Содержание
- Ошибки VPN
- Вы везунчик!
- Ошибки OpenVPN
- Как узнать какая OpenVPN ошибка возникла?
- Не могу выбрать «Connect» при нажатии на иконку в системном трее
- Connect to IP:Port failed, will try again in 5 seconds; No Route to Host
- Cannot load certificate file client.crt
- All TAP-Win32 adapters on this system are currently in use
- ERROR: Windows route add command failed: returned error code 1
- Initialization Sequence Completed With Errors
- MikroTik.by
- Ikev2 VPN на apple устройствах
- Ikev2 VPN на apple устройствах
- Re: Ikev2 VPN на apple устройствах
- Re: Ikev2 VPN на apple устройствах
- VPN Connection : An unexpected error occurred.
- 3.7 Beta 2: SSTP-клиенты не подключаются к VPN-сервер SSTP
- Вопрос
- Роман Сапегин
- Роман Сапегин
Ошибки VPN
Иногда случаются проблемы с VPN подключением или VPN не работает. На данной странице вы можете найти описание возникающей ошибки впн и самостоятельно исправить ее.
Вы везунчик!
Поздравляем! Вы нашли скрытый промо-код со скидкой 75% на покупку анонимного VPN без логов.
Промо-код действует только 1 час.
Ошибки OpenVPN
Если вы не знаете как узнать ошибку, возникшую в ходе подключения, нажмите на следующую ссылку:
Ниже представлен список возможных ошибок и методы их устранения. Нажмите на ошибку, чтобы узнать как ее устранить. Названия ошибок соответствуют записям в окне лога.
Как узнать какая OpenVPN ошибка возникла?
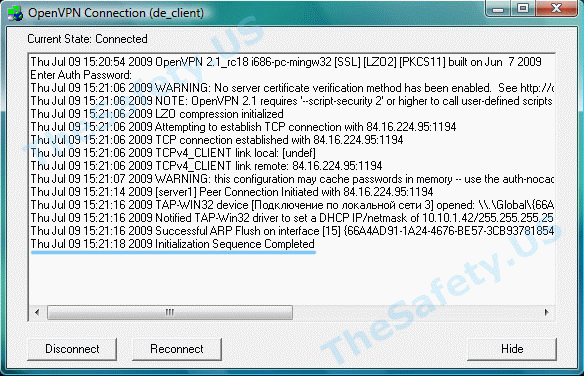
Программа OpenVPN имеет лог подключения. При подключении к OpenVPN серверу программа записывает данные подключения. Эта информация никуда не передается и остается на вашем компьютере, чтобы вы могли понять из-за чего возникла ошибка впн. Чтобы вызвать окно лога, нажмите дважды левой кнопкой мыши на иконку OpenVPN в системном трее.
Когда соединение прошло успешно, и вы подключены к VPN серверу, то окно лога должно выглядеть так:
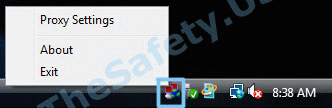
Не могу выбрать «Connect» при нажатии на иконку в системном трее
В списке есть только «Proxy Settings», «About» и «Exit», но нет пункта «Connect».
Это означает, что вы не скачали и/или не скопировали конфигурационный файл «client.ovpn» в «C:/Program Files/OpenVPN/config». Откройте еще раз Инструкцию по настройке OpenVPN соединения для вашей ОС и проверьте все шаги установки и настройки.
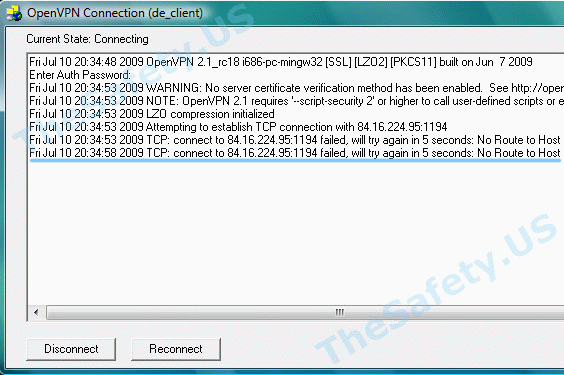
Connect to IP:Port failed, will try again in 5 seconds; No Route to Host
Данная ошибка означает, что у вас нет подключения к Интернету, либо его блокирует ваш Firewall или Антивирус.
Проверьте активно ли ваше Интернет подключение, отключите Firewall, Антивирус и подключитесь еще раз.
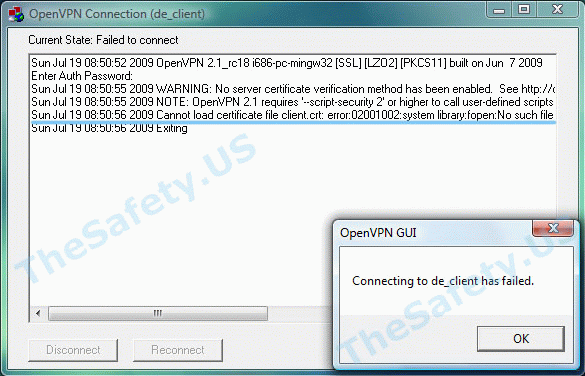
Cannot load certificate file client.crt
Данная ошибка связана с отсутствием сертификационных файлов в папке «C:Program FilesOpenVPNconfig».
В процессе установки было необходимо скачать архив с сертификатами и распаковать его в папку с программой. Откройте еще раз Инструкцию по настройке OpenVPN соединения для вашей ОС и проверьте все шаги установки и настройки.
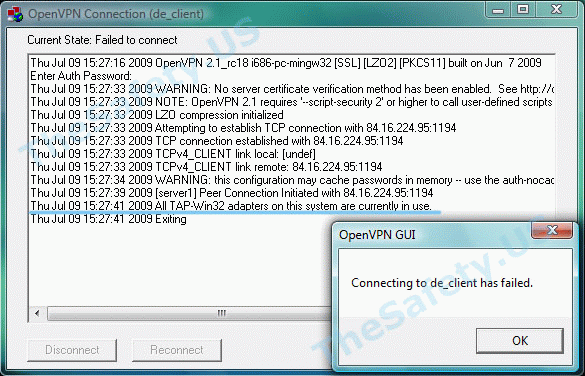
All TAP-Win32 adapters on this system are currently in use
Эта впн ошибка связана с некорректной работой Windows и программы OpenVPN. Также эта OpenVPN ошибка может возникнуть вследствие отключения Интернета без отключения сначала OpenVPN соединения. Всегда отключайте сначала OpenVPN соединение и только затем Интернет.
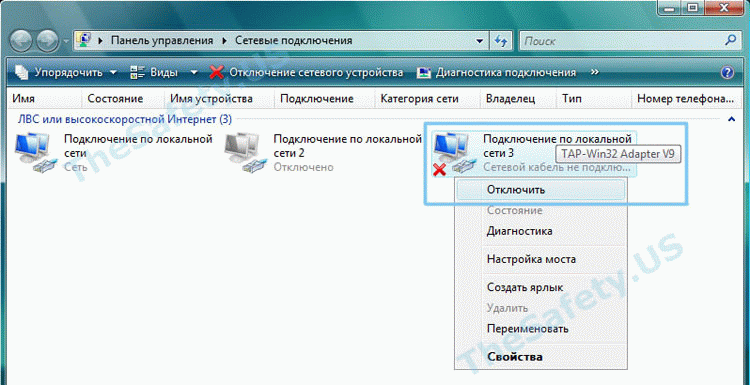
Для устранения ошибки, зайдите в «Пуск -> Сетевые подключения». Найдите «Подключение по локальной сети. TAP-Win32 Adapter» и правой кнопкой мышки щелкните на ярлыке. Выберите «Отключить».
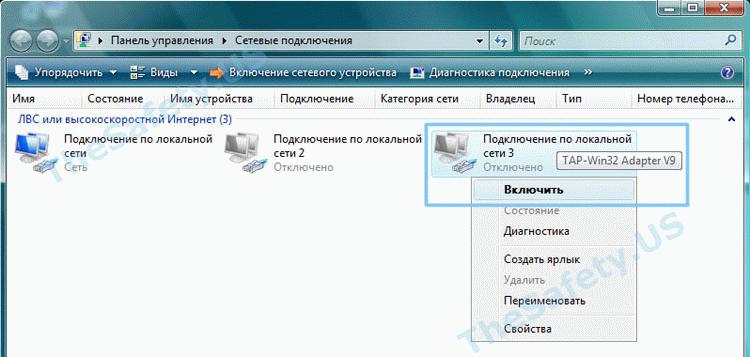
Затем, таким же образом, «Включите» данное подключение. После выполнения данных действий проблемы с VPN подключением должны исчезнуть.
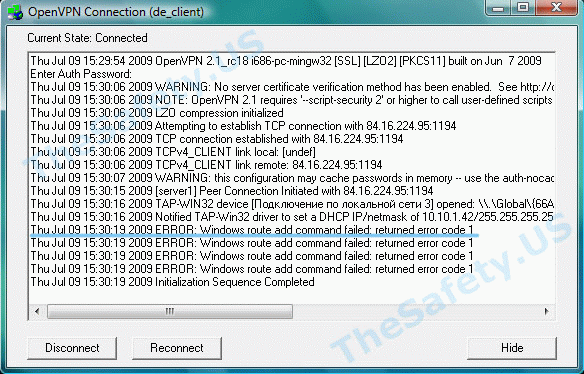
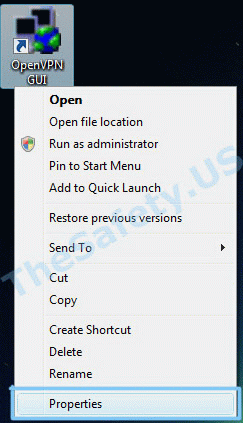
ERROR: Windows route add command failed: returned error code 1
Данная ошибка связана с ограничением прав в Windows Vista, Seven.
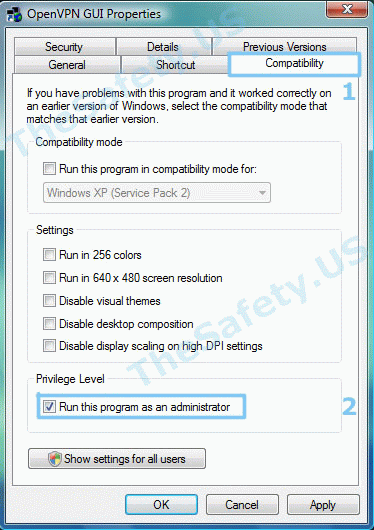
Для устранения ошибки, необходимо выйти из OpenVPN GUI. Правой кнопкой мышки нажать на иконку OpenVPN GUI на рабочем столе и выбрать пункт меню «Свойства»
На вкладке «Совместимость» поставьте галочку «Выполнять эту программу от имени администратора».
Теперь запустите OpenVPN GUI еще раз и подключитесь к VPN серверу.
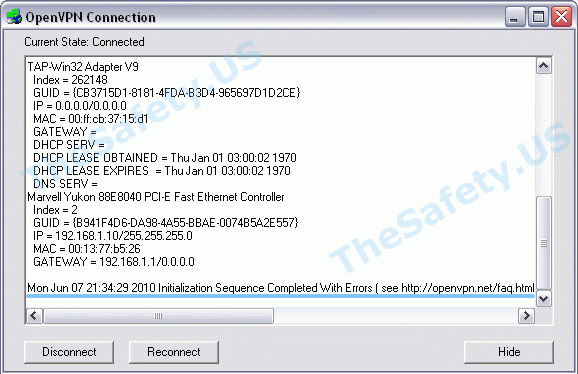
Initialization Sequence Completed With Errors
Данная ошибка связана с неправильной работой службы DHCP из-за антивирусов или фаерволов.
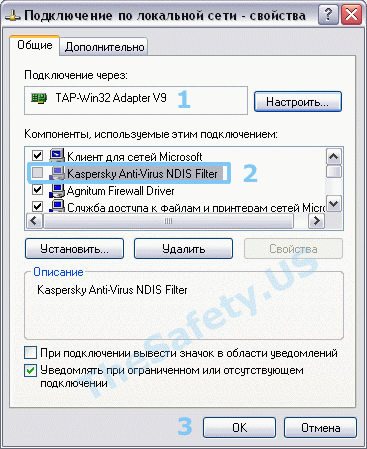
Ошибка наблюдалась постоянно у фаервола Outpost Firewall версии 2009 и ранее, наблюдается также у антивируса Касперского. Ниже представлено решение для антивируса Касперского. Сам алгоритм ничем не отличается от решения проблемы для других антивирусов и фаерволов.
Для устранения ошибки, необходимо зайти в «Пуск -> Панель Управления -> Сетевые подключения» и зайти в «Свойства» виртуального адаптера «TAP-Win 32 Adapter». На вкладке «Общие» в списке отключить Kaspersky Anti-Virus NDIS Filter и затем нажать «ОК».
Теперь подключитесь к VPN и подключение должно пройти успешно.
Источник
MikroTik.by
For every complex problem, there is a solution that is simple, neat, and wrong.
Ikev2 VPN на apple устройствах
Ikev2 VPN на apple устройствах
Сообщение nevolex » 20 фев 2021, 13:03
есть такая проблема, на которую к сожалению я не могу найти ответ
Есть Ikev2 vpn сервет на микротик, для авторизации использую сертификаты
Vpn работает отлично на виндовс и андроиде
Vpn не работает на мак ос и ios вообще никак, выдается ошибка
» VPN Connection
An unexpected error occurred «
я слышал что заставить впн рабоать на apple это боль не всеже может можно
вот логи mac os и конфиг может кто-то поможет навести на мысль. спасибо
Re: Ikev2 VPN на apple устройствах
Сообщение nevolex » 20 фев 2021, 23:51
Requirements for trusted certificates in iOS 13 and macOS 10.15
All TLS server certificates must comply with these new security requirements in iOS 13 and macOS 10.15:
1- TLS server certificates and issuing CAs using RSA keys must use key sizes greater than or equal to 2048 bits. Certificates using RSA key sizes smaller than 2048 bits are no longer trusted for TLS.
2- TLS server certificates and issuing CAs must use a hash algorithm from the SHA-2 family in the signature algorithm. SHA-1 signed certificates are no longer trusted for TLS.
3- TLS server certificates must present the DNS name of the server in the Subject Alternative Name extension of the certificate. DNS names in the CommonName of a certificate are no longer trusted.
Re: Ikev2 VPN на apple устройствах
Сообщение nevolex » 21 фев 2021, 13:49
после часов тестов оказалось что в мак ос нужно было выбрать авторизацию как none а потом сертификат. Если выбирать сразу сертификат — ничего не работает, правда была ошибка немного другая — identity not found for server
23:33:19 ipsec,error peer’s ID does not match certificate
23:33:19 ipsec,error ipsec: peer’s ID does not match certificate
23:33:19 ipsec,error peer’s ID does not match certificate
Источник
VPN Connection : An unexpected error occurred.
I am suddenly unable to get my built-in VPN connection to work on my iMac running OS X 10.11.5. I get the message VPN Connection : An unexpected error occurred. I have been using this VPN setup to connect to work for several months successfully.
But last week (and I don’t know if this had anything to do with this), I went on vacation and used a Tim Hortons free wi-fi setup. I had a LOT of trouble getting the Login page to come up, and I was checking any playing with various Network settings without success. When a change didn’t work, I set it back to its original setting. Finally, I learned to use Safari to access Tim’s free wi-fi Login page. Then once logged on, everything was OK.
But when I returned home a week later and needed to start my VPN connection to access work, it would not start up. I checked and double-check all of my various Network preference settings but could not find any that were wrong. I even deleted and re-entered my VPN service definition without resolving the problem.
Thinking the problem could be the newly installed ISP equipment from Bell (we switched from Rogers while I was away), I used my BlackBerry smartphone (issued by my employer) to create a wi-fi hotspot and accessed the internet using that connection which bypassed my home ISP equipment entirely. But still I was unable to establish a VPN connection.
I then tried my iPad’s VPN connection, and it worked! I then defined a VPN service on my wife’s iMac and my daughter’s iMac and was able to successfully establish a VPN connection to my work just fine, using the exact same VPN configuration. This led me to conclude it was a problem on my iMac (and not with my new ISP or with my work’s VPN system which had no changes made to it), but I still cannot find what is «broken». I ran Onyx for my OS X 10.11.5 iMac and repaired permissions and cleaned cache and everything else that it does to «fix» issues. But the problem persisted.
Is there a corrupt preference file somewhere (that scan option is no longer on the current version of Onyx for some reason)?
Do I still have a network system setting wrong somewhere that I need to change back to is proper value?
Here is the VPN attempt from the system.log file (with certain values hidden in case they expose my work’s VPN access):
Jun 26 16:13:48 Myrons-iMac nesessionmanager[439]: NESMLegacySession[VPN Work:295091 E5-xxxx-4B6A-xxxx-F7A7xxxxxxAA ]: Received a start command from SystemUIServer[257]
Jun 26 16:13:48 Myrons-iMac nesessionmanager[439]: NESMLegacySession[VPN Work:295091 E5-xxxx-4B6A-xxxx-F7A7xxxxxxAA ]: status changed to connecting
Jun 26 16:13:48 Myrons-iMac nesessionmanager[439]: IPSec connecting to server nnn.nnn.n.n
Jun 26 16:13:48 Myrons-iMac nesessionmanager[439]: IPSec Phase1 starting.
Jun 26 16:13:48 Myrons-iMac racoon[520]: accepted connection on vpn control socket.
Jun 26 16:13:48 — last message repeated 1 time —
Jun 26 16:13:48 Myrons-iMac racoon[520]: IPSec connecting to server nnn.nnn.n.n
Jun 26 16:13:48 — last message repeated 1 time —
Jun 26 16:13:48 Myrons-iMac racoon[520]: Connecting.
Jun 26 16:13:48 Myrons-iMac racoon[520]: IPSec Phase 1 started (Initiated by me).
Jun 26 16:13:48 — last message repeated 1 time —
Jun 26 16:13:48 Myrons-iMac racoon[520]: bind 1 (Can’t assign requested address)
Jun 26 16:13:48 — last message repeated 1 time —
Jun 26 16:13:48 Myrons-iMac racoon[520]: sendfromto failed
Jun 26 16:13:48 — last message repeated 1 time —
Jun 26 16:13:48 Myrons-iMac racoon[520]: Phase 1 negotiation failed due to send error. 94437eb7d5b1b6e8:0000000000000000
Jun 26 16:13:48 — last message repeated 1 time —
Jun 26 16:13:48 Myrons-iMac racoon[520]: failed to send packet
Jun 26 16:13:48 — last message repeated 1 time —
Jun 26 16:13:48 Myrons-iMac racoon[520]: IKE Packet: transmit failed. (Initiator, Aggressive-Mode Message 1).
Jun 26 16:13:48 Myrons-iMac nesessionmanager[439]: IPSec Controller: IKE FAILED. phase 1, assert 0
Jun 26 16:13:48 Myrons-iMac nesessionmanager[439]: NESMLegacySession[VPN Work:295091 E5-xxxx-4B6A-xxxx-F7A7xxxxxxAA ]: status changed to disconnecting
Jun 26 16:13:48 Myrons-iMac nesessionmanager[439]: IPSec disconnecting from server 142.201.5.6
Jun 26 16:13:48 Myrons-iMac racoon[520]: IPSec disconnecting from server nnn.nnn.n.n
Jun 26 16:13:48 — last message repeated 3 times —
Jun 26 16:13:48 Myrons-iMac nesessionmanager[439]: NESMLegacySession[VPN Work:295091E5-xxxx-4B6A-xxxx-F7A7xxxxxxAA]: status changed to disconnected, last stop reason None
Any help or insight would be most helpful and appreciated. so that I can work from home again. 🙂
VIN,iMac (21.5-inch Late 2009), OS X El Capitan (10.11.5)
Источник
3.7 Beta 2: SSTP-клиенты не подключаются к VPN-сервер SSTP
Спросил Роман Сапегин,
2 сентября, 2021
Вопрос

Роман Сапегин
Роман Сапегин

После обновления с 3.7 Beta 1 до 3.7 Beta 2, перестал подключатся клиент к VPN-сервер SSTP. Проверено с клиента на Windows и c Andoid.
[15:03:22] Establish VPN connection
[15:03:27] An unexpected event occurred:
SSLException
Read error: ssl=0x771a6e6008: I/O error during system call, Connection reset by peer
com.android.org.conscrypt.NativeCrypto.SSL_read(Native Method)
com.android.org.conscrypt.NativeSsl.read(NativeSsl.java:407)
com.android.org.conscrypt.ConscryptFileDescriptorSocket$SSLInputStream.read(ConscryptFileDescriptorSocket.java:579)
kittoku.opensstpclient.misc.IncomingBuffer.supply(IncomingBuffer.kt:40)
kittoku.opensstpclient.misc.IncomingBuffer.challenge$app_release(IncomingBuffer.kt:70)
kittoku.opensstpclient.negotiator.SstpNegotiatorKt.challengeWholePacket(SstpNegotiator.kt:27)
kittoku.opensstpclient.layer.SstpClient.proceedRequestSent(SstpClietnt.kt:23)
kittoku.opensstpclient.layer.SstpClient.proceed$app_release(SstpClietnt.kt:171)
kittoku.opensstpclient.ControlClient$run$1.invokeSuspend(ControlClient.kt:82)
kotlin.coroutines.jvm.internal.BaseContinuationImpl.resumeWith(ContinuationImpl.kt:33)
kotlinx.coroutines.DispatchedTask.run(DispatchedTask.kt:56)
kotlinx.coroutines.scheduling.CoroutineScheduler.runSafely(CoroutineScheduler.kt:571)
kotlinx.coroutines.scheduling.CoroutineScheduler$Worker.executeTask(CoroutineScheduler.kt:738)
kotlinx.coroutines.scheduling.CoroutineScheduler$Worker.runWorker(CoroutineScheduler.kt:678)
kotlinx.coroutines.scheduling.CoroutineScheduler$Worker.run(CoroutineScheduler.kt:665)
[15:03:27] Terminate VPN connection
Лог с роутера Extra (KN-1711) который подключается к V PN-сервер SSTP
Источник
@davidemyers Just did exactly what you said. I used the server install on DigitalOcean and after installing it, I used the mobileconfig file to add the profile on Mac OS X. It gave me the exact same error «The VPN server did not respond» .. also here’s the log of what happened.
TASK [Gathering Facts] ****************************************************************************************************************************************************
ok: [localhost]
[pause]
What provider would you like to use?
1. DigitalOcean
2. Amazon Lightsail
3. Amazon EC2
4. Vultr
5. Microsoft Azure
6. Google Compute Engine
7. Scaleway
8. OpenStack (DreamCompute optimised)
9. Install to existing Ubuntu 18.04 server (Advanced)
Enter the number of your desired provider
:
1
TASK [pause] **************************************************************************************************************************************************************
ok: [localhost]
TASK [Set facts based on the input] ***************************************************************************************************************************************
ok: [localhost]
[pause]
Name the vpn server
[algo]
:
roubys
TASK [pause] **************************************************************************************************************************************************************
ok: [localhost]
[pause]
Do you want macOS/iOS clients to enable «VPN On Demand» when connected to cellular networks?
[y/N]
:
N
TASK [pause] **************************************************************************************************************************************************************
ok: [localhost]
[pause]
Do you want macOS/iOS clients to enable «VPN On Demand» when connected to Wi-Fi?
[y/N]
:
N
TASK [pause] **************************************************************************************************************************************************************
ok: [localhost]
[pause]
Do you want to install a DNS resolver on this VPN server, to block ads while surfing?
[y/N]
:
N
TASK [pause] **************************************************************************************************************************************************************
ok: [localhost]
[pause]
Do you want each user to have their own account for SSH tunneling?
[y/N]
:
N
TASK [pause] **************************************************************************************************************************************************************
ok: [localhost]
[pause]
Do you want the VPN to support Windows 10 or Linux Desktop clients? (enables compatible ciphers and key exchange, less secure)
[y/N]
:
N
TASK [pause] **************************************************************************************************************************************************************
ok: [localhost]
[pause]
Do you want to retain the CA key? (required to add users in the future, but less secure)
[y/N]
:
N
TASK [pause] **************************************************************************************************************************************************************
ok: [localhost]
TASK [Set facts based on the input] ***************************************************************************************************************************************
ok: [localhost]
PLAY [Provision the server] ***********************************************************************************************************************************************
TASK [Gathering Facts] ****************************************************************************************************************************************************
ok: [localhost]
—> Please include the following block of text when reporting issues:
Algo running on: Mac OS X 10.14.1
Created from git fork. Last commit: 80a7391 Add IPsec log watcher
Python 2.7.10
Runtime variables:
algo_provider «digitalocean»
algo_ondemand_cellular «False»
algo_ondemand_wifi «False»
algo_ondemand_wifi_exclude «_null»
algo_local_dns «False»
algo_ssh_tunneling «False»
algo_windows «False»
wireguard_enabled «True»
dns_encryption «True»
TASK [Display the invocation environment] *********************************************************************************************************************************
changed: [localhost -> localhost]
TASK [Install the requirements] *******************************************************************************************************************************************
changed: [localhost -> localhost]
TASK [Generate the SSH private key] ***************************************************************************************************************************************
changed: [localhost]
TASK [Generate the SSH public key] ****************************************************************************************************************************************
changed: [localhost]
TASK [cloud-digitalocean : Install requirements] **************************************************************************************************************************
changed: [localhost]
[cloud-digitalocean : pause]
Enter your API token. The token must have read and write permissions (https://cloud.digitalocean.com/settings/api/tokens):
(output is hidden):
TASK [cloud-digitalocean : pause] *****************************************************************************************************************************************
ok: [localhost]
TASK [cloud-digitalocean : Set the token as a fact] ***********************************************************************************************************************
ok: [localhost]
TASK [cloud-digitalocean : Get regions] ***********************************************************************************************************************************
ok: [localhost]
TASK [cloud-digitalocean : Set facts about thre regions] ******************************************************************************************************************
ok: [localhost]
TASK [cloud-digitalocean : Set default region] ****************************************************************************************************************************
ok: [localhost]
[cloud-digitalocean : pause]
What region should the server be located in?
1. ams3 Amsterdam 3
2. blr1 Bangalore 1
3. fra1 Frankfurt 1
4. lon1 London 1
5. nyc1 New York 1
6. nyc3 New York 3
7. sfo2 San Francisco 2
8. sgp1 Singapore 1
9. tor1 Toronto 1
Enter the number of your desired region
[6]
:
5
TASK [cloud-digitalocean : pause] *****************************************************************************************************************************************
ok: [localhost]
TASK [cloud-digitalocean : Set additional facts] **************************************************************************************************************************
ok: [localhost]
TASK [cloud-digitalocean : Delete the existing Algo SSH keys] *************************************************************************************************************
ok: [localhost]
TASK [cloud-digitalocean : Upload the SSH key] ****************************************************************************************************************************
changed: [localhost]
TASK [cloud-digitalocean : Creating a droplet…] *************************************************************************************************************************
changed: [localhost]
TASK [cloud-digitalocean : set_fact] **************************************************************************************************************************************
ok: [localhost]
TASK [cloud-digitalocean : Tag the droplet] *******************************************************************************************************************************
changed: [localhost]
FAILED — RETRYING: Delete the new Algo SSH key (10 retries left).
TASK [cloud-digitalocean : Delete the new Algo SSH key] *******************************************************************************************************************
ok: [localhost]
TASK [Set subjectAltName as afact] ****************************************************************************************************************************************
ok: [localhost]
TASK [Add the server to an inventory group] *******************************************************************************************************************************
changed: [localhost]
TASK [Additional variables for the server] ********************************************************************************************************************************
changed: [localhost]
TASK [Wait until SSH becomes ready…] ************************************************************************************************************************************
ok: [localhost]
TASK [debug] **************************************************************************************************************************************************************
ok: [localhost] => {
«IP_subject_alt_name»: «204.48.29.168»
}
Pausing for 20 seconds
(ctrl+C then ‘C’ = continue early, ctrl+C then ‘A’ = abort)
Press ‘C’ to continue the play or ‘A’ to abort
TASK [A short pause, in order to be sure the instance is ready] ***********************************************************************************************************
ok: [localhost]
PLAY [Configure the server and install required software] *****************************************************************************************************************
TASK [common : Check the system] ******************************************************************************************************************************************
changed: [204.48.29.168]
TASK [common : include_tasks] *********************************************************************************************************************************************
included: /Users/ahmadrefaat/Desktop/Algos/algo/roles/common/tasks/ubuntu.yml for 204.48.29.168
changed: [204.48.29.168] => (item=[u’python2.7′, u’sudo’])
TASK [common : Ubuntu | Install prerequisites] ****************************************************************************************************************************
TASK [common : Ubuntu | Configure defaults] *******************************************************************************************************************************
changed: [204.48.29.168]
TASK [common : Gather facts] **********************************************************************************************************************************************
ok: [204.48.29.168]
TASK [common : Install software updates] **********************************************************************************************************************************
changed: [204.48.29.168]
TASK [common : Check if reboot is required] *******************************************************************************************************************************
changed: [204.48.29.168]
TASK [common : Reboot] ****************************************************************************************************************************************************
changed: [204.48.29.168]
TASK [common : Wait until SSH becomes ready…] ***************************************************************************************************************************
ok: [204.48.29.168 -> localhost]
TASK [common : Install unattended-upgrades] *******************************************************************************************************************************
ok: [204.48.29.168]
TASK [common : Configure unattended-upgrades] *****************************************************************************************************************************
changed: [204.48.29.168]
TASK [common : Periodic upgrades configured] ******************************************************************************************************************************
changed: [204.48.29.168]
TASK [common : Unattended reboots configured] *****************************************************************************************************************************
changed: [204.48.29.168]
changed: [204.48.29.168] => (item={u’regexp’: u’^session.*optional.pam_motd.so.‘, u’line’: u’# MOTD DISABLED’, u’file’: u’/etc/pam.d/login’})
changed: [204.48.29.168] => (item={u’regexp’: u’^session.*optional.pam_motd.so.‘, u’line’: u’# MOTD DISABLED’, u’file’: u’/etc/pam.d/sshd’})
TASK [common : Disable MOTD on login and SSHD] ****************************************************************************************************************************
TASK [common : Loopback for services configured] **************************************************************************************************************************
changed: [204.48.29.168]
ok: [204.48.29.168] => (item=systemd-networkd)
ok: [204.48.29.168] => (item=systemd-resolved)
TASK [common : systemd services enabled and started] **********************************************************************************************************************
RUNNING HANDLER [common : restart systemd-networkd] ***********************************************************************************************************************
changed: [204.48.29.168]
TASK [common : Check apparmor support] ************************************************************************************************************************************
changed: [204.48.29.168]
TASK [common : set_fact] **************************************************************************************************************************************************
ok: [204.48.29.168]
TASK [common : set_fact] **************************************************************************************************************************************************
ok: [204.48.29.168]
ok: [204.48.29.168] => (item=git)
ok: [204.48.29.168] => (item=screen)
changed: [204.48.29.168] => (item=apparmor-utils)
ok: [204.48.29.168] => (item=uuid-runtime)
ok: [204.48.29.168] => (item=coreutils)
changed: [204.48.29.168] => (item=iptables-persistent)
changed: [204.48.29.168] => (item=cgroup-tools)
ok: [204.48.29.168] => (item=openssl)
TASK [common : Install tools] *********************************************************************************************************************************************
ok: [204.48.29.168] => (item=[u’linux-headers-generic’, u’linux-headers-4.15.0-38-generic’])
TASK [common : Install headers] *******************************************************************************************************************************************
TASK [common : Generate password for the CA key] **************************************************************************************************************************
changed: [204.48.29.168 -> localhost]
TASK [common : Generate p12 export password] ******************************************************************************************************************************
changed: [204.48.29.168 -> localhost]
TASK [common : Define facts] **********************************************************************************************************************************************
ok: [204.48.29.168]
TASK [common : set_fact] **************************************************************************************************************************************************
ok: [204.48.29.168]
TASK [common : Set IPv6 support as a fact] ********************************************************************************************************************************
ok: [204.48.29.168]
changed: [204.48.29.168] => (item={u’item’: u’net.ipv4.ip_forward’, u’value’: 1})
changed: [204.48.29.168] => (item={u’item’: u’net.ipv4.conf.all.forwarding’, u’value’: 1})
changed: [204.48.29.168] => (item={u’item’: u’net.ipv6.conf.all.forwarding’, u’value’: 1})
TASK [common : Sysctl tuning] *********************************************************************************************************************************************
TASK [dns_encryption : Include tasks for Ubuntu] **************************************************************************************************************************
included: /Users/ahmadrefaat/Desktop/Algos/algo/roles/dns_encryption/tasks/ubuntu.yml for 204.48.29.168
TASK [dns_encryption : Add the repository] ********************************************************************************************************************************
changed: [204.48.29.168]
TASK [dns_encryption : Install dnscrypt-proxy] ****************************************************************************************************************************
changed: [204.48.29.168]
TASK [dns_encryption : Configure unattended-upgrades] *********************************************************************************************************************
changed: [204.48.29.168]
TASK [dns_encryption : Ubuntu | Unbound profile for apparmor configured] **************************************************************************************************
changed: [204.48.29.168]
TASK [dns_encryption : Ubuntu | Enforce the dnscrypt-proxy AppArmor policy] ***********************************************************************************************
ok: [204.48.29.168]
TASK [dns_encryption : Ubuntu | Ensure that the dnscrypt-proxy service directory exist] ***********************************************************************************
changed: [204.48.29.168]
TASK [dns_encryption : Ubuntu | Add capabilities to bind ports] ***********************************************************************************************************
changed: [204.48.29.168]
TASK [dns_encryption : dnscrypt-proxy ip-blacklist configured] ************************************************************************************************************
changed: [204.48.29.168]
TASK [dns_encryption : dnscrypt-proxy configured] *************************************************************************************************************************
changed: [204.48.29.168]
TASK [dns_encryption : dnscrypt-proxy enabled and started] ****************************************************************************************************************
ok: [204.48.29.168]
RUNNING HANDLER [dns_encryption : restart dnscrypt-proxy] *****************************************************************************************************************
changed: [204.48.29.168]
changed: [204.48.29.168 -> localhost] => (item=private)
changed: [204.48.29.168 -> localhost] => (item=public)
TASK [wireguard : Ensure the required directories exist] ******************************************************************************************************************
TASK [wireguard : Include tasks for Ubuntu] *******************************************************************************************************************************
included: /Users/ahmadrefaat/Desktop/Algos/algo/roles/wireguard/tasks/ubuntu.yml for 204.48.29.168
TASK [wireguard : WireGuard repository configured] ************************************************************************************************************************
changed: [204.48.29.168]
TASK [wireguard : WireGuard installed] ************************************************************************************************************************************
changed: [204.48.29.168]
TASK [wireguard : WireGuard reload-module-on-update] **********************************************************************************************************************
changed: [204.48.29.168]
TASK [wireguard : Configure unattended-upgrades] **************************************************************************************************************************
changed: [204.48.29.168]
TASK [wireguard : set_fact] ***********************************************************************************************************************************************
ok: [204.48.29.168]
changed: [204.48.29.168] => (item=dan)
changed: [204.48.29.168] => (item=jack)
changed: [204.48.29.168] => (item=204.48.29.168)
TASK [wireguard : Generate private keys] **********************************************************************************************************************************
changed: [204.48.29.168] => (item=None)
changed: [204.48.29.168] => (item=None)
changed: [204.48.29.168] => (item=None)
TASK [wireguard : Save private keys] **************************************************************************************************************************************
changed: [204.48.29.168] => (item=dan)
changed: [204.48.29.168] => (item=jack)
changed: [204.48.29.168] => (item=204.48.29.168)
TASK [wireguard : Touch the lock file] ************************************************************************************************************************************
ok: [204.48.29.168] => (item=dan)
ok: [204.48.29.168] => (item=jack)
ok: [204.48.29.168] => (item=204.48.29.168)
TASK [wireguard : Generate public keys] ***********************************************************************************************************************************
changed: [204.48.29.168] => (item=None)
changed: [204.48.29.168] => (item=None)
changed: [204.48.29.168] => (item=None)
TASK [wireguard : Save public keys] ***************************************************************************************************************************************
changed: [204.48.29.168 -> localhost] => (item=dan)
changed: [204.48.29.168 -> localhost] => (item=jack)
TASK [wireguard : WireGuard user list updated] ****************************************************************************************************************************
TASK [wireguard : set_fact] ***********************************************************************************************************************************************
ok: [204.48.29.168 -> localhost]
changed: [204.48.29.168 -> localhost] => (item=(0, u’dan’))
changed: [204.48.29.168 -> localhost] => (item=(1, u’jack’))
TASK [wireguard : WireGuard users config generated] ***********************************************************************************************************************
ok: [204.48.29.168 -> localhost] => (item=(0, u’dan’))
ok: [204.48.29.168 -> localhost] => (item=(1, u’jack’))
TASK [wireguard : Generate QR codes] **************************************************************************************************************************************
TASK [wireguard : WireGuard configured] ***********************************************************************************************************************************
changed: [204.48.29.168]
TASK [wireguard : WireGuard enabled and started] **************************************************************************************************************************
changed: [204.48.29.168]
RUNNING HANDLER [wireguard : restart wireguard] ***************************************************************************************************************************
changed: [204.48.29.168]
TASK [vpn : Include WireGuard role] ***************************************************************************************************************************************
ok: [204.48.29.168 -> localhost] => (item=private)
ok: [204.48.29.168 -> localhost] => (item=public)
TASK [wireguard : Ensure the required directories exist] ******************************************************************************************************************
TASK [wireguard : Include tasks for Ubuntu] *******************************************************************************************************************************
included: /Users/ahmadrefaat/Desktop/Algos/algo/roles/wireguard/tasks/ubuntu.yml for 204.48.29.168
TASK [wireguard : WireGuard repository configured] ************************************************************************************************************************
ok: [204.48.29.168]
TASK [wireguard : WireGuard installed] ************************************************************************************************************************************
ok: [204.48.29.168]
TASK [wireguard : WireGuard reload-module-on-update] **********************************************************************************************************************
changed: [204.48.29.168]
TASK [wireguard : Configure unattended-upgrades] **************************************************************************************************************************
ok: [204.48.29.168]
TASK [wireguard : set_fact] ***********************************************************************************************************************************************
ok: [204.48.29.168]
ok: [204.48.29.168] => (item=dan)
ok: [204.48.29.168] => (item=jack)
ok: [204.48.29.168] => (item=204.48.29.168)
TASK [wireguard : Generate private keys] **********************************************************************************************************************************
ok: [204.48.29.168] => (item=dan)
ok: [204.48.29.168] => (item=jack)
ok: [204.48.29.168] => (item=204.48.29.168)
TASK [wireguard : Generate public keys] ***********************************************************************************************************************************
ok: [204.48.29.168] => (item=None)
ok: [204.48.29.168] => (item=None)
ok: [204.48.29.168] => (item=None)
TASK [wireguard : Save public keys] ***************************************************************************************************************************************
ok: [204.48.29.168 -> localhost] => (item=dan)
ok: [204.48.29.168 -> localhost] => (item=jack)
TASK [wireguard : WireGuard user list updated] ****************************************************************************************************************************
TASK [wireguard : set_fact] ***********************************************************************************************************************************************
ok: [204.48.29.168 -> localhost]
ok: [204.48.29.168 -> localhost] => (item=(0, u’dan’))
ok: [204.48.29.168 -> localhost] => (item=(1, u’jack’))
TASK [wireguard : WireGuard users config generated] ***********************************************************************************************************************
ok: [204.48.29.168 -> localhost] => (item=(0, u’dan’))
ok: [204.48.29.168 -> localhost] => (item=(1, u’jack’))
TASK [wireguard : Generate QR codes] **************************************************************************************************************************************
TASK [wireguard : WireGuard configured] ***********************************************************************************************************************************
ok: [204.48.29.168]
TASK [wireguard : WireGuard enabled and started] **************************************************************************************************************************
ok: [204.48.29.168]
TASK [vpn : include_tasks] ************************************************************************************************************************************************
included: /Users/ahmadrefaat/Desktop/Algos/algo/roles/vpn/tasks/ubuntu.yml for 204.48.29.168
TASK [vpn : set_fact] *****************************************************************************************************************************************************
ok: [204.48.29.168]
TASK [vpn : Ubuntu | Install strongSwan] **********************************************************************************************************************************
changed: [204.48.29.168]
changed: [204.48.29.168] => (item=/usr/lib/ipsec/charon)
changed: [204.48.29.168] => (item=/usr/lib/ipsec/lookip)
changed: [204.48.29.168] => (item=/usr/lib/ipsec/stroke)
TASK [vpn : Ubuntu | Enforcing ipsec with apparmor] ***********************************************************************************************************************
ok: [204.48.29.168] => (item=apparmor)
ok: [204.48.29.168] => (item=strongswan)
ok: [204.48.29.168] => (item=netfilter-persistent)
TASK [vpn : Ubuntu | Enable services] *************************************************************************************************************************************
TASK [vpn : Ubuntu | Ensure that the strongswan service directory exist] **************************************************************************************************
changed: [204.48.29.168]
TASK [vpn : Ubuntu | Setup the cgroup limitations for the ipsec daemon] ***************************************************************************************************
changed: [204.48.29.168]
TASK [vpn : Ubuntu | Install IPsec log watcher script] ********************************************************************************************************************
changed: [204.48.29.168]
TASK [vpn : Ubuntu | Enable IPsec log watcher sudo permissions] ***********************************************************************************************************
changed: [204.48.29.168]
TASK [vpn : Ubuntu | Feed IPsec log watcher program the system logs] ******************************************************************************************************
changed: [204.48.29.168]
TASK [vpn : include_tasks] ************************************************************************************************************************************************
included: /Users/ahmadrefaat/Desktop/Algos/algo/roles/vpn/tasks/iptables.yml for 204.48.29.168
changed: [204.48.29.168] => (item={u’dest’: u’/etc/iptables/rules.v4′, u’src’: u’rules.v4.j2′})
TASK [vpn : Iptables configured] ******************************************************************************************************************************************
changed: [204.48.29.168] => (item={u’dest’: u’/etc/iptables/rules.v6′, u’src’: u’rules.v6.j2′})
TASK [vpn : Iptables configured] ******************************************************************************************************************************************
TASK [vpn : Ensure that the strongswan user exist] ************************************************************************************************************************
ok: [204.48.29.168]
TASK [vpn : Install strongSwan] *******************************************************************************************************************************************
ok: [204.48.29.168]
changed: [204.48.29.168] => (item={u’dest’: u’/etc/strongswan.conf’, u’src’: u’strongswan.conf.j2′, u’group’: u’root’, u’mode’: u’0644′, u’owner’: u’root’})
changed: [204.48.29.168] => (item={u’dest’: u’/etc/ipsec.conf’, u’src’: u’ipsec.conf.j2′, u’group’: u’root’, u’mode’: u’0644′, u’owner’: u’root’})
changed: [204.48.29.168] => (item={u’dest’: u’/etc/ipsec.secrets’, u’src’: u’ipsec.secrets.j2′, u’group’: u’root’, u’mode’: u’0600′, u’owner’: u’strongswan’})
TASK [vpn : Setup the config files from our templates] ********************************************************************************************************************
TASK [vpn : Get loaded plugins] *******************************************************************************************************************************************
changed: [204.48.29.168]
changed: [204.48.29.168] => (item=md4)
changed: [204.48.29.168] => (item=counters)
changed: [204.48.29.168] => (item=updown)
changed: [204.48.29.168] => (item=resolve)
changed: [204.48.29.168] => (item=xcbc)
changed: [204.48.29.168] => (item=agent)
changed: [204.48.29.168] => (item=md5)
changed: [204.48.29.168] => (item=eap-mschapv2)
changed: [204.48.29.168] => (item=mgf1)
changed: [204.48.29.168] => (item=constraints)
changed: [204.48.29.168] => (item=connmark)
changed: [204.48.29.168] => (item=bypass-lan)
changed: [204.48.29.168] => (item=sha1)
changed: [204.48.29.168] => (item=pkcs1)
changed: [204.48.29.168] => (item=gmp)
changed: [204.48.29.168] => (item=dnskey)
changed: [204.48.29.168] => (item=sshkey)
changed: [204.48.29.168] => (item=rc2)
changed: [204.48.29.168] => (item=xauth-generic)
changed: [204.48.29.168] => (item=attr)
changed: [204.48.29.168] => (item=aesni)
changed: [204.48.29.168] => (item=fips-prf)
changed: [204.48.29.168] => (item=revocation)
changed: [204.48.29.168] => (item=nonce)
changed: [204.48.29.168] => (item=kernel-netlink)
changed: [204.48.29.168] => (item=aes)
changed: [204.48.29.168] => (item=pubkey)
changed: [204.48.29.168] => (item=pkcs8)
changed: [204.48.29.168] => (item=sha2)
changed: [204.48.29.168] => (item=stroke)
changed: [204.48.29.168] => (item=hmac)
changed: [204.48.29.168] => (item=openssl)
changed: [204.48.29.168] => (item=random)
changed: [204.48.29.168] => (item=x509)
changed: [204.48.29.168] => (item=pgp)
changed: [204.48.29.168] => (item=socket-default)
changed: [204.48.29.168] => (item=pkcs7)
changed: [204.48.29.168] => (item=pem)
changed: [204.48.29.168] => (item=pkcs12)
changed: [204.48.29.168] => (item=gcm)
TASK [vpn : Set subjectAltName as a fact] *********************************************************************************************************************************
ok: [204.48.29.168 -> localhost]
changed: [204.48.29.168 -> localhost] => (item=ecparams)
changed: [204.48.29.168 -> localhost] => (item=certs)
changed: [204.48.29.168 -> localhost] => (item=crl)
changed: [204.48.29.168 -> localhost] => (item=newcerts)
changed: [204.48.29.168 -> localhost] => (item=private)
changed: [204.48.29.168 -> localhost] => (item=public)
changed: [204.48.29.168 -> localhost] => (item=reqs)
TASK [vpn : Ensure the pki directories exist] *****************************************************************************************************************************
changed: [204.48.29.168 -> localhost] => (item=.rnd)
changed: [204.48.29.168 -> localhost] => (item=private/.rnd)
changed: [204.48.29.168 -> localhost] => (item=index.txt)
changed: [204.48.29.168 -> localhost] => (item=index.txt.attr)
changed: [204.48.29.168 -> localhost] => (item=serial)
TASK [vpn : Ensure the files exist] ***************************************************************************************************************************************
TASK [vpn : Generate the openssl server configs] **************************************************************************************************************************
changed: [204.48.29.168 -> localhost]
TASK [vpn : Build the CA pair] ********************************************************************************************************************************************
changed: [204.48.29.168 -> localhost]
TASK [vpn : Copy the CA certificate] **************************************************************************************************************************************
changed: [204.48.29.168 -> localhost]
TASK [vpn : Generate the serial number] ***********************************************************************************************************************************
changed: [204.48.29.168 -> localhost]
TASK [vpn : Build the server pair] ****************************************************************************************************************************************
changed: [204.48.29.168 -> localhost]
changed: [204.48.29.168 -> localhost] => (item=dan)
changed: [204.48.29.168 -> localhost] => (item=jack)
TASK [vpn : Build the client’s pair] **************************************************************************************************************************************
changed: [204.48.29.168 -> localhost] => (item=dan)
changed: [204.48.29.168 -> localhost] => (item=jack)
TASK [vpn : Create links for the private keys] ****************************************************************************************************************************
changed: [204.48.29.168 -> localhost] => (item=dan)
changed: [204.48.29.168 -> localhost] => (item=jack)
TASK [vpn : Build openssh public keys] ************************************************************************************************************************************
changed: [204.48.29.168 -> localhost] => (item=dan)
changed: [204.48.29.168 -> localhost] => (item=jack)
TASK [vpn : Build the client’s p12] ***************************************************************************************************************************************
changed: [204.48.29.168 -> localhost] => (item=dan)
changed: [204.48.29.168 -> localhost] => (item=jack)
TASK [vpn : Copy the p12 certificates] ************************************************************************************************************************************
TASK [vpn : Get active users] *********************************************************************************************************************************************
changed: [204.48.29.168 -> localhost]
changed: [204.48.29.168] => (item={u’dest’: u’/etc/ipsec.d/cacerts/ca.crt’, u’src’: u’configs/204.48.29.168/pki/cacert.pem’, u’group’: u’root’, u’mode’: u’0600′, u’owner’: u’strongswan’})
changed: [204.48.29.168] => (item={u’dest’: u’/etc/ipsec.d/certs/204.48.29.168.crt’, u’src’: u’configs/204.48.29.168/pki/certs/204.48.29.168.crt’, u’group’: u’root’, u’mode’: u’0600′, u’owner’: u’strongswan’})
changed: [204.48.29.168] => (item={u’dest’: u’/etc/ipsec.d/private/204.48.29.168.key’, u’src’: u’configs/204.48.29.168/pki/private/204.48.29.168.key’, u’group’: u’root’, u’mode’: u’0600′, u’owner’: u’strongswan’})
TASK [vpn : Copy the keys to the strongswan directory] ********************************************************************************************************************
changed: [204.48.29.168 -> localhost] => (item=dan)
changed: [204.48.29.168 -> localhost] => (item=jack)
TASK [vpn : Register p12 PayloadContent] **********************************************************************************************************************************
TASK [vpn : Set facts for mobileconfigs] **********************************************************************************************************************************
ok: [204.48.29.168 -> localhost]
changed: [204.48.29.168] => (item=None)
changed: [204.48.29.168] => (item=None)
TASK [vpn : Build the mobileconfigs] **************************************************************************************************************************************
changed: [204.48.29.168 -> localhost] => (item=dan)
changed: [204.48.29.168 -> localhost] => (item=jack)
TASK [vpn : Build the client ipsec config file] ***************************************************************************************************************************
changed: [204.48.29.168 -> localhost] => (item=dan)
changed: [204.48.29.168 -> localhost] => (item=jack)
TASK [vpn : Build the client ipsec secret file] ***************************************************************************************************************************
changed: [204.48.29.168 -> localhost] => (item=configs/204.48.29.168)
TASK [vpn : Restrict permissions for the local private directories] *******************************************************************************************************
TASK [vpn : strongSwan started] *******************************************************************************************************************************************
ok: [204.48.29.168]
RUNNING HANDLER [dns_adblocking : restart apparmor] ***********************************************************************************************************************
RUNNING HANDLER [vpn : restart strongswan] ********************************************************************************************************************************
changed: [204.48.29.168]
RUNNING HANDLER [vpn : daemon-reload] *************************************************************************************************************************************
changed: [204.48.29.168]
RUNNING HANDLER [vpn : restart iptables] **********************************************************************************************************************************
changed: [204.48.29.168]
RUNNING HANDLER [vpn : restart rsyslogd] **********************************************************************************************************************************
changed: [204.48.29.168]
TASK [Delete the CA key] **************************************************************************************************************************************************
changed: [204.48.29.168 -> localhost]
TASK [Dump the configuration] *********************************************************************************************************************************************
changed: [204.48.29.168 -> localhost]
- Remove From My Forums
-
Question
-
Hi,
I have a problem with one mac laptop, I setup Azure Point to site VPN client IKEv2 with authentication certificate on mac and when I try to connect I get next message : VPN Connection An unexpected error occurred , I try the same
setup for another mac mini and I did not see any problemDo you know what cause the problem
thank you,
Answers
-
-
Proposed as answer by
SubhashVasarapu-MSFTMicrosoft employee
Wednesday, December 18, 2019 9:23 AM -
Marked as answer by
Mooner09
Thursday, December 19, 2019 8:50 PM
-
Proposed as answer by
All replies
-
Greetings,
Here are some trouble
shooting scenarios for the certificate-based authentication while setting up P2S connection in your Mac OS X. If you have already gone through these earlier then please let us know for further analysis.
Also, there is a similar thread in SO, you can check it here.If you think your question has been answered, click «Mark as Answer» if just helped click «Vote as
helpful». This can be beneficial to other community members reading this forum thread.
Best regards
Subhash -
-
Proposed as answer by
SubhashVasarapu-MSFTMicrosoft employee
Wednesday, December 18, 2019 9:23 AM -
Marked as answer by
Mooner09
Thursday, December 19, 2019 8:50 PM
-
Proposed as answer by
-
Hi ,
thank you for your help, I did like you told me, and I get different error now : VPN Connection The VPN server did not respond see below
-
Hi ,
thank you for your help , now we able to connect Azure VPN , the problem
was and is Mobile Hotspot but it’s not related Azure VPN so we can close this questionthanks