Содержание
- Vmware view an ssl error occurred
- Vmware view an ssl error occurred
- Vmware view an ssl error occurred
Vmware view an ssl error occurred
as shown in figure below.
i’m doing VDI session test but some of the remote desktop session can’t be established and the Horizon Client show such message.
here’s my lab’s settings:
1. vSphere version:6.7U3
2. Horizon version:7.10
3. Horizon client version:5.2
4. windows 10 is utilized for client and target desktop VMs and the horizon client is installed in all the client VMs.
5. the client and target desktop pools’ type: instant clone, floating assignment
6. the «Do not verify server identity certificates» is configured in all the Horizon clients.
7. all the infrastructure and VMs are utilizing the same and the only one VLAN, does not need routing.
i also turned off all the firewalls on Horizon Connection server, client VMs and target VMs, however, when i perform the automatic VDI session test, some of the client VMs (randomly) always cannot connect to the target VMs.
since only some of the client VMs cannot connect to the Horizon Connection server, I doubt that there’s truly networking issues?
can anyone provide some clues for troubleshooting ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I checked the time sync between servers, hosts and desktops and corrected, unfortunately this did not help.
all the Horizon Clients are configured with «Do not verify server identity certificate» but the SSL error still occurred on dozens of windows client VMs randomly.
Now I believe that I found the ultimate solution:VMware Horizon View Client URI’s and SSL Issues
This post just saved my ass, according to my VDI test results.
By configuring the group policy of Horizon Client security setting in the golden image and use it for the desktop pool, the «SSL error» problem can be minimized or even solved completely.
if anyone knows a better solution please share.
@Amin thanks again for your professional answers, these are valuable for troubleshooting !
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Run the MMC and add the snap-in of certificates (for the local machine) in your client and Remove all related certificates (machine, web, . ) of the VDI servers from your client. Most of them are probably self-signed, So let it trust them again if you require, and next try to connect to the desktop pool. Tell us the result
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
thanks for answering!
i have a question,
my VDI test tool will automatically create some Active Directory users and control the client desktops’ local admin account, which is already logged in, to use these AD users access the Horizon Client for further testing.
so this SSL error issue seemed to be the client desktops’ problem? not the AD users which are created for Horizon Client login?
i’m wondering about whether i should add the certificate snap-in of either «my user account» or «computer account» in the client desktop.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
not the AD users which are created for Horizon Client login?
I don’t think it’s related to the AD Users, However you may need check the Horizon-side (Connection Servers) and Client-side logs and events more carefully.
i’m wondering about whether i should add the certificate snap-in of either «my user account» or «computer account» in the client desktop.
Add it for the Computer Account when you add the certmgr.msc in the MMC.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I did some work recently:
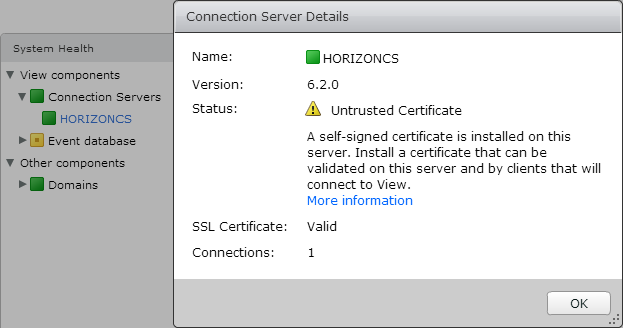
1. I followed this post’s instructions, and a self-signed certificate is installed on horizon connection server and the details of it in the connection server console is shown in figure below.
however, my VDI session tests’ results were not perfect and some client windows VMs still have the SSL error.
note that my client windows VMs are provisioned by the Horizon too.
so is it possible that the SSL error problem persist due to the «untrusted certificate»??
2. do I need to import the connection server’s certificate in to all the client VMs’ MMC?
3. I checked the Horizon Client’s logs on different windows desktops that had this «SSL error» and they all showed similar errors, as listed below:
ERROR (0750) [WinCDK] utils::ParseServerUrl : Unexpectedly unable to parse URL ».
ERROR (077C) [WinCDK] UpdateMgrCDS::CdsLogCallback : CdsUtil_RemoveFile: Unable to remove file C:UsersuserAppDataLocalTempcdstmp_1692_0
ERROR (077C) [WinCDK] UpdateMgrCDS::CdsLogCallback : Failed to finish active transfer for https://softwareupdate.vmware.com/horizon-clients/index.xml: CDS_HTTP_HOST_RESOLVE_ERROR
INFO (0750) [WinCDK] BaseServices::ErrorCallback : Error(Taskname:CdkSetLocaleTask, domain:54, code:35) Callback: Entry.
ERROR (0750) [WinCDK] DefaultErrorHandler::ProcessError : DefaultErrorHandler process error ‘Error: An SSL error occurred’ (code=35).
ERROR (0468) [WinCDK] UpdateMgrCDS::CdsLogCallback : CdsUtil_RemoveFile: Unable to remove file C:UsersuserAppDataLocalTempcdstmp_7824_0
2019-10-28T20:26:35.526-07:00| host-1128| I125: DictionaryLoad: Cannot open file «C:ProgramDataVMwareVMware Horizon Viewconfig.ini»: The system cannot find the file specified.
2019-10-28T20:26:35.526-07:00| host-1128| I125: [msg.dictionary.load.openFailed] Cannot open file «C:ProgramDataVMwareVMware Horizon Viewconfig.ini»: The system cannot find the file specified.
2019-10-28T20:26:35.526-07:00| host-1128| I125: PREF Optional preferences file not found at C:ProgramDataVMwareVMware Horizon Viewconfig.ini. Using default values.
2019-10-28T20:26:35.541-07:00| host-1128| I125: DictionaryLoad: Cannot open file «C:ProgramDataVMwareVMware Horizon Viewsettings.ini»: The system cannot find the file specified.
2019-10-28T20:26:35.541-07:00| host-1128| I125: [msg.dictionary.load.openFailed] Cannot open file «C:ProgramDataVMwareVMware Horizon Viewsettings.ini»: The system cannot find the file specified.
2019-10-28T20:26:35.541-07:00| host-1128| I125: PREF Optional preferences file not found at C:ProgramDataVMwareVMware Horizon Viewsettings.ini. Using default values.
2019-10-28T20:26:35.541-07:00| host-1128| I125: DictionaryLoad: Cannot open file «C:ProgramDataVMwareVMware Horizon Viewconfig.ini»: The system cannot find the file specified.
2019-10-28T20:26:35.541-07:00| host-1128| I125: [msg.dictionary.load.openFailed] Cannot open file «C:ProgramDataVMwareVMware Horizon Viewconfig.ini»: The system cannot find the file specified.
2019-10-28T20:26:35.541-07:00| host-1128| I125: PREF Optional preferences file not found at C:ProgramDataVMwareVMware Horizon Viewconfig.ini. Using default values.
2019-10-28T20:26:35.541-07:00| host-1128| I125: DictionaryLoad: Cannot open file «C:UsersuserAppDataRoamingVMwareconfig.ini»: The system cannot find the file specified.
2019-10-28T20:26:35.541-07:00| host-1128| I125: [msg.dictionary.load.openFailed] Cannot open file «C:UsersuserAppDataRoamingVMwareconfig.ini»: The system cannot find the file specified.
2019-10-28T20:26:35.541-07:00| host-1128| I125: PREF Optional preferences file not found at C:UsersuserAppDataRoamingVMwareconfig.ini. Using default values.
I attached the logs but I don’t think these error messages truly help.
Источник
Vmware view an ssl error occurred
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I’ve just begun a new job and the organization uses the Horizon Client and DoD CAC authentication. When I attempt to connect to the portal address I was provided, I am prompted to select a security certificate, then prompted for a PIN. After entering the PIN I get Error: An SSL Error Occurred and that’s it. I am not sure how to proceed at this point.
I’m running client v4.1.0 build 3977225 on a Windows 10 laptop. I tried running the support.bat with loglevel 3 and wound up with a 4MB zip files which I can provide if that’s helpful.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
When you use Linux client to authenticate the broker with PIV card, which is supported by Linux desktop smartcard redirection, you must add view.sslProtocolString = «TLSv1.1» configuration for the Linux client at
/.vmware/view-preferences to avoid SSL error.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks, but as mentioned I’m running Windows 10 not Linux. there doesn’t appear to be a view-preferences file anywhere in the VMWare directory.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
My bad. You can try disabling TLS 1.2 by adding registry values for DisabledByDefault to 1 and Enabled to 0 here:
This isn’t good practice (it lowers security for all of Windows) but may help isolate the problem. Ideally you shouldn’t have to do this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have a Windows 10 VM I dedicate to work. I VPN to the work network and then use Horizon client to get a desktop. This was all working fine up until I had my CAC renewed a week ago. Even though I had all the intermediate and root CA certs loaded, I started getting the «An SSL error has occurred» message. Previously I was using the Windows built-in smart card support and it was fine, no issues with using my CAC for VPN or the Horizon client.
I tried upgrading the Horizon client, several registry entries. nothing helped. The VPN client continued to work fine with the new CAC.
My «fix» was to install ActivClient 7.1. I am not sure what it did, but it stopped that stupid error from popping up. I have seen the SSL error once since installing, but an immediate reconnect fixed it.
If you are a DoD contractor you might be able to get ActivClient for free. Look on militarycac.com for some links (I had access to AKO). If not, I think it’s $35 to purchase a copy.
I hope this helps. It’s a really frustrating and unhelpful error message.
Источник
Vmware view an ssl error occurred
I’ve been using v3.0 View client without issue for a while. Today I started getting an SSL error sporadically while connected, note this did not disconnect the session.
Anyhow I disconnected, now when attempting to connect to the site I get the error message after clicking on the connection server icon and it doesn’t go any further. I’m familiar with the VDI infrastructure at the other end and there hasn’t been any changes. Also, I moved to a windows machine on the same network as my Mac and can connect to the same site with the windows View client ok.
Steps taken so far, I’ve installed the latest version of the client v3.2 and reboot the Mac, no change.
Client log file and wireshark is shown below,
any help appreciated,
Nov 13 17:40:55.075: vmware-view 264| TaskCombiner: CdkGetLaunchItemsTask(TODO) added, group task num:1, total task num:7.
Nov 13 17:40:55.077: vmware-view 264| TaskCombiner: CdkGetUserGlobalPreferencesTask(TODO) added, group task num:2, total task num:8.
Nov 13 17:40:55.136: vmware-view 264| TaskCombiner: CdkGetTunnelConnectionTask(TODO) added, group task num:3, total task num:9.
Nov 13 17:40:55.136: vmware-view 264| TaskCombiner: Group Tasks(3):CdkGetLaunchItemsTask(TODO),CdkGetUserGlobalPreferencesTask(TODO),CdkGetTunnelConnectionTask(TODO),
Nov 13 17:40:55.138: vmware-view 264| TaskCombiner: CdkGetConfigurationTask(TODO) added, group task num:1, total task num:10.
Nov 13 17:40:55.139: vmware-view 264| TaskCombiner: CdkSetLocaleTask(TODO) added, group task num:2, total task num:11.
Nov 13 17:40:55.139: vmware-view 264| TaskCombiner: Group Tasks(2):CdkGetConfigurationTask(TODO),CdkSetLocaleTask(TODO),
Nov 13 17:40:55.140: vmware-view 264| TaskCombiner: CreateRequest for CdkSetLocaleTask(REDY).
Nov 13 17:40:55.175: vmware-view 264| CdkUtil_SetLocalAddress: local ip address 192.168.1.226 is being picked.
Nov 13 17:40:55.175: vmware-view 264| Send request successful: 0x10396ebb0
Nov 13 17:40:55.573: vmware-view 264| Verify server’s certificate for Request 0x101d276e0
Nov 13 17:40:55.573: vmware-view 264| Find rpc request 0x101d276e0 from list
Nov 13 17:41:05.596: vmware-view 264| Common name entry 2 matches hostname vdi.example.com
Nov 13 17:41:05.596: vmware-view 264| Skipping non-useful EKU: TLS Web Client Authentication
Nov 13 17:41:05.596: vmware-view 264| Found a valid EKU: TLS Web Server Authentication
Nov 13 17:41:05.602: vmware-view 264| CdkRpc_HandleResponsesAsync: Handle Response with rpc call id: 7.
Nov 13 17:41:05.602: vmware-view 264| Got a response to request 7.
Nov 13 17:41:05.602: vmware-view 264| TaskCombiner: CdkGetLaunchItemsTask(FAIL) removed, group task num:2, total task num:10.
Nov 13 17:41:05.602: vmware-view 264| TaskCombiner: CdkGetUserGlobalPreferencesTask(FAIL) removed, group task num:1, total task num:9.
Nov 13 17:41:05.602: vmware-view 264| TaskCombiner: CdkGetTunnelConnectionTask(FAIL) removed, group task num:0, total task num:8.
Nov 13 17:41:05.602: vmware-view 264| TaskCombiner: CdkGetConfigurationTask(FAIL) removed, group task num:1, total task num:7.
Nov 13 17:41:05.602: vmware-view 264| -[CdkWindowController errorCallback:forTask:], CdkSetLocaleTask, task error: Error: An SSL error occurred, domain:cdk-basic-http-error, code:35
Источник
,
last updated February 17, 2016, in
This is a description of a quick and dirty way to get SSL to work correctly in a VMware Horizon View installation in a lab environment. Do not do this in production!
The Situation
The Horizon View Connection Server installer creates a self-signed certificate which it places in the computer’s personal certificate store. This certificate’s root is not trusted by anyone, least of all by the clients trying to connect to your apps and desktops.
Establishing Trust
To make the default self-signed certificate work correctly you need to export it from the computer’s personal certificate store and then re-import it in the trusted root certificate store.
Exporting
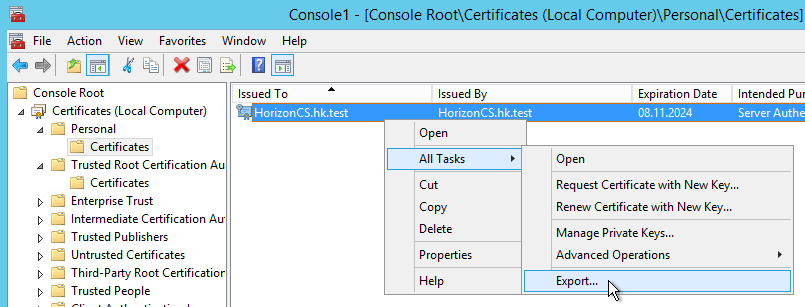
It is OK to export without a private key; leave the file format at the default.
Importing – Connection Server
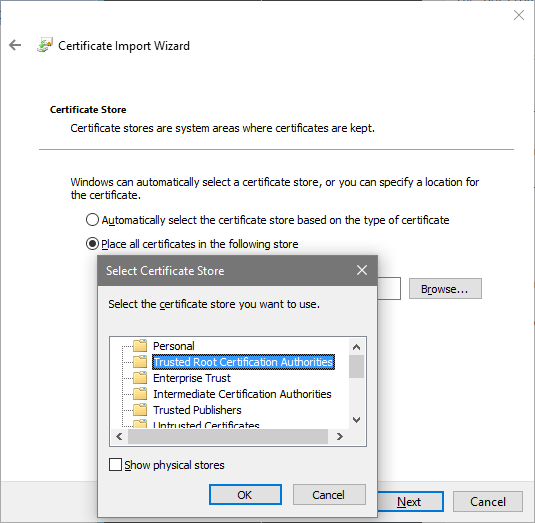
When re-importing the key on the Horizon View Connection Server manually select the computer’s Trusted Root Certification Authorities store:
After the import restart the Connection Server machine. View Administrator should now display the Connection Server status in green (certificate valid):
Importing – Clients
Clients that connect to Horizon need the certificate imported as trusted root certificate in the same way as described for the Connection Server above.
Name Resolution
Clients connecting to Horizon View need to be able to resolve the name as it is stored in the certificate, in all likelihood fully qualified. If your (lab) clients use a different DNS server than the Horizon installation the simplest solution is to add the Connection Server’s name and IP address to each client’s hosts file.
About the Author
Helge Klein (ex CTP, MVP and vExpert) worked as a consultant and developer before founding vast limits, the uberAgent company. Helge applied his extensive knowledge in IT infrastructure projects and architected the user profile management product whose successor is now available as Citrix Profile Management. Helge is the author of the popular tools Delprof2 and SetACL. He has presented at Citrix Synergy, BriForum, E2EVC, Splunk .conf and many other events. Helge is very active in the IT community and has co-founded Virtualization Community NRW (VCNRW).
Read more
This is the second part in a blog series of how to install and configure VMware Horizon View 5.2. In Part 1 we did the basic connection server install, and installed Adobe Flash player. Next up is configuring a trusted SSL certificate for VMware Horizon View.
There are a number of ways to request and mint SSL certificates. You could use a commercial CA, Microsoft internal CA or another flavor of CA if you wish. Unlike some vCenter components the View SSL certificate does not need any unusual properties beyond Server Authentication usage. No unique OU properties, no client authentication, no data encryption, etc. I would advise using a SAN certificate, so you can access the server via shortname and the FQDN without certificate errors.
I am using an Enterprise online Windows Server 2012 Certificate Authority in this example. The CA has been pre-configured to issue a variety of certificate template types, one of which I called “Server Authentication-SAN”. You don’t need a template with this name, but the template needs to support the SAN field, which the basic “computer” template will NOT. For general steps on how to configure a custom certificate template for a Microsoft CA, see my article here.
Additional articles in this series:
VMware Horizon View 5.2 Part 1: Basic Installation
VMware Horizon VIew 5.2 Part 3: Initial Config
VMware Horizon View 5.2 Part 4: VM and Pool Creation
VMware Horizon View SSL Certificate Installation
1. On the View server open a blank MMC. Add the Certificates snap-in and chose Computer account.
2. Open the Personal certificates container and expand Certificates. Depending on the auto-enrollment policy (if any) in your domain, you may find two or more certificates listed. One of the certificates will be the self-signed VMware certificate that we no longer want to use. You can see this by looking at the “Issued By” field.
3. Now we want to request a new certificate from our online CA via a the certificate request wizard. Right click on Certificates, select All Tasks, then Request New certificate.
4. A couple of clicks into the wizard you should see an Active Directory Enrollment Policy listed.
5. Click Next and you should now see one or more templates that your CA administrator has published. If you use the standard “Computer” template the CA will strip any SAN values that you enter. So if you want a SAN certificate you will need to use a CA template that allows for such usage. Since SAN certificate are not uncommon, I already had a certificate template ready. Again, for a link how to create a custom CA template see my article here.
6. Check the box next to your SAN template. Click on the line of text next to the yellow warning. On the Subject tab you now need to configure the “Common name” for the subject name and add two “DNS” alternative names. Use the View server FQDN for the Subject Name and add both the FQDN and short name DNS names for the alternative name, as shown below.
7. Click on the General tab and enter a friendly name of vdm.
8. Click on the Private Key tab and under Key Options allow the private key to be exportable.
9. Click OK then click on Enroll. If all goes well you should get a succeeded message.
10. In the MMC double click on the new certificate and validate all properties, including Subject Alternative Name are properly populated.
11. At this point you can either delete the self-signed VMware certificate, OR you must remove the vdm friendly name from the VMware certificate. View looks for a single certificate with the vdm friendly name. To remove the VDM friendly name from the VMware certificate just right click on the VMware certificate and select Properties, then delete the friendly name.
12. Restart all of the View services on your View server. The critical one is the VMware View Security Gateway Component. If it stops running shortly after you start it, there’s a problem with your certificate. The most common cause is having a certificate that does NOT allow exporting of the private key. You may see something like:
A fatal error occurred when attempting to access the SSL server credential private key. The error code returned from the cryptographic module is 0x8009030d. The internal error state is 10001.
13. Now you can launch the View administrator and change the URL to either the server’s short name or FQDN, and you should NOT see any browser SSL errors.
14. Once you login you can click on the Dashboard icon on the left and view the server details for your connection server. It should show a valid SSL certificate.
Congratulations on configuring your View Connection Server SSL certificate. Very easy, and straight forward (vCenter team are you listening?). Next up is Part 3, where configure basic parameters in the View Connection Server.