- Remove From My Forums
-
Вопрос
-
Добрый день.
Имеем:
Windows 2012 Server Standart
Роли — контроллер домена, AD DS, DNS, Hyper-V. Работает несколько виртуальных машин.
Весь журнал завален ошибками 5858 WMI-Activity, примерно такого содержания:
Имя журнала: Microsoft-Windows-WMI-Activity/Operational Источник: Microsoft-Windows-WMI-Activity Дата: 09.04.2013 6:58:27 Код события: 5858 Категория задачи:Отсутствует Уровень: Ошибка Ключевые слова: Пользователь: СИСТЕМА Компьютер: SRV-MAIN.XXXX.XXXXXXXX.com Описание: Id = {E25A1B35-A874-4BC4-9514-069B77BE1942}; ClientMachine = SRV-MAIN; User = ; ClientProcessId = 1356; Component = Unknown; Operation = Start IWbemServices::DeleteInstance - RootRsopUserS_1_5_21_2475379679_2976830835_2111589685_1105 : RSOP_ExtensionStatus.extensionGuid="{4CFB60C1-FAA6-47f1-89AA-0B18730C9FD3}"; ResultCode = 0x80041002; PossibleCause = Unknown Xml события: <Event xmlns="http://schemas.microsoft.com/win/2004/08/events/event"> <System> <Provider Name="Microsoft-Windows-WMI-Activity" Guid="{1418EF04-B0B4-4623-BF7E-D74AB47BBDAA}" /> <EventID>5858</EventID> <Version>0</Version> <Level>2</Level> <Task>0</Task> <Opcode>0</Opcode> <Keywords>0x4000000000000000</Keywords> <TimeCreated SystemTime="2013-04-08T21:58:27.850773400Z" /> <EventRecordID>35560</EventRecordID> <Correlation /> <Execution ProcessID="1356" ThreadID="21972" /> <Channel>Microsoft-Windows-WMI-Activity/Operational</Channel> <Computer>SRV-MAIN.XXXX.XXXXXXXX.com</Computer> <Security UserID="S-1-5-18" /> </System> <UserData> <Operation_ClientFailure xmlns="http://manifests.microsoft.com/win/2006/windows/WMI"> <Id>{E25A1B35-A874-4BC4-9514-069B77BE1942}</Id> <ClientMachine>SRV-MAIN</ClientMachine> <User> </User> <ClientProcessId>1356</ClientProcessId> <Component>Unknown</Component> <Operation>Start IWbemServices::DeleteInstance - RootRsopUserS_1_5_21_2475379679_2976830835_2111589685_1105 : RSOP_ExtensionStatus.extensionGuid="{4CFB60C1-FAA6-47f1-89AA-0B18730C9FD3}"</Operation> <ResultCode>0x80041002</ResultCode> <PossibleCause>Unknown</PossibleCause> </Operation_ClientFailure> </UserData> </Event>
Наверное не умею пользоваться поиском, но не получилось ни чего найти, кроме подобных ссылок, где ответов еще нет Event
5858 from WMI-ActivityПрошу помочь с этой проблемой. Куда копать, что смотреть.
Заранее спасибо.
Ответы
-
Тема старая, но на всякий случай напишу: Данная ошибка проявляется при удалённом подключении к новым серверам MS Sever 2012 с устаревших версий клиентских операционных систем (Windows 7, XP). Это ругаются датчики классов WMI,
и как таковые не несут в себе угрозу работе сервера. Рекомендовано их игнорировать. Ну или подключайтесь к серверам для работы в интерфейсе под windows 10И то не факт, что таких ошибок не будет вовсе.
-
Помечено в качестве ответа
3 ноября 2017 г. 8:34
-
Помечено в качестве ответа
- Remove From My Forums
-
Вопрос
-
Добрый день.
Имеем:
Windows 2012 Server Standart
Роли — контроллер домена, AD DS, DNS, Hyper-V. Работает несколько виртуальных машин.
Весь журнал завален ошибками 5858 WMI-Activity, примерно такого содержания:
Имя журнала: Microsoft-Windows-WMI-Activity/Operational Источник: Microsoft-Windows-WMI-Activity Дата: 09.04.2013 6:58:27 Код события: 5858 Категория задачи:Отсутствует Уровень: Ошибка Ключевые слова: Пользователь: СИСТЕМА Компьютер: SRV-MAIN.XXXX.XXXXXXXX.com Описание: Id = {E25A1B35-A874-4BC4-9514-069B77BE1942}; ClientMachine = SRV-MAIN; User = ; ClientProcessId = 1356; Component = Unknown; Operation = Start IWbemServices::DeleteInstance - RootRsopUserS_1_5_21_2475379679_2976830835_2111589685_1105 : RSOP_ExtensionStatus.extensionGuid="{4CFB60C1-FAA6-47f1-89AA-0B18730C9FD3}"; ResultCode = 0x80041002; PossibleCause = Unknown Xml события: <Event xmlns="http://schemas.microsoft.com/win/2004/08/events/event"> <System> <Provider Name="Microsoft-Windows-WMI-Activity" Guid="{1418EF04-B0B4-4623-BF7E-D74AB47BBDAA}" /> <EventID>5858</EventID> <Version>0</Version> <Level>2</Level> <Task>0</Task> <Opcode>0</Opcode> <Keywords>0x4000000000000000</Keywords> <TimeCreated SystemTime="2013-04-08T21:58:27.850773400Z" /> <EventRecordID>35560</EventRecordID> <Correlation /> <Execution ProcessID="1356" ThreadID="21972" /> <Channel>Microsoft-Windows-WMI-Activity/Operational</Channel> <Computer>SRV-MAIN.XXXX.XXXXXXXX.com</Computer> <Security UserID="S-1-5-18" /> </System> <UserData> <Operation_ClientFailure xmlns="http://manifests.microsoft.com/win/2006/windows/WMI"> <Id>{E25A1B35-A874-4BC4-9514-069B77BE1942}</Id> <ClientMachine>SRV-MAIN</ClientMachine> <User> </User> <ClientProcessId>1356</ClientProcessId> <Component>Unknown</Component> <Operation>Start IWbemServices::DeleteInstance - RootRsopUserS_1_5_21_2475379679_2976830835_2111589685_1105 : RSOP_ExtensionStatus.extensionGuid="{4CFB60C1-FAA6-47f1-89AA-0B18730C9FD3}"</Operation> <ResultCode>0x80041002</ResultCode> <PossibleCause>Unknown</PossibleCause> </Operation_ClientFailure> </UserData> </Event>Наверное не умею пользоваться поиском, но не получилось ни чего найти, кроме подобных ссылок, где ответов еще нет Event
5858 from WMI-ActivityПрошу помочь с этой проблемой. Куда копать, что смотреть.
Заранее спасибо.
Ответы
-
Тема старая, но на всякий случай напишу: Данная ошибка проявляется при удалённом подключении к новым серверам MS Sever 2012 с устаревших версий клиентских операционных систем (Windows 7, XP). Это ругаются датчики классов WMI,
и как таковые не несут в себе угрозу работе сервера. Рекомендовано их игнорировать. Ну или подключайтесь к серверам для работы в интерфейсе под windows 10И то не факт, что таких ошибок не будет вовсе.
- Помечено в качестве ответа
3 ноября 2017 г. 8:34
- Помечено в качестве ответа
| title | description | ms.date | author | ms.author | manager | audience | ms.topic | ms.prod | localization_priority | ms.reviewer | ms.custom | ms.technology |
|---|---|---|---|---|---|---|---|---|---|---|---|---|
|
WMI-Activity Event 5858 ResultCode 0x80041032 |
WMI-Activity Event ID 5858 is logged with ResultCode 0x80041032 when applications issue WMI queries. |
09/08/2020 |
Deland-Han |
delhan |
dcscontentpm |
ITPro |
troubleshooting |
windows-client |
medium |
kaushika, steved, cmyu, ssutari |
sap:wmi, csstroubleshoot |
windows-client-system-management-components |
This article provides a resolution to solve the WMI-Activity event ID 5858 that’s logged with ResultCode = 0x80041032 in Windows Server 2012 R2.
Applies to: Windows Server 2012 R2
Original KB number: 3124914
Symptoms
When using Windows Server 2012 R2 with applications that issue WMI queries using IWbemServices:ExecQuery, the administrator may observe the following event in Event Viewer:
Log Name: Microsoft-Windows-WMI-Activity/Operational
Source: WMI-Activity
Event ID: 5858
Level: Error
Id = {guid}; ClientMachine = <computer>; User = <user>; ClientProcessId = <process ID>; Component = Unknown; Operation = Start IWbemServices::ExecQuery - <WMI namespace>: <Select Query Statement>; ResultCode = 0x80041032; PossibleCause = Unknown
where 0x80041032 indicates WBEM_E_CALL_CANCELLED.
[!NOTE]
This event can occur with many different ResultCode values. The problem described in this article only applies whenResultCode = 0x80041032 (WBEM_E_CALL_CANCELLED).
Cause
WMI-Activity Error 5858 with ResultCode = 0x80041032 (WBEM_E_CALL_CANCELLED) indicates that the WMI caller has successfully issued IWbemServices:ExecQuery, but has released the IWbemContext object before retrieving the full result set using the IEnumWbemClassObject::Next method. If the WMI service is still holding data for the client when the client terminates the link (by releasing the IWbemContext object), this event will be logged.
This error can happen if the WMI application calls IEnumWbemClassObject::Next with a timeout value (lTimeout) that is not long enough to retrieve the object being queried, and is not checking for a return code of WBEM_S_TIMEDOUT (0x40004) in order to issue the request again.
Resolution
The WMI client application should be modified to issue calls to IEnumWbemClassObject::Next to retrieve the full result set, before releasing the IWbemContext object. If no objects are received, make sure that the timeout value (lTimeout) is greater than 0 and that WBEM_S_TIMEDOUT (0x40004) is not being returned.
More information
For more information, see:
-
IEnumWbemClassObject interface
[!NOTE]
The sample code included at the end of this page showsIEnumWbemClassObject::Nextbeing called with a timeout value (lTimeout) of 0, and is not checking for the WBEM_S_TIMEDOUT error. -
IWbemServices::ExecQuery method
-
IEnumWbemClassObject::Next method
Good morning,
This question is a copy of
the one, asked on the Microsoft community. I’ve been advised to copy this question here. Hereby my question:
On a customer’s system, I’ve installed a program, which launches quite some WMI queries, for determining the status of the machine.
Regularly those WMI queries are failing, and in event logs, there are lots of errors (event ID 5858), hereby a typical example (I’ve obfuscated computer name, customer name and GUID for security reasons):
Log Name: Microsoft-Windows-WMI-Activity/Operational
Source: Microsoft-Windows-WMI-Activity
Date: 1/04/2019 14:54:06
Event ID: 5858
Task Category: None
Level: Error
Keywords:
User: SYSTEM
Computer: Computer_Name.Customer.intra
Description:
Id = {00000000-0000-0000-0000-000000000000}; ClientMachine = Computer_Name; User = NT AUTHORITYSYSTEM; ClientProcessId = 6968; Component = Unknown; Operation = Start IWbemServices::ExecQuery — rootccmpolicymachine : select * from InventoryAction where InventoryActionID=»{00000000-0000-0000-0000-000000000001}»;
ResultCode = 0x80041032; PossibleCause = Unknown
Event Xml:
<Event xmlns=»http://schemas.microsoft.com/win/2004/08/events/event»>
<System>
<Provider Name=»Microsoft-Windows-WMI-Activity» Guid=»{……..-….-….-….-…………}» />
<EventID>5858</EventID>
<Version>0</Version>
<Level>2</Level>
<Task>0</Task>
<Opcode>0</Opcode>
<Keywords>0x4000000000000000</Keywords>
<TimeCreated SystemTime=»2019-04-01T12:54:06.515593700Z» />
<EventRecordID>570075</EventRecordID>
<Correlation />
<Execution ProcessID=»1736″ ThreadID=»30436″ />
<Channel>Microsoft-Windows-WMI-Activity/Operational</Channel>
<Computer>Computer_Name.Customer.intra</Computer>
<Security UserID=»S-1-5-18″ />
</System>
<UserData>
<Operation_ClientFailure xmlns=»http://manifests.microsoft.com/win/2006/windows/WMI»>
<Id>{00000000-0000-0000-0000-000000000000}</Id>
<ClientMachine>Computer_Name</ClientMachine>
<User>NT AUTHORITYSYSTEM</User>
<ClientProcessId>6968</ClientProcessId>
<Component>Unknown</Component>
<Operation>Start IWbemServices::ExecQuery — rootccmpolicymachine : select * from InventoryAction where InventoryActionID=»{00000000-0000-0000-0000-000000000001}»</Operation>
<ResultCode>0x80041032</ResultCode>
<PossibleCause>Unknown</PossibleCause>
</Operation_ClientFailure>
</UserData>
</Event>
There are 210 such events, the different «ResultCode» values are shown here:
| Amount of occurences | ResultCode |
| 1 | 0x80041033 |
| 1 | 0x800706BE |
| 2 | 0x80041017 |
| 6 | 0x80070422 |
| 14 | 0x80041001 |
| 18 | 0x80041010 |
| 42 | 0x80041002 |
| 44 | 0x80041032 |
| 82 | 0x8004101D |
The customer has Windows Server 2016.
Why are those error logs appearing and what can I do in order to avoid them? (Windows update, patch installation (which one?), …)
For your information, my program(s) is/are launching lots of WMI queries, some of them quite complicated, like this one:
SELECT Handle,Name,PageFileUsage,WorkingSetSize,VirtualSize,CommandLine FROM Win32_Process WHERE CommandLine IS NOT NULL AND (ProcessId=6968 or ProcessId=3796 or ProcessId=1120 or ProcessId=3056 or ProcessId=6620 or ProcessId=7520 or ProcessId=28980 or ProcessId=29328 or ProcessId=9012 or ProcessId=7588 or ProcessId=7212 or ProcessId=7744 or ProcessId=7300 or ProcessId=7380 or ProcessId=7416 or ProcessId=9936 or ProcessId=10000 or ProcessId=10068 or ProcessId=10136 or ProcessId=9824 or ProcessId=10808 or ProcessId=10868 or ProcessId=10928 or ProcessId=10996 or ProcessId=10768 or ProcessId=8724 or ProcessId=7136 or ProcessId=8756 or ProcessId=2752 or ProcessId=12984 or ProcessId=10988 or ProcessId=9312 or ProcessId=7308 or ProcessId=7752 or ProcessId=4 or ProcessId=2864 or ProcessId=1684 or ProcessId=2872 or ProcessId=3080 or ProcessId=5452 or ProcessId=6288 or ProcessId=5668 or ProcessId=7628 or ProcessId=38504 or ProcessId=6236 or ProcessId=34356 or ProcessId=3940 or ProcessId=5996 or ProcessId=3068 or ProcessId=3076 or ProcessId=8940 or ProcessId=2688 or ProcessId=3048 or ProcessId=2392 or ProcessId=912 or ProcessId=824 or ProcessId=12252 or ProcessId=2664 or ProcessId=30376 or ProcessId=1128 or ProcessId=2880 or ProcessId=108 or ProcessId=4472 or ProcessId=2960 or ProcessId=2912 or ProcessId=116 or ProcessId=712 or ProcessId=10672 or ProcessId=2284 or ProcessId=1748 or ProcessId=2056 or ProcessId=2572 or ProcessId=2580 or ProcessId=2588 or ProcessId=2760 or ProcessId=2768 or ProcessId=2844 or ProcessId=136 or ProcessId=1212 or ProcessId=1220 or ProcessId=1300 or ProcessId=1328 or ProcessId=1336 or ProcessId=1400 or ProcessId=1568 or ProcessId=1736 or ProcessId=816 or ProcessId=1600 or ProcessId=2640 or ProcessId=37004 or ProcessId=936 or ProcessId=968 or ProcessId=3648)
Thanks in advance
Dominique
- Edited by
Wednesday, April 3, 2019 10:31 AM
- Moved by
cloris_sun
Monday, April 8, 2019 9:50 AM
Good morning,
This question is a copy of
the one, asked on the Microsoft community. I’ve been advised to copy this question here. Hereby my question:
On a customer’s system, I’ve installed a program, which launches quite some WMI queries, for determining the status of the machine.
Regularly those WMI queries are failing, and in event logs, there are lots of errors (event ID 5858), hereby a typical example (I’ve obfuscated computer name, customer name and GUID for security reasons):
Log Name: Microsoft-Windows-WMI-Activity/Operational
Source: Microsoft-Windows-WMI-Activity
Date: 1/04/2019 14:54:06
Event ID: 5858
Task Category: None
Level: Error
Keywords:
User: SYSTEM
Computer: Computer_Name.Customer.intra
Description:
Id = {00000000-0000-0000-0000-000000000000}; ClientMachine = Computer_Name; User = NT AUTHORITYSYSTEM; ClientProcessId = 6968; Component = Unknown; Operation = Start IWbemServices::ExecQuery — rootccmpolicymachine : select * from InventoryAction where InventoryActionID=»{00000000-0000-0000-0000-000000000001}»;
ResultCode = 0x80041032; PossibleCause = Unknown
Event Xml:
<Event xmlns=»http://schemas.microsoft.com/win/2004/08/events/event»>
<System>
<Provider Name=»Microsoft-Windows-WMI-Activity» Guid=»{……..-….-….-….-…………}» />
<EventID>5858</EventID>
<Version>0</Version>
<Level>2</Level>
<Task>0</Task>
<Opcode>0</Opcode>
<Keywords>0x4000000000000000</Keywords>
<TimeCreated SystemTime=»2019-04-01T12:54:06.515593700Z» />
<EventRecordID>570075</EventRecordID>
<Correlation />
<Execution ProcessID=»1736″ ThreadID=»30436″ />
<Channel>Microsoft-Windows-WMI-Activity/Operational</Channel>
<Computer>Computer_Name.Customer.intra</Computer>
<Security UserID=»S-1-5-18″ />
</System>
<UserData>
<Operation_ClientFailure xmlns=»http://manifests.microsoft.com/win/2006/windows/WMI»>
<Id>{00000000-0000-0000-0000-000000000000}</Id>
<ClientMachine>Computer_Name</ClientMachine>
<User>NT AUTHORITYSYSTEM</User>
<ClientProcessId>6968</ClientProcessId>
<Component>Unknown</Component>
<Operation>Start IWbemServices::ExecQuery — rootccmpolicymachine : select * from InventoryAction where InventoryActionID=»{00000000-0000-0000-0000-000000000001}»</Operation>
<ResultCode>0x80041032</ResultCode>
<PossibleCause>Unknown</PossibleCause>
</Operation_ClientFailure>
</UserData>
</Event>
There are 210 such events, the different «ResultCode» values are shown here:
| Amount of occurences | ResultCode |
| 1 | 0x80041033 |
| 1 | 0x800706BE |
| 2 | 0x80041017 |
| 6 | 0x80070422 |
| 14 | 0x80041001 |
| 18 | 0x80041010 |
| 42 | 0x80041002 |
| 44 | 0x80041032 |
| 82 | 0x8004101D |
The customer has Windows Server 2016.
Why are those error logs appearing and what can I do in order to avoid them? (Windows update, patch installation (which one?), …)
For your information, my program(s) is/are launching lots of WMI queries, some of them quite complicated, like this one:
SELECT Handle,Name,PageFileUsage,WorkingSetSize,VirtualSize,CommandLine FROM Win32_Process WHERE CommandLine IS NOT NULL AND (ProcessId=6968 or ProcessId=3796 or ProcessId=1120 or ProcessId=3056 or ProcessId=6620 or ProcessId=7520 or ProcessId=28980 or ProcessId=29328 or ProcessId=9012 or ProcessId=7588 or ProcessId=7212 or ProcessId=7744 or ProcessId=7300 or ProcessId=7380 or ProcessId=7416 or ProcessId=9936 or ProcessId=10000 or ProcessId=10068 or ProcessId=10136 or ProcessId=9824 or ProcessId=10808 or ProcessId=10868 or ProcessId=10928 or ProcessId=10996 or ProcessId=10768 or ProcessId=8724 or ProcessId=7136 or ProcessId=8756 or ProcessId=2752 or ProcessId=12984 or ProcessId=10988 or ProcessId=9312 or ProcessId=7308 or ProcessId=7752 or ProcessId=4 or ProcessId=2864 or ProcessId=1684 or ProcessId=2872 or ProcessId=3080 or ProcessId=5452 or ProcessId=6288 or ProcessId=5668 or ProcessId=7628 or ProcessId=38504 or ProcessId=6236 or ProcessId=34356 or ProcessId=3940 or ProcessId=5996 or ProcessId=3068 or ProcessId=3076 or ProcessId=8940 or ProcessId=2688 or ProcessId=3048 or ProcessId=2392 or ProcessId=912 or ProcessId=824 or ProcessId=12252 or ProcessId=2664 or ProcessId=30376 or ProcessId=1128 or ProcessId=2880 or ProcessId=108 or ProcessId=4472 or ProcessId=2960 or ProcessId=2912 or ProcessId=116 or ProcessId=712 or ProcessId=10672 or ProcessId=2284 or ProcessId=1748 or ProcessId=2056 or ProcessId=2572 or ProcessId=2580 or ProcessId=2588 or ProcessId=2760 or ProcessId=2768 or ProcessId=2844 or ProcessId=136 or ProcessId=1212 or ProcessId=1220 or ProcessId=1300 or ProcessId=1328 or ProcessId=1336 or ProcessId=1400 or ProcessId=1568 or ProcessId=1736 or ProcessId=816 or ProcessId=1600 or ProcessId=2640 or ProcessId=37004 or ProcessId=936 or ProcessId=968 or ProcessId=3648)
Thanks in advance
Dominique
- Edited by
Wednesday, April 3, 2019 10:31 AM
- Moved by
cloris_sun
Monday, April 8, 2019 9:50 AM
Posted by DDoc 2013-12-10T18:07:47Z
I have a Windows 2012 R2 server that I periodically get several of the below (or similar) messages. Any idea what the issue might be?
Id = {BF062B92-ECEA-46B8-A09F-7E6D6F430BAA}; ClientMachine = ELM; User = ; ClientProcessId = 712; Component = Unknown; Operation = Start IWbemServices::DeleteInstance — RootRsopUserS_1_5_21_719535676_533339174_944726268_1292 : RSOP_ExtensionStatus.extensionGuid=»{0E28E245-9368-4853-AD84-6DA3BA35BB75}»; ResultCode = 0x80041002; PossibleCause = Unknown
1 Reply
lock
This topic has been locked by an administrator and is no longer open for commenting.
To continue this discussion, please ask a new question.
Read these next…
WINDOWS 10 «glitch» — file explorer
Windows
Hi.I have been experiencing a black line (glitch) on my file explorer which comes for milliseconds then it goes away. See screen grab. Is there anyone who has experienced such and how were they able to solve it?Thank you.
Are you updating workstations to Windows 11?
Windows
Has anyone started updating workstations on a AD domain to Windows 11? what type of issues are you facing?What is the user reaction been?Thanks!
Snap! — Psyche Probe, DIY Gene Editing, RaiBo, AI handwriting, Metric Pirates
Spiceworks Originals
Your daily dose of tech news, in brief.
Welcome to the Snap!
Flashback: January 27, 1880: Thomas Edison receives patent for the Electric Lamp. (Read more HERE.)
Bonus Flashback: January 27, 1967: Apollo 1 Tragedy (Read more HERE.)
You …
NEC Inmail Email doesn’t Change
Collaboration
Hey Everyone,Recently a client of mine wanted to change the email to their QA extension to her email as to help keep voicemails consolidated instead of spread out among different emails. Normally this wouldn’t be a huge deal. Logged in to to Webpro, hoppe…
I inherited some really cool equipment. I just have no clue how to use it!
Hardware
So I’ve got some switches, and some servers. The switches seem pretty straight forward, plug in packet go zoom, but I have no clue how these servers work. They’re headless rack servers. I know there must be a way to get some kind of UI going with a monito…
Windows 10: WMI activity even 5858 and no one seems to know how to fix it
Discus and support WMI activity even 5858 and no one seems to know how to fix it in Windows 10 Network and Sharing to solve the problem; I have been receiving these errors for a very long time on windows 10. My event viewer for the service WMI is completely full of 5858 errors. The only…
Discussion in ‘Windows 10 Network and Sharing’ started by JumpierElf91, Aug 26, 2021.
-
WMI activity even 5858 and no one seems to know how to fix it
I have been receiving these errors for a very long time on windows 10. My event viewer for the service WMI is completely full of 5858 errors. The only fix i haven’t tried is one that no one seems to be able to help me do.https://docs.microsoft.com/de-DE/troubleshoot/windows-client/system-management-components/wmi-activity-event-5858-logged-with-resultcode-0x80041032it explains that I should do the following.The WMI client application should be modified to IEnumWbemClassObject::Nextissue calls to get the full result set before the IWbemContext object is released. If no objec
-
WMI Activity generates event ID 5858 every 15 seconds
WMI Activity generates event ID 5858 every 15 seconds
Errors Are related to Intel CIntelWLANEvent, win32_perfformatteddata_perfdisk_physicaldisk CurrentDiskQueueLength, BIOSEventRan dism Sfc Chkdsk all without error.
Turned off WMI performance adapter Service and the errors ceased
At one point it had reconfigured all my apps
I have created a wmi activity evtx file
Error 11/15/2017 2:18:52 PM WMI-Activity 5858 NoneWindows 10 home Fall creators edition Dell 5567
[Moved from: Windows / Windows 10 / Windows settings]
-
WMI events 5858 on a Windows Server 2016, what to do?
Thanks for your quick reply.
As suggested I created a copy of this question on Technet forum: Technet
copy -
WMI activity even 5858 and no one seems to know how to fix it
Windows not shutting down, caused by Event Error 5858 ? (WMI Activity)
Regularly my pc does not shut down, it gets stuck on the blue screen with «Shutting Down»
After a while I need to shut down the pc, using the power-button on the case.I already untagged «Turn on fast start-up (recommended)»
under Control Panel->All Control Panel Items->Power Options->System Settings under ‘Shut-down settings»Regretfully that did not solve the issue.
I checked the event log between me initiating shutdown (event 1074) and rebooting.
There are quite a number of entries reading like this:
Event : 5858
Source : Microsoft-Windows-WMI-Activity
Description:
Id = {00000000-0000-0000-0000-000000000000}; ClientMachine = DESKTOP-JFFLEA5; User = NT AUTHORITYSYSTEM; ClientProcessId = 2908; Component = Unknown; Operation = Start IWbemServices::ExecQuery — rootwmi : select * from WDMClassesOfDriver where ClassName = «MSStorageDriver_ClassErrorLogEntry»; ResultCode = 80041032; PossibleCause Unknown
—
Event : 5858
Source : Microsoft-Windows-WMI-Activity
Description:
Id = {00000000-0000-0000-0000-000000000000}; ClientMachine = DESKTOP-JFFLEA5; User = NT AUTHORITYSYSTEM; ClientProcessId = 2908; Component = Unknown; Operation = Start IWbemServices::ExecQuery — rootwmi : select * from WMIBinaryMofResource where Name = «USBSTORDisk&Ven_WD&Prod_My_Book_1230&Rev_106557583231443934374E345956&0_0-{05901221-D566-11d1-B2F0-00A0C9062910}»; ResultCode = 80041032; PossibleCause = Unknown
=Note that I did have external drives running, but they were properly removed (ejected) and then, before shutting down, they were switched/powered off, i.e. they didn’t exist anymore for Windows.
Does anybody out there know how to handle this and what is causing this error?
Any solutions?Thanks!
=
Thema:
WMI activity even 5858 and no one seems to know how to fix it
-
WMI activity even 5858 and no one seems to know how to fix it — Similar Threads — WMI activity 5858
-
Repeated WMI Error 0x80041032 Event 5858 caused by swiservice.exe, cause «Unknown»
in Windows 10 BSOD Crashes and Debugging
Repeated WMI Error 0x80041032 Event 5858 caused by swiservice.exe, cause «Unknown»: Hi everyoneI came across this while looking into what’s gobbling up CPU power at startup. This is the output from Event Viewer > Applications and Service LogsMicrosoftWindowsWMI-ActivityOperational:Log Name: Microsoft-Windows-WMI-Activity/OperationalSource:…
-
Repeated WMI Error 0x80041032 Event 5858 caused by swiservice.exe, cause «Unknown»
in Windows 10 Gaming
Repeated WMI Error 0x80041032 Event 5858 caused by swiservice.exe, cause «Unknown»: Hi everyoneI came across this while looking into what’s gobbling up CPU power at startup. This is the output from Event Viewer > Applications and Service LogsMicrosoftWindowsWMI-ActivityOperational:Log Name: Microsoft-Windows-WMI-Activity/OperationalSource:…
-
Repeated WMI Error 0x80041032 Event 5858 caused by swiservice.exe, cause «Unknown»
in Windows 10 Software and Apps
Repeated WMI Error 0x80041032 Event 5858 caused by swiservice.exe, cause «Unknown»: Hi everyoneI came across this while looking into what’s gobbling up CPU power at startup. This is the output from Event Viewer > Applications and Service LogsMicrosoftWindowsWMI-ActivityOperational:Log Name: Microsoft-Windows-WMI-Activity/OperationalSource:…
-
Anyone know how to fix this?
in Windows 10 Ask Insider
Anyone know how to fix this?: Since my computer updated to Windows 10 Version 2004 it’s been virtually impossible to play games. Constant black screen crashes on multiple games and even basic stuff like watching Youtube. Been looking around for how to fix this but haven’t found anything and I’m not…
-
Anyone know how to fix this?
in Windows 10 Ask Insider
Anyone know how to fix this?: [ATTACH] submitted by /u/Antron_edition
[link] [comments] -
WMI issue with event id 5858
in Windows 10 BSOD Crashes and Debugging
WMI issue with event id 5858: I have Windows 10. I have an issue with the CPU usage and it seems to be connected to WMI. It means that my fan is constantly running and the machine seems to be always doing something. I have done a bit of research and have identified that the error seems to be caused by…
-
WMI-Activity Error
in Windows 10 Customization
WMI-Activity Error: Hiya, I was having trouble with WMI Provider Host, I googled it and did actually manage to find a thread on here linked below:…
-
WMI activity ERROR
in Windows 10 Network and Sharing
WMI activity ERROR: How can I fix the WMI error in Window 10?
https://answers.microsoft.com/en-us/windows/forum/all/wmi-activity-error/bd3ec1d0-89a6-48a1-9346-0f54a811fbd0
-
Windows not shutting down, caused by Event Error 5858 ? (WMI Activity)
in Windows 10 Performance & Maintenance
Windows not shutting down, caused by Event Error 5858 ? (WMI Activity): Regularly my pc does not shut down, it gets stuck on the blue screen with «Shutting Down»
After a while I need to shut down the pc, using the power-button on the case.I already untagged «Turn on fast start-up (recommended)»
under Control Panel->All Control Panel…
Users found this page by searching for:
-
wmi-activity event 5858 0x80041013
,
-
event id 5858 wmi-activity
Любой бывалый Windows-админ периодически сталкивается с проблемами в работе службы WMI (Windows Management Instrumentation) и ее компонентах. Наличие проблем в подсистеме WMI является критичным с точки зрения нормального функционирования Windows, поэтому администратору необходимо проверить и восстановить работоспособность WMI. В этой статье мы опишем простую методику диагностирования и устранения неполадок службы WMI в Windows.
О наличии проблем с WMI может свидетельствовать широкий спектр ошибок:
- Ошибки обработки WMI запросов в системных журналах и логах приложений (
0x80041002 - WBEM_E_NOT_FOUND
,
WMI: Not Found
,
0x80041010 WBEM_E_INVALID_CLASS
); - Ошибки обработки GPO, связанные на WMI ( некорректная работа wmi фильтров групповых политик, и пр.);
- WMI запросы выполняются очень медленно;
- Ошибки при установке или работе агентов SCCM/SCOM;
- Ошибки в работе скриптов (vbs или PowerShell), использующих пространство имен WMI (скрипты с Get-WmiObject и т.д.).
Содержание:
- Диагностика проблем с WMI
- Исправление WMI репозитория, перерегистрация библиотек, перекомпиляция MOF файлов
- Сброс и пересоздание WMI репозитория (хранилища)
В первую очередь нужно проверить служба Windows Management Instrumentation (Winmgmt) установлена в Windows и запущена. Вы можете проверить состояние службы в консоли services.msc или с помощью PowerShell:
Get-Service Winmgmt | Select DisplayName,Status,ServiceName
Если служба Winmgmt запущена, вы можете проверить работоспособность WMI, обратившись к ней с помощью простого WMI-запроса. Вы можете выполнить wmi запрос из командной строки или из PowerShell. Например, следующая команда выведет список установленных в Windows программ:
wmic product get name,version
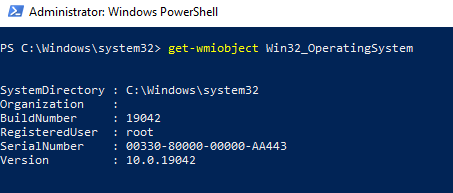
Простейшая PowerShell команда для получения информации о версии и билда Windows 10 через WMI может выглядеть так:
get-wmiobject Win32_OperatingSystem
Как вы видите, служба WMI ответила на запрос корректно. Если при выполнении такого WMI-запроса Windows возвращает ошибку, скорее всего сервиса WMI работает некорректно, поврежден WMI репозиторий или есть какие-то другие проблемы.
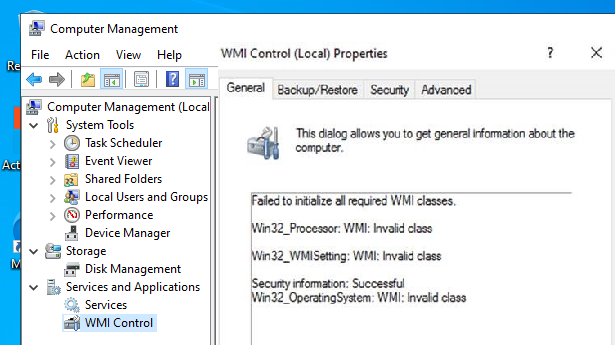
В моем случае, например, при открытии свойств WMI Control в консоли управления компьютером (compmgmt.msc) появлялась надпись:
Failed to initialize all required WMI classes Win32_Processor. WMI: Invalid namespace Win32_WMISetting. WMI: Invalid namespace Win32_OperationSystem. WMI: Invalid namespace
Ранее для диагностики WMI существовала официальная утилита от Microsoft – WMIDiag.vbs (Microsoft WMI Diagnosis). WMIdiag это vbs скрипт, который проверяет различные подсистемы WMI и записывает собранную информацию в лог файлы (по умолчанию логи находятся в каталоге %TEMP% — C:USERS%USERNAME%APPDATALOCALTEMP). Получившийся отчет состоит из файлов, имена которых начинаются с WMIDIAG-V2.2 и включает в себя следующие типы фалов:
- .log файлы содержат подробный отчет об активности и работе утилиты WMIDiag;
- .txt файлы содержат итоговые отчеты о найденных ошибках, на которые стоит обратить внимание;
- В .csv файлах содержится информация, нужная для долгосрочного анализа работы подсистемы WMI.
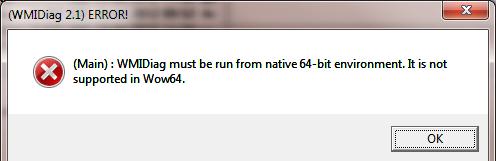
Совет. В 64 битных версиях Windows wmidiag нужно запускать так:
c:windowsSystem32cscript.exe wmidiag.vbs
в противном случае появится ошибка:
WMIDiag must be run from native 64-bit environment. It is not supported in Wow64.
После окончания работы утилиты WMIDiag администратор должен изучить полученные файлы логов, проанализировать и попытаться исправить найденные ошибки.
К сожалению, последняя версия WMIDiag 2.2 корректно работает только с версиями до Windows 8.1/Windows Server 2012 R2. На данный момент Microsoft даже удалила ссылку на загрузку WMIDiag из Download Center. Но при желании, этот скрипт можно найти в сети.
WMIDiag может дать подробную информацию по исправлению частных ошибок в WMI, но в большинстве случаев процесс это довольно трудоемкий и стоит потраченного времени только при решении инцидентов в критичных системах (как правило, на продуктивных серверах). Для массового сегмента рабочих станций пользователей сбросить и пересоздатьWMI репозиторий в Windows.
Исправление WMI репозитория, перерегистрация библиотек, перекомпиляция MOF файлов
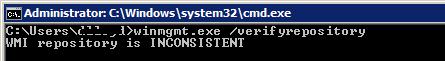
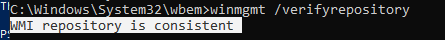
В Windows 10/Windows Server 2016 вы можете проверить целостность репозитория WMI с помощью команды:
winmgmt /verifyrepository
Если команда возвращает, что база данных WMI находится в неконсистентном состоянии (INCONSISTENT или WMI repository verification failed), стоит попробовать выполнить “мягкое” исправление ошибок репозитория:
Winmgmt /salvagerepository
WMI repository has been salvaged.
Данная команда выполняет проверку согласованности хранилища WMI и при обнаружении несогласованности перестраивает базу данных WMI.
Перезапустите службу WMI:
net stop Winmgmt
net start Winmgmt
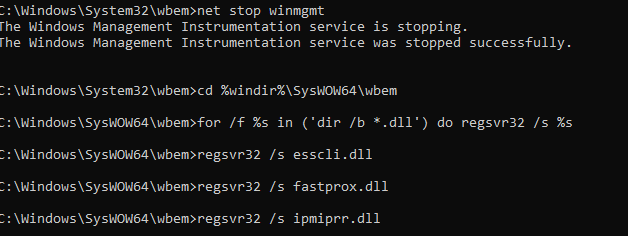
Если стандартный способ исправления ошибок в WMI не помог, попробуйте следующий скрипт. Данный скрипт представляет собой ”мягкий” вариант восстановления службы WMI на компьютере (выполняется перерегистрация dll библиотек и службы WMI, перекомпилируются mof файлы). Данная процедура является безопасной и ее выполнение не должно привести к каким-либо новым проблемам с системой.
sc config winmgmt start= disabled
net stop winmgmt
cd %windir%system32wbem
for /f %s in ('dir /b *.dll') do regsvr32 /s %s
wmiprvse /regserver
sc config winmgmt start= auto
net start winmgmt
for /f %s in ('dir /b *.mof') do mofcomp %s
for /f %s in ('dir /b *.mfl') do mofcomp %s
На 64 битной версии Windows эти действия нужно также выполнить для каталога SysWOW64. Замените третью строку на
cd %windir%SysWOW64wbem
Указанные команды можно выполнить путем простой вставки в окно командой строки, либо сохранить код в bat файле wmi_soft_repair.bat и запустить его с правами администратора. После окончания работы скрипта, перезагрузите Windows и проверьте работу WMI.
Сброс и пересоздание WMI репозитория (хранилища)
Если вам не помогли мягкие способ восстановления WMI, рассмотренные выше, придется перейти к более “жесткому” способу восстановления работоспособности службы WMI, заключающегося в пересоздании хранилищаWMI.
WMI репозиторий (хранилище) находится в каталоге
%windir%System32WbemRepository
и представляет собой базу данных, в которой содержится информация о метаданных и определениях WMI классов. В некоторых случаях WMI репозиторий может содержать статическую информацию классов. При повреждении репозитория WMI, в работе службы Windows Management Instrumentation (Winmgmt) могут наблюдаться ошибки вплоть до полной невозможности ее запустить.
Если вы подозреваете, что репозиторий WMI поврежден, имейте в виду, что его пересоздание — это последняя шаг, к которому нужно прибегнуть только тогда, когда другие операции не помогают реанимировать WMI.
Следующая команда выполнит сброс базы данных WMI к исходному состоянию (как после чистой установки Windows). Используйте эту команду для выполнения hard reset репозитория WMI, если параметре salvagerepository не исправил проблему:
Winmgmt /resetrepository
Совет. На практике бывают случаи, когда пересоздание хранилища WMI приводит к проблемам со сторонним софтом. Это связано с тем, что все записи в базе WMI обнуляются (до состояния чистой системы). Такие программы скорее всего, придется переустанавливать в режиме восстановления.
Если обе команды (
Winmgmt /salvagerepository
и
Winmgmt /resetrepository
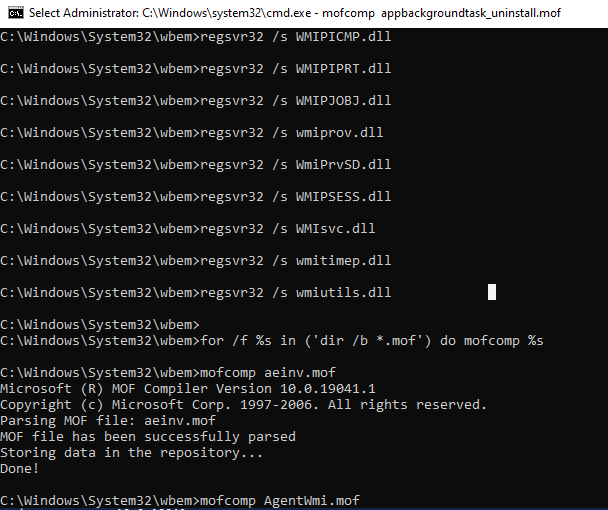
) не восстановили консистентное состояние базы WMI, попробуйте выполнить “жесткое” пересоздание базы WMI вручную таким скриптом:
sc config winmgmt start= disabled
net stop winmgmt
cd %windir%system32wbem
winmgmt /resetrepository
winmgmt /resyncperf
if exist Repos_bakup rd Repos_bakup /s /q
rename Repository Repos_bakup
regsvr32 /s %systemroot%system32scecli.dll
regsvr32 /s %systemroot%system32userenv.dll
for /f %s in ('dir /b *.dll') do regsvr32 /s %s
for /f %s in ('dir /b *.mof') do mofcomp %s
for /f %s in ('dir /b *.mfl') do mofcomp %s
sc config winmgmt start= auto
net start winmgmt
wmiprvse /regserver
На 64 битной версии Windows нужно также перерегистрировать dll/exe и перекомпилировать mof файлы в каталоге %windir%sysWOW64wbem.
Данный скрипт полностью пересоздает хранилище WMI (старый репозиторий сохраняется в каталог Repos_bakup). После окончания работы скрипта нужно перезагрузить Windows. Затем протестируйте работу службы WMI простым запросом.
Проверьте состояние WMI репозитория. Если ошибки исправлены, команда
winmgmt /verifyrepository
должна вернуть:
WMI repository is consistent
В этой статье мы собрали основные способы, позволяющие продиагностировать и устранить неполадки службы и репозитория WMI.
| title | description | ms.date | author | ms.author | manager | audience | ms.topic | ms.prod | localization_priority | ms.reviewer | ms.custom | ms.technology |
|---|---|---|---|---|---|---|---|---|---|---|---|---|
|
WMI-Activity Event 5858 ResultCode 0x80041032 |
WMI-Activity Event ID 5858 is logged with ResultCode 0x80041032 when applications issue WMI queries. |
09/08/2020 |
Deland-Han |
delhan |
dcscontentpm |
ITPro |
troubleshooting |
windows-client |
medium |
kaushika, steved, cmyu, ssutari |
sap:wmi, csstroubleshoot |
windows-client-system-management-components |
This article provides a resolution to solve the WMI-Activity event ID 5858 that’s logged with ResultCode = 0x80041032 in Windows Server 2012 R2.
Applies to: Windows Server 2012 R2
Original KB number: 3124914
Symptoms
When using Windows Server 2012 R2 with applications that issue WMI queries using IWbemServices:ExecQuery, the administrator may observe the following event in Event Viewer:
Log Name: Microsoft-Windows-WMI-Activity/Operational
Source: WMI-Activity
Event ID: 5858
Level: Error
Id = {guid}; ClientMachine = <computer>; User = <user>; ClientProcessId = <process ID>; Component = Unknown; Operation = Start IWbemServices::ExecQuery - <WMI namespace>: <Select Query Statement>; ResultCode = 0x80041032; PossibleCause = Unknown
where 0x80041032 indicates WBEM_E_CALL_CANCELLED.
[!NOTE]
This event can occur with many different ResultCode values. The problem described in this article only applies whenResultCode = 0x80041032 (WBEM_E_CALL_CANCELLED).
Cause
WMI-Activity Error 5858 with ResultCode = 0x80041032 (WBEM_E_CALL_CANCELLED) indicates that the WMI caller has successfully issued IWbemServices:ExecQuery, but has released the IWbemContext object before retrieving the full result set using the IEnumWbemClassObject::Next method. If the WMI service is still holding data for the client when the client terminates the link (by releasing the IWbemContext object), this event will be logged.
This error can happen if the WMI application calls IEnumWbemClassObject::Next with a timeout value (lTimeout) that is not long enough to retrieve the object being queried, and is not checking for a return code of WBEM_S_TIMEDOUT (0x40004) in order to issue the request again.
Resolution
The WMI client application should be modified to issue calls to IEnumWbemClassObject::Next to retrieve the full result set, before releasing the IWbemContext object. If no objects are received, make sure that the timeout value (lTimeout) is greater than 0 and that WBEM_S_TIMEDOUT (0x40004) is not being returned.
More information
For more information, see:
-
IEnumWbemClassObject interface
[!NOTE]
The sample code included at the end of this page showsIEnumWbemClassObject::Nextbeing called with a timeout value (lTimeout) of 0, and is not checking for the WBEM_S_TIMEDOUT error. -
IWbemServices::ExecQuery method
-
IEnumWbemClassObject::Next method
| title | description | ms.date | author | ms.author | manager | audience | ms.topic | ms.prod | localization_priority | ms.reviewer | ms.custom | ms.technology |
|---|---|---|---|---|---|---|---|---|---|---|---|---|
|
WMI-Activity Event 5858 ResultCode 0x80041032 |
WMI-Activity Event ID 5858 is logged with ResultCode 0x80041032 when applications issue WMI queries. |
09/08/2020 |
Deland-Han |
delhan |
dcscontentpm |
ITPro |
troubleshooting |
windows-client |
medium |
kaushika, steved, cmyu, ssutari |
sap:wmi, csstroubleshoot |
windows-client-system-management-components |
This article provides a resolution to solve the WMI-Activity event ID 5858 that’s logged with ResultCode = 0x80041032 in Windows Server 2012 R2.
Applies to: Windows Server 2012 R2
Original KB number: 3124914
Symptoms
When using Windows Server 2012 R2 with applications that issue WMI queries using IWbemServices:ExecQuery, the administrator may observe the following event in Event Viewer:
Log Name: Microsoft-Windows-WMI-Activity/Operational
Source: WMI-Activity
Event ID: 5858
Level: Error
Id = {guid}; ClientMachine = <computer>; User = <user>; ClientProcessId = <process ID>; Component = Unknown; Operation = Start IWbemServices::ExecQuery - <WMI namespace>: <Select Query Statement>; ResultCode = 0x80041032; PossibleCause = Unknown
where 0x80041032 indicates WBEM_E_CALL_CANCELLED.
[!NOTE]
This event can occur with many different ResultCode values. The problem described in this article only applies whenResultCode = 0x80041032 (WBEM_E_CALL_CANCELLED).
Cause
WMI-Activity Error 5858 with ResultCode = 0x80041032 (WBEM_E_CALL_CANCELLED) indicates that the WMI caller has successfully issued IWbemServices:ExecQuery, but has released the IWbemContext object before retrieving the full result set using the IEnumWbemClassObject::Next method. If the WMI service is still holding data for the client when the client terminates the link (by releasing the IWbemContext object), this event will be logged.
This error can happen if the WMI application calls IEnumWbemClassObject::Next with a timeout value (lTimeout) that is not long enough to retrieve the object being queried, and is not checking for a return code of WBEM_S_TIMEDOUT (0x40004) in order to issue the request again.
Resolution
The WMI client application should be modified to issue calls to IEnumWbemClassObject::Next to retrieve the full result set, before releasing the IWbemContext object. If no objects are received, make sure that the timeout value (lTimeout) is greater than 0 and that WBEM_S_TIMEDOUT (0x40004) is not being returned.
More information
For more information, see:
-
IEnumWbemClassObject interface
[!NOTE]
The sample code included at the end of this page showsIEnumWbemClassObject::Nextbeing called with a timeout value (lTimeout) of 0, and is not checking for the WBEM_S_TIMEDOUT error. -
IWbemServices::ExecQuery method
-
IEnumWbemClassObject::Next method
Windows 10: WMI activity even 5858 and no one seems to know how to fix it
Discus and support WMI activity even 5858 and no one seems to know how to fix it in Windows 10 Network and Sharing to solve the problem; I have been receiving these errors for a very long time on windows 10. My event viewer for the service WMI is completely full of 5858 errors. The only…
Discussion in ‘Windows 10 Network and Sharing’ started by JumpierElf91, Aug 26, 2021.
-
WMI activity even 5858 and no one seems to know how to fix it
I have been receiving these errors for a very long time on windows 10. My event viewer for the service WMI is completely full of 5858 errors. The only fix i haven’t tried is one that no one seems to be able to help me do.https://docs.microsoft.com/de-DE/troubleshoot/windows-client/system-management-components/wmi-activity-event-5858-logged-with-resultcode-0x80041032it explains that I should do the following.The WMI client application should be modified to IEnumWbemClassObject::Nextissue calls to get the full result set before the IWbemContext object is released. If no objec
-
WMI Activity generates event ID 5858 every 15 seconds
WMI Activity generates event ID 5858 every 15 seconds
Errors Are related to Intel CIntelWLANEvent, win32_perfformatteddata_perfdisk_physicaldisk CurrentDiskQueueLength, BIOSEventRan dism Sfc Chkdsk all without error.
Turned off WMI performance adapter Service and the errors ceased
At one point it had reconfigured all my apps
I have created a wmi activity evtx file
Error 11/15/2017 2:18:52 PM WMI-Activity 5858 NoneWindows 10 home Fall creators edition Dell 5567
[Moved from: Windows / Windows 10 / Windows settings]
-
WMI events 5858 on a Windows Server 2016, what to do?
Thanks for your quick reply.
As suggested I created a copy of this question on Technet forum: Technet
copy -
WMI activity even 5858 and no one seems to know how to fix it
Windows not shutting down, caused by Event Error 5858 ? (WMI Activity)
Regularly my pc does not shut down, it gets stuck on the blue screen with «Shutting Down»
After a while I need to shut down the pc, using the power-button on the case.I already untagged «Turn on fast start-up (recommended)»
under Control Panel->All Control Panel Items->Power Options->System Settings under ‘Shut-down settings»Regretfully that did not solve the issue.
I checked the event log between me initiating shutdown (event 1074) and rebooting.
There are quite a number of entries reading like this:
Event : 5858
Source : Microsoft-Windows-WMI-Activity
Description:
Id = {00000000-0000-0000-0000-000000000000}; ClientMachine = DESKTOP-JFFLEA5; User = NT AUTHORITYSYSTEM; ClientProcessId = 2908; Component = Unknown; Operation = Start IWbemServices::ExecQuery — rootwmi : select * from WDMClassesOfDriver where ClassName = «MSStorageDriver_ClassErrorLogEntry»; ResultCode = 80041032; PossibleCause Unknown
—
Event : 5858
Source : Microsoft-Windows-WMI-Activity
Description:
Id = {00000000-0000-0000-0000-000000000000}; ClientMachine = DESKTOP-JFFLEA5; User = NT AUTHORITYSYSTEM; ClientProcessId = 2908; Component = Unknown; Operation = Start IWbemServices::ExecQuery — rootwmi : select * from WMIBinaryMofResource where Name = «USBSTOR\Disk&Ven_WD&Prod_My_Book_1230&Rev_1065\57583231443934374E345956&0_0-{05901221-D566-11d1-B2F0-00A0C9062910}»; ResultCode = 80041032; PossibleCause = Unknown
=Note that I did have external drives running, but they were properly removed (ejected) and then, before shutting down, they were switched/powered off, i.e. they didn’t exist anymore for Windows.
Does anybody out there know how to handle this and what is causing this error?
Any solutions?Thanks!
=
WMI activity even 5858 and no one seems to know how to fix it
-
WMI activity even 5858 and no one seems to know how to fix it — Similar Threads — WMI activity 5858
-
Repeated WMI Error 0x80041032 Event 5858 caused by swiservice.exe, cause «Unknown»
in Windows 10 BSOD Crashes and Debugging
Repeated WMI Error 0x80041032 Event 5858 caused by swiservice.exe, cause «Unknown»: Hi everyoneI came across this while looking into what’s gobbling up CPU power at startup. This is the output from Event Viewer > Applications and Service LogsMicrosoftWindowsWMI-ActivityOperational:Log Name: Microsoft-Windows-WMI-Activity/OperationalSource:… -
Repeated WMI Error 0x80041032 Event 5858 caused by swiservice.exe, cause «Unknown»
in Windows 10 Gaming
Repeated WMI Error 0x80041032 Event 5858 caused by swiservice.exe, cause «Unknown»: Hi everyoneI came across this while looking into what’s gobbling up CPU power at startup. This is the output from Event Viewer > Applications and Service LogsMicrosoftWindowsWMI-ActivityOperational:Log Name: Microsoft-Windows-WMI-Activity/OperationalSource:… -
Repeated WMI Error 0x80041032 Event 5858 caused by swiservice.exe, cause «Unknown»
in Windows 10 Software and Apps
Repeated WMI Error 0x80041032 Event 5858 caused by swiservice.exe, cause «Unknown»: Hi everyoneI came across this while looking into what’s gobbling up CPU power at startup. This is the output from Event Viewer > Applications and Service LogsMicrosoftWindowsWMI-ActivityOperational:Log Name: Microsoft-Windows-WMI-Activity/OperationalSource:… -
Anyone know how to fix this?
in Windows 10 Ask Insider
Anyone know how to fix this?: Since my computer updated to Windows 10 Version 2004 it’s been virtually impossible to play games. Constant black screen crashes on multiple games and even basic stuff like watching Youtube. Been looking around for how to fix this but haven’t found anything and I’m not… -
Anyone know how to fix this?
in Windows 10 Ask Insider
Anyone know how to fix this?: [ATTACH] submitted by /u/Antron_edition
[link] [comments]https://www.reddit.com/r/Windows10/comments/k39blb/anyone_know_how_to_fix_this/
-
WMI issue with event id 5858
in Windows 10 BSOD Crashes and Debugging
WMI issue with event id 5858: I have Windows 10. I have an issue with the CPU usage and it seems to be connected to WMI. It means that my fan is constantly running and the machine seems to be always doing something. I have done a bit of research and have identified that the error seems to be caused by… -
WMI-Activity Error
in Windows 10 Customization
WMI-Activity Error: Hiya, I was having trouble with WMI Provider Host, I googled it and did actually manage to find a thread on here linked below:… -
WMI activity ERROR
in Windows 10 Network and Sharing
WMI activity ERROR: How can I fix the WMI error in Window 10?https://answers.microsoft.com/en-us/windows/forum/all/wmi-activity-error/bd3ec1d0-89a6-48a1-9346-0f54a811fbd0
-
Windows not shutting down, caused by Event Error 5858 ? (WMI Activity)
in Windows 10 Performance & Maintenance
Windows not shutting down, caused by Event Error 5858 ? (WMI Activity): Regularly my pc does not shut down, it gets stuck on the blue screen with «Shutting Down»
After a while I need to shut down the pc, using the power-button on the case.I already untagged «Turn on fast start-up (recommended)»
under Control Panel->All Control Panel…
Users found this page by searching for:
-
wmi-activity event 5858 0x80041013
,
-
event id 5858 wmi-activity

Posted by DDoc 2013-12-10T18:07:47Z
I have a Windows 2012 R2 server that I periodically get several of the below (or similar) messages. Any idea what the issue might be?
Id = {BF062B92-ECEA-46B8-A09F-7E6D6F430BAA}; ClientMachine = ELM; User = ; ClientProcessId = 712; Component = Unknown; Operation = Start IWbemServices::DeleteInstance — RootRsopUserS_1_5_21_719535676_533339174_944726268_1292 : RSOP_ExtensionStatus.extensionGuid=»{0E28E245-9368-4853-AD84-6DA3BA35BB75}»; ResultCode = 0x80041002; PossibleCause = Unknown
1 Reply
lock
This topic has been locked by an administrator and is no longer open for commenting.
To continue this discussion, please ask a new question.
Read these next…
Can’t communicate with scanner
Hardware
Hello everyone,I have a client that uses Kodak ScanMate i940 scanners at their desks. They recently got a new computer that we prepped and put on their domain. This new computer is recognizing the scanner but it is unusable with the error «can’t communica…
Different MAC address, same computer name — multiple DHCP leases
Windows
I’m noticing a lot more now that our Wifi DHCP scopes are filled by the same computer name, but with different mac addresses. I know there’s a feature in Windows 10 called Random hardware addresses, but that setting is off. Is there anything else that cou…
Snap! — No-Password Logins, Solar Powered Water Filter, Glitch in the Matrix?
Spiceworks Originals
Your daily dose of tech news, in brief.
Welcome to the Snap!
Flashback: February 9, 1996: Introduction of the Bandai Pippin (Read more HERE.)
Bonus Flashback: February 9, 1990: Galileo Probe does a Venus Flyby (Read more HERE.)
You nee…
Roku TV being used as Wallboard Issues
Hardware
Helping someone out at their shop. They have 4 large Roku screens and 2 laptops with dual HDMI ports for video. They are viewing static website business dashboards and PowerPoint. At first all 4 screens connected to wireless, worked for a while but with a…
Charging for SSO
Security
We have SSO set up with around 5 or 6 solution providers via our M365. Not one of them charges for this, they just sent us the documentation.I identified another online service in use by one of our departments which would benefit from using SSO for staff …
I recently upgraded my Hyper-V host from Server 2008 R2 to 2012 R2. It’s not domain-joined, and I did an in-place upgrade. Every 11 seconds, I was getting the following error in the Application event log:
Log Name: Application
Source: Microsoft-Windows-WMI
Event ID: 10
Level: Error
User: SYSTEM
Description:
Event filter with query “SELECT * FROM __InstanceOperationEvent WITHIN 10 WHERE (TargetInstance ISA ‘Msvm_ExternalEthernetPort’) OR (TargetInstance ISA ‘Msvm_VmLANEndpoint’) OR (TargetInstance ISA ‘Msvm_SyntheticEthernetPort’) OR (TargetInstance ISA ‘Msvm_ComputerSystem’) OR (TargetInstance ISA ‘Msvm_VLANEndpointSettingData’)” could not be reactivated in namespace “//./root/virtualization” because of error 0×80041010. Events cannot be delivered through this filter until the problem is corrected.
Each section below lists an attempted fix. Jump to the last section for “The Short Answer.”
Network Drivers
Microsoft Partner Support suggested that this might be caused by network drivers. This machine has both Broadcom and Intel NICs. For both, when I tried to update the driver, I got the message, “Windows has determined the driver software for your device is up to date.” Nonetheless, I decided to uninstall and reinstall the drivers to see if it helped.
First I uninstalled the Intel driver, version 6.3.9600.16384. After a reboot, the driver had re-installed itself, but with version 9.6.10.0. The WMI errors continued.
Next I uninstalled the Broadcom driver, version 7.4.23.2. After a reboot, the driver had re-installed itself, but with version 7.4.23.2. The WMI errors continued.
Note that uninstalling the driver causes Hyper-V to lose the NIC association; it reverts to being an Internal network. After the drivers re-installed, I had to go back to the Hyper-V Virtual Switch Manager and re-assign the existing switch to the External network.
WMI Rebuild
Another suggestion was to rebuild the WMI repository. I ran this script from TechNet:
http://blogs.technet.com/b/askperf/archive/2009/04/13/wmi-rebuilding-the-wmi-repository.aspx
After running the script, I ran winmgmt /verifyrepository. The repository is consistent. However, the errors continue every 11 seconds.
Process Monitor
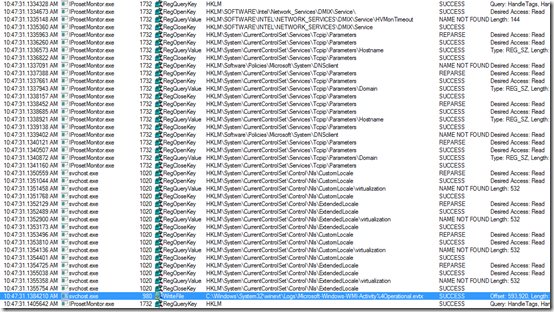
While working on another issue, I ran Process Monitor from Sysinternals. Interesting: there are a lot of references to IProsetMonitor.exe, including unsuccessful attempts to read a “virtualization” key in the registry, followed by writing to a special event log, Microsoft-Windows-WMI-Activity/Operational.
That log is small (1MB) so it only holds about 750 events. There are so many 5858 events being written to that log that it only holds about five seconds worth. It took some fast keyboarding to grab this sample:
Log Name: Microsoft-Windows-WMI-Activity/Operational
Source: Microsoft-Windows-WMI-Activity
Event ID: 5858
Level: Error
User: SYSTEM
Description:
Id = {4C4C4544-0031-0002-EAE0-B8E795DDCE01}; ClientMachine = MYHVSVR; User = NT AUTHORITYSYSTEM; ClientProcessId = 1732; Component = Unknown; Operation = Start IWbemServices::ExecNotificationQuery – rootvirtualization : SELECT * FROM __InstanceOperationEvent WITHIN 10 WHERE (TargetInstance ISA ‘Msvm_ExternalEthernetPort’) OR (TargetInstance ISA ‘Msvm_VmLANEndpoint’) OR (TargetInstance ISA ‘Msvm_SyntheticEthernetPort’) OR (TargetInstance ISA ‘Msvm_ComputerSystem’) OR (TargetInstance ISA ‘Msvm_VLANEndpointSettingData’); ResultCode = 0x80041010;
That “ClientProcessId = 1732” is interesting because it points back to IProsetMonitor.exe in Task Manager:
The Culprit: Intel PROSet Monitoring Service
So finally we know where the error is coming from: the Intel PROSet Monitoring Service. Sure enough, when I stopped that service, it stopped both the 5858 events in the Microsoft-Windows-WMI-Activity event log and the WMI 10 events in the Application event log. Phew! That’s a relief. I bet my system will run better without hundreds of events being written every few seconds.
So I need a version of PROSet that works on 2012 R2.
I tried re-installing the version that was working before (Dell calls is 14.0.0; Intel calls it 17.3.66), but I still get the WMI errors.
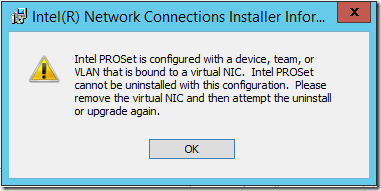
I tried installing the latest from Dell (14.5.1, Intel 18.2.63.0), but that will require deleting my virtual NIC:
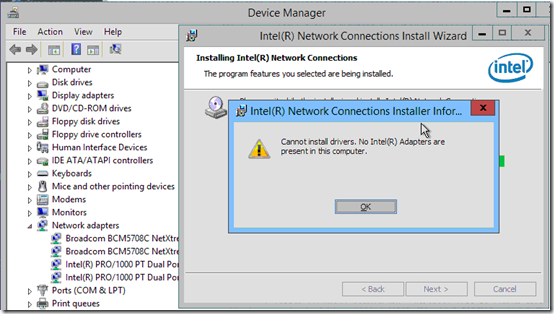
Well if I’m going to do that, maybe I should see if Intel has a later version specifically for 2012 R2. Yup, here’s ProWin64.exe version 18.7 for Server 2012 R2. I tried installing that and it said my computer has no Intel adapters (shown here next to Device Manager listing the Intel adapters):
So I went back to the latest Dell version 14.5.1. that installed okay, but the WMI errors were back.
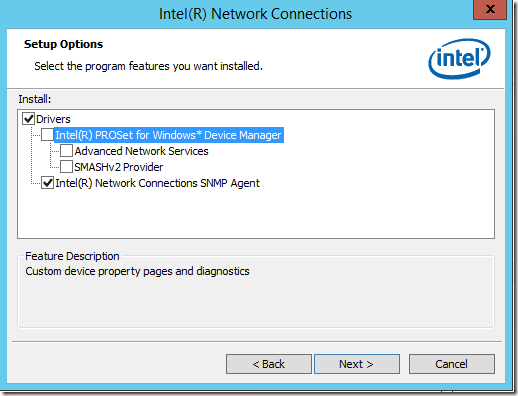
Eventually I found this Intel page about the level of 2012 R2 support for each of their NICs. It turns out that my PRO/1000 PT Server Adapter only has “In Box Support,” which means that PROSet for Windows Device Manager is not included. So I wound up doing a Modify installation on the latest Dell version, leaving only the drivers and the SNMP Agent installed:
In that configuration, PROSet is not active and the WMI errors are not happening.
Re-Activate the Virtual Adapter
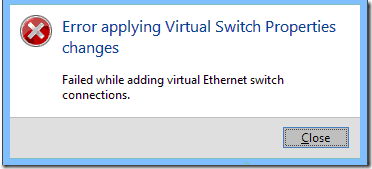
The last step is to re-connect the Hyper-V virtual switch to the physical NIC. After opening the Network Connections (ncpa.cpl) to confirm which NIC is plugged in, I went in to the Hyper-V Virtual Switch Manager and set the old virtual switch to use the “new” external NIC. That led to this message:
Great. How can every little step in setting up a computer be a failure? And why not give a reason for the failure?
Back to Google, I found lots of suggestions. One was to uninstall and re-install the network drivers. I thought I just did that, but I went to Device Manager, told it to uninstall and remove drivers on both Intel NICs, then rebooted.
Before the reboot, the Microsoft NIC driver was at version 9.6.10.0; an attempt to update gave a message that the latest driver is already installed. After the reboot, the Microsoft NIC driver was at version 9.13.41.3. Go figure.
Anyway, the driver uninstall/reinstall didn’t help. I kept getting the “Failed while adding virtual Ethernet switch connections” message.
This article had some low-level details on the errors. I followed the first part of those suggestions, including removing the old virtual switch from all virtual machines, but kept getting the error.
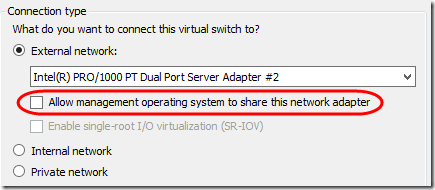
Finally on a whim, I tried unchecking “Allow management operating system to share this network adapter.”
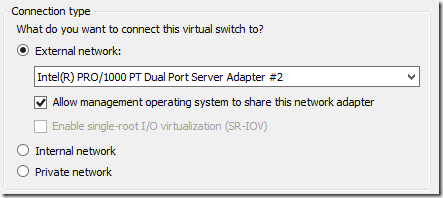
Voila! The virtual switch was created with no problem. Then I went back in and re-enabled management:
That also completed with no problem (other than losing the Remote Desktop session—be sure you have console access).
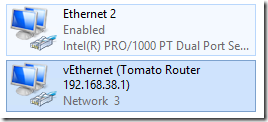
Finally, I went in to the new vEthernet switch and set the machines fixed IP address and DNS servers:
The Short Answer
If you’re getting WMI 10 errors every 11 seconds after a Server 2012 R2 upgrade, try these steps:
- In Event Viewer, go to Applications and Services Logs > Microsoft > Windows > WMI-Activity event log and check for 5858 errors. If you see errors that match the WMI 10 errors in the Application log, use the Process ID from the 5858 event to find out from Task Manager what process is causing the error.
- If IProsetMonitor.exe is causing the error, check this Intel page to see what level of support your NIC has under Server 2012 R2.
- If Full Support is available, you may be able to update your NIC driver. You’ll want to use the full package that includes the PROSet tools. Mine didn’t have full support so this didn’t work for me.
- If only Out of Box support is available, either uninstall the Intel tools entirely and just use the Microsoft driver, or Modify the install to remove PROSet but leave the driver.
If you need to remove and re-create your Hyper-V virtual switch in order to uninstall the driver, see notes in the previous section.
WMI (Windows Management Instrumentation) is the Microsoft implementation of the Web-Based Enterprise Management (WBEM) and Common Information Model (CIM) standards from the Distributed Management Task Force (DMTF). This allows for a unified way to manage a group of systems by administrators allowing them to get information about the system, its current state and to execute actions. Because of this many attackers leverage this for enumeration, lateral movement, and persistence. Defenders and security vendors leverage it heavily also, in fact, most vulnerability scanners would not be able to do a lot of what they do on windows hosts without it.
I wrote the PSGumshoe PowerShell module initially with a group of good friends of mine to help with the job of performing threat hunting and incident response. I maintain the module as my personal tool for working in my research of finding IOCs for the tools I write in my day job for the Red Team and the Pentest Team, also when I help out in some of the incident response engagements.
I would like to share some of the new functions I added to the module for the purpose of tracking some of the WMI activities that attackers may perform once they gained a foothold on the system.
Execution of Methods
In one engagement many years ago I learned that one could track WMI execution of class methods and even queries by enabling Other Object Access audit setting and then on each WMI namespace. A well-versed Windows Admin was able to track my queries and method executions and contain my action by having some well-tuned ingestion filters that alerted on any action which did not fit the normal behavior of the systems in his environment.
When configuring a GPO the setting is under Computer Configuration -> Windows Settings -> Security Settings -> Advanced Audit Policy Configuration -> Audit Policies -> Object Access
Audit Settings
Once the audit setting is set and pushed via GPO a logon script or manual process is needed to set the proper audit settings to track actions on a given namespace. To do this manually:
-
open the WMI Control MMC or Computer Management MMC and open the properties for WMI Control.
-
Select the Security tab, select the namespace to apply the adit settings to, and click on Security
On the next window we click on Advanced.
On the Advanced Security Settings for the namespace we do the following:
-
Click on the Auditing tab
-
Click on Add
In the Audit Entry window, do the following:
-
Select the Principal the rule will apply to, my recommendation would be either Everyone or Authenticated Users.
-
On Type select ALL since we want success and failure events.
-
In Advanced Permission, I would recommend starting with Execute Method to detect class methods for latera movement and Full Write in the case a malicious WMI Provider creates a class or Permanent event components are created outside the root/subscription namespace. Also helpful in detection of WMI used as a C2 Channel http://2014.hackitoergosum.org/slides/day1_WMI_Shell_Andrei_Dumitrescu.pdf
The settings shown will not cover queries, without a process and capability for validating and filtering events before sending them to the SIEM this would be too noisy in a production environment.
Once the settings have been applied any attempt like the one bellow where a locally the Win32_Process class Create() method is used to create a process using WMI to break parent child relation will be logged.
PS C:UsersAdmin> $proc = Get-WmiObject -List win32_process
PS C:UsersAdmin> $proc.Create("notepad.exe")
__GENUS : 2
__CLASS : __PARAMETERS
__SUPERCLASS :
__DYNASTY : __PARAMETERS
__RELPATH :
__PROPERTY_COUNT : 2
__DERIVATION : {}
__SERVER :
__NAMESPACE :
__PATH :
ProcessId : 5908
ReturnValue : 0
PSComputerName :When we examine the logs under Security we will se event with Id 4662 where the ObjectServer will be WMI. The event will include under what namespace the event happened and under what user context. Under AdditinalInformation fields we will see if it was local or remote and the method that was invoked.
Local Method Execution
When a method is executed against the host from a remote system like in the example bellow the log will show that the method was executed remotely.
PS C:UsersAdmin> $remoteproc = Get-WmiObject -List win32_process -ComputerName sddc01
PS C:UsersAdmin> $remoteproc.Create("cmd.exe")
__GENUS : 2
__CLASS : __PARAMETERS
__SUPERCLASS :
__DYNASTY : __PARAMETERS
__RELPATH :
__PROPERTY_COUNT : 2
__DERIVATION : {}
__SERVER :
__NAMESPACE :
__PATH :
ProcessId : 5812
ReturnValue : 0
PSComputerName :We will see under AdditionalInfo that the method execution is Remote Execute.
Remote Method Execution
In PSGumshoe to aid with looking for this types of IOC the Get-EventWmiObjectAccess function is available.
PS C:UsersCarlos PerezDesktop> help Get-EventWmiObjectAccess
NAME
Get-EventWmiObjectAccess
SYNOPSIS
Get WMI Object Access events (EventId 4662).
SYNTAX
Get-EventWmiObjectAccess [-LogName <String>] [-SubjectUserSid <String[]>] [-SubjectUserName <String[]>] [-SubjectDomainName
<String[]>] [-SubjectLogonId <String[]>] [-ObjectName <String[]>] [-AdditionalInfo <String[]>] [-AdditionalInfo2 <String[]>]
[-MaxEvents <Int64>] [-StartTime <DateTime>] [-EndTime <DateTime>] [-ChangeLogic] [<CommonParameters>]
Get-EventWmiObjectAccess [-LogName <String>] [-SubjectUserSid <String[]>] [-SubjectUserName <String[]>] [-SubjectDomainName
<String[]>] [-SubjectLogonId <String[]>] [-ObjectName <String[]>] [-AdditionalInfo <String[]>] [-AdditionalInfo2 <String[]>]
[-Path] <String[]> [-MaxEvents <Int64>] [-StartTime <DateTime>] [-EndTime <DateTime>] [-ChangeLogic] [<CommonParameters>]
Get-EventWmiObjectAccess [-LogName <String>] [-SubjectUserSid <String[]>] [-SubjectUserName <String[]>] [-SubjectDomainName
<String[]>] [-SubjectLogonId <String[]>] [-ObjectName <String[]>] [-AdditionalInfo <String[]>] [-AdditionalInfo2 <String[]>]
-ComputerName <String[]> [-Credential <PSCredential>] [-MaxEvents <Int64>] [-StartTime <DateTime>] [-EndTime <DateTime>]
[-ChangeLogic] [<CommonParameters>]
DESCRIPTION
Get WMI Object Access events (EventId 4662). from a local or remote host. Events can be filtered by fields.
RELATED LINKS
REMARKS
To see the examples, type: "get-help Get-EventWmiObjectAccess -examples".
For more information, type: "get-help Get-EventWmiObjectAccess -detailed".
For technical information, type: "get-help Get-EventWmiObjectAccess -full".As it can be seen in the help information the function allows for the filtering of events by some of the fields and one or more EVTX files can be passed, we can execute the function remotely or locally.
In the example bellow we are looking at a EVTX file that was pulled from a system and we are filtering for Local Execution of methods.
PS C:UsersCarlos PerezDesktop> Get-EventWmiObjectAccess -Path .wmiobjectaccess.evtx -AdditionalInfo "Local Execute (ExecMethod)"
EventId : 4662
Computer : SDDC01.acmelabs.pvt
EventRecordID : 610678
TimeCreated : 3/27/2022 11:15:07 AM
SubjectUserSid : S-1-5-21-2481759486-3878440335-2016164793-1000
SubjectUserName : Admin
SubjectDomainName : acmelabs
SubjectLogonId : 0x2ed6a
ObjectType : WMI Namespace
ObjectName : rootcimv2
AdditionalInfo : Local Execute (ExecMethod)
AdditionalInfo2 : rootcimv2:Win32_Process::Create
EventId : 4662
Computer : SDDC01.acmelabs.pvt
EventRecordID : 610678
TimeCreated : 3/27/2022 11:15:07 AM
SubjectUserSid : S-1-5-21-2481759486-3878440335-2016164793-1000
SubjectUserName : Admin
SubjectDomainName : acmelabs
SubjectLogonId : 0x2ed6a
ObjectType : WMI Namespace
ObjectName : rootcimv2
AdditionalInfo : Local Execute (ExecMethod)
AdditionalInfo2 : rootcimv2:Win32_Process::Create
EventId : 4662
Computer : SDDC01.acmelabs.pvt
EventRecordID : 610678
TimeCreated : 3/27/2022 11:15:07 AM
SubjectUserSid : S-1-5-21-2481759486-3878440335-2016164793-1000
SubjectUserName : Admin
SubjectDomainName : acmelabs
SubjectLogonId : 0x2ed6a
ObjectType : WMI Namespace
ObjectName : rootcimv2
AdditionalInfo : Local Execute (ExecMethod)
AdditionalInfo2 : rootcimv2:Win32_Process::CreateExample passing several EVTX files via the pipeline.
PS C:UsersCarlos PerezDesktop> ls *.evtx | Get-EventWmiObjectAccess -AdditionalInfo "Local Execute (ExecMethod)"
EventId : 4662
Computer : SDDC01.acmelabs.pvt
EventRecordID : 610678
TimeCreated : 3/27/2022 11:15:07 AM
SubjectUserSid : S-1-5-21-2481759486-3878440335-2016164793-1000
SubjectUserName : Admin
SubjectDomainName : acmelabs
SubjectLogonId : 0x2ed6a
ObjectType : WMI Namespace
ObjectName : rootcimv2
AdditionalInfo : Local Execute (ExecMethod)
AdditionalInfo2 : rootcimv2:Win32_Process::Create
EventId : 4662
Computer : SDDC01.acmelabs.pvt
EventRecordID : 610678
TimeCreated : 3/27/2022 11:15:07 AM
SubjectUserSid : S-1-5-21-2481759486-3878440335-2016164793-1000
SubjectUserName : Admin
SubjectDomainName : acmelabs
SubjectLogonId : 0x2ed6a
ObjectType : WMI Namespace
ObjectName : rootcimv2
AdditionalInfo : Local Execute (ExecMethod)
AdditionalInfo2 : rootcimv2:Win32_Process::Create
EventId : 4662
Computer : SDDC01.acmelabs.pvt
EventRecordID : 610678
TimeCreated : 3/27/2022 11:15:07 AM
SubjectUserSid : S-1-5-21-2481759486-3878440335-2016164793-1000
SubjectUserName : Admin
SubjectDomainName : acmelabs
SubjectLogonId : 0x2ed6a
ObjectType : WMI Namespace
ObjectName : rootcimv2
AdditionalInfo : Local Execute (ExecMethod)
AdditionalInfo2 : rootcimv2:Win32_Process::CreateWMI Operation Error Events
In the Microsoft-WMI-Arctivity/Operational log Windows logs all WMI related operation errors by default with Event ID 58585. On a day-to-day operation of Windows and also depending on the software installed on the OS the number of errors is a high one. If a SIEM solution allows for filters before forwarding the logs this will allow for improving the signal-to-noise ratio of the events sent. In the image below we can see that in my lab VM the number of errors is high.
PSGumshoe provides the Get-EventWmiOperationalError function to search and filter the error logs generated. An attacker may commit mistakes or simply do not have permission to perform an action generating an error to be logged. The event will include the computer and PID of the process that generated the even not only locally but also for remote actions.
Just like the other WMI function this function can be ran remotely against another computer, locally or against one or more EVTX files.
PS C:UsersAdmin> help Get-EventWmiOperationFailure
NAME
Get-EventWmiOperationFailure
SYNOPSIS
Get WMI Operation Failure events (EventId 5858).
SYNTAX
Get-EventWmiOperationFailure [-LogName <String>] [-User <String[]>] [-ClientMachine <String[]>] [-ClientProcessId <String[]>]
[-ResultCode <String[]>] [-Operation <String[]>] [-MaxEvents <Int64>] [-StartTime <DateTime>] [-EndTime <DateTime>] [-ChangeLogic]
[<CommonParameters>]
Get-EventWmiOperationFailure [-LogName <String>] [-User <String[]>] [-ClientMachine <String[]>] [-ClientProcessId <String[]>]
[-ResultCode <String[]>] [-Operation <String[]>] [-Path] <String[]> [-MaxEvents <Int64>] [-StartTime <DateTime>] [-EndTime <DateTime>]
[-ChangeLogic] [<CommonParameters>]
Get-EventWmiOperationFailure [-LogName <String>] [-User <String[]>] [-ClientMachine <String[]>] [-ClientProcessId <String[]>]
[-ResultCode <String[]>] [-Operation <String[]>] -ComputerName <String[]> [-Credential <PSCredential>] [-MaxEvents <Int64>] [-StartTime
<DateTime>] [-EndTime <DateTime>] [-ChangeLogic] [<CommonParameters>]
DESCRIPTION
Get WMI Operation Failure events (EventId 5858). from a local or remote host. Events can be filtered by fields.
RELATED LINKS
REMARKS
To see the examples, type: "get-help Get-EventWmiOperationFailure -examples".
For more information, type: "get-help Get-EventWmiOperationFailure -detailed".
For technical information, type: "get-help Get-EventWmiOperationFailure -full".We can query a remote host and look if there are events from others host by grouping by ClientMachine. In this example we can see there are 2 operation errors from SDCL1.
PS C:> Get-EventWmiOperationFailure -ComputerName sddc01 | group clientmachine
Count Name Group
----- ---- -----
490 SDDC01 {@{EventId=5858; Computer=SDDC01.acmelabs.pvt; EventRecordID=14335; TimeCreated=3/28/2022 2:54:11 PM; User=a...
2 SDCL1 {@{EventId=5858; Computer=SDDC01.acmelabs.pvt; EventRecordID=12823; TimeCreated=3/27/2022 8:49:06 PM; User=a...We can query the host so only events that match the suspicious ClientMachine. We can see they miss-spelled the class.
PS C:> Get-EventWmiOperationFailure -ComputerName sddc01 -ClientMachine sdcl1
EventId : 5858
Computer : SDDC01.acmelabs.pvt
EventRecordID : 12823
TimeCreated : 3/27/2022 8:49:06 PM
User : acmelabsAdmin
ClientMachine : SDCL1
ClientProcessId : 8868
Component : Unknown
Operation : Start IWbemServices::ExecQuery - rootcimv2 : select * from win32_proces
ResultCode : 0x80041010
PossibleCause : Unknown
EventId : 5858
Computer : SDDC01.acmelabs.pvt
EventRecordID : 12822
TimeCreated : 3/27/2022 8:48:29 PM
User : acmelabsAdmin
ClientMachine : SDCL1
ClientProcessId : 8868
Component : Unknown
Operation : Start IWbemServices::ExecQuery - rootcimv2 : select * from win32_proces
ResultCode : 0x80041010
PossibleCause : UnknownWe can group by Resultcode, Result code is the error number and we can use the error constant reference from Microsoft documentation to identify any of interest. https://docs.microsoft.com/en-us/windows/win32/wmisdk/wmi-error-constants?redirectedfrom=MSDN
PS C:> Get-EventWmiOperationFailure -ComputerName sddc01 | group -Property resultcode
Count Name Group
----- ---- -----
505 0x80041032 {@{EventId=5858; Computer=SDDC01.acmelabs.pvt; EventRecordID=14381; TimeCreated=3/28/2022 3:26:11 PM; User=a...
2 0x80041010 {@{EventId=5858; Computer=SDDC01.acmelabs.pvt; EventRecordID=12823; TimeCreated=3/27/2022 8:49:06 PM; User=a...
`WMI Provider Loading
WMI Providers for persistence is an old but not widely used technique where an attacker installs a WMI Provider on the system that when there is interaction with the Class or Classes it provides it loads, providing any capability coded into them, executing as SYSTEM. Casey Smith created and then removed the first public POC of the technique openly shared, followed by Jared Atkinson made a POC also public https://github.com/jaredcatkinson/EvilNetConnectionWMIProvider discussion of the technique has also been seen in some hacker forums but I’m not aware of its use in the wild.
When a provider is loaded and Event ID of 5857 in Microsoft-Windows-WMI-Activity/Operational will be created. The important field are the ProvierPath and the TimeCreated, since this can can be correlated to build a timeline of possible classes accessed since the provider will only be loaded when the wmiiprvse.exe needs the class to perform the requested action.
PsGumshoe provides the Get-EventWmiProviderStart function to query for this events.
PS C:> Get-EventWmiProviderStart | group hostprocess
Count Name Group
----- ---- -----
874 wmiprvse.exe {@{EventId=5857; Computer=SDCL1.acmelabs.pvt; EventRecordID=3406; TimeCreated=3/28/2022 10:22:19 AM; Provide...
PS C:UsersAdminDownloadsPSGumshoe-masterPSGumshoe-master> help Get-EventWmiProviderStart
NAME
Get-EventWmiProviderStart
SYNOPSIS
Get WMI Provider Start events (EventId 5857).
SYNTAX
Get-EventWmiProviderStart [-LogName <String>] [-ProviderName <String[]>] [-ProviderPath <String[]>] [-MaxEvents <Int64>] [-StartTime
<DateTime>] [-EndTime <DateTime>] [-ChangeLogic] [<CommonParameters>]
Get-EventWmiProviderStart [-LogName <String>] [-ProviderName <String[]>] [-ProviderPath <String[]>] [-Path] <String[]> [-MaxEvents
<Int64>] [-StartTime <DateTime>] [-EndTime <DateTime>] [-ChangeLogic] [<CommonParameters>]
Get-EventWmiProviderStart [-LogName <String>] [-ProviderName <String[]>] [-ProviderPath <String[]>] -ComputerName <String[]> [-Credential
<PSCredential>] [-MaxEvents <Int64>] [-StartTime <DateTime>] [-EndTime <DateTime>] [-ChangeLogic] [<CommonParameters>]
DESCRIPTION
Get WMI Provider Start events (EventId 5857). from a local or remote host. Events can be filtered by fields.
RELATED LINKS
REMARKS
To see the examples, type: "get-help Get-EventWmiProviderStart -examples".
For more information, type: "get-help Get-EventWmiProviderStart -detailed".
For technical information, type: "get-help Get-EventWmiProviderStart -full".Here is an example to see how many times each provider has been loaded, this may help in identifying suspicious providers in use.
PS C:> Get-EventWmiProviderStart | group providerpath | select count,name
Count Name
----- ----
129 C:WindowsSystem32wbemkrnlprov.dll
216 %systemroot%system32wbemwmipcima.dll
319 %systemroot%system32wbemcimwin32.dll
31 %SystemRoot%System32Win32_DeviceGuard.dll
31 C:WindowsSystem32wbemWin32_TPM.dll
32 C:WindowsSystem32wbemWmiPerfClass.dll
31 %SystemRoot%system32tscfgwmi.dll
41 %SystemRoot%System32sppwmi.dll
34 %systemroot%system32wbemwmiprov.dll
2 %systemroot%system32wbemstdprov.dll
2 %systemroot%system32umpowmi.dll
2 %SystemRoot%System32storagewmi.dll
2 %systemroot%system32wbemvdswmi.dll
2 C:WindowsSystem32wbemWmiPerfInst.dllWMI Permanent Events
WMI permanent events have been abused since the Windows 2000/XP days when they were first introduced as a method of persistence or taking an action when some type of event happened on a system. For the purpose of this blogpost I will only cover what a Permanent Event Subscription is in general terms, enough to understand what is being logged.
Permanent events are made of 3 components:
-
Filter – WQL Query for the events we want.
-
Consumer – An action to take upon triggering the filter
-
Binding – Registers a Filter to a Consumer.
Each component is an instance of a class that is created and stored inside the CIM database (objects.data) under the root or root/subscription namespace. When the consumer is executed the action is run as SYSTEM under the context of wmiprvse.exe. They do take a bit more effort since we have to build each part individually and saved it in the CIM database, but most attackers simply automate the process. Its limitation is that only a small set of consumer actions are available.
-
ActiveScriptEventConsumer — Executes a predefined script in an arbitrary scripting language when an event is delivered to it. This consumer is available on Windows 2000 and above.
-
CommandLineEventConsumer — Launches an arbitrary process in the local system context when an event is delivered to it. This consumer is available on Windows XP and above.
-
LogFileEventConsumer — Writes customized strings to a text log file when events are delivered to it. This consumer is available on Windows XP and above.
-
NTEventLogEventConsumer — Logs a specific message to the Windows NT event log when an event is delivered to it. This consumer is available on Windows XP and above.
-
SMTPEventConsumer — Sends an email message using SMTP every time that an event is delivered to it. This consumer is available on Windows 2000 and above.
For the Event Filter object, a query is created that monitors for intrinsic or extrinsic events in the WMI CIM database, these can be the creation, modification, or deletion of any class instance or subscribing to a provider that will generate an event for certain actions.
When a __EventFilter, and any of the consumer type class objects are used in the creation of a Binder instance in the WMI CIM Database to create a permanent event a eventlog entry with Id 5861 in Microsoft-Windows-WMI-Activity/Operational is created by default without any auditing needing to be enabled. The event is also created in modification if any of the component class instances are modified. The event will contain all the information associated with the permanent even in the UserData element under the PossibleCause subelement.
If we are using Sysmon and it is configured to capture WMI events each component being created will be captured. Sysmon provides the advantage of targeting the change to a filter or consumer that is already bound together so as to blend into an environment. APT28 has been seen modifying already existing consumers and filters in a target environment. Bellow is a configuration that will capture all events.
<Sysmon schemaversion="4.81">
<HashAlgorithms>sha1</HashAlgorithms>
<CheckRevocation/>
<EventFiltering>
<!-- Capture all WMI actions. -->
<RuleGroup name="WMI Actions" groupRelation="or">
<WmiEvent onmatch="exclude">
</WmiEvent>
</RuleGroup>
</EventFiltering>
</Sysmon>
In the following example we will create each component using PowerShell, the permanent event will detect when a USB device is plugged and copy to the device an executable and set a autorun.ini on the device.
We will start by creating an Event Filter instance that will trigger when a removable volume is added to the host.
##############################
# Filter for removable drive #
##############################
#Creating a new event filter
$RemovableDrvFilter = ([wmiclass]"\.rootsubscription:__EventFilter").CreateInstance()
# Set the properties of the instance
$RemovableDrvFilter.QueryLanguage = 'WQL'
$RemovableDrvFilter.Query = "SELECT * FROM __InstanceCreationEvent WITHIN 2 WHERE
TargetInstance ISA 'Win32_Volume' AND
TargetInstance.DriveType=2"
$RemovableDrvFilter.Name = "USBDrvFilter"
$RemovableDrvFilter.EventNamespace = 'rootcimv2'
# Sets the intance in the namespace
$FilterResult = $RemovableDrvFilter.Put()
$USBFilterObj = $FilterResult.PathWe can see that the action was logged under the Sysmon log with Event ID 19, it contains all parts of the filter event and the action is Created.
PSGumshoe has the Get-SysmonWmiFilter that allows for querying for this event and returns the results as an object we can work with.
PS C:> Get-SysmonWmiFilter -ComputerName sddc01
EventId : 19
EventType : WmiFilterEvent
Computer : SDDC01.acmelabs.pvt
EventRecordID : 273
RuleName : -
UtcTime : 2022-03-29 19:17:40.993
Operation : Created
User : acmelabsAdmin
EventNamespace : "root\cimv2"
Name : "USBDrvFilter"
Query : "SELECT * FROM __InstanceCreationEvent WITHIN 2 WHEREn TargetInstance ISA 'Win32_Volume' ANDn
TargetInstance.DriveType=2"An attacker as mentioned before, can modify an existing event filter and replace the query. Sysmon is able to track this change. Let’s Change the query so there are no newlines in it.
PS C:> $filters = Get-WmiObject -Namespace root/subscription -Class __eventfilter
PS C:> $filters | Set-WmiInstance -Arguments @{Query="SELECT * FROM __InstanceCreationEvent WITHIN 2 WHERE TargetInstance ISA 'Win32_Volume' AND TargetInstance.DriveType=2"}
__GENUS : 2
__CLASS : __EventFilter
__SUPERCLASS : __IndicationRelated
__DYNASTY : __SystemClass
__RELPATH : __EventFilter.Name="SCM Event Log Filter"
__PROPERTY_COUNT : 6
__DERIVATION : {__IndicationRelated, __SystemClass}
__SERVER : SDDC01
__NAMESPACE : ROOTsubscription
__PATH : \SDDC01ROOTsubscription:__EventFilter.Name="SCM Event Log Filter"
CreatorSID : {1, 2, 0, 0...}
EventAccess :
EventNamespace : rootcimv2
Name : SCM Event Log Filter
Query : SELECT * FROM __InstanceCreationEvent WITHIN 2 WHERE TargetInstance ISA 'Win32_Volume' AND
TargetInstance.DriveType=2
QueryLanguage : WQL
PSComputerName : SDDC01
__GENUS : 2
__CLASS : __EventFilter
__SUPERCLASS : __IndicationRelated
__DYNASTY : __SystemClass
__RELPATH : __EventFilter.Name="USBDrvFilter"
__PROPERTY_COUNT : 6
__DERIVATION : {__IndicationRelated, __SystemClass}
__SERVER : SDDC01
__NAMESPACE : ROOTsubscription
__PATH : \SDDC01ROOTsubscription:__EventFilter.Name="USBDrvFilter"
CreatorSID : {1, 5, 0, 0...}
EventAccess :
EventNamespace : rootcimv2
Name : USBDrvFilter
Query : SELECT * FROM __InstanceCreationEvent WITHIN 2 WHERE TargetInstance ISA 'Win32_Volume' AND
TargetInstance.DriveType=2
QueryLanguage : WQL
PSComputerName : SDDC01As we can see Sysmon logged the change with the same ID but the operation stated that it was modified.
The functions in PSGumshoe allow for filtering by field, so we can query for only the modied events. We see that Sysmon creates 2 events one with the instance before the changes and another with how the instance now looks.
PS C:> Get-SysmonWmiFilter -ComputerName sddc01 -Operation modified
EventId : 19
EventType : WmiFilterEvent
Computer : SDDC01.acmelabs.pvt
EventRecordID : 282
RuleName : -
UtcTime : 2022-03-29 20:00:55.044
Operation : Modified
User : acmelabsAdmin
EventNamespace : "root\cimv2"
Name : "USBDrvFilter"
Query : "SELECT * FROM __InstanceCreationEvent WITHIN 2 WHEREn TargetInstance ISA 'Win32_Volume' ANDn
TargetInstance.DriveType=2"
EventId : 19
EventType : WmiFilterEvent
Computer : SDDC01.acmelabs.pvt
EventRecordID : 281
RuleName : -
UtcTime : 2022-03-29 20:00:55.044
Operation : Modified
User : BUILTINAdministrators
EventNamespace : "root\cimv2"
Name : "SCM Event Log Filter"
Query : "SELECT * FROM __InstanceCreationEvent WITHIN 2 WHERE TargetInstance ISA 'Win32_Volume' AND TargetInstance.DriveType=2"Now we will create a Consumer instance, this consumer will be of type Action Script that will execute a VBScript Script that will Base64 decode a binary and store it on the removable drive, it will also create an autorun.ini and modify it so it is hidden on the drive.
$ScriptConsumer = ([wmiclass]"\.rootsubscription:ActiveScriptEventConsumer").CreateInstance()
$ScriptConsumer.Name = 'AutoRun'
$ScriptConsumer.ScriptText = '
Function Base64Decode(ByVal base64String)
Const Base64 = "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/"
Dim dataLength, sOut, groupBegin
base64String = Replace(base64String, vbCrLf, "")
base64String = Replace(base64String, vbTab, "")
base64String = Replace(base64String, " ", "")
dataLength = Len(base64String)
If dataLength Mod 4 <> 0 Then
Err.Raise 1, "Base64Decode", "Bad Base64 string."
Exit Function
End If
For groupBegin = 1 To dataLength Step 4
Dim numDataBytes, CharCounter, thisChar, thisData, nGroup, pOut
numDataBytes = 3
nGroup = 0
For CharCounter = 0 To 3
thisChar = Mid(base64String, groupBegin + CharCounter, 1)
If thisChar = "=" Then
numDataBytes = numDataBytes - 1
thisData = 0
Else
thisData = InStr(1, Base64, thisChar, vbBinaryCompare) - 1
End If
If thisData = -1 Then
Err.Raise 2, "Base64Decode", "Bad character In Base64 string."
Exit Function
End If
nGroup = 64 * nGroup + thisData
Next
nGroup = Hex(nGroup)
nGroup = String(6 - Len(nGroup), "0") & nGroup
pOut = Chr(CByte("&H" & Mid(nGroup, 1, 2))) + _
Chr(CByte("&H" & Mid(nGroup, 3, 2))) + _
Chr(CByte("&H" & Mid(nGroup, 5, 2)))
sOut = sOut & Left(pOut, numDataBytes)
Next
Base64Decode = sOut
End Function
Set objFSO=CreateObject("Scripting.FileSystemObject")
payContent = Base64Decode("SSdtIGEgZXZpbCBwYXlsb2Fk")
Set objPayload = objFSO.CreateTextFile("D:payload.exe",True)
objPayload.Write payContent
objPayload.Close
outFile= TargetEvent.TargetInstance.DriveLetter & "autorun.inf"
Set objFile = objFSO.CreateTextFile(outFile,True)
objFile.WriteLine("[AutoRun]")
payloadpath = "shellexecute=" & TargetEvent.TargetInstance.DriveLetter & "payload.exe"
objFile.WriteLine(payloadpath)
objFile.WriteLine("UseAutoPlay=1")
objFile.Close
Set autoRunsFile = objFSO.GetFile(outFile)
autoRunsFile.attributes = 2
'
$ScriptConsumer.ScriptingEngine = 'VBScript'
$scriptResult = $ScriptConsumer.Put()
$scriptObj = $scriptResult.PathThis action will be logged by Sysmon with Event ID 20 and will contain the entire script from the ActioScript consumer.
We can query for the event with the function Get-SysmonWmiConsumer to query for the events. Sysmon only logs Action Script and CommandLine event consumers only, the other consumers are not logged since they are not considered a security risk.
PS C:> Get-SysmonWmiConsumer -ComputerName sddc01
EventId : 20
EventType : WmiConsumerEvent
Computer : SDDC01.acmelabs.pvt
EventRecordID : 289
RuleName : -
UtcTime : 2022-03-29 20:51:56.053
Operation : Created
User : acmelabsAdmin
Name : "AutoRun"
Type : Script
Destination : "n Function Base64Decode(ByVal base64String)nn Const Base64 =
"ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/"n Dim dataLength, sOut, groupBeginn n
base64String = Replace(base64String, vbCrLf, "")n base64String = Replace(base64String, vbTab, "")n base64String =
Replace(base64String, " ", "")n nn dataLength = Len(base64String)n If dataLength Mod 4 <> 0 Thenn Err.Raise
1, "Base64Decode", "Bad Base64 string."n Exit Functionn End Ifn nn For groupBegin = 1 To dataLength Step
4n Dim numDataBytes, CharCounter, thisChar, thisData, nGroup, pOutnn numDataBytes = 3n nGroup = 0n For
CharCounter = 0 To 3nn thisChar = Mid(base64String, groupBegin + CharCounter, 1)n If thisChar = "=" Thenn
numDataBytes = numDataBytes - 1n thisData = 0n Elsen thisData = InStr(1, Base64, thisChar,
vbBinaryCompare) - 1n End Ifn If thisData = -1 Thenn Err.Raise 2, "Base64Decode", "Bad character In
Base64 string."n Exit Functionn End Ifn nGroup = 64 * nGroup + thisDatan Nextn nn nGroup
= Hex(nGroup)n nn nGroup = String(6 - Len(nGroup), "0") & nGroupn nn pOut = Chr(CByte("&H" & Mid(nGroup,
1, 2))) + _n Chr(CByte("&H" & Mid(nGroup, 3, 2))) + _n Chr(CByte("&H" & Mid(nGroup, 5, 2)))n nn
sOut = sOut & Left(pOut, numDataBytes)n Nextn Base64Decode = sOutnEnd FunctionnnSet
objFSO=CreateObject("Scripting.FileSystemObject")nnpayContent = Base64Decode("SSdtIGEgZXZpbCBwYXlsb2Fk")nSet objPayload
= objFSO.CreateTextFile("D:\payload.exe",True)nobjPayload.Write payContentnobjPayload.ClosennoutFile=
TargetEvent.TargetInstance.DriveLetter & "\autorun.inf"nSet objFile =
objFSO.CreateTextFile(outFile,True)nobjFile.WriteLine("[AutoRun]")npayloadpath = "shellexecute=" &
TargetEvent.TargetInstance.DriveLetter &
"\payload.exe"nobjFile.WriteLine(payloadpath)nobjFile.WriteLine("UseAutoPlay=1")nobjFile.ClosenSet autoRunsFile =
objFSO.GetFile(outFile)nautoRunsFile.attributes = 2nn"To make bound the filter with the consumer we need to create a Binder instance that references both together. It can be created in the Root namespace or in Root/Subscription. Let’s create first an instance in the Root/Subscription namespace that is the default one for this type of instance.
$instanceBinding = ([wmiclass]"\.rootsubscription:__FilterToConsumerBinding").CreateInstance()
$instanceBinding.Filter = $USBFilterObj
$instanceBinding.Consumer = $scriptObj
$result = $instanceBinding.Put()
$newBinding = $result.PathWindows will log all Binding events with the entire information for each part as part of its event under event ID 5861
We can query for this event with the Get-EventWmiPermanentEvent function.
PS C:> Get-EventWmiPermanentEvent -Computername sddc01
EventId : 5861
Computer : SDDC01.acmelabs.pvt
EventRecordID : 14820
TimeCreated : 3/29/2022 5:15:16 PM
Namespace : //./root/subscription
Filter : USBDrvFilter
Consumer : ActiveScriptEventConsumer="AutoRun"
Binder : Binding EventFilter:
instance of __EventFilter
{
CreatorSID = {1, 5, 0, 0, 0, 0, 0, 5, 21, 0, 0, 0, 254, 164, 236, 147, 143, 77, 44, 231, 185, 59, 44, 120, 232, 3, 0, 0};
EventNamespace = "root\cimv2";
Name = "USBDrvFilter";
Query = "SELECT * FROM __InstanceCreationEvent WITHIN 2 WHERE TargetInstance ISA 'Win32_Volume' AND
TargetInstance.DriveType=2";
QueryLanguage = "WQL";
};
Perm. Consumer:
instance of ActiveScriptEventConsumer
{
CreatorSID = {1, 5, 0, 0, 0, 0, 0, 5, 21, 0, 0, 0, 254, 164, 236, 147, 143, 77, 44, 231, 185, 59, 44, 120, 232, 3, 0, 0};
Name = "AutoRun";
ScriptingEngine = "VBScript";
ScriptText = "n Function Base64Decode(ByVal base64String)nn Const Base64 =
"ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/"n Dim dataLength, sOut, groupBeginn n
base64String = Replace(base64String, vbCrLf, "")n base64String = Replace(base64String, vbTab, "")n base64String =
Replace(base64String, " ", "")n nn dataLength = Len(base64String)n If dataLength Mod 4 <> 0 Thenn Err.Raise
1, "Base64Decode", "Bad Base64 string."n Exit Functionn End Ifn nn For groupBegin = 1 To dataLength Step
4n Dim numDataBytes, CharCounter, thisChar, thisData, nGroup, pOutnn numDataBytes = 3n nGroup = 0n For
CharCounter = 0 To 3nn thisChar = Mid(base64String, groupBegin + CharCounter, 1)n If thisChar = "=" Thenn
numDataBytes = numDataBytes - 1n thisData = 0n Elsen thisData = InStr(1, Base64, thisChar,
vbBinaryCompare) - 1n End Ifn If thisData = -1 Thenn Err.Raise 2, "Base64Decode", "Bad character In
Base64 string."n Exit Functionn End Ifn nGroup = 64 * nGroup + thisDatan Nextn nn nGroup
= Hex(nGroup)n nn nGroup = String(6 - Len(nGroup), "0") & nGroupn nn pOut = Chr(CByte("&H" & Mid(nGroup,
1, 2))) + _n Chr(CByte("&H" & Mid(nGroup, 3, 2))) + _n Chr(CByte("&H" & Mid(nGroup, 5, 2)))n nn
sOut = sOut & Left(pOut, numDataBytes)n Nextn Base64Decode = sOutnEnd FunctionnnSet
objFSO=CreateObject("Scripting.FileSystemObject")nnpayContent = Base64Decode("SSdtIGEgZXZpbCBwYXlsb2Fk")nSet objPayload
= objFSO.CreateTextFile("D:\payload.exe",True)nobjPayload.Write payContentnobjPayload.ClosennoutFile=
TargetEvent.TargetInstance.DriveLetter & "\autorun.inf"nSet objFile =
objFSO.CreateTextFile(outFile,True)nobjFile.WriteLine("[AutoRun]")npayloadpath = "shellexecute=" &
TargetEvent.TargetInstance.DriveLetter &
"\payload.exe"nobjFile.WriteLine(payloadpath)nobjFile.WriteLine("UseAutoPlay=1")nobjFile.ClosenSet autoRunsFile =
objFSO.GetFile(outFile)nautoRunsFile.attributes = 2nn";
};Sysmon will also log the event as event ID 21 but will simply reference the path of each component. We can query for the event with the Get-SysmonWmiBinding function.
Creating the binding event in Root will bypass both WMI-Activity and Sysmon, it is important to know this and in the case of suspicious processes under wmiprvse.exe to check also in the root path for possible permanent events that may be hidden.
PS C:> Get-CimInstance -ClassName __FilterToConsumerBinding -Namespace root
Consumer : ActiveScriptEventConsumer (Name = "AutoRun")
CreatorSID : {1, 5, 0, 0...}
DeliverSynchronously : False
DeliveryQoS :
Filter : __EventFilter (Name = "USBDrvFilter")
MaintainSecurityContext : False
SlowDownProviders : False
PSComputerName :Temporary Events
Some actors have moved to use temporary event consumers. They can be written in C++, .Net, WSH and PowerShell, they allow the use of WMI Event filters to trigger an action that is executed by the application itself. The biggest advantage is that we can leverage the capabilities of the language used to write the temporary event and not be limited to only Windows Scripting Host and Command-Line tools. We can track these events with event Id 5860. Once the application registers the Event Consumer the event is created. Sysmon does not offer detection of this type of event.
Here is an example in PowerShell of a temporary event consumer that simply writes the name of a process that has been launched.
# Query for new process events
$queryCreate = "SELECT * FROM __InstanceCreationEvent WITHIN 5" +
"WHERE TargetInstance ISA 'Win32_Process'"
# Create an Action
$CrateAction = {
$name = $event.SourceEventArgs.NewEvent.TargetInstance.name
write-host "Process $($name) was created."
}
# Register WMI event
Register-WMIEvent -Query $queryCreate -Action $CrateActionWhen the Event Consumer is registered with Register-WmiEvent we get the following event logged on the system.
We can use the function Get-EventWmiTemporaryEvent to query for this event. We will see that this type of event is used a lot inside of Windows.
PS C:> Get-EventWmiTemporaryEvent -ComputerName sddc01
EventId : 5860
Computer : SDDC01.acmelabs.pvt
EventRecordID : 14823
TimeCreated : 3/29/2022 5:49:28 PM
ClientMachine : SDDC01
Namespace : rootcimv2
Query : SELECT * FROM __InstanceCreationEvent WITHIN 5WHERE TargetInstance ISA 'Win32_Process'
ProcessId : 3628
PossibleCause : Temporary
EventId : 5860
Computer : SDDC01.acmelabs.pvt
EventRecordID : 14787
TimeCreated : 3/29/2022 12:51:09 AM
User :
ClientMachine : SDDC01
Namespace : ROOTCIMV2
Query : SELECT * FROM Win32_ProcessStartTrace WHERE ProcessName = 'wsmprovhost.exe'
ProcessId : 1380
PossibleCause : Temporary
EventId : 5860
Computer : SDDC01.acmelabs.pvt
EventRecordID : 14652
TimeCreated : 3/28/2022 6:19:55 PM
User :
ClientMachine : SDDC01
Namespace : ROOTSubscription
Query : SELECT * FROM __InstanceOperationEvent WITHIN 5WHERE TargetInstance ISA '__EventConsumer' OR TargetInstance ISA
'__EventFilter' OR TargetInstance ISA '__FilterToConsumerBinding'
ProcessId : 5992
PossibleCause : Temporary
EventId : 5860
Computer : SDDC01.acmelabs.pvt
EventRecordID : 13379
TimeCreated : 3/28/2022 3:31:38 AM
User :
ClientMachine : SDDC01
Namespace : ROOTCIMV2
Query : SELECT * FROM Win32_ProcessStartTrace WHERE ProcessName = 'wsmprovhost.exe'
ProcessId : 1380
PossibleCause : Temporarywe can pipe the objects in to Out-GridView to better visualize the output.
We can see that there is a query that looks for creation of instances for the classes that make up Permanent Evtn. We can see that the PID of the process is 5992, when we look at the process we see that the Sysmon service is running this subscription.
PS C:> Get-Process -PID 5992
Handles NPM(K) PM(K) WS(K) CPU(s) Id SI ProcessName
------- ------ ----- ----- ------ -- -- -----------
227 12 2964 10748 0.06 5992 0 SysmonConclusion
PSGumshoe PowerShell module offers great flexibility when investigating WMI type events generated by Windows and from Sysmon. The module is available in the PowerShell gallery and on GitHub


 И то не факт, что таких ошибок не будет вовсе.
И то не факт, что таких ошибок не будет вовсе.