the fact that SSL/TLS certificates have finite lifespans, so time is important. In fact, in some rather high profile cases of certificate expiration — like with the Oculus Rift VR system — internet users have even purposely set their system times back to a date before said expiration so that they could still connect. (More recent examples of notable certificate expiries affecting everything from COVID-19 reporting to streaming music services.)
Obviously, don’t change your system time. If you’re still getting the SSL/TLS handshake failed error and your system time is correct, the issue is originating somewhere else.
Browser Error
This isn’t like a browser error — this is literally your browser making a mistake. Sometimes your browser can become misconfigured, or a plugin can cause things to work a little bit differently and it results in problems connecting to otherwise legitimate websites. While diagnosing exactly what needs to be tweaked on your current browser may be a little bit more difficult, narrowing the issue down to a specific browser error is pretty simple: just try another browser and see what happens.
If you’re using Google Chrome, switch to your OS’s native browser like Apple Safari or Microsoft Edge. Otherwise, hop on Mozilla Firefox (my preference) if you have it.
Basically, just switch it up and try connecting to the site. If you get the same SSL/TLS handshake failed error, then you know it’s not the browser causing the issue. But if you can connect, now you know something is up with your plugins or settings.
Related: Secure Your Website with a Comodo SSL Certificate.
The fastest way to fix this SSL/TLS handshake error-causing issue is just to reset your browser to the default settings and disable all your plugins. From there, you can configure the browser however you want, testing your connection with the site in question as you tweak things. This may take a little bit of time, but it’s really the only way to address the issue if your browser is misconfigured or is making mistakes.
Man-in-the-Middle
A man-in-the-middle (MITM) is typically presented as a nefarious hacker that’s attempting to steal information or cause harm. That’s actually not always the case. A lot of programs and devices intercept traffic for inspection or some other non-malicious purpose like load balancing, and then send it along to the application server. This process technically constitutes a MITM, too.
Unfortunately, sometimes issues with those devices can cause a TLS handshake to fail. It could be something like a network firewall preventing the connection, or it could be a configuration on an edge device on the server-side network. So, this issue can actually be either a client- or server-side fix depending on the scenario.
Here’s the thing: If this issue is client-side, you risk exposing yourself if you jigger with the settings on your antivirus or VPN. There should generally be a way to whitelist or create an exception for the site in question. But NEVER drop your firewall or your antivirus just connect to a website. If the issue is server-side, it’s likely a configuration issue on an edge device.
Recently, Ross Thomas, was telling me about a device he dealt with once that was intercepting traffic and affixing a small data string to indicate it had passed inspection. That was causing the data to fail check-sum hashes and could also potentially mess with authentication.
Again, there are too many possible origins for me to narrow it down to a single fix here, but if you have a device inspecting or intercepting traffic, start there.
SSL/TLS Handshake Failed: Server-Side Errors
The majority of the time SSL/TLS handshake failures are the result of server-side issues. Some of these are easy to fix, some of them are a little more involved, and some might not be worth fixing at all.
Let’s take a look.
 Protocol Mismatch
Protocol Mismatch
This is actually an error that can occur on both the client- and the server-side, and it can actually be something that’s not worth fixing depending on the context. When it comes to supporting protocols and ciphers, the most important piece of wisdom is: always move forward, never move backwards.
TLS 1.2 came out more than a decade ago, yet there are still a small segment of websites that don’t support it. In 2018, TLS 1.3 was finally published as RFC 8446 by the IETF. As of August 2020, Qualys SSL Labs reports that 98.4% of the Alexa top 150,000 sites support TLS 1.2 and 32.8% support TLS 1.3.
In the other direction, PCI DSS requirements mandate that all websites that collect payment card information end support for SSL 3.0 and TLS 1.0. And the four major browser makers — Google, Firefox, Apple & Microsoft — jointly announced TLS 1.1 would be deprecated by 2020.
If you’re getting the SSL/TLS handshake failed error as a result of a protocol mismatch, it means that the client and server do not have mutual support for the same TLS version. Here’s an example:
| CLIENT | SERVER |
| Supports TLS 1.0, TLS 1.1 | Supports TLS 1.2 |
In this scenario, there is no mutually supported TLS protocol and the server likely isn’t supporting backwards versioning. And before you ask, no, the server shouldn’t fix this. In this example, the client should upgrade their browser, or, in the case that the browser is current — configure it to support the latest TLS versions.
At this point, you should be using TLS 1.2 or TLS 1.3. If you’re not, add support for them. But remember, never go backwards.
 Cipher Suite Mismatch
Cipher Suite Mismatch
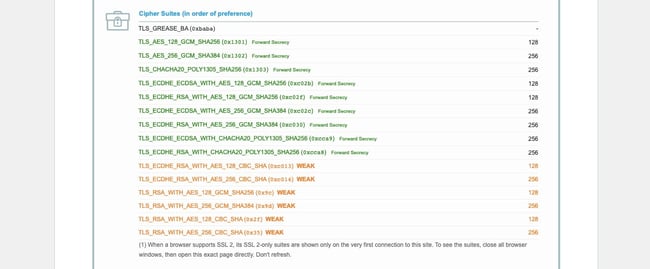
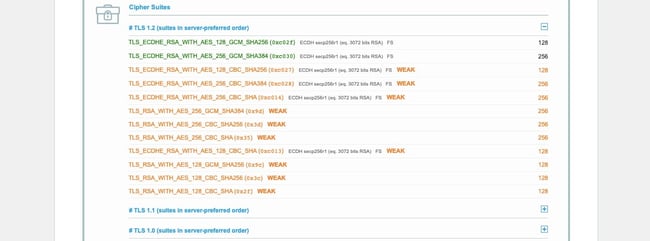
This is incredibly similar to the protocol mismatch — just a bit more granular. SSL/TLS isn’t just one algorithm that handles everything (though ECC is close), it’s actually a collection of algorithms that serve different functions and work in conjunction to make up SSL/TLS.
SSL/TLS is like the Megazord and the cipher suite is like the Power Rangers.
What? You try to make a grouping of algorithms sound more interesting.
Anyway, while the cipher suites used by TLS 1.3 have been refined, traditionally a Cipher Suite has had algorithms that handle:
- Asymmetric public key encryption
- Symmetric session key encryption
- Key generation
- Signature hashing
Different industries and government agencies have different encryption standards that suggest different cipher suites. Generally, there’s a lot of overlap there, and most websites support a handful of cipher suites so that clients have several options and will generally be able to find a mutually agreeable cipher. Obviously, the odds of successful negotiation would decrease substantially if a site only supported a single cipher suite.
Oftentimes this can happen within a network if you’re performing SSL bridging, where an edge device receives and decrypts HTTPS traffic, then re-encrypts it so send along to the application server. If the edge device and the application server don’t share a mutually supported cipher suite, it will cause errors.
Much like with protocol versions, you should only ever move forward with cipher suites — never backwards. Remember, when a protocol version or cipher suite is deprecated it’s not because the industry is trying to be difficult — it’s because a vulnerability has been found or is imminent. So, going backwards only makes your connections potentially less safe.
Incorrect SSL/TLS Certificate
There are a number of different things that can make a browser view an SSL/TLS certificate as incorrect and prevent the handshake from completing successfully. We’ll go through each in the next sub-sections. It’s also worth noting that, sometimes, these issues will materialize into a different error on the client-side as opposed to the SSL/TLS handshake failed message. Generally, something along the lines of the website not providing a secure connection. But on a technical level that error is occurring as the result of a failed handshake.
| ISSUE | DESCRIPTION |
| Host Name Mismatch | The CN in the certificate does not match the host name. |
| Incorrect Certificate Chain | The certificate chain is missing intermediates. |
| Expired/Revoked Certificate | The server presented an expired, revoked or untrusted certificate. |
| Self-Signed Replacements | (Internal Networks) Certificate replacements confused path. |
Incorrect Host Name
This used to be a problem with WWW and non-WWW versions of websites. However, this issue has largely been mitigated by the certificate authority community allowing one to be listed as a SAN (subject alternative name) domain free of charge. This issue can usually be fixed by re-issuing the certificate or sometimes by using a wildcard certificate.
Incorrect Certificate Chain
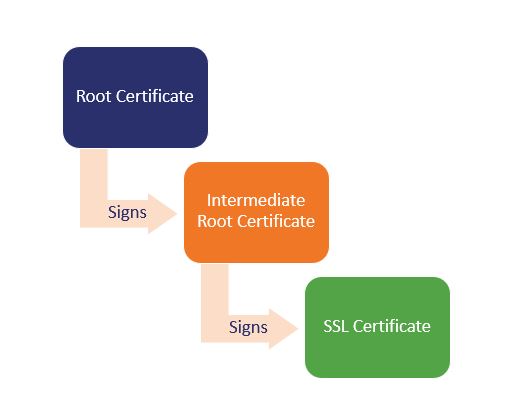
We went in-depth on certificate chains, roots and intermediate certificates in a previous article, but here’s the quick version. The trust model in SSL/TLS and PKI in general relies on meticulously-curated root programs. These are collections of trusted CA root certificates that literally live on a computer system.
| ROOT PROGRAM | USED BY |
| Mozilla | Firefox Desktop and Mobile |
| Android OS | |
| Apple | iOS, macOS |
| Microsoft | Windows |
These CA roots are invaluable — so much so that rather than risk issuing directly from them, certificate authorities spin up intermediate roots and sign SSL/TLS leaf (end-user) certificates with those intermediates. Here’s where the chain starts to come in. The Root CA certificate is used to digitally sign the intermediate roots. Those intermediates are used to sign other intermediates or end-user, leaf SSL/TLS certificates.
When a browser receives an SSL/TLS certificate, one of the things it does to check its authenticity is follows the signatures. It looks at the digital signature on the SSL/TLS certificate and follows it back to the intermediate root that signed it. Then it looks at that intermediate’s digital signature and follows it back to the certificate that signed the intermediate. So on and so forth until, eventually, it reaches one of the root CA certificates in its trust store.
If it can’t do this, the certificate chain is oftentimes incomplete, meaning that the browser couldn’t locate one of the intermediates and the SSL/TLS handshake failed. To remedy this, you’re going to need to find and install the missing intermediate certificate. Depending on which CA you purchased your certificate from, they should have their intermediates available on their website.
Expired/Revoked Certificates
While certificate revocation in the current SSL/TLS ecosystem leaves a lot to be desired, there are still some contexts where a browser will see that a certificate has been revoked and will fail a handshake on that basis. More often, it’s as a result of an expired certificate. SSL/TLS certificates are only valid for a set amount of time.
SSL/TLS certificate expiration occurs for a few potential reasons (depending on whom you ask):
- To ensure that validation information stays accurate.
- To proliferate protocol and cipher updates more quickly.
- To eliminate the need for certificate revocation lists (CRLs).
- To combat the possibility of cybercriminals from breaking standard encryption algorithms (although this is virtually impossible without quantum computing).
As of Sept. 1, 2020, max validity for an SSL/TLS certificate is now one year (398 days to be exact). That means you need to be swapping out certificates regularly. If you forgot to before one expired, that’s probably why the SSL/TLS handshake failed. Just get a valid certificate issued and install it — that should solve your problems.
Self-Signed Replacements
On the public internet, a self-signed certificate will return an error 100% of the time if the client hasn’t manually installed your private root in their root store. But, on internal networks self-signed certificates are fairly common. And if you swap them out enough, that can cause problems.
Most browsers will cache certificates so that upon return to a website it makes the handshake go faster. But if you’re generating new certificates at regular intervals, continuously adding all of those newly-generated certificates to the local database is going to cause confusion. Eventually, the browser will struggle with path-building and crash.
In the past, Firefox has struggled with this considerably — to the point where 7-8 certificate re-issues will cause significant latency, and 10 or more can cause the handshake to take upwards of 30 seconds.
SNI-Enabled Servers
This is more of an internal issue that exists between devices, but sometimes a client communicating with a server name indication server when it’s not SNI-enabled can be why the SSL/TLS handshake failed.
The first thing you’ll need to do is identify the host name and the port number of the server in question and make sure it’s SNI-enabled as well as that it’s communicating everything it needs to be. Again, this is usually less of a public-facing issue, but it can be the cause from time to time internally.
What Not to Do – Don’t Reward Bad SSL/TLS Implementations
A lot of the time website owners don’t want to make a change until there’s a problem they can’t ignore. While there are a few client-side fixes for the SSL/TLS handshake failed error, it’s generally going to be a server-side issue.
That means as a regular internet user, your options are limited when it comes to mitigating SSL/TLS handshake errors. The best thing to do is to inform the site owner of the problem and wait for them to fix it. If they don’t, it might be wise just to stop using the website.
- Don’t drop your firewall. You can usually whitelist a website, but don’t drop your firewall. Ever.
- Don’t disable your antivirus. Again, whitelist if possible, but keep it on and updated.
- Don’t connect via HTTP or click through interstitial warnings. This is bad any way you look at it and can result in a lot of issues.
If the website can’t offer a safe browsing experience, you shouldn’t be visiting it. Eliminating the SSL/TLS handshake error isn’t worth jeopardizing your security.
Note: This article on TLS handshake failed errors (SSL handshake failed errors) was originally written by Patrick Nohe on Nov. 14, 2018. It was updated and re-published by Casey Crane as a “rehash” of the content on Sept. 3, 2020.
As always, leave any comments or questions below…
Patrick Nohe
Patrick started his career as a beat reporter and columnist for the Miami Herald before moving into the cybersecurity industry a few years ago. Patrick covers encryption, hashing, browser UI/UX and general cyber security in a way that’s relatable for everyone.
Источник
SSL/TLS Handshake process begins when your browser sends a request to make a secure connection with a web server like Apache. Though sometimes an error occurs, and one of the commonly faced SSL/TLS errors is an “SSL Handshake Failed error,” or also known as “SSL Handshake Failed.”
If you’re not having the right answer to what this SSL error means, then no worries, we’ve got your back. Read further and know what’s this SSL Handshake Failed Error, why it occurs, and how to fix the SSL/TLS Handshake Failed Error.
What Does SSL/TLS Handshake Failed Mean and What Causes It?
The SSL Handshake Failed error occurs when there’s a protocol mismatch. In other words, whenever the client and the server do not have mutual support for the same SSL/TLS version, it shows this SSL/TLS Handshake failed error message.
Once the user sends the secure connection request to the web browser, the browser is expected to send a public key to your computer, which is automatically verified against a list of CAs. And, the computer generates a key and encrypts it with the public key after receiving the certificate.
This SSL/TLS Handshake Failed Error occurs whenever the OS hasn’t granted the read access to the OS, ultimately preventing the complete authentication of the webserver, which indicates that the browser’s connection with the web server is not secure.
Some Reasons That Causes SSL/TLS Handshake Failed Error
| CAUSE | DESCRIPTION | Who Can Fix It? |
|---|---|---|
| Incorrect System Time | The date and time of the client device are not correct. | Client |
| Browser Error | Configuration of a browser is causing the error | Client |
| Main-in-the-middle | The connection is manipulated or intercepted by a third-party. | Client |
| Protocol Mismatch | The server doesn’t support the protocol used by the client. | Server |
| Cipher Suite Mismatch | The server doesn’t support the cipher suite used by the client. | Server |
| SNI-Enabled Server | SNI-enabled servers can’t communicate with the client. | Server |
| Incorrect Certificate |
|
Server |
Now, let’s see each of the reasons for the SSL/TLS Handshake Fail error with the solution in detail.
Here’s the Client-Side Errors and its Solution
Whenever an SSL/TLS Handshake fails, it’s mostly due to certain things going on with the server, website, and the configuration of its installed SSL/TLS.
Presently the culprit is TLS configuration as support for SSL 3.0 is deprecated. However, there’s a distinct possibility that a client-side error can be the reason behind the SSL/TLS Handshake Failed error. And, some of the common ones are like incorrect system time or browser updates.
Let’s see some of the common causes of SSL Handshake fail error in detail.
1. Incorrect System Time
Not always happen, but sometimes the system clock differs from the actual time. Maybe you did it intentionally, accidental change of settings, or any other reason. It’s a fact that SSL/TLS certificates come with a specific validity period, so the date and time of the system is equally important.
So, the solution is to change the system time and date to correct one, if the system clock is not showing the right time and date. But again, there’s no need to change your system time if it’s correct, as it’s likely that the cause of the error is not the System time.
2. Browser Error
It’s not any browser error. But, SSL/TLS Handshake Failed Error is due to some mistakes made by your browser. Sometimes it happens, that your browser might be causing this error due to certain misconfiguration or a plugin can make sure things to work differently, which results in problems while connecting with the legitimate websites. While analyzing what’s exact needs to be fixed is not that easy on your current browser. So, you should try using a different browser.
For instance, if you’re using Google Chrome, then try using Mozilla Firefox or any other such as Apple Safari if OS is Mac or else Microsoft Edge for Windows.
However, if you still face the SSL/TLS Handshake Failed error, even after changing the browser, then the issue is not regarding browser but, most probably, the plugin. To verify whether the error can be solved or not, it’s recommended to disable all your installed plugins and reset your browser settings to default.
3. Man-in-the-Middle
Generally, the MITM (Man-in-the-Middle) attack comes across as a criminal activity that attempts to cause harm or steal user’s information. However, that’s not always the case. Many programs and devices intercept for inspection or any other reason like load balancing, which is sent along to the application server, and this is known as MITM too.
Nevertheless, sometimes issues occur with such devices, which causes the SSL Handshake Failure error. And, the reason could be a network firewall preventing the connection or else configuration on an edge device on the server-side network, which means there’s a possibility that this error could be from the client or server-side depending upon the scenario.
Lastly, if the issue is from the client-side, then you can take a chance of exposing yourself by tweaking the settings on your VPN or antivirus. Though, never drop your antivirus or firewall to connect with a website. And, if the server is causing the issue, then mostly configuration is creating an issue on an edge device.
Here’s the Server-Side Errors and Its Solution
Most of the time, SSL/TLS Handshake failure error is due to server-side issues. Some of them are easy to solve, and some aren’t, and some are not even worth solving at all.
Let’s look at some of the common server-side issues.
1. Protocol Mismatch
It’s one of the errors which can happen due to both the server-side or the client-side, and generally, it’s not worth solving depending upon the circumstance. And when it’s about ciphers and protocols, it’s advised to move forward rather than backward.
For instance:
TLS 1.2 came more than a decade ago, and small segments of websites still fail to support it. Earlier back in March 2018, the final version of TLS 1.3 was published as RFC 8446 by the IETF. And, sites were also advised for adding support for TLS 1.3 at their earliest.
So, if the SSL/TLS Handshake Failure error is due to protocol mismatch, it generally means the client and server do not have mutual support for the same TLS version.
For example:
- The client supports TLS 1.0 and TLS 1.1, whereas the server supports TLS 1.2.
As shown in this example, the TLS protocol is not supported mutually. So, it’s likely that the server won’t support backward versions. Nevertheless, the server shouldn’t fix this as well. In this above example, the client must be recommended to upgrade their browser, or else it must be latest with the latest TLS version supported. Presently all we can suggest is that TLS 1.2 or TLS 1.3 must be used, or else support must be added for it.
2. Cipher Suite Mismatch
A cipher suite is quite similar to the Protocol Mismatch. SSL/TLS isn’t just a single algorithm that handles everything on its own but a combination of numerous algorithms that serves different functions and work with each other to make up SSL/TLS.
Nevertheless, Cipher Suites used by TLS 1.3 has been refined. Earlier, Cipher Suite has algorithms that handled:
- Symmetric Session Key Encryption
- Asymmetric Public Key Encryption
- Signature Hashing
- Key Generation
Different Organizations and Government Agencies have different types of encryption standards that suggest different kinds of cipher suites so clients can have different options while being able to find a mutually acceptable cipher. No doubt, it’s less likely that you get a site that only supports a single cipher suite.
Many times, it happens within a network, if you’re doing SSL bridging, where an edge device receives and decrypts HTTPS traffic and then re-encrypts it to send it to the application server. If the application server and edge device fail to share a mutually supported cipher suite, it will cause errors. Similar to Protocol versions, it’s also advisable for cipher suites, to never go backward but only moves forward.
Lastly, a protocol version or cipher suite is deprecated because there’s a vulnerability in that version. So, going back to the earlier version will only make your connection less secure.
3. Incorrect SSL/TLS Certificate
Many different reasons can make a browser view at an SSL/TLS Certificate as incorrect while preventing it from the successful handshake. Let’s dive into it in the next sub-sections and try to materialize the different issues that result because of a failed handshake due to the technical level.
- Host Name Mismatch: Hostname fails to match with the CN in the certificate.
- Incorrect Certificate Chain: Intermediate missing in the certificate chain.
- Expired/Revoked Certificate: The server presents an untrusted, revoked, or expired SSL/TLS certificate.
- Self-Signed Replacements: Certificate replacements or Internal Networks confuses the path.
4. The hostname is Not Correct
Previously there was a problem with non-WWW and WWW versions of the websites, but it has been reduced radically by the Certificate Authority community allowing one of them to be listed as a SAN free of cost. The simple solution for this issue is to re-issue the certificate or sometimes use a Wildcard certificate.
5. Certificate Chain is Not Correct
The SSL/TLS and PKI trust model generally relies on root programs, which are the collections of trusted CA root certificates that are stored onto your computer system.
Some of the Root program examples:
- Mozilla root program used by Firefox Desktop and Mobile
- Google root program used by Android OS
- Apple root program used by iOS and macOS
- Microsoft root program used by Windows
Nevertheless, CA root programs are invaluable, that it’s not issued directly, but Certificate Authorities make use of intermediate roots for signing SSL/TLS leaf (end-user) certificates. And, here’s the chain comes into play. The Root CA certificate is used for digitally signing the intermediate roots, and those intermediates are further used for signing other intermediate or end-user leaf SSL/TLS certificates.
So, whenever the browser gets an SSL certificate, the browser does one of the things for sure. It will check whether the signatures follow their authenticity. Looks digital name on the SSL/TLS certificate with the Intermediate root that signed it. Then it looks at the digital signature of the intermediate certificate and checks it back to the certificate, which signed the intermediate. This process is continuous like this till it reaches one of the Root CA certificates in its trust store.
Hence, whenever this process remains incomplete due to any reason, means browser failing to locate even one of their intermediate certificates will result in the SSL handshake failed error. The solution is to install the missing intermediate certificate. To find the missing intermediate certificate solution is to go to the CAs website from whom you purchased your SSL/TLS certificate.
6. Revoked/Expired Certificates
Currently, the maximum validity of an SSL/TLS certificate is of 2 years and three months extra (Total 27 months because CAs allow carrying up three months over from previously installed certificate.) In case, if your SSL/TLS certificate gets expired or due to any reason it gets revoked, then it may result in SSL Handshake Failure error. If this is the reason, then get a valid certificate issued and installed.
7. Self-Signed Replacements
If you’ve installed a self-signed SSL/TLS certificate on your website and its live on the public internet, then it will generate an error. To resolve a mistake, get your SSL/TLS certificate issued from the trusted CAs like Sectigo, Comodo, or DigiCert.
8. SNI-Enabled Servers
Generally, it’s an internal issue that happens between devices, but sometimes there are chances of getting an SSL/TLS handshake failed error if a client communicating with a Server Named Indication (SNI) enabled server is not SNI enabled.
To solve this issue, you must identify what’s the hostname and the port number of the server, while verifying whether it’s SNI-enabled and it’s communicating everything it has to.
Summary
Many times, website owners don’t make any necessary changes until they face a problem, which can’t be overlooked. Though some of the client-side fixes for this SSL/TLS handshake failed, the error is there as its mentioned in this article, mostly it’s going to be server-side.
So, if you’re a regular internet user, your options are limited. The best thing you can do as a website visitor is to inform the owner of the website about the SSL/TLS handshake failed to issue and wait for them to fix it. If they don’t take any action onto it, then it’s best to avoid using that website.
Related Articles:
AboutSSL’s Best Stuff
Disclosure: AboutSSL appreciates your continuous support. It helps us tremendously to keep moving in the competitive SSL industry. Here most of the links which direct you to buy any SSL/TLS related service or products earns us a certain percentage of referral commission. Learn More
Hello. I’m trying to connect to a server with https. I have the certificate which is a self signed certificate which is being included in the verify parameter but the result is an error ‘certificate verify failed’ error. I was suspecting it had to do with the certificate being self signed (by Microsoft IIS) but with curl this works.
Thanks in advance!
This is the openssl output:
openssl s_client -showcerts -connect server:44300
CONNECTED(00000003)
depth=0 CN = server
verify error:num=20:unable to get local issuer certificate
verify return:1
depth=0 CN = server
verify error:num=21:unable to verify the first certificate
verify return:1
---
Certificate chain
0 s:/CN=server
i:/CN=server
-----BEGIN CERTIFICATE-----
<certificate data here>
-----END CERTIFICATE-----
---
Server certificate
subject=/CN=server
issuer=/CN=server
---
No client certificate CA names sent
Peer signing digest: SHA1
Server Temp Key: ECDH, P-256, 256 bits
---
SSL handshake has read 1477 bytes and written 431 bytes
---
New, TLSv1/SSLv3, Cipher is ECDHE-RSA-AES256-GCM-SHA384
Server public key is 2048 bit
Secure Renegotiation IS supported
Compression: NONE
Expansion: NONE
No ALPN negotiated
SSL-Session:
Protocol : TLSv1.2
Cipher : ECDHE-RSA-AES256-GCM-SHA384
Session-ID: CC4A000083B1E03B446416C9C0B16CBEAB79949E3CF5C936A309A6F92FA01364
Session-ID-ctx:
Master-Key: 798A570B0EC2A0CBB7C4C4DE6167E7579A92239942D869CD794B8BEBEA6EB5E492394634AD32665A8BB829DE1F3858D2
Key-Arg : None
PSK identity: None
PSK identity hint: None
SRP username: None
Start Time: 1510329948
Timeout : 300 (sec)
Verify return code: 21 (unable to verify the first certificate)
---
Expected Result
I’m expecting, since the certificate is in the verify parameter, that the connection won’t fail. If I try the same with curl outside python it works:
curl https://server:44300 --cacert /usr/share/ca-certificates/server.crt
HTTP/1.1 403 Forbidden
Cache-Control: no-store, no-cache, must-revalidate
Pragma: no-cache
Content-Length: 1158
Content-Type: text/html
Server: Microsoft-IIS/10.0
X-Frame-Options: SAMEORIGIN
P3P: CP=None
Access-Control-Allow-Methods: GET,POST,PUT,DELETE,OPTIONS
Access-Control-Allow-Headers: X-Requested-With,Content-Type
Access-Control-Allow-Credentials: true
Date: Fri, 10 Nov 2017 16:02:26 GMT
(It fails but not because of certificate issues)
Actual Result
Traceback (most recent call last):
File "<string>", line 1, in <module>
File "xxxxx/TestVirtualEnv/local/lib/python2.7/site-packages/requests/api.py", line 72, in get
return request('get', url, params=params, **kwargs)
File "xxxxx/TestVirtualEnv/local/lib/python2.7/site-packages/requests/api.py", line 58, in request
return session.request(method=method, url=url, **kwargs)
File "xxxxx/TestVirtualEnv/local/lib/python2.7/site-packages/requests/sessions.py", line 508, in request
resp = self.send(prep, **send_kwargs)
File "xxxxx/TestVirtualEnv/local/lib/python2.7/site-packages/requests/sessions.py", line 618, in send
r = adapter.send(request, **kwargs)
File "xxxxx/TestVirtualEnv/local/lib/python2.7/site-packages/requests/adapters.py", line 506, in send
raise SSLError(e, request=request)
requests.exceptions.SSLError: HTTPSConnectionPool(host='nlybstqvp4nb75n.code1.emi.philips.com', port=44300): Max retries exceeded with url: / (Caused by SSLError(SSLError("bad handshake: Error([('SSL routines', 'tls_process_server_certificate', 'certificate verify failed')],)",),))
Reproduction Steps
import requests requests.get('https://server:44300', verify='/usr/share/ca-certificates/server.crt')
System Information
$ python -m requests.help
{
"chardet": {
"version": "3.0.4"
},
"cryptography": {
"version": "2.1.3"
},
"idna": {
"version": "2.6"
},
"implementation": {
"name": "CPython",
"version": "2.7.12"
},
"platform": {
"release": "4.10.0-38-generic",
"system": "Linux"
},
"pyOpenSSL": {
"openssl_version": "1010007f",
"version": "17.3.0"
},
"requests": {
"version": "2.18.4"
},
"system_ssl": {
"version": "1000207f"
},
"urllib3": {
"version": "1.22"
},
"using_pyopenssl": true
}
This command is only available on Requests v2.16.4 and greater. Otherwise,
please provide some basic information about your system (Python version,
operating system, &c).
Open
Issue created Jul 07, 2020 by
Jira Integration with self signed cert throws unspecified certificate verification error even openssl works
Summary
We self host our JIRA and GitLab (Docker).
We want to integrate the JIRA Features in Gitlab like descripted here: https://docs.gitlab.com/ee/user/project/integrations/jira.html
We entered a valid administrator account in username / password-fields.
We entered a valid url (https://jira.DOMAIN.int:8443).
We looked for the right transition ID and entered it (71 in our case).
Error: Test failed. Save anyway.
The integration_json.log shows:
SSL_connect returned=1 errno=0 state=error: certificate verify failed (unspecified certificate verification error)
What we have done so far?
- entered the correct host in /etc/hosts
- download the self signed certificat with Chrome in 3 files (main certificat and 2 roots certificat)
- Run reconfigure in gitlab and see the output, that all 3 files are recognized in Recipe: gitlab::add_trusted_certs
- Look in the /opt/gitlab/embedded/ssl/certs and see 3 correct system links to the 3 files in /etc/gitlab/trusted-certs
- Run OpenSSL from Gitlab: Connected!
*root@c9cab22e6481:/etc/gitlab# echo | /opt/gitlab/embedded/bin/openssl s_client -connect jira.xxx.int:8443
CONNECTED(00000003)
Can’t use SSL_get_servername
depth=0 C = DE, ST = RLP, L = KO, O = xxx AG, OU = GOE, CN = JIRA
verify return:1
Certificate chain
0 s:C = DE, ST = RLP, L = KO, O = xxx AG, OU = GOE, CN = JIRA
i:C = DE, ST = RLP, L = KO, O = xxx AG, OU = GOE, CN = JIRA
Server certificate
——BEGIN CERTIFICATE——
MIIDVTCCAj2gAwIBAgIEU135NjANBgkqhkiG9w0BAQsFADBbMQswCQYDVQQGEwJE
RTEMMAoGA1UECBMDUkxQMQswCQYDVQQHEwJLTzEUMBIGA1UEChMLR09FUkxJVFog
QUcxDDAKBgNVBAsTA0dPRTENMAsGA1UEAxMESklSQTAeFw0xODA3MjMxMDU0NTRa
Fw0yMjA4MzExMDU0NTRaMFsxCzAJBgNVBAYTAkRFMQwwCgYDVQQIEwNSTFAxCzAJ
BgNVBAcTAktPMRQwEgYDVQQKEwtHT0VSTElUWiBBRzEMMAoGA1UECxMDR09FMQ0w
CwYDVQQDEwRKSVJBMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAjeh6
g6I5ErXj6ZaIf9f+RIHZRbDDjRxk1APXWN914iO6EA+l/tdGvSKY0e4WJu16hOPn
klUYq+iaMKVE9LTezu7W1LZ2r+QiDMus7GV3z+x1wq3UZ8m/Mxnr4iiz6WIemWEY
Gdifmsa6BVicai/RZs3sQeVpuO3qovKbKV1DxbJ9TX+g2OFrEYqwE6mZiRR23/kp
IzOeNOlhWtVYyjRXpIMmyGpWE+/H3ijVIMKBe2UDb59ORsxILGIk9llfDBWw7e1h
Zx7MfCwQ5tb5B75a1He4ROAolymYigszgU+lEwmFcM+cu58gfyU99eF/QaLESBSS
J3ZMP5+6xt2s3bCxEQIDAQABoyEwHzAdBgNVHQ4EFgQU3SRIHlvXyp+CDR5SCNww
ramoI8kwDQYJKoZIhvcNAQELBQADggEBAB/mB7rys9JHZdvxzXI9z068MjXVifcK
jif2GoSV3LC1PQXET4OxcpLdEVCuZP9KFKOQBYriblrlxT7uXoipqZ0VNN7EgYNv
ivEZcKV6+JtkASCJMD1Tv1iWqoKZeJHgu2EJVQUnL3ZOsl4u57awYAaou8u25O1s
ZtRe4V6GKdgetsp98qMK0B0YLM2+Ot8Nb2sWE6m+gDbMizRblny9hbv9znJbNSWE
WgDmPK+ZKJQyumXZU+oJ5bvmPfA79H69mqytHRl42d7ql9yQlscuBYGVHoxevOKk
Z94kd889sAjF2dZR7nc2JN4rV1qUNDB4tHV+o0RTmw9hBMg+E6sPYa4=
——END CERTIFICATE——
subject=C = DE, ST = RLP, L = KO, O = xxx AG, OU = GOE, CN = JIRA
issuer=C = DE, ST = RLP, L = KO, O = xxx AG, OU = GOE, CN = JIRA
No client certificate CA names sent
Peer signing digest: SHA256
Peer signature type: RSA
Server Temp Key: ECDH, P-256, 256 bits
SSL handshake has read 1345 bytes and written 419 bytes
Verification: OK
New, TLSv1.2, Cipher is ECDHE-RSA-AES256-GCM-SHA384
Server public key is 2048 bit
Secure Renegotiation IS supported
No ALPN negotiated
SSL-Session:
Protocol : TLSv1.2
Cipher : ECDHE-RSA-AES256-GCM-SHA384
Session-ID: 5F0445083881A3E4B6DE86A7C1238D35F05BFBB914FD9F8E6F463C4CA87BFF03
Session-ID-ctx:
Master-Key: 5CF9A153121058D6E1D9D3D0D63F8A17BB813ED22464FFA8A35398F8069D34580359299E6EA80E08413D9B2524714B7C
PSK identity: None
PSK identity hint: None
SRP username: None
Start Time: 1594115336
Timeout : 7200 (sec)
Verify return code: 0 (ok)
Extended master secret: yes
DONE*
- Run openssl x509 -in /etc/gitlab/trusted-certs/certificat.cer -text -noout
Certificate:
Data:
Version: 3 (0x2)
Serial Number: 1398667574 (0x535df936)
Signature Algorithm: sha256WithRSAEncryption
Issuer: C = DE, ST = RLP, L = KO, O = xxx AG, OU = GOE, CN = JIRA
Validity
Not Before: Jul 23 10:54:54 2018 GMT
Not After : Aug 31 10:54:54 2022 GMT
Subject: C = DE, ST = RLP, L = KO, O = xxx AG, OU = GOE, CN = JIRA
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public-Key: (2048 bit)
Modulus:
00:8d:e8:7a:83:a2:39:12:b5:e3:e9:96:88:7f:d7:
fe:44:81:d9:45:b0:c3:8d:1c:64:d4:03:d7:58:df:
75:e2:23:ba:10:0f:a5:fe:d7:46:bd:22:98:d1:ee:
16:26:ed:7a:84:e3:e7:92:55:18:ab:e8:9a:30:a5:
44:f4:b4:de:ce:ee:d6:d4:b6:76:af:e4:22:0c:cb:
ac:ec:65:77:cf:ec:75:c2:ad:d4:67:c9:bf:33:19:
eb:e2:28:b3:e9:62:1e:99:61:18:19:d8:9f:9a:c6:
ba:05:58:9c:6a:2f:d1:66:cd:ec:41:e5:69:b8:ed:
ea:a2:f2:9b:29:5d:43:c5:b2:7d:4d:7f:a0:d8:e1:
6b:11:8a:b0:13:a9:99:89:14:76:df:f9:29:23:33:
9e:34:e9:61:5a:d5:58:ca:34:57:a4:83:26:c8:6a:
56:13:ef:c7:de:28:d5:20:c2:81:7b:65:03:6f:9f:
4e:46:cc:48:2c:62:24:f6:59:5f:0c:15:b0:ed:ed:
61:67:1e:cc:7c:2c:10:e6:d6:f9:07:be:5a:d4:77:
b8:44:e0:28:97:29:98:8a:0b:33:81:4f:a5:13:09:
85:70:cf:9c:bb:9f:20:7f:25:3d:f5:e1:7f:41:a2:
c4:48:14:92:27:76:4c:3f:9f:ba:c6:dd:ac:dd:b0:
b1:11
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Subject Key Identifier:
DD:24:48:1E:5B:D7:CA:9F:82:0D:1E:52:08:DC:30:AD:A9:A8:23:C9
Signature Algorithm: sha256WithRSAEncryption
1f:e6:07:ba:f2:b3:d2:47:65:db:f1:cd:72:3d:cf:4e:bc:32:
35:d5:89:f7:0a:8e:27:f6:1a:84:95:dc:b0:b5:3d:05:c4:4f:
83:b1:72:92:dd:11:50:ae:64:ff:4a:14:a3:90:05:8a:e2:6e:
5a:e5:c5:3e:ee:5e:88:a9:a9:9d:15:34:de:c4:81:83:6f:8a:
f1:19:70:a5:7a:f8:9b:64:01:20:89:30:3d:53:bf:58:96:aa:
82:99:78:91:e0:bb:61:09:55:05:27:2f:76:4e:b2:5e:2e:e7:
b6:b0:60:06:a8:bb:cb:b6:e4:ed:6c:66:d4:5e:e1:5e:86:29:
d8:1e:b6:ca:7d:f2:a3:0a:d0:1d:18:2c:cd:be:3a:df:0d:6f:
6b:16:13:a9:be:80:36:cc:8b:34:5b:96:7c:bd:85:bb:fd:ce:
72:5b:35:25:84:5a:00:e6:3c:af:99:28:94:32:ba:65:d9:53:
ea:09:e5:bb:e6:3d:f0:3b:f4:7e:bd:9a:ac:ad:1d:19:78:d9:
de:ea:97:dc:90:96:c7:2e:05:81:95:1e:8c:5e:bc:e2:a4:67:
de:24:77:cf:3d:b0:08:c5:d9:d6:51:ee:77:36:24:de:2b:57:
5a:94:34:30:78:b4:75:7e:a3:44:53:9b:0f:61:04:c8:3e:13:
ab:0f:61:ae
- Flush trusted-certs-directory-hash with rm /var/opt/gitlab/trusted-certs-directory-hash
Steps to reproduce
See Summary
Example Project
Self hosted, cant to a example
What is the current bug behavior?
«Test failed» in the GUI.
Error in the integration_json.log:
{«severity»:»ERROR»,»time»:»2020-07-07T09:34:38.352Z»,»correlation_id»:»XRqyN3nTWLa»,»service_class»:»JiraService»,»project_id»:16,»project_path»:»vivavis-mgt/vivavis.platform.management»,»message»:»Error sending message»,»client_url»:»https://jira.DOMAIN.int:8443″,»error»:»SSL_connect returned=1 errno=0 state=error: certificate verify failed (unspecified certificate verification error)»}
What is the expected correct behavior?
Working as intendet 
Relevant logs and/or screenshots
Integrations_json.log:
{«severity»:»ERROR»,»time»:»2020-07-07T09:34:38.352Z»,»correlation_id»:»XRqyN3nTWLa»,»service_class»:»JiraService»,»project_id»:16,»project_path»:»vivavis-mgt/vivavis.platform.management»,»message»:»Error sending message»,»client_url»:»https://jira:8443″,»error»:»SSL_connect returned=1 errno=0 state=error: certificate verify failed (unspecified certificate verification error)»}
Output of checks
(If you are reporting a bug on GitLab.com, write: This bug happens on GitLab.com)
Results of GitLab environment info
System information
System:
Proxy: no
Current User: git
Using RVM: no
Ruby Version: 2.6.6p146
Gem Version: 2.7.10
Bundler Version:1.17.3
Rake Version: 12.3.3
Redis Version: 5.0.9
Git Version: 2.27.0
Sidekiq Version:5.2.7
Go Version: unknown
Results of GitLab application Check
Checking GitLab subtasks …
Checking GitLab Shell …
GitLab Shell: … GitLab Shell version >= 13.3.0 ? … OK (13.3.0)
Running /opt/gitlab/embedded/service/gitlab-shell/bin/check
Internal API available: OK
Redis available via internal API: OK
gitlab-shell self-check successful
Checking GitLab Shell … Finished
Checking Gitaly …
Gitaly: … default … OK
Checking Gitaly … Finished
Checking Sidekiq …
Sidekiq: … Running? … yes
Number of Sidekiq processes … 1
Checking Sidekiq … Finished
Checking Incoming Email …
Incoming Email: … Reply by email is disabled in config/gitlab.yml
Checking Incoming Email … Finished
Checking LDAP …
LDAP: … LDAP is disabled in config/gitlab.yml
Checking LDAP … Finished
Checking GitLab App …
Git configured correctly? … yes
Database config exists? … yes
All migrations up? … yes
Database contains orphaned GroupMembers? … no
GitLab config exists? … yes
GitLab config up to date? … yes
Log directory writable? … yes
Tmp directory writable? … yes
Uploads directory exists? … yes
Uploads directory has correct permissions? … yes
Uploads directory tmp has correct permissions? … yes
Init script exists? … skipped (omnibus-gitlab has no init script)
Init script up-to-date? … skipped (omnibus-gitlab has no init script)
Projects have namespace: …
11/1 … yes
5/2 … yes
8/3 … yes
8/4 … yes
8/5 … yes
5/6 … yes
5/7 … yes
5/8 … yes
12/9 … yes
11/12 … yes
11/13 … yes
11/14 … yes
5/15 … yes
12/16 … yes
13/19 … yes
14/20 … yes
8/21 … yes
12/22 … yes
17/24 … yes
8/25 … yes
Redis version >= 4.0.0? … yes
Ruby version >= 2.5.3 ? … yes (2.6.6)
Git version >= 2.22.0 ? … yes (2.27.0)
Git user has default SSH configuration? … yes
Active users: … 6
Is authorized keys file accessible? … yes
GitLab configured to store new projects in hashed storage? … yes
All projects are in hashed storage? … yes
Elasticsearch version 5.6 — 6.x? … skipped (elasticsearch is disabled)
Checking GitLab App … Finished
Checking GitLab subtasks … Finished
Edited Jul 07, 2020 by Rene Koch
I will tell you my situation step by step and ask me any necessary questions and help me to fix hmail certificate issue.
First of all :
1-
i am using a windows server 2008 — r2
2-
latest hmail server downloaded from it’s web site
3-
a little VPS using with static ip
4-
no extra smtp server
5-
firewall is off
6-
smtp ports -> 25, 587 — 465 (ssl) are open | imap ports -> 143 — 993(ssl) are open
7-
How did you create your certificate?
I installed openSSL latest x64 no-light version on VPS.
And here is the cmd commands on server machine (not local) :
Way 1 : from hmail web site (Self Signed Certificate)
openssl genrsa -des3 -out your_certificatedomain_com.key 2048
openssl rsa -in your_certificatedomain_com.key -out your_certificatedomain_com.key
openssl req -new -key your_certificatedomain_com.key -out your_certificatedomain_com.csr
US
New York
Rochester
Almas Ltd
Security
mydomain.com
info@mydomain.com
Blank
Blank
openssl x509 -req -days 365 -in your_certificatedomain_com.csr -signkey your_certificatedomain_com.key -out your_certificatedomain_com.crt
openssl s_client -connect smtp.mydomain.com:465
8-
How did you test your created certificate?
Here is the command and it’s result :
openssl s_client -connect smtp.mydomain.com:465 >> Log.txt
CONNECTED(00000110)
---
Certificate chain
0 s:/C=US/ST=New York/L=Rochester/O=Almas Ltd/OU=Security/CN=mydomain.com/emailAddress=info@mydomain.com
i:/C=US/ST=New York/L=Rochester/O=Almas Ltd/OU=Security/CN=mydomain.com/emailAddress=info@mydomain.com
---
Server certificate
-----BEGIN CERTIFICATE-----
MIIDsjCCApoCCQDupf4WHA0lRTANBgkqhkiG9w0BAQsFADCBmjELMAkGA1UEBhMC
VVMxETAPBgNVBAgMCE5ldyBZb3JrMRIwEAYDVQQHDAlSb2NoZXN0ZXIxEjAQBgNV
BAoMCUFsbWFzIEx0ZDERMA8GA1UECwwIU2VjdXJpdHkxGDAWBgNVBAMMD2dtYWls
YWNjb3VudC5ncTEjMCEGCSqGSIb3DQEJARYUaW5mb0BnbWFpbGFjY291bnQuZ3Ew
HhcNMTYwMTA1MTQyMDUzWhcNMTcwMTA0MTQyMDUzWjCBmjELMAkGA1UEBhMCVVMx
ETAPBgNVBAgMCE5ldyBZb3JrMRIwEAYDVQQHDAlSb2NoZXN0ZXIxEjAQBgNVBAoM
CUFsbWFzIEx0ZDERMA8GA1UECwwIU2VjdXJpdHkxGDAWBgNVBAMMD2dtYWlsYWNj
b3VudC5ncTEjMCEGCSqGSIb3DQEJARYUaW5mb0BnbWFpbGFjY291bnQuZ3EwggEi
MA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQCuPbmpoK0I1J/qPYC+G2CnVtY7
FxiXO6XUR2b1pVCvp2Cmo7dAbJ61mCo8SWwi7kRulJNnsqHpkD3EglrUmsjLIVMq
xsmqzwYzehV1+ydhVP/4b2DwIRnzojUgvklSY8wd07btOaUJF4/QBydu6IIRjngL
HU6PwxKP1CtBiIkbmCvnvrjElikpKAEmtZg0cIY5Z7mbaYAGN/VMoCToPSzmD6Ys
rrO0LD7p+334C59z/xI9O9o+PhspkN8xTuajycPFqudH9ZhuEzknUA82m8OF2ymZ
JW1Cu9crgC3xs73i4w/kl0k0SVD/yerEoJIOsdvtikHDFId/1EgKyMmpjJC/AgMB
AAEwDQYJKoZIhvcNAQELBQADggEBAFmLO2qT4TzlYY+MJ3+JdtmmAnj28vzVuaug
Q0vJNa8WlC9qPmK8jPMl2MNan+6GvC3w7EpkBZ6T+5ofXZaqJg72ITHMPHZdYcga
e0T6l1CxcptQeLwZww0ZEi4HS845zQhuE+aGbrSYCfHRIhFcPIfOGuHNEM0yBZeF
tMpnu+0LRmhm2A0o0S6OSVkdYnywHYrZnyPunD6bWart+NFwGZ/Vk6cW0MQW1mB5
v/uwI2tpE/QB1n263ui0o8G/WhGE7XkDmj61kfCWh77akeIowKaMYDr6+/lnsupK
+1QoMJ1KjQr5GwPPHsQmE88IaaH+cRCy0FqglV8KliFQHECgIBY=
-----END CERTIFICATE-----
subject=/C=US/ST=New York/L=Rochester/O=Almas Ltd/OU=Security/CN=mydomain.com/emailAddress=info@mydomain.com
issuer=/C=US/ST=New York/L=Rochester/O=Almas Ltd/OU=Security/CN=mydomain.com/emailAddress=info@mydomain.com
---
No client certificate CA names sent
Peer signing digest: SHA512
Server Temp Key: ECDH, P-256, 256 bits
---
SSL handshake has read 1609 bytes and written 443 bytes
---
New, TLSv1/SSLv3, Cipher is ECDHE-RSA-AES256-GCM-SHA384
Server public key is 2048 bit
Secure Renegotiation IS supported
Compression: NONE
Expansion: NONE
No ALPN negotiated
SSL-Session:
Protocol : TLSv1.2
Cipher : ECDHE-RSA-AES256-GCM-SHA384
Session-ID: 93C68F70C836320E98476E0578BAA1BC30CEB69A2496910D80A612DAFE812AD6
Session-ID-ctx:
Master-Key: A181E823F19A24D3E116B00807AED917E925539DB001B3D0B5B881C656F3B1861501857EFB3E160800F3BB20E9F077E9
Key-Arg : None
PSK identity: None
PSK identity hint: None
SRP username: None
TLS session ticket lifetime hint: 300 (seconds)
TLS session ticket:
0000 - 8d 7d 83 3f 45 70 db dd-ea ce 81 6f 4b 4e bb cf .}.?Ep.....oKN..
0010 - 28 8b 65 e6 1c 62 03 4c-79 ad 8b 00 76 2b a4 24 (.e..b.Ly...v+.$
0020 - dd 8d 7a f8 2c 28 3c 2c-24 8f c8 6d d6 29 ea c8 ..z.,(<,$..m.)..
0030 - b8 bc cc db 23 02 83 ac-a6 f0 2b 68 64 9d e0 85 ....#.....+hd...
0040 - a5 e6 09 ab ad af e6 74-e0 94 8d b4 a0 fc 79 3d .......t......y=
0050 - d8 3c d2 1f 49 8b 1f 06-da c0 63 59 46 cb 21 5b .<..I.....cYF.

 SSL/TLS Handshake Failed — Client Errors
SSL/TLS Handshake Failed — Client Errors
 Protocol Mismatch
Protocol Mismatch Cipher Suite Mismatch
Cipher Suite Mismatch