- Remove From My Forums
-
Question
-
Hi All,
Has anyone had problems installed Exchange 2016 on Win Server 2019 DC?
I am getting this issue;
D:>setup /mode:install /role:mailbox /iacceptexchangeserverlicenseterms
Microsoft Exchange Server 2016 Cumulative Update 10 Unattended Setup
Copying Files…
File copy complete. Setup will now collect additional information needed for installation.Languages
Management tools
Mailbox role: Transport service
Mailbox role: Client Access service
Mailbox role: Unified Messaging service
Mailbox role: Mailbox service
Mailbox role: Front End Transport service
Mailbox role: Client Access Front End servicePerforming Microsoft Exchange Server Prerequisite Check
Configuring Prerequisites
FAILEDThe following error was generated when «$error.Clear();
if (Get-Service MpsSvc* | ?{$_.Name -eq ‘MpsSvc’})
{Set-Service MpsSvc -StartupType Automatic
Start-SetupService -ServiceName MpsSvc
}
» was run:
«Microsoft.PowerShell.Commands.ServiceCommandException: Service ‘Windows Defender Firewall (MpsSvc)’ cannot be
configured due to the following error: Access is denied —> System.ComponentModel.Win32Exception: Access is deniedSetup seems to be trying to manipulate MpsSvc but it runs «System Protected Process» thingo to prevent tampering so setup can’t. Any ideas or is this a fix for <g class=»gr_ gr_39 gr-alert gr_gramm gr_inline_cards gr_run_anim
Style multiReplace» data-gr-id=»39″ id=»39″>CU11 ?</g>Peace,
Matt
P.S
I tried GUI installation too and the same error occured
-
Edited by
Tuesday, October 16, 2018 11:47 PM
Wierd spellcheck formatting thingy
-
Edited by
Answers
-
Hi,
As per my knowledge, it is not supported to install Exchange 2016 on Windows server 2019 so far, the supported OS versions for CU3 and later are Windows Server 2012, Windows Server 2012 R2 and Windows Server 2016.
Exchange Server Supportability Matrix
Regards,
Manu Meng
Please remember to
mark the replies as answers if they helped. If you have feedback for TechNet Subscriber Support, contact
tnsf@microsoft.com.
Click
here to learn more. Visit the dedicatedforum to share, explore and
talk to experts about Microsoft Teams.-
Marked as answer by
Starcrew
Wednesday, October 17, 2018 10:50 PM
-
Marked as answer by
I am unable to uninstall Exchange Server 2016 on a Windows 10 v1709 computer. Running setup.exe /mode:uninstall, I receive the following error during the prerequisites check:
——
The following error was generated when «$error.Clear();
if (Get-Service
MpsSvc* | ?{$_.Name -eq ‘MpsSvc’})
{
Set-Service MpsSvc -StartupType
Automatic
Start-SetupService -ServiceName MpsSvc
}
» was run:
«Microsoft.PowerShell.Commands.ServiceCommandException: Service ‘Windows
Defender Firewall (MpsSvc)’ cannot be configured due to the following error:
Access is denied —> System.ComponentModel.Win32Exception: Access is denied
——
I am attempting to uninstall while using a domain admin / Exchange admin account which is also an administrator on the administrative workstation.
What do I need to do so that Exchange Setup passes this prerequisite check to allow Exchange to be uninstalled from the administrative workstation?
As background, I was trying to install only the Exchange management tools on a workstation that is used for system administration. Upon initially running Exchange Setup via the GUI on the administrative workstation and selecting only the management tools option, I received a message indicating that a previous installation had been attempted, and would I like to try to continue with that installation, to which I responded Yes. (I had tried to install the management tools previously, but the installation at that time failed. However, I do not recall what the specific installation error was for that failed installation attempt.)
After allowing the Exchange installation to continue, the result was that the installation completed successfully, but appears to have installed a full instance of Exchange Server on the workstation, not just the management tools. This has now resulted in the administrative workstation now hosting shadow queues for Exchange, which is interfering with mail delivery (the intended environment is just a single-server Exchange installation.)
Содержание
- Вики IT-KB
- Инструменты пользователя
- Инструменты сайта
- Боковая панель
- Содержание
- Как корректно отключить и включить Брандмауэр Windows
- Утилита netsh
- Командлеты PowerShell
- Mpssvc firewall do windows
- Default Settings
- Default Behavior
- Dependencies
- Restore Default Startup Configuration for Windows Defender Firewall
- Аудит изменения политики на уровне правил MPSSVC Audit MPSSVC Rule-Level Policy Change
- Mpssvc firewall do windows
- Answered by:
- Question
- Audit MPSSVC Rule-Level Policy Change
Вики IT-KB
Пошаговые руководства, шпаргалки, полезные ссылки.
Инструменты пользователя
Инструменты сайта
Боковая панель
Содержание
Как корректно отключить и включить Брандмауэр Windows

Утилита netsh
Чтобы выключить все профили брандмауэра Windows с помощью утилиты netsh, с правами администратора выполним команду:
Чтобы включить обратно, выполним команду:
Командлеты PowerShell
Чтобы выключить все профили брандмауэра Windows с помощью PowerShell, с правами администратора выполним команду:
Чтобы включить обратно, выполним команду:
Обратите внимание на то, что если в домене Active Directory правила брандмауэра Windows настраиваются с помощью групповых политик, указанные выше команды могут не дать желаемого результата, не смотря на то, что отрабатывать они будут без ошибок.
Проверено на следующих конфигурациях:
| Версия ОС |
|---|
| Windows 10 1803 (17134.345) Professional RU 64-bit |

Алексей Максимов
Время публикации: 16.10.2018 16:24
Mpssvc firewall do windows
Windows Defender Firewall helps protect your computer by preventing unauthorized users from gaining access to your computer through the Internet or a network.
Default Settings
| Startup type: | Automatic |
| Display name: | Windows Defender Firewall |
| Service name: | mpssvc |
| Service type: | share |
| Error control: | normal |
| Group: | NetworkProvider |
| Object: | NT AuthorityLocalService |
| Path: | %SystemRoot%system32svchost.exe -k LocalServiceNoNetworkFirewall -p |
| File: | %SystemRoot%system32mpssvc.dll |
| Registry key: | HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesmpssvc |
| Privileges: |
|
Default Behavior
Windows Defender Firewall is a Win32 service. In Windows 10 it is starting automatically when the operating system starts. Then the Windows Defender Firewall service is running as NT AuthorityLocalService in a shared process of svchost.exe along with other services. If Windows Defender Firewall fails to start, the failure details are being recorded into Event Log. Then Windows 10 will start up and notify the user that the mpssvc service has failed to start due to the error.
Dependencies
Windows Defender Firewall cannot be started under any conditions, if the following services are disabled, deleted or working improperly:
Restore Default Startup Configuration for Windows Defender Firewall
1. Run the Command Prompt as an administrator.
2. Copy the commands below, paste them into the command window and press ENTER:
sc config mpssvc start= auto
sc start mpssvc
3. Close the command window and restart the computer.
Аудит изменения политики на уровне правил MPSSVC Audit MPSSVC Rule-Level Policy Change
Область применения Applies to
- Windows 10 Windows 10
- Windows Server 2016 Windows Server 2016
Аудит изменения политики MPSSVC Rule-Level определяет, генерирует ли операционная система события аудита при внесении изменений в правила политики для службы защиты Майкрософт (MPSSVC.exe). Audit MPSSVC Rule-Level Policy Change determines whether the operating system generates audit events when changes are made to policy rules for the Microsoft Protection Service (MPSSVC.exe).
Служба Защиты (Майкрософт), используемая брандмауэром Windows, является неотъемлемой частью защиты компьютера от вредоносных программ. The Microsoft Protection Service, which is used by Windows Firewall, is an integral part of the computer’s threat protection against malware. К отслеживаемой активности относятся: The tracked activities include:
Активные политики при запускается служба брандмауэра Windows. Active policies when the Windows Firewall service starts.
Изменения правил брандмауэра Windows. Changes to Windows Firewall rules.
Изменения в списке исключений брандмауэра Windows. Changes to the Windows Firewall exception list.
Изменения параметров брандмауэра Windows. Changes to Windows Firewall settings.
Правила игнорируются или не применяются службой брандмауэра Windows. Rules ignored or not applied by the Windows Firewall service.
Изменения параметров групповой политики брандмауэра Windows. Changes to Windows Firewall Group Policy settings.
Изменения правил брандмауэра важны для понимания состояния безопасности компьютера и его защиты от сетевых атак. Changes to firewall rules are important for understanding the security state of the computer and how well it is protected against network attacks.
Объем события: средний. Event volume: Medium.
| Тип компьютера Computer Type | Общий успех General Success | Общий сбой General Failure | Более успешный успех Stronger Success | Более сильное сбой Stronger Failure | Комментарии Comments |
|---|---|---|---|---|---|
| Контроллер домена Domain Controller | Да Yes | Да Yes | Да Yes | Да Yes | События успеха показывают изменения в правилах и параметрах брандмауэра Windows, активной конфигурации и правилах после запуска службы брандмауэра Windows и действий по восстановлению конфигурации по умолчанию. Success events shows you changes in Windows Firewall rules and settings, active configuration and rules after Windows Firewall Service startup and default configuration restore actions. Сбои могут помочь выявить проблемы конфигурации с правилами и настройками брандмауэра Windows. Failure events may help to identify configuration problems with Windows Firewall rules or settings. |
| Сервер-член Member Server | Да Yes | Да Yes | Да Yes | Да Yes | События успеха показывают изменения в правилах и параметрах брандмауэра Windows, активной конфигурации и правилах после запуска службы брандмауэра Windows и действий по восстановлению конфигурации по умолчанию. Success events shows you changes in Windows Firewall rules and settings, active configuration and rules after Windows Firewall Service startup and default configuration restore actions. Сбои могут помочь выявить проблемы конфигурации с правилами и настройками брандмауэра Windows. Failure events may help to identify configuration problems with Windows Firewall rules or settings. |
| Workstation Workstation | Да Yes | Да Yes | Да Yes | Да Yes | События успеха показывают изменения в правилах и параметрах брандмауэра Windows, активной конфигурации и правилах после запуска службы брандмауэра Windows и действий по восстановлению конфигурации по умолчанию. Success events shows you changes in Windows Firewall rules and settings, active configuration and rules after Windows Firewall Service startup and default configuration restore actions. Сбои могут помочь выявить проблемы конфигурации с правилами и настройками брандмауэра Windows. Failure events may help to identify configuration problems with Windows Firewall rules or settings. |
Список событий: Events List:
4944(S): следующая политика была активна при работе брандмауэра Windows. 4944(S): The following policy was active when the Windows Firewall started.
4945(S): правило было перечислены при работе брандмауэра Windows. 4945(S): A rule was listed when the Windows Firewall started.
4946(S): в список исключений брандмауэра Windows было внося изменения. 4946(S): A change has been made to Windows Firewall exception list. Было добавлено правило. A rule was added.
4947(S): в список исключений брандмауэра Windows было внося изменения. 4947(S): A change has been made to Windows Firewall exception list. Правило было изменено. A rule was modified.
4948(S): в список исключений брандмауэра Windows было внося изменения. 4948(S): A change has been made to Windows Firewall exception list. Правило было удалено. A rule was deleted.
4949(S): параметры брандмауэра Windows восстановлены до значений по умолчанию. 4949(S): Windows Firewall settings were restored to the default values.
4950(S): параметр брандмауэра Windows изменился. 4950(S): A Windows Firewall setting has changed.
4951(F): правило игнорируется, так как его основной номер версии не распознается брандмауэром Windows. 4951(F): A rule has been ignored because its major version number was not recognized by Windows Firewall.
4952(F): части правила были проигнорированы, так как его номер версии не был распознан брандмауэром Windows. 4952(F): Parts of a rule have been ignored because its minor version number was not recognized by Windows Firewall. Другие части правила будут применены. The other parts of the rule will be enforced.
4953(F): брандмауэр Windows проигнорировал правило, так как ему не удалось его разлить. 4953(F): A rule has been ignored by Windows Firewall because it could not parse the rule.
4954(S): параметры групповой политики брандмауэра Windows изменились. 4954(S): Windows Firewall Group Policy settings have changed. Были применены новые параметры. The new settings have been applied.
4956(S): брандмауэр Windows изменил активный профиль. 4956(S): Windows Firewall has changed the active profile.
4957(F): Брандмауэр Windows не применял следующее правило: 4957(F): Windows Firewall did not apply the following rule:
4958(F): Брандмауэр Windows не применял следующее правило, так как правило ссылалось на элементы, не настроенные на этом компьютере: 4958(F): Windows Firewall did not apply the following rule because the rule referred to items not configured on this computer:
Mpssvc firewall do windows
This forum has migrated to Microsoft Q&A. Visit Microsoft Q&A to post new questions.
Answered by:
Question
Has anyone had problems installed Exchange 2016 on Win Server 2019 DC?
I am getting this issue;
D:>setup /mode:install /role:mailbox /iacceptexchangeserverlicenseterms
Microsoft Exchange Server 2016 Cumulative Update 10 Unattended Setup
Copying Files.
File copy complete. Setup will now collect additional information needed for installation.
Languages
Management tools
Mailbox role: Transport service
Mailbox role: Client Access service
Mailbox role: Unified Messaging service
Mailbox role: Mailbox service
Mailbox role: Front End Transport service
Mailbox role: Client Access Front End service
Performing Microsoft Exchange Server Prerequisite Check
Configuring Prerequisites FAILED
The following error was generated when «$error.Clear();
if (Get-Service MpsSvc* | ?<$_.Name -eq ‘MpsSvc’>)
<
Set-Service MpsSvc -StartupType Automatic
Start-SetupService -ServiceName MpsSvc
>
» was run:
«Microsoft.PowerShell.Commands.ServiceCommandException: Service ‘Windows Defender Firewall (MpsSvc)’ cannot be
configured due to the following error: Access is denied —> System.ComponentModel.Win32Exception: Access is denied
Setup seems to be trying to manipulate MpsSvc but it runs «System Protected Process» thingo to prevent tampering so setup can’t. Any ideas or is this a fix for CU11 ?
I tried GUI installation too and the same error occured
Audit MPSSVC Rule-Level Policy Change
Applies to
- Windows 10
- Windows Server 2016
Audit MPSSVC Rule-Level Policy Change determines whether the operating system generates audit events when changes are made to policy rules for the Microsoft Protection Service (MPSSVC.exe).
The Microsoft Protection Service, which is used by Windows Firewall, is an integral part of the computer’s threat protection against malware. The tracked activities include:
Active policies when the Windows Firewall service starts.
Changes to Windows Firewall rules.
Changes to the Windows Firewall exception list.
Changes to Windows Firewall settings.
Rules ignored or not applied by the Windows Firewall service.
Changes to Windows Firewall Group Policy settings.
Changes to firewall rules are important for understanding the security state of the computer and how well it is protected against network attacks.
Event volume: Medium.
| Computer Type | General Success | General Failure | Stronger Success | Stronger Failure | Comments |
|---|---|---|---|---|---|
| Domain Controller | Yes | Yes | Yes | Yes | Success events shows you changes in Windows Firewall rules and settings, active configuration and rules after Windows Firewall Service startup and default configuration restore actions. Failure events may help to identify configuration problems with Windows Firewall rules or settings. |
| Member Server | Yes | Yes | Yes | Yes | Success events shows you changes in Windows Firewall rules and settings, active configuration and rules after Windows Firewall Service startup and default configuration restore actions. Failure events may help to identify configuration problems with Windows Firewall rules or settings. |
| Workstation | Yes | Yes | Yes | Yes | Success events shows you changes in Windows Firewall rules and settings, active configuration and rules after Windows Firewall Service startup and default configuration restore actions. Failure events may help to identify configuration problems with Windows Firewall rules or settings. |
Events List:
4944(S): The following policy was active when the Windows Firewall started.
4945(S): A rule was listed when the Windows Firewall started.
4946(S): A change has been made to Windows Firewall exception list. A rule was added.
4947(S): A change has been made to Windows Firewall exception list. A rule was modified.
4948(S): A change has been made to Windows Firewall exception list. A rule was deleted.
4949(S): Windows Firewall settings were restored to the default values.
4950(S): A Windows Firewall setting has changed.
4951(F): A rule has been ignored because its major version number was not recognized by Windows Firewall.
4952(F): Parts of a rule have been ignored because its minor version number was not recognized by Windows Firewall. The other parts of the rule will be enforced.
4953(F): A rule has been ignored by Windows Firewall because it could not parse the rule.
4954(S): Windows Firewall Group Policy settings have changed. The new settings have been applied.
4956(S): Windows Firewall has changed the active profile.
4957(F): Windows Firewall did not apply the following rule:
4958(F): Windows Firewall did not apply the following rule because the rule referred to items not configured on this computer:
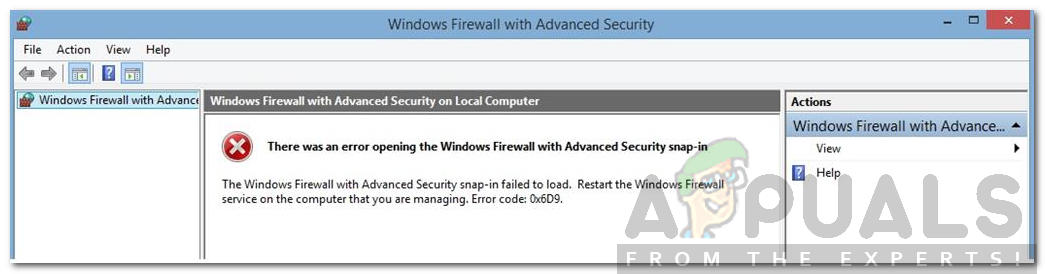
Accessing the internet has become a mandatory task in our daily lives. The Windows Firewall was introduced to control the incoming and outgoing requests of your computer system. The firewall receives its share of updates and Microsoft tends to improve drastically with every major update. Some of us like to keep the Windows Defender Firewall off as it can sometimes block certain requests that prevent us from doing what we aimed to. Sometimes, if you try to turn the Windows Defender Firewall back on, you will be given the error code 0x6d9 with a message stating ‘There was an error opening the Windows Firewall with Advanced Security snap-in’.
This error message often pops up if the Windows Firewall service is not running or if any of the services required for Windows Firewall are not running i.e BFE. Besides, it can be due to a few other reasons that we will discuss below. So let us get into it.
What causes the Windows Defender Firewall Error Code 0x6d9?
The error message suggests that the issue is due to the required services not running. However, that is not it. It can be, overall, due to the following reasons —
- Windows Firewall and Dependent Services not Running: This cause is quite obvious as it is mentioned in the error message itself. Windows Firewall requires a few services to be running to operate properly. If they are not running, the Firewall will not work.
- Windows Firewall Configuration: Sometimes, the issue can be due to the configuration of Windows Defender Firewall. In such a case, you will have to reset them.
- Malware on the System: In some scenarios, the issue can also be due to some malware on your system. To resolve the issue, you will have to run scans to remove the malware.
Now that you know of the causes of the issue, let us get into the solutions that you can implement to get the issue resolved. Please try to implement all of the solutions as some of the mentioned solutions might not work in your case.
Solution 1: Run the Windows Defender Troubleshooter
The first thing you need to do when you face this error is to run the Windows Defender troubleshooter. The troubleshooter will scan for any issues with the Firewall and try to resolve them. Here’s how to do it:
- First, grab the Windows Defender Firewall troubleshooter from here.
- Once it has finished downloading, run the downloaded file.
Windows Firewall Troubleshooter - Go through the prompts and let it finish.
- See if it resolves the issue.
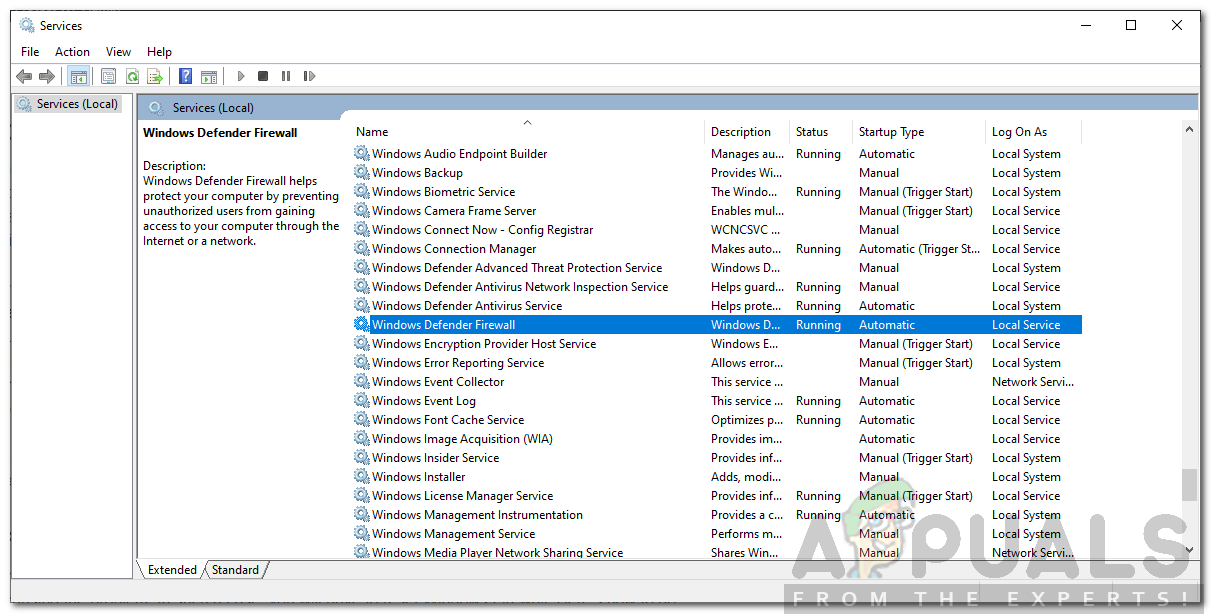
Solution 2: Check the Required Services
Another reason that the Windows Defender Firewall might not be starting is that the services required to initiate the Firewall are not running. The primary service is Windows Firewall service along with a few dependent services that are also needed to be running. You will have to check whether these services are running or not. Here’s how to do it:
- Press Windows Key + R to open up the Run dialog box.
- Type in services.msc and hit Enter.
- This will open up the Services window.
- Now, search for Windows Defender Firewall and Base Filtering Engine one by one and make sure that they are running.
Windows Firewall Service Running - Also, make sure that their Startup type is set to Automatic. To do this, double-click on the service to open up the Properties window. There, in front of Startup type, choose Automatic.
- If the service is running, you will have to stop it to make this change.
- Once done, see if the issue persists.
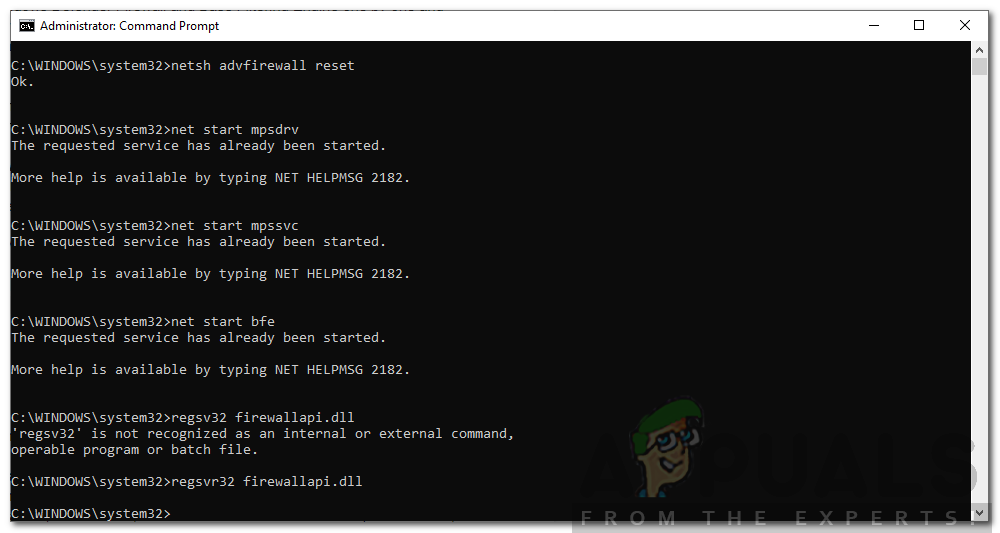
Solution 3: Reset Windows Firewall
If the issue is still there even after checking the Windows Firewall services, this can mean that the configuration of the Firewall is causing the problem. In such a case, you will have to reset Windows Firewall. Here’s how to do it:
- Open up the Start Menu, type cmd, right-click on the first result and select Run as an Administrator.
- After, type in the following commands one by one:
-
netsh advfirewall reset net start mpsdrv net start mpssvc net start bfe regsvr32 firewallapi.dll
Resetting Windows Firewall - Once done, close the cmd window and see if the issue has been solved.
Solution 4: Perform a System Scan
In case the Windows Defender Firewall still does not start up, there might be chances of malware on your system that might be causing the issue. You can deal with this by downloading this safety scanner provided by Microsoft to scan your system. Just download it and then run it. It will scan your system for any malware and remove it if found.
In case you are using a 32-bit Windows, you will have to download the utility from here.
Solution 5: Perform a System Restore
Finally, if your issue has not been resolved after trying all the given solutions, then, you will have to perform a System Restore. A System Restore will restore your operating system to a point in the past. This can help solve many issues.
Please refer to this article on our site for a detailed guide on System Restore. If you are using Windows 8 or 7, go ahead to this article instead.
Kevin Arrows
Kevin is a dynamic and self-motivated information technology professional, with a Thorough knowledge of all facets pertaining to network infrastructure design, implementation and administration. Superior record of delivering simultaneous large-scale mission critical projects on time and under budget.