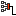ERROR: CN=server, require nsCertType=SERVER
Thu Jul 19 22:08:53 2018 us=496430 VERIFY nsCertType ERROR: CN=server, require nsCertType=SERVER
Thu Jul 19 22:08:53 2018 us=496430 OpenSSL: error:14090086:SSL routines:ssl3_get_server_certificate:certificate verify failed
Thu Jul 19 22:08:53 2018 us=496430 TLS_ERROR: BIO read tls_read_plaintext error
Thu Jul 19 22:08:53 2018 us=496430 TLS Error: TLS object -> incoming plaintext read error
Thu Jul 19 22:08:53 2018 us=496430 TLS Error: TLS handshake failed
Thu Jul 19 22:08:53 2018 us=496430 Fatal TLS error (check_tls_errors_co), restarting
Thu Jul 19 22:08:53 2018 us=496430 TCP/UDP: Closing socket
Thu Jul 19 22:08:53 2018 us=496430 SIGUSR1[soft,tls-error] received, process restarting
Thu Jul 19 22:08:53 2018 us=496430 Restart pause, 5 second(s)
Thu Jul 19 22:08:58 2018 us=513046 WARNING: —ns-cert-type is DEPRECATED. Use —remote-cert-tls instead.
Thu Jul 19 22:08:58 2018 us=513046 Re-using SSL/TLS context
Thu Jul 19 22:08:58 2018 us=513046 Control Channel MTU parms [ L:1591 D:1210 EF:40 EB:0 ET:0 EL:3 ]
Thu Jul 19 22:08:58 2018 us=513046 Socket Buffers: R=[65536->65536] S=[65536->65536]
Thu Jul 19 22:08:58 2018 us=513046 Data Channel MTU parms [ L:1591 D:1450 EF:59 EB:12 ET:32 EL:3 ]
Thu Jul 19 22:08:58 2018 us=513046 Local Options String: ‘V4,dev-type tap,link-mtu 1591,tun-mtu 1532,proto TCPv4_CLIENT,cipher AES-256-CBC,auth SHA1,keysize 256,key-method 2,tls-client’
Thu Jul 19 22:08:58 2018 us=513046 Expected Remote Options String: ‘V4,dev-type tap,link-mtu 1591,tun-mtu 1532,proto TCPv4_SERVER,cipher AES-256-CBC,auth SHA1,keysize 256,key-method 2,tls-server’
Thu Jul 19 22:08:58 2018 us=513046 Local Options hash (VER=V4): ‘b60e7885’
Thu Jul 19 22:08:58 2018 us=513046 Expected Remote Options hash (VER=V4): ‘fbeb66e6’
Thu Jul 19 22:08:58 2018 us=513046 Attempting to establish TCP connection with [AF_INET]118.70.183.88:1194 [nonblock]
Thu Jul 19 22:08:59 2018 us=527226 TCP connection established with [AF_INET]118.70.183.88:1194
Thu Jul 19 22:08:59 2018 us=527226 TCPv4_CLIENT link local: [undef]
Thu Jul 19 22:08:59 2018 us=527226 TCPv4_CLIENT link remote: [AF_INET]118.70.183.88:1194
Thu Jul 19 22:08:59 2018 us=527226 TLS: Initial packet from [AF_INET]118.70.183.88:1194, sid=e578598e f6cbf22e
Thu Jul 19 22:09:00 2018 us=199170 VERIFY OK: depth=1, CN=myCA
Thu Jul 19 22:09:00 2018 us=199170 VERIFY nsCertType ERROR: CN=server, require nsCertType=SERVER
Thu Jul 19 22:09:00 2018 us=199170 OpenSSL: error:14090086:SSL routines:ssl3_get_server_certificate:certificate verify failed
Thu Jul 19 22:09:00 2018 us=214709 TLS_ERROR: BIO read tls_read_plaintext error
Thu Jul 19 22:09:00 2018 us=214709 TLS Error: TLS object -> incoming plaintext read error
Thu Jul 19 22:09:00 2018 us=214709 TLS Error: TLS handshake failed
Thu Jul 19 22:09:00 2018 us=214709 Fatal TLS error (check_tls_errors_co), restarting
Thu Jul 19 22:09:00 2018 us=214709 TCP/UDP: Closing socket
Thu Jul 19 22:09:00 2018 us=214709 SIGUSR1[soft,tls-error] received, process restarting
Thu Jul 19 22:09:00 2018 us=214709 Restart pause, 5 second(s)
Содержание
- OpenVPN Support Forum
- Zeroshell 3.0 router: VERIFY nsCertType ERROR
- Zeroshell 3.0 router: VERIFY nsCertType ERROR
- Re: VERIFY nsCertType ERROR
- Re: VERIFY nsCertType ERROR
- Re: VERIFY nsCertType ERROR
- Re: VERIFY nsCertType ERROR
- Re: VERIFY nsCertType ERROR
- Re: VERIFY nsCertType ERROR
- Re: VERIFY nsCertType ERROR
- Re: VERIFY nsCertType ERROR
- Re: VERIFY nsCertType ERROR
- Re: VERIFY nsCertType ERROR
- Re: VERIFY nsCertType ERROR
- Re: Zeroshell 3.0 router: VERIFY nsCertType ERROR
- OpenVPN Support Forum
- [Solved] OpenVPN on Asus RT-AC68U nsCertType
- [Solved] OpenVPN on Asus RT-AC68U nsCertType
- OpenVPN Support Forum
- Unable to start OpenVPN Server
- Unable to start OpenVPN Server
- Re: Unable to start OpenVPN Server
- Re: Unable to start OpenVPN Server
- Re: Unable to start OpenVPN Server
- Re: Unable to start OpenVPN Server
- Re: Unable to start OpenVPN Server
- OpenVPN Support Forum
- nsCertType ERROR (TLS Error)
- nsCertType ERROR (TLS Error)
- forum.lissyara.su
- OpenVPN не заводиться 🙁
- OpenVPN не заводиться 🙁
- Услуги хостинговой компании Host-Food.ru
- Re: OpenVPN не заводиться 🙁
- Re: OpenVPN не заводиться 🙁
OpenVPN Support Forum
Community Support Forum
Zeroshell 3.0 router: VERIFY nsCertType ERROR
Zeroshell 3.0 router: VERIFY nsCertType ERROR
Post by nulluse » Sat Apr 16, 2016 6:13 pm
We followed the instructions at http://www.zeroshell.org/openvpn-client/ and downloaded the sample config file http://www.zeroshell.org/download/zeroshell.ovpn and exported CA.pem file from the router login page. The user placed the config file and CA.pem into the
What are we doing wrong?
Re: VERIFY nsCertType ERROR
Post by nulluse » Mon Apr 18, 2016 7:54 pm
Re: VERIFY nsCertType ERROR
Post by Traffic » Mon Apr 18, 2016 8:23 pm
I would say that you have not created your server certificate correctly.
Of course .. you have only posted 1 of 4 requirements ..
Please see the Forum rules (top of this page)
Re: VERIFY nsCertType ERROR
Post by nulluse » Mon Apr 18, 2016 9:00 pm
Sorry, this is too cryptic for me: I posted 1 out of 4. what exactly?
If you are referring to the config file, than it is the one I linked above. The only difference of the actual file used is the external IP of the router box.
If you are referring to out certificate, than this is exactly what I am asking: what specifically in the certificate should I look at? The certificate is large and has lots of info. Posting it entirely for the world to see would defeat the purpose of VPN as anyone would be able to connect using that cert. So I have to post something from the cert, but don’t know which parts. Do you agree?
You have pointed me at a 41 page document which I may not be able to follow, as it talks about running command-line tools, whereas in Zeroshell I only have a link on the log in page to download a CA.pem file that is generated when Zeroshell starts up for the 1st time.
Re: VERIFY nsCertType ERROR
Post by Traffic » Mon Apr 18, 2016 11:19 pm
Traffic wrote: Of course .. you have only posted 1 of 4 requirements ..
Please see the Forum rules (top of this page)
The rules are there to save this sort of banta ..
I suggest you read the EasyRSA README (included with easyrsa)
Re: VERIFY nsCertType ERROR
Post by nulluse » Mon Apr 18, 2016 11:38 pm
Traffic wrote: Of course .. you have only posted 1 of 4 requirements ..
Please see the Forum rules (top of this page)
The rules are there to save this sort of banta ..
I suggest you read the EasyRSA README (included with easyrsa)
Re: VERIFY nsCertType ERROR
Post by Traffic » Mon Apr 18, 2016 11:48 pm
Re: VERIFY nsCertType ERROR
Post by Traffic » Tue Apr 19, 2016 12:30 pm
There are two ways to designate a certificate as a server:
- nscerttype server (deprecated)
- remote-cert-tls server
There may be more but these are documented by EasyRSA .. so read the README/vars file for EasyRSA
I suspect you are using the wrong designation in your config. (which you have not posted)
Re: VERIFY nsCertType ERROR
Post by nulluse » Tue Apr 19, 2016 1:26 pm
Traffic wrote: There are two ways to designate a certificate as a server:
- nscerttype server (deprecated)
- remote-cert-tls server
There may be more but these are documented by EasyRSA .. so read the README/vars file for EasyRSA
I suspect you are using the wrong designation in your config. (which you have not posted)
Re: VERIFY nsCertType ERROR
Post by Traffic » Tue Apr 19, 2016 1:49 pm
Sorry .. I am not debugging Zeroshell tutorials .. I suggest you ask on Zeroshell Forum ..
Re: VERIFY nsCertType ERROR
Post by nulluse » Tue Apr 19, 2016 1:50 pm
Re: VERIFY nsCertType ERROR
Post by nulluse » Tue Apr 19, 2016 1:52 pm
Traffic wrote: Sorry .. I am not debugging Zeroshell tutorials .. I suggest you ask on Zeroshell Forum ..
Re: Zeroshell 3.0 router: VERIFY nsCertType ERROR
Post by Traffic » Tue Apr 19, 2016 1:59 pm
Источник
OpenVPN Support Forum
Community Support Forum
[Solved] OpenVPN on Asus RT-AC68U nsCertType
[Solved] OpenVPN on Asus RT-AC68U nsCertType
Post by chris_vpn » Wed Jan 18, 2017 6:52 pm
I downloaded EasyRSA-3.0.0-rc2 and have done the following
easyrsa init-pki
easyrsa build-ca — left common name default [Easy-RSA CA]
easyrsa build-server-full server nopass
easyrsa build-client-full client1
easyrsa gen-dh
On the router advanced page I paste in the CA.CRT / Server.CRt / Server.key and dh.pem and apply changes and the system log indicate that the openVPN is running.
Jan 18 11:43:07 rc_service: httpd 453:notify_rc restart_openvpnd;restart_chpass;restart_samba
Jan 18 11:43:10 openvpn[24720]: OpenVPN 2.3.2 arm-unknown-linux-gnu [SSL (OpenSSL)] [LZO] [EPOLL] [eurephia] [MH] [IPv6] built on Nov 18 2016
Jan 18 11:43:10 openvpn[24720]: PLUGIN_INIT: POST /usr/lib/openvpn-plugin-auth-pam.so ‘[/usr/lib/openvpn-plugin-auth-pam.so] [openvpn]’ intercepted=PLUGIN_AUTH_USER_PASS_VERIFY
Jan 18 11:43:10 openvpn[24720]: Diffie-Hellman initialized with 2048 bit key
Jan 18 11:43:10 openvpn[24720]: Socket Buffers: R=[122880->131072] S=[122880->131072]
Jan 18 11:43:10 openvpn[24720]: TUN/TAP device tun21 opened
Jan 18 11:43:10 openvpn[24720]: TUN/TAP TX queue length set to 100
Jan 18 11:43:10 openvpn[24720]: do_ifconfig, tt->ipv6=0, tt->did_ifconfig_ipv6_setup=0
Jan 18 11:43:10 openvpn[24720]: /sbin/ifconfig tun21 10.8.0.1 pointopoint 10.8.0.2 mtu 1500
Jan 18 11:43:10 openvpn[24720]: /sbin/route add -net 10.8.0.0 netmask 255.255.255.0 gw 10.8.0.2
Jan 18 11:43:10 openvpn[24726]: UDPv4 link local (bound): [undef]
Jan 18 11:43:10 openvpn[24726]: UDPv4 link remote: [undef]
Jan 18 11:43:10 openvpn[24726]: MULTI: multi_init called, r=256 v=256
Jan 18 11:43:10 openvpn[24726]: IFCONFIG POOL: base=10.8.0.4 size=62, ipv6=0
Jan 18 11:43:10 openvpn[24726]: Initialization Sequence Completed
I then export a ovpn file from the router itself and I have tried various combination on my phone
I filled in the client cert and client key info in the OVPN file and imported to OpenVPN connect but everytime I attempt to connect I get this error
OpenVPN server certificate verification failed : PolarSSL:SSL read error : X509 — Certificate verification failed, e.g. CRL, CA or signature check failed.
I also tried OpenVPN for android and here I have attempted the OVPN file from above, and I have also tried to directly in the setup for my connection to point at the CRT/Key files on my phone. Here I get a slightly different error
2017-01-18 13:32:09 VERIFY OK: depth=1, CN=Easy-RSA CA
2017-01-18 13:32:09 VERIFY nsCertType ERROR: CN=server, require nsCertType=SERVER
2017-01-18 13:32:09 OpenSSL: error:14090086:SSL routines:ssl3_get_server_certificate:certificate verify failed
Источник
OpenVPN Support Forum
Community Support Forum
Unable to start OpenVPN Server
Unable to start OpenVPN Server
Post by beaksdale » Sat Apr 30, 2016 1:14 pm
Re: Unable to start OpenVPN Server
Post by Traffic » Sat Apr 30, 2016 4:53 pm
Re: Unable to start OpenVPN Server
Post by beaksdale » Sun May 01, 2016 5:40 pm
Re: Unable to start OpenVPN Server
Post by Traffic » Mon May 02, 2016 12:19 pm
Using EasyRSA protects certificates with a password by default.
The easiest solution for you would be to recreate your server and client certs with the nopass option.
Re: Unable to start OpenVPN Server
Post by beaksdale » Mon May 09, 2016 5:26 pm
Re: Unable to start OpenVPN Server
Post by Traffic » Mon May 09, 2016 5:42 pm
By default, EasyRSA no longer uses nsCertType .. so — ns-cert-type server should not be used in the client config.
Instead, if you use EasyRSA.3x for your PKI then use — remote-cert-tls server in your client config.
Источник
OpenVPN Support Forum
Community Support Forum
nsCertType ERROR (TLS Error)
nsCertType ERROR (TLS Error)
Post by Tobbe » Tue Jan 31, 2017 7:48 pm
Trying to get VPN work on my synology NAS.
Getting this error and don’t know why (see below). Created the keys using this guide https://forum.synology.com/enu/viewtopi . 3&t=100066. Adjusted som configs according to this guide http://bpmsg.com/how-to-make-your-synol . nt-page-1/
Opened up ports correctly on both synology firewall and my router.
I have the ta.key username.key and username.crt and ca.crt in my Windows OPENVPN config subdir.
I have tried to add my certificate to the Synology GUI (security->certificate) with no success.
I have tried re-creating server crt and key and replaced the old ones with the new with no success.
push «route 192.168.1.0 255.255.255.0»
push «route 10.8.0.0 255.255.255.0»
management 127.0.0.1 1195
server 10.8.0.0 255.255.255.0
# The backup task will include this location
dh /var/packages/VPNCenter/target/etc/openvpn/keys/dh2048.pem
ca /var/packages/VPNCenter/target/etc/openvpn/keys/ca.crt
cert /var/packages/VPNCenter/target/etc/openvpn/keys/server.crt
key /var/packages/VPNCenter/target/etc/openvpn/keys/server.key
tls-auth /var/packages/VPNCenter/target/etc/openvpn/keys/ta.key 0
# Don’t forget logrotate script
log-append /var/log/openvpn.log
keepalive 10 60
reneg-sec 0
plugin /var/packages/VPNCenter/target/lib/radiusplugin.so /var/packages/VPNCenter/target/etc/openvpn/radiusplugin.cnf
# KEEP THIS DISABLED
#client-cert-not-required
username-as-common-name
duplicate-cn
status /tmp/ovpn_status_2_result 30
status-version 2
proto tcp6-server
Источник
forum.lissyara.su
Мы — долго запрягаем, быстро ездим, и сильно тормозим.
OpenVPN не заводиться 🙁
Модераторы: GRooVE, alexco
OpenVPN не заводиться 🙁
Непрочитанное сообщение Гость » 2008-09-19 12:35:43
Доброго времени суток ВСЕМ
Можете мне подсказать что не так ?
У клиента в логах openvpn.log ругань:
Сертификаты готовились на сервере, ось FreeBSD6.2 и OpenVPN 2.0.6
Клиент живет на FreeBSD4.8 и OpenVPN 2.0.6
Подскажите что не так.
Спасибо!
Услуги хостинговой компании Host-Food.ru
Re: OpenVPN не заводиться 🙁
Re: OpenVPN не заводиться 🙁
После совета проверить firewal, в логах клиента ситуация немного изменилась:
У клиента в логах openvpn.log ругань:
##########################################################
OpenVPN 2.0.6 i386-portbld-freebsd4.8 [SSL] [LZO] built on Sep 17 2008
Control Channel Authentication: using ‘/usr/local/etc/openvpn/keys/ta.key’ as a OpenVPN static key file
Outgoing Control Channel Authentication: Using 128 bit message hash ‘MD5’ for HMAC authentication
Incoming Control Channel Authentication: Using 128 bit message hash ‘MD5’ for HMAC authentication
LZO compression initialized
Control Channel MTU parms [ L:1538 D:162 EF:62 EB:0 ET:0 EL:0 ]
Data Channel MTU parms [ L:1538 D:1450 EF:38 EB:135 ET:0 EL:0 AF:3/1 ]
Local Options hash (VER=V4): ’03fa487d’
Expected Remote Options hash (VER=V4): ‘1056bce3’
UDPv4 link local (bound): [undef]:2000
UDPv4 link remote: ip.ser.ve.ra:2000
TLS Error: Unroutable control packet received from ip.ser.ve.ra:2000 (si=3 op=P_ACK_V1)
TLS Error: Unroutable control packet received from ip.ser.ve.ra:2000 (si=3 op=P_ACK_V1)
.
.
.
VERIFY nsCertType ERROR: /C=UA/ST=Kiev/L=Kiev/O=server/OU=server/CN=server/emailAddress=admin@domen.com.ua, require nsCertType=SERVER
TLS_ERROR: BIO read tls_read_plaintext error: error:14090086:SSL routines:SSL3_GET_SERVER_CERTIFICATE:certificate verify failed
TLS Error: TLS object -> incoming plaintext read error
TLS Error: TLS handshake failed
TCP/UDP: Closing socket
SIGUSR1[soft,tls-error] received, process restarting
Restart pause, 2 second(s)
У сервера ругань почти не изменилась:
##########################################################
ip.cli.en.ta:2000 TLS: new session incoming connection from 62.80.178.22:2000
ip.cli.en.ta:2000 TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity)
ip.cli.en.ta:2000 TLS Error: TLS handshake failed
ip.cli.en.ta:2000 SIGUSR1[soft,tls-error] received, client-instance restarting
MULTI: multi_create_instance called
как я понимаю что то с сертификатами. Генерил как написано
Источник
Hi,
I’m running psSense 2.0-BETA4 (i386) built on Mon Dec 20 20:21:46 EST 2010. Loving it so far!
I am setting up an OpenVPN server and I am using pfSense’s Certificate Manager to create the certificates. I have created all of the necessary certificates and keys (e.g. ca, server, client) and configured the OpenVPN server on pfSense and an OpenVPN client on Windows XP.
When I set up the client configuration file, I used the sample client configuration file included with OpenVPN as a template. Then I changed certain settings as needed (e.g. remote server address).
Initially, I couldn’t connect from the client. I tracked it down to this error in the OpenVPN log on the client side (confidential parts obfuscated with ###):
Fri Jan 07 09:46:13 2011 VERIFY nsCertType ERROR: /C=###/ST=###/L=###/O=###/emailAddress=###@###.com/CN=###, require nsCertType=SERVER
I was able to workaround the problem and successfully connect by commenting out (with a ‘;’ character) the following line in the client configuration:
ns-cert-type server
The comment above that setting recommends using the setting (i.e. not commenting it out) to prevent a possible man in the middle attack:
# Verify server certificate by checking
# that the certicate has the nsCertType
# field set to "server". This is an
# important precaution to protect against
# a potential attack discussed here:
# http://openvpn.net/howto.html#mitm
#
# To use this feature, you will need to generate
# your server certificates with the nsCertType
# field set to "server". The build-key-server
# script in the easy-rsa folder will do this.
For now, I’m okay with commenting out that setting. However, I would prefer if pfSense’s Certificate Manager would give you the option of adding extensions to certificates (in this case, the extension nsCertType=SERVER) . As far as I know, there is no way to do it with the current web interface.
Question 1): Is there a way to add this extension by creating a certificate from the command line in pfSense? If easy-rsa were installed (don’t think it is?) it would be simple. You would run the script build-key-server instead of build-key.
Question 2): Would it be possible to add this option to the Certificate Manager web interface?
Cheers
|
View previous topic :: View next topic |
||||||||
| Author | Message | |||||||
|---|---|---|---|---|---|---|---|---|
| muhammad-saleh DD-WRT Novice Joined: 12 Dec 2016 |
|
|||||||
| Back to top |
|
|||||||
| Sponsor | ||||||||
| muhammad-saleh DD-WRT Novice Joined: 12 Dec 2016 |
|
|||||||
| Back to top |
|
|||||||
| vibit DD-WRT Novice Joined: 21 Apr 2016 |
|
|||||||
| Back to top |
|
|||||||
| LaimisV DD-WRT User Joined: 01 Mar 2016 |
|
|||||||
| Back to top |
|
|||||||
| Xx_iDon_xX DD-WRT Novice Joined: 26 May 2018 |
|
|||||||
| Back to top |
|
|||||||
| source87 DD-WRT Novice Joined: 14 Apr 2019 |
|
|||||||
| Back to top |
|
|||||||
| Per Yngve Berg DD-WRT Guru Joined: 13 Aug 2013 |
|
|||||||
| Back to top |
|
|||||||
| source87 DD-WRT Novice Joined: 14 Apr 2019 |
|
|||||||
| Back to top |
|
|||||||
| source87 DD-WRT Novice Joined: 14 Apr 2019 |
|
|||||||
| Back to top |
|
|||||||
|
Navigation
|
You cannot post new topics in this forum |
Модераторы: GRooVE, alexco
Правила форума
Убедительная просьба юзать теги [code] при оформлении листингов.
Сообщения не оформленные должным образом имеют все шансы быть незамеченными.
-
Гость
- проходил мимо
OpenVPN не заводиться 
Доброго времени суток ВСЕМ
Можете мне подсказать что не так ?
У клиента в логах openvpn.log ругань:
Код: Выделить всё
##########################################################
event_wait : Interrupted system call (code=4)
TCP/UDP: Closing socket
SIGTERM[hard,] received, process exiting
OpenVPN 2.0.6 i386-portbld-freebsd4.8 [SSL] [LZO] built on Sep 17 2008
Control Channel Authentication: using '/usr/local/etc/openvpn/keys/ta.key' as a OpenVPN static key file
Outgoing Control Channel Authentication: Using 128 bit message hash 'MD5' for HMAC authentication
Incoming Control Channel Authentication: Using 128 bit message hash 'MD5' for HMAC authentication
LZO compression initialized
Control Channel MTU parms [ L:1538 D:162 EF:62 EB:0 ET:0 EL:0 ]
Data Channel MTU parms [ L:1538 D:1450 EF:38 EB:135 ET:0 EL:0 AF:3/1 ]
Local Options hash (VER=V4): '03fa487d'
Expected Remote Options hash (VER=V4): '1056bce3'
UDPv4 link local (bound): [undef]:2000
UDPv4 link remote: xxx.xxx.xxx.xxx:2000
[b]TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity)
TLS Error: TLS handshake failed[/b]
TCP/UDP: Closing socket
SIGUSR1[soft,tls-error] received, process restarting
Restart pause, 2 second(s)
Re-using SSL/TLS context
LZO compression initialized
Control Channel MTU parms [ L:1538 D:162 EF:62 EB:0 ET:0 EL:0 ]
Data Channel MTU parms [ L:1538 D:1450 EF:38 EB:135 ET:0 EL:0 AF:3/1 ]
Local Options hash (VER=V4): '03fa487d'
Expected Remote Options hash (VER=V4): '1056bce3'
UDPv4 link local (bound): [undef]:2000
UDPv4 link remote: xxx.xxx.xxx.xxx:2000А в логах сервера вот такая ругань:
##########################################################
Код: Выделить всё
[b]xx.xx.xx.xx:2000 TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity)
TLS Error: TLS handshake failed
xx.xx.xx.xx:2000 SIGUSR1[soft,tls-error] received, client-instance restarting
MULTI: multi_create_instance called[/b]
Re-using SSL/TLS context
LZO compression initialized
Control Channel MTU parms [ L:1538 D:162 EF:62 EB:0 ET:0 EL:0 ]
xx.xx.xx.xx:2000 Data Channel MTU parms [ L:1538 D:1450 EF:38 EB:135 ET:0 EL:0 AF:3/1 ]
xx.xx.xx.xx:2000 Local Options hash (VER=V4): '1056bce3'
xx.xx.xx.xx:2000 Expected Remote Options hash (VER=V4): '03fa487d'
xx.xx.xx.xx:2000 TLS: Initial packet from 62.80.178.22:2000, sid=ede7e96a 84c81a85
xx.xx.xx.xx:2000 write UDPv4: Permission denied (code=13)
xx.xx.xx.xx:2000 write UDPv4: Permission denied (code=13)ifconfig сервера:
Код: Выделить всё
##########################################################
tun1: flags=8051<UP,POINTOPOINT,RUNNING,MULTICAST> mtu 1500
inet 10.10.200.1 --> 10.10.200.2 netmask 0xffffffff
Opened by PID 19690
##########################################################Сертификаты готовились на сервере, ось FreeBSD6.2 и OpenVPN 2.0.6
Клиент живет на FreeBSD4.8 и OpenVPN 2.0.6
Подскажите что не так.
Спасибо!
Последний раз редактировалось zingel 2008-09-19 12:45:26, всего редактировалось 1 раз.
Причина: юзай [code][/code]
-
Хостинг HostFood.ru
Услуги хостинговой компании Host-Food.ru
Хостинг HostFood.ru
Тарифы на хостинг в России, от 12 рублей: https://www.host-food.ru/tariffs/hosting/
Тарифы на виртуальные сервера (VPS/VDS/KVM) в РФ, от 189 руб.: https://www.host-food.ru/tariffs/virtualny-server-vps/
Выделенные сервера, Россия, Москва, от 2000 рублей (HP Proliant G5, Intel Xeon E5430 (2.66GHz, Quad-Core, 12Mb), 8Gb RAM, 2x300Gb SAS HDD, P400i, 512Mb, BBU):
https://www.host-food.ru/tariffs/vydelennyi-server-ds/
Недорогие домены в популярных зонах: https://www.host-food.ru/domains/
-
hizel
- дядя поня
- Сообщения: 9032
- Зарегистрирован: 2007-06-29 10:05:02
- Откуда: Выборг
Re: OpenVPN не заводиться 
Непрочитанное сообщение
hizel » 2008-09-19 12:41:22
Код: Выделить всё
xx.xx.xx.xx:2000 write UDPv4: Permission denied (code=13)
xx.xx.xx.xx:2000 write UDPv4: Permission denied (code=13)
эти строчки мне не нравятся
фаервол?
В дурацкие игры он не играет. Он просто жуткий, чу-чу, паровозик, и зовут его Блейн. Блейн — это Боль.
-
BI_J
- сержант
- Сообщения: 154
- Зарегистрирован: 2008-09-19 12:21:10
Re: OpenVPN не заводиться 
Непрочитанное сообщение
BI_J » 2008-09-19 12:52:58
Все делалось по статье уважаемого mak_v_.
http://www.lissyara.su/?id=1685&comment … mment_4718
После совета проверить firewal, в логах клиента ситуация немного изменилась:
У клиента в логах openvpn.log ругань:
##########################################################
OpenVPN 2.0.6 i386-portbld-freebsd4.8 [SSL] [LZO] built on Sep 17 2008
Control Channel Authentication: using ‘/usr/local/etc/openvpn/keys/ta.key’ as a OpenVPN static key file
Outgoing Control Channel Authentication: Using 128 bit message hash ‘MD5’ for HMAC authentication
Incoming Control Channel Authentication: Using 128 bit message hash ‘MD5’ for HMAC authentication
LZO compression initialized
Control Channel MTU parms [ L:1538 D:162 EF:62 EB:0 ET:0 EL:0 ]
Data Channel MTU parms [ L:1538 D:1450 EF:38 EB:135 ET:0 EL:0 AF:3/1 ]
Local Options hash (VER=V4): ’03fa487d’
Expected Remote Options hash (VER=V4): ‘1056bce3’
UDPv4 link local (bound): [undef]:2000
UDPv4 link remote: ip.ser.ve.ra:2000
TLS Error: Unroutable control packet received from ip.ser.ve.ra:2000 (si=3 op=P_ACK_V1)
TLS Error: Unroutable control packet received from ip.ser.ve.ra:2000 (si=3 op=P_ACK_V1)
.
.
.
VERIFY nsCertType ERROR: /C=UA/ST=Kiev/L=Kiev/O=server/OU=server/CN=server/emailAddress=admin@domen.com.ua, require nsCertType=SERVER
TLS_ERROR: BIO read tls_read_plaintext error: error:14090086:SSL routines:SSL3_GET_SERVER_CERTIFICATE:certificate verify failed
TLS Error: TLS object -> incoming plaintext read error
TLS Error: TLS handshake failed
TCP/UDP: Closing socket
SIGUSR1[soft,tls-error] received, process restarting
Restart pause, 2 second(s)
У сервера ругань почти не изменилась:
##########################################################
ip.cli.en.ta:2000 TLS: new session incoming connection from 62.80.178.22:2000
ip.cli.en.ta:2000 TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity)
ip.cli.en.ta:2000 TLS Error: TLS handshake failed
ip.cli.en.ta:2000 SIGUSR1[soft,tls-error] received, client-instance restarting
MULTI: multi_create_instance called
как я понимаю что то с сертификатами. Генерил как написано
-
serge
- майор
- Сообщения: 2133
- Зарегистрирован: 2006-07-30 15:34:14
- Откуда: Саратов
- Контактная информация:
Re: OpenVPN не заводиться 
Непрочитанное сообщение
serge » 2008-09-19 14:52:30
Случаем не в клетке OpenVPN сидит?
Вот это смущает…
Unroutable control packet received from ip.ser.ve.ra:2000
-
hizel
- дядя поня
- Сообщения: 9032
- Зарегистрирован: 2007-06-29 10:05:02
- Откуда: Выборг
Re: OpenVPN не заводиться 
Непрочитанное сообщение
hizel » 2008-09-19 14:57:22
и всетаки попробуйте ище раз пегенерировать сертификаты
у вас тип сертификата не совпадает
В дурацкие игры он не играет. Он просто жуткий, чу-чу, паровозик, и зовут его Блейн. Блейн — это Боль.
-
serge
- майор
- Сообщения: 2133
- Зарегистрирован: 2006-07-30 15:34:14
- Откуда: Саратов
- Контактная информация:
Re: OpenVPN не заводиться 
Непрочитанное сообщение
serge » 2008-09-19 15:08:49
TLS key negotiation failed to occur within 60 seconds (check your network connectivity)
дословно гуглом
TLS ключевые переговоры «не произойдет в течение 60 секунд (проверьте ваши сетевые подключения)
имхо, главная часть
проверьте ваши сетевые подключения
-
BI_J
- сержант
- Сообщения: 154
- Зарегистрирован: 2008-09-19 12:21:10
Re: OpenVPN не заводиться 
Непрочитанное сообщение
BI_J » 2008-09-19 15:14:23
Спасибо за подсказки.
После очередной перегенирации сертификатов ситуация резко улучшилась
Но VPN так и не поднялся.
Теперь проблема кажеться в маршрутах со стороны клиента.
У клиента в логах openvpn.log
##########################################################
Код: Выделить всё
[server] Peer Connection Initiated with ip.ser.ve.ra:2000
SENT CONTROL [server]: 'PUSH_REQUEST' (status=1)
PUSH: Received control message: 'PUSH_REPLY,route 192.168.0.0 255.255.255.0,route 10.10.200.1,ping 10,ping-
restart 120,ifconfig 10.10.200.2 10.10.200.1'
OPTIONS IMPORT: timers and/or timeouts modified
OPTIONS IMPORT: --ifconfig/up options modified
OPTIONS IMPORT: route options modified
gw ip.pro.vay.da
TUN/TAP device /dev/tun1 opened
/sbin/ifconfig tun1 10.10.200.2 10.10.200.1 mtu 1500 netmask 255.255.255.255 up
/usr/local/etc/openvpn/openvpn_up.sh tun1 1500 1538 10.10.200.2 10.10.200.1 init
/usr/local/etc/openvpn/openvpn_up.sh: permission denied
script failed: shell command exited with error status: 126
Fri Sep 19 14:02:08 2008 Exiting##########################################################
Интернет удаленный клиент получает через модем провайдера через вот такое соединение:
ifconfig:
Код: Выделить всё
tun0: flags=8051<UP,POINTOPOINT,RUNNING,MULTICAST> mtu 1492
inet ip.cli.en.ta --> ip.pro.vay.da netmask 0xffffffff
Opened by PID 88нужно как то рулить это дело
-
zingel
- beastie
- Сообщения: 6204
- Зарегистрирован: 2007-10-30 3:56:49
- Откуда: Moscow
- Контактная информация:
Re: OpenVPN не заводиться 
Непрочитанное сообщение
zingel » 2008-09-19 15:14:47
TLS ключевые переговоры «не произойдет в течение 60 секунд (проверьте ваши сетевые подключения)
Это гугловский переводчик такую ересь выдал? Я в шоке…
Z301171463546 — можно пожертвовать мне денег
-
BI_J
- сержант
- Сообщения: 154
- Зарегистрирован: 2008-09-19 12:21:10
Re: OpenVPN не заводиться 
Непрочитанное сообщение
BI_J » 2008-09-19 17:03:49
Сижу, смотрю на ошибку и в упор не замечаю грабли (стыдно белое перо ):
Код: Выделить всё
usr/local/etc/openvpn/openvpn_up.sh tun1 1500 1538 10.10.200.2 10.10.200.1 init
/usr/local/etc/openvpn/openvpn_up.sh: permission denied
script failed: shell command exited with error status: 126
после выполнения:
chmod 755 /usr/local/etc/openvpn/openvpn_up.sh
положение улучшилось
пинг пошол между 10.10.200.2 и 10.10.200.1
хух
-
makihtow
- проходил мимо
- Сообщения: 8
- Зарегистрирован: 2009-02-05 14:18:31
OpenVPN не заводиться
Непрочитанное сообщение
makihtow » 2009-02-05 14:23:37
Здрасти ребята. У меня такая вот проблема. Что делать? Подскажите пожалуйста.
Thu Feb 05 13:22:02 2009 Data Channel MTU parms [ L:1538 D:1450 EF:38 EB:135 ET:0 EL:0 AF:3/1 ]
Thu Feb 05 13:22:02 2009 Local Options hash (VER=V4): ’03fa487d’
Thu Feb 05 13:22:02 2009 Expected Remote Options hash (VER=V4): ‘1056bce3’
Thu Feb 05 13:22:02 2009 UDPv4 link local (bound): [undef]:2000
Thu Feb 05 13:22:02 2009 UDPv4 link remote: 22.22.22.22:2000
Thu Feb 05 13:23:01 2009 TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity)
Thu Feb 05 13:23:01 2009 TLS Error: TLS handshake failed
Thu Feb 05 13:23:01 2009 TCP/UDP: Closing socket
Thu Feb 05 13:23:01 2009 SIGUSR1[soft,tls-error] received, process restarting
Thu Feb 05 13:23:01 2009 Restart pause, 2 second(s)
Thu Feb 05 13:23:03 2009 Re-using SSL/TLS context
Thu Feb 05 13:23:03 2009 LZO compression initialized
Thu Feb 05 13:23:03 2009 Control Channel MTU parms [ L:1538 D:162 EF:62 EB:0 ET:0 EL:0 ]
Thu Feb 05 13:23:03 2009 Data Channel MTU parms [ L:1538 D:1450 EF:38 EB:135 ET:0 EL:0 AF:3/1 ]
Thu Feb 05 13:23:03 2009 Local Options hash (VER=V4): ’03fa487d’
Thu Feb 05 13:23:03 2009 Expected Remote Options hash (VER=V4): ‘1056bce3’
Thu Feb 05 13:23:03 2009 UDPv4 link local (bound): [undef]:2000
Thu Feb 05 13:23:03 2009 UDPv4 link remote: 22.22.22.22:2000
-
hizel
- дядя поня
- Сообщения: 9032
- Зарегистрирован: 2007-06-29 10:05:02
- Откуда: Выборг
Re: OpenVPN не заводиться 
Непрочитанное сообщение
hizel » 2009-02-05 14:36:05
check your network connectivity
перевод требуется ?
В дурацкие игры он не играет. Он просто жуткий, чу-чу, паровозик, и зовут его Блейн. Блейн — это Боль.
-
hizel
- дядя поня
- Сообщения: 9032
- Зарегистрирован: 2007-06-29 10:05:02
- Откуда: Выборг
Re: OpenVPN не заводиться 
Непрочитанное сообщение
hizel » 2009-02-05 14:42:50
фаервол прверить
tcpdump-ом посмотреть
В дурацкие игры он не играет. Он просто жуткий, чу-чу, паровозик, и зовут его Блейн. Блейн — это Боль.
-
makihtow
- проходил мимо
- Сообщения: 8
- Зарегистрирован: 2009-02-05 14:18:31
Re: OpenVPN не заводиться 
Непрочитанное сообщение
makihtow » 2009-02-05 14:44:35
tcpdump -om
tcpdump version 3.9.4
libpcap version 0.9.4
Usage: tcpdump [-aAdDeflLnNOpqRStuUvxX] [-c count] [ -C file_size ]
[ -E algo:secret ] [ -F file ] [ -i interface ] [ -M secret ]
[ -r file ] [ -s snaplen ] [ -T type ] [ -w file ]
[ -W filecount ] [ -y datalinktype ] [ -Z user ]
[ expression ]
-
hizel
- дядя поня
- Сообщения: 9032
- Зарегистрирован: 2007-06-29 10:05:02
- Откуда: Выборг
Re: OpenVPN не заводиться 
Непрочитанное сообщение
hizel » 2009-02-05 14:46:45
где <int> интерфейс через который openvpn ломится в интернет
2000 порт и можно еще приписать
В дурацкие игры он не играет. Он просто жуткий, чу-чу, паровозик, и зовут его Блейн. Блейн — это Боль.
-
makihtow
- проходил мимо
- Сообщения: 8
- Зарегистрирован: 2009-02-05 14:18:31
Re: OpenVPN не заводиться 
Непрочитанное сообщение
makihtow » 2009-02-05 15:10:00
#tcpdump -i fxp0 -np port 2000 and udp
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on fxp0, link-type EN10MB (Ethernet), capture size 96 bytes
-
hizel
- дядя поня
- Сообщения: 9032
- Зарегистрирован: 2007-06-29 10:05:02
- Откуда: Выборг
Re: OpenVPN не заводиться 
Непрочитанное сообщение
hizel » 2009-02-05 15:11:41
ну и при запущенном tcpdump рестартануть openvpn
В дурацкие игры он не играет. Он просто жуткий, чу-чу, паровозик, и зовут его Блейн. Блейн — это Боль.
-
makihtow
- проходил мимо
- Сообщения: 8
- Зарегистрирован: 2009-02-05 14:18:31
Re: OpenVPN не заводиться 
Непрочитанное сообщение
makihtow » 2009-02-05 15:40:25
Запустил tcpdump и сделал рестарт openvpn. Вот результат.
Код: Выделить всё
#tcpdump -i fxp0 -np port 2000 and udp
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on fxp0, link-type EN10MB (Ethernet), capture size 96 bytes
Код: Выделить всё
38 packets captured
4492 packets received by filter
0 packets dropped by kernel-
hizel
- дядя поня
- Сообщения: 9032
- Зарегистрирован: 2007-06-29 10:05:02
- Откуда: Выборг
Re: OpenVPN не заводиться 
Непрочитанное сообщение
hizel » 2009-02-05 15:47:18
у вас openvpn точно работает на 2000 порту udp?
если да то проверяйте фаервол
В дурацкие игры он не играет. Он просто жуткий, чу-чу, паровозик, и зовут его Блейн. Блейн — это Боль.
-
hz
- проходил мимо
- Сообщения: 4
- Зарегистрирован: 2009-03-24 9:59:09
Re: OpenVPN не заводиться 
Непрочитанное сообщение
hz » 2009-03-24 10:27:16
День добрый.Помогите советом куда копать.Трабл в следующем:всё поднималось по описанию mac_v (отдельное спасибо).Туннель поднялся.Но проблема в следующем-внутрення сеть «филиала» видит внутреннее пространство за сервером впн.В обратную же сторону,т.е. то что находится внутри «головного офиса» не видит сетку «филиала».Выдаёт на ping ошибку ping: sendto: Invalid argument.Маршуты все прописаны.Руками прописывать пробывал маршрут до подсети «филиала» — ответ маршрут сущ-т.
-
zingel
- beastie
- Сообщения: 6204
- Зарегистрирован: 2007-10-30 3:56:49
- Откуда: Moscow
- Контактная информация:
Re: OpenVPN не заводиться 
Непрочитанное сообщение
zingel » 2009-03-24 13:29:05
отдельную тему лучше
Z301171463546 — можно пожертвовать мне денег
-
Sanya0413
- проходил мимо
- Сообщения: 2
- Зарегистрирован: 2010-03-30 15:30:44
Re: OpenVPN не заводиться 
Непрочитанное сообщение
Sanya0413 » 2010-03-30 16:31:46
# !/bin/sh
/bin/sh: Event not found.
# /sbin/route add -net 192.168.1.0 10.10.200.1
route: writing to routing socket: Network is unreachable
add net 193.168.1.0: gateway 10.10.200.1: Network is unreachable
при создании файла openvpn_up.sh пишет вот такую ругню.
все создал по статье, sockstat ‘ ом проверил openvpn поднялся на сервере и на клиенте, но пинги не идут((
I have read in other places softether does not support certificate authentication but I am using OpenVPN GUI v11.14.0.0 and recently updated Softether server 4.32, and using the below .ovpn it does connect to my server; of course I have a user created and selected certificate authentication, created and add the corresponding certificates in my .ovpn file, below the log successfully connecting (top to bottom)
Wed Mar 18 17:47:41 2020 OpenVPN 2.4.8 x86_64-w64-mingw32 [SSL (OpenSSL)] [LZO] [LZ4] [PKCS11] [AEAD] built on Oct 31 2019
Wed Mar 18 17:47:41 2020 Windows version 6.2 (Windows 8 or greater) 64bit
Wed Mar 18 17:47:41 2020 library versions: OpenSSL 1.1.0l 10 Sep 2019, LZO 2.10
Enter Management Password:
Wed Mar 18 17:47:41 2020 MANAGEMENT: TCP Socket listening on [AF_INET]127.0.0.1:25341
Wed Mar 18 17:47:41 2020 Need hold release from management interface, waiting…
Wed Mar 18 17:47:41 2020 MANAGEMENT: Client connected from [AF_INET]127.0.0.1:25341
Wed Mar 18 17:47:41 2020 MANAGEMENT: CMD ‘state on’
Wed Mar 18 17:47:41 2020 MANAGEMENT: CMD ‘log all on’
Wed Mar 18 17:47:41 2020 MANAGEMENT: CMD ‘echo all on’
Wed Mar 18 17:47:41 2020 MANAGEMENT: CMD ‘bytecount 5’
Wed Mar 18 17:47:41 2020 MANAGEMENT: CMD ‘hold off’
Wed Mar 18 17:47:41 2020 MANAGEMENT: CMD ‘hold release’
Wed Mar 18 17:47:41 2020 TCP/UDP: Preserving recently used remote address: [AF_INET][myserverip]:443
Wed Mar 18 17:47:41 2020 Socket Buffers: R=[65536->65536] S=[65536->65536]
Wed Mar 18 17:47:41 2020 Attempting to establish TCP connection with [AF_INET][myserverip]:443 [nonblock]
Wed Mar 18 17:47:41 2020 MANAGEMENT: >STATE:1584553661,TCP_CONNECT,,,,,,
Wed Mar 18 17:47:42 2020 TCP connection established with [AF_INET][myserverip]:443
Wed Mar 18 17:47:42 2020 TCP_CLIENT link local: (not bound)
Wed Mar 18 17:47:42 2020 TCP_CLIENT link remote: [AF_INET][myserverip]:443
Wed Mar 18 17:47:42 2020 MANAGEMENT: >STATE:1584553662,WAIT,,,,,,
Wed Mar 18 17:47:42 2020 MANAGEMENT: >STATE:1584553662,AUTH,,,,,,
Wed Mar 18 17:47:42 2020 TLS: Initial packet from [AF_INET][myserverip]:443, sid=504f73ba 0867b040
Wed Mar 18 17:47:43 2020 VERIFY KU OK
Wed Mar 18 17:47:43 2020 Validating certificate extended key usage
Wed Mar 18 17:47:43 2020 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
Wed Mar 18 17:47:43 2020 VERIFY EKU OK
Wed Mar 18 17:47:43 2020 VERIFY OK: depth=0, CN=[vpnNumber].softether.net, O=[vpnNumber].softether.net, OU=[vpnNumber].softether.net, C=US
Wed Mar 18 17:47:43 2020 Control Channel: TLSv1.2, cipher TLSv1.2 ECDHE-RSA-AES256-GCM-SHA384, 2048 bit RSA
Wed Mar 18 17:47:43 2020 [[vpnNumber].softether.net] Peer Connection Initiated with [AF_INET][myserverip]:443
Wed Mar 18 17:47:44 2020 MANAGEMENT: >STATE:1584553664,GET_CONFIG,,,,,,
Wed Mar 18 17:47:44 2020 SENT CONTROL [[vpnNumber].softether.net]: ‘PUSH_REQUEST’ (status=1)
Wed Mar 18 17:47:44 2020 PUSH: Received control message: ‘PUSH_REPLY,ping 3,ping-restart 10,ifconfig 192.168.30.21 192.168.30.22,route 192.168.30.0 255.255.255.0 vpn_gateway’
Wed Mar 18 17:47:44 2020 OPTIONS IMPORT: timers and/or timeouts modified
Wed Mar 18 17:47:44 2020 OPTIONS IMPORT: —ifconfig/up options modified
Wed Mar 18 17:47:44 2020 OPTIONS IMPORT: route options modified
Wed Mar 18 17:47:44 2020 Outgoing Data Channel: Cipher ‘AES-256-CBC’ initialized with 256 bit key
Wed Mar 18 17:47:44 2020 Outgoing Data Channel: Using 160 bit message hash ‘SHA1’ for HMAC authentication
Wed Mar 18 17:47:44 2020 Incoming Data Channel: Cipher ‘AES-256-CBC’ initialized with 256 bit key
Wed Mar 18 17:47:44 2020 Incoming Data Channel: Using 160 bit message hash ‘SHA1’ for HMAC authentication
Wed Mar 18 17:47:44 2020 interactive service msg_channel=620
Wed Mar 18 17:47:44 2020 ROUTE_GATEWAY 192.168.13.1/255.255.255.0 I=11 HWADDR=48:2a:e3:3f:5f:99
Wed Mar 18 17:47:44 2020 open_tun
Wed Mar 18 17:47:44 2020 TAP-WIN32 device [Talk2m-eCatcher] opened: \.Global{418A9F47-1307-4650-9C3C-28893C93D82E}.tap
Wed Mar 18 17:47:44 2020 TAP-Windows Driver Version 9.24
Wed Mar 18 17:47:44 2020 Notified TAP-Windows driver to set a DHCP IP/netmask of 192.168.30.21/255.255.255.252 on interface {418A9F47-1307-4650-9C3C-28893C93D82E} [DHCP-serv: 192.168.30.22, lease-time: 31536000]
Wed Mar 18 17:47:44 2020 Successful ARP Flush on interface [18] {418A9F47-1307-4650-9C3C-28893C93D82E}
Wed Mar 18 17:47:44 2020 MANAGEMENT: >STATE:1584553664,ASSIGN_IP,,192.168.30.21,,,,
Wed Mar 18 17:47:49 2020 TEST ROUTES: 1/1 succeeded len=1 ret=1 a=0 u/d=up
Wed Mar 18 17:47:49 2020 MANAGEMENT: >STATE:1584553669,ADD_ROUTES,,,,,,
Wed Mar 18 17:47:49 2020 C:WINDOWSsystem32route.exe ADD 192.168.30.0 MASK 255.255.255.0 192.168.30.22
Wed Mar 18 17:47:49 2020 Route addition via service succeeded
Wed Mar 18 17:47:49 2020 WARNING: this configuration may cache passwords in memory — use the auth-nocache option to prevent this
Wed Mar 18 17:47:49 2020 Initialization Sequence Completed
Wed Mar 18 17:47:49 2020 MANAGEMENT: >STATE:1584553669,CONNECTED,SUCCESS,192.168.30.21,[myserverip],443,192.168.13.49,62877
But when I tried the same config file in ewon router (flexy 205) I get this error (read bottom to top)
19/03/2020 16:21:10 VPN SIGTERM[soft,tls-error] received, process exiting 161585 53
19/03/2020 16:21:10 VPN TCP/UDP: Closing socket 161585 52
19/03/2020 16:21:10 VPN Fatal TLS error (check_tls_errors_co), restarting 161585 51
19/03/2020 16:21:10 VPN TLS Error: TLS handshake failed 161585 50
19/03/2020 16:21:10 VPN TLS Error: TLS object -> incoming plaintext read error 161585 49
19/03/2020 16:21:10 VPN TLS_ERROR: BIO read tls_read_plaintext error: error:14090086:SSL routines:ssl3_get_server_certificate:certificate verify failed 161585 48
19/03/2020 16:21:10 VPN VERIFY nsCertType ERROR: /CN=[serverNumber].softether.net/O=[serverNumber].softether.net/OU=[serverNumber].softether.net/C=US, require nsCertType=SERVER 161585 47
19/03/2020 16:21:10 VPN TLS: Initial packet from [myserverIP]:443, sid=f842da4b 13db23f0 161492 46
19/03/2020 16:21:10 VPN TCPv4_CLIENT link remote: [myserverIP]:443 161482 45
19/03/2020 16:21:10 VPN TCPv4_CLIENT link local: [undef] 161482 44
19/03/2020 16:21:10 VPN TCP connection established with [myserverIP]:443 161482 43
19/03/2020 16:21:10 VPN Attempting to establish TCP connection with [myserverIP]:443 161470 42
19/03/2020 16:21:10 VPN Expected Remote Options hash (VER=V4): ’79ef4284′ 161470 41
19/03/2020 16:21:10 VPN Local Options hash (VER=V4): ‘958c5492’ 161470 40
19/03/2020 16:21:10 VPN Data Channel MTU parms [ L:1560 D:1450 EF:60 EB:135 ET:0 EL:0 AF:3/1 ] 161470 39
19/03/2020 16:21:10 VPN Control Channel MTU parms [ L:1560 D:140 EF:40 EB:0 ET:0 EL:0 ] 161470 38
19/03/2020 16:21:10 VPN LZO compression initialized 161470 37
19/03/2020 16:21:10 VPN OpenVPN 2.0.9 arm-ewon-linux-gnueabi [SSL] [LZO] [EPOLL] build date removed 161470 36
any ideas?
Code: Select all
client
dev tun
proto tcp
remote [my server ip]
port 443
resolv-retry infinite
nobind
persist-key
persist-tun
verb 3
remote-cert-tls server
cipher AES-256-CBC
auth SHA1
<ca>
-----BEGIN CERTIFICATE-----
...
-----END CERTIFICATE-----
</ca>
<cert>
-----BEGIN CERTIFICATE-----
...
-----END PRIVATE KEY-----
</cert>
<key>
-----BEGIN PRIVATE KEY-----
...
-----END PRIVATE KEY-----
</key>- Печать
Страницы: 1 2 [3] 4 Вниз
Тема: Ошибки OpenVPN и их решение (Прочитано 100060 раз)
0 Пользователей и 1 Гость просматривают эту тему.
Целый день промучился чтоб поднять VPN, но никак не удается, точнее удается, но инет работает секунд 30 и все, потом пауза на полторы минуты и реконнект. Подозреваю, что проблема вот в этом: NOTE: FlushIpNetTable failed on interface [4] {AAA1E80D-7F37-4FEE-9FD2-9FADCAA4DF1B} (status=1413) : Неверный индекс. Лог прилагается. По нему видно, что идет реконнект каждые 2 минуты. Подскажите пожалуйста, что не так?
PS: через спринт все прекрасно работает, но есть необходимость в OpenVPN.
Thu Mar 08 23:42:32 2012 OpenVPN 2.0.9 Win32-MinGW [SSL] [LZO] built on Feb 9 2007
Thu Mar 08 23:42:32 2012 IMPORTANT: OpenVPN’s default port number is now 1194, based on an official port number assignment by IANA. OpenVPN 2.0-beta16 and earlier used 5000 as the default port.
Thu Mar 08 23:42:32 2012 LZO compression initialized
Thu Mar 08 23:42:32 2012 Control Channel MTU parms [ L:1574 D:138 EF:38 EB:0 ET:0 EL:0 ]
Thu Mar 08 23:42:32 2012 Data Channel MTU parms [ L:1574 D:1450 EF:42 EB:135 ET:32 EL:0 AF:3/1 ]
Thu Mar 08 23:42:32 2012 Local Options hash (VER=V4): ‘d79ca330’
Thu Mar 08 23:42:32 2012 Expected Remote Options hash (VER=V4): ‘f7df56b8’
Thu Mar 08 23:42:32 2012 UDPv4 link local: [undef]
Thu Mar 08 23:42:32 2012 UDPv4 link remote: 80.81.209.162:55000
Thu Mar 08 23:42:34 2012 TLS: Initial packet from 80.81.209.162:55000, sid=3cb4f370 128799e1
Thu Mar 08 23:42:43 2012 VERIFY OK: depth=1, /C=RU/ST=MW/L=MOSCOW/O=RadugaVPN/emailAddress=support@telecom-service.net
Thu Mar 08 23:42:43 2012 VERIFY OK: nsCertType=SERVER
Thu Mar 08 23:42:43 2012 VERIFY OK: depth=0, /C=RU/ST=MW/O=RadugaVPN/CN=RadugaVPN/emailAddress=support@telecom-service.net
Thu Mar 08 23:42:49 2012 Data Channel Encrypt: Cipher ‘BF-CBC’ initialized with 128 bit key
Thu Mar 08 23:42:49 2012 Data Channel Encrypt: Using 160 bit message hash ‘SHA1’ for HMAC authentication
Thu Mar 08 23:42:49 2012 Data Channel Decrypt: Cipher ‘BF-CBC’ initialized with 128 bit key
Thu Mar 08 23:42:49 2012 Data Channel Decrypt: Using 160 bit message hash ‘SHA1’ for HMAC authentication
Thu Mar 08 23:42:49 2012 Control Channel: TLSv1, cipher TLSv1/SSLv3 DHE-RSA-AES256-SHA, 1024 bit RSA
Thu Mar 08 23:42:49 2012 [RadugaVPN] Peer Connection Initiated with 80.81.209.162:55000
Thu Mar 08 23:42:50 2012 SENT CONTROL [RadugaVPN]: ‘PUSH_REQUEST’ (status=1)
Thu Mar 08 23:42:52 2012 PUSH: Received control message: ‘PUSH_REPLY,redirect-gateway,dhcp-option DNS 80.81.208.66,route-gateway 10.251.0.1,ping 30,ping-restart 120,route 0.0.0.0 0.0.0.0 10.251.0.1,dhcp-option DNS 80.81.209.162,ifconfig 10.251.157.251 255.255.0.0’
Thu Mar 08 23:42:52 2012 OPTIONS IMPORT: timers and/or timeouts modified
Thu Mar 08 23:42:52 2012 OPTIONS IMPORT: —ifconfig/up options modified
Thu Mar 08 23:42:52 2012 OPTIONS IMPORT: route options modified
Thu Mar 08 23:42:52 2012 OPTIONS IMPORT: —ip-win32 and/or —dhcp-option options modified
Thu Mar 08 23:42:52 2012 TAP-WIN32 device [Raduga] opened: \.Global{AAA1E80D-7F37-4FEE-9FD2-9FADCAA4DF1B}.tap
Thu Mar 08 23:42:52 2012 TAP-Win32 Driver Version 8.4
Thu Mar 08 23:42:52 2012 TAP-Win32 MTU=1500
Thu Mar 08 23:42:52 2012 Notified TAP-Win32 driver to set a DHCP IP/netmask of 10.251.157.251/255.255.0.0 on interface {AAA1E80D-7F37-4FEE-9FD2-9FADCAA4DF1B} [DHCP-serv: 10.251.0.0, lease-time: 31536000]
Thu Mar 08 23:42:52 2012 NOTE: FlushIpNetTable failed on interface [4] {AAA1E80D-7F37-4FEE-9FD2-9FADCAA4DF1B} (status=1413) : Неверный индекс.
Thu Mar 08 23:42:52 2012 TEST ROUTES: 0/0 succeeded len=1 ret=0 a=0 u/d=down
Thu Mar 08 23:42:52 2012 Route: Waiting for TUN/TAP interface to come up…
Thu Mar 08 23:42:53 2012 TEST ROUTES: 0/0 succeeded len=1 ret=0 a=0 u/d=down
Thu Mar 08 23:42:53 2012 Route: Waiting for TUN/TAP interface to come up…
Thu Mar 08 23:42:54 2012 TEST ROUTES: 0/0 succeeded len=1 ret=0 a=0 u/d=down
Thu Mar 08 23:42:54 2012 Route: Waiting for TUN/TAP interface to come up…
Thu Mar 08 23:42:55 2012 TEST ROUTES: 2/2 succeeded len=1 ret=1 a=0 u/d=up
Thu Mar 08 23:42:55 2012 route ADD 80.81.209.162 MASK 255.255.255.255 175.0.167.117
Thu Mar 08 23:42:55 2012 route DELETE 0.0.0.0 MASK 0.0.0.0 175.0.167.117
Thu Mar 08 23:42:55 2012 route ADD 0.0.0.0 MASK 0.0.0.0 10.251.0.1
Thu Mar 08 23:42:55 2012 route ADD 0.0.0.0 MASK 0.0.0.0 10.251.0.1
Thu Mar 08 23:42:55 2012 Initialization Sequence Completed
Thu Mar 08 23:44:55 2012 [RadugaVPN] Inactivity timeout (—ping-restart), restarting
Thu Mar 08 23:44:55 2012 TCP/UDP: Closing socket
Thu Mar 08 23:44:55 2012 SIGUSR1[soft,ping-restart] received, process restarting
Thu Mar 08 23:44:55 2012 Restart pause, 2 second(s)
Thu Mar 08 23:44:57 2012 IMPORTANT: OpenVPN’s default port number is now 1194, based on an official port number assignment by IANA. OpenVPN 2.0-beta16 and earlier used 5000 as the default port.
Thu Mar 08 23:44:57 2012 Re-using SSL/TLS context
Thu Mar 08 23:44:57 2012 LZO compression initialized
Thu Mar 08 23:44:57 2012 Control Channel MTU parms [ L:1574 D:138 EF:38 EB:0 ET:0 EL:0 ]
Thu Mar 08 23:44:57 2012 Data Channel MTU parms [ L:1574 D:1450 EF:42 EB:135 ET:32 EL:0 AF:3/1 ]
Thu Mar 08 23:44:57 2012 Local Options hash (VER=V4): ‘d79ca330’
Thu Mar 08 23:44:57 2012 Expected Remote Options hash (VER=V4): ‘f7df56b8’
Thu Mar 08 23:44:57 2012 UDPv4 link local: [undef]
Thu Mar 08 23:44:57 2012 UDPv4 link remote: 80.81.209.162:55000
Thu Mar 08 23:44:58 2012 TLS: Initial packet from 80.81.209.162:55000, sid=87a6e26e 5bf5c044
Thu Mar 08 23:45:00 2012 VERIFY OK: depth=1, /C=RU/ST=MW/L=MOSCOW/O=RadugaVPN/emailAddress=support@telecom-service.net
Thu Mar 08 23:45:00 2012 VERIFY OK: nsCertType=SERVER
Thu Mar 08 23:45:00 2012 VERIFY OK: depth=0, /C=RU/ST=MW/O=RadugaVPN/CN=RadugaVPN/emailAddress=support@telecom-service.net
Thu Mar 08 23:45:11 2012 Data Channel Encrypt: Cipher ‘BF-CBC’ initialized with 128 bit key
Thu Mar 08 23:45:11 2012 Data Channel Encrypt: Using 160 bit message hash ‘SHA1’ for HMAC authentication
Thu Mar 08 23:45:11 2012 Data Channel Decrypt: Cipher ‘BF-CBC’ initialized with 128 bit key
Thu Mar 08 23:45:11 2012 Data Channel Decrypt: Using 160 bit message hash ‘SHA1’ for HMAC authentication
Thu Mar 08 23:45:11 2012 Control Channel: TLSv1, cipher TLSv1/SSLv3 DHE-RSA-AES256-SHA, 1024 bit RSA
Thu Mar 08 23:45:11 2012 [RadugaVPN] Peer Connection Initiated with 80.81.209.162:55000
Thu Mar 08 23:45:12 2012 SENT CONTROL [RadugaVPN]: ‘PUSH_REQUEST’ (status=1)
Thu Mar 08 23:45:12 2012 PUSH: Received control message: ‘PUSH_REPLY,redirect-gateway,dhcp-option DNS 80.81.208.66,route-gateway 10.251.0.1,ping 30,ping-restart 120,route 0.0.0.0 0.0.0.0 10.251.0.1,dhcp-option DNS 80.81.209.162,ifconfig 10.251.157.251 255.255.0.0’
Thu Mar 08 23:45:12 2012 OPTIONS IMPORT: timers and/or timeouts modified
Thu Mar 08 23:45:12 2012 OPTIONS IMPORT: —ifconfig/up options modified
Thu Mar 08 23:45:12 2012 OPTIONS IMPORT: route options modified
Thu Mar 08 23:45:12 2012 OPTIONS IMPORT: —ip-win32 and/or —dhcp-option options modified
Thu Mar 08 23:45:12 2012 Preserving previous TUN/TAP instance: Raduga
Thu Mar 08 23:45:12 2012 Initialization Sequence Completed
у вас может какие-нибудь файрволы или антивири установлены? винда какая? если 7 — от админа ставили и запускаете?
Записан
1) Хочешь сделать что-то ХОРОШО, сделай это САМ…
2) Кто в саппорте служил — тот в цирке не смеется…
3) Настоящий мужчина скидок не просит и сдачу не берет!
у вас может какие-нибудь файрволы или антивири установлены? винда какая? если 7 — от админа ставили и запускаете?
Установлен Windows XP. Из файрволов стоит Agnitum Outpost, но он находится в режиме «Приостановить защиту»
Сейчас попробую на другой машине с голой XP.
Записан
Установил по новой XP. Скачал openvpn-2.0.9-install.exe. Установил. Файервол виндовый отключен, посторонние не устанавливались. Все запустилось и законнектилось (Initialization Sequence Completed). Но коннект держится 2-2,5 минуты, а потом происходит реконнект ([RadugaVPN] Inactivity timeout (—ping-restart), restarting). После коннекта сразу начинаю пинговать 8.8.8.8. Пинг идет секунд 30-40 и потом пишет, что превышен интервал ожидания, хотя запрос по земле уходит.
Пробовал на двух платформах: 90C и 90Ku.
Подскажите пожалуйста в каком направлении копать?
вот кусок лога:
Fri Mar 09 114210 2012 OpenVPN 2.0.9 Win32-MinGW [SSL] [LZO] built on Feb 9 2007
Fri Mar 09 114210 2012 IMPORTANT OpenVPN’s default port number is now 1194, based on an official port number assignment by IANA. OpenVPN 2.0-beta16 and earlier used 5000 as the default port.
Fri Mar 09 114210 2012 LZO compression initialized
Fri Mar 09 114210 2012 Control Channel MTU parms [ L1574 D138 EF38 EB0 ET0 EL0 ]
Fri Mar 09 114210 2012 Data Channel MTU parms [ L1574 D1450 EF42 EB135 ET32 EL0 AF31 ]
Fri Mar 09 114210 2012 Local Options hash (VER=V4) ‘d79ca330’
Fri Mar 09 114210 2012 Expected Remote Options hash (VER=V4) ‘f7df56b8’
Fri Mar 09 114210 2012 UDPv4 link local [undef]
Fri Mar 09 114210 2012 UDPv4 link remote 217.17.162.255000
Fri Mar 09 114215 2012 TLS Initial packet from 217.17.162.255000, sid=f54a2229 278c80d4
Fri Mar 09 114217 2012 VERIFY OK depth=1, C=RUST=MWL=MOSCOWO=RadugaVPNemailAddress=support@telecom-service.net
Fri Mar 09 114217 2012 VERIFY OK nsCertType=SERVER
Fri Mar 09 114217 2012 VERIFY OK depth=0, C=RUST=MWO=RadugaVPNCN=RadugaVPNemailAddress=support@telecom-service.net
Fri Mar 09 114221 2012 Data Channel Encrypt Cipher ‘BF-CBC’ initialized with 128 bit key
Fri Mar 09 114221 2012 Data Channel Encrypt Using 160 bit message hash ‘SHA1’ for HMAC authentication
Fri Mar 09 114221 2012 Data Channel Decrypt Cipher ‘BF-CBC’ initialized with 128 bit key
Fri Mar 09 114221 2012 Data Channel Decrypt Using 160 bit message hash ‘SHA1’ for HMAC authentication
Fri Mar 09 114221 2012 Control Channel TLSv1, cipher TLSv1SSLv3 DHE-RSA-AES256-SHA, 1024 bit RSA
Fri Mar 09 114221 2012 [RadugaVPN] Peer Connection Initiated with 217.17.162.255000
Fri Mar 09 114222 2012 SENT CONTROL [RadugaVPN] ‘PUSH_REQUEST’ (status=1)
Fri Mar 09 114223 2012 PUSH Received control message ‘PUSH_REPLY,redirect-gateway,dhcp-option DNS 217.17.162.2,route-gateway 172.18.0.1,ping 30,ping-restart 120,route 0.0.0.0 0.0.0.0 172.18.0.1,dhcp-option DNS 217.17.162.2,ifconfig 172.18.104.134 255.255.0.0’
Fri Mar 09 114223 2012 OPTIONS IMPORT timers andor timeouts modified
Fri Mar 09 114223 2012 OPTIONS IMPORT —ifconfigup options modified
Fri Mar 09 114223 2012 OPTIONS IMPORT route options modified
Fri Mar 09 114223 2012 OPTIONS IMPORT —ip-win32 andor —dhcp-option options modified
Fri Mar 09 114223 2012 TAP-WIN32 device [Raduga] opened .Global{A53943B4-134D-408E-A5C6-480422068E34}.tap
Fri Mar 09 114223 2012 TAP-Win32 Driver Version 8.4
Fri Mar 09 114223 2012 TAP-Win32 MTU=1500
Fri Mar 09 114223 2012 Notified TAP-Win32 driver to set a DHCP IPnetmask of 172.18.104.134255.255.0.0 on interface {A53943B4-134D-408E-A5C6-480422068E34} [DHCP-serv 172.18.0.0, lease-time 31536000]
Fri Mar 09 114223 2012 Successful ARP Flush on interface [524296] {A53943B4-134D-408E-A5C6-480422068E34}
Fri Mar 09 114223 2012 TEST ROUTES 00 succeeded len=1 ret=0 a=0 ud=down
Fri Mar 09 114223 2012 Route Waiting for TUNTAP interface to come up…
Fri Mar 09 114224 2012 TEST ROUTES 00 succeeded len=1 ret=0 a=0 ud=down
Fri Mar 09 114224 2012 Route Waiting for TUNTAP interface to come up…
Fri Mar 09 114225 2012 TEST ROUTES 00 succeeded len=1 ret=0 a=0 ud=down
Fri Mar 09 114225 2012 Route Waiting for TUNTAP interface to come up…
Fri Mar 09 114226 2012 TEST ROUTES 00 succeeded len=1 ret=0 a=0 ud=down
Fri Mar 09 114226 2012 Route Waiting for TUNTAP interface to come up…
Fri Mar 09 114227 2012 TEST ROUTES 00 succeeded len=1 ret=0 a=0 ud=down
Fri Mar 09 114227 2012 Route Waiting for TUNTAP interface to come up…
Fri Mar 09 114228 2012 TEST ROUTES 00 succeeded len=1 ret=0 a=0 ud=down
Fri Mar 09 114228 2012 Route Waiting for TUNTAP interface to come up…
Fri Mar 09 114229 2012 TEST ROUTES 22 succeeded len=1 ret=1 a=0 ud=up
Fri Mar 09 114229 2012 route ADD 217.17.162.2 MASK 255.255.255.255 175.0.57.2
Fri Mar 09 114229 2012 Route addition via IPAPI succeeded
Fri Mar 09 114229 2012 route DELETE 0.0.0.0 MASK 0.0.0.0 175.0.57.2
Fri Mar 09 114229 2012 Route deletion via IPAPI succeeded
Fri Mar 09 114229 2012 route ADD 0.0.0.0 MASK 0.0.0.0 172.18.0.1
Fri Mar 09 114229 2012 Route addition via IPAPI succeeded
Fri Mar 09 114229 2012 route ADD 0.0.0.0 MASK 0.0.0.0 172.18.0.1
Fri Mar 09 114229 2012 Route addition via IPAPI succeeded
Fri Mar 09 114229 2012 Initialization Sequence Completed
Fri Mar 09 114438 2012 [RadugaVPN] Inactivity timeout (—ping-restart), restarting
Fri Mar 09 114438 2012 TCPUDP Closing socket
Fri Mar 09 114438 2012 SIGUSR1[soft,ping-restart] received, process restarting
Fri Mar 09 114438 2012 Restart pause, 2 second(s)
Fri Mar 09 114440 2012 IMPORTANT OpenVPN’s default port number is now 1194, based on an official port number assignment by IANA. OpenVPN 2.0-beta16 and earlier used 5000 as the default port.
Fri Mar 09 114440 2012 Re-using SSLTLS context
Fri Mar 09 114440 2012 LZO compression initialized
а вот так пинги идут
Ответ от 8.8.8.8 число байт=32 время=618мс TTL=49
Ответ от 8.8.8.8 число байт=32 время=636мс TTL=49
Ответ от 8.8.8.8 число байт=32 время=677мс TTL=49
Ответ от 8.8.8.8 число байт=32 время=625мс TTL=49
Ответ от 8.8.8.8 число байт=32 время=620мс TTL=49
Ответ от 8.8.8.8 число байт=32 время=717мс TTL=49
Ответ от 8.8.8.8 число байт=32 время=667мс TTL=50
Ответ от 8.8.8.8 число байт=32 время=638мс TTL=49
Ответ от 8.8.8.8 число байт=32 время=587мс TTL=50
Превышен интервал ожидания для запроса.
Превышен интервал ожидания для запроса.
Превышен интервал ожидания для запроса.
Превышен интервал ожидания для запроса.
Превышен интервал ожидания для запроса.
Превышен интервал ожидания для запроса.
Превышен интервал ожидания для запроса.
Превышен интервал ожидания для запроса.
Превышен интервал ожидания для запроса.
Записан
админы отписали что проверили вашу подписку, все корректно работает…
а вам из каких-то принципиальных соображений требуется ОпенВПН? почему не поставить Спринт с ТАПом? ну или глобакс?
Записан
1) Хочешь сделать что-то ХОРОШО, сделай это САМ…
2) Кто в саппорте служил — тот в цирке не смеется…
3) Настоящий мужчина скидок не просит и сдачу не берет!
Через спринте не получается полноценное расшаривание интернета. Очень нужно расшарить интернет на телефон. HTTP без проблем идет, а все остальное не работает, например GooglePlay.
Записан
Через спринте не получается полноценное расшаривание интернета. Очень нужно расшарить интернет на телефон. HTTP без проблем идет, а все остальное не работает, например GooglePlay.
а глобакс пробовали? я его когда по сетке раздавал-тестил-вроде нормально все работало…причем разработчик утверждает что там даже по DHCP можно, но это я потестить в тот раз не успел, а потом что-то времени не было…
но на связке теннексовской все раздается и на телефон и по вайфаю и шнурком…ну через глобакс понятно…
Если у вас не ямал-Си и решите попробовать-пишите номер договора, подключу возможность использовать новый глоб под радугу.
Записан
1) Хочешь сделать что-то ХОРОШО, сделай это САМ…
2) Кто в саппорте служил — тот в цирке не смеется…
3) Настоящий мужчина скидок не просит и сдачу не берет!
Глобакс не пробовал. Давайте попробуем. Договор 505993.
Записан
Глобакс не пробовал. Давайте попробуем. Договор 505993.
это ямал-си, я же написал что его не подключаю
Записан
1) Хочешь сделать что-то ХОРОШО, сделай это САМ…
2) Кто в саппорте служил — тот в цирке не смеется…
3) Настоящий мужчина скидок не просит и сдачу не берет!
Записан
перевел подписку на Ku.
подключил, пробуйте
Записан
1) Хочешь сделать что-то ХОРОШО, сделай это САМ…
2) Кто в саппорте служил — тот в цирке не смеется…
3) Настоящий мужчина скидок не просит и сдачу не берет!
Ура! Всё работает! И даже на телефон все без проблем расшарилось. Спасибо.
Записан
Договор 527315.немогу установить причину ошибки OpenVPN.ошибка Connecting to client has failed.постоянно выходит
Fri Dec 06 21:47:33 2013 OpenVPN 2.0.9 Win32-MinGW [SSL] [LZO] built on Feb 9 2007
Fri Dec 06 21:47:33 2013 IMPORTANT: OpenVPN’s default port number is now 1194, based on an official port number assignment by IANA. OpenVPN 2.0-beta16 and earlier used 5000 as the default port.
Fri Dec 06 21:47:33 2013 LZO compression initialized
Fri Dec 06 21:47:33 2013 Control Channel MTU parms [ L:1574 D:138 EF:38 EB:0 ET:0 EL:0 ]
Fri Dec 06 21:47:33 2013 Data Channel MTU parms [ L:1574 D:1450 EF:42 EB:135 ET:32 EL:0 AF:3/1 ]
Fri Dec 06 21:47:33 2013 Local Options hash (VER=V4): ‘d79ca330’
Fri Dec 06 21:47:33 2013 Expected Remote Options hash (VER=V4): ‘f7df56b8’
Fri Dec 06 21:47:33 2013 UDPv4 link local: [undef]
Fri Dec 06 21:47:33 2013 UDPv4 link remote: 80.81.209.162:55000
Fri Dec 06 21:47:33 2013 TLS: Initial packet from 80.81.209.162:55000, sid=3a080c5a 58103e5c
Fri Dec 06 21:47:34 2013 VERIFY OK: depth=1, /C=RU/ST=MW/L=MOSCOW/O=RadugaVPN/emailAddress=support@telecom-service.net
Fri Dec 06 21:47:34 2013 VERIFY OK: nsCertType=SERVER
Fri Dec 06 21:47:34 2013 VERIFY OK: depth=0, /C=RU/ST=MW/O=RadugaVPN/CN=RadugaVPN/emailAddress=support@telecom-service.net
Fri Dec 06 21:47:34 2013 Data Channel Encrypt: Cipher ‘BF-CBC’ initialized with 128 bit key
Fri Dec 06 21:47:34 2013 Data Channel Encrypt: Using 160 bit message hash ‘SHA1’ for HMAC authentication
Fri Dec 06 21:47:34 2013 Data Channel Decrypt: Cipher ‘BF-CBC’ initialized with 128 bit key
Fri Dec 06 21:47:34 2013 Data Channel Decrypt: Using 160 bit message hash ‘SHA1’ for HMAC authentication
Fri Dec 06 21:47:34 2013 Control Channel: TLSv1, cipher TLSv1/SSLv3 DHE-RSA-AES256-SHA, 1024 bit RSA
Fri Dec 06 21:47:34 2013 [RadugaVPN] Peer Connection Initiated with 80.81.209.162:55000
Fri Dec 06 21:47:36 2013 SENT CONTROL [RadugaVPN]: ‘PUSH_REQUEST’ (status=1)
Fri Dec 06 21:47:36 2013 PUSH: Received control message: ‘PUSH_REPLY,redirect-gateway,dhcp-option DNS 80.81.208.66,route-gateway 10.251.0.1,ping 30,ping-restart 120,route 0.0.0.0 0.0.0.0 10.251.0.1,dhcp-option DNS 80.81.209.162,ifconfig 10.251.166.84 255.255.0.0’
Fri Dec 06 21:47:36 2013 OPTIONS IMPORT: timers and/or timeouts modified
Fri Dec 06 21:47:36 2013 OPTIONS IMPORT: —ifconfig/up options modified
Fri Dec 06 21:47:36 2013 OPTIONS IMPORT: route options modified
Fri Dec 06 21:47:36 2013 OPTIONS IMPORT: —ip-win32 and/or —dhcp-option options modified
Fri Dec 06 21:47:36 2013 TAP-Win32 adapter ‘Raduga’ not found
Fri Dec 06 21:47:36 2013 Exiting
подскажите где копать .программа хр .SkyStar2 . антивирус отлючен.
Записан
Договор 527315.немогу установить причину ошибки OpenVPN.ошибка Connecting to client has failed.постоянно выходит
Fri Dec 06 21:47:33 2013 OpenVPN 2.0.9 Win32-MinGW [SSL] [LZO] built on Feb 9 2007
Fri Dec 06 21:47:33 2013 IMPORTANT: OpenVPN’s default port number is now 1194, based on an official port number assignment by IANA. OpenVPN 2.0-beta16 and earlier used 5000 as the default port.
Fri Dec 06 21:47:33 2013 LZO compression initialized
Fri Dec 06 21:47:33 2013 Control Channel MTU parms [ L:1574 D:138 EF:38 EB:0 ET:0 EL:0 ]
Fri Dec 06 21:47:33 2013 Data Channel MTU parms [ L:1574 D:1450 EF:42 EB:135 ET:32 EL:0 AF:3/1 ]
Fri Dec 06 21:47:33 2013 Local Options hash (VER=V4): ‘d79ca330’
Fri Dec 06 21:47:33 2013 Expected Remote Options hash (VER=V4): ‘f7df56b8’
Fri Dec 06 21:47:33 2013 UDPv4 link local: [undef]
Fri Dec 06 21:47:33 2013 UDPv4 link remote: 80.81.209.162:55000
Fri Dec 06 21:47:33 2013 TLS: Initial packet from 80.81.209.162:55000, sid=3a080c5a 58103e5c
Fri Dec 06 21:47:34 2013 VERIFY OK: depth=1, /C=RU/ST=MW/L=MOSCOW/O=RadugaVPN/emailAddress=support@telecom-service.net
Fri Dec 06 21:47:34 2013 VERIFY OK: nsCertType=SERVER
Fri Dec 06 21:47:34 2013 VERIFY OK: depth=0, /C=RU/ST=MW/O=RadugaVPN/CN=RadugaVPN/emailAddress=support@telecom-service.net
Fri Dec 06 21:47:34 2013 Data Channel Encrypt: Cipher ‘BF-CBC’ initialized with 128 bit key
Fri Dec 06 21:47:34 2013 Data Channel Encrypt: Using 160 bit message hash ‘SHA1’ for HMAC authentication
Fri Dec 06 21:47:34 2013 Data Channel Decrypt: Cipher ‘BF-CBC’ initialized with 128 bit key
Fri Dec 06 21:47:34 2013 Data Channel Decrypt: Using 160 bit message hash ‘SHA1’ for HMAC authentication
Fri Dec 06 21:47:34 2013 Control Channel: TLSv1, cipher TLSv1/SSLv3 DHE-RSA-AES256-SHA, 1024 bit RSA
Fri Dec 06 21:47:34 2013 [RadugaVPN] Peer Connection Initiated with 80.81.209.162:55000
Fri Dec 06 21:47:36 2013 SENT CONTROL [RadugaVPN]: ‘PUSH_REQUEST’ (status=1)
Fri Dec 06 21:47:36 2013 PUSH: Received control message: ‘PUSH_REPLY,redirect-gateway,dhcp-option DNS 80.81.208.66,route-gateway 10.251.0.1,ping 30,ping-restart 120,route 0.0.0.0 0.0.0.0 10.251.0.1,dhcp-option DNS 80.81.209.162,ifconfig 10.251.166.84 255.255.0.0’
Fri Dec 06 21:47:36 2013 OPTIONS IMPORT: timers and/or timeouts modified
Fri Dec 06 21:47:36 2013 OPTIONS IMPORT: —ifconfig/up options modified
Fri Dec 06 21:47:36 2013 OPTIONS IMPORT: route options modified
Fri Dec 06 21:47:36 2013 OPTIONS IMPORT: —ip-win32 and/or —dhcp-option options modified
Fri Dec 06 21:47:36 2013 TAP-Win32 adapter ‘Raduga’ not found
Fri Dec 06 21:47:36 2013 Exitingподскажите где копать .программа хр .SkyStar2 . антивирус отлючен.
Fri Dec 06 21:47:36 2013 TAP-Win32 adapter ‘Raduga’ not found
переименуйте ТАПочек
Записан
1) Хочешь сделать что-то ХОРОШО, сделай это САМ…
2) Кто в саппорте служил — тот в цирке не смеется…
3) Настоящий мужчина скидок не просит и сдачу не берет!
поясните что это такое переименуйте ТАПочек где переименовать.
Записан
поясните что это такое переименуйте ТАПочек где переименовать.
при установке ОпенВПН ставится ТАП-адаптер. вот его и надо переименовать именно в Raduga
Записан
1) Хочешь сделать что-то ХОРОШО, сделай это САМ…
2) Кто в саппорте служил — тот в цирке не смеется…
3) Настоящий мужчина скидок не просит и сдачу не берет!
- Печать
Страницы: 1 2 [3] 4 Вверх