Introduction
This document describes a troubleshooting scenario which applies to applications that do not work through the Cisco AnyConnect VPN Client.
Prerequisites
Requirements
There are no specific requirements for this document.
Components Used
The information in this document is based on a Cisco Adaptive Security Appliance (ASA) that runs Version 8.x.
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, make sure that you understand the potential impact of any command.
Troubleshooting Process
This typical troubleshooting scenario applies to applications that do not work through the Cisco AnyConnect VPN Client for end-users with Microsoft Windows-based computers. These sections address and provide solutions to the problems:
- Installation and Virtual Adapter Issues
- Disconnection or Inability to Establish Initial Connection
- Problems with Passing Traffic
- AnyConnect Crash Issues
- Fragmentation / Passing Traffic Issues
Installation and Virtual Adapter Issues
Complete these steps:
- Obtain the device log file:
- Windows XP / Windows 2000:
Windowssetupapi.log
- Windows Vista:
Note: Hidden folders must be made visible in order to see these files.
WindowsInfsetupapi.app.log
WindowsInfsetupapi.dev.log
If you see errors in the setupapi log file, you can turn up verbosity to 0x2000FFFF.
- Windows XP / Windows 2000:
- Obtain the MSI installer log file:
If this is an initial web deploy install, this log is located in the per-user temp directory.
- Windows XP / Windows 2000:
Documents and Settings<username>Local SettingsTemp
- Windows Vista:
Users<username>AppDataLocalTemp
If this is an automatic upgrade, this log is in the temp directory of the system:
WindowsTemp
The filename is in this format: anyconnect-win-x.x.xxxx-k9-install-yyyyyyyyyyyyyy.log. Obtain the most recent file for the version of the client you want to install. The x.xxxx changes based on the version, such as 2.0.0343, and yyyyyyyyyyyyyy is the date and time of the install.
- Windows XP / Windows 2000:
- Obtain the PC system information file:
- From a Command Prompt/DOS box, type this:
- Windows XP / Windows 2000:
winmsd /nfo c:msinfo.nfo
- Windows Vista:
msinfo32 /nfo c:msinfo.nfo
Note: After you type into this prompt, wait. It can take between two to five minutes for the file to complete.
- Windows XP / Windows 2000:
- Obtain a systeminfo file dump from a Command Prompt:
Windows XP and Windows Vista:
systeminfo c:sysinfo.txt
- From a Command Prompt/DOS box, type this:
Refer to AnyConnect: Corrupt Driver Database Issue in order to debug the driver issue.
Disconnection or Inability to Establish Initial Connection
If you experience connection problems with the AnyConnect client, such as disconnections or the inability to establish an initial connection, obtain these files:
- The configuration file from the ASA in order to determine if anything in the configuration causes the connection failure:
From the console of the ASA, type
write net x.x.x.x:ASA-Config.txtwherex.x.x.xis the IP address of a TFTP server on the network.OR
From the console of the ASA, type
show running-config. Let the configuration complete on the screen, then cut-and-paste to a text editor and save. - The ASA event logs:
- In order to enable logging on the ASA for auth, WebVPN, Secure Sockets Layer (SSL), and SSL VPN Client (SVC) events, issue these CLI commands:
config terminal
logging enable
logging timestamp
logging class auth console debugging
logging class webvpn console debugging
logging class ssl console debugging
logging class svc console debugging - Originate an AnyConnect session and ensure that the failure can be reproduced. Capture the logging output from the console to a text editor and save.
- In order to disable logging, issue
no logging enable.
- In order to enable logging on the ASA for auth, WebVPN, Secure Sockets Layer (SSL), and SSL VPN Client (SVC) events, issue these CLI commands:
- The Cisco AnyConnect VPN Client log from the Windows Event Viewer of the client PC:
- Choose Start > Run.
- Enter:
eventvwr.msc /s
- Right-click the Cisco AnyConnect VPN Client log, and select Save Log File as AnyConnect.evt.
Note: Always save it as the .evt file format.
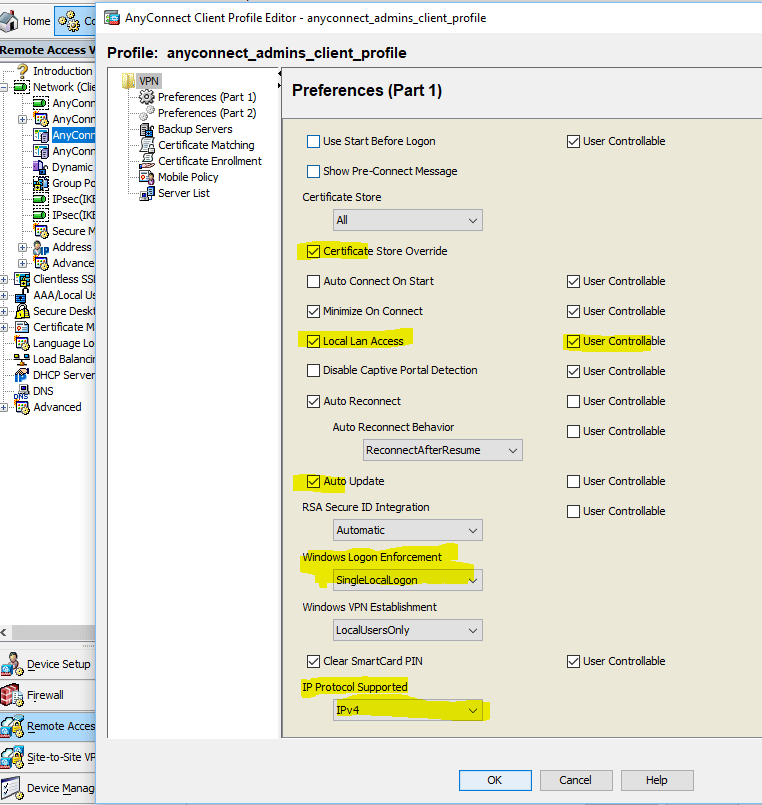
If the user cannot connect with the AnyConnect VPN Client, the issue might be related to an established Remote Desktop Protocol (RDP) session or Fast User Switching enabled on the client PC. The user can see the AnyConnect profile settings mandate a single local user, but multiple local users are currently logged into your computer. A VPN connection will not be established error message error on the client PC. In order to resolve this issue, disconnect any established RDP sessions and disable Fast User Switching. This behavior is controlled by the Windows Logon Enforcement attribute in the client profile, however currently there is no setting that actually allows a user to establish a VPN connection while multiple users are logged on simultaneously on the same machine. Enhancement request CSCsx15061 
Note: Make sure that port 443 is not blocked so the AnyConnect client can connect to the ASA.
When a user cannot connect the AnyConnect VPN Client to the ASA, the issue might be caused by an incompatibility between the AnyConnect client version and the ASA software image version. In this case, the user receives this error message: The installer was not able to start the Cisco VPN client, clientless access is not available.
In order to resolve this issue, upgrade the AnyConnect client version to be compatible with the ASA software image.
When you log in the first time to the AnyConnect, the login script does not run. If you disconnect and log in again, then the login script runs fine. This is the expected behavior.
When you connect the AnyConnect VPN Client to the ASA, you might receive this error: User not authorized for AnyConnect Client access, contact your administrator.
This error is seen when the AnyConnect image is missing from the ASA. Once the image is loaded to the ASA, AnyConnect can connect without any issues to the ASA.
This error can be resolved by disabling Datagram Transport Layer Security (DTLS). Go to Configuration > Remote Access VPN > Network (Client) Access > AnyConnect Connection Profiles and uncheck the Enable DTLS check box. This disables DTLS.
The dartbundle files show this error message when the user gets disconnected: TUNNELPROTOCOLDPDMGR_ERROR_NO_DPD_RESPONSE:The secure gateway failed to respond to Dead Peer Detection packets. This error means that the DTLS channel was torn due to Dead Peer Detection (DPD) failure. This error is resolved if you tweak the DPD keepalives and issue these commands:
webvpn
svc keepalive 30
svc dpd-interval client 80
svc dpd-interval gateway 80
The svc keepalive and svc dpd-interval commands are replaced by the anyconnect keepalive and anyconnect dpd-interval commands respectively in ASA Version 8.4(1) and later as shown here:
webvpn
anyconnect ssl keepalive 15
anyconnect dpd-interval client 5
anyconnect dpd-interval gateway 5
Problems with Passing Traffic
When problems are detected with passing traffic to the private network with an AnyConnect session through the ASA, complete these data-gathering steps:
- Obtain the output of the show vpn-sessiondb detail svc filter name <username> ASA command from the console. If the output shows
Filter Name: XXXXX, then gather the output for show access-list XXXXX. Verify that the access-list XXXXX does not block the intended traffic flow. - Export the AnyConnect statistics from AnyConnect VPN Client > Statistics > Details > Export (AnyConnect-ExportedStats.txt).
- Check the ASA configuration file for nat statements. If Network Address Translation (NAT) is enabled, these must exempt data that returns to the client as a result of NAT. For example, to NAT exempt (nat 0) the IP addresses from the AnyConnect pool, use this on the CLI:
access-list in_nat0_out extended permit ip any 10.136.246.0 255.255.255.0
ip local pool IPPool1 10.136.246.1-10.136.246.254 mask 255.252.0.0
nat (inside) 0 access-list in_nat0_out - Determine if the tunneled default gateway needs to be enabled for the setup. The traditional default gateway is the gateway of last resort for non-decrypted traffic.
Example:
!--- Route outside 0 0 is an incorrect statement.
route outside 0 0 10.145.50.1
route inside 0 0 10.0.4.2 tunneledFor example, if the VPN Client needs to access a resource which is not in the routing table of the VPN Gateway, the packet is routed through the standard default gateway. The VPN gateway does not need the complete internal routing table in order to resolve this. The tunneled keyword can be used in this instance.
- Verify if the AnyConnect traffic is dropped by the inspection policy of the ASA. You could exempt the specific application that is used by AnyConnct client if you implement the Modular Policy Framework of Cisco ASA. For example, you could exempt the skinny protocol with these commands.
ASA(config)# policy-map global_policy
ASA(config-pmap)# class inspection_default
ASA(config-pmap-c)# no inspect skinny
AnyConnect Crash Issues
Complete these data-gathering steps:
- Ensure that the Microsoft Utility Dr Watson is enabled. In order to do this, choose Start > Run, and run Drwtsn32.exe. Configure this and click OK:
Number of Instructions : 25
Number of Errors To Save : 25
Crash Dump Type : Mini
Dump Symbol Table : Checked
Dump All Thread Contexts : Checked
Append To Existing Log File : Checked
Visual Notification : Checked
Create Crash Dump File : CheckedWhen the crash occurs, gather the .log and .dmp files from C:Documents and SettingsAll UsersApplication DataMicrosoftDr Watson. If these files appear to be in use, then use ntbackup.exe.
- Obtain the Cisco AnyConnect VPN Client log from the Windows Event Viewer of the client PC:
- Choose Start > Run.
- Enter:
eventvwr.msc /s
- Right-click the Cisco AnyConnect VPN Client log, and select Save Log File As AnyConnect.evt.
Note: Always save it as the .evt file format.
Fragmentation / Passing Traffic Issues
Some applications, such as Microsoft Outlook, do not work. However, the tunnel is able to pass other traffic such as small pings.
This can provide clues as to a fragmentation issue in the network. Consumer routers are particularly poor at packet fragmentation and reassembly.
Try a scaling set of pings in order to determine if it fails at a certain size. For example, ping -l 500, ping -l 1000, ping -l 1500, ping -l 2000.
It is recommended that you configure a special group for users that experience fragmentation, and set the SVC Maximum Transition Unit (MTU) for this group to 1200. This allows you to remediate users who experience this issue, but not impact the broader user base.
Problem
TCP connections hang once connected with AnyConnect.
Solution
In order to verify if your user has a fragmentation issue, adjust the MTU for AnyConnect clients on the ASA.
ASA(config)#group-policy <name> attributes
webvpn
svc mtu 1200
Uninstall Automatically
Problem
The AnyConnect VPN Client uninstalls itself once the connection terminates. The client logs show that keep installed is set to disabled.
Solution
AnyConnect uninstalls itself despite that the keep installed option is selected on the Adaptive Security Device Manager (ASDM). In order to resolve this issue, configure the svc keep-installer installed command under group-policy.
Issue Populating the Cluster FQDN
Problem: AnyConnect client is pre-populated with the hostname instead of the cluster Fully Qualified Domain Name (FQDN).
When you have a load-balancing cluster set up for SSL VPN and the client attempts to connect to the cluster, the request is redirected to the node ASA and the client logs in successfully. After some time, when the client tries to connect to the cluster again, the cluster FQDN is not seen in the Connect to entries. Instead, the node ASA entry to which the client has been redirected is seen.
Solution
This occurs because the AnyConnect client retains the host name to which it last connected. This behavior is observed and a bug has been filed. For complete details about the bug, refer to Cisco bug ID CSCsz39019. The suggested workaround is to upgrade the Cisco AnyConnect to Version 2.5.
Backup Server List Configuration
A backup server list is configured in case the main server selected by the user is not reachable. This is defined in the Backup Server pane in the AnyConnect profile. Complete these steps:
- Download the AnyConnect Profile Editor (registered customers only) . The file name is AnyConnectProfileEditor2_4_1.jar.
- Create an XML file with the AnyConnect Profile Editor.
- Go to the server list tab.
- Click Add.
- Type the main server on the Hostname field.
- Add the backup server below the backup server list on the Host address field. Then, click Add.
- Once you have the XML file, you need to assign it to the connection you use on the ASA.
- In ASDM, choose Configuration > Remote Access VPN > Network (Client) Access > AnyConnect Connection Profiles.
- Select your profile and click Edit.
- Click Manage from the Default Group Policy section.
- Select your group-policy and click Edit.
- Select Advanced and then click SSL VPN Client.
- Click New. Then, you need to type a name for the Profile and assign the XML file.
- Connect the client to the session in order to download the XML file.
AnyConnect: Corrupt Driver Database Issue
This entry in the SetupAPI.log file suggests that the catalog system is corrupt:
W239 driver signing class list "C:WINDOWSINFcertclas.inf" was missing or invalid. Error 0xfffffde5: Unknown Error., assuming all device classes are subject to driver signing policy.
You can also receive this error message: Error(3/17): Unable to start VA, setup shared queue, or VA gave up shared queue.
You can receive this log on the client: "The VPN client driver has encountered an error".
Repair
This issue is due to Cisco bug ID CSCsm54689. In order to resolve this issue, make sure that Routing and Remote Access Service is disabled before you start AnyConnect. If this does not resolve the issue, complete these steps:
- Open a command prompt as an Administrator on the PC (elevated prompt on Vista).
- Run
net stop CryptSvc. - Run:
esentutl /p%systemroot%System32catroot2
{F750E6C3-38EE-11D1-85E5-00C04FC295EE}catdb - When prompted, choose OK in order to attempt the repair.
- Exit the command prompt.
- Reboot.
Failed Repair
If the repair fails, complete these steps:
- Open a command prompt as an Administrator on the PC (elevated prompt on Vista).
- Run
net stop CryptSvc. - Rename the %WINDIR%system32catroot2 to catroot2_old directory.
- Exit the command prompt.
- Reboot.
Analyze the Database
You can analyze the database at any time in order to determine if it is valid.
- Open a command prompt as an Admimistrator on the PC.
- Run:
esentutl /g%systemroot%System32catroot2
{F750E6C3-38EE-11D1-85E5-00C04FC295EE}catdbRefer to System Catalog Database Integrity for more information.
Error Messages
Error: Unable to Update the Session Management Database
While the SSL VPN is connected through a web browser, the Unable to Update the Session Management Database. error message appears, and the ASA logs show %ASA-3-211001: Memory allocation Error. The adaptive security appliance failed to allocate RAM system memory.
Solution 1
This issue is due to Cisco bug ID CSCsm51093. In order to resolve this issue, reload the ASA or upgrade the ASA software to the interim release mentioned in the bug. Refer to Cisco bug ID CSCsm51093 
Solution 2
This issue can also be resolved if you disable threat-detection on ASA if threat-detection is used.
Error: «Module c:Program FilesCiscoCisco AnyConnect VPN Clientvpnapi.dll failed to register»
When you use the AnyConnect client on laptops or PCs, an error occurs during the install:
"Module C:Program FilesCiscoCisco AnyConnect VPN Clientvpnapi.dll failed
to register..."
When this error is encountered, the installer cannot move forward and the client is removed.
Solution
These are the possible workarounds to resolve this error:
- The latest AnyConnect client is no longer officially supported with Microsoft Windows 2000. It is a registry problem with the 2000 computer.
- Remove the VMware applications. Once AnyConnect is installed, VMware applications can be added back to the PC.
- Add the ASA to their trusted sites.
- Copy these files from the ProgramFilesCiscoCiscoAnyconnect folder to a new folder and run the regsvr32 vpnapi.dll command prompt:
- vpnapi.dll
- vpncommon.dll
- vpncommoncrypt.dll
- Reimage the operating system on the laptop/PC.
The log message related to this error on the AnyConnect client looks similar to this:
DEBUG: Error 2911: Could not remove the folderC:Program FilesCiscoCisco AnyConnect
VPN Client.
The installer has encountered an unexpected error installing this package. This may
indicate a problem with this package. The error code is 2911. The arguments are:
C:Program FilesCiscoCisco AnyConnect VPN Client, ,
DEBUG: Error 2911: Could not remove the folder C:Program FilesCiscoCisco AnyConnect
VPN Client.
The installer has encountered an unexpected error installing this package. This may
indicate a problem with this package. The error code is 2911. The arguments are:
C:Program FilesCiscoCisco AnyConnect VPN Client, ,
Info 1721. There is a problem with this Windows Installer package. A program required for
this install to complete could not be run. Contact your support personnel or package
vendor. Action: InstallHelper.exe, location: C:Program FilesCiscoCisco AnyConnect VPN
ClientInstallHelper.exe, command: -acl "C:Documents and SettingsAll UsersApplication
DataCiscoCisco AnyConnect VPN Client\" -r
Error: «An error was received from the secure gateway in response to the VPN negotiation request. Please contact your network administrator»
When clients try to connect to the VPN with the Cisco AnyConnect VPN Client, this error is received.
This message was received from the secure gateway:
«Illegal address class» or «Host or network is 0» or «Other error»
Solution
The issue occurs because of the ASA local IP pool depletion. As the VPN pool resource is exhausted, the IP pool range must be enlarged.
Cisco bug ID is CSCsl82188 is filed for this issue. This error usually occurs when the local pool for address assignment is exhausted, or if a 32-bit subnet mask is used for the address pool. The workaround is to expand the address pool and use a 24-bit subnet mask for the pool.
Error: Session could not be established. Session limit of 2 reached.
When you try to connect more than two clients with the AnyConnect VPN Client, you receive the Login Failed error message on the Client and a warning message in the ASA logs that states Session could not be established. Session limit of 2 reached. I have the AnyConnect essential license on the ASA, which runs Version 8.0.4.
Solution 1
This error occurs because the AnyConnect essential license is not supported by ASA version 8.0.4. You need to upgrade the ASA to version 8.2.2. This resolves the error.
Note: Regardless of the license used, if the session limit is reached, the user will receive the login failed error message.
Solution 2
This error can also occur if the vpn-sessiondb max-anyconnect-premium-or-essentials-limit session-limit command is used to set the limit of VPN sessions permitted to be established. If the session-limit is set as two, then the user cannot establish more than two sessions even though the license installed supports more sessions. Set the session-limit to the number of VPN sessions required in order to avoid this error message.
Error: Anyconnect not enabled on VPN server while trying to connect anyconnect to ASA
You receive the Anyconnect not enabled on VPN server error message when you try to connect AnyConnect to the ASA.
Solution
This error is resolved if you enable AnyConnect on the outside interface of the ASA with ASDM. For more information on how to enable AnyConnect on the outside interface, refer to Configure Clientless SSL VPN (WebVPN) on the ASA.
Error:- %ASA-6-722036: Group client-group User xxxx IP x.x.x.x Transmitting large packet 1220 (threshold 1206)
The %ASA-6-722036: Group < client-group > User < xxxx > IP < x.x.x.x> Transmitting large packet 1220 (threshold 1206) error message appears in the logs of the ASA. What does this log mean and how is this resolved?
Solution
This log message states that a large packet was sent to the client. The source of the packet is not aware of the MTU of the client. This can also be due to compression of non-compressible data. The workaround is to turn off the SVC compression with the svc compression none command. This resolves the issue.
Error: The secure gateway has rejected the agent’s vpn connect or reconnect request.
When you connect to the AnyConnect Client, this error is received: "The secure gateway has rejected the agent's vpn connect or reconnect request. A new connection requires re-authentication and must be started manually. Please contact your network administrator if this problem persists. The following message was received from the secure gateway: no assigned address".
This error is also received when you connect to the AnyConnect Client: "The secure gateway has rejected the connection attempt. A new connection attempt to the same or another secure gateway is needed, which requires re-authentication. The following message was received from the secure gateway:Host or network is 0".
This error is also received when you connect to the AnyConnect Client: "The secure gateway has rejected the agent's vpn connect or reconnect request. A new connection requires a re-authentication and must be started manually. Please contact the network administrator if the problem persists. The following message was received from the secure gateway: No License".
Solution
The router was missing pool configuration after reload. You need to add the concerned configuration back to the router.
Router#show run | in pool
ip local pool SSLPOOL 192.168.30.2 192.168.30.254
svc address-pool SSLPOO
The "The secure gateway has rejected the agent's vpn connect or reconnect request. A new connection requires a re-authentication and must be started manually. Please contact the network administrator if the problem persists. The following message was received from the secure gateway: No License" error occurs when the AnyConnect mobility license is missing. Once the license is installed, the issue is resolved.
Error: «Unable to update the session management database»
When you try to authenticate in WebPortal, this error message is received: "Unable to update the session management database".
Solution
This problem is related to memory allocation on the ASA. This issue is mostly encountered when the ASA Version is 8.2.1. Originally, this requires a 512MB RAM for its complete functionality.
As a permanent workaround, upgrade the memory to 512MB.
As a temporary workaround, try to free the memory with these steps:
- Disable the threat-detection.
- Disable SVC compression.
- Reload the ASA.
Error: «The VPN client driver has encountered an error»
This is an error message obtained on the client machine when you try to connect to AnyConnect.
Solution
In order to resolve this error, complete this procedure in order to manually set the AnyConnect VPN agent to Interactive:
- Right-click My Computer > Manage > Services and Applications > Services > and select the Cisco AnyConnect VPN Agent.
- Right-click Properties, then log on, and select Allow service to interact with the desktop.
This sets the registry Type value DWORD to 110 (default is 010) for the HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesvpnagent.
Note: If this is to be used, then the preference would be to use the .MST transform in this instance. This is because if you set this manually with these methods, it requires that this be set after every install/upgrade process. This is why there is a need to identify the application that causes this problem.
When Routing and Remote Access Service (RRAS) is enabled on the Windows PC, AnyConnect fails with the
The VPN client driver has encountered an error.error message. In order to resolve this issue, make sure that Routing and RRAS is disabled before starting AnyConnect. Refer to Cisco bug ID CSCsm54689 for more information.
Error: «Unable to process response from xxx.xxx.xxx.xxx»
AnyConnect clients fail to connect to a Cisco ASA. The error in the AnyConnect window is "Unable to process response from xxx.xxx.xxx.xxx".
Solution
In order to resolve this error, try these workarounds:
- Remove WebVPN from the ASA and reenable it.<
- Change the port number to 444 from the existing 443 and reenable it on 443.
For more information on how to enable WebVPN and change the port for WebVPN, refer to this Solution.
Error: «Login Denied , unauthorized connection mechanism , contact your administrator»
AnyConnect clients fail to connect to a Cisco ASA. The error in the AnyConnect window is "Login Denied , unauthorized connection mechanism , contact your administrator".
Solution
This error message occurs mostly because of configuration issues that are improper or an incomplete configuration. Check the configuration and make sure it is as required to resolve the issue.
<
Error: «Anyconnect package unavailable or corrupted. Contact your system administrator»
This error occurs when you try to launch the AnyConnect software from a Macintosh client in order to connect to an ASA.
Solution
In order to resolve this, complete these steps:
- Upload the Macintosh AnyConnect package to the flash of the ASA.
- Modify the WebVPN configuration in order to specify the AnyConnect package that is used.
webvpn
svc image disk0:/anyconnect-macosx-i386-2.3.2016-k9.pkg 2
svc image disk0:/anyconnect-macosx-powerpc-2.3.2016-k9.pkg 3The svc image command is replaced by the anyconnect image command in ASA Version 8.4(1) and later as shown here:
hostname(config)#webvpn
hostname(config-webvpn)#anyconnect image disk0:/
anyconnect-win-3.0.0527-k9.pkg 1hostname(config-webvpn)#anyconnect image disk0:/
anyconnect-macosx-i386-3.0.0414-k9.pkg 2
Error: «The AnyConnect package on the secure gateway could not be located»
This error is caused on the user’s Linux machine when it tries to connect to the ASA by launching AnyConnect. Here is the complete error:
"The AnyConnect package on the secure gateway could not be located. You may
be experiencing network connectivity issues. Please try connecting again."
Solution
In order to resolve this error message, verify whether the Operating System (OS) that is used on the client machine is supported by the AnyConnect client.
If the OS is supported, then verify if the AnyConnect package is specified in the WebVPN configuration or not. See the Anyconnect package unavailable or corrupted section of this document for more information.
Error: «Secure VPN via remote desktop is not supported»
Users are unable to perform a remote desktop access. The Secure VPN via remote desktop is not supported error message appears.
Solution
This issue is due to these Cisco bug IDs: CSCsu22088 and CSCso42825. If you upgrade the AnyConnect VPN Client, it can resolve the issue. Refer to these bugs for more information.
Error: «The server certificate received or its chain does not comply with FIPS. A VPN connection will not be established»
When you attempt to VPN to the ASA 5505, the The server certificate received or its chain does not comply with FIPS. A VPN connection will not be established error message appears.
Solution
In order to resolve this error, you must disable the Federal Information Processing Standards (FIPS) in the AnyConnect Local Policy file. This file can usually be found at C:ProgramDataCiscoCisco AnyConnect VPN ClientAnyConnectLocalPolicy.xml. If this file is not found in this path, then locate the file at a different directory with a path such as C:Documents and SettingsAll UsersApplication DataCisco AnyConnectVPNClientAnyConnectLocalPolicy.xml. Once you locate the xml file, make changes to this file as shown here:
Change the phrase:
<FipsMode>true</FipsMode>
To:
<FipsMode>false</FipsMode>
Then, restart the computer. Users must have administrative permissions in order to modify this file.
Error: «Certificate Validation Failure»
Users are unable to launch AnyConnect and receive the Certificate Validation Failure error.
Solution
Certificate authentication works differently with AnyConnect compared to the IPSec client. In order for certificate authentication to work, you must import the client certificate to your browser and change the connection profile in order to use certificate authentication. You also need to enable this command on your ASA in order to allow SSL client-certificates to be used on the outside interface:
ssl certificate-authentication interface outside port 443
Error: «VPN Agent Service has encountered a problem and needs to close. We are sorry for the inconvenience»
When AnyConnect Version 2.4.0202 is installed on a Windows XP PC, it stops at updating localization files and an error message shows that the vpnagent.exe fails.
Solution
This behavior is logged in Cisco bug ID CSCsq49102. The suggested workaround is to disable the Citrix client.
Error: «This installation package could not be opened. Verify that the package exists»
When AnyConnect is downloaded, this error message is received:
"Contact your system administrator. The installer failed with the following error: This installation package could not be opened. Verify that the package exists and that you can access it, or contact the application vendor to verify that this is a valid Windows Installer package."
Solution
Complete these steps in order to fix this issue:
- Remove any anti-virus software.
- Disable the Windows firewall.
- If neither Step 1 or 2 helps, then format the machine and then install.
- If the problem still persists, open a TAC Case.
Error: «Error applying transforms. Verify that the specified transform paths are valid.»
This error message is recieved during the auto-download of AnyConnect from the ASA:
"Contact your system administrator. The installer failed with the following error:
Error applying transforms. Verify that the specified transform paths are valid."
This is the error message received when connecting with AnyConnect for MacOS:
"The AnyConnect package on the secure gateway could not be located. You may be
experiencing network connectivity issues. Please try connecting again."
Solution
Complete one of these workarounds in order to resolve this issue:
- The root cause of this error might be due to a corrupted MST translation file (for example, imported). Perform these steps to fix this:
- Remove the MST translation table.
- Configure the AnyConnect image for MacOS in the ASA.
- From the ASDM, follow the Network (Client) Access > AnyConnect Custom > Installs path and delete the AnyConnect package file. Make sure the package remains in Network (Client) Access > Advanced > SSL VPN > Client Setting.
If neither of these workarounds resolve the issue, contact Cisco Technical Support.
Error: «The VPN client driver has encountered an error»
This error is received:
The VPN client driver has encountered an error when connecting through Cisco
AnyConnect Client.
Solution
This issue can be resolved when you uninstall the AnyConnect Client, and then remove the anti-virus software. After this, reinstall the AnyConnect Client. If this resolution does not work, then reformat the PC in order to fix this issue.
Error: «A VPN reconnect resulted in different configuration setting. The VPN network setting is being re-initialized. Applications utilizing the private network may need to be restored.»
This error is received when you try to launch AnyConnect:
"A VPN reconnect resulted in different configuration setting. The VPN network
setting is being re-initialized. Applications utilizing the private network may
need to be restarted."
Solution
In order to resolve this error, use this:
group-policy <Name> attributes
webvpn
svc mtu 1200
The svc mtu command is replaced by the anyconnect mtu command in ASA Version 8.4(1) and later as shown here:
hostname(config)#group-policy <Name> attributes
hostname(config-group-policy)#webvpnhostname(config-group-webvpn)#anyconnect mtu 500
AnyConnect Error While Logging In
Problem
The AnyConnect receives this error when it connects to the Client:
The VPN connection is not allowed via a local proxy. This can be changed
through AnyConnect profile settings.
Solution
The issue can be resolved if you make these changes to the AnyConnect profile:
Add this line to the AnyConnect profile:
<ProxySettings>IgnoreProxy</ProxySettings><
AllowLocalProxyConnections>
false</AllowLocalProxyConnections>
IE Proxy Setting is Not Restored after AnyConnect Disconnect on Windows 7
Problem
In Windows 7, if the IE proxy setting is configured for Automatically detect settings and AnyConnect pushes down a new proxy setting, the IE proxy setting is not restored back to Automatically detect settings after the user ends the AnyConnect session. This causes LAN issues for users who need their proxy setting configured for Automatically detect settings.
Solution
This behavior is logged in Cisco bug ID CSCtj51376. The suggested workaround is to upgrade to AnyConnect 3.0.
Error: AnyConnect Essentials can not be enabled until all these sessions are closed.
This error message is received on Cisco ASDM when you attempt to enable the AnyConnect Essentials license:
There are currently 2 clientless SSL VPN sessions in progress. AnyConnect
Essentials can not be enabled until all these sessions are closed.
Solution
This is the normal behavior of the ASA. AnyConnect Essentials is a separately licensed SSL VPN client. It is entirely configured on the ASA and provides the full AnyConnect capability, with these exceptions:
- No Cisco Secure Desktop (CSD) (including HostScan/Vault/Cache Cleaner)
- No clientless SSL VPN
- Optional Windows Mobile Support
This license cannot be used at the same time as the shared SSL VPN premium license. When you need to use one license, you need to disable the other.
Error: Connection tab on Internet option of Internet Explorer hides after getting connected to the AnyConnect client.
The connection tab on the Internet option of Internet Explorer hides after you are connected to the AnyConnect client.
Solution
This is due to the msie-proxy lockdown feature. If you enable this feature, it hides the Connections tab in Microsoft Internet Explorer for the duration of an AnyConnect VPN session. If you disable the feature, it leaves the display of the Connections tab unchanged.
Error: Few users getting Login Failed Error message when others are able to connect successfully through AnyConnect VPN
A few users receive the Login Failed Error message when others can connect successfully through the AnyConnect VPN.
Solution
This issue can be resolved if you make sure the do not require pre-authentication checkbox is checked for the users.
Error: The certificate you are viewing does not match with the name of the site you are trying to view.
During the AnyConnect profile update, an error is shown that says the certificate is invalid. This occurs with Windows only and at the profile update phase. The error message is shown here:
The certificate you are viewing does not match with the name of the site
you are trying to view.
Solution
This can be resolved if you modify the server list of the AnyConnect profile in order to use the FQDN of the certificate.
This is a sample of the XML profile:
<ServerList><HostEntry>
<HostName>vpn1.ccsd.net</HostName>
</HostEntry>
</ServerList>
Note: If there is an existing entry for the Public IP address of the server such as <HostAddress>, then remove it and retain only the FQDN of the server (for example, <HostName> but not <Host Address>).
Cannot Launch AnyConnect From the CSD Vault From a Windows 7 Machine
When the AnyConnect is launched from the CSD vault, it does not work. This is attempted on Windows 7 machines.
Solution
Currently, this is not possible because it is not supported.
AnyConnect Profile Does Not Get Replicated to the Standby After Failover
The AnyConnect 3.0 VPN client with ASA Version 8.4.1 software works fine. However, after failover, there is no replication for the AnyConnect profile related configuration.
Solution
This problem has been observed and logged under Cisco bug ID CSCtn71662. The temporary workaround is to manually copy the files to the standby unit.
AnyConnect Client Crashes if Internet Explorer Goes Offline
When this occurs, the AnyConnect event log contains entries similar to these:
Description : Function:
CAdapterNetworkStateIfc::SetConnectedStateToConnected
File: .AdapterNetworkStateIfc.cpp
Line: 147
Invoked Function: InternetSetOption
Return Code: 12010 (0x00002EEA)
Description: The length is incorrect for the option typeDescription : Function: CTransportWinHttp::InitTransport
File: .CTransportWinHttp.cpp
Line: 252
Invoked Function: CConnectedStateIfc::SetConnectedStateToConnected
Return Code: -25362420 (0xFE7D000C)
Description: CADAPTERNETWORKSTATEIFC_ERROR_SET_OPTION
Solution
This behavior is observed and logged under Cisco bug ID CSCtx28970. In order to resolve this, quit the AnyConnect application and relaunch. The connection entries reappear after relaunch.
Error Message: TLSPROTOCOL_ERROR_INSUFFICIENT_BUFFER
The AnyConnect client fails to connect and the Unable to establish a connection error message is received. In the AnyConnect event log, the TLSPROTOCOL_ERROR_INSUFFICIENT_BUFFER error is found.
Solution
This occurs when the headend is configured for split-tunneling with a very large split-tunnel list (approximately 180-200 entries) and one or more other client attributes are configured in the group-policy, such as dns-server.
In order to resolve this issue, complete these steps:
- Reduce the number of entries in the split-tunnel list.
- Use this configuration in order to disable DTLS:
group-policy groupName attributes
webvpn
svc dtls none
For more information, refer to Cisco bug ID CSCtc41770.
Error Message: «Connection attempt has failed due to invalid host entry»
The Connection attempt has failed due to invalid host entry error message is received while AnyConnect is authenticated with the use of a certificate.
Solution
In order to resolve this issue, try either of these possible solutions:
- Upgrade the AnyConnect to Version 3.0.
- Disable Cisco Secure Desktop on your computer.
For more information, refer to Cisco bug ID CSCti73316.
Error: «Ensure your server certificates can pass strict mode if you configure always-on VPN»
When you enable the Always-On feature on AnyConnect, the Ensure your server certificates can pass strict mode if you configure always-on VPN error message is received.
Solution
This error message implies that if you want to use the Always-On feature, you need a valid sever certificate configured on the headend. Without a valid server certificate, this feature does not work. Strict Cert Mode is an option that you set in the AnyConnect local policy file in order to ensure the connections use a valid certificate. If you enable this option in the policy file and connect with a bogus certificate, the connection fails.
Error: «An internal error occurred in the Microsoft Windows HTTP Services»
This Diagnostic AnyConnect Reporting Tool (DART) shows one failed attempt:
******************************************
Date : 03/25/2014
Time : 09:52:21
Type : Error
Source : acvpnuiDescription : Function: CTransportWinHttp::SendRequest
File: .CTransportWinHttp.cpp
Line: 1170
Invoked Function: HttpSendRequest
Return Code: 12004 (0x00002EE4)
Description: An internal error occurred in the Microsoft
Windows HTTP Services
*****************************************
Date : 03/25/2014
Time : 09:52:21
Type : Error
Source : acvpnuiDescription : Function: ConnectIfc::connect
File: .ConnectIfc.cpp
Line: 472
Invoked Function: ConnectIfc::sendRequest
Return Code: -30015443 (0xFE36002D)
Description: CTRANSPORT_ERROR_CONN_UNKNOWN
******************************************
Date : 03/25/2014
Time : 09:52:21
Type : Error
Source : acvpnuiDescription : Function: ConnectIfc::TranslateStatusCode
File: .ConnectIfc.cpp
Line: 2999
Invoked Function: ConnectIfc::TranslateStatusCode
Return Code: -30015443 (0xFE36002D)
Description: CTRANSPORT_ERROR_CONN_UNKNOWN
Connection attempt failed. Please try again.******************************************
Also, refer to the event viewer logs on the Windows machine.
Solution
This could be caused due to a corrupted Winsock connection. Reset the connection from the command promt with this command and restart your windows machine:
netsh winsock reset
Refer to the How to determine and to recover from Winsock2 corruption in Windows Server 2003, in Windows XP, and in Windows Vista knowledge base article for more information.
Error: «The SSL transport received a Secure Channel Failure. May be a result of a unsupported crypto configuration on the Secure Gateway.»
This Diagnostic AnyConnect Reporting Tool (DART) shows one failed attempt:
******************************************
Date : 10/27/2014
Time : 16:29:09
Type : Error
Source : acvpnuiDescription : Function: CTransportWinHttp::handleRequestError
File: .CTransportWinHttp.cpp
Line: 854
The SSL transport received a Secure Channel Failure. May be a result of a unsupported crypto configuration on the Secure Gateway.******************************************
Date : 10/27/2014
Time : 16:29:09
Type : Error
Source : acvpnuiDescription : Function: CTransportWinHttp::SendRequest
File: .CTransportWinHttp.cpp
Line: 1199
Invoked Function: CTransportWinHttp::handleRequestError
Return Code: -30015418 (0xFE360046)
Description: CTRANSPORT_ERROR_SECURE_CHANNEL_FAILURE******************************************
Date : 10/27/2014
Time : 16:29:09
Type : Error
Source : acvpnuiDescription : Function: ConnectIfc::TranslateStatusCode
File: .ConnectIfc.cpp
Line: 3026
Invoked Function: ConnectIfc::TranslateStatusCode
Return Code: -30015418 (0xFE360046)
Description: CTRANSPORT_ERROR_SECURE_CHANNEL_FAILURE
Connection attempt failed. Please try again.
******************************************
Solution
Windows 8.1 does not support RC4 according to the following KB update:
http://support2.microsoft.com/kb/2868725
Either configure DES/3DES ciphers for SSL VPN on the ASA using the command «ssl encryption 3des-sha1 aes128-sha1 aes256-sha1 des-sha1» OR edit the Windows Registry file on the client machine as mentioned below:
https://technet.microsoft.com/en-us/library/dn303404.aspx
Related Information
- Cisco ASA 5500 Series Adaptive Security Appliances
- AnyConnect VPN Client FAQ
- Cisco Secure Desktop (CSD) FAQ
- Cisco AnyConnect VPN Client
- Technical Support & Documentation — Cisco Systems
This post will cover one interesting root cause of getting AnyConnect Certificate Validation Failure. I was working on setting up a Cisco AnyConnect Management Tunnel, which I will cover in another post, and for some reason when I was trying to establish AnyConnect SSL VPN from a Windows client, it was just failing dropping the message Certificate Validation Failure on the screen.
I thought there was something wrong with the client certificate or maybe the trust point on the ASA that is configured to authenticate AnyConnect clients. Checking on the client side, all was looking good, and the user and machine certs were successfully installed, and the issuer root CA certificate was in the trusted store.
Similarly on the ASA side, the ASA identity certificate was looking good, as well as the trust point that is responsible to authenticate the clients. This trust point is configured with OCSP for the revocation check. the OCSP is a Windows server. I also checked the OCSP configuration on the Windows server and all was looking good and functional.
I then enabled debug crypto ca 7 on the ASA, and I tried to establish the VPN tunnel again to capture some debug. Here is a snippet from the debug output:
PKI[7]: revocation status queued for session 0x14981ed1 and cert_idx 0, rev_status 6 PKI[7]: Chain revocation status: good: 0, exempt: 0, cached: 0, revoked: 0, error: 0, pending: 1 PKI[7]: Evaluating session revocation status, 1 certs to check PKI[7]: starting OCSP FSM #0 CRYPTO_PKI: Attempting to find OCSP override for peer cert: serial number: <omitted>, subject name: CN=test1,CN=Users,DC=mylab,DC=local, issuer_name: CN=WIN-2K12-01-CA,DC=mylab,DC=local. CRYPTO_PKI: No OCSP overrides found. PKI[4]: no AIA for OCSP revocation checking, cert index 0 PKI[7]: OCSP revocation AIA list built for cert index 0 with 0 AIAs, error FALSE PKI[4]: No more AIAs found to try PKI[7]: revocation status queued for session 0x14981ed1 and cert_idx 0, rev_status 6 PKI[7]: Chain revocation status: good: 0, exempt: 0, cached: 0, revoked: 0, error: 0, pending: 1 PKI[7]: Evaluating session revocation status, 1 certs to check PKI[7]: Chain revocation status: good: 0, exempt: 0, cached: 0, revoked: 0, error: 1, pending: 0 PKI[7]: session: 0x14981ed1, all revocation processing complete PKI[5]: session: 0x14981ed1, error during revocation check of certificate 0 PKI[5]: session 0x14981ed1, Error in revocation check or revoked certs found
Looking online for some help, I found this Cisco documentation:
OCSP Service Nonces
Microsoft implementation of OCSP is compliant with RFC 5019 The Lightweight Online Certificate Status Protocol (OCSP) Profile for High-Volume Environments , which is a simplified version of RFC 2560 X.509 Internet Public Key Infrastructure Online Certificate Status Protocol — OCSP .
The ASA uses RFC 2560 for OCSP. One of the differences in the two RFCs is that RFC 5019 does not accept signed requests sent by ASA.
It is possible to force the Microsoft OCSP service to accept those signed requests and reply with the correct signed response.
So, it clearly states that Windows servers and ASA use two different RFCs when it comes to OCSP. You can apply one of two fixes to fix this issue. One is through the OCSP responder configuration on the Windows server, and another on the ASA trust point that is configured to authenticate AnyConnect clients. However, Cisco does not recommend this fix on the ASA.
Option 1: Fix on OCSP Windows Server
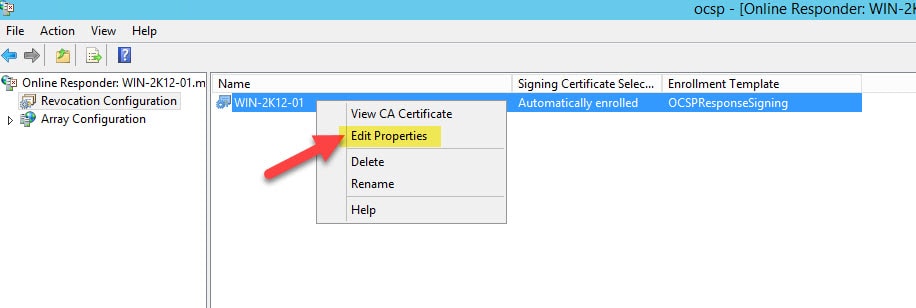
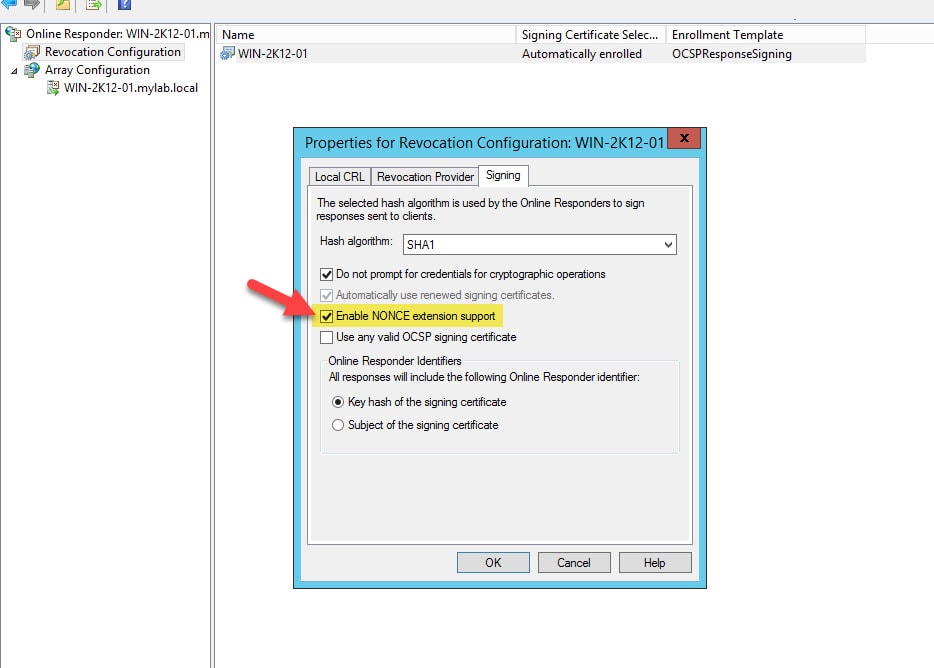
Go to Administrative Tools > Online Responder Management > Revocation Configuration and tick the checkbox next to Enable NONCE extension support
If you are facing “Cisco AnyConnect Certificate Validation Failure” problem while trying to connect on the AnyConnect Client, then you are in right place. Here, we are discussing on “How to fix AnyConnect Certificate error” in details and providing some recommended methods to fix this error. Let’s starts the discussion.
What is Cisco AnyConnect?
“Cisco AnyConnect” is proprietary application that lets users connect to VPN service. Many universities use this application as part of service they pay for from Cisco that’s why public institutions unnecessarily rely on this closed-source software for their own students. This doesn’t just amount to handling control to a private corporation, thereby privatizing public money. This software also provide extra security layer to reduce potentially unwanted attacks and privacy vulnerability.
Cisco AnyConnect is unified endpoint agent that delivers multiple security services to protect the enterprise. Its wide range of security services includes functions such as remote access, posture enforcement, web security features, and roaming protection. It gives all the security features for IT department to provide a robust, user-friendly, and highly secure mobile experience as well.
Cisco AnyConnect security mobility client is modular endpoint software product that not only provides VPN access via SSL (Secure Socket Layer) and IPsec IKEv2 but also offers improved security via various built-in modules including compliance through VPN and ASA or through wired /wireless, and VPN with Cisco identity Services Engine (ISE), Off-network roaming protection with Cisco Umbrella.
Since, Cisco has been a long-term target of NSA spying program. It also doesn’t work well on Linux. There is nothing wrong with supporting free and open source solutions like OpenVPN which are used by numerous users worldwide. Linux, iOS, Windows, MacOS and Android OS are some of the popular tools that integrate with Cisco Anyconnect.
Cisco AnyConnect Review: Features
- Mobile Device Support: AnyConnect services can be delayed on most popular devices used by today’s diverse workforce. Administrators need to support end-user productivity by providing personal mobile devices with remote access to the computer network.
- Off-Network Protection (DNS Layer Security): Cisco AnyConnect protects devices when they are off the corporate network. The Umbrella roaming enforces security at DNS layer to protect against malware, phishing and Command -and-Control callbacks over any protocol whether you turn Off the VPN or forgot to turn it on.
- Web security: Cisco AnyConnect has in-built web security feature based on cloud web security. Combining web security with VPN access, administrators can provide comprehensive, high security mobility to all end users.
- Network Visibility: Cisco AnyConnect network visibility module on MacOS, Windows OS, Linux and Samsung Knox-enabled devices gives administrators the ability to monitor endpoint application usage to uncover potential behavior anomalies and to make more informed network designed decisions.
What is “Cisco AnyConnect Certificate Validation Failure” Error on Windows?
“AnyConnect Certificate error” is common error reported by numerous users on Cisco official forum site or other popular platforms and asked for the solution. Users explained on Cisco Community website that the error appears when they run their own CA that gives out the client certificates for our users as well as the identity certificate for ASA, and in order to click on “Connect” on AnyConnect Client, their client receives “No Valid Certificates available for authentication” message.
Furthermore, he also created a DART bundle and in there I can see that the certificate is selected from the “Microsoft Store”, but after that he receive several errors regarding SCHANNEL. Then, he tried another certificate authentication and finds no certificates followed by “Cisco AnyConnect Certificate Validation Failure” Error.
Certificate Validation Failure Error States:
When we talk about “Anyconect Certificate validation Failure error”, it explained that it can’t verify the VPN server which is to be expected since it uses the self-signed certificate, but if they connect anyway, then they receive the certification selection and the login works fine. It means username & password for login is taken from the certificate.
[Tips & Tricks] How to fix Cisco AnyConnect Certificate Validation Failure Problem?
Procedure 1: Repair the Installation
Step 1: Click on “Start” button and type “Control Panel” in Windows search and open “Control Panel”
Step 2: In the opened “Control Panel”, choose “Uninstall a program” and find “Cisco AnyConnect VPN” client and choose “Repair”
Step 3: Follow On-Screen instructions to finish the repairing process. Once done, restart your computer and please check if the problem is resolved.
Procedure 2: Allow VPN to freely communicate through Firewall
Step 1: Click on “Start” button and type “Allow an App” in Windows Search and open “Allow an App through Windows Firewall”
Step 2: Now, click on “Change Settings”
Step 3: Make sure that “Cisco VPN” is on the list and it’s allowed to communicate through Windows Firewall. If not, click “Allow another App” and add it
Step 4: Check both “Private” and “Publicrong” > Network boxes
Step 5: Confirm changes and open Cisco VPN
Procedure 3: Check Virtual Adapter driver in Device Manger and update it
Step 1: Press “Windows + X” key from keyboard and select “Device Manager”
Step 2: In the opened “Device Manager” window, locate and expand “Network Adapters”
Step 3: Right-click on Virtual Adapter and select “Update driver software”
Step 4: Follow On-Screen instructions to finish the updating process.
Step 5: Once done, restart your computer and please check if the problem is resolved.
Procedure 4: Tweak Registry and Repair Cisco VPN
Step 1: Press “Windows + R” keys together from keyboard and type “regedit” in “Run Dialog Box” and then hit “Ok” button
Step 2: In the opened “Registry Editor” window, navigate to “HKEY_LOCAL_MACHINE/SYSTEM/Current/Control/SetServices/CVirtA”
Step 3: Right-click on the “DisplayName” registry entry and choose “Modify”
Step 4: Under “Value Data” section, make sure that the only body of text which stands is Cisco System VPN Adapter
Step 5: Save the changes and try running Cisco AnyConnect VPN again.
Procedure 5: Update the AnyConnect
Step 1: Go to “ASDM > Configuration > Remote Access VPN > Network (Client) Access > AnyConnect Client Software”
Step 2: You can either replace the existing the image or add a new one.
Step 3: After that, connect to the ASA. The client will be updated automatically.
Procedure 6: Create Trustpoints for each certificate being installed
Step 1: Open the “Cisco ASDM”
Step 2: Under “Remote Access VPN” window pane, click on “Configuration” tab and expand “Certificate Management” and click on “CA Certificates”
Step 3: Click on “Add” button
Step 4: Assign a “TrustPoint Name” to the certificate like “DigiCertCA2” and select “Install from the file” Radio button and browse to “DigiCertCA2.crt”, then click on “Install Certificate”. Repeat this process of adding new trustpoint and installing certificate file for “DigiCertCA.crt”
Step 5: Under “Remote Access VPN”, expand “Certificate Management” to “Identify Certificates”. Select the identity you created for the CSR with “Expiry Data” and click on “Install > Install Certificate”
Step 6: The Certificate now needs to be enabled. To do so, click on “Advanced > SSL Settings > Edit > Primary Enrolled Certificate” and select your certificate and then click on “Ok”
Step 7: ASDM will then show your Certificate details under trustpoint
Procedure 7: Perform Clean Reinstallation
Step 1: Navigate to “Control Panel” and choose “Uninstall a program”
Step 2: Uninstall “Cisco AnyConnect VPN Client”
Step 3: Navigate to System partition and delete everything Cisco-related from programs folder
Step 4: Once uninstalled completely, restart your computer
Step 5: After that, download latest version of “Cisco AnyConnect” from “Cisco official website”
Step 6: Double-click on installer file and follow on-screen instructions to finish the installation.
Step 7: Once installed, restart your computer again and please check if the AnyConnect Certificate error is resolved.
Conclusion
Cisco AnyConnect is VPN service that offers Standard VPN encryption and protection. When we talk about AnyConnect Secure Mobility Client, it is modular endpoint software product. It not only provides Virtual Private Network (VPN) access through Secure Sockets layer (SSL) and Internet Protocol Security (IPsec) Internet Key Exchange version2 (IKEv2), but also offers enhanced security through various built-in modules.
I am sure this article helped you to “Fix Cisco AnyConnect Certificate Validation Failure Windows 10” with several easy methods/procedures. You can choose/follow either one or all procedures to fix this issue.
If you are unable to fix Cisco AnyConnect Certificate Validation Failure problem with the solutions mentioned above, then it might possible that your System has infected with malware or viruses. According to security researchers, malware or viruses cause several damages in your computer.
In this case, you can scan your computer with powerful antivirus software that has the ability to delete all types of malware or viruses from System.
I have installed cisco anyconnect secure mobile client 4.2.01022 (+all required packages).
Then added .pfx certificates to gnone2-key storage.
Then I launched cisco anyconnect secure mobile client typed where to connect — but cisco keep saying me that Certificate validation failure
Tried this:
sudo cp /etc/ssl/certs/Global* /opt/.cisco/certificates/ca
link was created but didn’t help. How to connect?
UPD:
This way I have extracted some certificates in different formats:
openssl pkcs12 -in store.pfx -clcerts -nokeys -out domain.cer
openssl pkcs12 -in store.pfx -nocerts -nodes -out domain.key
openssl pkcs12 -in store.pfx -out domain.crt -nodes -nokeys -cacerts
openssl pkcs12 -in store.pfx -nocerts -out domain.pem -nodes
Got 4 files:
domain.cer
domain.key
domain.crt
domain.pem
Placed all 4 of them in 3 different places:
~/.cisco/certificates/ca ~
Trusted CA and root certificates
~/.cisco/certificates/client
Client certificates
~/.cisco/certificates/client/private
Private keys
Same error.
UPD2: Tried to configure cisco anyconnect compatible with openconnect (which integrated to linux network center):
It asks to set:
CA certificate (it has to be domain.crt, so chosen it)
User certificate (that is it? - didnt choose)
Private key (I think its domain.key, so chosen it)
But if tries to connect:
Certificate from VPN server [host ip] failed verification.
Reason: certificate does not match hostname
Do you want to accept it?
Certificate from VPN server "194.176.96.4" failed verification.
Reason: certificate does not match hostname
Do you want to accept it?
With below info:
X.509 Certificate Information:
Version: 3
Serial Number (hex): ****
Issuer: C=US,O=DigiCert Inc,OU=www.digicert.com,CN=GeoTrust RSA CA 2018
Validity:
Not Before: **
Not After: **
Subject: C=RU,ST=[city],L=[city],O=[company name],OU=IT,CN=vpn.[companyname].ru
Subject Public Key Algorithm: RSA
Algorithm Security Level: Medium (2048 bits)
....
I accept — and same error Certificate validation failure, full log:
POST https://[host_name]/
Attempting to connect to server [host_name]:443
SSL negotiation with [host_name]
Server certificate verify failed: certificate does not match hostname
Connected to HTTPS on [host_name]
Got HTTP response: HTTP/1.1 200 OK
Content-Type: text/html; charset=utf-8
Transfer-Encoding: chunked
Cache-Control: no-cache
Pragma: no-cache
Connection: Keep-Alive
Date: Sun, 26 Aug 2018 08:43:32 GMT
X-Frame-Options: SAMEORIGIN
X-Aggregate-Auth: 1
HTTP body chunked (-2)
Server requested SSL client certificate; none was configured
POST https://[host_name]/
Got HTTP response: HTTP/1.1 200 OK
Content-Type: text/html; charset=utf-8
Transfer-Encoding: chunked
Cache-Control: no-cache
Pragma: no-cache
Connection: Keep-Alive
Date: Sun, 26 Aug 2018 08:43:32 GMT
X-Frame-Options: SAMEORIGIN
X-Aggregate-Auth: 1
HTTP body chunked (-2)
XML POST enabled
PS: On windows same steps worked, added cert by double clicking then launched cisco client, typed server, then he asked password to server I quess — and then I was connected.
- Remove From My Forums
-
Question
-
HI All,
We have couple window machine where when try to connect to VPN thru cisco anyconnect secure mobility client , we get an error certificate validation failure. GPUpdate is succesffull
Is this issue related to AD. or what is the possible cause for this?
Regards
Aamir
NA
Answers
-
I would start by digging further into the Group Policy Object that is supposed to be pushing the certificates out. Does everything look like it’s configure properly?(https://blogs.technet.microsoft.com/yungchou/2013/10/21/enterprise-pki-with-windows-server-2012-r2-active-directory-certificate-services-part-1-of-2/)
If it’s just a small set of machines aren’t getting the certificates, is there anything in common with those machines or users? Are they in the same Active Directory OU? Are they getting other group policies? Try to figure out what makes
these particular users/machines different.-
Edited by
Friday, April 8, 2016 7:01 PM
-
Proposed as answer by
Teemo TangMicrosoft contingent staff
Friday, April 15, 2016 7:39 AM -
Marked as answer by
MeipoXuMicrosoft contingent staff
Friday, April 29, 2016 1:45 AM
-
Edited by
by Loredana Harsana
Loredana is a passionate writer with a keen interest in PC software and technology. She started off writing about mobile phones back when Samsung Galaxy S II was… read more
Published on May 29, 2022
- The most common reason for certificate validation failure on VPN is an expired certificate.
- VPN certificates are essential because they are a more secure way for authentication than preshared keys.
- Users reported that updating the certificate will solve the certificate validation failure error.
VPN, an acronym for Virtual Privacy Networks has certificates by a public authority that manages them. They are essential electronic documents, as VPN devices use them to indicate if they are the ones you connect to. Thus, it is imperative to quickly fix any VPN certificate validation failure.
Digital certificates of VPN are also used for authentication, and this is more secure than preshared keys. VPN certificates expire due to security reasons and when there is a need to replace them.
It used to take a more extended period of time for a valid VPN certificate to last, however, in 2021, SSL certificate expiration was reduced and a valid certificate lasted for 12 months only.
Still, this may not be the sole reason you are getting a failure in certificate validation. There are many other reasons why this may be happening with Cisco or some other VPN service provider.
Virtual Privacy Networks improve your security and privacy as you browse the Internet, which is why people use them. Therefore if you cannot validate VPN security, the purpose of getting the VPN in the first place is defeated.
How do I get a VPN certificate?
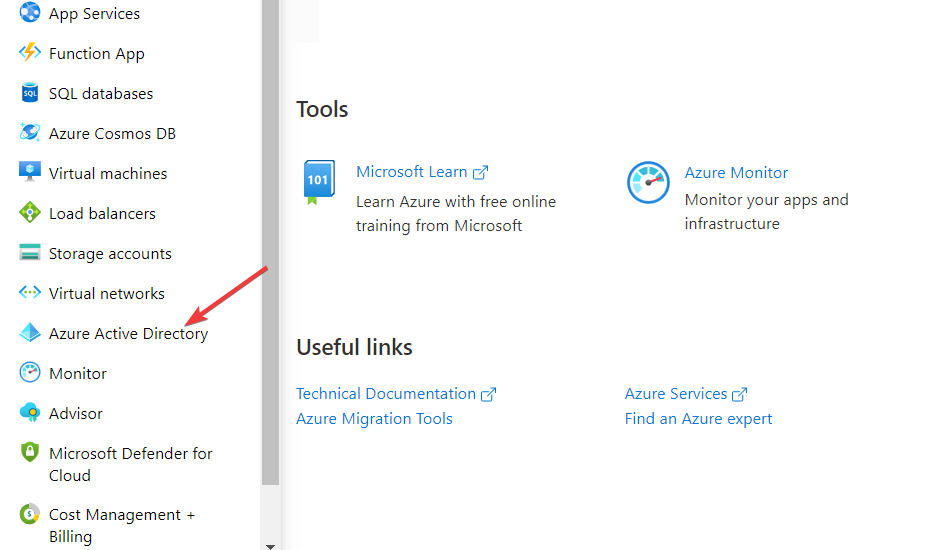
- Visit the Azure portal as an administrator.
- Click on Azure Active Directory on the left menu.
- Go to the Manage section in the Azure Active Directory menu and click on Security.
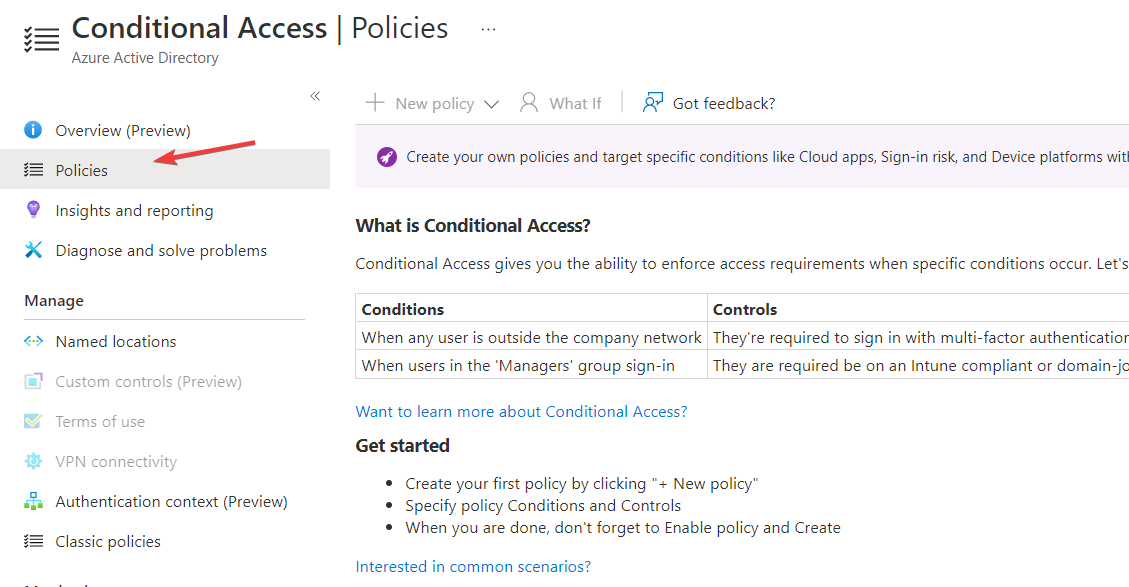
- Click on the Protect section on the Security page and select Conditional Access.
- Go to the Policies page on the Conditional access page and click on VPN Connectivity.
- Click New Certificate and generate one for yourself.
To have access to generate a new VPN certificate, you need to create an Azure Microsoft account. Microsoft has a free trial that you can use to gain access before you need to pay.
When your VPN certificate expires, you need to update it. If you do not update your VPN certificate, you lose security and become exposed to threats that make your private and classified information vulnerable.
How do I update my VPN certificate?
In order to update your VPN certificate, you will have to enter the Certificates – Local Computer app from your system and tweak your current certificate.
For an in-depth, step-by-step guide on how to achieve this, follow the second solution from the list below in order to update your VPN certificate.
Do VPN certificates expire?
VPN certificates are issued with an expiration date for the sake of increased security. After that date has passed, the certificates must be updated with fresh ones.
There is a validity period of three years attached to the VPN certificates that were issued by both the Internal RSA CA for Gateways and the Internal ECDSA CA.
How do I fix VPN validation failure?
1. Check the validity of your VPN certificate
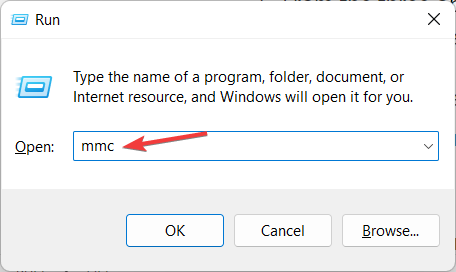
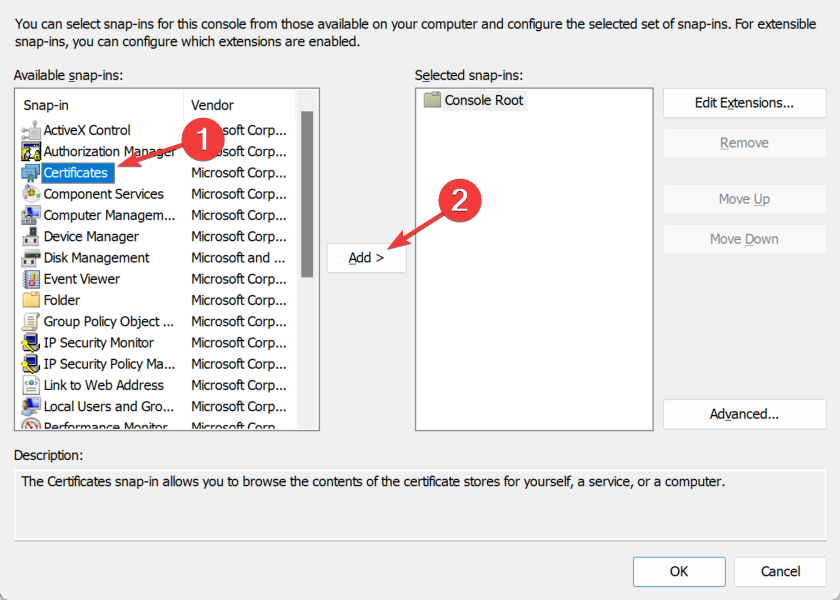
- Press the Windows and R keys on your device to open the Run tab and type in mmc then press Enter.
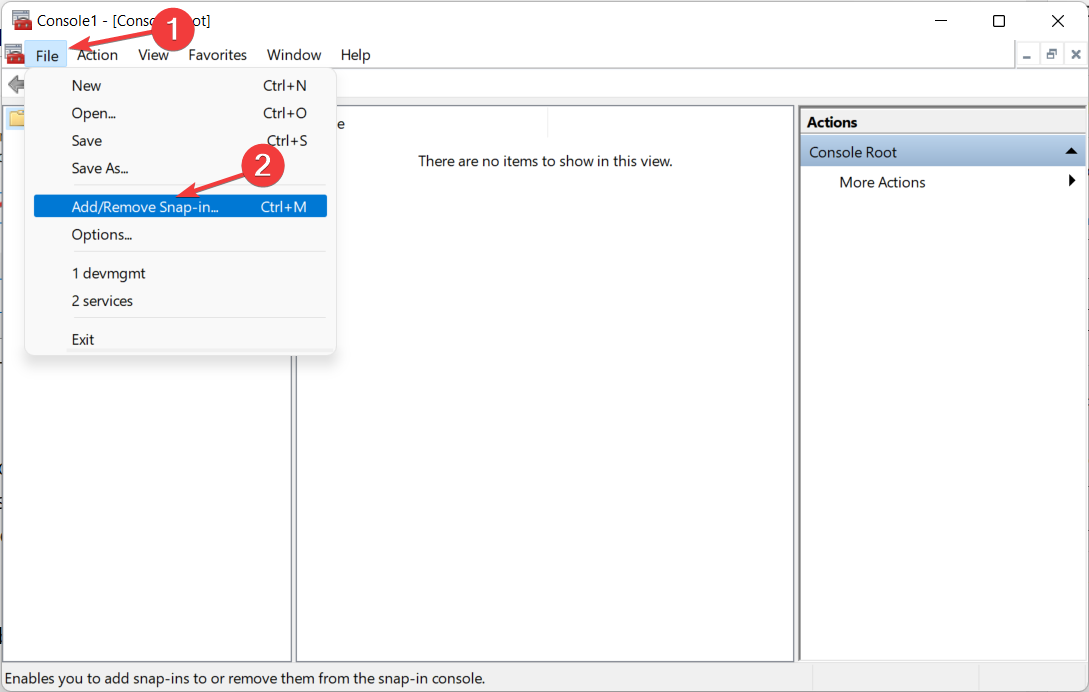
- Click on the File option in the top right corner and select Add/Remove Snap-in from the drop-down menu.
- Choose Certificates from the Available snap-ins section then click on the Add button.
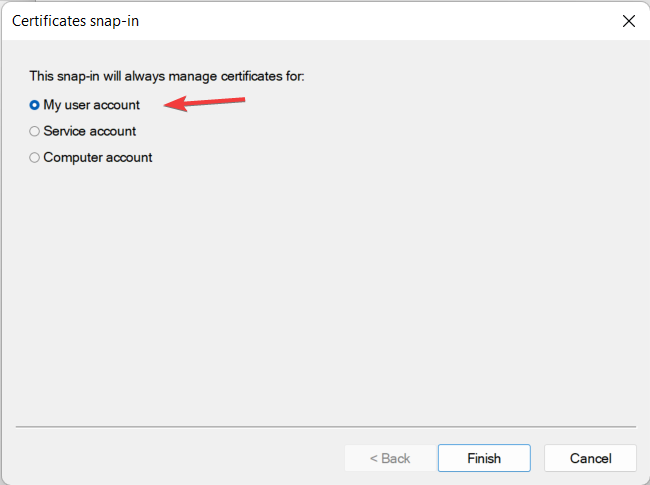
- From the three options, click on My User Account.
These steps will enable you access to the current User certificates to see the certificate that you have in the system. When you double-click on the certificate, you can see the details, which include the validity and expiry date.
After you check, and find that your VPN certificate may have expired, proceed to renew it.
- Fix: WiFi certificate error on Windows 10 [Can’t Connect]
- Set up a Windows 11 Ikev2 VPN in record time and with ease
- FIX: Cannot connect to L2TP VPN on Windows 10/11
2. Update your VPN certificate
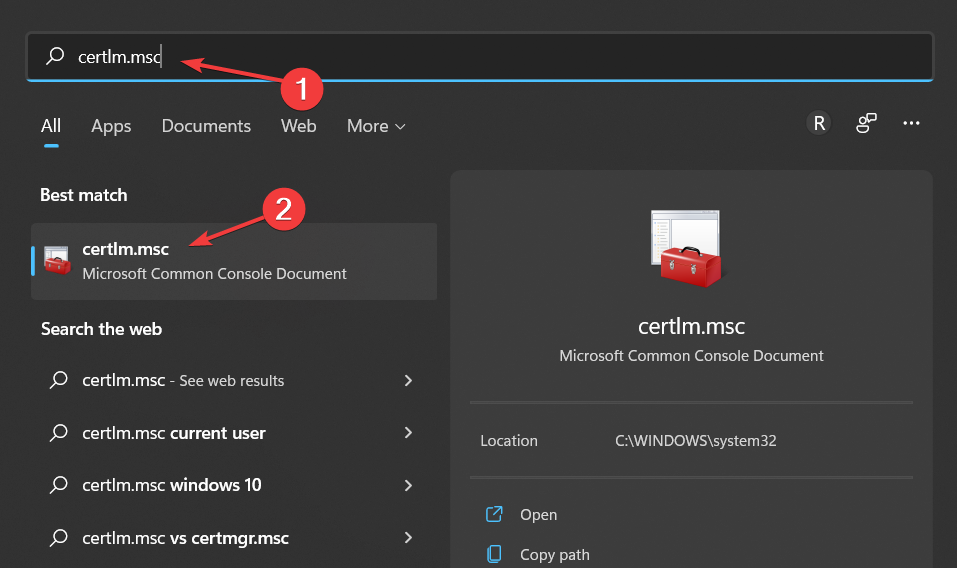
- Click on the magnifying glass icon from your Taskbar then type in certlm.msc and select the topmost result.
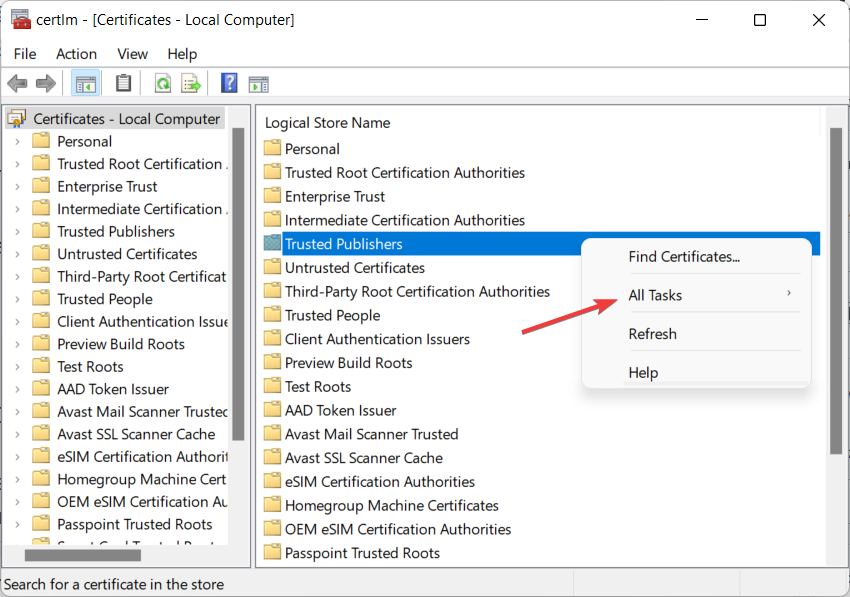
- Right-click on the open space and select All Tasks.
- Click on Advanced Operations and select Create Custom Request.
- Select Proceed without enrollment and continue with the onscreen steps.
- Click on the arrow next to Details and select Properties from the drop-down menu.
- Name the certificate a title that is easy to remember then click on Subject and select common name from the Full QDN drop-down menu.
- Enter the Fully Qualified Domain Name and click Add followed by Next.
- Go back to Properties and select the Extensions tab.
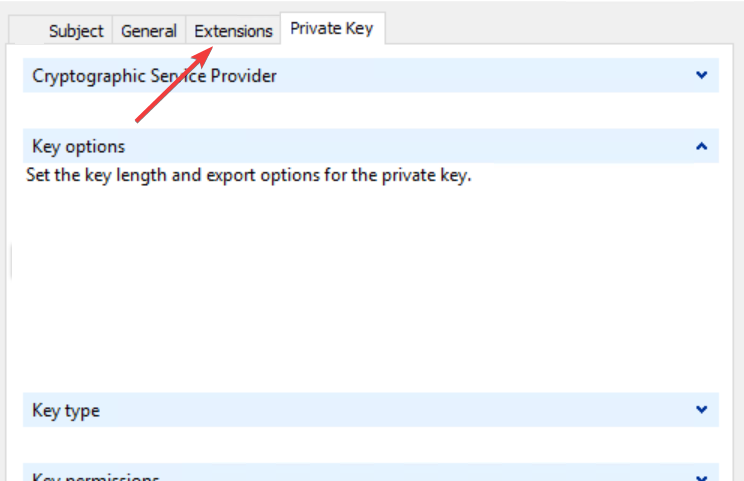
- Select Extended Key Usage, and click on Server Authentication and Add.
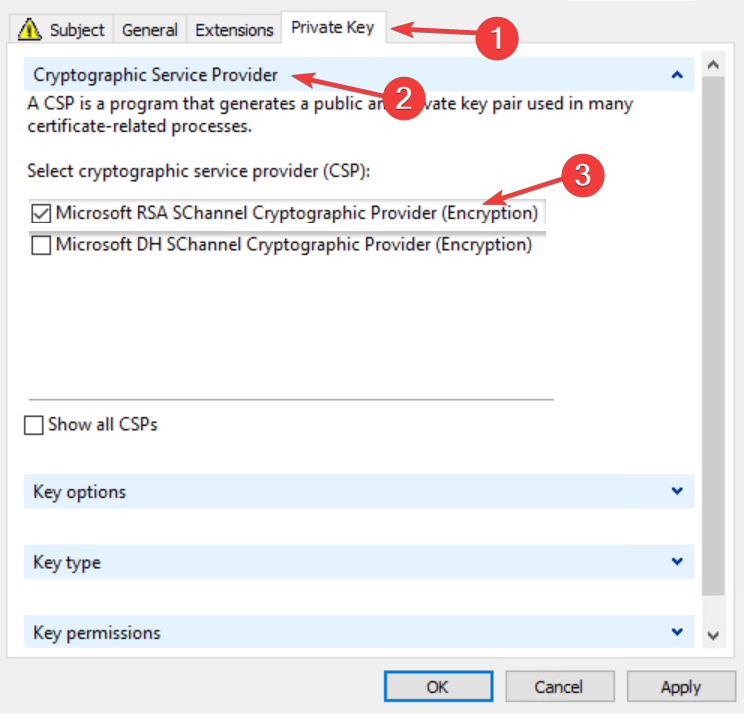
- Click on the Private Key tab then select Cryptographic service provider and check the Microsoft RSA or Microsoft DH option as you wish.
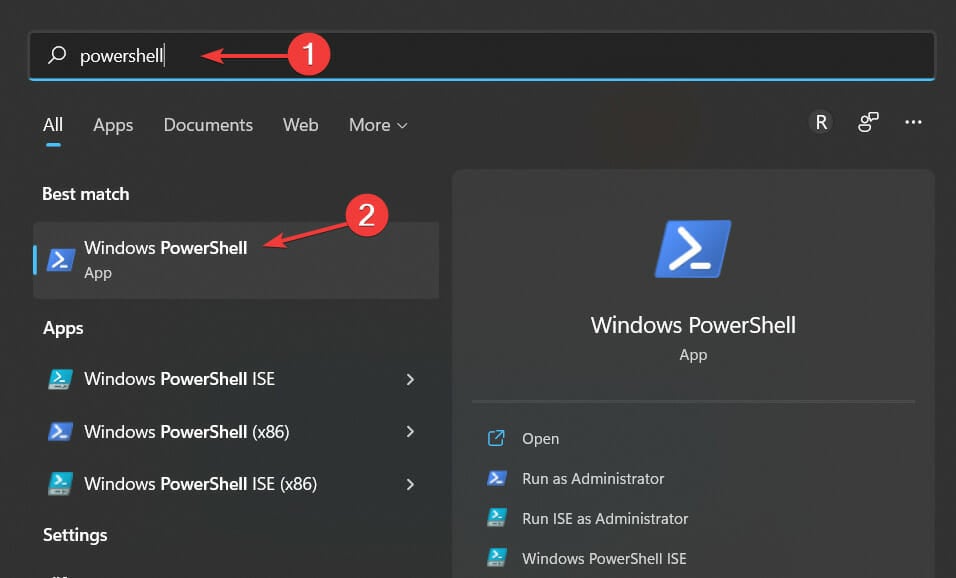
- Save everything by clicking on Apply and OK then click on the magnifying glass icon on your Taskbar and type PowerShell. Finally, click on the topmost result in order to open it.
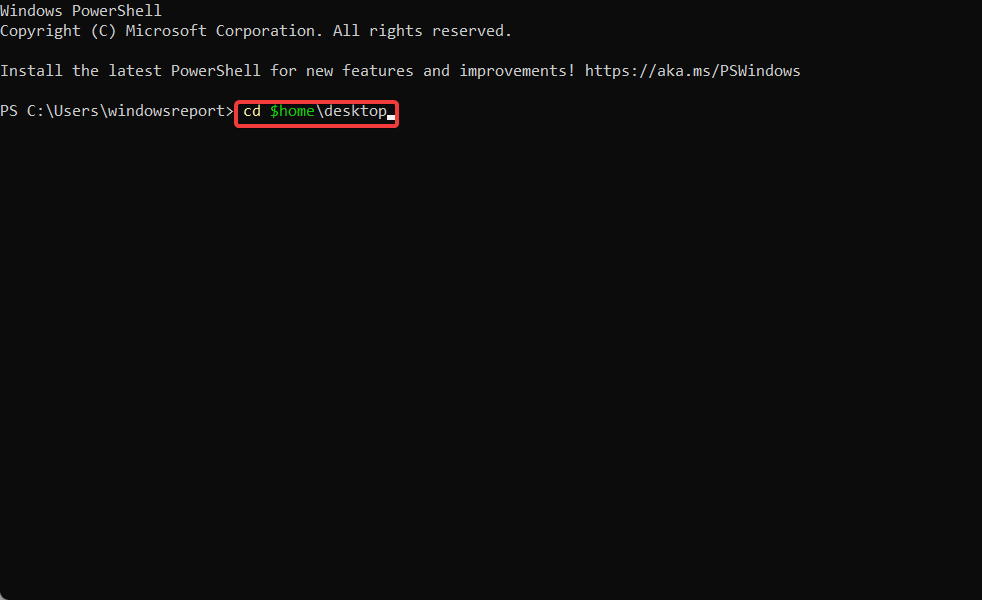
- Type in the following command and press Enter:
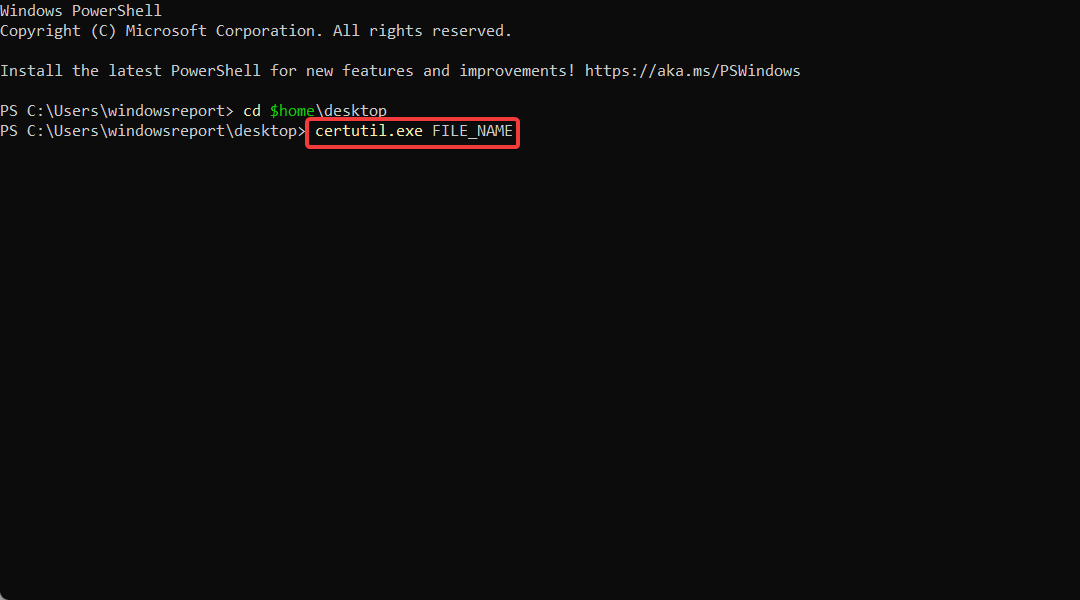
cd $homedesktop - On the next line, type in the following command and replace the FILE_NAME with your certificate’s name:
certutil.exe FILE_NAME - Copy the content of the file and submit it to your public certification authority for signing.
To fix certificate validation failure VPN Cisco, and certificate validation failure VPN anyconnect, you have to first verify that the hostname and host address are still valid and then check if the certificate has expired before you proceed to install a new certificate or update the existing one.
3. Turn on OCSP Nonce on the Windows server
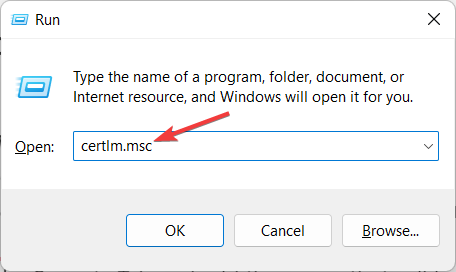
- Press the Windows and R keys to open a command bar and type certlm.msc to open the Certificate Service Management Console.
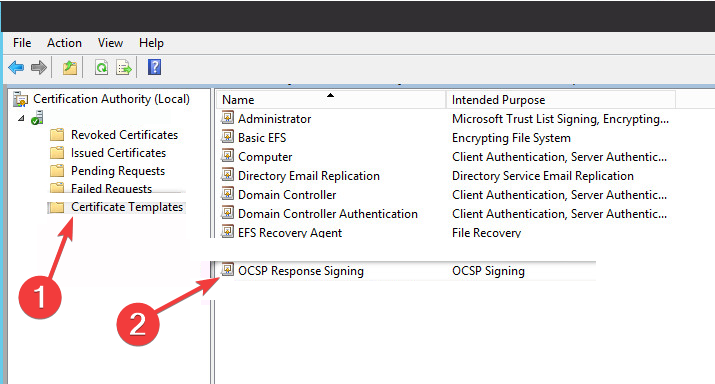
- Select Certificate template from the left menu and click on Manage then find OCSP Respond Signing from the drop-down menu and select it.
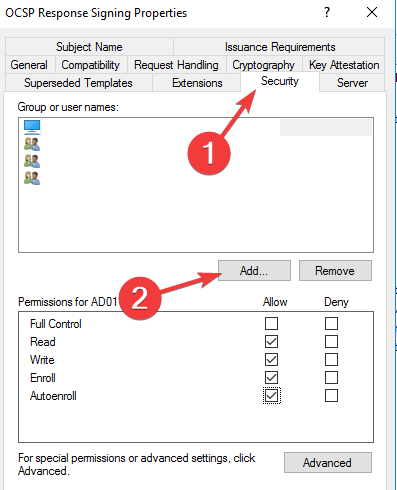
- Right-click on it and select Properties.
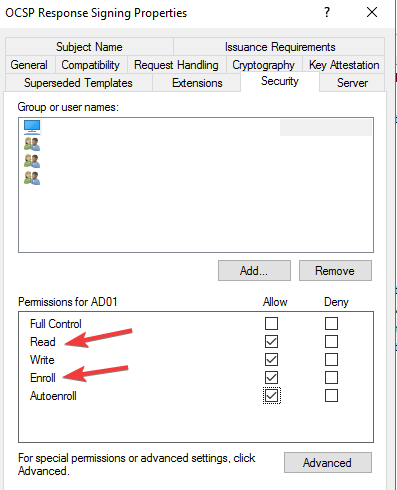
- Click on the Security tab and add the server that will be hosting the OCSP services.
- Check Read and Enrol then go back to Certificate template. Click on New, select Certificate Template to issue, and choose OCSP signing.
- Click on the certificate server and select Properties.
- Select the Extension tab and choose Authority Information Access. Select the URL of the server and click on Add.
- Go to the dashboard of the server manager of the OCSP service and click on Add roles and features.
- Check Active directory services and select Role services. Uncheck Certification Authority and check Online Responder.
- Launch the Online Responder management console.
OCSP is Online Certificate Status Protocol, and it is a method that browsers use to ensure that a security certificate is valid. Enabling OCSP service nonce protects secure network communication.
Microsoft Windows uses RFC 5019 while Cisco AnyConnect VPN ASA uses RFC 2560. This disparity causes VPN validation failure, and as such needs fixing.
When OpenVPN certificate verification failed and VPN certificate validation failure occurs, these are the steps that you can follow to rectify them.
Also, for IBM VPN certificate validation failure, there is a renew certificate application in the IBM store that can help you with renewing your certificate if it is outdated.
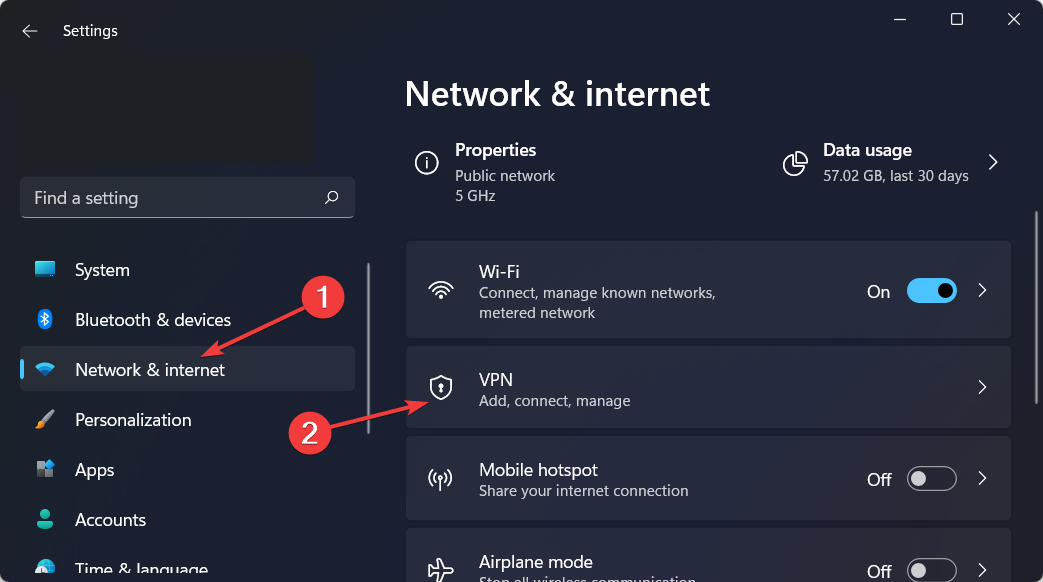
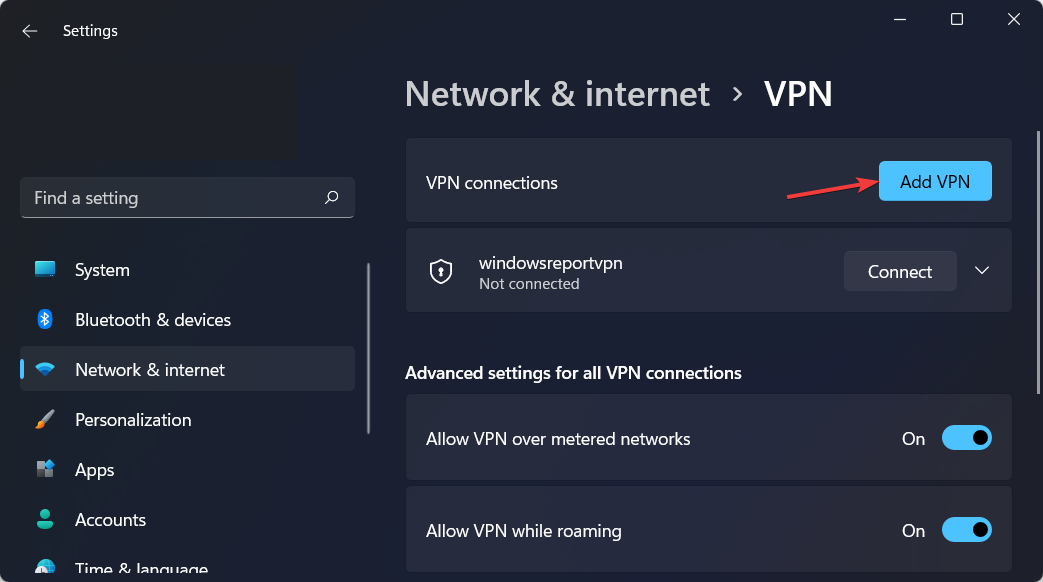
How do I add a VPN certificate to Windows 10/11?
- Open Settings by holding Windows and I together then go to Network and Internet followed by VPN.
- Click on Add VPN.
- On the dropdown menu, select Windows built-in as the VPN provider.
- Type in a name for the VPN connection in the Connection name field.
- Get the server name and address from the provider and type it into the Server address field.
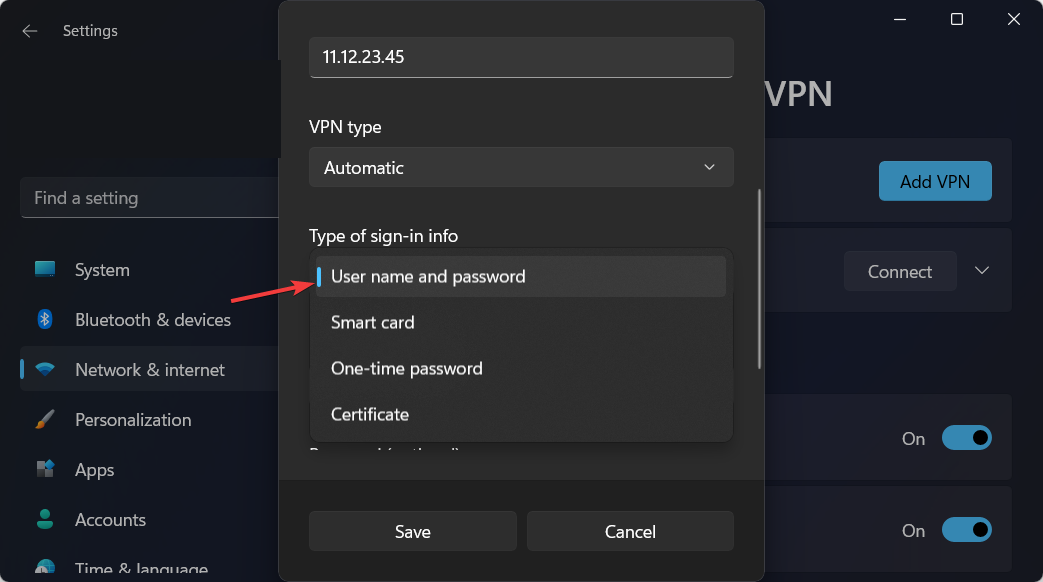
- In the Type-of-sign-in info bar, type in the one your VPN provider uses and click on Save.
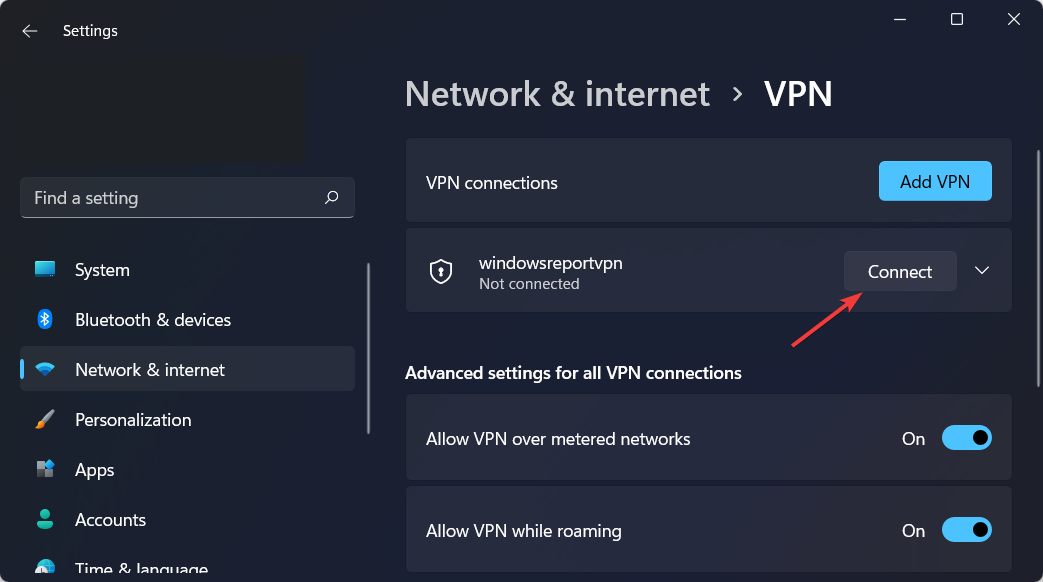
- When the name of the VPN appears, connect to it.
Is there any good 3rd party VPN for business?
There is another security method to protect all your business data and avoid certificate validation failure for your VPN protection.
You can use the Perimeter 81 as a Zero Trust Application Access software and secure any sensitive data from public use. This way, you guarantee private communication with IPSec or WireGuard technology.
Plus, it provides safer digital support against data leaking or cyber threats with access by role, a cloud-based interface, or monitoring tools.
⇒ Get Perimeter 81
In conclusion, VPN is vital because of the protection and security that users get from it. These steps will fix the validation failure that pops up. However, if these do not work, you can disconnect completely and start a new connection.
Check out our post with the five best VPNs for Windows 11, after 3 months of usage and tests, to decide which one to get on your devices.
We hope our guide proved to be useful to you. Don’t hesitate to share your thoughts with us in the comments section below. Thanks for reading!
Newsletter
На чтение 10 мин Просмотров 2.8к. Опубликовано 01.12.2020
Я установил безопасный мобильный клиент cisco anyconnect 4.2.01022 (+ все необходимые пакеты).
Затем добавили .pfx сертификатов в хранилище gnone2-key .
Затем я запустил cisco anyconnect, защищенный мобильный клиент, набрал, где подключиться, но cisco продолжает говорить мне, что Certificate validation failure
была создана, но не помогла. Как подключиться?
Таким образом, я извлек некоторые сертификаты в разных форматах:
Поместили все 4 из них в 3 разных местах:
Доверенные CA и корневые сертификаты
UPD2: пытался настроить cisco anyconnect, совместимый с openconnect (который интегрирован в сетевой центр linux): Он просит установить:
Но если пытается подключиться:
Я принимаю — и ту же ошибку Ошибка проверки сертификата, полный журнал:
PS: На окнах выполняются одинаковые шаги, добавлен сертификат двойным щелчком, затем запускается клиент cisco, набирается сервер, затем он спрашивает пароль на сервере, которого я хочу, — и затем я был подключен.
Когда я пытаюсь подключиться, используя Cisco AnyConnect VPN Client, я получаю эту ошибку:
Попытка подключения не удалась из-за проблемы с сертификатом сервера .
У меня была эта проблема в моей предыдущей установке Ubuntu 11.10. Тогда я мог бы исправить это, используя некоторые учебники в Интернете (я не помню, какой именно). В основном они предложили установить 4-5 пакетов, а затем и несколько ln -s . Но на этот раз никто из них не работает. Может ли кто-нибудь помочь мне шаг за шагом?
7 ответов
Я могу подтвердить, что эта проблема существует. Клиент Anyconnect работал нормально с 11.10, но перестает работать с 12.04. Старый трюк со ссылками на библиотеки Firefox больше не работает. Я использую OpenConnect.
Подробнее о проблеме Cisco Anyconnect:
Как видно из журнала: пользователь был удалось войти, но клиенту Anyconnect все еще не удалось установить vpn-соединение.
Клиент Cisco AnyConnect VPN (версия 2.5.3055).
Убедитесь, что у вас установлен Firefox и вы можете его успешно запустить. Если все прошло успешно, попробуйте выполнить еще несколько шагов по устранению неполадок.
Вот как я это сделал.
Затем я выяснил, какой центр сертификации мы используем, а именно COMODO, нашел сайт, который использует этот ЦС, загрузил его с помощью браузера и поместил в
Проблема решена в Ubuntu 12.04 64 бит. смотрите здесь: http://www.oit.uci.edu/security/vpn/vpn-lin.html
У меня сработало следующее исправление — новая установка 12.04 LTS 32bit (с Firefox 12). Установил клиент AnyConnect, затем попытался запустить его.
Получил это сообщение:
AnyConnect не может подтвердить, что он подключен к вашему безопасному шлюзу. Локальная сеть может быть ненадежной. Пожалуйста, попробуйте другую сеть.
Проверен системный журнал в Ubuntu. Много такого рода вещей:
Создано / .cisco/certificates/ca каталогов в /opt с использованием sudo
Мы используем Globalsign в качестве нашего центра сертификации. Поэтому я просто скопировал все файлы Globalsign .pem из /etc/ssl/certs . Если вы не знаете своего провайдера, вы можете просто скопировать все.
или если CA неизвестен
Мне удалось запустить клиент AnyConnect и подключиться к VPN
Надеюсь, это поможет.
Я попробовал эти решения, перечисленные выше, и ни одно из них не помогло. Но когда я попробовал некоторые из приведенных ниже решений, связанных с библиотеками Firefox, я добился успеха!
Я не могу сказать, какое решение является ЛУЧШИМ, но я следовал указаниям на обоих этих сайтах и имел успех. Возможно, вы можете найти решение, которое работает для вас. Если вы знаете, какой из них лучший, пожалуйста, сообщите нам, какая переменная решает проблему немедленно. Все, что я знаю, это то, что после внесения некоторых из этих изменений я наконец-то заработал на своей Cisco Anyconnect VPN. Я Firefox на Ubuntu 12.04.
Сразу хочу отметить, — не собираюсь устраивать холивар на счет того, что лучше — ASDM or console: на вкус и цвет все фломастеры разные…Я предпочитаю ASDM и настройки такого плана произвожу именно через нее. Поэтому статья будет насыщенна картинками (скринами)
Итак, приступим. Начнем с настройки LDAP сервера (в нашем случае это DC ActiveDirectory), для этого переходим в Configuration > DeviceManagement > Users/AAA > AAA Server Groups и создаем группу, назовем ее OFFICE, Protocol указываем LDAP
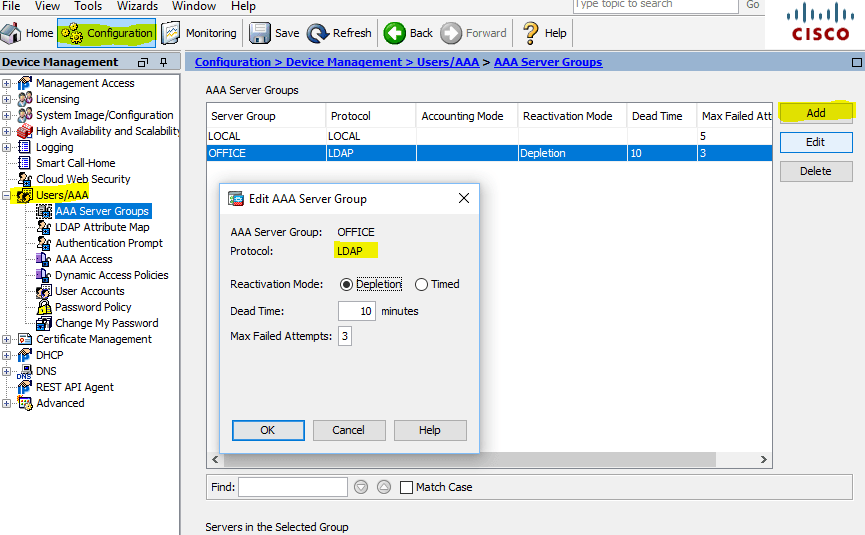
Configuration Cisco ASA AAA Server Groups
Для того, чтобы добавить сервер в созданную группу, нам необходимо предварительно создать LDAP Atribute Map. Для этого переходим в соответствующий раздел: Configuration > DeviceManagement > Users/AAA >LDAP Attribute Map и создаем новую карту: в нашем случае это Map Name: AD, Mapping of Attribute Name > LDAP Attribute Name: memberOf, Cisco Attribute Name: IETF-Radius-Class
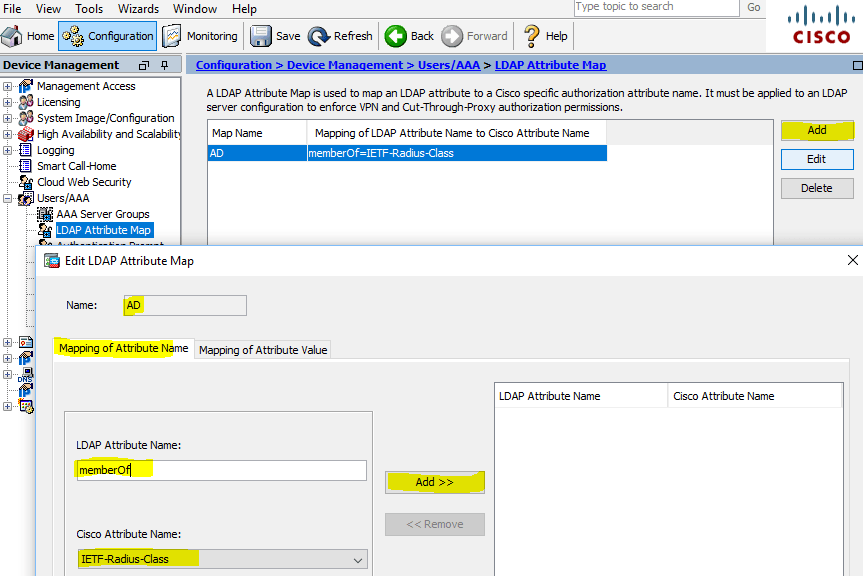
LDAP Attribute Map
Теперь можно добавить сервер (настроить подключение к контроллеру домена), указываем интерфейс, через который будем подключаться, IP адрес DC, Server Type: Microsoft, Base DN, Naming Attribute: sAMAccountName, Login DN, Login Password, только что созданную карту LDAP Attribute Map: AD, Group Base DN:
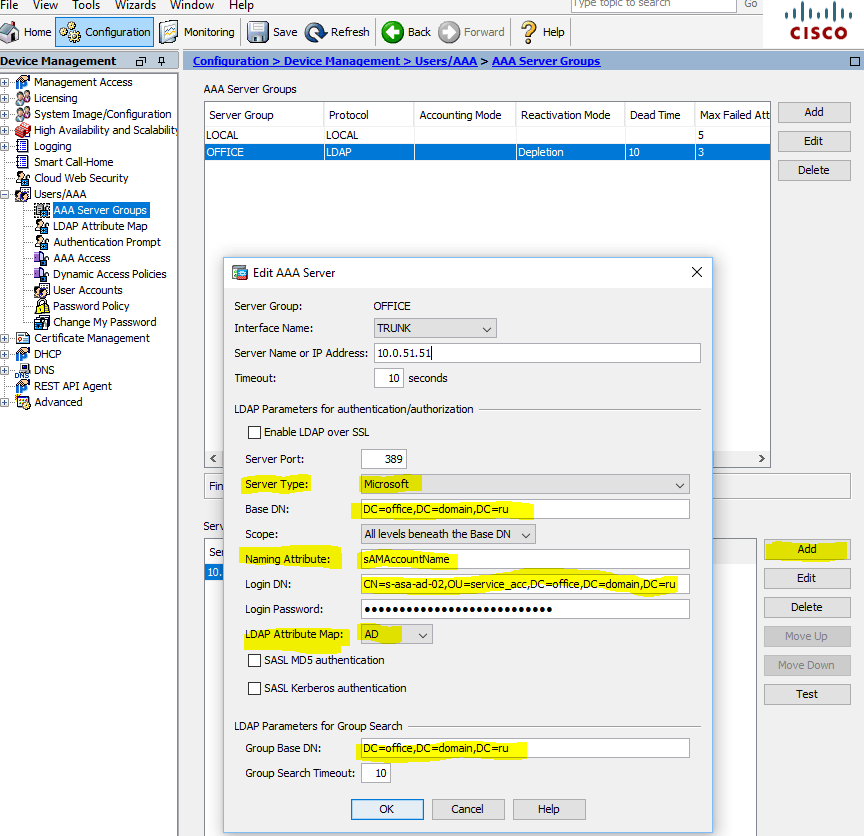
AAA Server — Microsoft DC
Add AAA Server
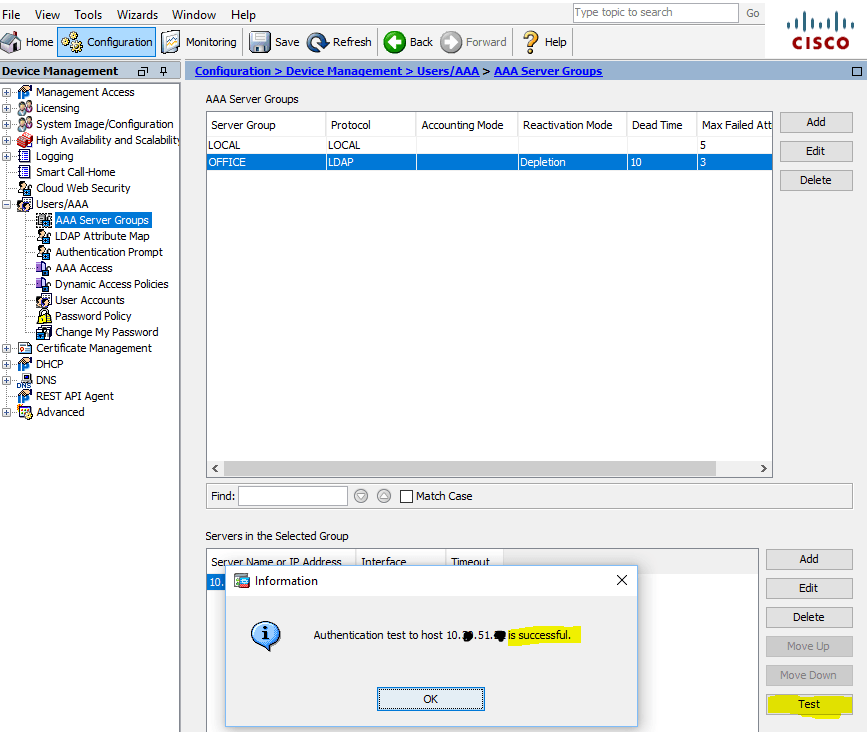
После добавления сервера делаем проверку, проходим аутентификацию учетной записью AD:
Test AAA Server — Authentication
Теперь можно добавить сертификат удостоверяющего центра (используется Microsoft CA, в рамках статьи о его настройке рассказывать не буду, единственное о чем следует обязательно помнить: Cisco ASA не воспринимает сертификаты с Signature algorithm RSASSA-PSS, который Microsoft предлагает использовать по умолчанию. мы меняли на sha512RSA):
Identity Certificates Signature algorithm RSASSA-PSS — sha512
Переходим Configuration > DeviceManagement >Certificate Management > Identity Certificates и импортируем в формате PKCS12 (*.pfx сертификат + private key):

Identity Certificates Signature algorithm sha512RSA (ECDSA 521 bits)
С подготовительными действиями закончили, можно переходить к настройке профилей для AnyConnect VPN. Для примера, будем использовать 2 профиля, у которых будут разные IP Address Pools и соотв. ACL, Dynamic Access Policies, Group Policies и соответственно 2 группы ActiveDirectory. При подключении пользователей по ВПН используем политику «Туннелирование только указанных сетей», так называемый Split Tunneling, чтобы не гнать весь пользовательский траффик через впн. Но это «на любителя», может кому-то, наоборот, такое потребуется — последнее время это очень актуально 😉
Начнем с IP Address Pools, для этого переходим в Configuration > Remote Access VPN > Network (Client) Access > Address Assignment > Address Pools
Создадим пул адресов (сегмент) для администраторов (назовем, например VPN_Admins):
Address Assignment — Address Pools
Далее создадим политику (это основная часть настроеек профиля, в которой можно задат: протоколы, которые будут использоваться для туннелей, время доступа, количество одновременных логинов, закрыть доступы к определенным VLAN, выставить таймауты, задать DNS серверы, настроить Split Tunneling, клиентский файерволл и тд и тп) — в общем этой настройке следует уделить особое внимание! Итак, начнем: Configuration > Remote Access VPN > Network (Client) Access > Group Policies, Add Internal Group Policy
Все выставленные параметры сугубо индивидуальны — в нашем случае немного параноидальны Указаны протоколы, которые допускаются для создания туннеля (Tunneling Protocols), временной период для доступа по ВПН (Access Hours), количество одновременных подключений с одной учетной записью (Simultaneous Logins), максимальное время для сеанса и пр.:
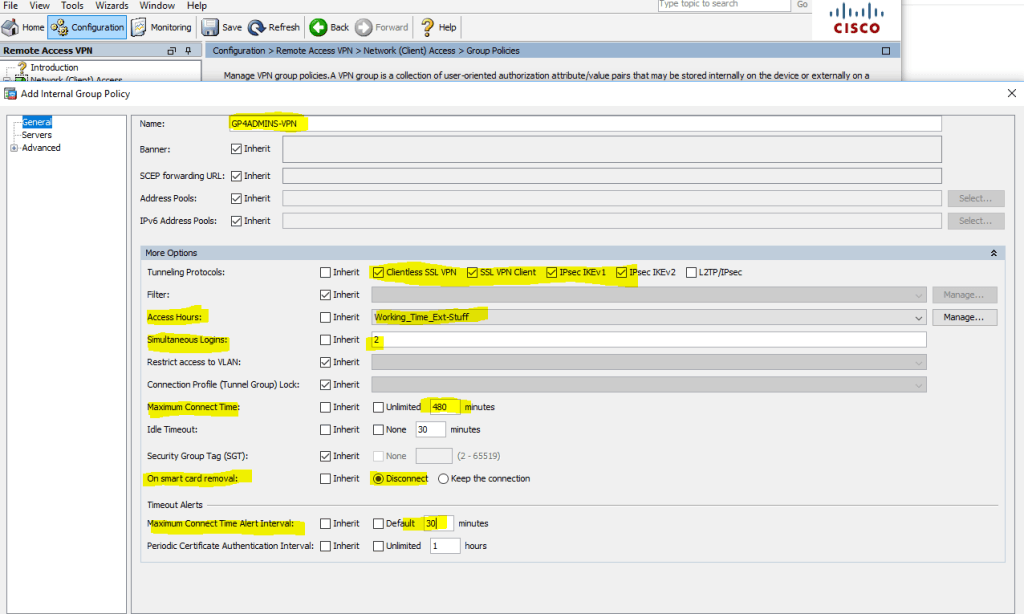
Configuration > Remote Access VPN > Network (Client) Access > Group Policies > Add Internal Group Policy
Следующая полезная настройка — вкладка Servers, в которой мы можем указать внутр. ДНС серверы, для пользователей ВПН AnyConnect, чтобы они могли обращаться к внутренним ресурсам по имени:
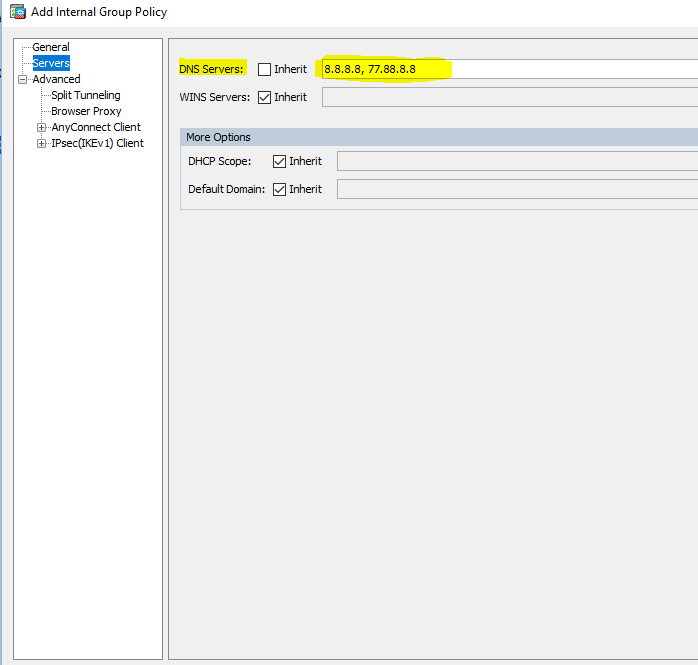
Configuration > Remote Access VPN > Network (Client) Access > Group Policies > Edit Internal Group Policy — Servers
Теперь перейдем к еще одной интересной опции — настройке Split Tunneling. Как я уже писал ранее — будем использовать политику «туннелирование только указанных сетей» (мы не заворачиваем в туннель весь траффик пользователей и разрешаем доступ к локальным ресурсам — опция «Local Lan Access» далее будет отдельно рассмотрена):
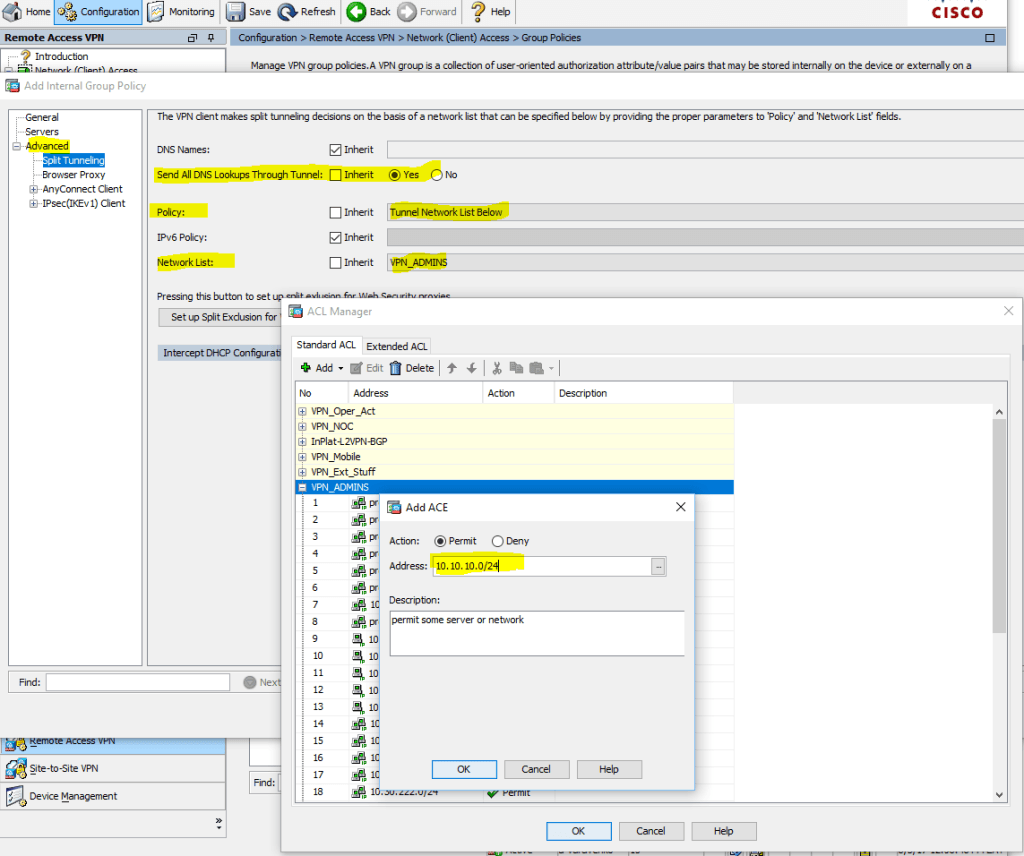
Configuration > Remote Access VPN > Network (Client) Access > Group Policies > Edit Internal Group Policy > Advanced > Split Tunneling >
Ранее мы указали к каким сетямхостам мы разрешили доступ, теперь ограничим доступ к ним по протоколампортам (еще один ACL):

Configuration > Remote Access VPN > Network (Client) Access > Group Policies > Edit Internal Group Policy > Advanced > AnyConnect Client > Client Firewall > Private Network Rule
В итоге, после подключения к впн AnyConnect клиентом, можно увидеть маршруты в сторону туннеля и правила файерволла:

AnyConnect Client > Route Details
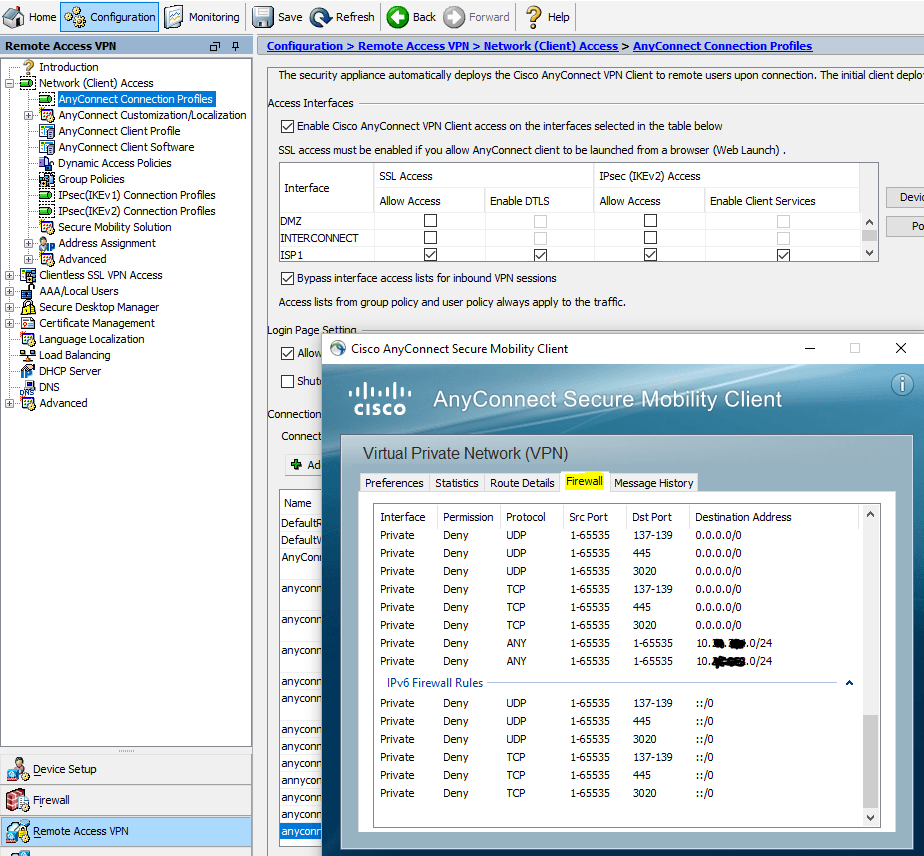
AnyConnect Client > Firewall
Теперь можно перейти непосредственно к созданию профиля AnyConnect, переходим Configuration > Remote Access VPN > Network (Client) Access > AnyConnect Connection Profiles >, Add AnyConnect Connection Profile
и указываем: Name, Aliases, далее Authentication Method (AAA and certificate), AAA Server Group, Client Address Pools, Group Policy — все созданное ранее!

Configuration > Remote Access VPN > Network (Client) Access > AnyConnect Connection Profiles > Add AnyConnect Connection Profile > Basic
И теперь небольшой «лайфхак» — мы из пользовательского сертификата вытащим значение E-mail и с помощью регулярки (.*)@ отрежем от него @domain.ru
(значение E-mail должно быть %AD username%@somedomain.ru ) и подставим его в поле Username при подключении.

Configuration > Remote Access VPN > Network (Client) Access > AnyConnect Connection Profiles > Add AnyConnect Connection Profile > Advanced > Authentication > Username Mapping from Certificate
Когда профили настроили — мы уже можем подключаться, потому как будет отрабатывать политика по умолчанию DfltAccessPolicy для всех пользователей, прошедших аутентификацию (у нее самый высокий приоритет). Мы же хотим, чтобы для разных групп ActiveDirectory использовался свой профиль и отрабатывала своя групповая политика политика доступа. Поэтому, переходим: Configuration > Remote Access VPN > Network (Client) Access > Dynamic Access Policies и запрещаем DfltAccessPolicy (на самом деле не запрещаем, а делаем Terminate с уведомлением пользователя — хорошая диагностика того, что пользователь не включен в требую группу ActiveDirectory):
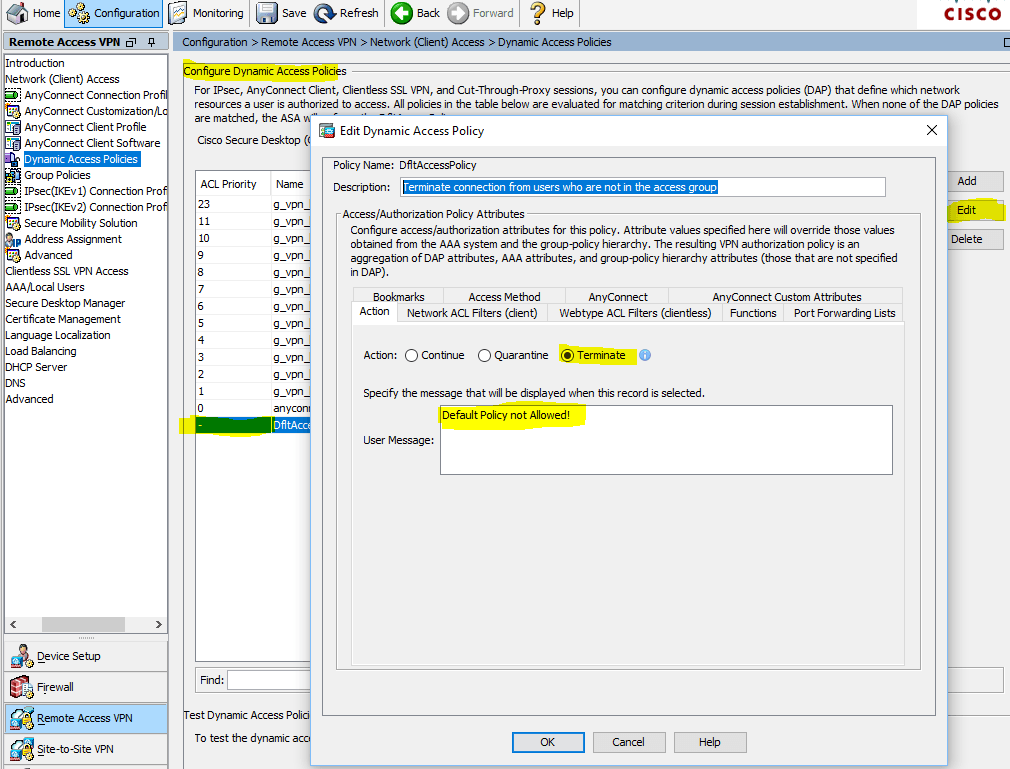
Configuration > Remote Access VPN > Network (Client) Access > Dynamic Access Policies
Terminate connection from users who are not in the access group
После того, как политику по умолчанию запретили, — создадим новую:
Configuration > Remote Access VPN > Network (Client) Access > Dynamic Access Policies > Add Dynamic Access Policy

Configuration > Remote Access VPN > Network (Client) Access > Dynamic Access Policies > Add Dynamic Access Policy with AAA Attributes
где g_vpn_level_01 — созданная в ActiveDirectory группа безопасности, куда мы включаем необходимые админские учетки, для подключения по ВПН AnyConnect с профилем VPN-ADMINS:

Configuration > Remote Access VPN > Network (Client) Access > Dynamic Access Policies > Add Dynamic Access Policy with AAA Attributes > Get AD Groups
ну и заключительный «штрих» — рекомендую сохранить созданный профиль в файл (полезно, например, для синхронизации профилей для StandBy unit при Failover конфигурации):
Configuration > Remote Access VPN > Network (Client) Access > AnyConnect Client Profile
После того, как профиль сохранен — его можно немного «потюнинговать»: помните я говорил про опцию»Local Lan Access«? Она как раз здесь настраивается. А еще здесь же можно настроить выбор хранилища сертификатов; автообновление клиента AnyConnect; разрешитьзапретить возможность подключения к компьютеру через рдп, при подключенном впн; указать версию протокола (IPv4 or IPv6 or both); параметры сертификатов и серверов; мобильные политики. В общем — есть, что «подкрутить» под ваши нужды!
Configuration > Remote Access VPN > Network (Client) Access > AnyConnect Client Profile > Edit
Для второй группы — «VPN-USERS» проделываем тоже самое…
Содержание
- How to Fix “VPN Certificate Validation Failure” Error
- 1. Go through standard troubleshooting steps
- 2. Double-check the VPN client profile
- 3. Has the SSL/TLS certificate expired?
- 4. Install a new SSL or TLS certificate
- I want to use the PEM client certificate. What should I do?
- 5. Configure cryptography
- 1. Allowing SSL client certificates to be used on the outside
- 2. Fixing TLS version mismatch and changing cryptography method
- 6. Enable or disable Windows OCSP Service Nonce
- 1. Enable OCSP Nonce on Windows Server
- 2. Disable Nonce via ASA TrustPoint
- Milan
- Certificate validation failure cisco anyconnect как исправить mac os
- Certificate validation failure cisco anyconnect как исправить mac os
- What is Cisco AnyConnect?
- Cisco AnyConnect Review: Features
- What is “Cisco AnyConnect Certificate Validation Failure” Error on Windows?
- [Tips & Tricks] How to fix Cisco AnyConnect Certificate Validation Failure Problem?
- Procedure 1: Repair the Installation
- Procedure 2: Allow VPN to freely communicate through Firewall
- Procedure 3: Check Virtual Adapter driver in Device Manger and update it
- Procedure 4: Tweak Registry and Repair Cisco VPN
- Procedure 5: Update the AnyConnect
- Procedure 6: Create Trustpoints for each certificate being installed
- Procedure 7: Perform Clean Reinstallation
- Conclusion
- Руководство по настройке проверки подлинности ASA AnyConnect с проверкой, сопоставлением и предварительным заполнением сертификата
- Параметры загрузки
- Об этом переводе
- Содержание
- Введение
- Предварительные условия
- Требования
- Используемые компоненты
- Настройка
- Сертификат для AnyConnect
- Установка сертификатов на ASA
- Конфигурация ASA для одинарной проверки подлинности и проверки сертификата
- Проверка
- .debug
- Конфигурация ASA для двойной проверки подлинности и проверки сертификата
- Проверка
- .debug
- Конфигурация ASA для двойной проверки подлинности и предварительного заполнения
- Проверка
- .debug
- Конфигурация ASA для сопоставления двойной аутентификации и сертификата
- Проверка
- .debug
- Устранение неполадок
- Подтвержденный сертификат отсутствует
How to Fix “VPN Certificate Validation Failure” Error
The “VPN certificate validation failure” error is exclusive to the Cisco AnyConnect VPN client for Windows, Mac, and Linux. An added reason for a quick solution is that the software is frequently used in a business setting, interconnecting computers into a secure, efficient network. And while it performs wonderfully most of the time, things sure can go wrong unexpectedly. What’s more, employees can’t always reach a network engineer and are often left to their own devices. That’s precisely when we’d like to swoop in and save the day. Let’s demonstrate how to fix the “VPN certificate validation failure” error.
1. Go through standard troubleshooting steps
Before you get into an array of unnecessary steps, make sure the problem isn’t a glitch, bug, or temporary downtime. By this, we mean going through steps 1 through 6 in our “VPN connection failed. The Request was aborted” error fix guide. Once you’ve tried that and it didn’t work, press on.
2. Double-check the VPN client profile
In essence, you need to verify the hostname and host address are still valid. Even if you haven’t made changes manually, your network admin might have, to the server or the client. To demonstrate this, we’ll use Cisco AnyConnect VPN client profile on macOS:
3. Has the SSL/TLS certificate expired?
A common cause of the “VPN certificate validation failure” error is the expiration of the SSL certificate. While in the past they were issued for longer, in 2022 the period is reduced to either 12 months or 13 months (397 days). Although there are many ways to do this, we’ll use the ASDM client to demonstrate checking SSL/TLS certificate expiration date:
4. Install a new SSL or TLS certificate
If your certificate expired, then you know regenerating them is the way to fix the “VPN certificate validation failure” error. Here’s what to do:
I want to use the PEM client certificate. What should I do?
So, you’re using AnyConnect VPN on Linux or Mac. If you haven’t installed certificates yet, download the client certificate and its private key and place them here:
/.cisco/certificates/client/private/” (private key here)
Clarification. The certificate must end with .pem while the private key must end with .key. Also, they must have identical file names.
5. Configure cryptography
Although there are ways to do this within the GUI, it’s much quicker and easier to simply run CLI (command-line interface) commands. Here’s what you can try:
1. Allowing SSL client certificates to be used on the outside
This is a step Cisco itself recommends as a permanent fix for the “VPN certificate validation failure” error. It simply makes client-side certificates available externally. Here’s how to proceed:
2. Fixing TLS version mismatch and changing cryptography method
There’s a chance that your VPN client isn’t up to date, or that there’s some sort of conflict which makes it use TLS 1.0 or TLS 1.1. This creates a problem when your cryptography tries to negotiate TLS 1.2. To fix this, open the CLI and proceed in one of 3 ways:
6. Enable or disable Windows OCSP Service Nonce
Without getting into specifics, you should know that Microsoft Windows uses RFC 5019 while Cisco AnyConnect VPN’s ASA is only compliant with RFC 2560. As such, on Windows, it won’t accept requests signed by ASA certificates and thus print “VPN certificate validation failure” error. You can fix this in one of 2 ways:
1. Enable OCSP Nonce on Windows Server
Are you (or your company) using an Online Certificate Status Protocol (OCSP) responder on your Windows Server? If so, do this:
2. Disable Nonce via ASA TrustPoint
Although Cisco recommends the method above, you can also try to disable OCSP via the CLI. After launching the appropriate interface, use these commands:
Tip. Replace WIN-2K12-01_Root_CA with the actual TrustPoint name of your certificate (you can see it using method 4).
Milan
VPN is one of my passions. I love being secure and helping others avoid any potential threats online. I also contribute to several VPN guide websites online.
Источник
Certificate validation failure cisco anyconnect как исправить mac os
I have an anyconnect account set up using version 3.0.5080 and connecting to an ASA 5510 base 8.2(2)17. We are using certificates for authentication. If I try and use the account on a windows machine it all works fine.
However on a mac running Lion if I try and connect via a web browser or already have the anyconnect client loaded and try to connect I always get “certificate Validation Failure”. I double checked the certificate was correct and am sure that is correct as it is the same certificate on the Windows and the mac. After searching online I have also tried editing the anyconnect profile to so it is set “certificate store override”, and put the certificates and key in the “user/.cisco/certificates” and “/opt/.cisco/certificates” folders.
After further testing, if I change the anyconnect connection profile to “authentication aaa” I can connect fine. Then if I disconnect, change it back to “authentication certificate” I can connect fine the first time, but all the following subsequent efforts I make fail. If I repeat this process this happens each time, I can connect the first time but after that it fails with the same “certificate Validation Failure” error message. When it connects this first time I checked and confirmed that it is definitely using the certificate. I have also tried using both authentication methods (“authentication aaa certificate”) and had the same problem.
This leads me to believe that my configuration is correct and it is some bug in the anyconnect client or the ASA image. I have had a look through bugs and read somewhere that there was a bug on earlier versions of 8.4, but nothing about 8.2. Does anyone have any recommendations of anything else I can try to fix the problem.
Источник
Certificate validation failure cisco anyconnect как исправить mac os
If you are facing “Cisco AnyConnect Certificate Validation Failure” problem while trying to connect on the AnyConnect Client, then you are in right place. Here, we are discussing on “ How to fix AnyConnect Certificate error ” in details and providing some recommended methods to fix this error. Let’s starts the discussion.
What is Cisco AnyConnect?
“Cisco AnyConnect” is proprietary application that lets users connect to VPN service. Many universities use this application as part of service they pay for from Cisco that’s why public institutions unnecessarily rely on this closed-source software for their own students. This doesn’t just amount to handling control to a private corporation, thereby privatizing public money. This software also provide extra security layer to reduce potentially unwanted attacks and privacy vulnerability.
Cisco AnyConnect is unified endpoint agent that delivers multiple security services to protect the enterprise. Its wide range of security services includes functions such as remote access, posture enforcement, web security features, and roaming protection. It gives all the security features for IT department to provide a robust, user-friendly, and highly secure mobile experience as well.
Cisco AnyConnect security mobility client is modular endpoint software product that not only provides VPN access via SSL (Secure Socket Layer) and IPsec IKEv2 but also offers improved security via various built-in modules including compliance through VPN and ASA or through wired /wireless, and VPN with Cisco identity Services Engine (ISE), Off-network roaming protection with Cisco Umbrella.
Since, Cisco has been a long-term target of NSA spying program. It also doesn’t work well on Linux. There is nothing wrong with supporting free and open source solutions like OpenVPN which are used by numerous users worldwide. Linux, iOS, Windows, MacOS and Android OS are some of the popular tools that integrate with Cisco Anyconnect.
Cisco AnyConnect Review: Features
What is “Cisco AnyConnect Certificate Validation Failure” Error on Windows?
“AnyConnect Certificate error” is common error reported by numerous users on Cisco official forum site or other popular platforms and asked for the solution. Users explained on Cisco Community website that the error appears when they run their own CA that gives out the client certificates for our users as well as the identity certificate for ASA, and in order to click on “Connect” on AnyConnect Client, their client receives “No Valid Certificates available for authentication” message.
Furthermore, he also created a DART bundle and in there I can see that the certificate is selected from the “Microsoft Store”, but after that he receive several errors regarding SCHANNEL. Then, he tried another certificate authentication and finds no certificates followed by “Cisco AnyConnect Certificate Validation Failure” Error.
Certificate Validation Failure Error States:
When we talk about “Anyconect Certificate validation Failure error”, it explained that it can’t verify the VPN server which is to be expected since it uses the self-signed certificate, but if they connect anyway, then they receive the certification selection and the login works fine. It means username & password for login is taken from the certificate.
[Tips & Tricks] How to fix Cisco AnyConnect Certificate Validation Failure Problem?
Procedure 1: Repair the Installation
Step 1: Click on “Start” button and type “Control Panel” in Windows search and open “Control Panel”
Step 2: In the opened “Control Panel”, choose “Uninstall a program” and find “Cisco AnyConnect VPN” client and choose “Repair”
Step 3: Follow On-Screen instructions to finish the repairing process. Once done, restart your computer and please check if the problem is resolved.
Procedure 2: Allow VPN to freely communicate through Firewall
Step 1: Click on “Start” button and type “Allow an App” in Windows Search and open “Allow an App through Windows Firewall”
Step 2: Now, click on “Change Settings”
Step 3: Make sure that “Cisco VPN” is on the list and it’s allowed to communicate through Windows Firewall. If not, click “Allow another App” and add it
Step 4: Check both “Private” and “Publicrong” > Network boxes
Step 5: Confirm changes and open Cisco VPN
Procedure 3: Check Virtual Adapter driver in Device Manger and update it

Step 1: Press “Windows + X” key from keyboard and select “Device Manager”
Step 2: In the opened “Device Manager” window, locate and expand “Network Adapters”
Step 3: Right-click on Virtual Adapter and select “Update driver software”
Step 4: Follow On-Screen instructions to finish the updating process.
Step 5: Once done, restart your computer and please check if the problem is resolved.
Procedure 4: Tweak Registry and Repair Cisco VPN
Step 1: Press “Windows + R” keys together from keyboard and type “regedit” in “Run Dialog Box” and then hit “Ok” button
Step 2: In the opened “Registry Editor” window, navigate to “HKEY_LOCAL_MACHINE/SYSTEM/Current/Control/SetServices/CVirtA”
Step 3: Right-click on the “DisplayName” registry entry and choose “Modify”
Step 4: Under “Value Data” section, make sure that the only body of text which stands is Cisco System VPN Adapter
Step 5: Save the changes and try running Cisco AnyConnect VPN again.
Procedure 5: Update the AnyConnect
Step 1: Go to “ASDM > Configuration > Remote Access VPN > Network (Client) Access > AnyConnect Client Software”
Step 2: You can either replace the existing the image or add a new one.
Step 3: After that, connect to the ASA. The client will be updated automatically.
Procedure 6: Create Trustpoints for each certificate being installed
Step 1: Open the “Cisco ASDM”
Step 2: Under “Remote Access VPN” window pane, click on “Configuration” tab and expand “Certificate Management” and click on “CA Certificates”
Step 3: Click on “Add” button
Step 4: Assign a “TrustPoint Name” to the certificate like “DigiCertCA2” and select “Install from the file” Radio button and browse to “DigiCertCA2.crt”, then click on “Install Certificate”. Repeat this process of adding new trustpoint and installing certificate file for “DigiCertCA.crt”
Step 5: Under “Remote Access VPN”, expand “Certificate Management” to “Identify Certificates”. Select the identity you created for the CSR with “Expiry Data” and click on “Install > Install Certificate”
Step 6: The Certificate now needs to be enabled. To do so, click on “Advanced > SSL Settings > Edit > Primary Enrolled Certificate” and select your certificate and then click on “Ok”
Step 7: ASDM will then show your Certificate details under trustpoint
Procedure 7: Perform Clean Reinstallation
Step 1: Navigate to “Control Panel” and choose “Uninstall a program”
Step 2: Uninstall “Cisco AnyConnect VPN Client”
Step 3: Navigate to System partition and delete everything Cisco-related from programs folder
Step 4: Once uninstalled completely, restart your computer
Step 5: After that, download latest version of “Cisco AnyConnect” from “Cisco official website”
Step 6: Double-click on installer file and follow on-screen instructions to finish the installation.
Step 7: Once installed, restart your computer again and please check if the AnyConnect Certificate error is resolved.
Conclusion
Cisco AnyConnect is VPN service that offers Standard VPN encryption and protection. When we talk about AnyConnect Secure Mobility Client, it is modular endpoint software product. It not only provides Virtual Private Network (VPN) access through Secure Sockets layer (SSL) and Internet Protocol Security (IPsec) Internet Key Exchange version2 (IKEv2), but also offers enhanced security through various built-in modules.
I am sure this article helped you to “Fix Cisco AnyConnect Certificate Validation Failure Windows 10” with several easy methods/procedures. You can choose/follow either one or all procedures to fix this issue.
If you are unable to fix Cisco AnyConnect Certificate Validation Failure problem with the solutions mentioned above, then it might possible that your System has infected with malware or viruses. According to security researchers, malware or viruses cause several damages in your computer.
In this case, you can scan your computer with powerful antivirus software that has the ability to delete all types of malware or viruses from System.
Источник
Руководство по настройке проверки подлинности ASA AnyConnect с проверкой, сопоставлением и предварительным заполнением сертификата
Параметры загрузки
Об этом переводе
Этот документ был переведен Cisco с помощью машинного перевода, при ограниченном участии переводчика, чтобы сделать материалы и ресурсы поддержки доступными пользователям на их родном языке. Обратите внимание: даже лучший машинный перевод не может быть настолько точным и правильным, как перевод, выполненный профессиональным переводчиком. Компания Cisco Systems, Inc. не несет ответственности за точность этих переводов и рекомендует обращаться к английской версии документа (ссылка предоставлена) для уточнения.
Содержание
Введение
Этот документ описывает пример конфигурации для доступа к клиенту Cisco AnyConnect Secure Mobility Client на платформе Adaptive Security Appliance, который использует двойную проверку подлинности с проверкой сертификата. Как и все остальные пользователи AnyConnect, вы должны предоставить правильный сертификат и указать учетные данные для основной и дополнительной проверки подлинности, чтобы получить доступ к VPN. В этом документе также приведен пример сопоставления сертификатов с функцией предварительного заполнения.
Предварительные условия
Требования
Компания Cisco рекомендует предварительно ознакомиться со следующими предметами:
Используемые компоненты
Сведения, содержащиеся в этом документе, касаются следующих версий программного обеспечения:
Предполагается, что вы используете внешний Центр сертификации (ЦС) для создания:
Настройка
Примечание.Воспользуйтесь инструментом Command Lookup ( только для зарегистрированных заказчиков), чтобы получить дополнительную информацию о командах, используемых в этом разделе.
Сертификат для AnyConnect
Чтобы установить образец сертификата, дважды щелкните файл anyconnect.pfx и установите сертификат как персональный сертификат.
Используйте диспетчер сертификатов (certmgr.msc), чтобы проверить установку:
По умолчанию AnyConnect пытается найти сертификат в пользовательском магазине Microsoft; изменять профиль AnyConnect не нужно.
Установка сертификатов на ASA
Этот пример демонстрирует импорт сертификата PKCS # 12 в кодировке base64 с платформы ASA:
Выполните команду show crypto ca certificates, чтобы проверить импорт:
Примечание. Средство интерпретации выходных данных (только для зарегистрированных заказчиков) поддерживает некоторые команды show. Используйте Средство интерпретации выходных данных, чтобы просмотреть анализ выходных данных команды show.
Конфигурация ASA для одинарной проверки подлинности и проверки сертификата
ASA использует как аутентификацию ААА (проверка подлинности, авторизация и обработка учетных записей), так и проверку подлинности сертификата. Проверка достоверности сертификата является обязательной. Для аутентификации AAA (проверка подлинности, авторизация и обработка учетных записей) используется локальная база данных.
В этом примере показана одинарная проверка подлинности с проверкой сертификата.
Помимо этой конфигурации, можно выполнить авторизацию LDAP, используя имя пользователя из конкретного поля сертификата (например, поле имени сертификата (CN)). После этого можно получить и применить дополнительные атрибуты для VPN-сеанса. Дополнительные сведения о проверке подлинности и авторизации сертификата см. в разделе «Авторизация ASA Anyconnect VPN и OpenLDAP с примерами настраиваемой схемы и конфигураций сертификатов.»
Проверка
Примечание. Средство интерпретации выходных данных (только для зарегистрированных заказчиков) поддерживает некоторые команды show. Используйте Средство интерпретации выходных данных, чтобы просмотреть анализ выходных данных команды show.
Для тестирования этой конфигурации укажите локальные учетные данные (имя пользователя cisco и пароль cisco). Требуется наличие сертификата:
Выполните команду show vpn-sessiondb detail anyconnect на ASA:
.debug
Примечание.Перед использованием команд debug обратитесь к документу Важные сведения о командах отладки.
В этом примере сертификат не кэшируется в базе данных, найден соответствующий ЦС; использован правильный ключ (CLientAuthentication), и сертификат успешно прошел проверку достоверности:
Подробные команды отладки, такие как debug webvpn 255, могут создавать множество журналов в рабочей среде и размещать на ASA интенсивную рабочую нагрузку. Некоторые процедуры отладки WebVPN удалены для ясности:
Это попытка найти подходящую группу туннелей. Конкретные правила сопоставления сертификатов отсутствуют, и используется указанная группа туннелей:
Далее приведены процедуры отладки SSL и общего сеанса:
Конфигурация ASA для двойной проверки подлинности и проверки сертификата
Здесь приводится пример двойной проверки подлинности, где используется сервер основной проверки подлинности LOCAL и сервер дополнительной проверки подлинности LDAP. Проверка достоверности сертификата по-прежнему включена.
В этом примере демонстрируется конфигурация LDAP:
Здесь показано добавление сервера дополнительной проверки подлинности:
В конфигурации не отображается «authentication-server-group LOCAL», так как это параметр по умолчанию.
Для «authentication-server-group» можно использовать все остальные серверы AAA Для «secondary-authentication-server-group» можно использовать все серверы AAA кроме сервера Security Dynamics International (SDI); в этом случае SDI может выступать в роли сервера основной проверки подлинности.
Проверка
Примечание. Средство интерпретации выходных данных (только для зарегистрированных заказчиков) поддерживает некоторые команды show. Используйте Средство интерпретации выходных данных, чтобы просмотреть анализ выходных данных команды show.
Чтобы протестировать эту конфигурацию, укажите локальные учетные данные (имя пользователя cisco и пароль cisco) и учетные данные LDAP (имя пользователя cisco и пароль из LDAP). Требуется наличие сертификата:
Выполните команду show vpn-sessiondb detail anyconnect на ASA.
.debug
Отладка сеанса WebVPN и проверки подлинности во многом схожи. См. раздел «Конфигурация ASA для одинарной проверки подлинности, проверки достоверности сертификата и отладки» Отображается один дополнительный процесс проверки подлинности:
Процедуры отладки LDAP отображают сведения, которые могут отличаться от конфигурации LDAP:
Конфигурация ASA для двойной проверки подлинности и предварительного заполнения
Можно сопоставить отдельные поля сертификата с именем пользователя, которое используется для основной и дополнительной проверки подлинности:
В этом примере клиент использует сертификат: cn=test1,ou=Безопасность,o=Cisco,l=Krakow,st=PL,c=PL.
Для основной проверки подлинности имя пользователя берется из имени сертификата, и именно по этой причине создан локальный пользователь «test1».
Для дополнительной проверки подлинности имя пользователя взято из организационного подразделения (OU, по этой причине на сервере LDAP создан пользователь «Security»).
Кроме того, возможно принудительно настроить в AnyConnect использование специальных команд для предварительного заполнения основного и дополнительного имени пользователя.
В реальном сценарии в качестве сервера основной проверки подлинности обычно используется сервер AD или LDAP, а в качестве сервера дополнительной проверки подлинности — сервер Rivest, Shamir и Adelman (RSA), который использует пароли токенов. В этом сценарии пользователю необходимо указать учетные данные AD/LDAP (которые известны пользователю), пароль токена RSA (который есть у пользователя) и сертификат (на используемом компьютере).
Проверка
Обратите внимание, что нельзя изменить основное или дополнительное имя пользователя, поскольку оно предварительно заполнено на основе данных из полей CN и OU:
.debug
В этом примере показан предварительно заполненный запрос, который отправляется в AnyConnect:
Здесь показано, что для проверки подлинности используются правильные имена пользователей:
Конфигурация ASA для сопоставления двойной аутентификации и сертификата
Кроме того, можно сопоставить конкретные клиентские сертификаты с отдельными группами туннелей, как показано в этом примере:
Таким образом, все сертификаты пользователей, выданные ЦС Cisco Technical Assistance Center (TAC), сопоставляются с группой туннелей с именем «RA»
Примечание. Сопоставление сертификатов для SSL настраивается иначе, чем сопоставление сертификатов для IPSec. Для IPSec сопоставление настраивается с использованием правил «tunnel-group-map» в режиме глобальной конфигурации. Для SSL сопоставление настраивается с использованием правила «certificate-group-map» в режиме конфигурации webvpn.
Проверка
Обратите внимание, что после включения сопоставления сертификатов выбор группы туннелей больше не требуется:
.debug
В этом примере правило сопоставления сертификатов разрешает поиск группы туннелей:
Устранение неполадок
Этот раздел обеспечивает информацию, которую вы можете использовать для того, чтобы устранить неисправность в вашей конфигурации.
Подтвержденный сертификат отсутствует
После удаления действующего сертификата из Windows 7 AnyConnect не может найти действующие сертификаты:
На ASA похоже, что сеанс завершен клиентом (Сброс-I):
Источник
Содержание
- AnyConnect VPN Client Troubleshooting Guide — Common Problems
- Available Languages
- Download Options
- Bias-Free Language
- Contents
- Introduction
- Prerequisites
- Requirements
- Components Used
- Troubleshooting Process
- Installation and Virtual Adapter Issues
- Disconnection or Inability to Establish Initial Connection
- Problems with Passing Traffic
- AnyConnect Crash Issues
- Fragmentation / Passing Traffic Issues
- Uninstall Automatically
- Issue Populating the Cluster FQDN
- Backup Server List Configuration
- AnyConnect: Corrupt Driver Database Issue
- Repair
- Failed Repair
- Analyze the Database
- Error Messages
- Error: Unable to Update the Session Management Database
- Solution 1
- Solution 2
- Error: «Module c:Program FilesCiscoCisco AnyConnect VPN Clientvpnapi.dll failed to register»
- Solution
- Error: «An error was received from the secure gateway in response to the VPN negotiation request. Please contact your network administrator»
- Solution
- Error: Session could not be established. Session limit of 2 reached.
- Solution 1
- Solution 2
- Error: Anyconnect not enabled on VPN server while trying to connect anyconnect to ASA
- Solution
- Error:- %ASA-6-722036: Group client-group User xxxx IP x.x.x.x Transmitting large packet 1220 (threshold 1206)
- Solution
- Error: The secure gateway has rejected the agent’s vpn connect or reconnect request.
- Solution
- Error: «Unable to update the session management database»
- Solution
- Error: «The VPN client driver has encountered an error»
- Solution
- Error: «Unable to process response from xxx.xxx.xxx.xxx»
- Solution
- Solution
- Solution
- Error: «The server certificate received or its chain does not comply with FIPS. A VPN connection will not be established»
- Solution
- Error: «Certificate Validation Failure»
- Solution
- Error: «VPN Agent Service has encountered a problem and needs to close. We are sorry for the inconvenience»
- Solution
- Error: «This installation package could not be opened. Verify that the package exists»
- Solution
- Error: «Error applying transforms. Verify that the specified transform paths are valid.»
- Solution
- Error: «The VPN client driver has encountered an error»
- Solution
- Error: «A VPN reconnect resulted in different configuration setting. The VPN network setting is being re-initialized. Applications utilizing the private network may need to be restored.»
- Solution
- AnyConnect Error While Logging In
- Solution
- IE Proxy Setting is Not Restored after AnyConnect Disconnect on Windows 7
- Solution
- Error: AnyConnect Essentials can not be enabled until all these sessions are closed.
- Solution
- Error: Connection tab on Internet option of Internet Explorer hides after getting connected to the AnyConnect client.
- Solution
- Error: Few users getting Login Failed Error message when others are able to connect successfully through AnyConnect VPN
- Solution
- Error: The certificate you are viewing does not match with the name of the site you are trying to view.
- Solution
- Cannot Launch AnyConnect From the CSD Vault From a Windows 7 Machine
- Solution
- AnyConnect Profile Does Not Get Replicated to the Standby After Failover
- Solution
- AnyConnect Client Crashes if Internet Explorer Goes Offline
- Solution
- Error Message: TLSPROTOCOL_ERROR_INSUFFICIENT_BUFFER
- Solution
- Error Message: «Connection attempt has failed due to invalid host entry»
- Solution
- Error: «Ensure your server certificates can pass strict mode if you configure always-on VPN»
- Solution
- Error: «An internal error occurred in the Microsoft Windows HTTP Services»
- Solution
- Error: «The SSL transport received a Secure Channel Failure. May be a result of a unsupported crypto configuration on the Secure Gateway.»
- Solution
AnyConnect VPN Client Troubleshooting Guide — Common Problems
Available Languages
Download Options
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
Contents
Introduction
This document describes a troubleshooting scenario which applies to applications that do not work through the Cisco AnyConnect VPN Client.
Prerequisites
Requirements
There are no specific requirements for this document.
Components Used
The information in this document is based on a Cisco Adaptive Security Appliance (ASA) that runs Version 8.x.
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, make sure that you understand the potential impact of any command.
Troubleshooting Process
This typical troubleshooting scenario applies to applications that do not work through the Cisco AnyConnect VPN Client for end-users with Microsoft Windows-based computers. These sections address and provide solutions to the problems:
Installation and Virtual Adapter Issues
Complete these steps:
- Obtain the device log file:
- Windows XP / Windows 2000:
Note: Hidden folders must be made visible in order to see these files.
If you see errors in the setupapi log file, you can turn up verbosity to 0x2000FFFF.
Obtain the MSI installer log file:
If this is an initial web deploy install, this log is located in the per-user temp directory.
- Windows XP / Windows 2000:
If this is an automatic upgrade, this log is in the temp directory of the system:
The filename is in this format: anyconnect-win-x.x.xxxx-k9-install-yyyyyyyyyyyyyy.log. Obtain the most recent file for the version of the client you want to install. The x.xxxx changes based on the version, such as 2.0.0343, and yyyyyyyyyyyyyy is the date and time of the install.
Obtain the PC system information file:
- From a Command Prompt/DOS box, type this:
- Windows XP / Windows 2000:
Note: After you type into this prompt, wait. It can take between two to five minutes for the file to complete.
Obtain a systeminfo file dump from a Command Prompt:
Windows XP and Windows Vista:
Refer to AnyConnect: Corrupt Driver Database Issue in order to debug the driver issue.
Disconnection or Inability to Establish Initial Connection
If you experience connection problems with the AnyConnect client, such as disconnections or the inability to establish an initial connection, obtain these files:
- The configuration file from the ASA in order to determine if anything in the configuration causes the connection failure:
From the console of the ASA, type write net x.x.x.x:ASA-Config.txt where x.x.x.x is the IP address of a TFTP server on the network.
From the console of the ASA, type show running-config . Let the configuration complete on the screen, then cut-and-paste to a text editor and save.
The ASA event logs:
- In order to enable logging on the ASA for auth, WebVPN, Secure Sockets Layer (SSL), and SSL VPN Client (SVC) events, issue these CLI commands:
Originate an AnyConnect session and ensure that the failure can be reproduced. Capture the logging output from the console to a text editor and save.
In order to disable logging, issue no logging enable .
The Cisco AnyConnect VPN Client log from the Windows Event Viewer of the client PC:
- Choose Start > Run.
Right-click the Cisco AnyConnect VPN Client log, and select Save Log File as AnyConnect.evt.
Note: Always save it as the .evt file format.
If the user cannot connect with the AnyConnect VPN Client, the issue might be related to an established Remote Desktop Protocol (RDP) session or Fast User Switching enabled on the client PC. The user can see the AnyConnect profile settings mandate a single local user, but multiple local users are currently logged into your computer. A VPN connection will not be established error message error on the client PC. In order to resolve this issue, disconnect any established RDP sessions and disable Fast User Switching. This behavior is controlled by the Windows Logon Enforcement attribute in the client profile, however currently there is no setting that actually allows a user to establish a VPN connection while multiple users are logged on simultaneously on the same machine. Enhancement request CSCsx15061 
Note: Make sure that port 443 is not blocked so the AnyConnect client can connect to the ASA.
When a user cannot connect the AnyConnect VPN Client to the ASA, the issue might be caused by an incompatibility between the AnyConnect client version and the ASA software image version. In this case, the user receives this error message: The installer was not able to start the Cisco VPN client, clientless access is not available .
In order to resolve this issue, upgrade the AnyConnect client version to be compatible with the ASA software image.
When you log in the first time to the AnyConnect, the login script does not run. If you disconnect and log in again, then the login script runs fine. This is the expected behavior.
When you connect the AnyConnect VPN Client to the ASA, you might receive this error: User not authorized for AnyConnect Client access, contact your administrator .
This error is seen when the AnyConnect image is missing from the ASA. Once the image is loaded to the ASA, AnyConnect can connect without any issues to the ASA.
This error can be resolved by disabling Datagram Transport Layer Security (DTLS). Go to Configuration > Remote Access VPN > Network (Client) Access > AnyConnect Connection Profiles and uncheck the Enable DTLS check box. This disables DTLS.
The dartbundle files show this error message when the user gets disconnected: TUNNELPROTOCOLDPDMGR_ERROR_NO_DPD_RESPONSE:The secure gateway failed to respond to Dead Peer Detection packets . This error means that the DTLS channel was torn due to Dead Peer Detection (DPD) failure. This error is resolved if you tweak the DPD keepalives and issue these commands:
The svc keepalive and svc dpd-interval commands are replaced by the anyconnect keepalive and anyconnect dpd-interval commands respectively in ASA Version 8.4(1) and later as shown here:
Problems with Passing Traffic
When problems are detected with passing traffic to the private network with an AnyConnect session through the ASA, complete these data-gathering steps:
- Obtain the output of the show vpn-sessiondb detail svc filter name ASA command from the console. If the output shows Filter Name: XXXXX , then gather the output for show access-list XXXXX. Verify that the access-list XXXXX does not block the intended traffic flow.
Export the AnyConnect statistics from AnyConnect VPN Client > Statistics > Details > Export (AnyConnect-ExportedStats.txt).
Check the ASA configuration file for nat statements. If Network Address Translation (NAT) is enabled, these must exempt data that returns to the client as a result of NAT. For example, to NAT exempt (nat 0) the IP addresses from the AnyConnect pool, use this on the CLI:
Determine if the tunneled default gateway needs to be enabled for the setup. The traditional default gateway is the gateway of last resort for non-decrypted traffic.
For example, if the VPN Client needs to access a resource which is not in the routing table of the VPN Gateway, the packet is routed through the standard default gateway. The VPN gateway does not need the complete internal routing table in order to resolve this. The tunneled keyword can be used in this instance.
Verify if the AnyConnect traffic is dropped by the inspection policy of the ASA. You could exempt the specific application that is used by AnyConnct client if you implement the Modular Policy Framework of Cisco ASA. For example, you could exempt the skinny protocol with these commands.
AnyConnect Crash Issues
Complete these data-gathering steps:
- Ensure that the Microsoft Utility Dr Watson is enabled. In order to do this, choose Start > Run, and run Drwtsn32.exe. Configure this and click OK:
When the crash occurs, gather the .log and .dmp files from C:Documents and SettingsAll UsersApplication DataMicrosoftDr Watson. If these files appear to be in use, then use ntbackup.exe.
Obtain the Cisco AnyConnect VPN Client log from the Windows Event Viewer of the client PC:
- Choose Start > Run.
Right-click the Cisco AnyConnect VPN Client log, and select Save Log File As AnyConnect.evt.
Note: Always save it as the .evt file format.
Fragmentation / Passing Traffic Issues
Some applications, such as Microsoft Outlook, do not work. However, the tunnel is able to pass other traffic such as small pings.
This can provide clues as to a fragmentation issue in the network. Consumer routers are particularly poor at packet fragmentation and reassembly.
Try a scaling set of pings in order to determine if it fails at a certain size. For example, ping -l 500, ping -l 1000, ping -l 1500, ping -l 2000.
It is recommended that you configure a special group for users that experience fragmentation, and set the SVC Maximum Transition Unit (MTU) for this group to 1200. This allows you to remediate users who experience this issue, but not impact the broader user base.
Problem
TCP connections hang once connected with AnyConnect.
Solution
In order to verify if your user has a fragmentation issue, adjust the MTU for AnyConnect clients on the ASA.
Uninstall Automatically
Problem
The AnyConnect VPN Client uninstalls itself once the connection terminates. The client logs show that keep installed is set to disabled.
Solution
AnyConnect uninstalls itself despite that the keep installed option is selected on the Adaptive Security Device Manager (ASDM). In order to resolve this issue, configure the svc keep-installer installed command under group-policy.
Issue Populating the Cluster FQDN
Problem: AnyConnect client is pre-populated with the hostname instead of the cluster Fully Qualified Domain Name (FQDN).
When you have a load-balancing cluster set up for SSL VPN and the client attempts to connect to the cluster, the request is redirected to the node ASA and the client logs in successfully. After some time, when the client tries to connect to the cluster again, the cluster FQDN is not seen in the Connect to entries. Instead, the node ASA entry to which the client has been redirected is seen.
Solution
This occurs because the AnyConnect client retains the host name to which it last connected. This behavior is observed and a bug has been filed. For complete details about the bug, refer to Cisco bug ID CSCsz39019. The suggested workaround is to upgrade the Cisco AnyConnect to Version 2.5.
Backup Server List Configuration
A backup server list is configured in case the main server selected by the user is not reachable. This is defined in the Backup Server pane in the AnyConnect profile. Complete these steps:
- Download the AnyConnect Profile Editor (registered customers only) . The file name is AnyConnectProfileEditor2_4_1.jar.
Create an XML file with the AnyConnect Profile Editor.
- Go to the server list tab.
Click Add.
Type the main server on the Hostname field.
Once you have the XML file, you need to assign it to the connection you use on the ASA.
- In ASDM, choose Configuration >Remote Access VPN >Network (Client) Access >AnyConnect Connection Profiles.
Select your profile and click Edit.
Click Manage from the Default Group Policy section.
Select your group-policy and click Edit.
Select Advanced and then click SSL VPN Client.
AnyConnect: Corrupt Driver Database Issue
This entry in the SetupAPI.log file suggests that the catalog system is corrupt:
W239 driver signing class list «C:WINDOWSINFcertclas.inf» was missing or invalid. Error 0xfffffde5: Unknown Error. , assuming all device classes are subject to driver signing policy.
You can also receive this error message: Error(3/17): Unable to start VA, setup shared queue, or VA gave up shared queue .
You can receive this log on the client: «The VPN client driver has encountered an error» .
Repair
This issue is due to Cisco bug ID CSCsm54689. In order to resolve this issue, make sure that Routing and Remote Access Service is disabled before you start AnyConnect. If this does not resolve the issue, complete these steps:
- Open a command prompt as an Administrator on the PC (elevated prompt on Vista).
Run net stop CryptSvc .
Failed Repair
If the repair fails, complete these steps:
- Open a command prompt as an Administrator on the PC (elevated prompt on Vista).
Run net stop CryptSvc .
Rename the %WINDIR%system32catroot2 to catroot2_old directory.
Exit the command prompt.
Analyze the Database
You can analyze the database at any time in order to determine if it is valid.
- Open a command prompt as an Admimistrator on the PC.
Error Messages
Error: Unable to Update the Session Management Database
While the SSL VPN is connected through a web browser, the Unable to Update the Session Management Database. error message appears, and the ASA logs show %ASA-3-211001: Memory allocation Error. The adaptive security appliance failed to allocate RAM system memory .
Solution 1
This issue is due to Cisco bug ID CSCsm51093. In order to resolve this issue, reload the ASA or upgrade the ASA software to the interim release mentioned in the bug. Refer to Cisco bug ID CSCsm51093 
Solution 2
This issue can also be resolved if you disable threat-detection on ASA if threat-detection is used.
Error: «Module c:Program FilesCiscoCisco AnyConnect VPN Clientvpnapi.dll failed to register»
When you use the AnyConnect client on laptops or PCs, an error occurs during the install:
When this error is encountered, the installer cannot move forward and the client is removed.
Solution
These are the possible workarounds to resolve this error:
- The latest AnyConnect client is no longer officially supported with Microsoft Windows 2000. It is a registry problem with the 2000 computer.
Remove the VMware applications. Once AnyConnect is installed, VMware applications can be added back to the PC.
Add the ASA to their trusted sites.
Copy these files from the ProgramFilesCiscoCiscoAnyconnect folder to a new folder and run the regsvr32 vpnapi.dll command prompt:
- vpnapi.dll
- vpncommon.dll
- vpncommoncrypt.dll
The log message related to this error on the AnyConnect client looks similar to this:
Error: «An error was received from the secure gateway in response to the VPN negotiation request. Please contact your network administrator»
When clients try to connect to the VPN with the Cisco AnyConnect VPN Client, this error is received.
This message was received from the secure gateway:
«Illegal address class» or «Host or network is 0» or «Other error»
Solution
The issue occurs because of the ASA local IP pool depletion. As the VPN pool resource is exhausted, the IP pool range must be enlarged.
Cisco bug ID is CSCsl82188 is filed for this issue. This error usually occurs when the local pool for address assignment is exhausted, or if a 32-bit subnet mask is used for the address pool. The workaround is to expand the address pool and use a 24-bit subnet mask for the pool.
Error: Session could not be established. Session limit of 2 reached.
When you try to connect more than two clients with the AnyConnect VPN Client, you receive the Login Failed error message on the Client and a warning message in the ASA logs that states Session could not be established. Session limit of 2 reached . I have the AnyConnect essential license on the ASA, which runs Version 8.0.4.
Solution 1
This error occurs because the AnyConnect essential license is not supported by ASA version 8.0.4. You need to upgrade the ASA to version 8.2.2. This resolves the error.
Note: Regardless of the license used, if the session limit is reached, the user will receive the login failed error message.
Solution 2
This error can also occur if the vpn-sessiondb max-anyconnect-premium-or-essentials-limit session-limit command is used to set the limit of VPN sessions permitted to be established. If the session-limit is set as two, then the user cannot establish more than two sessions even though the license installed supports more sessions. Set the session-limit to the number of VPN sessions required in order to avoid this error message.
Error: Anyconnect not enabled on VPN server while trying to connect anyconnect to ASA
You receive the Anyconnect not enabled on VPN server error message when you try to connect AnyConnect to the ASA.
Solution
This error is resolved if you enable AnyConnect on the outside interface of the ASA with ASDM. For more information on how to enable AnyConnect on the outside interface, refer to Configure Clientless SSL VPN (WebVPN) on the ASA.
Error:- %ASA-6-722036: Group client-group User xxxx IP x.x.x.x Transmitting large packet 1220 (threshold 1206)
The %ASA-6-722036: Group User IP Transmitting large packet 1220 (threshold 1206) error message appears in the logs of the ASA. What does this log mean and how is this resolved?
Solution
This log message states that a large packet was sent to the client. The source of the packet is not aware of the MTU of the client. This can also be due to compression of non-compressible data. The workaround is to turn off the SVC compression with the svc compression none command. This resolves the issue.
Error: The secure gateway has rejected the agent’s vpn connect or reconnect request.
When you connect to the AnyConnect Client, this error is received: «The secure gateway has rejected the agent’s vpn connect or reconnect request. A new connection requires re-authentication and must be started manually. Please contact your network administrator if this problem persists. The following message was received from the secure gateway: no assigned address» .
This error is also received when you connect to the AnyConnect Client: «The secure gateway has rejected the connection attempt. A new connection attempt to the same or another secure gateway is needed, which requires re-authentication. The following message was received from the secure gateway:Host or network is 0» .
This error is also received when you connect to the AnyConnect Client: «The secure gateway has rejected the agent’s vpn connect or reconnect request. A new connection requires a re-authentication and must be started manually. Please contact the network administrator if the problem persists. The following message was received from the secure gateway: No License» .
Solution
The router was missing pool configuration after reload. You need to add the concerned configuration back to the router.
The «The secure gateway has rejected the agent’s vpn connect or reconnect request. A new connection requires a re-authentication and must be started manually. Please contact the network administrator if the problem persists. The following message was received from the secure gateway: No License» error occurs when the AnyConnect mobility license is missing. Once the license is installed, the issue is resolved.
Error: «Unable to update the session management database»
When you try to authenticate in WebPortal, this error message is received: «Unable to update the session management database» .
Solution
This problem is related to memory allocation on the ASA. This issue is mostly encountered when the ASA Version is 8.2.1. Originally, this requires a 512MB RAM for its complete functionality.
As a permanent workaround, upgrade the memory to 512MB.
As a temporary workaround, try to free the memory with these steps:
- Disable the threat-detection.
Disable SVC compression.
Error: «The VPN client driver has encountered an error»
This is an error message obtained on the client machine when you try to connect to AnyConnect.
Solution
In order to resolve this error, complete this procedure in order to manually set the AnyConnect VPN agent to Interactive:
- Right-click My Computer > Manage > Services and Applications > Services > and select the Cisco AnyConnect VPN Agent.
Right-click Properties, then log on, and select Allow service to interact with the desktop.
This sets the registry Type value DWORD to 110 (default is 010) for the HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesvpnagent.
Note: If this is to be used, then the preference would be to use the .MST transform in this instance. This is because if you set this manually with these methods, it requires that this be set after every install/upgrade process. This is why there is a need to identify the application that causes this problem.
When Routing and Remote Access Service (RRAS) is enabled on the Windows PC, AnyConnect fails with the The VPN client driver has encountered an error. error message. In order to resolve this issue, make sure that Routing and RRAS is disabled before starting AnyConnect. Refer to Cisco bug ID CSCsm54689 for more information.
Error: «Unable to process response from xxx.xxx.xxx.xxx»
AnyConnect clients fail to connect to a Cisco ASA. The error in the AnyConnect window is «Unable to process response from xxx.xxx.xxx.xxx» .
Solution
In order to resolve this error, try these workarounds:
- Remove WebVPN from the ASA and reenable it. «Login Denied , unauthorized connection mechanism , contact your administrator» .
Solution
This error message occurs mostly because of configuration issues that are improper or an incomplete configuration. Check the configuration and make sure it is as required to resolve the issue.
Secure VPN via remote desktop is not supported error message appears.
Solution
This issue is due to these Cisco bug IDs: CSCsu22088 and CSCso42825. If you upgrade the AnyConnect VPN Client, it can resolve the issue. Refer to these bugs for more information.
Error: «The server certificate received or its chain does not comply with FIPS. A VPN connection will not be established»
When you attempt to VPN to the ASA 5505, the The server certificate received or its chain does not comply with FIPS. A VPN connection will not be established error message appears.
Solution
In order to resolve this error, you must disable the Federal Information Processing Standards (FIPS) in the AnyConnect Local Policy file. This file can usually be found at C:ProgramDataCiscoCisco AnyConnect VPN ClientAnyConnectLocalPolicy.xml . If this file is not found in this path, then locate the file at a different directory with a path such as C:Documents and SettingsAll UsersApplication DataCisco AnyConnectVPNClientAnyConnectLocalPolicy.xml . Once you locate the xml file, make changes to this file as shown here:
Change the phrase:
true
false
Then, restart the computer. Users must have administrative permissions in order to modify this file.
Error: «Certificate Validation Failure»
Users are unable to launch AnyConnect and receive the Certificate Validation Failure error.
Solution
Certificate authentication works differently with AnyConnect compared to the IPSec client. In order for certificate authentication to work, you must import the client certificate to your browser and change the connection profile in order to use certificate authentication. You also need to enable this command on your ASA in order to allow SSL client-certificates to be used on the outside interface:
ssl certificate-authentication interface outside port 443
Error: «VPN Agent Service has encountered a problem and needs to close. We are sorry for the inconvenience»
When AnyConnect Version 2.4.0202 is installed on a Windows XP PC, it stops at updating localization files and an error message shows that the vpnagent.exe fails.
Solution
This behavior is logged in Cisco bug ID CSCsq49102. The suggested workaround is to disable the Citrix client.
Error: «This installation package could not be opened. Verify that the package exists»
When AnyConnect is downloaded, this error message is received:
«Contact your system administrator. The installer failed with the following error: This installation package could not be opened. Verify that the package exists and that you can access it, or contact the application vendor to verify that this is a valid Windows Installer package.»
Solution
Complete these steps in order to fix this issue:
- Remove any anti-virus software.
Disable the Windows firewall.
If neither Step 1 or 2 helps, then format the machine and then install.
Error: «Error applying transforms. Verify that the specified transform paths are valid.»
This error message is recieved during the auto-download of AnyConnect from the ASA:
This is the error message received when connecting with AnyConnect for MacOS:
Solution
Complete one of these workarounds in order to resolve this issue:
- The root cause of this error might be due to a corrupted MST translation file (for example, imported). Perform these steps to fix this:
- Remove the MST translation table.
If neither of these workarounds resolve the issue, contact Cisco Technical Support.
Error: «The VPN client driver has encountered an error»
This error is received:
Solution
This issue can be resolved when you uninstall the AnyConnect Client, and then remove the anti-virus software. After this, reinstall the AnyConnect Client. If this resolution does not work, then reformat the PC in order to fix this issue.
Error: «A VPN reconnect resulted in different configuration setting. The VPN network setting is being re-initialized. Applications utilizing the private network may need to be restored.»
This error is received when you try to launch AnyConnect:
Solution
In order to resolve this error, use this:
The svc mtu command is replaced by the anyconnect mtu command in ASA Version 8.4(1) and later as shown here:
AnyConnect Error While Logging In
Problem
The AnyConnect receives this error when it connects to the Client:
Solution
The issue can be resolved if you make these changes to the AnyConnect profile:
Add this line to the AnyConnect profile:
IE Proxy Setting is Not Restored after AnyConnect Disconnect on Windows 7
Problem
In Windows 7, if the IE proxy setting is configured for Automatically detect settings and AnyConnect pushes down a new proxy setting, the IE proxy setting is not restored back to Automatically detect settings after the user ends the AnyConnect session. This causes LAN issues for users who need their proxy setting configured for Automatically detect settings.
Solution
This behavior is logged in Cisco bug ID CSCtj51376. The suggested workaround is to upgrade to AnyConnect 3.0.
Error: AnyConnect Essentials can not be enabled until all these sessions are closed.
This error message is received on Cisco ASDM when you attempt to enable the AnyConnect Essentials license:
Solution
This is the normal behavior of the ASA. AnyConnect Essentials is a separately licensed SSL VPN client. It is entirely configured on the ASA and provides the full AnyConnect capability, with these exceptions:
- No Cisco Secure Desktop (CSD) (including HostScan/Vault/Cache Cleaner)
No clientless SSL VPN
Optional Windows Mobile Support
This license cannot be used at the same time as the shared SSL VPN premium license. When you need to use one license, you need to disable the other.
Error: Connection tab on Internet option of Internet Explorer hides after getting connected to the AnyConnect client.
The connection tab on the Internet option of Internet Explorer hides after you are connected to the AnyConnect client.
Solution
This is due to the msie-proxy lockdown feature. If you enable this feature, it hides the Connections tab in Microsoft Internet Explorer for the duration of an AnyConnect VPN session. If you disable the feature, it leaves the display of the Connections tab unchanged.
Error: Few users getting Login Failed Error message when others are able to connect successfully through AnyConnect VPN
A few users receive the Login Failed Error message when others can connect successfully through the AnyConnect VPN.
Solution
This issue can be resolved if you make sure the do not require pre-authentication checkbox is checked for the users.
Error: The certificate you are viewing does not match with the name of the site you are trying to view.
During the AnyConnect profile update, an error is shown that says the certificate is invalid. This occurs with Windows only and at the profile update phase. The error message is shown here:
Solution
This can be resolved if you modify the server list of the AnyConnect profile in order to use the FQDN of the certificate.
This is a sample of the XML profile:
Note: If there is an existing entry for the Public IP address of the server such as , then remove it and retain only the FQDN of the server (for example, but not ).
Cannot Launch AnyConnect From the CSD Vault From a Windows 7 Machine
When the AnyConnect is launched from the CSD vault, it does not work. This is attempted on Windows 7 machines.
Solution
Currently, this is not possible because it is not supported.
AnyConnect Profile Does Not Get Replicated to the Standby After Failover
The AnyConnect 3.0 VPN client with ASA Version 8.4.1 software works fine. However, after failover, there is no replication for the AnyConnect profile related configuration.
Solution
This problem has been observed and logged under Cisco bug ID CSCtn71662. The temporary workaround is to manually copy the files to the standby unit.
AnyConnect Client Crashes if Internet Explorer Goes Offline
When this occurs, the AnyConnect event log contains entries similar to these:
Solution
This behavior is observed and logged under Cisco bug ID CSCtx28970. In order to resolve this, quit the AnyConnect application and relaunch. The connection entries reappear after relaunch.
Error Message: TLSPROTOCOL_ERROR_INSUFFICIENT_BUFFER
The AnyConnect client fails to connect and the Unable to establish a connection error message is received. In the AnyConnect event log, the TLSPROTOCOL_ERROR_INSUFFICIENT_BUFFER error is found.
Solution
This occurs when the headend is configured for split-tunneling with a very large split-tunnel list (approximately 180-200 entries) and one or more other client attributes are configured in the group-policy, such as dns-server.
In order to resolve this issue, complete these steps:
- Reduce the number of entries in the split-tunnel list.
Use this configuration in order to disable DTLS:
For more information, refer to Cisco bug ID CSCtc41770.
Error Message: «Connection attempt has failed due to invalid host entry»
The Connection attempt has failed due to invalid host entry error message is received while AnyConnect is authenticated with the use of a certificate.
Solution
In order to resolve this issue, try either of these possible solutions:
- Upgrade the AnyConnect to Version 3.0.
- Disable Cisco Secure Desktop on your computer.
For more information, refer to Cisco bug ID CSCti73316.
Error: «Ensure your server certificates can pass strict mode if you configure always-on VPN»
When you enable the Always-On feature on AnyConnect, the Ensure your server certificates can pass strict mode if you configure always-on VPN error message is received.
Solution
This error message implies that if you want to use the Always-On feature, you need a valid sever certificate configured on the headend. Without a valid server certificate, this feature does not work. Strict Cert Mode is an option that you set in the AnyConnect local policy file in order to ensure the connections use a valid certificate. If you enable this option in the policy file and connect with a bogus certificate, the connection fails.
Error: «An internal error occurred in the Microsoft Windows HTTP Services»
This Diagnostic AnyConnect Reporting Tool (DART) shows one failed attempt:
Also, refer to the event viewer logs on the Windows machine.
Solution
This could be caused due to a corrupted Winsock connection. Reset the connection from the command promt with this command and restart your windows machine:
netsh winsock reset
Error: «The SSL transport received a Secure Channel Failure. May be a result of a unsupported crypto configuration on the Secure Gateway.»
This Diagnostic AnyConnect Reporting Tool (DART) shows one failed attempt:
Solution
Windows 8.1 does not support RC4 according to the following KB update:
Either configure DES/3DES ciphers for SSL VPN on the ASA using the command «ssl encryption 3des-sha1 aes128-sha1 aes256-sha1 des-sha1» OR edit the Windows Registry file on the client machine as mentioned below:
Источник